Fast and Reliable Burst Data Transmission for Backscatter Communications
Abstract
1. Introduction
- We propose a method for burst data transmission by fragmenting large data packets into blocks. Then, we dynamically adjust the frame length of every block through an online adjustment strategy at runtime by the feedback of the reader.
- We introduce a burst transmission mechanism. The core idea is to let a tag occupy all time slots for burst transmission when there are critical and emergency data to be transmitted, which reduces the idle time slot.
- We utilize erasure codes to reduce acknowledgement frame waiting delay and to avoid retransmission overhead, which improves system robustness and reliability.
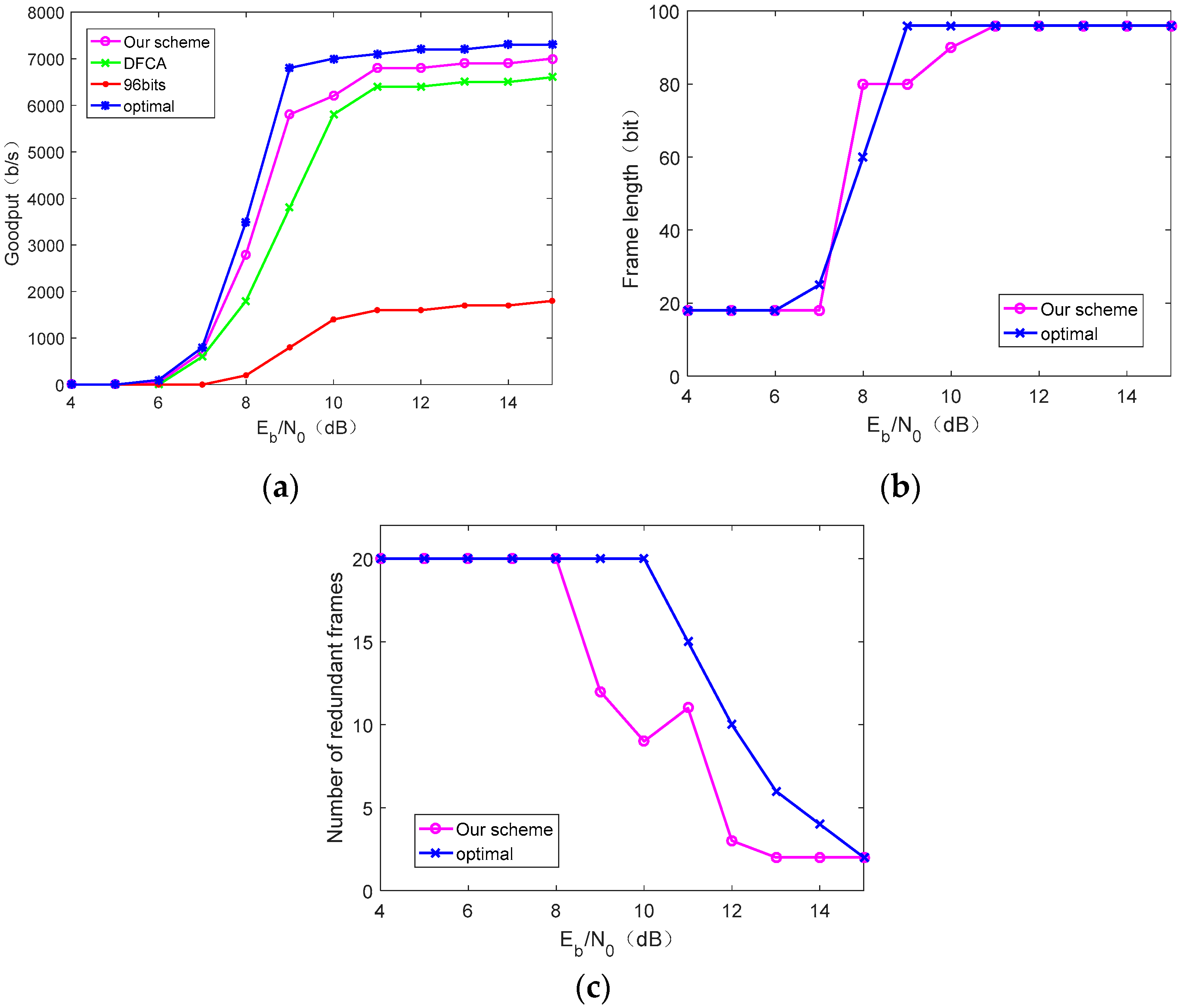
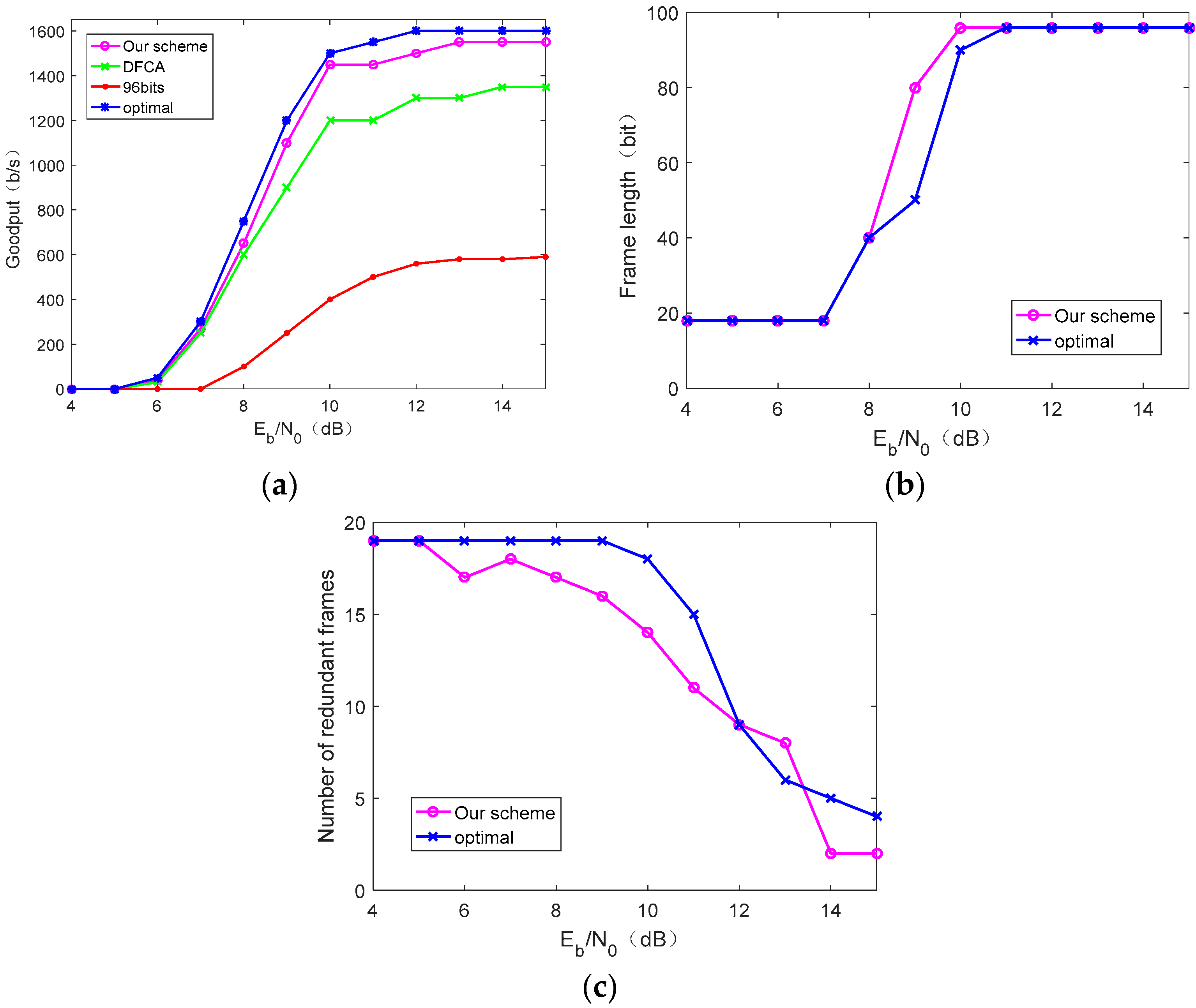
- Under specific energy-harvesting and channel conditions, our proposed scheme is much better than the EPC C1G2 protocol fixed frame length approach and DFCA scheme, and the performance can converge to near optimal. When there are abundant critical and emergency data to be transmitted, our scheme can achieve fast and reliable bulk burst data transmission.
2. Related Work
3. Challenge and Motivation
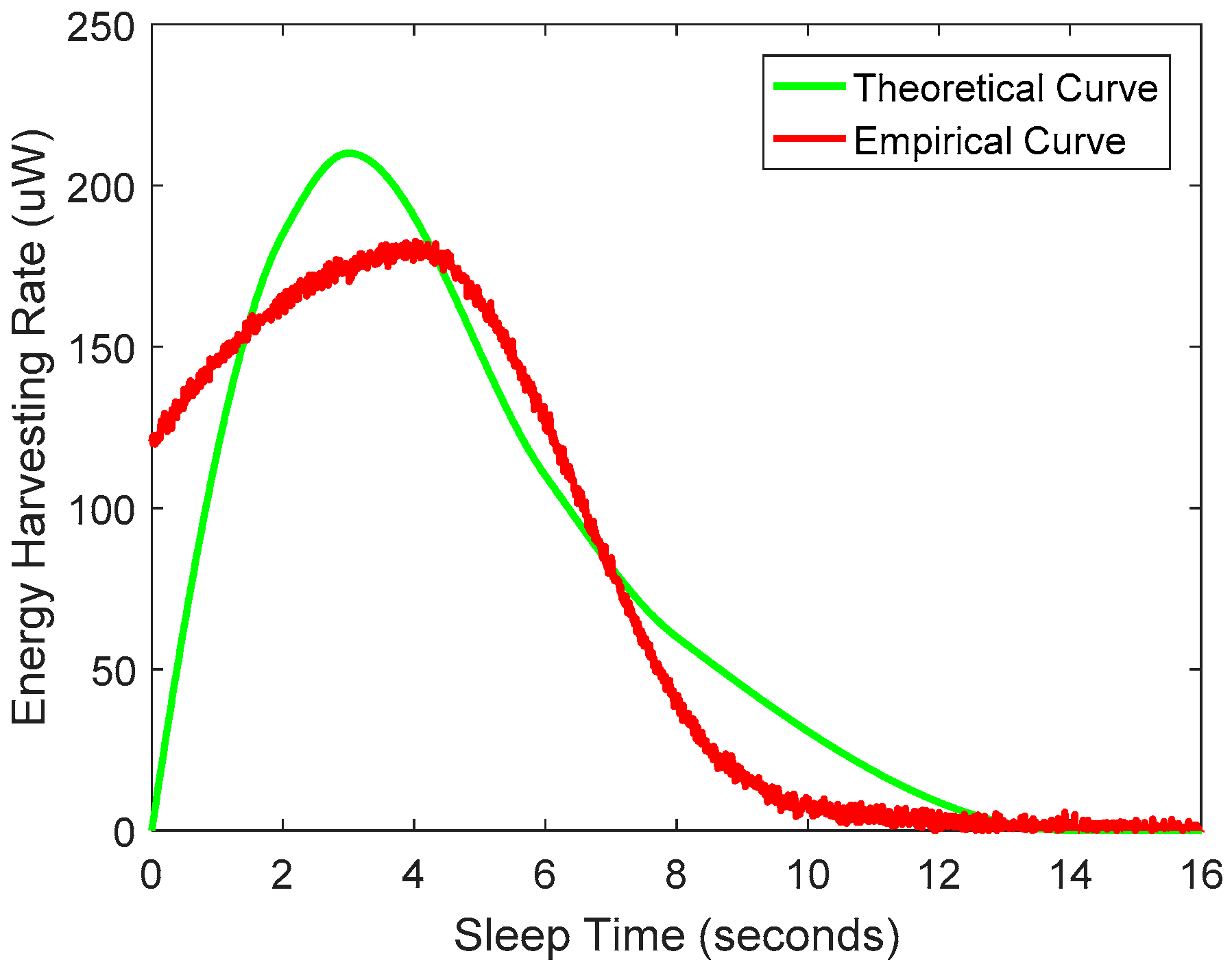
3.1. Challenge 1: Variable Energy per Transmission
3.2. Challenge 2: Variable Harvesting Rate
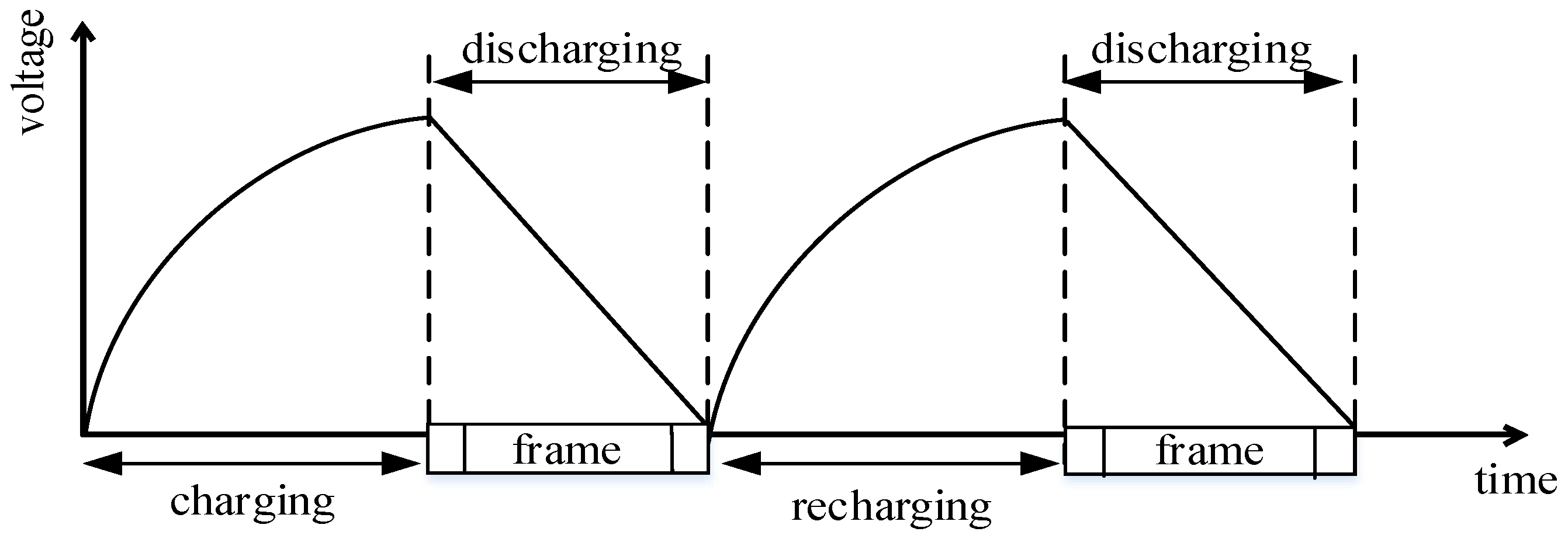
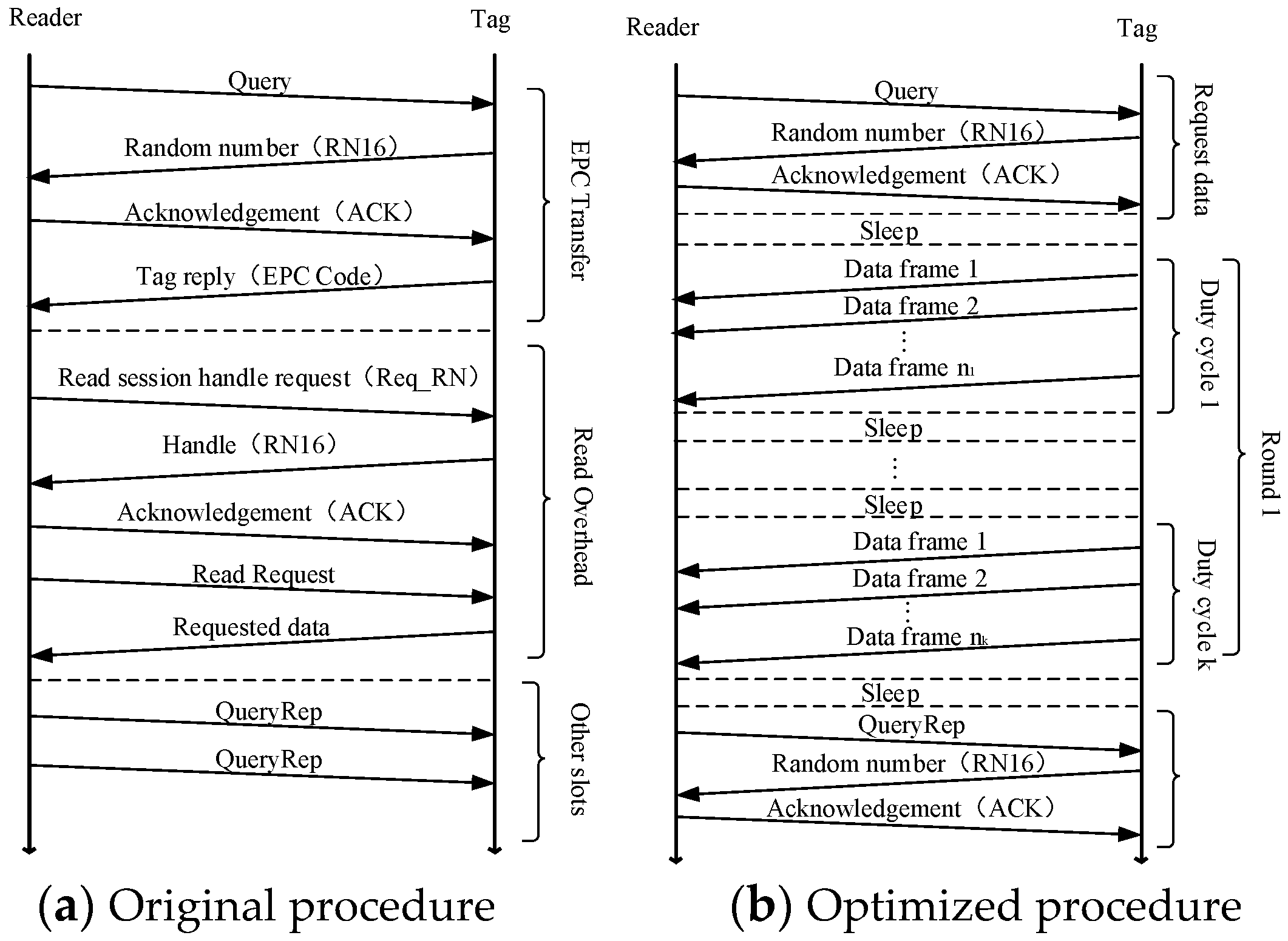
4. CRFID Operating Procedure Optimization
4.1. CRFID Operating Procedure
4.2. Goodput Analysis and Optimization
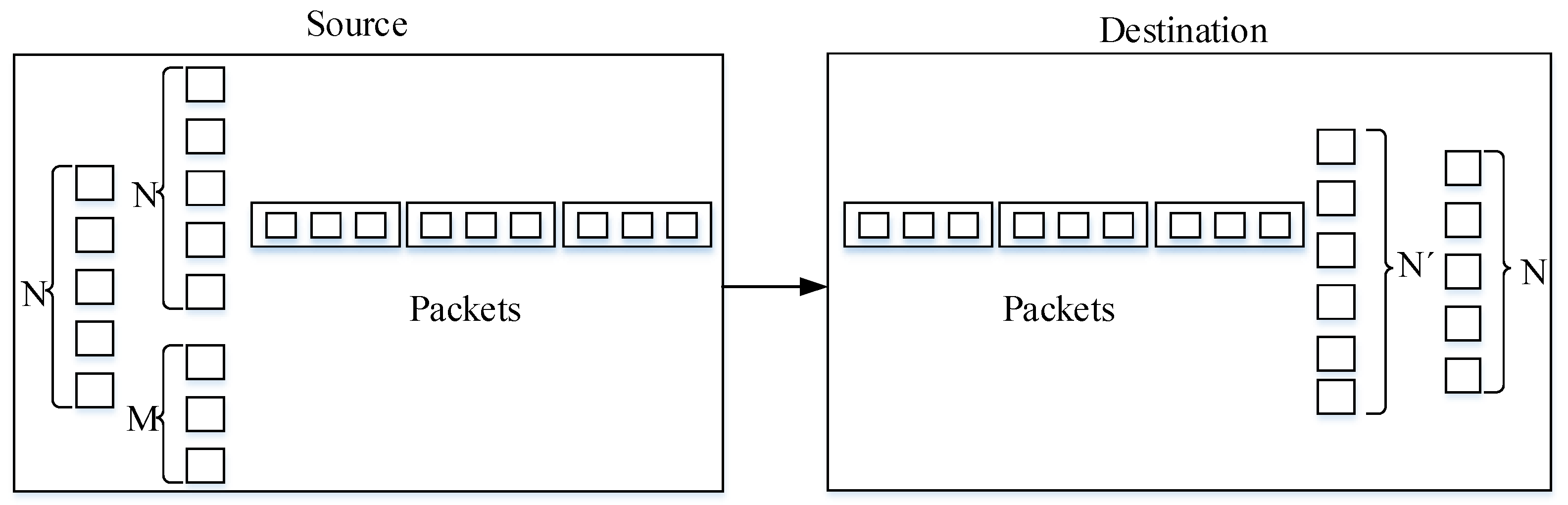
