Selfishness in Vehicular Delay-Tolerant Networks: A Review
Abstract
1. Introduction
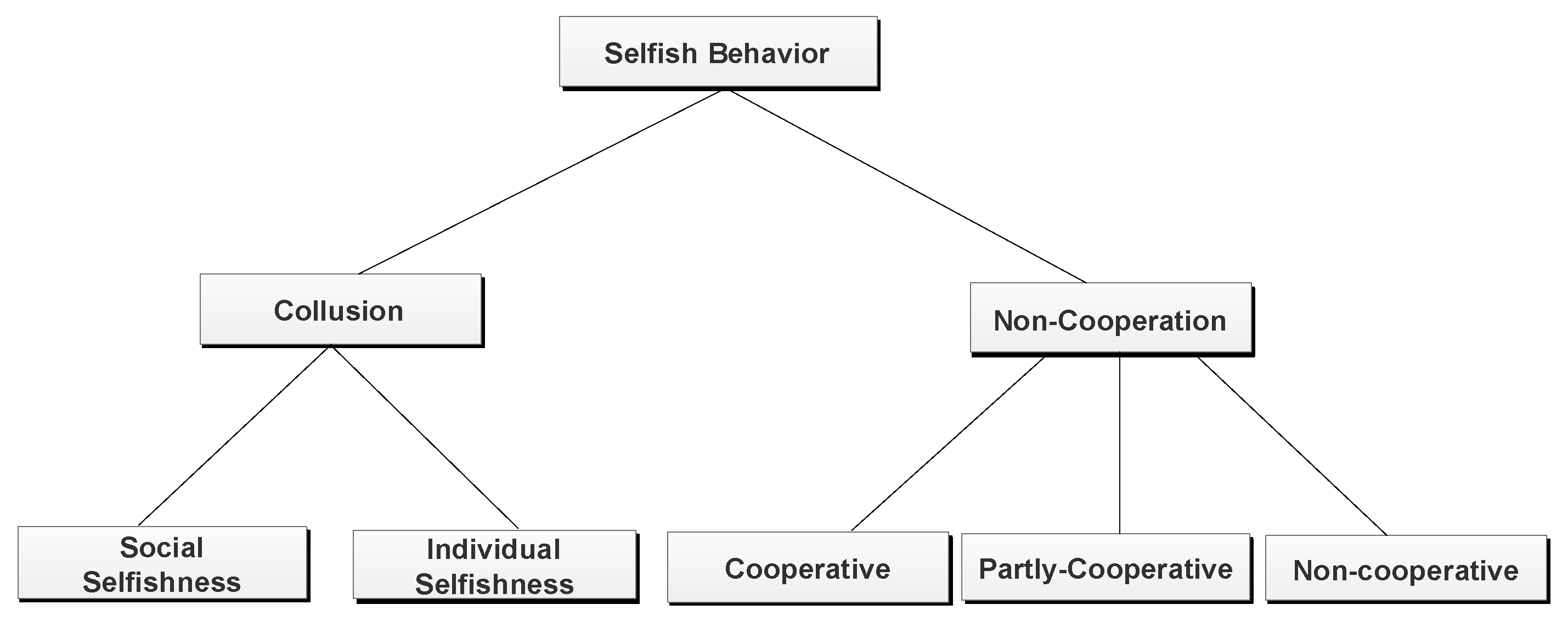
- Classified the selfish behavior of nodes into two different types, namely, collusion and non-cooperation.
- Classified different incentive schemes into four different types, namely, credit-based, reputation-based, barter-based system, and game-theoretic incentive schemes with advantages and disadvantages have been analyzed.
- The related work in different incentive techniques has been categorized and its contributions have been summarized.
- The selected techniques are compared on the basis of different parameters, namely, cost, approach, detection of nodes, scalability, applicability, detection accuracy, buffer consumption, etc.
- Future directions have been identified for the selfish behavior of nodes in VDTNs.
2. Background
3. Methods
3.1. Incentive Techniques
Credit-Based Schemes
3.2. Reputation-Based Schemes
3.3. Barter-Based Schemes
3.4. Game-Theoretic Schemes
4. Discussion
5. Conclusions and Future Research Directions
- More parameters should be analyzed in the study in addition to cost, buffer consumption, and detection accuracy.
- The fair exchange principle greatly improves the cooperation ratio accomplished by the barter-based system. However, sometimes it is very challenging for the connected nodes to reach the level of complete fair exchange principle. Therefore, it is very tough for the connected nodes to make an arrangement during rounds of bargaining. This incomplete agreement between two nodes could waste the valuable resources of the nodes like power, energy, and bandwidth. In what manner the round bargaining problem should be tackled remains an ongoing problem.
