Abstract
Mobile radio frequency identification (RFID) has been extensively applied in a wide range of fields. In supply chain management, RFID is used to more efficiently manage the ownership transfer of cargo. The transfer of a group of tags belonging to multiple owners is often required at the front end of a supply chain. This study, therefore, proposes a secure, high-performance threshold multi-owner partial tag ownership transfer protocol that supports a mobile RFID environment and features the capabilities and security required for supporting existing ownership transfer environments (e.g., application for different authorities, designation of the transfer target, and ownership transfer of a group of tags). Moreover, the proposed protocol can resist against most of the known attacks on RFID.
1. Introduction
Mobile radio frequency identification (RFID) is a combination of a wireless network, mobile telecommunication technology, and RFID systems [1,2]. Mobile RFID is characterized by simple computing power, storage capacity, and the simultaneous reading and writing of multi-tag information. These features facilitate product identification and follow-up management. Mobile RFID is widely applied in supply chain management, access control, bill payment, smart home development, military supply control, and health care medication administration. Because RFID can effectively manage the flow and processing of goods, large-scale retail chain stores such as Walmart have saved roughly $1.4 billion USD in cost by using RFID technologies [1].
RFID has become an integral part of supply chain management in recent years and has been continually advancing and becoming more affordable. Therefore, various components of a supply chain, including raw material supplier, product manufacturer, wholesaler, retailer, and end consumer, can employ RFID for follow-up management. Manufacturers use RFID tags to identify goods information and conduct inventory. Retailers use RFID tags to keep track of and manage product information and provide consumers with a convenient shopping platform and various services. Consumers use RFID tags to obtain product and post-sale information. To facilitate the management of supply chain automation and effectively engage in product ownership transfer [3,4,5,6,7,8,9], products labeled with RFID tags undergo multiple ownership transfers throughout their life cycle from their introduction to the decline stage.
For secure transfer of product ownership, designation must be ensured while also avoiding the windowing problem (i.e., new and old owners simultaneously owning a tag) and providing forward and backward secrecy. Forward secrecy means that the new owner cannot identify and decrypt messages that were transmitted between the tag and its old owner. Backward secrecy means that the old owner cannot receive and decrypt the messages transmitted between the tag and its new owner. In the process of tag ownership transfer, since a tag has limited computing power and an RFID system employs wireless transmission, hackers can access messages sent by the tag or reader. The RFID system may also suffer from security threats, such as message modification, replay attack, man-in-the-middle attack, tracking attack, denial-of-service (DoS) attack, and a counterfeit tag reader attack.
When products are at the end of a supply chain, each product owner usually owns only a small number of products. Therefore, owners perform ownership transfer only once for a small number of products. Osaka et al. [6] proposed an ownership transfer method for a single tag in such an application environment in which few tags are being transferred. However, their method is associated with security flaws. For example, update-key messages are vulnerable to modification attacks, which causes an asynchronous service, compromised forward secrecy, and the windowing problem during the transfer period [9,10]. Jäppinen et al. [11] verified the integrity of update-key messages to reduce the likelihood of asynchronous communication between tags and end servers, but the methods for doing so still engender vulnerability to attacks, which results in persistent asynchronous problems [12]. Hence, Yoon et al. [13], Chen et al. [14], Yang et al. [15], and Dimitriou et al. [16] proposed new ownership transfer methods to address the asynchronous service problem and ensure the forward secrecy of ownership transfer. However, the protocol presented by Dimitriou et al. [16] is vulnerable to counterfeiting and replay attacks [17]. The methods developed by Yoon et al. [13] and Chen et al. [14] are also associated with security concerns such as lack of support for backward secrecy, the inability to ensure location privacy, and windowing problems [9,18]. Yang et al. [19] proposed layered object transport protocol (LOTP), which is applicable for environments employing mobile RFID. LOTP [19] involves the transfer of tag ownership through a trusted third party (TTP) to overcome attacks that occur during ownership transfer through mobile RFID. However, LOTP can only transfer one tagged object at a time and cannot efficiently transfer a large number of tagged objects.
Therefore, when products are at the front end of a supply chain, manufacturers or wholesalers generally perform a single transfer of ownership for an extremely large number of products. However, a protocol causes problems due to inefficiency if it can only transfer the ownership of a single tag. Zuo [12] and He et al. [20] used group keys to simultaneously authenticate and transfer the ownership of all tags in a group. However, Zuo’s protocol resulted in denial of service (DoS) attack when the updated key was subject to a desynchronization attack. Subsequently, Jannati et al. [21] proposed a solution to the DoS problem caused by a modification to update-key messages. However, all of these group transfer protocols have a limitation of only being able to perform a single transfer for all tags of an owner and not being able to perform a partial transfer of only some tags in a group. In other words, the flexibility in object ownership transfer is limited, which renders relevant methods impractical. Therefore, Molnar et al. [22] proposed using a split back-end server and a tree of secrets shared between a large number of tags to achieve partial ownership transfer. The number of nodes in the tree represents the number of times that a reader is authorized to read a tag after a binary tree has been transferred from the reader to the back-end server. The new owner can achieve partial ownership transfer by obtaining the tree of secrets of a tag through the back-end server. Tsai et al. [23] proposed an ownership transfer method with grouping the proof protocol that allows for grouping proof and partial ownership transfer of tag groups while ensuring the integrity of the tagged cargo. Yang et al. proposed a tag group ownership transfer protocol with a trust third party (TTP) [24] and without a TTP [25]. This protocol generates a key for a tree of partial group communication by employing the group communication key shared between the tags and server to achieve partial ownership transfer of tag groups. In addition, this protocol can resist most known attacks and protect and secure the privacy of owners.
