Abstract
Agriculture plays an important role for many countries. It provides raw materials for food and provides large employment opportunities for people in the country, especially for countries with a dense population. To enhance agriculture productivity, modern technology such as wireless sensor networks (WSNs) can be utilized to help in monitoring important parameters in thw agricultural field such as temperature, light, soil moisture, etc. During the monitoring process, if security compromises happen, such as interception or modification of the parameters, it may lead to false decisions and bring damage to agriculture productivity. Therefore, it is very important to develop secure authentication and key agreement for the system. Recently, Ali et al. proposed an authentication and key agreement scheme using WSNs for agriculture monitoring. However, it fails to provide user untraceability, user anonymity, and session key security; it suffers from sensor node impersonation attack and perfect forward secrecy attack; and even worse has denial of service as a service. This study discusses these limitations and proposes a new secure and more efficient authentication and key agreement scheme for agriculture monitoring using WSNs. The proposed scheme utilizes dynamic pseudonym identity to guarantee user privacy and eliminates redundant computations to enhance efficiency.
1. Introduction
Agriculture plays an important role for many countries around the world. In some countries, agriculture is not only essential to provide food and raw material supply for its citizen, but also to provide large employment opportunities for its people. In some dense populated countries like India [1], Nigeria [2], and Pakistan [3], agriculture even becomes their economic backbone. Since agriculture is essential for life, when the world population is rising, the demand for agriculture products is also increasing and if there is no improvement in agriculture production, someday people may face challenges about food availability.
Food availability depends on crops productivity and many other diverse factors such as livestock, labor, sophisticated machines, etc. While other diverse factors such as livestock, labor, climates, soils, tools, and technology vary from country to country or even from farm to farm [4]; the factors related to crop productivity almost remain similar anywhere, such as whether the farms have enough water, fertilizer, temperature, light, etc. On the other hand, farmers are also facing many challenges such as labor shortage, natural disaster (drought, flood, typhoon, etc.), land degradation, water availability, climate change, or any other stressors which might bring a decline in crop productivity. If there is no innovation to maintain or even increasing crop productivity, it is possible that someday the world might suffer from food supply shortage. If this happen, it might bring chaos in many countries and people may suffer from poverty, malnutrition, and hunger. Therefore, a good agriculture system to help in managing and facing those many challenges are important. For example, to make sure the crop succeeds, physical or environmental parameters such as temperature, luminance, humidity, wind direction, wind speed, moisture, acidity, water level, pollutant, etc. need to be routinely and constantly monitored. To make crop productivity sustainable, integrating traditional farming methods and information technology such as Wireless Sensor Networks (WSNs) in agriculture can help this necessity. Applications used for WSNs in agriculture may use different kinds of sensor devices to ones in healthcare, forests, urban areas, and the military since their monitoring range, functionality, and power supply status are different. Additionally, wireless sensor network technology for agriculture monitoring can monitor farm temperature, humidity, light, carbon dioxide, soil moisture, acidity, pests, etc., and can be used for plant epidemic monitoring and early warning systems. For the deployment, the sensors in the forest and military must consider the terrain such as rivers, valleys, etc. that are irregular. The distribution of urban sensors must consider factors such as roads and buildings. The sensors for the human body must consider body shape and portability. The sensors in farms are often arranged in rows due to the arrangement of crops. In terms of function, the sensors in forests and farms sense temperature, humidity, light, carbon dioxide, soil moisture, acidity, pests, etc. The urban sensors sense dust, air pollution, temperature, humidity, etc. In addition to sensing sound and images, sensors in the military must sometimes be able to sense toxic or chemical substances.
WSN is a network infrastructure formed by a large number of sensor nodes to wirelessly monitor physical or environmental parameters. It can constantly monitor those important parameters in agriculture and instantly give clear notifications to user/agriculture professionals if some abnormal conditions are found. Therefore, WSNs can be used to manage or even improved crop productivity by monitoring important parameters in agriculture fields that affect the growth of the crops.
Figure 1 shows the structure of agriculture monitoring system using WSNs. Sensor nodes are manually deployed in the agriculture field and then routinely collect the data from physical or environmental parameters. First, these sensor nodes automatically collect data from physical or environmental parameter in the field and then send the collected data to the gateway node via wireless technology. The gateway node then sends the collected data to the user/agriculture professional via Internet. The user/agriculture professional will use these collected data as a basis to help them in decision making. Any misleading data such as false command, data modification, or wrong parameters may lead to a false decision which in turn could bring damage to crop productivity, such as crop failure and low return. It means that these collected data need to be protected from illegal access or data modification since they play an important role in agriculture decision support systems and are very important to help user/agriculture professionals in decision making. To accommodate this purpose, a clear mechanism about how the collected data are exchanged between legal participants is needed. This study proposes a secure and efficient authentication and key agreement scheme in agriculture monitoring system to meet these necessities.
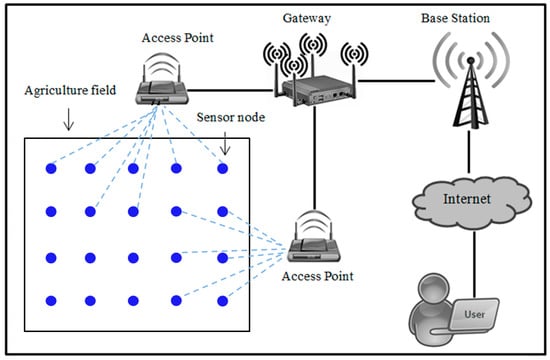
Figure 1.
Agriculture monitoring system model of the proposed scheme.
1.1. Literature Reviews
Agriculture monitoring will help farmers to optimize their natural or artificial resources in their agricultural activities, which will influence their crop productivity. Some initial researches about the framework for agriculture monitoring based on WSNs [5,6,7,8] give important background about WSNs utilization in agriculture, especially about how this system can help decision support systems through better monitoring of their agriculture field. For example, Luis, et al. [5] gave a review about wireless sensor technologies for the agriculture and food industry; Jiber, et al. [6] and Anurag, et al. [7] presented a precision agriculture monitoring framework using WSNs; and Panchard, et al. [8] showed how wireless sensor technology can be used to help farming decision support. However, those existing frameworks do not explain about how those particular participants are authenticated between each other.
