1. Introduction
In recent innovations and applications, the involvement of a cyber-physical system (CPS) can be seen widely in different areas of research such as business, intelligent driving system, tele-operated surgeries and healthcare systems. The roots of CPS is older, however and gained attention when Helen Gill through this concept in the air at the National Science Foundation (NSF). The CPS was initially introduced by Lee [
1] in a NSF workshop where they discussed how physical process and computations were integrated. Presently, it has revolutionized E-healthcare technology up to the new heights of advancements [
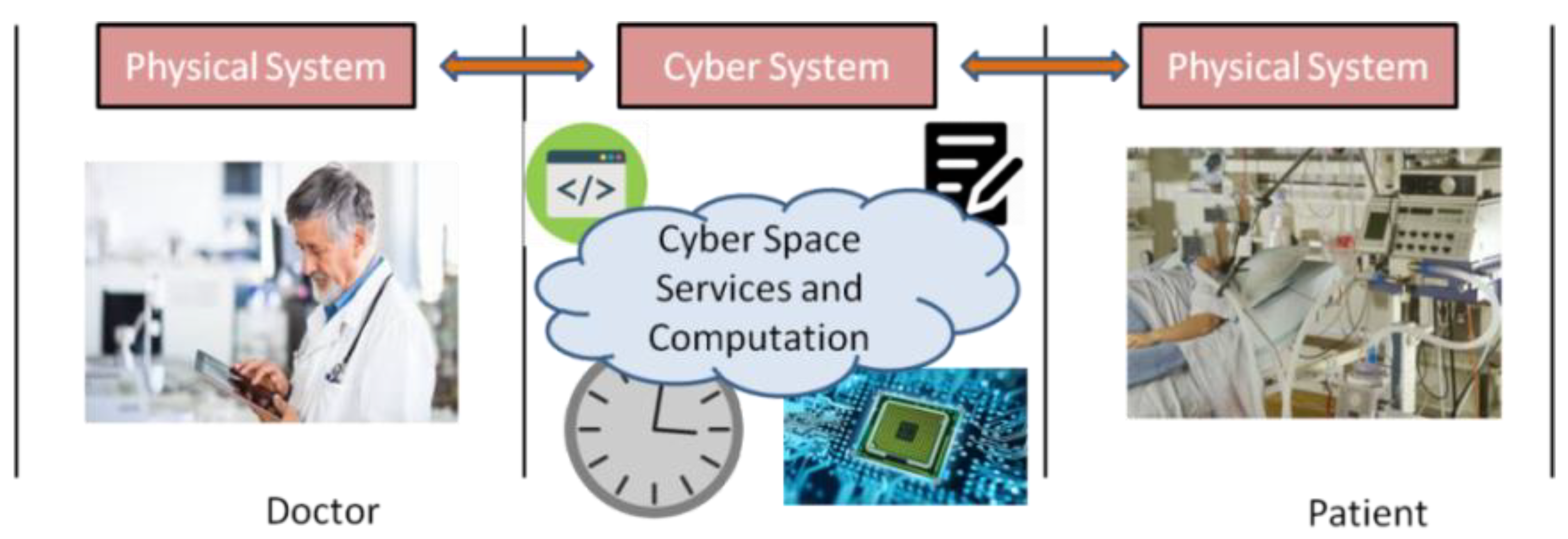
2] in order to fulfill the user’s expectations in the tele-operated mode of healthcare services. An E-healthcare CPS is generally a combination of a cyber-system of networks and physical system of sensors, medical equipment that provides the monitoring data to the practitioners /experts. This facility allows the patient to be observed from remote location by the medical practitioners where the data is observed either over a wireless network, wired network or mixed network. The diagram in
Figure 1 shows an E-health CPS where practitioner monitors the health of their patient over the cyber space. Here, the health data from the equipment is transmitted through the cyber space to the practitioners at remote location. The cyber space consists of a network and an intelligent computational components where the whole working of CPS lies mostly on the intelligent component. However, the healthcare services are sometime critical and severely constrained with several parameters such as energy, risk, reliability, capacity and availability. Lots of researchers are seeking to strengthen the CPS. However, none of them have been concerned about their computational procedures. Recently, it has been found that the consumption of energy is a major issue for performing the computation and in CPS it is recommended to design an energy-efficient CPS. Furthermore, due to the environmental bar on energy resources, it is efficient to consume resources wisely. Therefore, research in CPS leads to green computations. Also, sometimes the working of CPS is found for critical services and when we are considering critical healthcare then it can be a matter of loss of life. Critical healthcare services are needed to be provided to the patient within requested service time (RST). The RST is the time for which a patient can survive, moreover, the RST of the patient also relies on the mean-time-to-failure (MTTF) of the services. The parameters discussed in the above paragraph need to be firmed up by providing agreements between service providers and users. These agreements are known as service-level-agreements (SLAs). Here, in the case of critical healthcare CPS, the SLAs are drawn in between practitioner and patient in terms of RST and MTTF of the service. These SLAs are the promise toward the satisfaction of services and provide the quality of service (QoS).