5. Burst Data Transmission Scheme
5.1. Design
| Algorithm 1 The computational radio frequency identification (CRFID) operation procedure. |
| 1: while the buffer id not empty do 2: if receive Query or QueryRep command then 3: return RN16 4: end 5: if receive the ACK containing the same RN16 then 6: extract data frames of length and encode into ( and are carried in the ACK) 7: end 8: repeat 9: track the capacitance voltage and obtain and , and sleep for a period of 10: compute the optimal number of transmission frames via Equation (6); then, transmit it to the reader 11: until all frames have been transmitted 12: end |
| Algorithm 2 The reader operation procedure. |
| 1: Initialize = 16 bits, = , = 0, = 0, = 0 2: send the Query or QueryRep command 3: if receive the RN16 from CRFID then 4: return an ACK with the same RN16 and and 5: end 6: if receive the frame from CRFID 7: if the frame is correct then 8: ; 9: else 10: end 11: if or then 12: compute , where is the transmission time of the current round 13: if and then 14: 15: else if and then 16: 17: end 18: end 19: compute the number of redundant frames via Equation (7) for the next round 20: end |
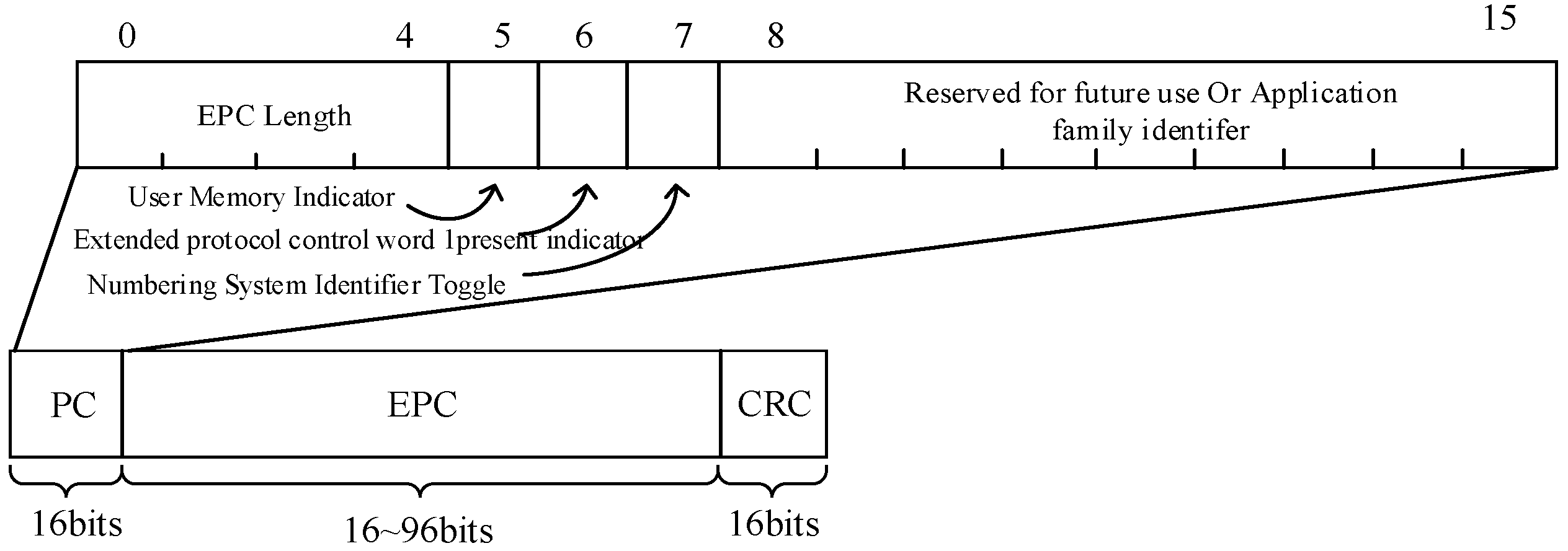
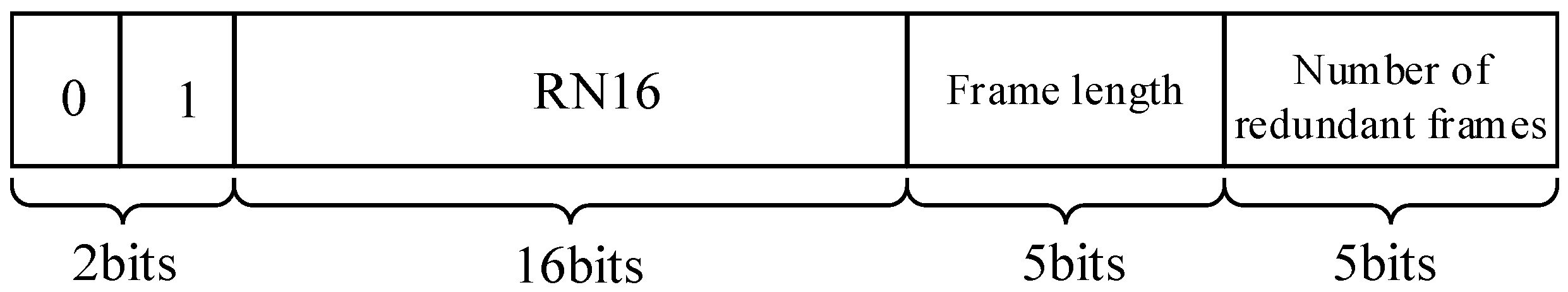
5.2. Frame Format
6. Performance Evaluation
6.1. Platforms
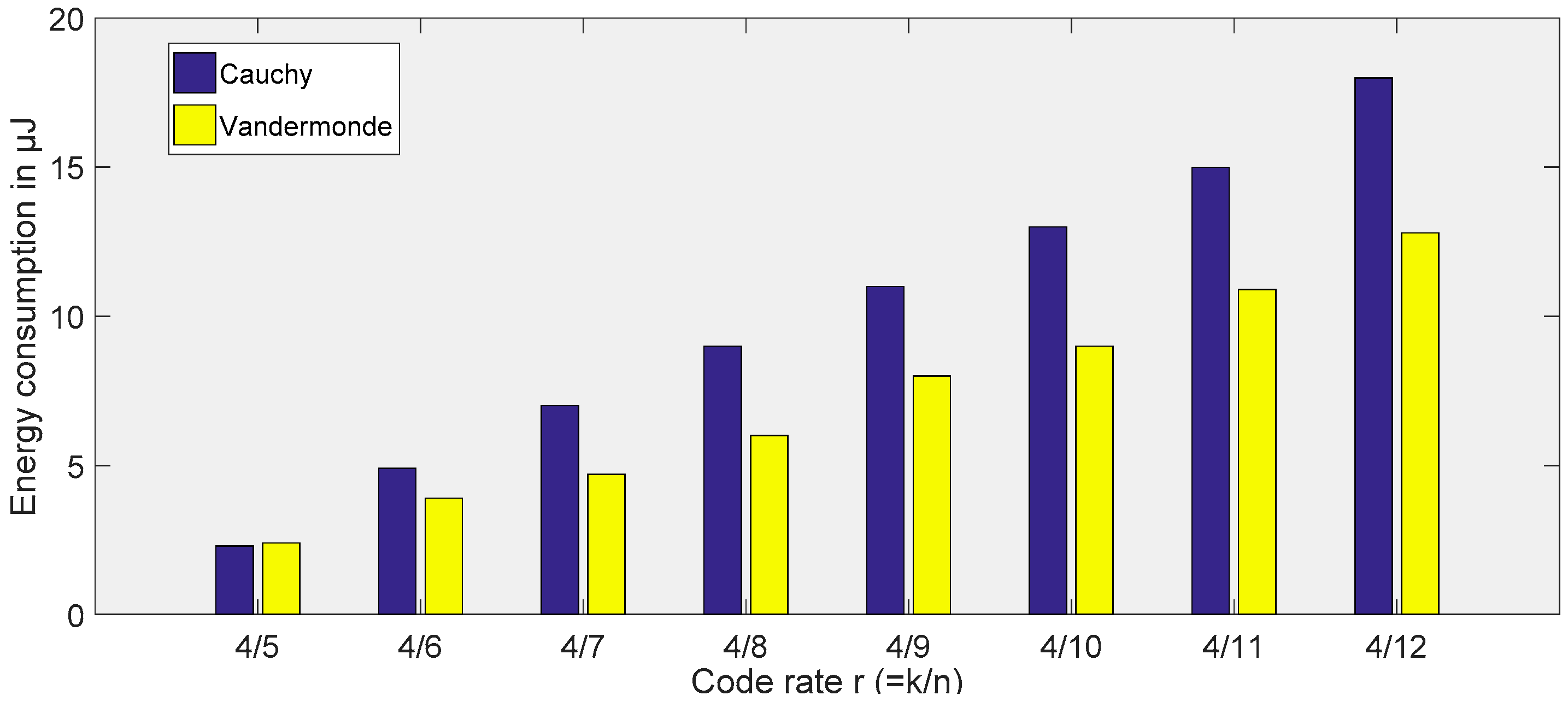
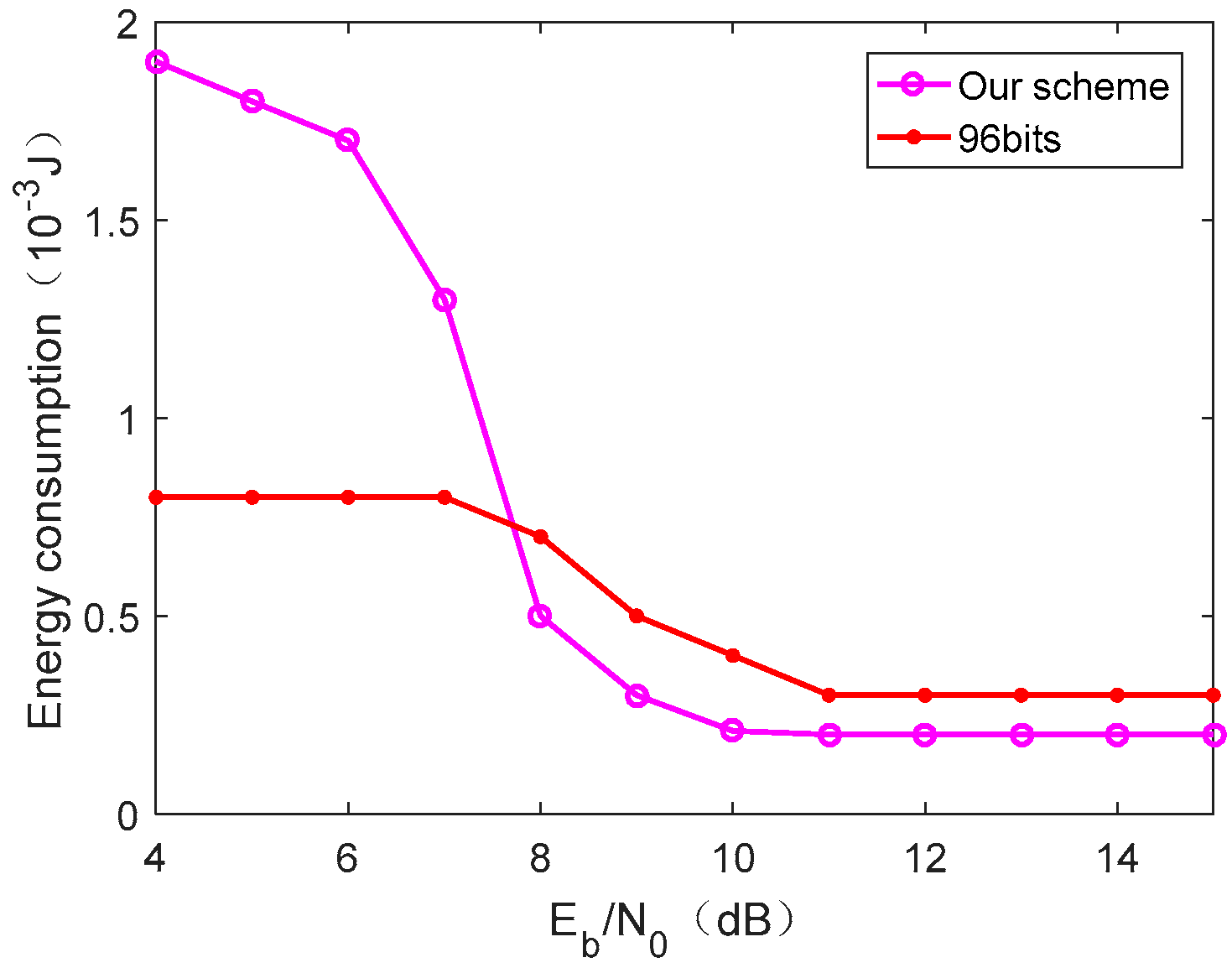
6.2. Trimming Overheads
6.3. Evaluation