In recent years, more and more researchers proposed an authentication and key-agreement scheme for WSNs environment [9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26]. Most of them proposed schemes for general purposes [9,10,11,12,13,14,15,17,24] and few of them proposed schemes for specific purposes [16,18,19,20,25,26]. For example, in 2009, Pecori and Veltri [25] proposed a new alternative key agreement protocol for setting up multimedia sessions between user agents (UAs) without requiring any pre-shared key or trust relationship or PKI, and it has been implemented and integrated in a publicly available VoIP UA. In 2012, Pecori [26] developed a new protocol for establishing a security association between two peers willing to set up a VoIP or multimedia communication through the standard SIP protocol. The proposed protocol is based on the MIKEY protocol and the Diffie-Hellman algorithm for key establishment, and allows the authentication via peer certificates without using any centralized PKI. In the same year, Das, et al. [9] proposed a dynamic password-based user authentication scheme for large-scale hierarchical WSNs. It consists of three entities which are the user, base station, and cluster head. Then, in 2013, Xue et al. [10] proposed a temporal-credential-based for WSNs and Shi et al. [11] proposed a new user authentication protocol using elliptic curves cryptography for WSNs. In 2015, there was even a study about group key management for WSNs [13]. Followed these studies, there were Li et al. [12] and He et al. [15] whose showed weaknesses of Xue et al.’s scheme [10] and both of them then proposed an improved scheme. In 2015, Lee [14] showed weaknesses of Li et al.’s scheme [12] and then proposed an improved scheme using extended chaotic maps. In the same year, Mesit and Brusta [24] proposed a secured node-to-node key agreement protocol, whose shared key is based on a symmetric encryption algorithm to solve the resource-constrained problem. Moreover, in 2016, Kumari et al. [17] mentioned weaknesses of both Li et al.’s scheme [12] and He et al.’s scheme [15] and then proposed an improved scheme using chaotic maps.
Fewer researchers discuss about authentication and key agreement scheme using WSNs for specific purposes, for example, WSNs for healthcare through body sensor networks [16,18,19,20], WSNs for military [21] or multimedia [22] or agriculture monitoring [23].
1.2. Motivation and Contributions
The importance of modern technology utilization in agriculture is already described in above. It also followed by how essential a secure and efficient user authentication and key-agreement scheme for agriculture monitoring using WSNs.
Dynamic pseudonym identity schemes [27,28,29], which were used by both Ali et al.’s scheme [23] and the proposed scheme, are quite popular and widely used in many security researches area. Dynamic pseudonym identity means that the transaction uses anonym identity and that the specific anonym identity dynamically changes in every new transaction. Anonymity is important in the agriculture area because it provides legitimate users with protection of their real identities. In the agriculture environment, we can assume that sensor nodes are put openly in the field. If a system does not provide anonymity, an attacker who targeting a particular participant can easily distinguish a transaction belongs to whom. Then he/she is able to perform attacks to his/her particular target. For example, Alice is an epidemic specialist and works on a farm. An adversary who tries to harm the farm facilities obtains Alice’s identity and knows that she is responsible for assisting in monitoring the farm’s temperature, humidity, and pests. The adversary may perform social engineering or dictionary attacks to obtain Alice’s password or login information, and then can log in to the system for agriculture monitoring to tamper with information and damage facilities. Therefore, by using dynamic pseudonym identity, the scheme is expected to be able to provide un-traceability, privacy and user anonymity to its user. However, Ali et al.’s scheme fails to provide user anonymity and user un-traceability. It also suffered from other severe security compromises such as insider attack, sensor node attack, perfect forward secrecy, and session key security. Moreover, Ali et al.’s scheme even suffered from denial of service which happened after a user/agriculture professional has successfully updated their password.
The rest of this study is organized as follows. Section 2 reviews Ali et al.’s scheme and discusses the detail of security weaknesses in Ali et al.’s scheme. Section 3 presents the proposed scheme. Section 4 presents security analysis of the proposed scheme. Section 5 analyzes security and performances comparisons with Ali et al.’s scheme. Finally, Section 6 draws conclusions.
2. Preliminary
Although this study discusses the weaknesses of Ali et al.’s scheme, this study also recognizes the importance and advantages of their scheme, especially because of the novelty of their study. This study also followed their architecture for agriculture monitoring using WSNs, also utilizes dynamic pseudonym identity and three-factor-security, which are similar with Ali et al.’s scheme. This section consists of three sub-sections which discuss about the importance and advantage of Ali et al.’s scheme, Ali et al.’s scheme, and the weaknesses of Ali et al.’s scheme.
The notations used in Ali et al.’s scheme and in the proposed scheme are elaborated in Table 1.

Table 1.
Notations of the proposed scheme.
2.1. The Importance and Advantage of Ali et al.’s Scheme
Ali et al. proposed a novel authentication and key agreement scheme using WSNs for agriculture monitoring. At first, they mentioned about how important agriculture is for economic systems and how WSNs technology can be utilized to face many challenges that exist in agriculture. Then, they reviewed some literature that related to security in the WSNs environment and summarized security requirements that need to be fulfilled in a scheme. Then, they presented their scheme, the security analysis and the performance evaluation of their scheme.
Compare with other existing WSNs schemes where most of them consist of three entities, Ali et al.’s scheme consist of four entities instead, which are the user/agriculture professional, base station , sensor node, and gateway node. The acts as system administrator and becomes the central entity to authenticate other entities. Without , other entities will never have the chance to truly trust each other in the authentication and key agreement scheme.
2.2. Ali et al.’s Scheme
In 2017, Ali et al. [23] proposed a WSNs scheme for agriculture monitoring, which consists of system setup phase; user/agriculture professional registration phase; login, authentication, and session key agreement phase; password update phase; and dynamic node addition phase.
2.2.1. System Setup Phase
To initialize the organization, the system administrator selects distinct identity for sensor node , where and also selects distinct identity for each gateway node . computes the shared key for , where is the secret key of the base station and computes the shared key for . Finally, keeps into ’s memory and keeps {, } into ’s memory. Then, deploys each sensor node and in a target area. Here, the acts as representative to initialize the identity and the shared key with and .