For the best explanation, there is a huge literature available to support the proposed system model and concepts. Although healthcare services are important requirements in society, sometimes risk of life loss is associated with the services. Therefore criticality constraint has to be applied. The continuity constraint to these applications is a very important parameter to fulfil the availability of energy requested to transmit the data between two specific ends. The healthcare data is sometime important and critical and must not be tempered; therefore, there is a need to propose some framework that provides a critical and energy-efficient CPS during the response of critical services. Furthermore, along with critical and energy-efficient CPS, security is considered to a great concern where patient health data is assumed to be confidential from ethical and legal perspectives. In the above paragraphs and literature, it has been analyzed that the discussed issues are highly sensitive toward the working of a CPS. Therefore, in this paper, we are considering the energy and SLA constraints collectively towards the proper functioning of CPS. Also, here we are assuming that our physical system is perfect and in functioning order. CPS has gradually becoming a widespread replacement technique with sensible cost-efficient emulation for connectivity to the family networking and community; it is officious to venture a proficient and safe communication mechanism. In CPS, security can be agreed simply because of its broadcasting, dynamic and distributed nature. Consequently, an ornate verification approach and a secure data transmission practice should be vital to promise that only legitimate devices have access to a variety of services with well-organized network recital. However, over these networks (wired/wireless), a patient’s data can be compromised due to the attacks. Therefore, special attention has been paid towards designing a secure architecture toward CPS. During the real-time transmission of messages, personal communication between patient and practitioner or storage of the patient’s report, there may be a possibility of an attack happening. A malicious node or a user may enter into an environment or hack one more legitimate node to behave maliciously where the attackers aim is to steal the communication between practitioner and patient, forge the patient’s reports, or perform some malicious activities in order to consume the network resources or slow down the communication process.
The proposal of the algorithm and mathematical formulation purely depends on the amount of healthcare data to be transmitted between two specific ends. The proposed mechanism follows end-to-end mechanism; therefore, the continuous maximum flow of healthcare data depends on the first and second equation. To deal with the workload, the maximum capacity has been considered at links. However, to deal with constant flow condition, the capacity of the path has been considered minimum with respect to the maximum healthcare data to be transmitted. Therefore, there is a need to propose some security mechanisms for an E-health CPS along with critical and energy efficient mechanisms. In order to ensure security during data transmission or personal communication between patient and practitioner or the storage of a patient’s report where malicious nodes or users are willing to disrupt the legitimate users or sensors, there is a need to deal with this issue.
The rest of the paper is structured into sections.
Section 2 draws on the related work of the problem.
Section 3 represents the proposed algorithms and preliminaries of the paper. Empirical analysis is carried out to highlight the theoretical results in
Section 4.
