A Privacy-Preserving Traffic Monitoring Scheme via Vehicular Crowdsourcing
Abstract
1. Introduction
- First, inspired by the fact that the average speed would be sufficient to achieve traffic monitoring, we propose PPTM, which uses the super-increasing sequence and homomorphic Paillier cryptosystem to realize privacy-preserving speed aggregation and efficient traffic monitoring. Concretely, each vehicle uses a well defined super-increasing sequence to aggregate its multiple speeds and encrypts the aggregated result before uploading it to the RSU. Then, the RSU will aggregate all reports and cooperate with a service provider to calculate each road segment’s average speed. During this process, vehicles’ identity, speed, and location privacy will not be disclosed to any other party.
- Second, we find that the anonymous technologies such as pseudonyms and randomizable signature are not suitable for certain VANET-based applications because of the time link attack. To mitigate this attack, we design a privacy-preserving data aggregation approach. Through a comprehensive security analysis, the proposed PPTM is proven to be secure and privacy preservation. Particularly, the proposed scheme can achieve report privacy preservation, report authentication, data integrity, and identity preservation, as well as defend against the collusion attack. The detailed analysis is given in Section 5.
- Third, we conducted extensive simulations to show PPTM is practical and efficient. Compared with a traditional baseline scheme, PPTM could significantly reduce computational costs and communication overhead, indicating that the proposed scheme can indeed realize real-time traffic monitoring.
2. System Model, Security Requirements, and Design goals
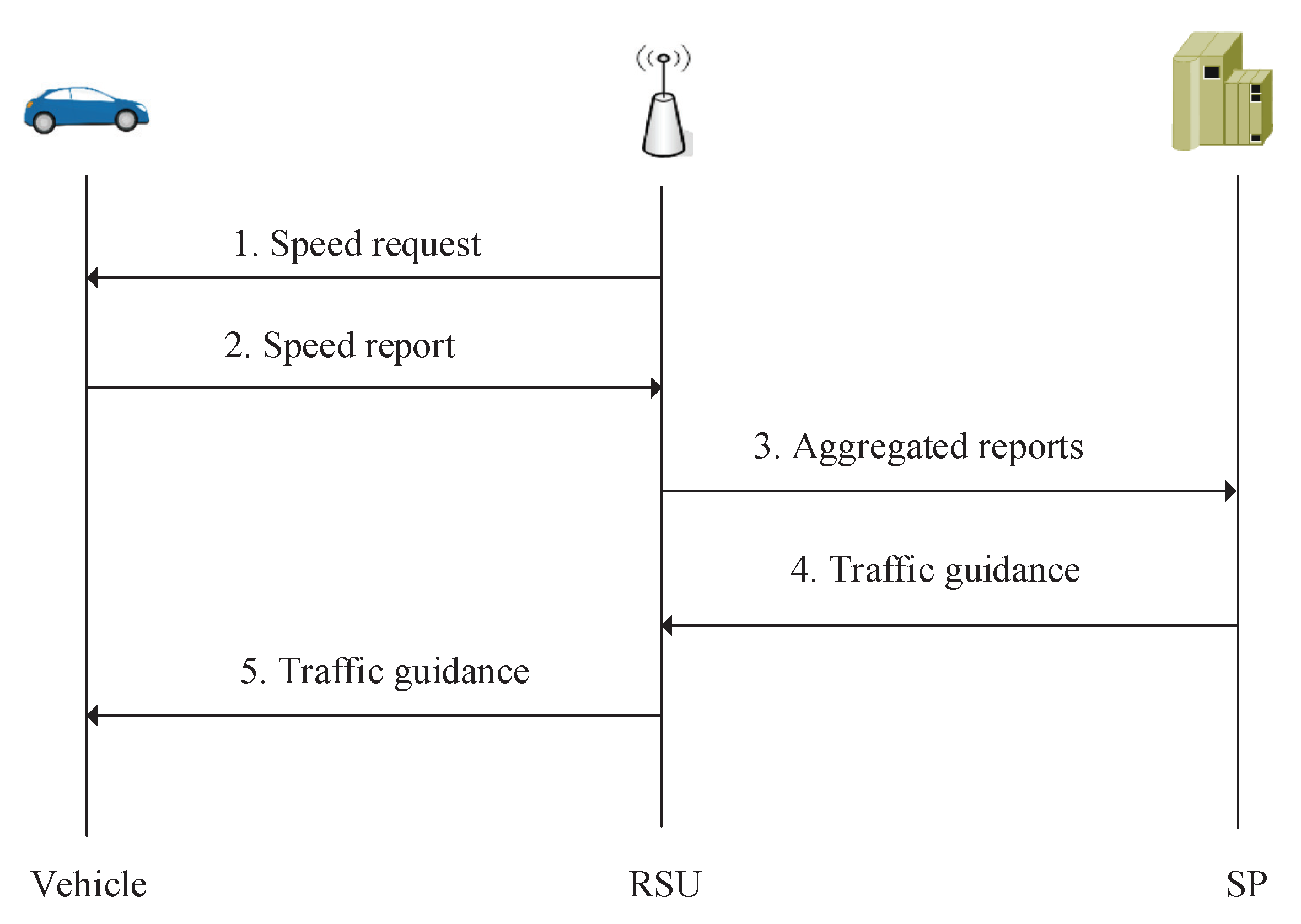
2.1. System Model
- Trust authority (TA): TA is a fully trusted entity that is responsible for the registration of vehicles and RSUs. It builds public/secret key pairs for all entities, and generates sufficient pseudonyms for vehicles before their next registration.
- Vehicles: All vehicles are embedded with OBUs, which enable them to communicate with RSUs and surrounding vehicles through wireless communications. Besides, they also have the ability to generate and run their own homomorphic cryptosystem.