2.2.2. User/Agriculture Professional Registration Phase
As shown in Figure 2, user/agriculture professional needs to register to the base station . The following steps were executed when want to become a legitimate user in this agriculture monitoring system.
| Step 1: | The selects his/her own identity , password and imprints biometric on the sensor device and then computes , , where is a generate function of fuzzy extractor and are, respectively, secret and public keys. Now, sends to via trustworthy channel. |
| Step 2: | When obtained the registration request from , firstly calculates , , and Afterwards, issues a smartcard having parameters, i.e., and sends it to via the same channel. |
| Step 3: | After obtaining the smartcard from , embeds and in the memory of smartcard, i.e., . |
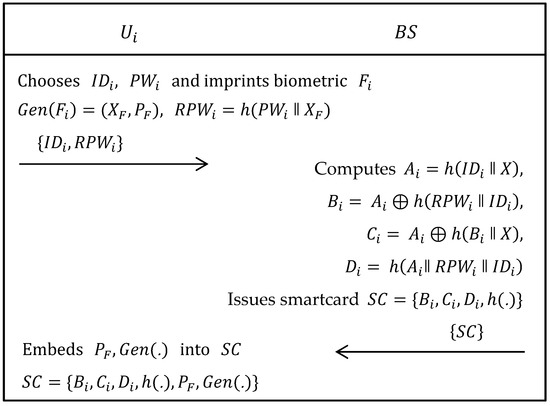
Figure 2.
Registration phase of Ali et al.’s scheme.
2.2.3. Login Phase
When a user/agriculture professional wants to know the environmental information such as temperature, light, humidity, soil etc., he/she has to login to access these information. As shown in Figure 3, the following steps were executed to accomplish this login phase.
| Step 1: | The inserts his/her own smartcard into card reader and inputs , and also imprints on a sensor device. Now, the card reader computes , = , = , = ⊕ , = , = ⊕ and verifies if equals . If this verification holds then the system continues the process. Otherwise, the session is terminated. |
| Step 2: | Now, generates a random nonce and enumerates , , and sends to via public channel. |

Figure 3.
Login, authentication and key agreement phase of Ali et al.’s scheme.
2.2.4. Authentication and Session Key Agreement Phase
As shown in Figure 3, after login phase is successfully authenticated, the authentication and session-key phase were executed in the following steps.
| Step 1: | Upon obtaining the message from , the computes , and checks if holds. If this does not true, then session expires. Otherwise, computes and verifies if equals or not. If it holds, then is legal and goes to next step. Otherwise, the session is rejected. |
| Step 2: | Now, the produces a random nonce and computes , and then sends to via public channel. |
| Step 3: | After getting request message from , the computes and , then checks if two condition and hold. If both conditions are true then it proceeds further. Otherwise, the session is terminated. |
| Step 4: | Now, the generates a random nonce and calculates , and then sends to . |
| Step 5: | Upon obtaining the message from , the computes , and then verifies if two conditions and hold. If both are true, then goes to the next step, Otherwise, the session is terminated. |
| Step 6: | Now, the generates a random nonce , computes , , and sends to via public channel. |
| Step 7: | After getting the message from , firstly verifies if holds. If true, the process continues. Otherwise, the session expires. Then, calculates , and , then checks if . If it holds, the next step proceeds. Otherwise, the session is terminated. |
| Step 8: | The computes and sends to via public channel. |
| Step 9: | After getting the message from , computes and verifies if holds. If it holds, the next step proceeds. |
| Step 10: | The calculates =, and checks if holds. If it holds, mutual-authentication and session-key agreement holds. |
2.2.5. Password Updates or Change Phase
In Ali et al.’s password update or change phase, user modifies his/her password without intervention with the base station. As shown in Figure 4, the following steps were executed to update or change password.
| Step 1: | The inserts his/her own smartcard into the card reader and enters , and imprints on a sensor device. Now, the card reader computes , = , , ⊕ , , = ⊕ and verifies if . If this verification holds, then continues the process. Otherwise, the session is terminated. |
| Step 2: | The enters new password and computes , ⊕⊕, , and . Then, are replaced with . |
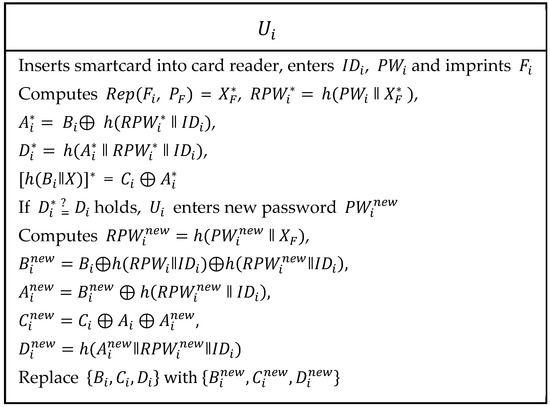
Figure 4.
Password update phase of Ali et al.’s scheme.
2.2.6. Dynamic Node Addition Phase
This phase was used to add, replace, or drop a sensor node in the field. Let becomes a sensor node that will be added into the field. chooses of , calculates and keeps into sensor nodes memory. At last, deploys to the field.
2.3. Weaknesses of Ali et al.’s Scheme
This section discusses the weaknesses of Ali et al.’s scheme in detail. Ali et al.’s scheme weaknesses are divided into three sections which are violation of traceability, insider attack, and denial of service as a service. For the insider attack, it is divided into four other sub-sections which are violation of user anonymity, sensor node impersonation attack, perfect forward secrecy, and violation of session key security. The details are described as follows.
2.3.1. Violation of User Traceability
User traceability means the ability to distinguish if any transactions belong to or came from a certain user. Ali et al.’s scheme was trying to protect users’ real identity by using pseudonym identity , where = . However, the value of is constant in every transaction. By using or checking the , the adversary is able to distinguish existing transactions easily whether they are generated from the same user or not. Since the transaction is easily be distinguished, therefore, the scheme of Ali et al. fails to provide user un-traceability.
2.3.2. Insider Attack
Insider attack happens when a malicious legal participant successfully captures key values of others, such as a shared key, and then uses that key to launch some security violations or attacks. In Ali et al.’s scheme, each sensor node has a shared key with base station , where and it should be known only by and . But, other legal participants such as and can also obtain automatically from a legal transaction during the authentication and session key agreement phase. and obtain when they decrypt and , respectively, where = and . After these legal and obtain , they can use to release some security violations or attacks such as sensor node capture attacks, impersonation attacks, and perfect forward secrecy attacks.