- There are always selfish and malicious nodes in the network. The main challenge is not to detect the selfish behavior of the nodes but to identify all those packets which are malicious in nature.
- The preventive algorithm should be designed to prevent the nodes from overusing its limited resources.
- Security impeachment is also a very serious issue and we should consider it. Such security threats have a negative impact on these networks and some solutions must be presented to reduce its negative impact.
- Selfish behavior such as maximizing its own performance, saving buffer, CPU time, and memory are discussed in the literature. However, still there are types of selfish behavior such as plotting and scheming, self-centeredness, and manipulation are completely ignored.
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Mao, Y.; Zhou, C.; Ling, Y.; Lloret, J. An optimized probabilistic delay tolerant network (DTN) routing protocol based on scheduling mechanism for internet of things (IoT). Sensors 2019, 19, 243. [Google Scholar] [CrossRef] [PubMed]
- Zhang, J.; Wang, G.; Liu, C.; Zhao, F.; Zhang, X. Delay-Tolerant Network and the Algorithms of DTN Routing. J. Phys. Conf. Ser. IOP Publ. 2019, 1169, 012058. [Google Scholar] [CrossRef]
- Puri, P.; Singh, M.P. A survey paper on routing in delay-tolerant networks. In Proceedings of the IEEE International Conference on Information Systems and Computer Networks, Mathura, India, 9–10 March 2013; pp. 215–220. [Google Scholar]
- Sobin, C.C.; Raychoudhury, V.; Marfia, G.; Singla, A. A survey of routing and data dissemination in delay tolerant networks. J. Netw. Comput. Appl. 2016, 67, 128–146. [Google Scholar]
- Almelu, S.; Deen, A.J.; Silakari, S. Delay tolerant network routing protocol: A comprehensive survey with hybrid technique. Int. J. Res. Eng. Technol. 2015, 4, 481–487. [Google Scholar]
- Spaho, E. Energy consumption analysis of different routing protocols in a Delay-Tolerant Network. J. Ambient. Intell. Humaniz. Comput. 2019, 1–7. [Google Scholar] [CrossRef]
- Fall, K. Retrospective on a delay-tolerant network architecture for challenged internets. ACM SIGCOMM Comput. Commun. Rev. 2019, 49, 75–76. [Google Scholar] [CrossRef]
- Basilico, N.; Cesana, M.; Gatti, N. Algorithms to find two-hop routing policies in multiclass delay tolerant networks. IEEE Trans. Wirel. Commun. 2016, 15, 4017–4031. [Google Scholar] [CrossRef]
- Li, F.; Jiang, H.; Li, H.; Cheng, Y.; Wang, Y. SEBAR: Social-energy-based routing for mobile social delay-tolerant networks. IEEE Trans. Veh. Technol. 2017, 66, 7195–7206. [Google Scholar] [CrossRef]
- Sakai, K.; Sun, M.T.; Ku, W.S.; Wu, J.; Alanazi, F.S. Performance and security analyses of onion-based anonymous routing for delay tolerant networks. IEEE Trans. Mob. Comput. 2017, 16, 3473–3487. [Google Scholar] [CrossRef]
- Zeadally, S.; Guerrero, J.; Contreras, J. A tutorial survey on vehicle-to-vehicle communications. Telecommun. Syst. 2020, 73, 469–489. [Google Scholar] [CrossRef]
- Abbasi, I.A.; Khan, A.S.; Ali, S. Dynamic multiple junction selection based routing protocol for VANETs in city environment. Appl. Sci. 2018, 8, 687. [Google Scholar] [CrossRef]
- Abbasi, I.A.; Shahid, K.A. A review of vehicle to vehicle communication protocols for VANETs in the urban environment. Future Internet 2018, 10, 14. [Google Scholar] [CrossRef]
- Dhamgaye, A.; Chavhan, N. Survey on security challenges in VANET. Int. J. Comput. Sci. Network 2013, 2, 88–96. [Google Scholar]
- Hasrouny, H.; Samhat, A.E.; Bassil, C.; Laouiti, A. VANet security challenges and solutions: A survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Sakiz, F.; Sen, S. A survey of attacks and detection mechanisms on intelligent transportation systems: VANETs and IoV. Ad Hoc Netw. 2017, 61, 33–50. [Google Scholar] [CrossRef]
- He, M.; Guan, Z.; Bao, L.; Zhou, Z.; Anisetti, M.; Damiani, E.; Jeon, G. Performance Analysis of a Polling-Based Access Control Combining with the Sleeping Schema in V2I VANETs for Smart Cities. Sustainability 2019, 11, 503. [Google Scholar] [CrossRef]
- Urquiza-Aguiar, L.; Tripp-Barba, C.; Aguilar, I.M. A geographical heuristic routing protocol for VANETs. Sensors 2016, 16, 1567. [Google Scholar] [CrossRef]