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Margolies, R.; Gorlatova, M.; Sarik, J.; Stanje, G.; Zhu, J.; Miller, P.; Szczodrak, M.; Vigraham, B.; Carloni, L.; Kinget, P.; et al. Energy-harvesting active networked tags (EnHANTs): Prototyping and experimentation. ACM Trans. Sens. Netw. 2015, 11, 62. [Google Scholar] [CrossRef]
- Kim, S.; Vyas, R.; Bito, J.; Niotaki, K.; Collado, A.; Georgiadis, A.; Tentzeris, M.M. Ambient RF energy-harvesting technologies for self-sustainable standalone wireless sensor platforms. Proc. IEEE 2014, 102, 1649–1666. [Google Scholar] [CrossRef]
- Buettner, M.; Greenstein, B.; Sample, A.; Smith, J.R.; Wetherall, D.; Sample, A.P. Revisiting smart dust with RFID sensor networks. In Proceedings of the 7th ACM Workshop on Hot Topics in Networks (HotNets-VII), Calgary, AB, Canada, 6–7 October 2008. [Google Scholar]
- Fu, L.; Cheng, P.; Gu, Y.; Chen, J.; He, T. Optimal charging in wireless rechargeable sensor networks. IEEE Trans. Veh. Technol. 2015, 65, 278–291. [Google Scholar] [CrossRef]
- He, L.; Kong, L.; Lin, S.; Ying, S.; Gu, Y.; He, T.; Liu, C. Reconfiguration-assisted charging in large-scale Lithium-ion battery systems. In Proceedings of the ICCPS’14: ACM/IEEE 5th International Conference on Cyber-Physical Systems (with CPS Week 2014), Berlin, Germany, 14–17 April 2014; pp. 60–71. [Google Scholar]
- Wu, J.; Meng, Z.; Yang, T.; Shi, G.; Johansson, K.H. Sampled-data consensus over random networks. IEEE Trans. Signal Process. 2016, 64, 4479–4492. [Google Scholar] [CrossRef]
- Sample, A.P.; Yeager, D.J.; Powledge, P.S.; Mamishev, A.V.; Smith, J.R. Design of an RFID-based battery-free programmable sensing platform. IEEE Trans. Instrum. Meas. 2008, 57, 2608–2615. [Google Scholar] [CrossRef]
