A Dynamic Access Probability Adjustment Strategy for Coded Random Access Schemes
Abstract
:1. Introduction
2. Preliminaries
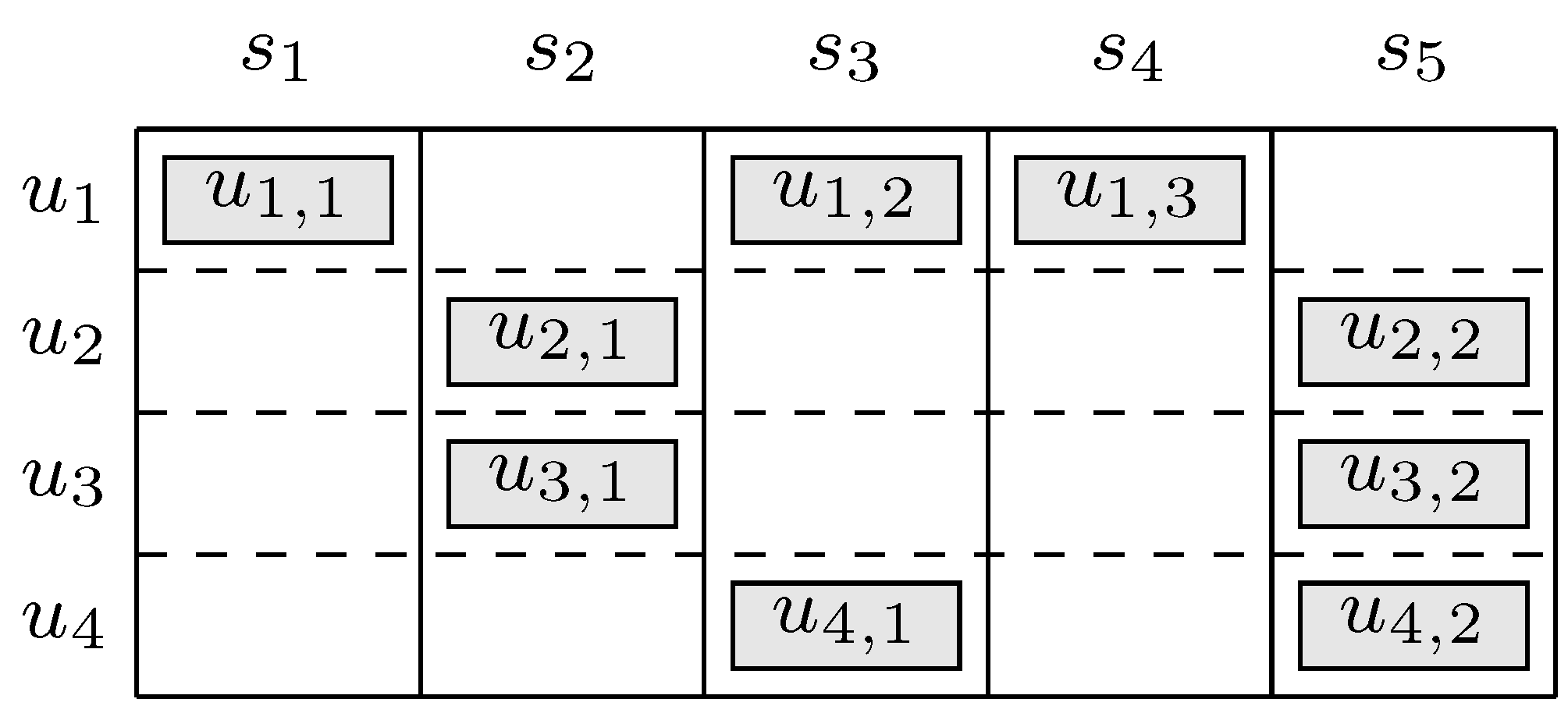
2.1. System Model
2.2. Threshold Definition and Notation
2.3. Combinatorial Parameters
3. Dynamic Access Probability Algorithm
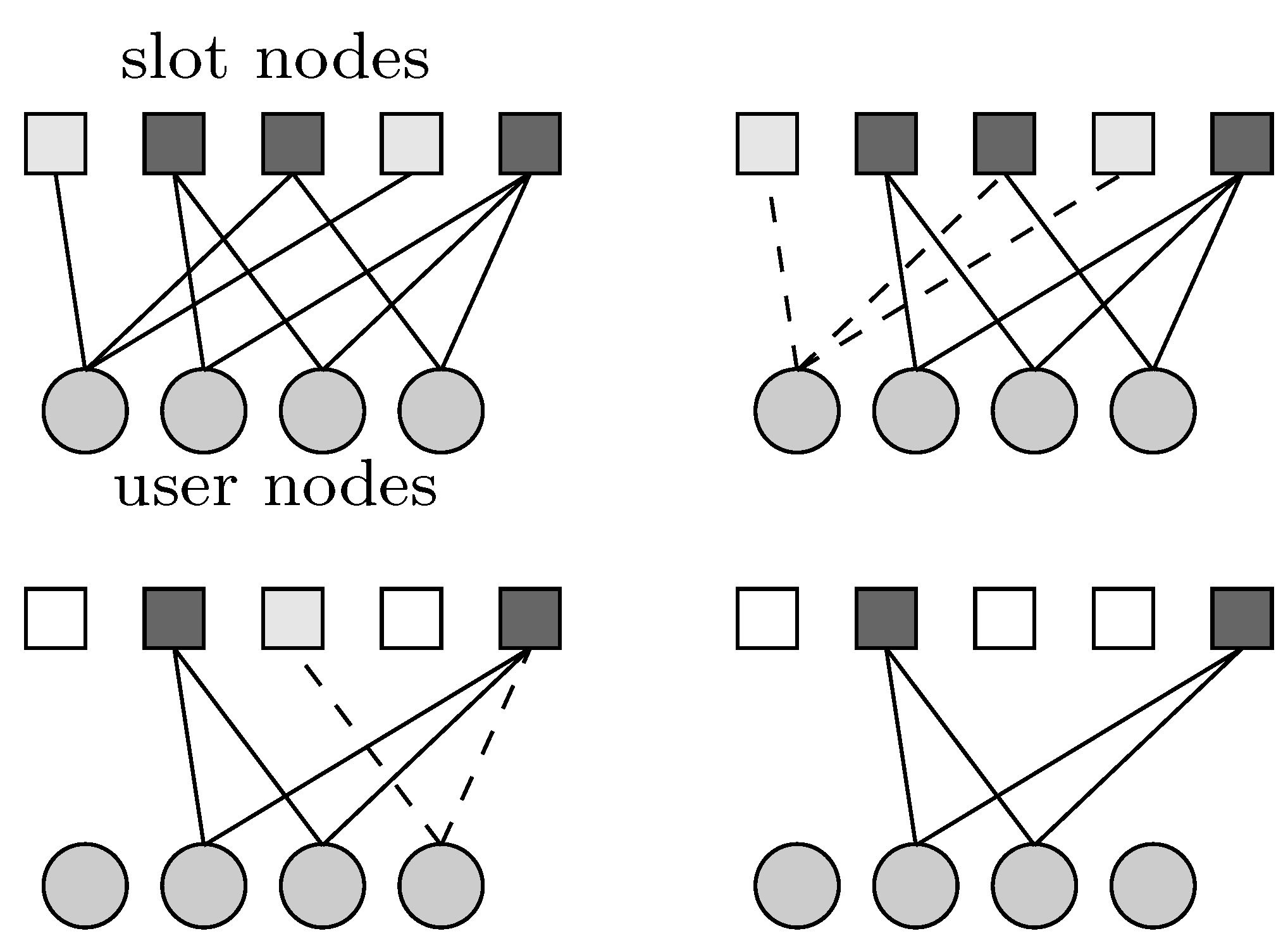
3.1. Number of Transmitting Users Estimation
3.2. Access Probability Adjustment Strategy
- Not fully reliable estimate. In high load conditions, SIC typically stops prematurely with a relatively small number of recovered users. We say that the estimate is not fully reliable when the number of users recovered by processing the frame is smaller than the number of users that could not be recovered:or, equivalently,
- Congestion with reliable estimate. The number of active users is above threshold , but the number of users recovered by processing the frame is not less than the number of users that could not be recovered:
- No congestion. The number of active users is below threshold :
| Algorithm 1: Receiver procedure |
 |
- If (congestion), in the next frame each backlogged user attempts access to the frame with probability equal to the new access probability. Each non-backlogged user is prevented from transmitting new packets;
- If (no congestion), users that are in a backlog state retransmit their packet. Users that are not backlogged take their normal access activity.
