Design and Implementation of a Trust Information Management Platform for Social Internet of Things Environments
Abstract
1. Introduction
2. Background
2.1. Definition and Attribution of Trust
2.2. Previous Studies on Trust in SIoT
- “co-location” relationships, established among objects used always in the same place;
- “co-work” relationships, established whenever objects collaborate to provide a common IoT application;
- “parental” relationships, related to objects belonging to the same production batch (e.g., same manufacturer, same model);
- “co-ownership” relationships, established among heterogeneous objects which belong to the same user.
3. Trust Information Management Framework
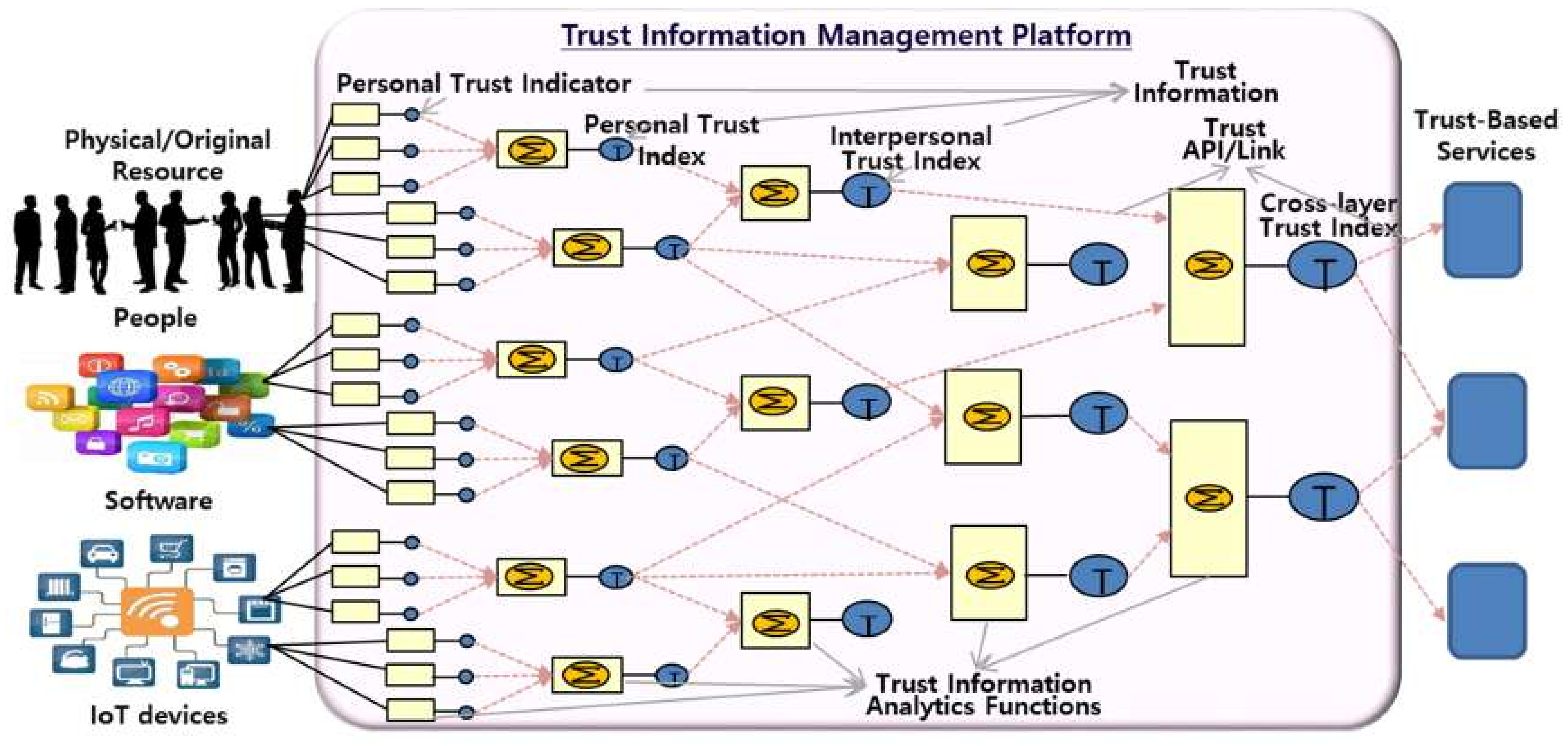