- Benamar, M.; Ahnana, S.; Saiyari, F.Z.; Benamar, N.; El Ouadghiri, M.D.; Bonnin, J.M. Study of VDTN Routing Protocols Performances in Sparse and Dense Traffic in the Presence of Relay Nodes. J. Mob. Multimed. 2014, 10, 78–93. [Google Scholar]
- Gonçalves Filho, J.; Patel, A.; Batista, B.L.A.; Júnior, J.C. A systematic technical survey of DTN and VDTN routing protocols. Comput. Stand. Interfaces 2016, 48, 139–159. [Google Scholar] [CrossRef]
- Hamza-Cherif, A.; Boussetta, K.; Diaz, G.; Lahfa, F. Performance evaluation and comparative study of main VDTN routing protocols under small- and large-scale scenarios. Ad Hoc Netw. 2018, 81, 122–142. [Google Scholar] [CrossRef]
- Amla, R.; Jangra, S.; Pandit, A. Improving Security and Performance Parameter using Social Skeleton in heterogeneous VDTN. In Proceedings of the IEEE 3rd International Conference On Internet of Things: Smart Innovation and Usages (IoT-SIU), Bhimtal, India, 23–24 February 2018; pp. 1–7. [Google Scholar]
- Parmar, K.; Patel, T. Increased Message Delivery Using Improved PRoPHET Routing Technique in VDTN. J. Mob. Comput. Commun. Mob. Netw. 2017, 3, 34–40. [Google Scholar]
- Nasir, M.K.; Noor, R.M.; Iftikhar, M.; Imran, M.; Abdul Wahab, A.W.; Jabbarpour, M.R.; Khokhar, R.H. A framework and mathematical modeling for the vehicular delay tolerant network routing. Mob. Inf. Syst. 2016, 2016, 8163893. [Google Scholar] [CrossRef]
- Ahmed, S.H.; Kang, H.; Kim, D. Vehicular delay tolerant network (VDTN): Routing perspectives. In Proceedings of the IEEE 12th Annual IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2015; pp. 898–903. [Google Scholar]
- Fan, N.; Duan, Z.; Zhu, G. A data dissemination mechanism based on evaluating behavior for vehicular delay-tolerant networks. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719865509. [Google Scholar] [CrossRef]
- Zhou, J.; Dong, X.; Cao, Z.; Vasilakos, A.V. Secure and privacy preserving protocol for cloud-based vehicular DTNs. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1299–1314. [Google Scholar] [CrossRef]
- Dias, J.A.; Rodrigues, J.J.; Zhou, L. Cooperation advances on vehicular communications: A survey. Veh. Commun. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Roy, A.; Acharya, T.; DasBit, S. Quality of service in delay tolerant networks: A survey. Comput. Netw. 2018, 130, 121–133. [Google Scholar] [CrossRef]
- Loudari, S.; Abouhassane, A.; Benamar, N.; Younis, M. DASH: A Distributed Approach for Selfishness Handling in a DTN. In Proceedings of the 2nd IEEE Middle East and North Africa COMMunications Conference (MENACOMM), Manama, Bahrain, 19–21 November 2019; pp. 1–6. [Google Scholar]
- Fernandes, F.; Magaia, N.; Pereira, P.R. Friendship-based Routing Protocol for Delay-Tolerant Networks. In Proceedings of the IEEE 16th International Conference on Intelligent Transportation Systems Telecommunications (ITST), Lisboa, Portugal, 15–17 October 2018; pp. 1–7. [Google Scholar]
- Saha, S.; Nandi, S.; Verma, R.; Sengupta, S.; Singh, K.; Sinha, V.; Das, S.K. Design of efficient lightweight strategies to combat DoS attack in delay tolerant network routing. Wirel. Netw. 2018, 24, 173–194. [Google Scholar] [CrossRef]
- Dias, J.A.; Rodrigues, J.J.; Isento, J.N.; Niu, J. The impact of cooperative nodes on the performance of vehicular delay-tolerant networks. Mob. Netw. Appl. 2013, 18, 867–878. [Google Scholar] [CrossRef]
- Colomo-Palacios, R.; Fernandes, E.; de Amescua-Seco, A. M-PeopleNet: Mobile human and intellectual capital management based on the cloud. In Proceedings of the First International Conference on Technological Ecosystem for Enhancing Multiculturality, Salamanca, Spain, 14–15 November 2013. [Google Scholar]
- Motani, M.; Srinivasan, V.; Nuggehalli, P.S. Peoplenet: Engineering a wireless virtual social network. In Proceedings of the 11th Annual International Conference on Mobile Computing and Networking, Cologne, Germany, 28 August–2 September 2005; pp. 243–257. [Google Scholar]