Ownership transfer is frequently required for a large number of products, particularly when the raw materials or goods of upstream industries are distributed along the supply chain. These raw materials and goods generally belong to different owners and are simultaneously loaded onto the same cargo ship or cargo truck. However, existing methods for secure tag group ownership transfer are limited to only the transfer of objects of a single owner and are not applicable to ownership transfer for multi-object owners. Hence, Kapoor et al. [26] proposed a multi-owner ownership transfer method. However, their method is vulnerable to DoS attacks because it places the tag and server key in a desynchronized state when the key is updated. Moreover, their protocol can only transfer the ownership of a single tag of multiple owners. The transfer efficiency is reduced when transferring the ownership of multiple tags because each tag must independently perform all steps to authenticate the updated key, which increases the information and calculation load. To address this problem, Sundaresan et al. [27] proposed a multi-owner/multi-tag ownership transfer method that uses a group secret value shared between the owners and a group of tags to generate acknowledgments for every tag that must be transferred and send the acknowledgments to all tags in the group. Because each tag group that is designated for transfer generates a message based on its tag identification number (ID), each tag must examine every message received for a tag ID to acknowledge that its tag ID is contained in the transfer of this tag group to simultaneously partially transfer the ownership of tag groups of the owners. However, because the owners in a group use a shared secret to protect the tag message, the method cannot protect the data privacy of the owners in that group. Subsequently, Sundaresan et al. proposed another approach for protecting group communication privacy by applying different group secret values to each owner and tag group [28]. However, in both methods, the process of ownership transfer requires each tag in a group to compute the message for each tag that needs to be transferred in order to acknowledge that its tag needs to be transferred. For example, if a group containing 2000 tags needs to transfer 1000 tags to a new owner, then these 2000 tags must acknowledge that the 1000 messages contain its tag ID. Therefore, each tag requires a large amount of information, a high calculation load, and long transfer time. In addition, the two previously mentioned methods of ownership transfer for multi-owner and partial tag group environments are vulnerable to attacks (e.g., replay, tracking, or DoS attacks) and do not achieve forward secrecy [29]. Table 1 summarized the categories of RFID ownership transfer protocols.

Table 1.
Categories of RFID ownership transfer protocols.
This study proposes a secure, high-performance multi-owner partial ownership transfer protocol to overcome the problems concerning the performance of existing multi-owner tag ownership transfer methods and address the security threats and privacy concerns that may arise in the process of ownership transfer. In this proposed multi-owner ownership transfer protocol, the old owners and new owners of a tag group may differ regarding their jurisdiction. In our protocol, the permissions of several owners are required to transfer a tag or multiple tags from a group of owners to the others. A single user cannot transfer his/her ownership of the tags to others. Our protocol is useful in the supply chain management. The factory assigns ownership of tags to a group of employees. However, it is not necessary to obtain the consent of each employee when transferring ownership. When one of the old owners initiates ownership transfer, a threshold scheme is used to ensure that (1) the consent of a certain number of old owners is obtained before the owner can partially transfer the ownership of a tag group to new owners, and (2) the proposed method can resist most of the known attacks and offer most of the security and privacy protection properties for ownership transfer. This study makes the following contributions to the literature. The multi-owner multi-tag partial ownership transfer protocol (1) is applicable in a mobile RFID environment, (2) can transfer the ownership of one, some, or all tags, (3) provides two-way authentication between a tag, reader, and a back-end server, (4) ensures that tag ownership is only transferred to the designated owners, (5) is secure and immune to replay attacks, eavesdropping, message modification attacks, and tracking attacks (i.e., protects owner privacy) and provides forward and backward secrecy. Lastly, it (6) features high performance that is not related to the reader participating in the transfer or the number of tags and does not increase information and calculation load considerably when the number of owners and tags increases.
This paper is organized as follows. Section 2 introduces the environmental assumptions of the proposed ownership transfer protocol and the relationships among the tag, reader, and the back-end server. Section 3 provides a detailed description of the proposed protocol. Section 4 compares and analyzes the security of the proposed method and other RFID ownership transfer methods. Section 5 presents the calculation performance of the proposed protocol for analysis and a comparison with those introduced in relevant studies, and, lastly, Section 6 concludes this study.
2. Multi-Owner Multi-Tag Ownership Transfer Method
This study proposes a secure multi-owner multi-tag ownership transfer method for a mobile RFID network environment. Figure 1 illustrates the architecture of the proposed system. The mobile device of a member of the old owner group sends a signal for ownership transfer, reads the partial tags in the group to be transferred, and sends the transfer message collectively generated by these tags to a back-end server. The server then notifies the group of old owners. If the partial signature of n old owners who consent to partial tag ownership transfer exceeds the threshold value, then the group of old owners and the group of new owners jointly conduct ownership transfer.
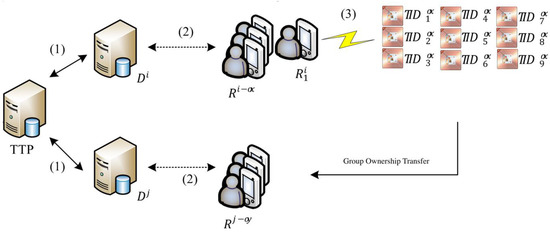
Figure 1.
Multi-owner ownership transfer architecture.
2.1. System Architecture
The ownership network architecture in Figure 1 reveals that the servers, mobile readers, and tags have different computing capabilities. Connection security is discussed in three parts marked by (1), (2), and (3) in Figure 1. Connection (1) in Figure 1 shows that the server exhibits a computing capability sufficiently powerful to support existing encryption algorithms such as the Advanced Encryption Standard (AES) and Rivest–Shamir–Adleman (RSA). Therefore, the proposed protocol employs existing encryption methods to ensure secure communication between the servers. Connection (2) in Figure 1 indicates that the mobile readers engage in two-way communication with other mobile readers by using existing mobile communication technologies or wireless network technologies and back-end servers. Extant security communication technologies such as the X.509 security architecture of telecommunication networks or IEEE802.11i are employed to protect the transfer security of intermediate messages. Connection (3) in Figure 1 reveals that, because tags have limited computing capability, lightweight cryptography methods such as the data encryption standard lightweight [30] or Grain [31] should be used when communicating with mobile readers to secure the messages communicated between the tag and mobile reader. Because the environment involved in part (3) is the riskiest, the present study assumes that the network environment in connection (3) is an insecure communication environment that is vulnerable to attacks. To provide a detailed description of the proposed ownership transfer method, the ownership transfer environment of the tag management service is assumed to be characterized by four properties.