- RSUs: RSUs act as the role of access points, which are widely deployed in the urban area. They can communicate with vehicles via wireless communications and the service provider by wired communications.
- Service provider (SP): SP is a centralized entity that is responsible for providing traffic monitoring services. It connects with all RSUs through fast communication technology, such as wired cables.
2.2. Security Requirements
2.3. Design Goals
3. Preliminaries
3.1. Bilinear Pairings
- Bilinearity: , for all and .
- Non-degeneracy: , for all .
- Computability: can be efficiently computed, for all .
3.2. Paillier Cryptosystem
- Key Generation: With a security parameter , select two large -bit primes , and calculate and the least common multiple of and , i.e., . Then, define a function , and calculate , where . Then, the public/private keys are and .
- Message Encryption: Given a plaintext , after choosing a random value , the message is encrypted as .
- Ciphertext Decryption: Given a ciphertext , the message is recovered as .
4. Proposed PPTM Scheme
4.1. System Initialization
4.2. Speed Request and Speed Reporting
4.3. Privacy-Preserving Report Aggregation
- Step 1. Calculate the aggregated results and based on the encrypted data and as follows.
- Step 2. Use the secret key to generate a signature as
- Step 3. Send the aggregated and encrypted data to the SP.
4.4. Secure Report Reading
- Step 1. Considering , and , the aggregated ciphertexts are still valid ciphertexts of Paillier cryptosystem. Hence, the SP can use the secret key to obtain and as
- Step 2. SP then invokes Algorithm 1 to recover the aggregated vehicles and speed , where and , .
| Algorithm 1: Recover the aggregated report. |
| Input: , and Output: and 1 Set ; 2 for do  5 6 return |
4.5. Traffic Guidance and Identity Tracing
5. Security Analysis
6. Performance Evaluation
6.1. Computational Costs
6.2. Communication Overhead
7. Related Works
8. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Voelcker, J. 1.2 Billion Vehicles On World’s Roads Now, 2 Billion By 2035: Report. Available online: https://www.greencarreports.com/news/1093560_1-2-billion-vehicles-on-worlds-roads-now-2-billion-by-2035-report/ (accessed on 29 July 2014).
- Moskvitch, K. Can a City Every Be Traffic Jam-Free? Available online: http://www.bbc.com/future/story/20140611-can-we-ever-end-traffic-jams/ (accessed on 11 June 2014).