3.1. Converged Trust Information Management
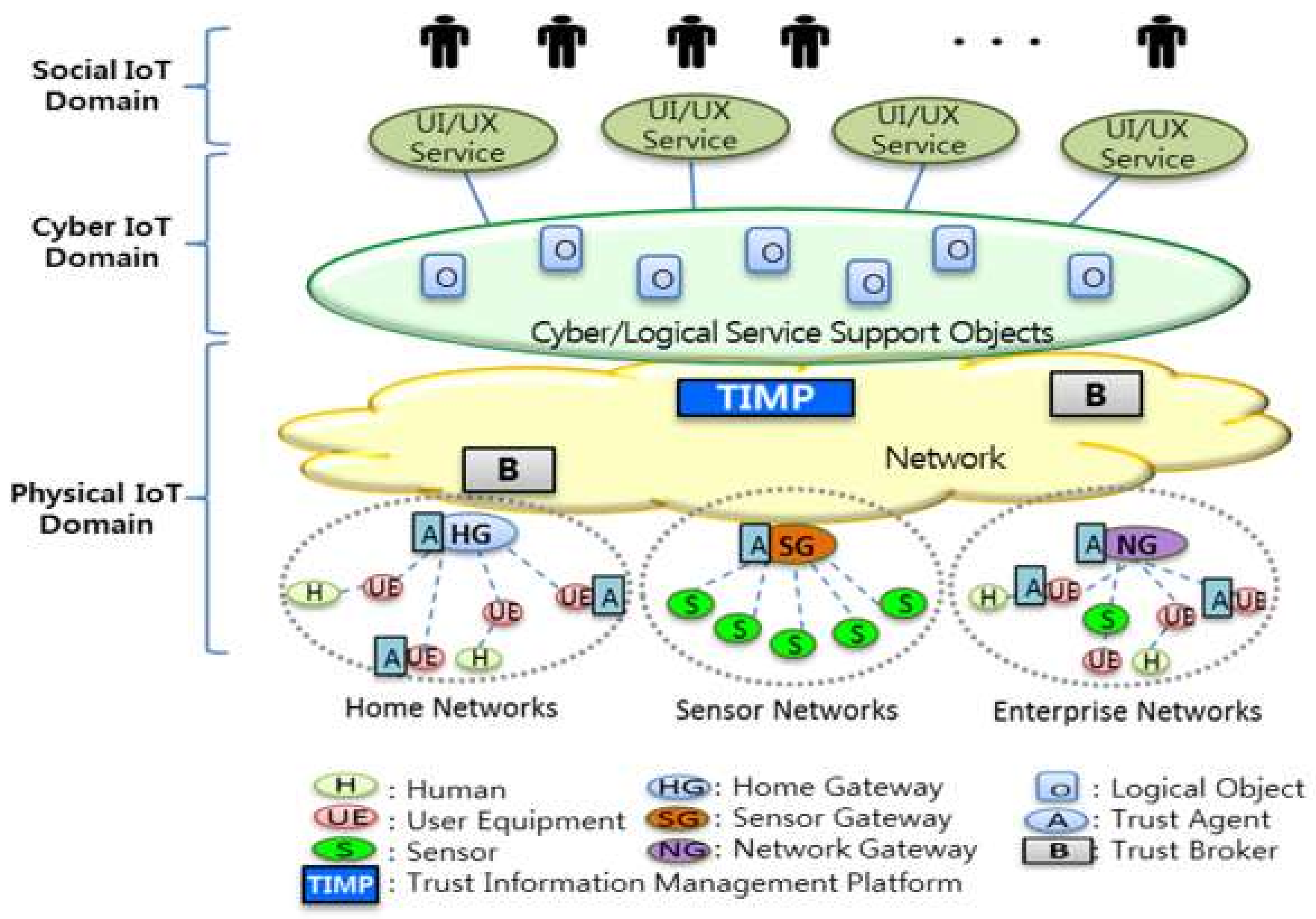
3.2. Generic IoT Trust Reference Model
3.3. Constraints on Data Acquisition
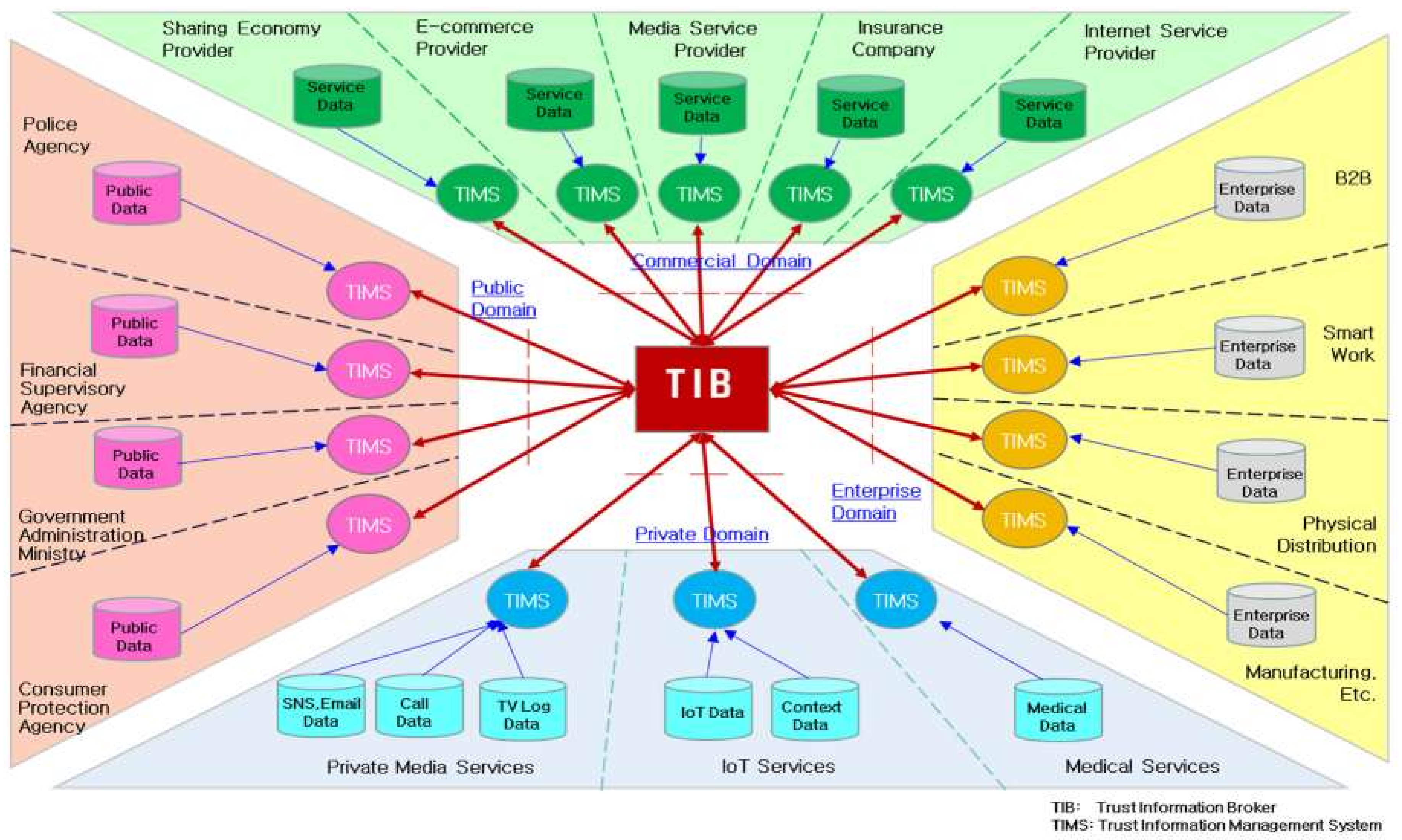
4. Trust Information Management Platform
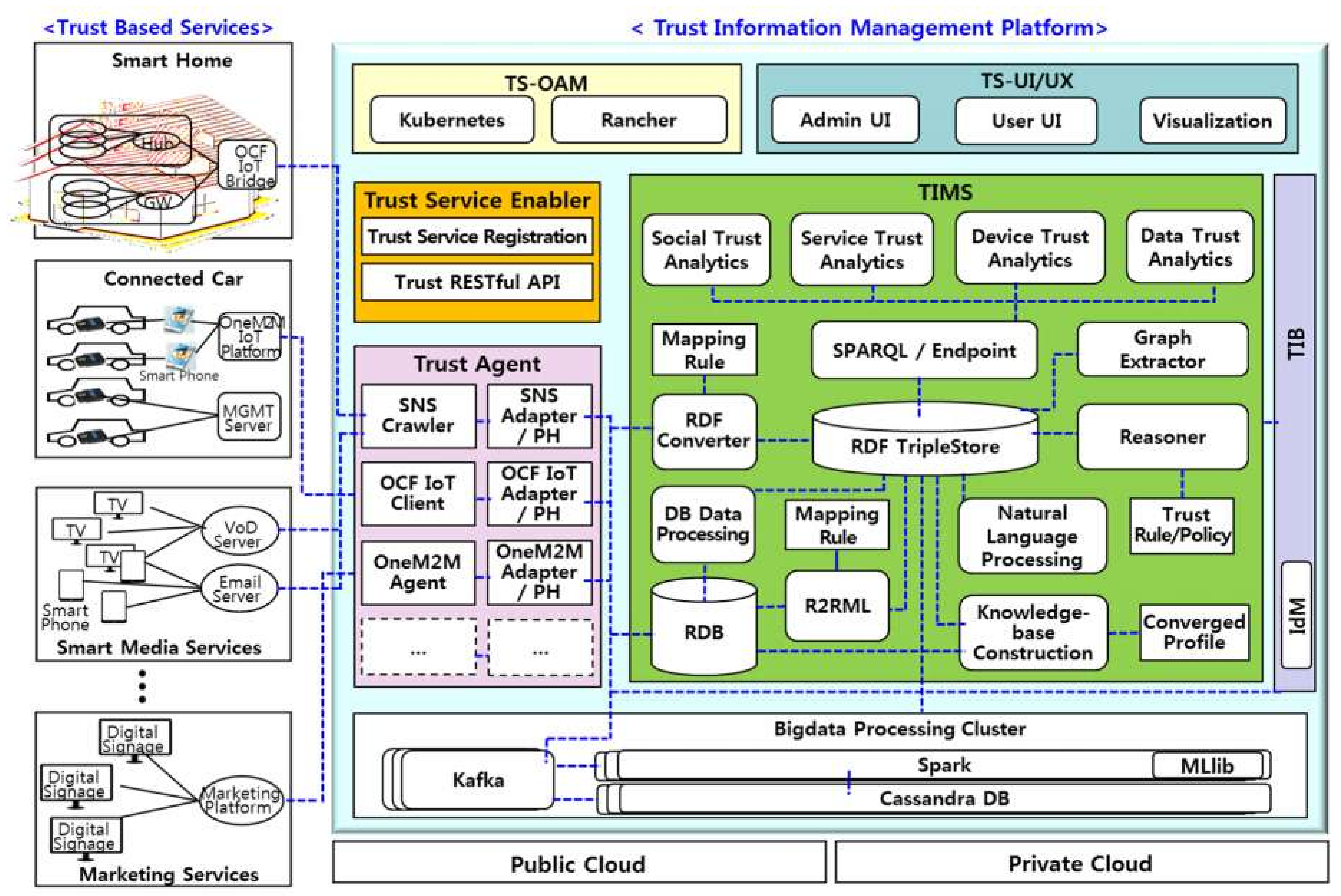
4.1. TIMP Architecture
- (1)
- Trust Service Enabler (TSE)