The first property is that a mobile reader connects only to a single back-end server during communication to manage the tags and that the back-end server under the authority of the mobile reader to which ownership is transferred in and out is likely the same back-end server or a back-end server under different authority. In the set of a readers under the authority of back-end server with ID , any one of the readers with independent ID must satisfy the relation in Equation (1).
where is under the authority of and is under the authority of , which satisfies the equation below.
The second property is that the set of readers under the back-end server consists of a set of readers owned by p owners, and, in this multi-owner set , all of the owners have collective ownership to the tags in group . Without loss of generality, an ownership transfer protocol implemented through reader must satisfy the relation in Equation (2).
The third property is that v tags in multi-owner set , which is managed by the back-end server , belong to group , with the group key defined as . The server splits the tag groups into a k-ary tree of group keys, which generates a key tree with the height . Next, the sequence of the k-ary group ID moves from top to bottom and from left to right. The parent node , the children nodes through to , and their relationship with the rules are shown in Figure 2a. Group key can encrypt the group message to through to , and tag IDs can use the keys shared with the server to decrypt the group message that is encrypted by group key . Therefore, the node with the group ID is composed of one to k subtrees, and the group key containing any node is expressed in Equation (3). The group key consists of a parent group containing , the intersection of with equals , and the intersection of the difference between and with is the empty set, as shown in Equation (4).
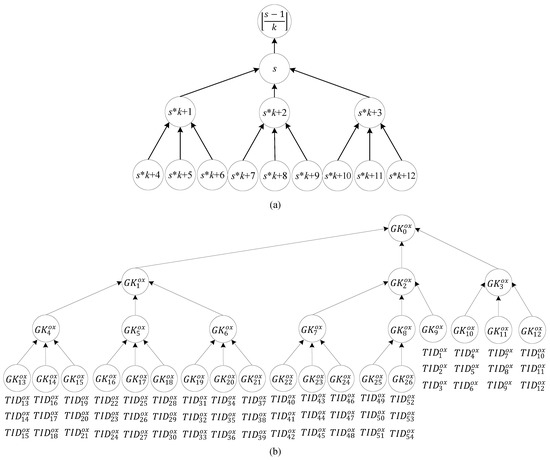
Figure 2.
(a) Tags naming rule (b) Tree of tag group key.
The fourth property is the leaf group that is defined as the leaf node with IDs through on key trees connected to the tags, as shown in Equation (5). For example, tag IDs are connected to the leaf node with group ID .
Figure 3 presents an example in which an owner’s reader intends to transfer the ownership of tag IDs in tag group (indicated by the dashed line in the middle of the key tree) from the owner group under the authority of to the owner group under the authority of . If the owner’s reader obtains consent from the group of old owners through the server of the old owner group to partially transfer tags, then server uses the communication key shared between and the tags on the topmost level in Figure 3 to generate and send the ownership transfer message to a trust third party (TTP). Subsequently, the TTP sends an update-key message to multi-owner sets and and tag group to simultaneously update the key and avoid the windowing problem. As indicated on the right of Figure 3, because the back-end server has authority over its own key tree, when tag IDs and are transferred to multi-owner sets , the owner inserts tag IDs in tag group on the far right, and these IDs are not necessarily the same as the output tag IDs. Lastly, the TTP changes the shared keys of tags and under , as shown at the bottom of Figure 3, to a shared management key of tags under . Details of the ownership transfer protocol are provided in Section 3.
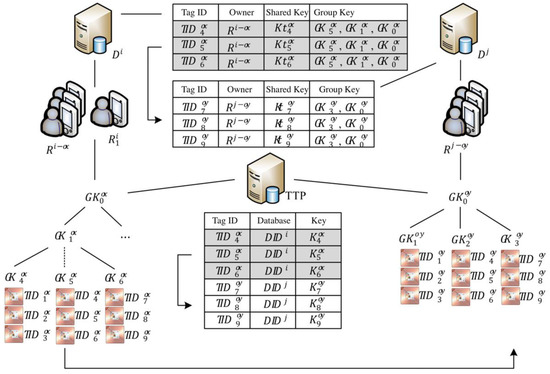
Figure 3.
Example of tag group transfer IDs.
2.2. Transfer of Multiple Tag Groups
Tags to be transferred may belong to different groups. In other words, the transfer of ownership of all the tags to be transferred cannot be achieved by transferring the tags of a single group. In this case, the proposed multi-owner multi-tag ownership transfer method is implemented multiple times to solve this problem. As indicated in Figure 2b, because the tags , , and belong to different groups and the transfer of ownership of all of the tags cannot be achieved by transferring the tags of a single group. Transferring these tags requires the ownership of tag groups , , and to be transferred three times. The owners’ readers are activated to send the ownership transfer request (OT) of groups IDs , , and to the tags. The ownership transfer of group IDs , , and can be simultaneously conducted by implementing the proposed protocol multiple times.
3. Multi-Owner Multi-Tag Ownership Transfer Protocol
3.1. Initialization
Table 2 lists the notations in this paper. In our protocol, consent must be obtained from the majority of owners of the reader set before ownership transfer. Therefore, the threshold signature scheme presented by Harn [32] is used to confirm majority consent before proceeding to transfer ownership. When n owners receive a transfer request, the partial signatures of only t consenting owners are required and are sent to the server for grouping and verification. If the partial signatures match the ownership transfer message, then most owners consented to tag ownership transfer. The next three steps are described as follows.