Section 5 is used for illustration of proposed algorithm and its time complexity. Experiment setup, results and discussion is given in
Section 6. Finally, conclusion and future directions are given in the last section.
2. Related Work
With the passage of time, it has been seen that researchers from eminent research fields pioneered the powerful methods and tools to deal with the emerging CPS [
3]. Development in physical systems improved CPS via advances in state space analysis, time and frequency domain analysis, tracking, optimization and filtering etc. Also, a number of scientists were concerned about the development of computational components technology with the design of new programming, body area sensors, biomedical sensors, computer system reliability, fault tolerance and cyber security. The below section discussed some of the energy SLA efficient, security frameworks needed to firm a strong basis for the development of proposed E-healthcare systems in a CPS.
The author in [
4] discussed the importance of CPS in next-generation applications for the computing and integration of different applications such as transportation, health, manufacturing, energy and interdisciplinary applications. The functioning of CPS lies in three basic components sensing, computing/processing and networking [
5]. The continued advances in wireless sensor networks (WSNs), medical sensors and reliable networks extended the involvement of CPS throughout in the field of E-healthcare and home-to-hospital (HTH) care or vice versa [
6,
7]. These applications became involved in body-area sensor networks and medical sensors, and therefore the research in this area became a hot topic [
8,
9]. Various researchers added their efforts to make these healthcare services easy and compatible using these sensors. However, it is difficult to manage wired sensor networks, and therefore the advancement of these sensors depends on the wireless sensor networks (WSNs) which gives the more comfort to the practitioner and patient. In addition to this, sometimes these healthcare services have been provided at remote locations via networking. This health data transmission has been requested as quickest with minimum delay. A number of authors [
10,
11,
12,
13,
14,
15] have been associated with the quickest path problem (QPP).
As this point, the health data of patient is helpful to provide necessary diagnostic /treatment/prescription to deal with the matter of patient life [
16]. It is thanks to researchers that they have been provided with better solutions to deal with this compromising situation [
17]. To add to this, while we deals with the wireless, wired or mixed sensor network then the health data over this are severely affected by the certain constraints [
5] like energy, storage capacity, service level agreements, intelligent computing and processing etc. A number of authors have been associated with the different sections of the CPS [
5,
18]. However, lots of research has been underway in the field of networking to support the critical and continue health data transmission in the CPS [
19].
In order to manage abnormal heart rate and cardiac diseases variability, authors in [
20] have proposed a fractal technique for pacemaker design using a constrained horizon optimal controller issue. The proposed approach is achieved by moulding the dynamics of heart rate using fractional differential and calculus variations. Finally, along with practical implementation, researchers have discussed its hardware complexity. Also, authors in [
21] have proposed an approach in order to facilitate the optimizing and designing of robust and efficient CPS for reducing diabetic costs in healthcare. The authors have designed a hardware model and proposed a mathematical model for amending the insulin injection problem for resolving the multi-fractal control issue. The accuracy of the proposed mathematical model is validated against existing non-fractal models. Later, in order to capture cross dependencies in spatial temporal fractal among united processes, authors have proposed a compact mathematical model. The proposed model is generalized and improved the accuracy for dynamic biological processes. Furthermore, the model is validated over certain medical observations [
22]. In addition to this, authors in [
23] have proposed a mathematical scheme for building accurate and compact complex system with the aim of scrutinizing influences and casual effects. In order to specify a single state at a time, the derived framework enables the incorporation of knowledge about inter-events and casual dynamics of magnitude increments. The presented framework permits us to examine the appropriateness of multi-fractional for various complex systems. The proposed approach validates the experimental results over various physiological processes against state of art techniques.