Violation of User Anonymity
User anonymity is important since it protects the real identity of a user and ensures his/her privacy. In Ali et al.’s scheme, once a legal participant obtained a shared key , he/she can catch others’ existing transactions from the public channel, use to decrypt , and then get the of , where . Therefore, the proposed scheme fails to provide user anonymity.
Sensor Node Impersonation Attack
Sensor node impersonation attack occurred when a malicious insider successfully acts as a legitimate sensor node. When a legitimate sensor node is breached or captured by an adversary, it might result in severe security breaches [30], such as eavesdropping, node malfunctioning, denial of service, node subversion, node outage, message corruption, false nodes, and node replication. In Ali et al.’s scheme, when a malicious user or gateway node tries to impersonate a sensor node by using the shared key , first they catch the request message and then decrypt , such as shown in previous subsection Violation of user anonymity. After that, they generate a timestamp , a random nonce and then compute , and , where , , . Then, he/she sends {} to and will send it to the user. Since both the key and procedure are true during computation, both and will not find any suspicious activity and will trust that malicious . Therefore, Ali et al.’s scheme cannot withstand sensor node impersonation attack.
Perfect Forward Secrecy Attack
A perfect forward secrecy attack occurs when an adversary can successfully obtain previous session keys by using a compromised key. In Ali et al.’s scheme, a malicious user or gateway node tries to generate previous session key by using known shared key . First, he/she obtains and through , such as shown in in previous subsection Violation of user anonymity. Then, using and , he/she decrypts , where . Then, he/she calculates and , respectively, where = and . To verify if is true, the attacker compares with previous publicly known in {}. If equals, the adversary has confirmation that is true. Therefore, Ali et al.’s scheme cannot withstand perfect forward secrecy attack.
Violation of Session Key Security
A session key is important to ensure the communication between legal participants in each session is secure. Violation of session key security happens when a non-legal participant can successfully generate a session key with other legal participants. In Ali et al.’s scheme, such as described in previous subsection Sensor node impersonation attack, a malicious insider successfully acts as a legitimate sensor node and is authenticated by a legal user . When authentication and key agreement succeed, they will generate a session key and use that session key to communicate with each other. Therefore, Ali et al.’s scheme fails to provide session key security.
2.3.3. Denial of Services as a Service in Authentication and Key Agreement Phase
Denial of Service as a Service (DoSaaS) happened when a service cannot continue to the next step simply because of the incompatibility procedures of the exchange scheme or because of false data calculation procedures in the scheme. In Ali et al.’s scheme, the denial of services as a service happens after user successfully updates his/her password.
In the update password phase, when wants to update his/her password, he/she first inserts his/her smart card and password, then inserts his/her new password . Then, , , , and are computed, where , , , and . At last, previous that were saved in the smart card are replaced with , respectively. When wants to login after successfully updating his/her password, the login process fails due to denial of service. Details are explained below.
As shown in the login phase in Section 2.3, computes = , where is the new and is the new , which means = . Unfortunately, in the update password phase, , which means = = . Using this , computes , and , where = , , , respectively, and send {} to .
When get the request message {} from , will calculate and , where = and . Then compare whether equals . Since from was calculated by using and from was calculated by using , and will never be equal. When they do not equal, will reject the request message from . Therefore, Ali et al.’s scheme suffers from DoSaaS.
3. Proposed Authentication and Key-Agreement Scheme Using WSNs for Agriculture Monitoring
The proposed scheme proposed some significant improvements compared to Ali et al.’s scheme. For example, to overcome violation of traceability in Ali et al.’s scheme, instead of using static and , the proposed scheme uses dynamic and . The proposed scheme also eliminates sensor node impersonation attack, perfect forward secrecy and violation of user anonymity by keeping the shared secret key to be known only by and , while in Ali et al.’s scheme, the is known by all participants. To overcome Denial of Service as a Service in Ali et al.’s scheme, the proposed scheme proposes a different structure for password update phase, where in order to complete the password update process, the user needs to send the new updated parameters to the base station BS to be processed. Moreover, to significantly improved efficiency, the proposed scheme only uses hash function in its computation, while Ali et al. used symmetric encryption-decryption for their scheme.
The proposed scheme consists of six phases, which are system setup phase; user/agriculture professional registration phase; login phase, authentication and session key agreement phase; password update or change phase; and dynamic node addition phase. Since the system setup phase and the dynamic node addition phase of the proposed scheme are similar with Ali et al.’s scheme, they are not presented here. Therefore, only user/agriculture professional registration phase; login phase; authentication and session key agreement phase; and password update or change phase are described in detail as follows.
3.1. User/Agriculture Professional Registration Phase
In this phase, the user/agriculture professional registers to the base station . Each user has a which contains a pre-configured identity and a random number . The pre-configured data is also stored in BS’s storage. The is transferred by using physical delivery. As shown in Figure 5, the following steps are executed to complete the registration phase.
| Step 1: | The selects his/her own identity , password , and imprints biometric on the sensor device and then computes , , where is a generate function of fuzzy extractor and are secret and public key respectively. Now, computes and sends to . |
| Step 2: | When the registration request is received from , if successfully verifies that () is in ’s storage and has not been registered, then computes , and . Afterwards, computes and sends {} to . |
| Step 3: | After receiving the response from , computes , and embeds and in the memory of . |
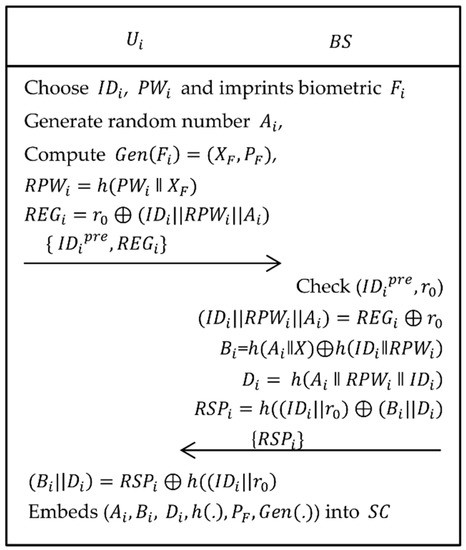
Figure 5.
User registration phase of the proposed scheme.