Table 2.
Notations.
The first step is the group key and the secret key generation stage. This step must be completed before ownership transfer. Each owner is allocated a secret key for partial signature generation, a verification key for partial signature generation, and a verification key for group signature generation.
The second step is the partial signature generation stage. When one of the owners of the reader set sends an ownership transfer request message (OT), the server asks other owners whether they consent to ownership transfer. Consenting owners send the partial signature generated by the request message to the server for verification.
The third step is the group signature verification stage. The server conducts verification and grouping after receiving the partial signature and then verifies whether the group signature matches the OT message. If the message matches, then most owners agreed to proceed with the ownership transfer.
3.2. Ownership Transfer Request
Figure 4 shows the selected reader wants to get the ownership transfer permission from the original owners. In Step 1, the reader belonging to one of the owners in the multi-owner set of tag group expresses intent to transfer the ownership of the object represented by each tag in the tag group to the owners in the multi-owner set . First, owner generates a random number and uses the key to encrypt an OT, tag list (TL) of all the tags to be transferred, pseudo-random number , server ID of the transfer target, and multi-owner set of the new owner. After encryption, message is generated and sent to the management server of requesting to ask other owners whether they consent to ownership transfer.
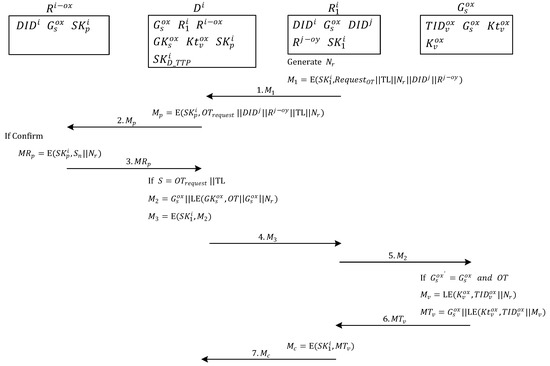
Figure 4.
Ownership transfer request.
In Step 2, after server receives , it decrypts the message by using the key shared with owner , and confirms that owner wants to transfer the tags in the TL. Server encrypts the OT, server ID of the transfer target, multi-owner set of the new owner, TL of all the tags to be transferred, and pseudo-random number by using the key , which is shared between server and each owner in the multi-owner set . Lastly, the server sends message to each owner in the multi-owner set asking whether they consent to the ownership transfer.
In Step 3, when each owner in the multiowner set with the ownership of tag group receives , the message is decrypted using the key , which is shared between server and each owner. The consent of the owner to the ownership transfer is verified. If consent is provided, then the key shared between server and each owner is used to encrypt the partial signature and pseudo-random number , which generates the message . This is then sent to server .
In Step 4, server collects the message from owners in the multi-owner set and uses the key , which is shared between server and owners, to decrypt message and perform the verification of partial signature to check whether it matches the signature message . If the signature matches, then most owners consented to ownership transfer and the protocol proceeds with the ownership transfer. If the collected partial signatures are not enough, or the signature does not match, then owners did not consent to ownership transfer and the protocol terminates the ownership transfer.
When most owners provide consent to proceed with ownership transfer, server first identifies the communication key of the tag group in the TL. Next, it uses the group communication key to encrypt the OT (approved by the owners in the multi-owner set ), group of tags to be transferred, the pseudo-random number , and group ID , subsequently generating message . Message is then encrypted using the communication key , which is shared with the owner, to produce message , which is transmitted to owner .
In Step 5, after owner receives message , it decrypts the message by using the communication key shared with server . Then the extracted message is sent to tag group as a broadcast message.
In Step 6, when any tag in tag group receives message , the tag confirms whether the group tag ID in the message matches the ID of the tag group to which it belongs. After confirming that it belongs to the tag group , each tag uses the communication key shared with server to decrypt the OT (approved by owners in the multi-owner set ) and then reconfirms that the tag group to be transferred matches the ID of the tag group to which it belongs. If the IDs match, then the tag uses the management key shared with the TTP to encrypt its tag ID and the pseudo-random number from owner , which produced the authentication message . Next, the tag uses the communication key shared with server to encrypt tag ID , pseudo-random number , and its tag group ID , which generates message and is sent to owner .
In Step 7, after owner receives message , it decrypts the message by using the communication key shared with server , subsequently producing message , which is then sent to the management server of .
3.3. Authentication of Tags and Transfer of Ownership
Figure 5 shows the authentication of tags and the ownership transfer process. In Step 8, because tag group may contain more than one tag, server must collect message sent by all of the tags in tag group . Subsequently, because tag group is a set of all leaf nodes of the group ID subtree of group , comprises all of the tags in tag group . When server receives message , the server decrypts each message by using the key shared with owner to extract and then decrypts each message by using the secret value shared between server and each tag to compare the tag ID with the authentication tag. Next, the server performs comparisons to determine whether all of the tag IDs in tag group are consistent with the tag IDs received, checks whether all tags in tag group are available, and checks whether has ownership of tag group .
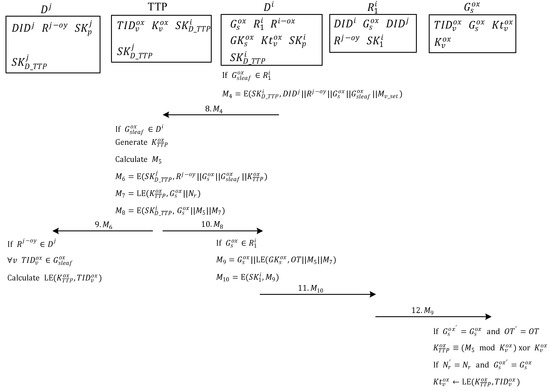
Figure 5.
Authentication of tags and transfer of ownership.