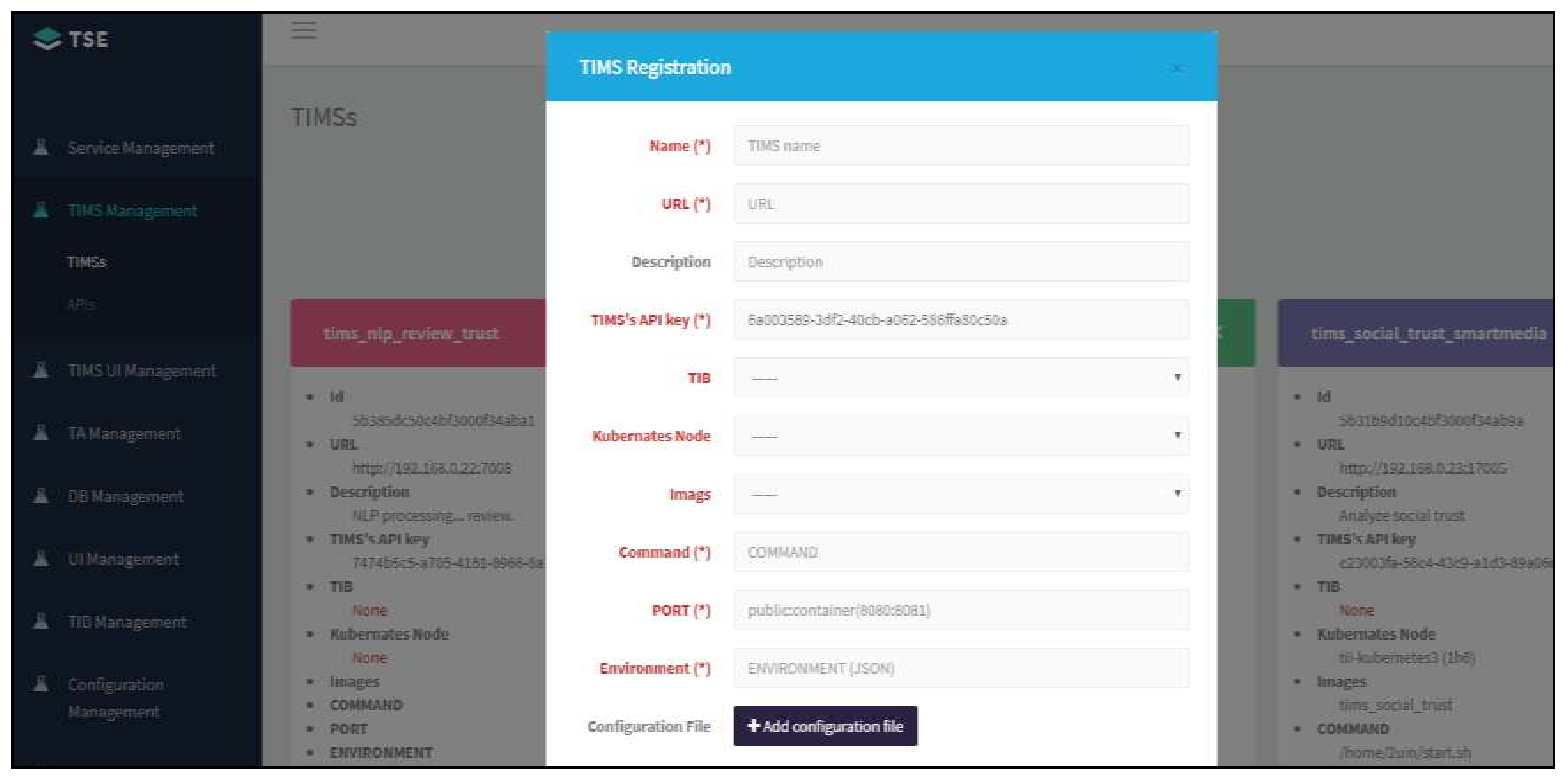
- Trust RESTful API is an interface that enables various trust system modules such as the TA, TIMS, TIB, and databases to be registered and managed in the TSE. Trust system module providers such as the TA, TIMS, TIB, and databases can receive usage fees based on their usage when their modules registered with TSE are used for trust services.