- Barua, R.; Shadman, S.; Chakrabarty, A. Pngp: A social relationship based routing algorithm for pocket switched network. In Proceedings of the IEEE 19th International Conference on Computer and Information Technology (ICCIT), Dhaka, Bangladesh, 18–20 December 2016. [Google Scholar]
- Haq, A.; Faheem, Y. A peer-to-peer communication based content distribution protocol for incentive-aware delay tolerant networks. Wirel. Netw. 2020, 26, 583–601. [Google Scholar] [CrossRef]
- Wang, H.; Wang, H.; Guo, F.; Feng, G.; Lv, H. ARAG: A routing algorithm based on incentive mechanisms for DTN with nodes’ selfishness. IEEE Access 2018, 6, 29419–29425. [Google Scholar] [CrossRef]
- Jethawa, H.; Madria, S. Reputation and credit based incentive mechanism for data-centric message delivery in DTNs. In Proceedings of the 19th IEEE International Conference on Mobile Data Management (MDM), Aalborg, Denmark, 25–28 June 2018. [Google Scholar]
- Yu, S.; Zhang, L.; Li, L.; Wang, X. Cost-aware cooperative theory based routing in mobile opportunistic networks. In Interrnational Conference on Wireless Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2018; pp. 3–11. [Google Scholar]
- Loudari, S.E.; Benamar, M.; Benamar, N. New classification of nodes cooperation in delay tolerant networks. In International Symposium on Ubiquitous Networking; Springer: Berlin/Heidelberg, Germany, 2015; pp. 301–309. [Google Scholar]
- Li, Y.; Hui, P.; Jin, D.; Su, L.; Zeng, L. Evaluating the impact of social selfishness on the epidemic routing in delay tolerant networks. IEEE Commun. Lett. 2010, 14, 1026–1028. [Google Scholar] [CrossRef]
- Bigwood, G.; Henderson, T. Ironman: Using social networks to add incentives and reputation to opportunistic networks. In Proceedings of the IEEE International Conference on Privacy, Security, Risk and Trust and 2011 IEEE Third International Conference on Social Computing, Boston, MA, USA, 9–11 October 2011; pp. 65–72. [Google Scholar]
- Zhu, Z.; Hu, B.; Song, H.; Liu, X. A Social-Aware Routing Protocol for Two Different Scenarios in Vehicular Ad-Hoc Network. In International Conference on Communications and Networking; Springer: Berlin/Heidelberg, Germany, 2017; pp. 563–575. [Google Scholar]
- Yu, L.; Liu, P. A service-based selfish routing for mobile social networks. Int. J. Distrib. Sens. Netw. 2015, 11, 910635. [Google Scholar] [CrossRef]
- Singh, A.K.; Pamula, R. IRS: Incentive based routing strategy for socially aware delay tolerant networks. In Proceedings of the IEEE 5th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 22–23 February 2018; pp. 343–347. [Google Scholar]
- Socievole, A.; Caputo, A.; De Rango, F.; Fazio, P. Routing in mobile opportunistic social networks with selfish nodes. Wirel. Commun. Mob. Comput. 2019, 2019, 6359806. [Google Scholar] [CrossRef]
- Ning, Z.; Liu, L.; Xia, F.; Jedari, B.; Lee, I.; Zhang, W. CAIS: A copy adjustable incentive scheme in community-based socially aware networking. IEEE Trans. Veh. Technol. 2017, 66, 3406–3419. [Google Scholar] [CrossRef]
- Abirami, K.R.; Sumithra, M.G. Preventing the impact of selfish behavior under MANET using Neighbor Credit Value based AODV routing algorithm. Sādhanā 2018, 43, 60. [Google Scholar] [CrossRef]
- Li, L.; Zhong, X.; Jiang, Y. IAR-GT: An Incentive Aware Routing based on Game Theory for Selfish Opportunistic Networks. TIIS 2019, 13, 152–171. [Google Scholar]
- Liu, Y.; Li, F.; Wang, Y. Incentives for delay-constrained data query and feedback in mobile opportunistic crowdsensing. Sensors 2016, 16, 1138. [Google Scholar] [CrossRef]
- Wang, Y.; Chuah, M.C.; Chen, Y. Incentive based data sharing in delay tolerant mobile networks. IEEE Trans. Wirel. Commun. 2013, 13, 370–381. [Google Scholar] [CrossRef]
- Wu, F.; Chen, T.; Zhong, S.; Qiao, C.; Chen, G. A bargaining-based approach for incentive-compatible message forwarding in opportunistic networks. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; pp. 789–793. [Google Scholar]
- Ogah, C.P.A.; Cruickshank, H.; Sun, Z.; Chandrasekaran, G.; Cao, Y.; Asuquo, P.M.; Al Tawqi, M. Privacy-enhanced group communication for vehicular delay tolerant networks. In Proceedings of the 2015 9th IEEE International Conference on Next Generation Mobile Applications, Services and Technologies, Cambridge, UK, 9–11 September 2015; pp. 193–198. [Google Scholar]