- Zhang, H.; Gummeson, J.; Ransford, B.; Fu, K. Moo: A Batteryless Computational RFID and Sensing Platform; Computer Science Technical Report UM-CS-2011-020; University of Massachusetts Amherst: Amherst, MA, USA, 2011. [Google Scholar]
- Xie, L.; Wang, C.; Bu, Y.; Sun, J.; Cai, Q.; Wu, J.; Lu, S. TaggedAR: An RFID-Based Approach for Recognition of Multiple Tagged Objects in Augmented Reality Systems. IEEE Trans. Mob. Comput. 2018, 18, 1188–1202. [Google Scholar] [CrossRef]
- Xia, C.; Jin, X.; Kong, L.; Zeng, P. Scheduling for emergency tasks in industrial wireless sensor networks. Sensors 2017, 17, 1674. [Google Scholar] [CrossRef]
- Niu, C.; Zhang, H.; Lin, T. An Enhanced Q Algorithm Based on EPC-C1G2 RFID Protocol. In Proceedings of the 2016 International Conference on Modeling, Simulation and Optimization Technologies and Applications (MSOTA2016), Xiamen, China, 18–19 December 2016. [Google Scholar]
- Peng, L.; Zeng, Y.; Liu, H.; Tan, H.Z. An improved Q-algorithm based on EPC Class 1 Generation 2 protocol. In Proceedings of the 2nd International Conference on Intelligent Information Processing, Bangkok, Thailand, 17–18 July 2017; p. 5. [Google Scholar]
- Lee, T.J.; Lee, J.Y.; Lee, M.G.; Ahn, J.H. Method, Apparatus and System for Collecting Tags Using Bit Map in RFID System. U.S. Patent 9,785,803, 10 October 2017. [Google Scholar]
- Lu, Y.; Xi, W. Research on Multi-Tag Transmission Control Algorithm Based on Channel Division Dynamic Frame Slot. J. Comput. 2018, 29, 261–267. [Google Scholar]