3.2. Login Phase
When a user/agriculture professional wants to know the environmental information such as temperature, light, humidity, soil etc., he/she has to login to access these information. As shown in Figure 6, the following steps are executed to accomplish the login phase.
| Step 1: | The inserts his/her own smartcard into card reader, inputs , and imprints his/her biometric on sensor device. Now, the card reader computes , = , = , = , = and verifies if equals . If the verification holds, the system continues to process the request. Otherwise, the session is terminated. |
| Step 2: | Now, generates a random nonce , computes and , then send to via public channel. |
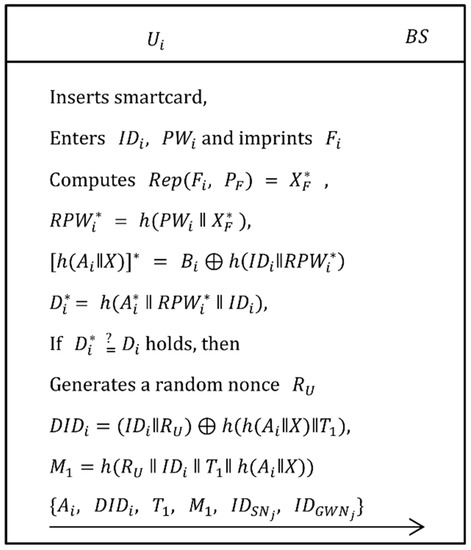
Figure 6.
Login phase of the proposed scheme.
3.3. Authentication and Session Key Agreement Phase
As shown in Figure 7, after the is successfully authenticated in the login phase, the authentication and session-key agreement phase is executed as the following steps.
| Step 1: | Upon obtaining the message from , the checks if holds. If this does not true then session expires. Otherwise, calculates and computes , then verifies if equals or not. If this holds, goes to next step. Otherwise, the session is rejected. |
| Step 2: | Now, generates a random nonce and computes a new , where = Then, computes =⊕, , and ⊕ and sends to via public channel. |
| Step 3: | After getting the request message from , the checks if holds. If this does not true then session expires. Otherwise, calculates and , then checks if holds. If the condition is true then it proceeds further. Otherwise, the session is terminated. |
| Step 4: | Now, the generates a random nonce , calculates = and , then sends to . |
| Step 5: | Upon obtaining the message from , the checks if holds. If this does not true then session expires. Otherwise, calculates , and . Then, verifies if holds. If the condition is true then it proceeds further. Otherwise, the session is terminated. |
| Step 6: | Now, the generates a random nonce , computes , and . Then, sends to . |
| Step 7: | Upon receiving the message from , firstly verifies if holds. If this is not true then the session expires. Otherwise, calculates , and , then checks if holds. If the condition is true then further is proceeded. Otherwise, the session is terminated. |
| Step 8: | The computes and . Then, sends to . |
| Step 9: | Upon receiving the message from , firstly verifies if holds. If this does not true then session expires. Otherwise, computes =⊕, =, , and verifies if holds. If the condition is true then mutual authentication and session key agreement holds. Otherwise, the session is terminated. |
| Step 10: | The computes and . Then, replaces with , , , respectively. |

Figure 7.
Authentication and key agreement phase of the proposed scheme.
3.4. Password Updates or Change Phase
As shown in Figure 8, the following steps were executed to update or change user’s password.
| Step 1: | The user inserts his/her own smartcard into card reader and enters , and imprints on sensor device. The card reader computes , = , , , = and . Then, verifies if holds. If condition is true then further is proceeded. Otherwise, the session is terminated. |
| Step 2: | The enters new password and computes , and . Then, are replaced with , respectively. |
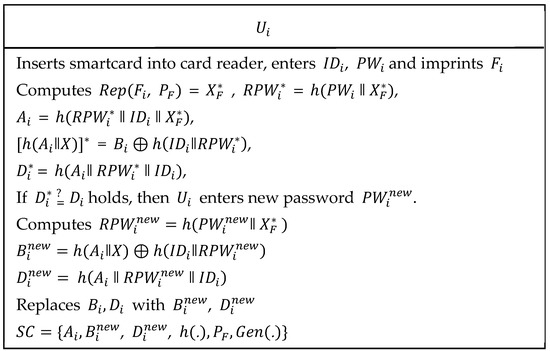
Figure 8.
Password update phase of the proposed scheme.
4. Security Analysis
4.1. Authentication Proof of the Proposed Scheme Using BAN Logic
This section validates session key agreement and mutual authentication of the proposed scheme using BAN (Burrows-Abadi-Needham) logic [31]. The BAN includes a set of rules to verify the message source, freshness, and trustworthiness of the scheme. Table 2 lists the notations and their respective abbreviations related to the BAN logic.

Table 2.
BAN (Burrows-Abadi-Needham) logic notations and respective abbreviations.
4.1.1. Basic Rules of BAN Logic
Some rules or logical postulates used in the BAN logic are given as follows:
- Rule 1. Message-meaning rule:If the entity believes that the secret is shared with and sees message is encrypted using , then believes that once said .
- Rule 2. Jurisdiction rule:If the entity believes that has jurisdiction over and believes , then believes that is true.
- Rule 3. Nonce-verification rule:If the entity believes that is fresh and the entity once said , then believes that believes .
- Rule 4. Session key rule:If the entity believes that is fresh and believes , then believes the secret that is shared between both entities and .
- Rule 5. Freshness-conjuncatenation rule:If the entity believes that is fresh, then believes the freshness of .
4.1.2. Goals
The proposed scheme needs to satisfy the following goals to ensure its security under BAN logic, using the above assumptions and postulates.
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
- Goal 5:
- Goal 6:
- Goal 7:
- Goal 8:
- Goal 9:
- Goal 10:
4.1.3. Idealized Form
Initially, the message of login, authentication, and key agreement scheme in the proposed scheme can be transformed into idealized form in the following manner.
- Message 1., , , , , :
- Message 2., , , , , :
- Message 3. ( , , , , , , :
- Message 4. (, , , , :
- Message 5. ( , , , :
4.1.4. Assumptions
The following initial assumptions have been established to prove the security of the proposed scheme using BAN logic.
- A1: | #(, , , )
- A2: | #(, )
- A3: | #(, , , )
- A4: | #(, , , )
- A5: |
- A6: |
- A7: |
- A8: |
- A9: |
- A10: |
- A11: |
- A12: |
- A13: |
- A14: |
4.1.5. Verification
Verification shows the correctness of the proposed scheme confirmed by analyzing the idealized form using the above assumptions and the rules of the BAN logic.