- Trust service registration performs the function of dynamically configuring and allocating a virtual TIMS to the service provider by receiving the registration of the trust information service from the service users and orchestrating the registered trust system modules using the Trust RESTful API.
- (2)
- Trust Agent (TA)
- Social Networking Service (SNS) crawler periodically acquires user data from various social network services such as Facebook, Twitter, Gmail and so on.
- SNS adapter and privacy handler (PH) performs the function of anonymizing the user data received from the SNS crawler and transmitting it to the database of the TIMS. Because the TIMS stores, analyzes, and manages trust information based on anonymized personal information, it can cope with the leakage of personal information due to hacking and similar.
- OCF/OneM2M IoT clients are IoT data collection interfaces according to the OCF (Open Connectivity Foundation) standards and OneM2M standards, respectively.
- OCF/OneM2M IoT adapter and PH modules anonymize and transfer data collected from the OCF/OneM2M IoT Client to the TIMS, similar to the role described for the SNS adapter and PH.
- (3)
- Trust Information and Management System (TIMS)
- The social network analysis module serves to deduce the trust indexes among users by analyzing patterns of communication between users through social network services and e-mails. It uses ontology methods to share and deliver social network data in a systematic representation format. Several ontologies, such as friend-of-a-friend (FOAF) [24], are used to represent social networks. FOAF ontologies, which provide information extracted from user profiles and lists, are widely used to provide portability between social networking sites and to model user-generated information and content in a machine-readable manner, since they can describe their relationships and online activities. In addition, resource description framework (RDF)-based social data descriptions provide a much more effective way of representing online social networks than existing social network models. In addition, semantic web technology is also very useful for improving information retrieval performance and increasing flexibility in data access.
- A natural language processing module finds information such as stakeholder trust, IoT trust, service trust, and data trust based on text data collected from Facebook, Twitter, and Gmail, and builds a knowledge base.