Server uses the communication key shared with a TTP to encrypt the server’s identity of the transfer target, multi-owner set of the new owner, tag group , and tag group , which consists of the IDs of all the tags to be transferred. of message is transmitted by all of the tags in tag group . is defined in Equation (6). Subsequently, message is generated and transmitted to the TTP, which requests that the TTP use the management key shared between the TTP and the tags to update the communication key on the tag for completing the ownership transfer.
In Steps 9 and 10, after the TTP receives message , the communication key shared with server is used to decrypt message . After confirming that the tag group belongs to server , the TTP uses the management key shared between each tag and the TTP to decrypt each tag message in the . The TTP then extracts tag ID to authenticate the tag and determine whether each tag ID in tag group within message matches the tag IDs in and checks whether the pseudo-random number is the same for all tag messages . If all of them match, then the TTP randomly generates a new secret value and uses the Chinese remainder theorem [33] in Equation (7) to calculate message .
The TTP encrypts the multi-owner set of the new owner, tag group , and tag group , which consists of the IDs of all of the tags to be transferred, and the secret value into message by using the communication key shared between the TTP and server Next, the random number and are encrypted into message by using the secret value . , , and are encrypted into message by using the communication key shared between the TTP and server Messages and are then sent to the new owners and the old owners for ownership transfer.
After server of the new owners receives messages , it decrypts the message by using the communication key shared with the TTP. Next, server determines that the tag group is to be transferred to the multi-owner set . It first verifies that is under the authority of , obtains the secret value that is used to generate the communication key of all individual tags in tag group , and uses this secret value to encrypt each tag ID to update the communication key of the new owner’s back-end server.
In Step 11, after server of the old owners receives messages , it decrypts the message by using the communication key shared with the TTP and determines that is part of the transfer message of the requesting owner in . The server then uses group communication key to encrypt the OT, , , and group ID into message . Subsequently, it uses the communication key shared with owner to encrypt message into message , which is then sent to owner
In Step 12, after the owner receives messages , it decrypts the message by using the communication key shared with server to extract message , which is sent to tag group as a broadcast message. When any tag receives message , it confirms whether the group tag ID in the message matches the ID of the tag group to which it belongs. After confirming that it belongs to the tag group , each tag uses the communication key shared with server to decrypt and compare the OT. Tag uses message to calculate the secret value that is used to generate the communication key of all individual tags in tag group . Next, the tag uses the calculated secret value to decrypt message , checks whether tag group matches the claimed tag group ID, and then checks whether the random numbers are identical (if they are identical, then they represent the same communication). After authentication, the secret value is used to encrypt tag ID to replace tag and the communication key of the back-end server. When all tags in tag group are completely updated, the ownership of this group has been transferred from the multi-owner set to the set .
3.4. Group Update and Balancing of the Key Tree
When implementation of the ownership transfer protocol is complete, the shared key on each transferred tag has been updated to the key shared with the back-end server of the new multi-owner set. Therefore, the server of the old owners can no longer be updated. However, a group communication key has yet to be established. When a member joins or leaves a group, the group communication key must be updated, and the balance state of the tree architecture must be checked. After the tag group architecture has been reconstructed in the server, existing methods for updating the group communication key, such as the approach proposed by Xu et al. [34], are used to update the communication key shared between groups.
4. Security Analysis
The method proposed in this study assumes that, after the mobile reader and back-end server authenticate each other by using an existing network security architecture, a shared communication key can be used in the subsequent protocol to identify the message deliverer and that, during communication, a shared communication key can be used for encryption to ensure secure communication. Hence, the following sections provide a security analysis of confidentiality between the tag and mobile reader, anti-replay attack, anti–man-in-the-middle attack, forward and backward secrecy, the windowing problem, location privacy protection, and an anti-DoS attack.
- A.
- Confidentiality
Communication between a mobile reader and a back-end server is encrypted using a shared communication key to ensure secure communication. Communication between a tag and mobile reader is encrypted using a communication key shared by the tag and the back-end server and a management key shared by the tag and the TTP. Attackers cannot decrypt the encrypted messages and, thus, cannot access the communicated information.
- B.
- Anti-Replay Attack
A random number and the communicated message are collectively encrypted so that, during the process of communication at all stages of the protocol, the sent message read by each tag changes, according to the random number. In step 1, if the attacker resends M1, the server will easily find it after decryption. This prevents attackers from completing authentication by replaying the previously acquired message.
- C.
- Anti–Man-in-the-Middle Attack
Communication among a mobile reader, tags, and the back-end server is encrypted, and a communication key shared among these three entities is used to confirm identity in order to proceed with ownership transfer. Additionally, because attackers do not have a shared key and cannot complete authentication through replay attacks, attackers cannot counterfeit the reader or tag to implement a man-in-the-middle attack.
- D.
- Forward Secrecy
In the protocol, the authentication and communication encryption key currently used by a tag are not given to the new owner. Instead, the new owner receives a new communication key, which is derived from a tag ID encrypted with a secret value that is randomly generated by the TTP. Therefore, the new owner cannot obtain the tag’s original communication key to decrypt any messages that were encrypted previously using the tag’s original key. Thus, forward secrecy is achieved.
- E.
- Backward Secrecy
After the new owner acquires the new communication key of a tag, the TTP updates the key, which is shared between the old owner and the tag, through the old owner. Because the old owner’s server and mobile reader have no access to the management key shared by the tags and the TTP, the old owner cannot access the secret value, which is randomly generated by the TTP and used to generate a new communication key. Therefore, the old owner cannot continue to track the tag’s subsequent information. Thus, backward secrecy is achieved.
- F.
- Windowing Problem
Because the old owner’s server and mobile reader have no access to the management key shared by the tags and the TTP, the old owner cannot access the secret value, which is randomly generated by the TTP and used to generate a new communication key. Moreover, neither the old owner nor attackers can successfully update the tag’s key by replaying the update-key message in the previous stage. This approach, thus, prevents the windowing problem in which both old and new owners hold tag ownership.
- G.