- Sun, Y.; Wu, L.; Wu, S.; Li, S.; Zhang, T.; Zhang, L.; Xiong, Y. Security and Privacy in the Internet of Vehicles. In Proceedings of the IEEE 2015 International Conference on Identification, Information, and Knowledge in the Internet of Things (IIKI), Beijing, China, 22–23 October 2015. [Google Scholar]
- Zhan, Y.; Xia, Y.; Zhang, J.; Wang, Y. Incentive mechanism design in mobile opportunistic data collection with time sensitivity. IEEE Internet Things J. 2017, 5, 246–256. [Google Scholar] [CrossRef]
- Beraldi, R.; Mtibaa, A.; Mian, A.N. CICO: A credit-based incentive mechanism for cooperative fog computing paradigms. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, UAE, 9–13 December 2018. [Google Scholar]
- Chen, T.; Wu, F.; Zhong, S. Fits: A finite-time reputation system for cooperation in wireless ad hoc networks. IEEE Trans. Comput. 2011, 60, 1045–1056. [Google Scholar] [CrossRef]
- Erdinç, O.; Taşcıkaraoğlu, A.; Paterakis, N.G.; Catalão, J.P. An energy credit based incentive mechanism for the direct load control of residential HVAC systems incorporation in day-ahead planning. In Proceedings of the 2017 IEEE Manchester PowerTech, Manchester, UK, 18–22 June 2017; pp. 1–6. [Google Scholar]
- Katmada, A.; Satsiou, A.; Kompatsiaris, I. A reputation-based incentive mechanism for a crowdsourcing platform for financial awareness. In Collective Online Platforms for Financial and Environmental Awareness; Springer: Berlin/Heidelberg, Germany, 2016; pp. 57–80. [Google Scholar]
- Mantas, N.; Louta, M.; Karapistoli, E.; Karetsos, G.T.; Kraounakis, S.; Obaidat, M.S. Towards an incentive-compatible, reputation-based framework for stimulating cooperation in opportunistic networks: A survey. IET Netw. 2017, 6, 169–178. [Google Scholar] [CrossRef]
- Wang, E.K.; Liang, Z.; Chen, C.M.; Kumari, S.; Khan, M.K. PoRX: A reputation incentive scheme for blockchain consensus of IIoT. Future Gener. Comput. Syst. 2020, 102, 140–151. [Google Scholar] [CrossRef]
- El Khatib, R.F.; Zorba, N.; Hassanein, H.S. A fair reputation-based incentive mechanism for cooperative crowd sensing. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, UAE, 9–13 December 2018. [Google Scholar]
- Goswami, A.; Parashari, G.S.; Gupta, R. Evolutionary stability of reputation-based incentive mechanisms in p2p systems. IEEE Commun. Lett. 2017, 22, 268–271. [Google Scholar] [CrossRef]
- Tian, F.; Liu, B.; Sun, X.; Zhang, X.; Cao, G.; Gui, L. Movement-based incentive for crowdsourcing. IEEE Trans. Veh. Technol. 2017, 66, 7223–7233. [Google Scholar] [CrossRef]
- Peng, D.; Wu, F.; Chen, G. Data quality guided incentive mechanism design for crowdsensing. IEEE Trans. Mob. Comput. 2017, 17, 307–319. [Google Scholar] [CrossRef]
- Luo, T.; Kanhere, S.S.; Huang, J.; Das, S.K.; Wu, F. Sustainable incentives for mobile crowdsensing: Auctions, lotteries, and trust and reputation systems. IEEE Commun. Mag. 2017, 55, 68–74. [Google Scholar] [CrossRef]
- Guo, Y.; Schildt, S.; Pögel, T.; Wolf, L. Detecting malicious behavior in a vehicular DTN for public transportation. In Proceedings of the IEEE Global Information Infrastructure Symposium-GIIS 2013, Trento, Italy, 28–31 October 2013. [Google Scholar]
- Guo, Y.; Schildt, S.; Po, T.; Rottmann, S.; Wolf, L. Mitigating blackhole attacks in a hybrid VDTN. In Proceedings of the IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Sydney, Australia, 19 June 2014. [Google Scholar]
- Zhan, Y.; Xia, Y.; Liu, Y.; Li, F.; Wang, Y. Incentive-aware time-sensitive data collection in mobile opportunistic crowdsensing. IEEE Trans. Veh. Technol. 2018, 66, 7849–7861. [Google Scholar] [CrossRef]
- Xia, F.; Jedari, B.; Yang, L.T.; Ma, J.; Huang, R. A signaling game for uncertain data delivery in selfish mobile social networks. IEEE Trans. Comput. Soc. Syst. 2016, 3, 100–112. [Google Scholar] [CrossRef]
- Hui, Y.; Su, Z.; Luan, T.H.; Cai, J. Content in motion: An edge computing based relay scheme for content dissemination in urban vehicular networks. IEEE Trans. Intell. Transp. Syst. 2018, 20, 3115–3128. [Google Scholar] [CrossRef]