- Jara, A.J.; Lopez, P.; Fernandez, D.; Castillo, J.F.; Zamora, M.A.; Skarmeta, A.F. Mobile digcovery: Discovering and interacting with the world through the internet of things. Pers. Ubiquitous Comput. 2014, 18, 323–338. [Google Scholar] [CrossRef]
- Farris, I.; Pizzi, S.; Merenda, M.; Molinaro, A.; Carotenuto, R.; Iera, A. 6lo-RFID: A framework for full integration of smart UHF RFID tags into the internet of things. IEEE Netw. 2017, 31, 66–73. [Google Scholar] [CrossRef]
- Jara, A.J.; Moreno-Sanchez, P.; Skarmeta, A.F.; Varakliotis, S.; Kirstein, P. IPv6 addressing proxy: Mapping native addressing from legacy technologies and devices to the Internet of Things (IPv6). Sensors 2013, 13, 6687–6712. [Google Scholar] [CrossRef] [PubMed]
- Catarinucci, L.; De Donno, D.; Mainetti, L.; Palano, L.; Patrono, L.; Stef, M.L. An IoT-aware architecture for smart healthcare systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Xu, C.; Yang, L.; Zhang, P. Practical backscatter communication systems for battery-free Internet of Things: A tutorial and survey of recent research. IEEE Signal Process. Mag. 2018, 35, 16–27. [Google Scholar] [CrossRef]
- Bharadia, D.; Joshi, K.R.; Kotaru, M.; Katti, S. Backfi: High throughput wifi backscatter. ACM Sigcomm Comput. Commun. Rev. 2015, 45, 283–296. [Google Scholar] [CrossRef]
- Zhang, P.; Gummeson, J.; Ganesan, D. Blink: A high throughput link layer for backscatter communication. In Proceedings of the 10th International Conference on Mobile Systems, Applications, and Services, Low Wood Bay, UK, 25–29 June 2012; pp. 99–112. [Google Scholar]