Networking abstractions to make the compatible CPS for healthcare are being developed [
19] and lots of researchers are dealing with this [
24,
25,
26]. Sometimes, healthcare services request reliable and promising health data transmission services [
27,
28,
29]. Recently, it has been found that critical healthcare services relies more over the cyber component such as networking intelligent computing etc. Moreover, the health data is critical and there are requests for the reliable connection of networks [
30,
31,
32]. A second delay in the services can lead to loss of life, and therefore for the need to design a health data transmission system without any violation in service level agreement [
33,
34]. For these types of services these SLAs plays a vital role in the support of CPS. The research in CPS shows the constraints of energy also; therefore, consideration of energy consumption can hold the computation of health data transmission [
35]. Ignorance of energy constraints may interrupt services due to the lack of a sufficient amount of energy for health data transmission [
36,
37]. Also, due to deteriorating conditions of the environment and a bar on consumption of energy resources we are forced to consider these constraints on the data transmission [
38]. In the networks, this confidential healthcare data of patient is requested to be made available to all concerned authorized medical personnel and, therefore, the chances of s security threat exist [
39]. To tackle the crucial healthcare challenges, the authors have proposed a network on chip multi core platform for enabling the efficient molecular interaction among the entities. For analysing the interactions, communication and computation requirements, the authors have designed a high-performance network on chip (NoC) model that sustains a 1.36E5 events/ms throughput by consuming 15 mL energy per 1E5 stochastic events. The proposed approach offers 23% improvement with 20% less energy consumption against regular mesh NoC [
40]. The authors in [
41] have described two major fundamental challenges while designing a CPS framework for personalized healthcare systems. The need of a unifying mathematical description for designing CPS for providing dynamic interactions among cyber states and bio physiological events is considered as one major issue. Furthermore, the author has addressed secondary challenges for building a precise mathematical model for optimizing and designing wireless and wired NoCs.
Furthermore, a number of scientists and researchers have planned various safe routing approaches by defining several trusted and cryptographic based methods. For building the interaction from the outside world, a cyber-physical system must be reliable, efficient and secure. In order to optimize such systems, certain workload features such as non-stationary and self-similarity needed to be established. Authors have improved the CPS framework by enhancing the statistical approaches such as normalization group theory, master equations and fractional derivatives [
42]. In [
43], the authors proposed a feasible attack pattern mechanism against remote state estimation in CPS to analyze its corresponding effect on the performance metrics. To examine the optimal strategies for attacker and sensor, a game theoretic approach is built and the stability for mutually sides is deliberated. To identify the cyber-attack, the authors in [
44] proposed a distributed multi-agent scheme over the protection systems of power grids. The malicious nodes on that protection system mimic legitimate faults and disable communication or cause component failure. The agents in the proposed mechanism employ both physical and cyber properties to strengthen the detection approach. The proposed approach is authorized through a benchmark power structure under several cyber-threat and fault scenarios. In order to explain and analyze the trustworthiness of cyber-physical measuring systems (CPMSs), generalized stochastic Petri nets are adopted by measuring against three metrics, i.e., availability, reliability and security in [
45]. A malicious software spreading dynamics model is presented to learn about the trustworthiness evolution of CPMSs. The author in [
46] proposed a service-oriented development approach for wide-area physical system such as vehicular networks and smart grid. Dissimilar to the traditional approach, the proposed methodology intrinsically permits disruption-free deployment. The proposed methodology broadens traditional service-oriented computing (SOC) concepts for managing real-time CPS features by pioneering QoS and resource-aware operation phases. The author in [
47] presents a study of synthesis and analysis of the security and reliability of power CPS (PCPS). In this framework, the author considered the security management scenarios attained from the nature of each sort of cyber threat. The authors in [
48] highlight industrial CPS security threats. The efficiency of the proposed scheme is verified by constructing an experimental fit. The simulated results reveal that the scheme deliberates a highly accurate solution that can effectively work in real-time scenarios. A number of secure approaches have been proposed for CPS against various applications such as industries, smart homes, and E-health. However, none of the proposed mechanism can provide the security in real-time scenarios with minimum delay, as time is also considered to be an important parameter while considering a E-health care CPS. A significant delay to ensure the security or legitimate the requested user allow number of intruders to analyse or consume the network resources. Therefore, along with a SLA critical and energy efficient mechanism, a secure E-healthcare CPS is needed to attract the users to rely on this application.