By using Message 1:
V1: ⨞ {, , , , , : }
From A5, V1 and Rule 1:
V2: | |~
From A2, V2 and Rule 3:
V3: | |
Then, from A6, V3 and Rule 2:
V4: |
According to A2, V3 and Rule 4:
| V5: | | Goal1 |
Further, using A2, V5 and Rule 3:
| V6: | | | Goal2 |
By using Message 2:
V6: {, , , , , : }
From A7, V7 and Rule 1:
V8: | |~
From A3, V8 and Rule 3:
V9: | |
Then, from A8, V9 and Rule 2:
V10: |
According to A3, V9 and Rule 4:
| V11: | | Goal3 |
Further, using A3, V11 and Rule 3:
| V12: | | | Goal4 |
By using Message 3:
V13: ⨞ {, , , , , , : }
From A9, V13 and Rule 1:
V14: | |~
From A4, V14 and Rule 3:
V15: | |
Then, from A10, V15 and Rule 2:
V16: |
According to A4, V15 and Rule 4:
| V17: | | Goal5 |
Further, using A4, V17 and Rule 3:
| V18: | | | Goal6 |
By using Message 4:
V19: ⨞ {, , , , : }
From A11, V19 and Rule 1:
V20: | |~
From A3, V20 and Rule 3:
V21: | |
Then, from A12, V21 and Rule 2:
V22: |
According to A3, V21 and Rule 4:
| V23: | | Goal7 |
Further, using A4, V17 and Rule 3:
| V24: | | | Goal8 |
By using Message 5:
V25: ⨞ {, , , : }
From A13, V25 and Rule 1:
V26: | |~
From A1 and Rule 5:
V27: | #()
Then, from V26, V27 and Rule 3:
V28: | |
Moreover, from A14, V28 and Rule 2:
V29: |
According to V27, V28 and Rule 4:
| V30: | | Goal9 |
Then, using V27, V30 and Rule 3:
| V31: | | | Goal10 |
4.2. Informal Security Analysis
This section presents informal security analysis of the proposed scheme. Table 2 summarizes security analysis comparisons between Ali et al.’s scheme [23] and the proposed scheme.
4.2.1. User Anonymity
When base station gets a request message from user , base station checks whether the request message comes from a legitimate user by calculating ), where is ’s secret key that is known only by . checks whether equals . If it holds, confirms that the request message is coming from a legitimate .
Assume an adversary tries to get the real identity of a legitimate user from an existing message that can be obtained from public channel. In order to successfully get the real , the adversary needs to calculate ). However, is only known by the legitimate and is also protected by the hash operation that makes is computationally infeasible to calculate. Without knowledge of , the adversary cannot derive the real . Therefore, the proposed scheme provides user anonymity.
4.2.2. User Traceability
In the proposed scheme, the real identity of a user is protected by using dynamic pseudonym identity , where ). is random and is timestamp that newly generated for each transaction, means is dynamic for every transaction. Moreover, different values of for each transaction prevents adversaries to identify a transaction belonging to whom or related with any specific user. Therefore, the proposed scheme provides protection to user traceability.
4.2.3. Three-Factor Security
To provide protection in the login phase, the proposed scheme uses three-factor security which means only a user with the correct password, correct biometric characteristics, and correct smart card is allowed to login to the remote server [32].
Assume an adversary has any two factors of security which are password and smartcard, or smartcard and biometric, or password and smartcard. When he/she tries to login into the system, the proposed scheme will check whether equals with , where = and = . Based on this checking, the system always completely checks three factor security first before allowed any request to successfully login into the system. This process means an adversary who has only two factors of security does not have a chance to enter into the system. Therefore, the proposed scheme provides three-factor security.
4.2.4. Session Key Security
In an authentication and key agreement phase, the session key must be made and known only by legal participants. In the proposed scheme, is computed by using random numbers from each legal participant that freshly generated in each session. Furthermore, also depends on and , where and it was protected by that is only known by and . It is also computationally infeasible to calculate the session key due to the characteristics of the hash operation. Therefore, the proposed scheme withstands session key computation attack.
4.2.5. Perfect Forward Secrecy Attack
The proposed scheme ensures the secrecy of previous session keys even if the master secret key of the server or shared secret key between legal participants are compromised.
In the proposed scheme, the session key is not related to the master secret key that belongs to the base station . Also, the session key is not related with any shared secret key that exists between legal participants, such as the shared key between and gateway node or the shared key between and sensor node . Instead, the session key is built from each random number that is freshly generated by every legal participant from each session. Therefore, the proposed scheme provides perfect forward secrecy.
4.2.6. Sensor Node Impersonation Attack
Assume an adversary tries to impersonate a sensor node by sending a request message to a gateway node . Upon receiving the request message, to verify if the request message comes from a legitimate sensor node or not, computes and checks if equals or not.
In the proposed scheme, in order to compute verifiable , both and need to obtain , where is a random nonce belongs to the base station . As shown in authentication and session key agreement phase, in order to obtain , both and need to use their own shared secret key with the , where uses its shared secret key and uses its shared secret key . Without shared secret key, an adversary will not be able to obtain . Without the right , will never be successfully verified by . By verifying the , will immediately detect that the request message is coming from legal or not. Therefore, the proposed scheme withstands sensor node impersonation attack.
4.2.7. Gateway Node Impersonation Attack
Gateway node impersonation attack occurs when an adversary acts as a legitimate gateway node by sending a request message to user or sensor node and that request message is successfully authenticated as a legitimate by or .
Assume an adversary tries to impersonate by sending a request message to or to , where , , and . To compute , , and , the adversary needs to obtain , and using shared key , where . However, without the knowledge of , it is computationally infeasible to calculate these parameters due to the characteristics of the hash operation. Without the right parameters, and will immediately recognize if the request is not coming from a legitimate . Therefore, the proposed scheme withstands a gateway node impersonation attack.
4.2.8. User/Agriculture Impersonation Attack
A user impersonation attacks occur when an adversary acts as a legitimate user and is successfully authenticated by the base station .
Assume an adversary tries to impersonate a legitimate user by sending a request message to , where , , and . However, it is impossible for an adversary to calculate due to biometrics, unknown user identity and user password .