- Gong, W.; Chen, S.; Liu, J. Towards higher throughput rate adaptation for backscatter networks. In Proceedings of the 2017 IEEE 25th International Conference on Network Protocols (ICNP), Toronto, ON, Canada, 10–13 October 2017. [Google Scholar]
- Gong, W.; Liu, H.; Liu, J.; Fan, X.; Liu, K.; Ma, Q.; Ji, X. Channel-aware rate adaptation for backscatter networks. IEEE ACM Trans. Netw. 2018, 26, 751–764. [Google Scholar] [CrossRef]
- Zhang, P.; Ganesan, D. Enabling bit-by-bit backscatter communication in severe energy harvesting environments. In Proceedings of the 11th USENIX Symposium on Networked Systems Design and Implementation (NSDI 14), Seattle, WA, USA, 2–4 April 2014; pp. 345–357. [Google Scholar]
- Ransford, B.; Sorber, J.; Fu, K. Mementos: System support for long-running computation on RFID-scale devices. ACM SIGARCH Comput. Archit. News 2011, 39, 159–170. [Google Scholar] [CrossRef]
- Buettner, M.; Greenstein, B.; Wetherall, D. Dewdrop: An energy-aware runtime for computational RFID. In Proceedings of the USENIX NSDI, Boston, MA, USA, 30 March–1 April 2011; pp. 197–210. [Google Scholar]
- Wang, J.; Hassanieh, H.; Katabi, D.; Indyk, P. Efficient and reliable low-power backscatter networks. In Proceedings of the ACM SIGCOMM 2012 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communication, Helsinki, Finland, 13–17 August 2012; pp. 61–72. [Google Scholar]