- A service trust analysis module analyzes service utilization data in smart homes, connected cars, and smart media services, which are generated by the service itself.
- (4)
- Trust Information Broker (TIB)
- (5)
- Trust System—Operations, Administration, and Management (TS-OAM)
4.2. Trust Data Analytics Procedure
5. Implementation and Use Case
5.1. TIMP Implementation
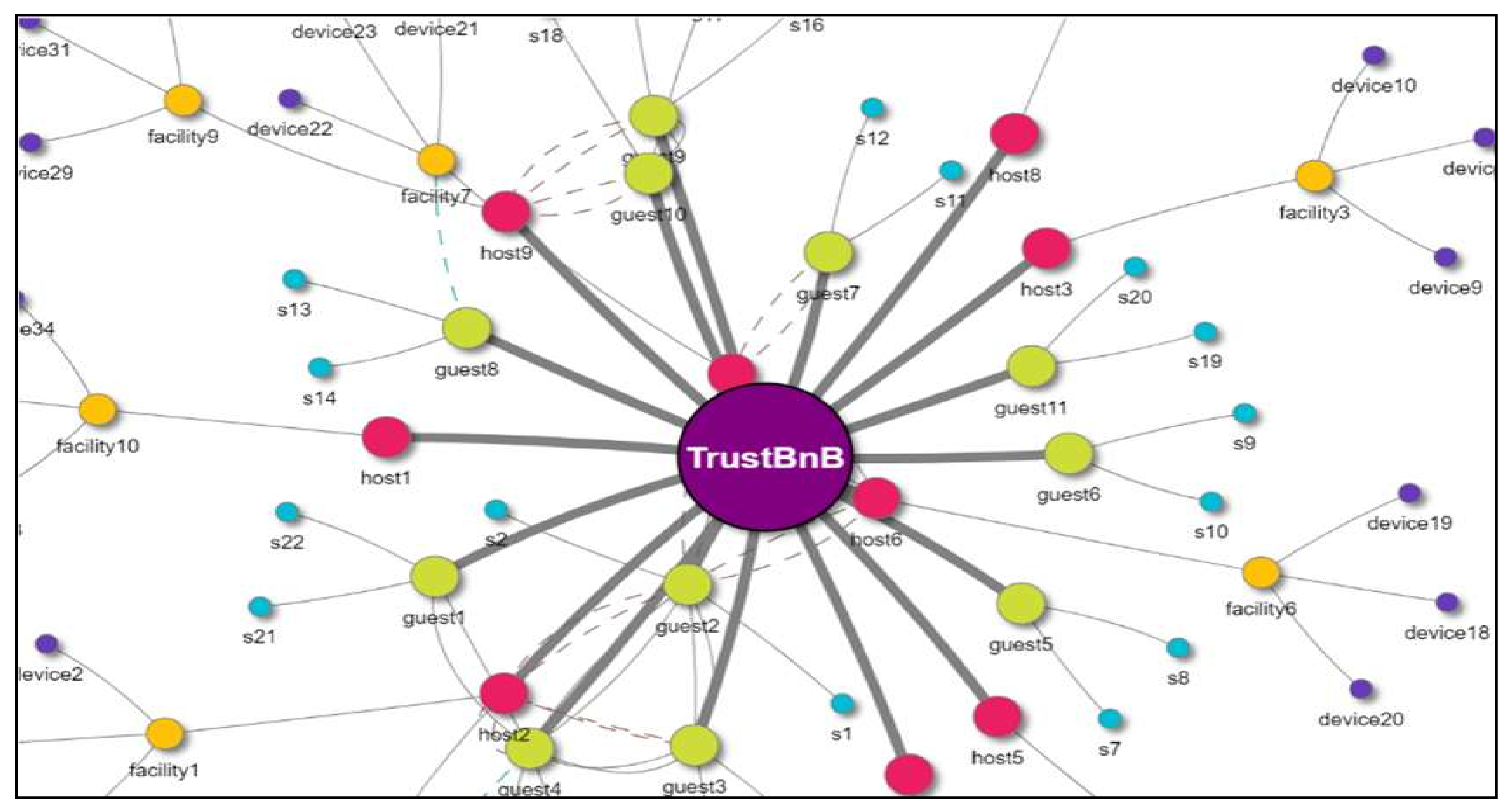
5.2. TIMP-Based Service Use Case
- Based on past offer history and reputation or the trust information at the time of resource registration, the resource provider undergoes a verification process for the service target (or shared resource) and the charge.
- A minimum user trust index necessary for use permission of the user when the provider provides a resource is set, and a user trust index set by the provider is compared with the trust index of a user to control the use of the resource in response to the comparison result.
- The TIMP collects resource use status information from the resource and analyzes IoT data from the collected resource to determine whether contract violation, resource failure, or safety problems have occurred; if it is determined that contract violation, resource failure, or safety problems have occurred while the user is using the resource, the provider or the user is notified of this.
- The resource user exchanges information with the service system of the service intermediary; inputs a target resource, a location, a number of users, and the like; searches for an available resource; and exchanges various aspects service transaction information. At this time, the user inputs the required trust level of the resource to be used.
- After the user selects one of the listed resources and makes a reservation, when visiting the accommodation or taking over the automobile at the scheduled time, the user uses the resource according to the contract details.
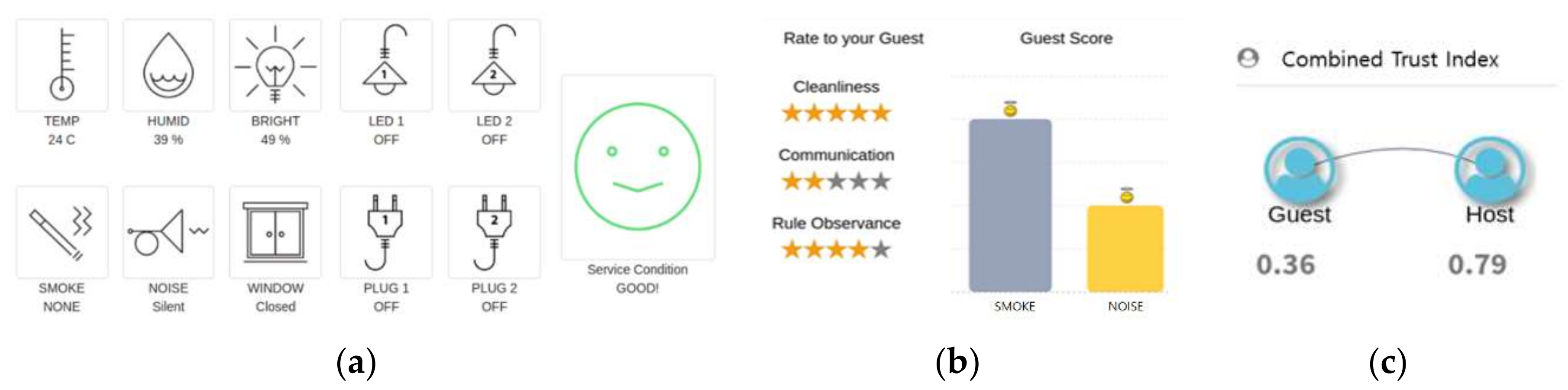
- The TIMP generates and manages the trust index of a user using the resource by checking IoT data on resource management status (e.g., energy usage, whether a door is locked or not, smoking, etc.) during a resource use period. It can examine whether the service contract has actually been observed through IoT functions (e.g., smoking, whether the number of contracted person is exceeded, safety observance, etc.).