In literature, CPS and its applications have been discussed widely and rigorously. In this paper, the authors have tried to add the recent issues related to healthcare applications of CPS. The contribution can be seen as we have considered the energy constraint for the support of continuity of services for healthcare. This can be seen with the perspective of green computing which provides sustainable healthcare service of CPS. While we consider healthcare services, the assured services are the utmost requirement, and therefore another consideration can be seen by proposing SLAs for the healthcare data-transmission services. These SLAs are useful to support the critical healthcare application with the service assurance of CPS. In addition to this, sometimes healthcare data is confidential and, therefore, we have proposed a secure routing mechanism by doing some adjustment to the AODV protocol. The proposed security mechanism efficiently prevents the disruption of data packets during the transmission by addressing the security threat i.e., grey hole or black hole attack. The proposed method is confirmed against traditional routing mechanisms over several network metrics. The proposed approach is analyzed against the average number of paths, mean hop counts for path and mean energy efficiency. These results have been discussed for both cases without the involvement of a malicious device and with the involvement of a malicious device.
4. Empirical Analysis
Generally, there are
different capacities
present in any CCCN. The minimum energy and SLA cooperative link capacity is given below in Equations (13) and (14), and corresponding to this the minimum SLA and energy supportive link capacity is also revealed as in Equation (15):
The Equation (14), helps to corporate the efficient use of energy for continues data transmission. Therefore, the procedure has been given as follows for the support of continuity.
where
and
are the competence lies in the minimum supportive energy and SLA ability, respectively and link capacity Equation (15) provides the label of least link capacity to hold the criticality and continuity in message transmission if
and
. A
path
is feasible if
. The above equations kind the least capacity which integrates both continues and critical data transmission allowing for the AND rule. The AND rule is mentioned here as for a precise link together parameters Energy and SLA needs to be satisfied. Let us assume that when a link chains several parameters then the logic has been given it as “1” otherwise “0”. Now using possessions of AND gate, the link will support the least capacity
only when both parameter gives logic “1”. Therefore,
has to trail the AND rule for secure, energy and SLA-efficient healthcare message transmission for task-critical relevance. From Equation (15),
number of sub-networks has been sort and every link has to pursue the given variation for the path capacity
.
Lemma 1. Suppose a pathhas been recognized as thepath in a sub-network then that path has been identified as SLA- and energy-cooperative (SESE).
Proof. Path
is
path in the sub-network, the path capacity
has to follow
, where
. Hence:
□
Lemma 2. Let apathis thought to be a possible path having capacity of path, thenis a path in.
Proof. From above Lemma 1, let
is possible.
□
By satisfying Equation (16), the path
is
path in network
. The computation of path
depends on the shortest path problem (SPP) which follows Dijkastra’s algorithm. The computation of the path depends on the cost function which is taken as link delays i.e.,
.
After Equation (17), Lemma 3 needs to be explained as below:
Lemma 3. Given,is a most favorable path computed bygiven that. In that case, no other most favorable path is there for algorithm SESE having capacity.
Proof. Take;
as a
possible path for the algorithm SESE having capacity
, then
is a path in
.
Hence, cannot be a most favorable path for the algorithm SESE. □
Theorem 1. Considerbe a most favorable path for SESE and. Then,is a most favorable path ofand any most favorable path ofis a most favorable path.
Proof. Given that
is an
possible path for SESE having capacity
, then
is an
path in
. Consider
is a
possible path in network
, then
. Also, if
, then
which disagree with the condition of most favorable path
. In addition to this, using Lemma 3, capacity of
shortest path
in
is
. Hence,
is a
possible path for SESE such that
is the most favorable path. □