4. Numerical Results
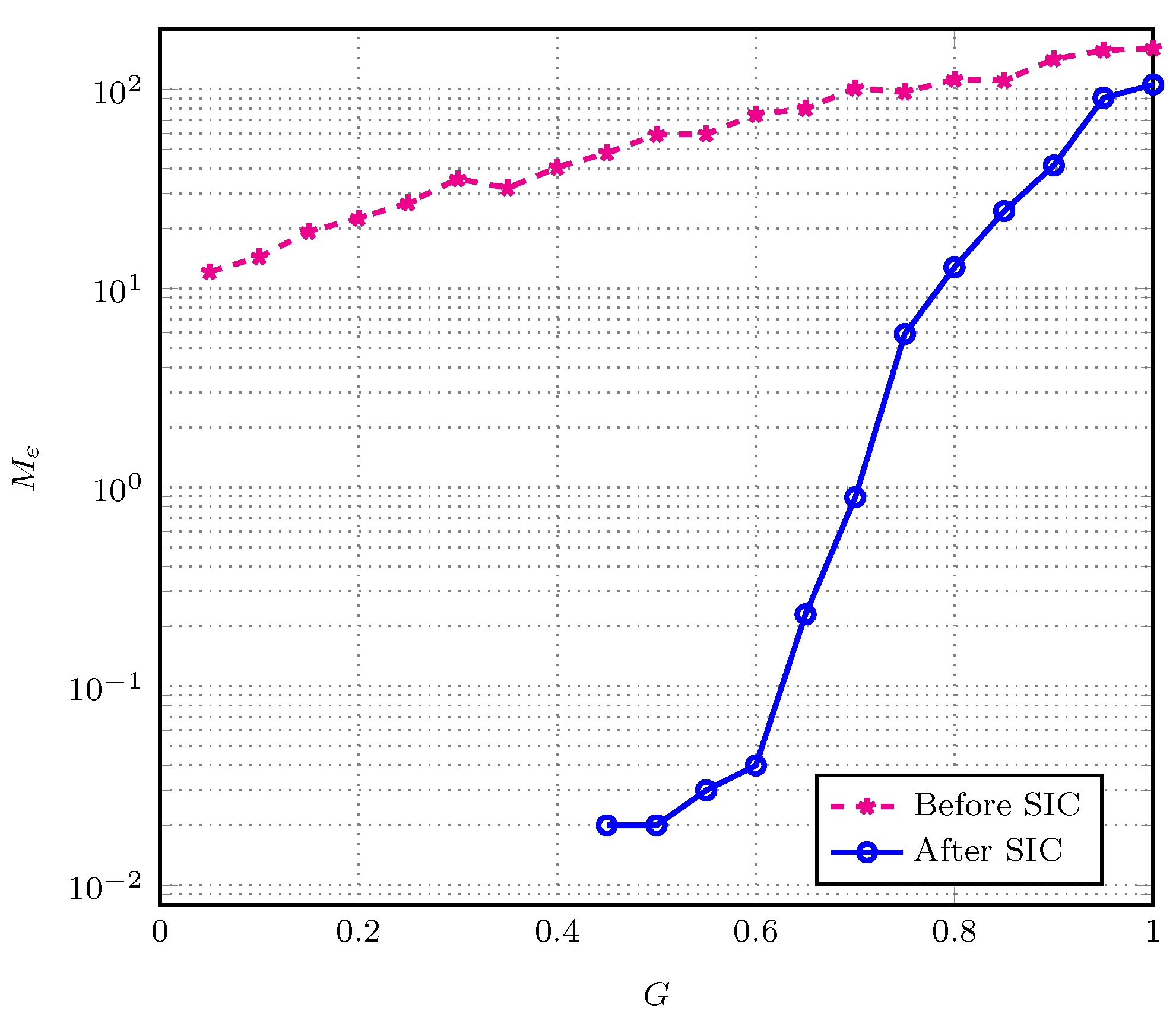