- Seregina, T.; Brun, O.; El-Azouzi, R.; Prabhu, B.J. On the design of a reward-based incentive mechanism for delay tolerant networks. IEEE Trans. Mob. Comput. 2016, 16, 453–465. [Google Scholar] [CrossRef]
- Park, Y.; Sur, C.; Rhee, K.H. A secure incentive scheme for vehicular delay tolerant networks using cryptocurrency. Secur. Commun. Netw. 2018, 2018, 5932183. [Google Scholar] [CrossRef]
- Gong, H.; Yu, L.; Zhang, X. Social contribution-based routing protocol for vehicular network with selfish nodes. Int. J. Distrib. Sens. Netw. 2014, 10, 753024. [Google Scholar] [CrossRef]
- Dubey, B.B.; Chauhan, N.; Chand, N. Efficient Technique for Improving Data Availability in VANETs. J. Comput. Eng. 2016, 62–68. [Google Scholar] [CrossRef]
- Jiang, Q.; Men, C.; Tian, Z. A Credit-Based Congestion-Aware Incentive Scheme for DTNs. Information 2016, 7, 71. [Google Scholar] [CrossRef]
- Xie, Y.; Zhang, Y. A secure, service priority-based incentive scheme for delay tolerant networks. Secur. Commun. Netw. 2016, 9, 5–18. [Google Scholar] [CrossRef]
- Chen, H.; Lou, W.; Wang, Z.; Wang, Q. A secure credit-based incentive mechanism for message forwarding in non-cooperative DTNs. IEEE Trans. Veh. Technol. 2015, 65, 6377–6388. [Google Scholar] [CrossRef]
- Cai, Y.; Fan, Y.; Wen, D. An incentive-compatible routing protocol for two-hop delay-tolerant networks. IEEE Trans. Veh. Technol. 2015, 65, 266–277. [Google Scholar] [CrossRef]
- Dias, J.A.; Rodrigues, J.J.; Xia, F.; Mavromoustakis, C.X. A cooperative watchdog system to detect misbehavior nodes in vehicular delay-tolerant networks. IEEE Trans. Ind. Electron. 2015, 62, 7929–7937. [Google Scholar] [CrossRef]
- Rehman, G.U.; Ghani, A.; Zubair, M.; Naqvi, S.H.A.; Singh, D.; Muhammad, S. IPS: Incentive and Punishment Scheme for Omitting Selfishness in the Internet of Vehicles (IoV). IEEE Access 2019, 7, 109026–109037. [Google Scholar] [CrossRef]
- Dias, J.A.; Rodrigues, J.J.; Kumar, N.; Saleem, K. Cooperation strategies for vehicular delay-tolerant networks. IEEE Commun. Mag. 2015, 53, 88–94. [Google Scholar] [CrossRef]
- Lin, H.; Zhang, F. A scheme for stimulating message relaying cooperation. Int. J. Distrib. Sens. Netw. 2020, 6. [Google Scholar] [CrossRef]
- Dias, J.A.; Rodrigues, J.J.; Shu, L.; Ullah, S. Performance evaluation of a cooperative reputation system for vehicular delay-tolerant networks. EURASIP J. Wirel. Commun. Netw. 2014, 1, 88. [Google Scholar] [CrossRef]
- Kou, M.; Zhao, Y.; Cai, H.; Fan, X. Study of a routing algorithm of Internet of vehicles based on selfishness. In Proceedings of the IEEE International Conference on Smart Internet of Things (SmartIoT), Xi’an, China, 17–19 August 2018; pp. 34–39. [Google Scholar]
- Magaia, N.; Sheng, Z. ReFIoV: A novel reputation framework for information-centric vehicular applications. IEEE Trans. Veh. Technol. 2018, 68, 1810–1823. [Google Scholar] [CrossRef]
- Moreira, E. An evaluation of reputation with regard to the opportunistic forwarding of messages in VANETs. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 204. [Google Scholar]
- Liu, L.; Yang, Q.; Kong, X.; Liaqat, H.B.; Ahmed, A.M.; Deonauth, N.; Xia, F. Com-BIS: A community-based barter incentive scheme in socially aware networking. Int. J. Distrib. Sens. Netw. 2015, 11, 671012. [Google Scholar] [CrossRef]
- Zhou, H.; Wu, J.; Zhao, H.; Tang, S.; Chen, C.; Chen, J. Incentive-driven and freshness-aware content dissemination in selfish opportunistic mobile networks. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 2493–2505. [Google Scholar] [CrossRef]
- Buttyán, L.; Dóra, L.; Félegyházi, M.; Vajda, I. Barter trade improves message delivery in opportunistic networks. Ad Hoc Netw. 2010, 8, 1–14. [Google Scholar] [CrossRef]
- Chen, K.; Shen, H.; Yan, L. Multicent: A multifunctional incentive scheme adaptive to diverse performance objectives for DTN routing. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 1643–1653. [Google Scholar] [CrossRef]
- Yin, L.; Lu, H.M.; Gao, J.M. Cooperation in delay tolerant networks. In Proceedings of the IEEE 2nd International Conference on Signal Processing Systems, Dalian, China, 5–7 July 2010; pp. 202–205. [Google Scholar]