- Jin, M.; He, Y.; Meng, X.; Zheng, Y.; Fang, D.; Chen, X. Fliptracer: Practical parallel decoding for backscatter communication. IEEE ACM Trans. Netw. 2019, 27, 330–343. [Google Scholar] [CrossRef]
- Ou, J.; Li, M.; Zheng, Y. Come and be served: Parallel decoding for cots rfid tags. In Proceedings of the 21st Annual International Conference on Mobile Computing and Networking, Paris, France, 7–11 September 2015; pp. 500–511. [Google Scholar]
- Mafole, P.; Manabe, Y.; Kitasuka, T.; Aritsugi, M. Energy efficient backoff-free fragment retransmission fragmentation scheme for IEEE 802.11 WLAN. In Frontier and Innovation in Future Computing and Communications; Springer: Dordrecht, The Netherland, 2014; pp. 169–176. [Google Scholar]
- Dong, W.; Chen, C.; Liu, X.; He, Y.; Liu, Y.; Bu, J.; Xu, X. Dynamic packet length control in wireless sensor networks. IEEE Trans. Wirel. Commun. 2014, 13, 1172–1181. [Google Scholar] [CrossRef]
- Yi, B.; Xiang, M.; Huang, T.; Huang, H.; Qiu, K.; Li, W. Data gathering with distributed rateless coding based on enhanced online fountain codes over wireless sensor networks. AEU-Int. J. Electron. Commun. 2018, 92, 86–92. [Google Scholar] [CrossRef]
- Geethu, K.S.; Babu, A.V. A Hybrid ARQ scheme combining erasure codes and selective retransmissions for reliable data transfer in underwater acoustic sensor networks. EURASIP J. Wirel. Commun. Netw. 2017, 2017, 32. [Google Scholar] [CrossRef]
- Kumar, C.P.; Selvakumar, R. Erasure Codes for Reliable Communication in Internet of Things (IoT) Embedded with Wireless Sensors. In Cognitive Computing for Big Data Systems over IoT; Springer: Cham, Switzerland, 2018; pp. 115–137. [Google Scholar]