4.1. Estimation of Transmitting Users
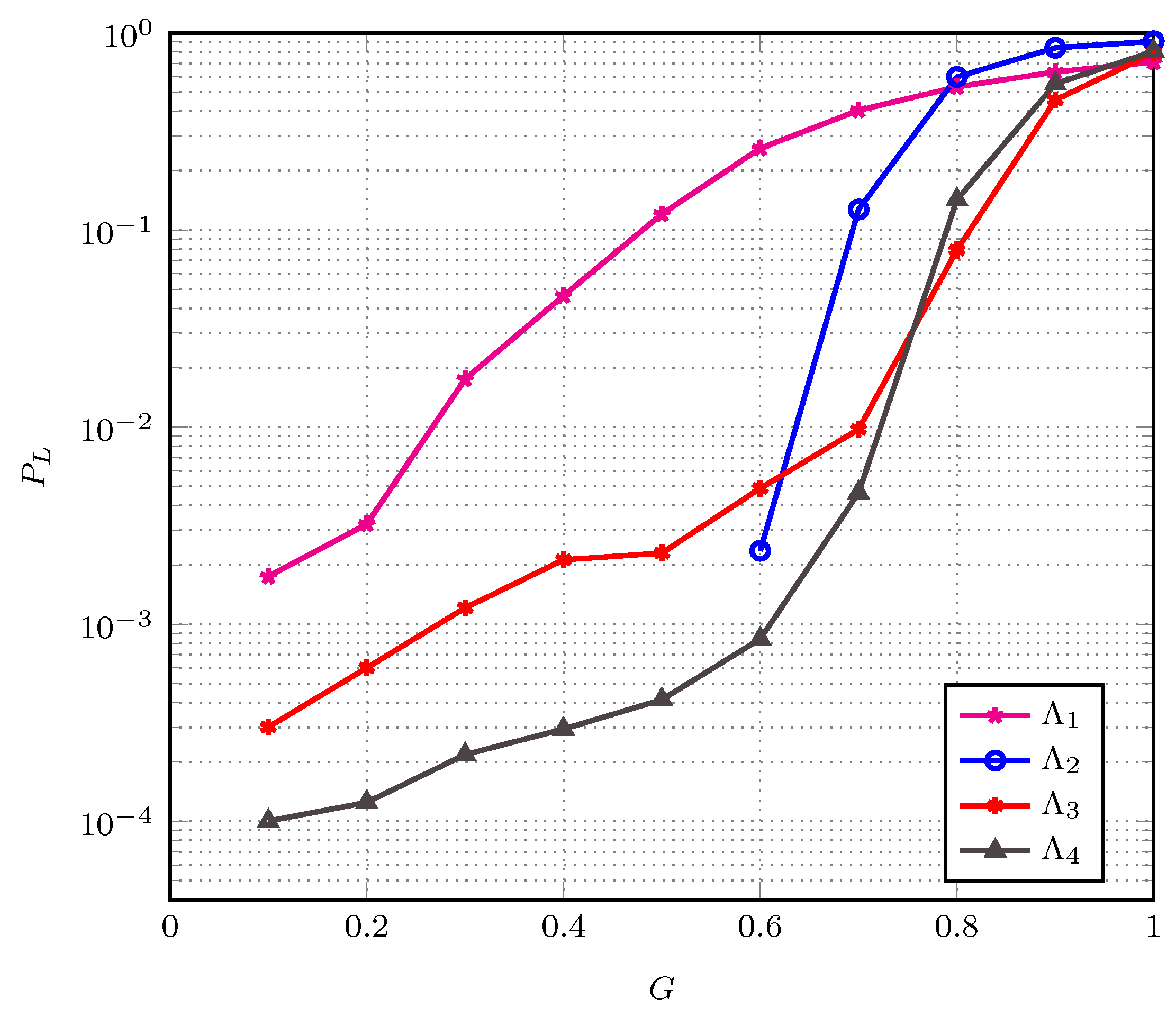