Upon receiving the request message from , will immediately recognize that the request message is coming from a legitimate user or not by checking whether equals or not. Therefore, the proposed scheme withstands user/agriculture impersonation attack.
4.2.9. Offline Password Guessing Attack
An off-line password guessing attack occurs when a smart card is lost or stolen and the adversary tries to guess the password to log into the system. Let us assume an adversary obtains information within the smart card by using channel side attacks and successfully obtains , where , , and . To guess the password through the parameter that are stored inside the smart card, the adversary needs to invert the value of or . However, inverting the values of or is computationally infeasible due to the characteristics of the hash operation. Neither . or are ever directly revealed or exposed and an adversary for sure cannot guess or change the password. Therefore, the proposed scheme withstands an offline password guessing attack.
4.2.10. Replay Attack
An off-line password guessing attack occurs when a smart card is lost or stolen and the adversary replay attack happens when an adversary tries to retransmit previous request message as a new transaction request and it has successfully been accepted as a new legitimate request by other legal participants.
Assume an adversary tries to replay existing messages as a new transaction request. However, any message contains a timestamp , , , , or . Other legitimate participants will immediately identify the replay attack when they check the freshness of , , , , and . Therefore, the proposed scheme withstands replay attack.
4.2.11. Insider Attack
An insider attack happens when a malicious legal participant successfully captures key values of others, such as a shared key, and then uses that key to launch some security violations or attacks. The proposed scheme ensures that the key shared between participants is known only by the right participant and will never be leaked to other irrelevant participants.
Assume a malicious legal participant tries to obtain a shared secret key that belongs to another legal participant. In the proposed scheme, there are three shared secret key which are , and . All of them are generated by base station and contains secret key . Since the secret key of is only known by and never revealed to others, and since the shared key between participants is never revealed to other irrelevant participants too, the proposed scheme is safe from shared secret key leakage. Therefore, the proposed scheme withstands insider attack.
5. Performance and Functionality Comparisons
This section analyzes and compares Ali et al.’s scheme with the proposed scheme. Security functionality comparisons and performance comparisons in login, authentication, and key agreement phase are presented as follows.
5.1. Security Functionality Comparisons
Table 3 shows comparisons between the proposed scheme and Ali et al.’s scheme in terms of functionality in security. It shows that the proposed scheme enables provision of more security functionality where there are lacks in Ali et al.’s scheme. Detailed explanations about how Ali et al.’s scheme suffers from those attacks was already described in Section 2.3.

Table 3.
Functionality comparisons.
5.2. Performance Comparisons
As WSNs has limited power capacity, the computation cost for login, authentication, and key-agreement scheme must be made as minimal as possible. Table 4 shows the comparison of login, authentication, and key agreement phases between the proposed scheme and Ali et al.’s scheme in terms of performance. Table 5 shows hardware/software specifications and used algorithms in our simulation environment. The proposed scheme involves a user , a base station , a gateway node , and a sensor node . denotes the execution time of hash operation and donates the execution time of symmetric encryption/decryption.

Table 4.
Performance comparisons.

Table 5.
Simulation environment.
Ali et al.’s scheme [23] requires 19 hash function and nine symmetric en/decryption operations. Although the proposed scheme requires more hash function operations, it does not require nine symmetric en/decryption operations. Therefore, the proposed scheme provides better efficiency compared with the previous scheme.
6. Conclusions
This paper reviewed Ali et al.’s scheme and demonstrated that it cannot provide user anonymity, user traceability, session key security, and is insecure against insider attacks, perfect forward secrecy attacks, and sensor node impersonation attacks. Moreover, after a user successfully updates his/her password, Ali et al.’s scheme will immediately suffer from Denial of Service as a Service (DoSaaS) in its authentication and key agreement scheme. The proposed scheme eliminated those security weaknesses by proposed four new phases of six existing phases. To promote efficiency, the proposed scheme eliminates symmetric encryption–decryption computation that was used in the previous scheme and only utilizes hash operation in its computation. The proposed scheme not only eliminates weaknesses in Ali et al.’s scheme, but is also 80 times more efficient compares with Ali et al.’s scheme. The efficiency, security and functionalities showed in the proposed scheme overcomes Ali et al.’s scheme. Therefore, the proposed scheme is more suitable for agriculture monitoring using WSNs.
Author Contributions
Conceptualization, M.C.; formal analysis, M.C.; investigation, M.C. and T.-F.L.; methodology, T.-F.L.; project administration, T.-F.L.; resources, J.-I.P.; validation, J.-I.P.; writing – original draft, M.C.; writing – review and editing, T.-F.L.
Funding
This research was funded by Ministry of Science and Technology under the grants MOST 106-2221-E-320-001 and Tzu Chi University under the grants TCRPP107013.
Acknowledgments
Ted Knoy is appreciated for his editorial assistance.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Arjun, K.M. Indian agriculture—Status, importance and role in Indian economy. Int. J. Res. Agric. Food Sci. 2013, 4, 343–346. [Google Scholar]
- Omorogiuwa, O.; Zivkovic, J.; Ademoh, F. The role of agriculture in the economic development of Nigeria. Eur. Sci. J. 2014, 10, 4. [Google Scholar]
- Raza, S.A.; Ali, Y.; Mehboob, F. Role of agriculture in economic growth of Pakistan. Int. Res. J. Financ. Econ. 2012, 83. [Google Scholar]
- Sustainable Development Solutions Network, A Global Initiative for the United Nations. Solutions for Sustainable Agriculture and Food Systems. Available online: http://unsdsn.org/resources/publications/solutions-for-sustainable-agriculture-and-food-systems/ (accessed on 11 December 2018).