- Wu, C.; Ji, Y.; Liu, F.; Ohzahata, S.; Kato, T. Toward Practical and Intelligent Routing in Vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2015, 64, 5503–5519. [Google Scholar] [CrossRef]
- Abboud, K.; Zhuang, W. Stochastic Modeling of Single-Hop Cluster Stability in Vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2016, 65, 226–240. [Google Scholar] [CrossRef]
- Zhu, L.; Zhang, C.; Xu, C.; Du, X.; Xu, R.; Sharif, K.; Guizani, M. PRIF: A Privacy-Preserving Interest-Based Forwarding Scheme for Social Internet of Vehicles. IEEE Internet Things J. 2018, 5, 2457–2466. [Google Scholar] [CrossRef]
- Wu, D.J.; Zimmerman, J.; Planul, J.; Mitchell, J.C. Privacy-Preserving Shortest Path Computation. In Proceedings of the 23rd Annual Network and Distributed System Security Symposium, San Diego, CA, USA, 21–24 February 2016. [Google Scholar]
- Waze. Available online: https://www.waze.com/ (accessed on 1 January 2016).
- Xu, J.; Xue, K.; Yang, Q.; Hong, P. PSAP: Pseudonym-Based Secure Authentication Protocol for NFC Applications. IEEE Trans. Consum. Electron. 2018, 64, 83–91. [Google Scholar] [CrossRef]
- Yang, Q.; Xue, K.; Xu, J.; Wang, J.; Li, F.; Yu, N. AnFRA: Anonymous and Fast Roaming Authentication for Space Information Network. IEEE Trans. Inf. Forensics Secur. 2019, 14, 486–497. [Google Scholar] [CrossRef]
- Lwamo, N.M.R.; Zhu, L.; Xu, C.; Sharif, K.; Liu, X.; Zhang, C. SUAA: A Secure User Authentication Scheme with Anonymity for the Single & Multi-server Environments. Inf. Sci. 2019, 477, 369–385. [Google Scholar] [CrossRef]
- Du, X.; Chen, H. Security in wireless sensor networks. IEEE Wirel. Commun. 2008, 15, 60–66. [Google Scholar]
- Ni, J.; Lin, X.; Zhang, K.; Shen, X. Privacy-Preserving Real-Time Navigation System Using Vehicular Crowdsourcing. In Proceedings of the IEEE 84th Vehicular Technology Conference, VTC Fall 2016, Montreal, QC, Canada, 18–21 September 2016; pp. 1–5. [Google Scholar]
- Golle, P.; Partridge, K. On the Anonymity of Home/Work Location Pairs. In Proceedings of the 7th International Conference on Pervasive Computing, Nara, Japan, 11–14 May 2009; pp. 390–397. [Google Scholar]
- Zhang, C.; Zhu, L.; Xu, C.; Sharif, K.; Du, X.; Guizani, M. LPTD: Achieving lightweight and privacy-preserving truth discovery in CIoT. Future Gener. Comp. Syst. 2019, 90, 175–184. [Google Scholar] [CrossRef]
- Xue, K.; Hong, J.; Ma, Y.; Wei, D.S.L.; Hong, P.; Yu, N. Fog-Aided Verifiable Privacy Preserving Access Control for Latency-Sensitive Data Sharing in Vehicular Cloud Computing. IEEE Netw. 2018, 32, 7–13. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M.K. Identity-Based Encryption from the Weil Pairing. SIAM J. Comput. 2003, 32, 586–615. [Google Scholar] [CrossRef]
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; pp. 223–238. [Google Scholar]
- Abdalla, M.; Bellare, M.; Rogaway, P. The Oracle Diffie-Hellman Assumptions and an Analysis of DHIES. In Proceedings of the RSA Conference on Topics in Cryptology, San Francisco, CA, USA, 8–12 April 2001; pp. 143–158. [Google Scholar]
- Xu, C.; Lu, R.; Wang, H.; Zhu, L.; Huang, C. TJET: Ternary Join-Exit-Tree Based Dynamic Key Management for Vehicle Platooning. IEEE Access 2017, 5, 26973–26989. [Google Scholar] [CrossRef]