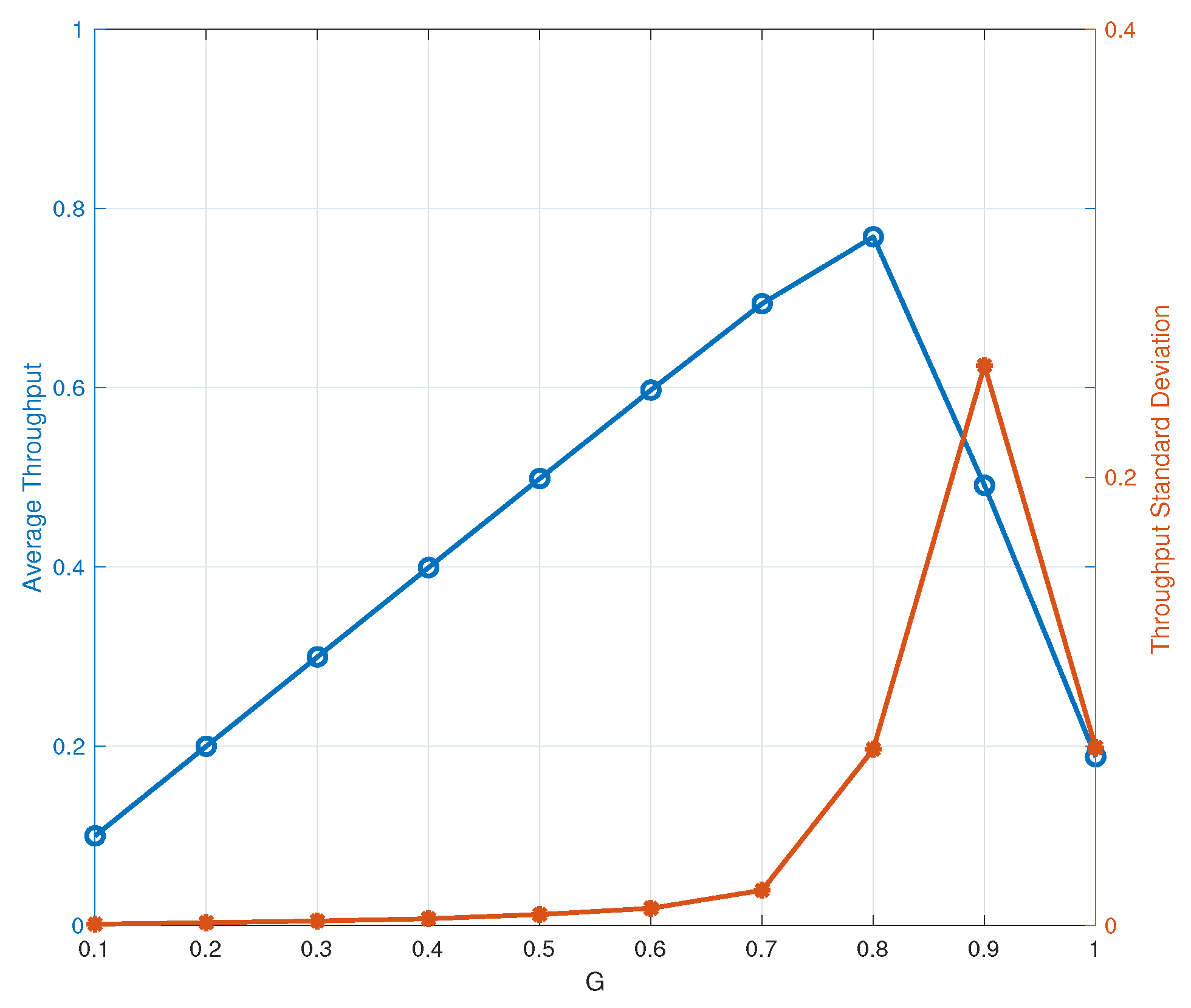
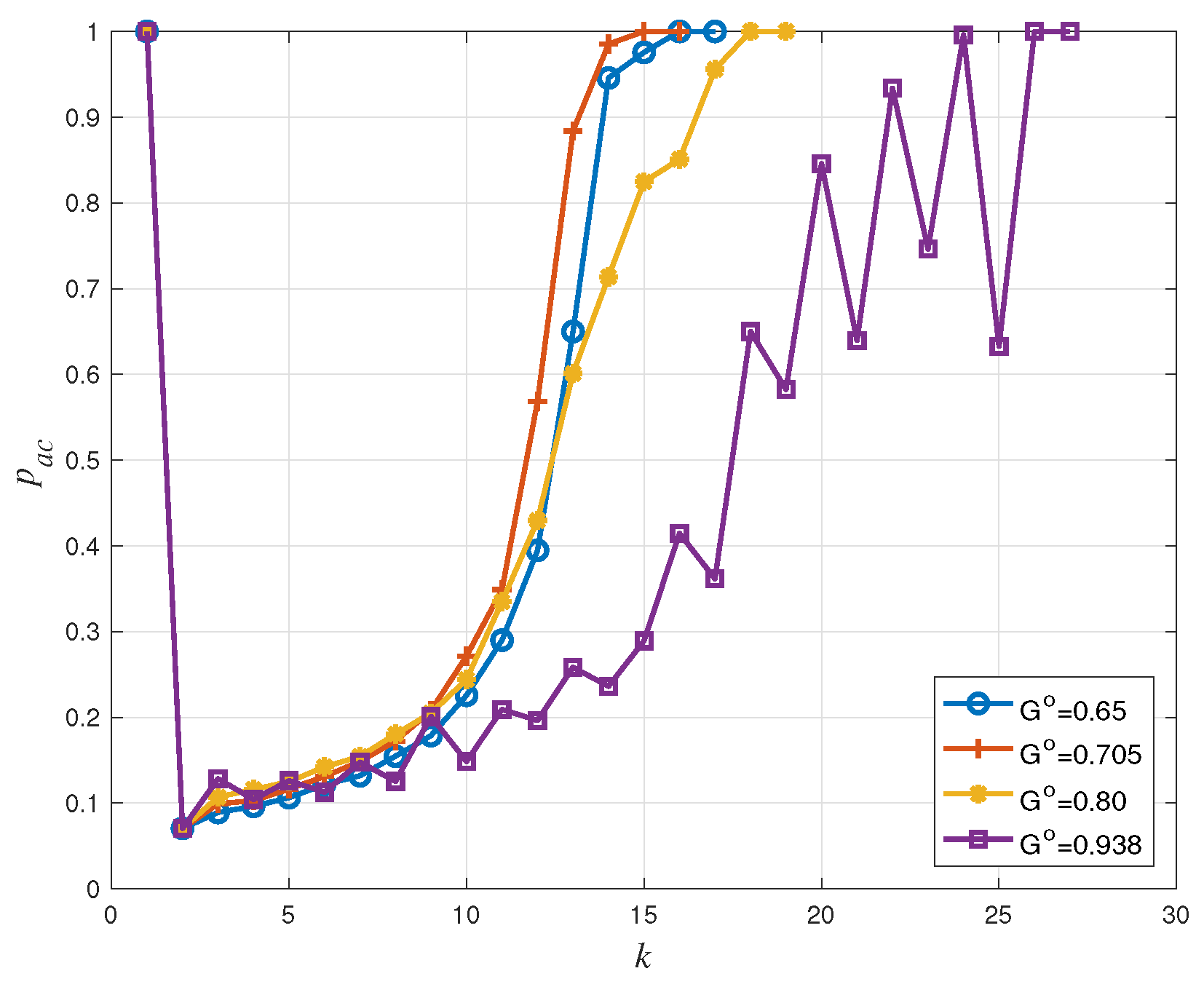