- The TIMP analyzes the trust information as follows:
- .
- Set-up of functional goals of analysis algorithms;
- .
- Type of analysis: system trust, personal trust, interpersonal trust (social interaction);
- .
- Filtering and priority decision based on trust information;
- .
- Selection of a trust analysis algorithm appropriate for each entity’s type of trust information (e.g., Rule-based algorithm, Machine-based algorithm, Graph-based algorithm, etc.)
- The TIMS calculates a user trust index by adding objective use status data collected from the IoT sensors and subjective data from a resource provider, and by reflecting past history between the user–resource provider entities.
- The TIMP controls the use of the resource based on the user trust index and the resource trust index. It can limit the use of the resource by the user when the comparison result indicates that the trust index of the user to use the resource is lower than the trust index for resource permission set by the provider.
- The TIMP updates the trust information based on the feedback from the user and the resource provider, for example by re-adjusting the trust index of the corresponding user and the trust index of the corresponding resource.
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Lee, J.; Bagheri, B.; Kao, H.-A. A Cyber-Physical Systems architecture for Industry 4.0-based manufacturing systems. Manuf. Lett. 2015, 3, 18–23. [Google Scholar] [CrossRef]
- Yan, Z.; Zhang, P.; Vasilakos, A.V. A survey on trust management for Internet of Things. J. Netw. Comput. Appl. 2014, 42, 120–134. [Google Scholar] [CrossRef]
- Wang, F.-Y. The Emergence of Intelligent Enterprises: From CPS to CPSS. IEEE Intell. Syst. 2010, 25, 85–88. [Google Scholar] [CrossRef]
- Social Internet of Things. Available online: http://www.social-iot.org./ (accessed on 29 October 2019).
- Atzori, L.; Iera, A.; Morabito, G.; Nitti, M. The Social Internet of Things (SIoT)—When social networks meet the Internet of Things: Concept, architecture and network characterization. Comput. Netw. 2012, 56, 3594–3608. [Google Scholar] [CrossRef]
- Möllering, G. The nature of trust: From Georg Simmel to a theory of expectation, interpretation and suspension. Sociology 2001, 35, 403–420. [Google Scholar] [CrossRef]
- Huang, F. Building social trust: A human-capital approach. J. Inst. Theor. Econ. 2007, 163, 552–573. [Google Scholar] [CrossRef]
- Marsh, S.P. Formalising Trust as a Computational Concept. Ph.D. Thesis, Dept. Computing Science and Mathematics, University of Stirling, Stirling, UK, 1994. [Google Scholar]
- ITU. Trust Provisioning for Future ICT Infrastructures and Services; Technical Report; ITU-T: Geneva, Switzerland, 2016. [Google Scholar]
- Kim, S.; Yoon, Y. Recommendation system for sharing economy based on multidimensional trust model. Multimed. Tools Appl. 2016, 75, 15297–15310. [Google Scholar] [CrossRef]
- ITU. Overview of Trust Provisioning in ICT Infrastructures and Services; Recommendation Y.3052; ITU-T: Geneva, Switzerland, 2017. [Google Scholar]
- Azer, M.A.; El-Kassas, S.M.; Hassan, A.W.F.; El-Soudani, M.S. A survey on trust and reputation schemes in ad hoc networks. In Proceedings of the Third International Conference on Availability, Reliability and Security ARES, Barcelona, Spain, 4–7 March 2008; pp. 881–886. [Google Scholar]
- Paydar, S.; Kahani, M.; Zarrinkalam, F. PAD: A Semantic Social Network. In Proceedings of the ICCKE, Mashhad, Iran, 31 October–1 November 2013; pp. 102–107. [Google Scholar]
- Lee, K.-S.; Hong, M.-D.; Jung, J.-G.; Jo, G. Building a Semantic Social Network Based on Interpersonal Relationships. In Proceedings of the Third FTRA International Conference on Mobile, Ubiquitous, and Intelligent Computing, Vancouver, BC, Canada, 26–28 June 2012; pp. 90–95. [Google Scholar]
- Gloor, P.A.; Krauss, J.; Nann, S.; Fischbach, K.; Schoder, D. Web Science 2.0: Identifying Trends through Semantic Social Network Analysis. In Proceedings of the International Conference on Computational Science and Engineering, Vancouver, BC, Canada, 29–31 August 2009; pp. 215–222. [Google Scholar]
- Pankong, N.; Prakancharoen, S.; Buranarach, M. A combined semantic social network analysis framework to integrate social media data. In Proceedings of the Knowledge and Smart Technology, Chonburi, Thailand, 7–8 July 2012; pp. 37–42. [Google Scholar]