| Methods | Advantages | Disadvantages |
|---|---|---|
| Credit-Based | Motivate nodes in the network for cooperation through reward | It is not suitable for scenarios where there is a high probability of selfish nodes |
| Reputation-Based | Even useful in an environment where the majority of the nodes in the network have selfish behavior | Consider intermediate node cooperation to be selfish behavior |
| Barter-Based | Exchange of the same amount of message needed | If the node has not sufficient messages to exchange, then it cannot deliver messages to another node even when there is a connection with the destination node hence degrading the routing performance |
| Game-Theoretic-Based | The bargaining possibility increases with an increase in the number of nodes | The cost of game-theoretic approaches are high as it uses more resources |
| Credit-Based | Reputation-Based | Barter-Based | Game-Theoretic Based |
|---|---|---|---|
| Seregina et al. [73] | Dias et al. [81] | Liu et al. [89] | Chen et al. [92] |
| Park et al. [74] | Rehman et al. [82] | Zhou et al. [90] | Yin et al. [93] |
| Gong et al. [75] | Dias e8 al. [83] | Buttyan et al. [91] | |
| Dubey et al. [76] | Lin et al. [84] | ||
| Jiang et al. [77] | Dias et al. [85] | ||
| Xie et al. [78] | Kou et al. [86] | ||
| Chen et al. [79] | Magaia et al. [87] | ||
| Ying et al. [80] | Moreira et al. [88] |
| Article | Incentive Schemes | Cost | Approach | Detected Nodes | Scalability | Detection Accuracy | Buffer Consumption | Applicability |
|---|---|---|---|---|---|---|---|---|
| Seregina et al. [73] | Credit | H | Detective | Selfish | Yes | Average | Medium | DTN |
| Park et al. [74] | Credit | H | Detective | Selfish | Yes | Good | Low | VDTN |
| Gong et al. [75] | Credit | H | Detective | Social Selfish | No | Average | Medium | VDTN |
| Dubey et al. [76] | Credit | H | Detective | Selfish | Yes | Low | High | VDTN |
| Jiang et al. [77] | Credit | H | Preventive | Selfish | No | Average | High | DTN |
| Xie et al. [78] | Credit | H | Detective | Selfish | No | Average | Medium | DTN |
| Chen et al. [79] | Credit | H | Detective | Malicious | Yes | Average | Medium | DTN |
| Ying et al. [80] | Credit | H | Preventive | Malicious | Yes | Good | Low | DTN |
| Dias et al. [81] | Reputation | H/L | Detective | Selfish | Yes | Average | High | VDTN |
| Rehman et al. [82] | Reputation | H/L | Preventive | Selfish | Yes | Average | Medium | VDTN |
| Dias et al. [83] | Reputation | H/L | Detective | Selfish | Yes | Average | Medium | VDTN |
| Lin et al. [84] | Reputation | H/L | Preventive | Selfish | Yes | Average | High | DTN |
| Dias et al. [85] | Reputation | H/L | Detective | Social Selfish | Yes | Good | Medium | VDTN |
| Kou et al. [86] | Reputation | H/L | Preventive | Selfish | Yes | Average | High | VDTN |
| Magaia et al. [87] | Reputation | H/L | Preventive | Selfish | No | Average | High | VDTN |
| Moreira et al. [88] | Reputation | H/L | Detective | Selfish | Yes | Good | Medium | VDTN |
| Liu et al. [89] | Barter | L | Detective | Selfish | No | Low | Low | DTN |
| Zhou et al. [90] | Barter | L | Detective | Selfish | No | Low | Low | DTN |
| Buttyan et al. [91] | Barter | L | Detective | Selfish | Yes | Low | Low | DTN |
| Chen et al. [92] | Game | H | Detective | Selfish | Yes | Average | Medium | DTN |
| Yin et al. [93] | Game | L | Detective | Selfish | Yes | Low | Low | DTN |
| Article | Advantages | Disadvantages |
|---|---|---|
| Seregina et al. [73] | Use of adaptive strategy: The source chooses to provide the relay with complete information, partial information or even no information at the time it reaches it, depending on the contact times with that relay | The reward assigned by the source to the relay nodes is the same. There is no reward distinction for full state information to no information delivered by the relay nodes. |
| Park et al. [74] | Usage of the unique public key procedure to improve vehicle interactions privacy and reward transactions. | It does not satisfy unlinkability requirement |