- Location Privacy Protection
In the protocol, the mobile reader is only responsible for sending out a message because a mobile reader in a mobile RFID environment may be a malicious attacker. Therefore, the message sent between a tag and the back-end server is encrypted along with a random number. Thus, the attacker cannot track the tag by analyzing the content of the message sent between the mobile reader and tag or by analyzing the messages sent at different stages between the mobile reader and tag. In other words, the method proposed in the present study can protect the tag’s location privacy.
- H.
- Asynchronous Denial-of-Service Attack
Asynchronous DoS attack on the back-end server and tags may occur when a message is lost or when attackers maliciously block a message. In the proposed protocol, the back-end server retains the tags’ keys before and after they are updated. Therefore, if the update-key message is lost or maliciously blocked, then the tag’s pre-updated key can be used to decrypt the message sent by a tag, which enables the owner to read the message. This is otherwise prevented when the server and tag become asynchronized.
Table 3 presents a comparison of the proposed protocol and other ownership transfer methods in terms of the following security concerns: forward secrecy (FS), backward secrecy (BS), replay attack (RA), DoS attack, the windowing problem (WP), and group ownership transfer (GO). In Table 3, “V” represents a secure protocol and “X” denotes an unsecure protocol.

Table 3.
Comparison of security.
5. Performance Analysis
This section details the analysis conducted in the present study on the calculation and information load of the proposed ownership transfer method. In this study, the proposed method is compared with other methods by analyzing and comparing the calculation load required to transfer the ownership of n tags belonging to old owners os to new owners ns. TE represents the amount of time required to calculate encryption and decryption once. TLE represents the amount of time required to calculate lightweight encryption and decryption once. TRNG represents the amount of time required to generate a random number, and TH represents the amount of time required to compute a hash function once.
The following aspects were compared between the method proposed in the present study and those proposed by Kapoor et al. [26] and Sundaresan et al [27,28]: the calculation load of tags, readers, servers, and the information load of the whole protocol. In the multi-owner single-tag ownership transfer method developed by Kapoor et al., encryption/decryption, hash functions, exclusive or (XOR), and random numbers are used. In their protocol, tags are transferred individually. To transfer a large number of tags, the protocol must be implemented multiple times, which results in decreased efficiency. Similarly, the multi-owner multi-tag ownership transfer method presented by Sundaresan et al. uses only pseudorandom number generator (PRNG), XOR, and random numbers. However, in their protocol, the group key shared among the server, the tag group, and the owners is used to individually generate transfer request messages for the transfer of each tag. Consequently, transfer efficiency is affected by the number of owners and tags. The method proposed in the present study uses k-ary to generate a tag group key tree architecture, which leads to different situations when transferring ownership.
Situation (1): the whole group of tags is transferred, as illustrated in Figure 6. In this situation, the server only requires one set of group keys to notify all tags of the transfer request. Regarding the calculation, each tag only requires encryption/decryption to be performed six times. The reader, in order to send the message to all tags and read the message returned by each tag to the server, only needs to perform multi-owner confirmation once and message broadcasting once. The server is only required to perform the calculation once.
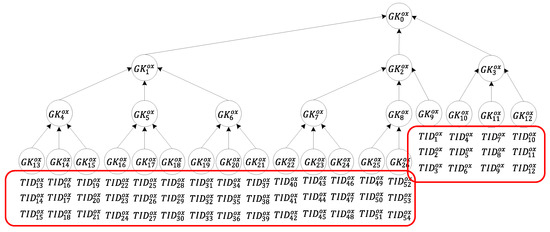
Figure 6.
Tag transfer in Situation (1).
Situation (2): Only two tag groups are transferred, as shown in Figure 7. In this situation, the server requires two sets of group keys and to notify all tags of the transfer request. Regarding calculation, each tag is only required to conduct encryption/decryption computation six times. The reader, in order to send a message to all tags to be transferred and read the message that is returned by each of these tags to the server, is only required to perform multi-owner confirmation once and message broadcasting twice. The server is only required to perform calculation twice.
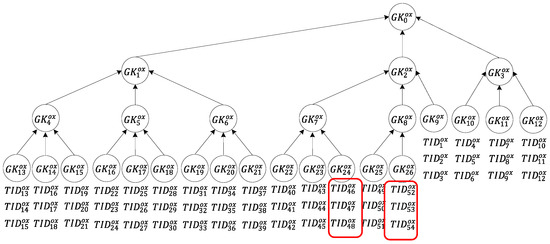
Figure 7.
Tag transfer in Situation (2).
Situation (3): Only a single tag is not transferred, as depicted in Figure 8. In this situation, the server requires four sets of group keys and two sets of tag keys , , , , , and to notify the tags that are to be transferred of the transfer request. Regarding calculation, each tag is only required to conduct encryption/decryption computation six times, and the reader, in order to send a message to all tags to be transferred and read the message that is returned by each of these tags to the server, is only required to perform multi-owner confirmation once and message broadcasting six times. The server only needs to perform the calculation six times.
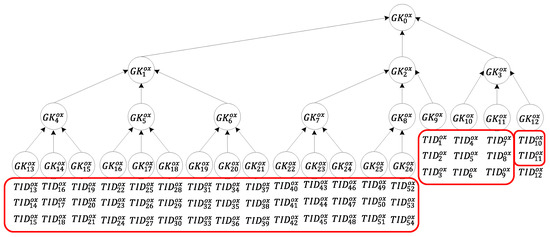
Figure 8.
Tag transfer in Situation (3).
The calculation load of the proposed ownership transfer method is indicated in Table 4, which provides an analysis of all components participating in the ownership transfer process. Compared with the encryption method, XOR operation and comparison operation exhibit a lighter calculation load and, thus, are negligible. In Table 4, message encryption and decryption are assumed to be performed through one calculation. The server calculates TRNG once for each key produced.

Table 4.
Performance comparison.