- Ruta, M.; Scioscia, F.; Loseto, G.; di Sciascio, E. A Semantic-Enabled Social Network of Devices for Building Automation. IEEE Trans. Ind. Inform. 2017, 13, 3379–3388. [Google Scholar] [CrossRef]
- Um, T.-W.; Lee, G.M.; Lee, H.-W. Trustworthiness management in sharing CDN infrastructure. In Proceedings of the 2018 International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 10–12 January 2018; pp. 73–75. [Google Scholar]
- Jayasinghe, U.; Truong, N.B.; Lee, G.M.; Um, T. RpR: A Trust Computation Model for Social Internet of Things. In Proceedings of the Smart World Congress, Intl IEEE Conferences on Ubiquitous Intelligence & Computing, Toulouse, France, 18–21 July 2016; pp. 930–937. [Google Scholar]
- Truong, N.B.; Lee, H.; Askwith, B.; Lee, G.M. Toward a Trust Evaluation Mechanism in the Social Internet of Things. Sensors 2017, 17, 1346. [Google Scholar] [CrossRef] [PubMed]
- Jayasinghe, U.; Lee, G.M.; Um, T.; Shi, Q. Machine Learning based Trust Computational Model for IoT Services. IEEE Trans. Sustain. Comput. 2019, 4, 39–52. [Google Scholar] [CrossRef]
- Truong, N.B.; Lee, G.M.; Um, T.; Mackay, M. Trust Evaluation Mechanism for User Recruitment in Mobile Crowd-Sensing in the Internet of Things. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2705–2719. [Google Scholar] [CrossRef]
- Um, T.; Lee, G.M.; Choi, J.K. Strengthening trust in the Future Social-Cyber-Physical infrastructure: An ITU-T Perspective. IEEE Commun. Mag. 2016, 64, 36–42. [Google Scholar] [CrossRef]
- Friend of a Friend (FOAF) Project. Available online: http://www.foaf-project.org/ (accessed on 29 October 2019).
- Kubernetes. Available online: https://kubernetes.io/ (accessed on 29 October 2019).
- Rancher Labs. Available online: https://rancher.com/ (accessed on 29 October 2019).



| From the Viewpoint of | Usage of User or Resource Trust Information |
|---|---|
| Resource provider | - Sets the minimum user trust index of a user who is allowed to use the provider’s resource (e.g., select from 1 to 5 stars). - Grant resource use permission only for a trustworthy user. - Suggest differentiated charges and resource use options according to a user trust index (e.g., for five-star graded user, free internet and free parking with a $50 accommodation rental fee; for a three-star graded user, a $60 accommodation rental fee and an extra fee for convenient facilities). |
| Resource user | - The trust index of a resource is able to be checked through a trust-based resource-sharing service. - Only resources with a trust index are selected by filtering by trust index in a resource use reservation search window. - Resource use with better conditions in the future is possible through observation the resource use rules (or contract) and enhancing user trust. |
| Resource-sharing service intermediary | - Provision of differentiated resource use fees and options according to trust indexes when the service system is in operation. - The trust-based resource-use service system is configured with a trust index matching method on both sides (e.g., resource provider and user). - In order to increase their user trust index, a user is encouraged to comply with the contract during resource use. - For a provider, a resource trust index is recognized as being linked to increased revenue to encourage efforts to manage users and resources. |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Um, T.-W.; Lee, E.; Lee, G.M.; Yoon, Y. Design and Implementation of a Trust Information Management Platform for Social Internet of Things Environments. Sensors 2019, 19, 4707. https://doi.org/10.3390/s19214707
Um T-W, Lee E, Lee GM, Yoon Y. Design and Implementation of a Trust Information Management Platform for Social Internet of Things Environments. Sensors. 2019; 19(21):4707. https://doi.org/10.3390/s19214707
Chicago/Turabian StyleUm, Tai-Won, Eunhee Lee, Gyu Myoung Lee, and Yongik Yoon. 2019. "Design and Implementation of a Trust Information Management Platform for Social Internet of Things Environments" Sensors 19, no. 21: 4707. https://doi.org/10.3390/s19214707
APA StyleUm, T.-W., Lee, E., Lee, G. M., & Yoon, Y. (2019). Design and Implementation of a Trust Information Management Platform for Social Internet of Things Environments. Sensors, 19(21), 4707. https://doi.org/10.3390/s19214707