- Boneh, D.; Lynn, B.; Shacham, H. Short Signatures from the Weil Pairing. J. Cryptol. 2004, 17, 297–319. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Random Oracles are Practical: A Paradigm for Designing Efficient Protocols. In Proceedings of the 1st ACM Conference on Computer and Communications Security, Fairfax, VA, USA, 3–5 November 1993; pp. 62–73. [Google Scholar]
- Du, X.; Xiao, Y.; Guizani, M.; Chen, H. An effective key management scheme for heterogeneous sensor networks. Ad Hoc Netw. 2007, 5, 24–34. [Google Scholar] [CrossRef]
- Xiao, Y.; Du, X.; Zhang, J.; Hu, F.; Guizani, S. Internet Protocol Television (IPTV): The Killer Application for the Next-Generation Internet. IEEE Commun. Mag. 2007, 45, 126–134. [Google Scholar] [CrossRef]
- Chim, T.W.; Yiu, S.; Hui, L.C.K.; Li, V.O.K. VSPN: VANET-Based Secure and Privacy-Preserving Navigation. IEEE Trans. Comput. 2014, 63, 510–524. [Google Scholar] [CrossRef]
- Sur, C.; Park, Y.; Rhee, K.H. An efficient and secure navigation protocol based on vehicular cloud. Int. J. Comput. Math. 2016, 93, 325–344. [Google Scholar] [CrossRef]
- Rabieh, K.; Mahmoud, M.M.E.A.; Younis, M.F. Privacy-Preserving Route Reporting Schemes for Traffic Management Systems. IEEE Trans. Veh. Technol. 2017, 66, 2703–2713. [Google Scholar] [CrossRef]
- Wang, L.; Liu, G.; Sun, L. A Secure and Privacy-Preserving Navigation Scheme Using Spatial Crowdsourcing in Fog-Based VANETs. Sensors 2017, 17, 668. [Google Scholar] [CrossRef]
- Du, X.; Guizani, M.; Xiao, Y.; Chen, H. Transactions papers a routing-driven Elliptic Curve Cryptography based key management scheme for Heterogeneous Sensor Networks. IEEE Trans. Wirel. Commun. 2009, 8, 1223–1229. [Google Scholar] [CrossRef]
- Xiao, Y.; Rayi, V.K.; Sun, B.; Du, X.; Hu, F.; Galloway, M. A survey of key management schemes in wireless sensor networks. Comput. Commun. 2007, 30, 2314–2341. [Google Scholar] [CrossRef]
- Lu, R.; Liang, X.; Li, X.; Lin, X.; Shen, X. EPPA: An Efficient and Privacy-Preserving Aggregation Scheme for Secure Smart Grid Communications. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1621–1631. [Google Scholar]







| PPTM | TRPM | |
|---|---|---|
| Vehicle | ||
| RSU | ||
| SP |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, C.; Zhu, L.; Xu, C.; Du, X.; Guizani, M. A Privacy-Preserving Traffic Monitoring Scheme via Vehicular Crowdsourcing. Sensors 2019, 19, 1274. https://doi.org/10.3390/s19061274
Zhang C, Zhu L, Xu C, Du X, Guizani M. A Privacy-Preserving Traffic Monitoring Scheme via Vehicular Crowdsourcing. Sensors. 2019; 19(6):1274. https://doi.org/10.3390/s19061274
Chicago/Turabian StyleZhang, Chuan, Liehuang Zhu, Chang Xu, Xiaojiang Du, and Mohsen Guizani. 2019. "A Privacy-Preserving Traffic Monitoring Scheme via Vehicular Crowdsourcing" Sensors 19, no. 6: 1274. https://doi.org/10.3390/s19061274
APA StyleZhang, C., Zhu, L., Xu, C., Du, X., & Guizani, M. (2019). A Privacy-Preserving Traffic Monitoring Scheme via Vehicular Crowdsourcing. Sensors, 19(6), 1274. https://doi.org/10.3390/s19061274