Figure 9, Figure 10 and Figure 11 compare the calculation load of the tags, readers, and servers between the method proposed in the present study and existing multi-owner ownership transfer methods.
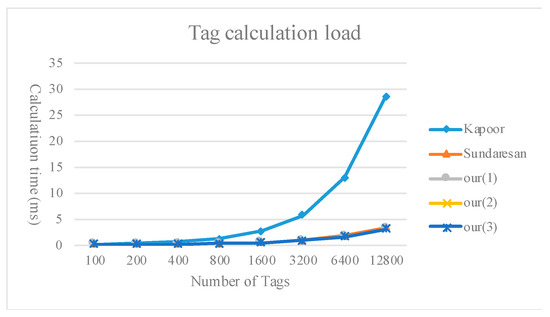
Figure 9.
Comparison of the tag calculation load.
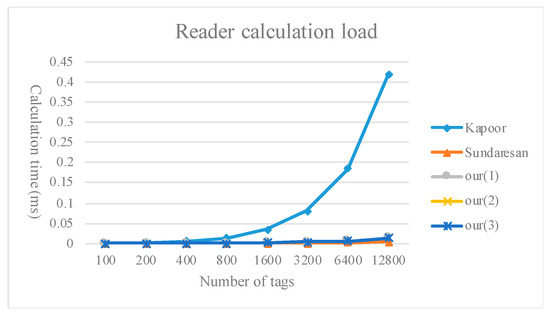
Figure 10.
Comparison of the reader calculation load.
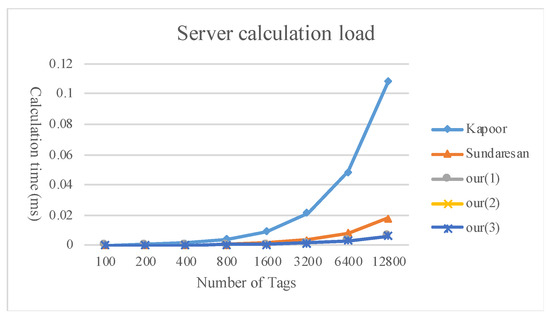
Figure 11.
Comparison of the server calculation load.
6. Conclusions
The present study proposes a secure, high-performance multi-owner partial tag ownership transfer protocol. A threshold scheme is adopted to ensure that the consent of a specific number of old owners is obtained before the ownership of a tag group can be partially transferred to new owners. This study introduces a method that can transfer the ownership of one, some, or all tags. The calculation load of the tags, readers, and corresponding servers was analyzed and compared with those of other multi-owner ownership transfer protocols. The results verified the high performance of the proposed protocol. Additionally, compared with other multi-owner ownership transfer methods, the proposed protocol is effectively more immune to RFID-defined attacks, such as eavesdropping, replay, man-in-the-middle, and DoS attacks. With the proposed protocol, the owners at the front end of a supply chain can transfer their ownership securely and efficiently.
Author Contributions
J.-N.L. and M.-H.Y.: conceived and designed the protocols. J.-N.L.: security and performance analysis, wrote the paper. J.-N.L.: review and editing. All authors have read and agreed to the published version of the manuscript.
Funding
The Taiwan Information Security Center (TWISC) and the Ministry of Science and Technology (MOST) under Grant Nos. MOST 108-2218-E-011-021 and MOST 108-2221-E-033-016 funded this research.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Juels, A. RFID security and privacy: A research survey. IEEE J. Sel. Areas Commun. 2006, 24, 381–394. [Google Scholar] [CrossRef]
- Seidler, C. RFID Opportunities for Mobile Telecommunication Services, ITU-T Lighthouse Technical Paper. 2005. Available online: http://www.itu.int/ITU-T/techwatch/rfid.pdf (accessed on 17 December 2019).
- Lee, H.; Kim, J. Privacy threats and issues in mobile RFID. In Proceedings of the First International Conference on Availability, Reliability and Security (ARES’06), Vienna, Austria, 20–22 April 2006. [Google Scholar]
- Engberg, S.J.; Harning, M.B.; Jensen, C.D. Zero-knowledge Device Authentication: Privacy & Security Enhanced RFID preserving Business Value and Consumer Convenience. In Proceedings of the Second Annual Conference on Privacy, Security and Trust, Fredericton, NB, Canada, 13–15 October 2004; pp. 89–101. [Google Scholar]
- Van Deursen, T.; Mauw, S.; Radomirović, S.; Vullers, P. Secure ownership and ownership transfer in RFID systems. In Proceedings of the European Symposium on Research in Computer Security, Saint-Malo, France, 21–23 September 2009; pp. 637–654. [Google Scholar]
- Osaka, K.; Takagi, T.; Yamazaki, K.; Takahashi, O. An efficient and secure RFID security method with ownership transfer. In RFID Security; Springer: Boston, MA, USA, 2008; pp. 147–176. [Google Scholar]
- Juels, A.; Pappu, R. RFID privacy: An overview of problems and proposed solutions. IEEE Secur. Priv. 2005, 3, 34–43. [Google Scholar]
- Fouladgar, S.; Afifi, H. An efficient delegation and transfer of ownership protocol for RFID tags. In Proceedings of the First International EURASIP Workshop on RFID Technology, Vienna, Austria, 24 September 2007; pp. 68–93. [Google Scholar]
- Taqieddin, E.; Al-Dahoud, H.; Niu, H.; Sarangapani, J. Tag Ownership Transfer in Radio Frequency Identification Systems: A Survey of Existing Protocols and Open Challenges. IEEE Access 2018, 6, 32117–32155. [Google Scholar] [CrossRef]
- Kapoor, G.; Piramuthu, S. Vulnerabilities in Some Recently Proposed RFID Ownership Transfer Protocols. IEEE Commun. Lett. 2010, 14, 260–262. [Google Scholar] [CrossRef]
- Jäppinen, P.; Hämäläinen, H. Enhanced RFID security method with ownership transfer. In Proceedings of the 2008 International Conference on Computational Intelligence and Security, Suzhou, China, 13–17 December 2008; pp. 382–385. [Google Scholar]
- Zuo, Y.J. Changing Hands Together: A Secure Group Ownership Transfer Protocol for RFID Tags. In Proceedings of the 2010 43rd Hawaii International Conference on System Sciences, Honolulu, HI, USA, 5–8 January 2010; pp. 1–10. [Google Scholar]