- Luis, R.G.; Lunadei, L.; Barreiro, P.; Robla, J.I. A review of wireless sensor technologies and applications in agriculture and food industry: State of the art and current trends. Sensors 2009, 9, 4728–4750. [Google Scholar] [CrossRef]
- Jiber, Y.; Harroud, H.; Karmouch, A. Precision agriculture monitoring framework based on WSN. In Proceedings of the 7th International Wireless Communications and Mobile Computing Conference, Istanbul, Turkey, 4–8 July 2011; pp. 2015–2020. [Google Scholar] [CrossRef]
- Anurag, D.; Roy, S.; Bandyopadhyay, S. Agro-sense: Precision agriculture using sensor-based wireless mesh networks. In Proceedings of the First ITU-T Kaleidoscope Academic Conference Innovation in NGN: Future Network and Services, Geneva, Switzerland, 12–13 May 2008; pp. 383–388. [Google Scholar] [CrossRef]
- Panchard, J.; Papadimitratos, P.; Hubaux, J.P.; Rao, P.R.S.; Sheshshayee, M.S.; Kumar, S. Wireless Sensor Networking for Rain-fed Farming Decision Support. In Proceedings of the ACM SIGCOMM Workshop on Networked Systems for Developing Regions, Seattle, WA, USA, 17–22 August 2008; pp. 31–36. [Google Scholar] [CrossRef]
- Das, A.K.; Sharma, P.; Chatterje, S.; Sing, J.K. A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J. Netw. Comput. Appl. 2012, 35, 1646–1656. [Google Scholar] [CrossRef]
- Xue, K.P.; Ma, C.S.; Hong, P.L.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Shi, W.B.; Gong, P. A new user authentication protocol for wireless sensor networks using elliptic curves cryptography. Int. J. Distrib. Sens. Netw. 2013, 9, 4. [Google Scholar] [CrossRef]
- Li, C.T.; Weng, C.Y.; Lee, C.C. An advanced temporal credential-based security scheme with mutual authentication and key agreement scheme for wireless sensor networks. Sensors 2013, 13, 9589–9603. [Google Scholar] [CrossRef]
- Rahman, M.; Sampalli, S. An Efficient Pairwise and Group Key Management Protocol for Wireless Sensor Network. Wirel. Pers. Commun. 2015, 84, 2035–2053. [Google Scholar] [CrossRef]
- Lee, T.F. Efficient and secure temporal credential-based authenticated key agreement scheme using extended chaotic maps for wireless sensor networks. Sensors 2015, 15, 14960–14980. [Google Scholar] [CrossRef]
- He, D.P.; Kumar, N.; Chilamkurti, N. A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. 2015, 321, 263–277. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.K.H.; Biswas, G.P.; Khan, M.K.; Kumar, N. A robust and anonymous patient monitoring system using wireless sensor networks. Future Gener. Comput. Syst. 2018, 80, 483–495. [Google Scholar] [CrossRef]
- Kumari, S.; Li, X.; Wu, F.; Das, A.K.; Arshad, H.; Khan, M.K. A user friendly mutual authentication and key agreement scheme for wireless sensor networks using chaotic maps. Future Gener. Comput. Syst. 2016, 63, 56–75. [Google Scholar] [CrossRef]
- Zebboudj, S.; Cherifi, F.; Mohammedi, M.; Omar, M. Secure and efficient ECG-based authentication scheme for medical body area sensor networks. Smart Health 2017, 3–4, 75–84. [Google Scholar] [CrossRef]
- Li, X.; Ibrahim, M.H.; Kumari, S.; Sangaiah, A.K.; Gupta, V.; Choo, K.K.R. Anonymous mutual authentication and key agreement scheme for wearable sensors in wireless body area networks. Comput. Netw. 2017, 2, 429–443. [Google Scholar] [CrossRef]
- Liu, J.W.; Li, Q.; Yan, R.; Sun, S. Efficient authenticated key exchange protocols for wireless body area networks. Eur. J. Wirel. Commun. Netw. 2015, 188. [Google Scholar] [CrossRef]
- Gupta, R.; Sultania, K.; Singh, P.; Gupta, A. Security for Wireless Sensor Networks in Military Operations. In Proceedings of the Fourth International Conference on Computing, Communications and Networking Technologies, Tiruchengode, India, 4–6 July 2013. [Google Scholar] [CrossRef]
- Costa, D.G.; Figueredo, S.; Oliveira, G. Cryptography in Wireless Multimedia Sensor Networks: A Survey and Research Directions. Cryptography 2017, 1, 4. [Google Scholar] [CrossRef]
- Ali, R.; Pal, A.K.; Kumari, S.; Karuppiah, M.; Conti, M. A secure user authentication and key-agreement scheme using wireless sensor networks for agriculture monitoring. Future Gener. Comput. Syst. 2018, 84, 200–215. [Google Scholar] [CrossRef]
- Mesit, J.; Brust, M.R. Secured node-to-node key agreement for wireless sensor networks. In Proceedings of the 2015 International Conference on Information Networking (ICOIN), Siem Reap, Cambodia, 12–14 January 2015; pp. 37–39. [Google Scholar]
- Pecori, R.; Veltri, L. A Key Agreement Protocol for P2P VoIP Applications. In Proceedings of the International Conference on Software Telecommunications and Computer Networks, Hvar, Croatia, 24–26 September 2009; pp. 276–280. [Google Scholar]
- Pecori, R. A PKI-free Key Agreement Protocol for P2P VoIP Applications. In Proceedings of the ICC 2012 1st International Workshop on Security and Forensics in Communication Systems, Ottawa, ON, Canada, 10–12 June 2012; pp. 6748–6752. [Google Scholar] [CrossRef]
- Lee, T.F. An efficient dynamic id-based user authentication scheme using smart cards without verifier tables. Appl. Math. Inf. Sci. 2015, 9, 485–490. [Google Scholar] [CrossRef]
- Xue, K.P.; Hong, P.L.; Ma, C.S. A lightweight dynamic pseudonym identity based authentication and key agreement protocol without verification tables for multi-server architecture. J. Comput. Syst. Sci. 2014, 80, 195–206. [Google Scholar] [CrossRef]
- Lee, C.C.; Li, C.T.; Chiu, S.T.; Lai, Y.M. A new three-party-authenticated key agreement scheme based on chaotic maps without password table. Nonlinear Dyn. 2015, 79, 2485–2495. [Google Scholar] [CrossRef]
- Jokhio, S.H.; Jokhio, I.A.; Kemp, A.H. Node capture attack detection and defence in wireless sensor networks. IET Wirel. Sens. Syst. 2012, 2, 161–169. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 1836. [Google Scholar] [CrossRef]
- Fan, C.I.; Lin, Y.H. Provably secure remote truly three-factor authentication scheme with privacy protection on biometrics. IEEE Trans. Inf. Forensics Secur. 2009, 4, 933–945. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).