- Aygun, B.; Mandelli, S.; Wild, T.; Saur, S.; Schaich, F. Side-link assisted hybrid automatic repeat request for ultra-reliable low latency communications. In Proceedings of the WSA 2017, 21th International ITG Workshop on Smart Antennas, Berlin, Germany, 15–17 March 2017; pp. 1–7. [Google Scholar]
- Li, Y.; Fu, L.; Ying, Y.; Ying, Y.; Chi, K.; Zhu, Y. Goodput optimization via dynamic frame length and charging time adaptation for backscatter communication. Peer-Peer Netw. Appl. 2017, 10, 440–452. [Google Scholar] [CrossRef]

| Parameters | Values |
|---|---|
| payload length (bit) | 16~96 |
| PC and CRC length (bit) | 32 |
| RC constant | 2, 3 |
| maximum voltage (V) | 6, 5 |
| weight coefficient | 0.35 |
| minimum redundant frames | 1 |
| maximum redundant frames | 20 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, J.; Liu, X.; Li, D. Fast and Reliable Burst Data Transmission for Backscatter Communications. Sensors 2019, 19, 5418. https://doi.org/10.3390/s19245418
Zhao J, Liu X, Li D. Fast and Reliable Burst Data Transmission for Backscatter Communications. Sensors. 2019; 19(24):5418. https://doi.org/10.3390/s19245418
Chicago/Turabian StyleZhao, Jumin, Xiaojuan Liu, and Dengao Li. 2019. "Fast and Reliable Burst Data Transmission for Backscatter Communications" Sensors 19, no. 24: 5418. https://doi.org/10.3390/s19245418
APA StyleZhao, J., Liu, X., & Li, D. (2019). Fast and Reliable Burst Data Transmission for Backscatter Communications. Sensors, 19(24), 5418. https://doi.org/10.3390/s19245418