- Yoon, E.J.; Yoo, K.Y. Two Security Problems of RFID Security Method with Ownership Transfer. In Proceedings of the 2008 IFIP International Conference on Network and Parallel Computing, Shanghai, China, 18–21 October 2008; pp. 68–73. [Google Scholar]
- Chen, H.B.; Lee, W.B.; Zhao, Y.H.; Chen, Y.L. Enhancement of the RFID Security Method with Ownership Transfer. In Proceedings of the 3rd International Conference on Ubiquitous Information Management and Communication, SKKU, Suwon, Korea, 15–16 January 2009; pp. 251–254. [Google Scholar]
- Yang, X.; Xu, C.; Li, C. A privacy model for RFID tag ownership transfer. Secur. Commun. Netw. 2017, 2017, 5084636. [Google Scholar] [CrossRef]
- Dimitriou, T. Key Evolving RFID Systems: Forward/Backward Privacy and Ownership Transfer of RFID Tags. Ad Hoc Netw. 2016, 37, 195–208. [Google Scholar] [CrossRef]
- Lee, C.C.; Cheng, C.L.; Lai, Y.M.; Li, C.T. Cryptanalysis of Dimitriou’s key evolving RFID systems. In Proceedings of the Fifth International Conference on Network, Communication and Computing, Kyoto, Japan, 17–21 December 2016; pp. 229–233. [Google Scholar]
- Kapoor, G.; Piramuthu, S. Single RFID tag ownership transfer protocols. IEEE Trans. Syst. Manand Cybern. Part C (Appl. Rev.) 2010, 42, 164–173. [Google Scholar] [CrossRef]
- Yang, M.H. Across-authority Lightweight Ownership Transfer Protocol. Electron. Commer. Res. Appl. 2011, 10, 375–383. [Google Scholar] [CrossRef]
- He, L.Y.; Gan, Y.; Yin, Y. Secure Group Ownership Transfer Protocol with Independence of Old Owner for RFID Tags. Comput. Model. New Technol. 2014, 18, 209–214. [Google Scholar]
- Jannati, H.; Falahati, A. Cryptanalysis and enhancement of a secure group ownership transfer protocol for RFID tags. In Proceedings of the Global Security, Safety and Sustainability & e-Democracy, Thessaloniki, Greece, 24–26 August 2011; pp. 186–193. [Google Scholar]
- Molnar, D.; Soppera, A.; Wagner, D. A scalable, delegatable pseudonym protocol enabling ownership transfer of RFID tags. In Proceedings of the Selected Areas in Cryptography, Kingston, ON, Canada, 15–17 August 2005; Volume 3897, pp. 276–290. [Google Scholar]
- Tsai, K.Y.; Luo, J.N.; Yang, M.H.; Liew, W.T. Novel designated ownership transfer with grouping proof. Appl. Sci. 2019, 9, 724. [Google Scholar] [CrossRef]
- Yang, M.H.; Xie, K.P. TTP-Based Group Ownership Transfer in A Mobile RFID Environment. Int. J. Digit. Content Technol. Its Appl. 2013, 7, 51. [Google Scholar]
- Yang, M.H. Secure Multiple Group Ownership Transfer Protocol for Mobile RFID. Electron. Commer. Res. Appl. 2012, 11, 361–373. [Google Scholar] [CrossRef]
- Kapoor, G.; Zhou, W.; Piramuthu, S. Multi-tag and Multi-owner RFID Ownership Transfer in Supply Chains. Decis. Support Syst. 2011, 52, 258–270. [Google Scholar] [CrossRef]
- Sundaresan, S.; Doss, R.; Zhou, W. Secure ownership transfer in multi-tag/multi-owner passive RFID systems. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013; pp. 2891–2896. [Google Scholar]
- Sundaresan, S.; Doss, R.; Zhou, W.; Piramuthu, S. Secure Ownership Transfer for Multi-tag Multi-owner Passive RFID Environment with Individual-owner-privacy. Comput. Commun. 2015, 55, 112–124. [Google Scholar] [CrossRef]
- Munilla, J.; Burmester, M.; Peinado, A. Attacks on ownership transfer scheme for multi-tag multi-owner passive RFID environments. Comput. Commun. 2016, 88, 84–88. [Google Scholar] [CrossRef]
- Poschmann, A.; Leander, G.; Schramm, K.; Paar, C. New light-weight crypto algorithms for RFID. In Proceedings of the 2007 IEEE International Symposium on Circuits and Systems, New Orleans, LA, USA, 27–30 May 2007; pp. 1843–1846. [Google Scholar]
- Ågren, M.; Hell, M.; Johansson, T.; Meier, W. Grain-128 a: A new version of Grain-128 with optional authentication. Int. J. Wirel. Mob. Comput. 2011, 5, 48–59. [Google Scholar] [CrossRef]
- Harn, L. Group-oriented (t, n) threshold digital signature scheme and digital multisignature. IEEE Proc. Comput. Digit. Tech. 1994, 141, 307–313. [Google Scholar] [CrossRef]
- Zhou, J.; Ou, Y.H. Key tree and Chinese remainder theorem based group key distribution scheme. In Proceedings of the International Conference on Algorithms and Architectures for Parallel Processing, Taipei, Taiwan, 8–11 June 2009; pp. 254–265. [Google Scholar]
- Xu, L.; Huang, C. Computation-efficient multicast key distribution. IEEE Trans. Parallel Distrib. Syst. 2008, 19, 577–587. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).