| Gong et al. [75] | Makes forwarding decisions on the basis of the delivery probability and the social involvement of the relay node | No proper security measures adopted in the payment process |
| Dubey et al. [76] | Allocate rewards for relay nodes to minimize selfishness and increase network coalition. | Bonus is given to the last two nodes only |
| Jiang et al. [77] | Monitoring system to discourage overloaded nodes from intentionally discarding messages | Each node needs routing table for indicating next hop |
| Xie et al. [78] | Optimize network bandwidth and the overall delivery ratio for bundles Uses a service priority to encourage cooperation among nodes | Uses third-party supervision for trust manner |
| Chen et al. [79] | Prevent typically manipulative behavior of selfish nodes | Ignore some of the selfish behavior such as plotting and scheming, manipulation and self-centered etc. |
| Ying et al. [80] | Better defense against attacks by forgers Forwarding nodes are selected according to the optimal sequential stopping rule | Multi-copy messages replication |
| Dias et al. [81] | Watchdog mechanism aiming at detecting and avoiding selfish nodes in order to minimize their influence on cooperative node performance | The performance decreased with increase in selfish nodes |
| Rehman et al. [82] | Solving Weight tie problem by using cooperation criteria | Monitoring node can also be selfish but it only monitors the behaviors of the selfish node |
| Dias et al. [83] | Control the number of resources exchanged with several other nodes so that the credibility of nodes is not compromised | When threshold value of the cooperation decreased then the delay of bundle delivery gets increased |
| Lin et al. [84] | Requires minimal computing power and a minimal amount of memory space for storing private informations | Nodes may be expelled from the network due to high reputational threshold |
| Dias et al. [85] | Uses scalable reputation system variant so as to prevent selfish node form behaving selfishly | Message delivery is decreased when the number of selfish nodes are increases |
| Kou et al. [86] | Selfish nodes are detected and their behaviors are recorded | Every node needs its own local memory for saving reputation table |
| Magaia et al. [87] | Very limited number of selfish nodes identified incorrectly | Every node needs its own local memory for saving reputation table |
| Moreira et al. [88] | Vehicles received confirmation on the behavioral variables for message generation and forwarding | Lack of privacy |
| Liu et al. [89] | Useful for improving the probability of exchanging messages | It generates high overhead |
| Zhou et al. [90] | Contents utility decides the exchange order in each contact | When the number of channels are increases then its performance is degrade |
| Buttyan et al. [91] | Users receive and transmit messages even when they are not involved in them and thus by reducing selfishness | High latency issue |
| Chen et al. [92] | Performance of the network improves with a high hit rate in messages forwarding and storing | Motivation of nodes to forward messages in different sequences cannot be achieved for different performance objectives |
| Yin et al. [93] | It is useful to stimulate cooperation among selfish nodes in the network | applied to networks where topology does not change and communication can not be disconnected |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rehman, G.-U.; Ghani, A.; Muhammad, S.; Singh, M.; Singh, D. Selfishness in Vehicular Delay-Tolerant Networks: A Review. Sensors 2020, 20, 3000. https://doi.org/10.3390/s20103000
Rehman G-U, Ghani A, Muhammad S, Singh M, Singh D. Selfishness in Vehicular Delay-Tolerant Networks: A Review. Sensors. 2020; 20(10):3000. https://doi.org/10.3390/s20103000
Chicago/Turabian StyleRehman, Ghani-Ur, Anwar Ghani, Shad Muhammad, Madhusudan Singh, and Dhananjay Singh. 2020. "Selfishness in Vehicular Delay-Tolerant Networks: A Review" Sensors 20, no. 10: 3000. https://doi.org/10.3390/s20103000
APA StyleRehman, G.-U., Ghani, A., Muhammad, S., Singh, M., & Singh, D. (2020). Selfishness in Vehicular Delay-Tolerant Networks: A Review. Sensors, 20(10), 3000. https://doi.org/10.3390/s20103000