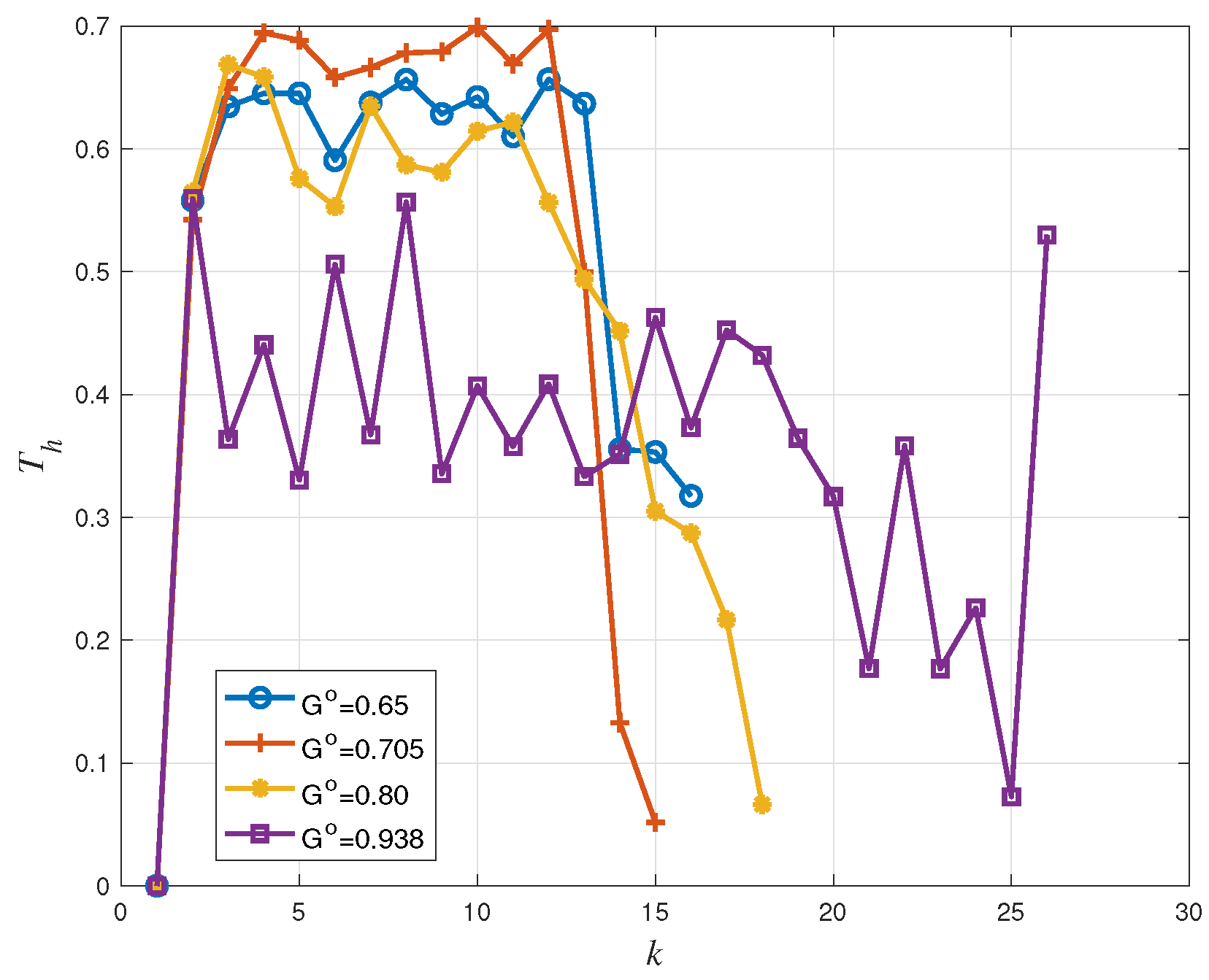
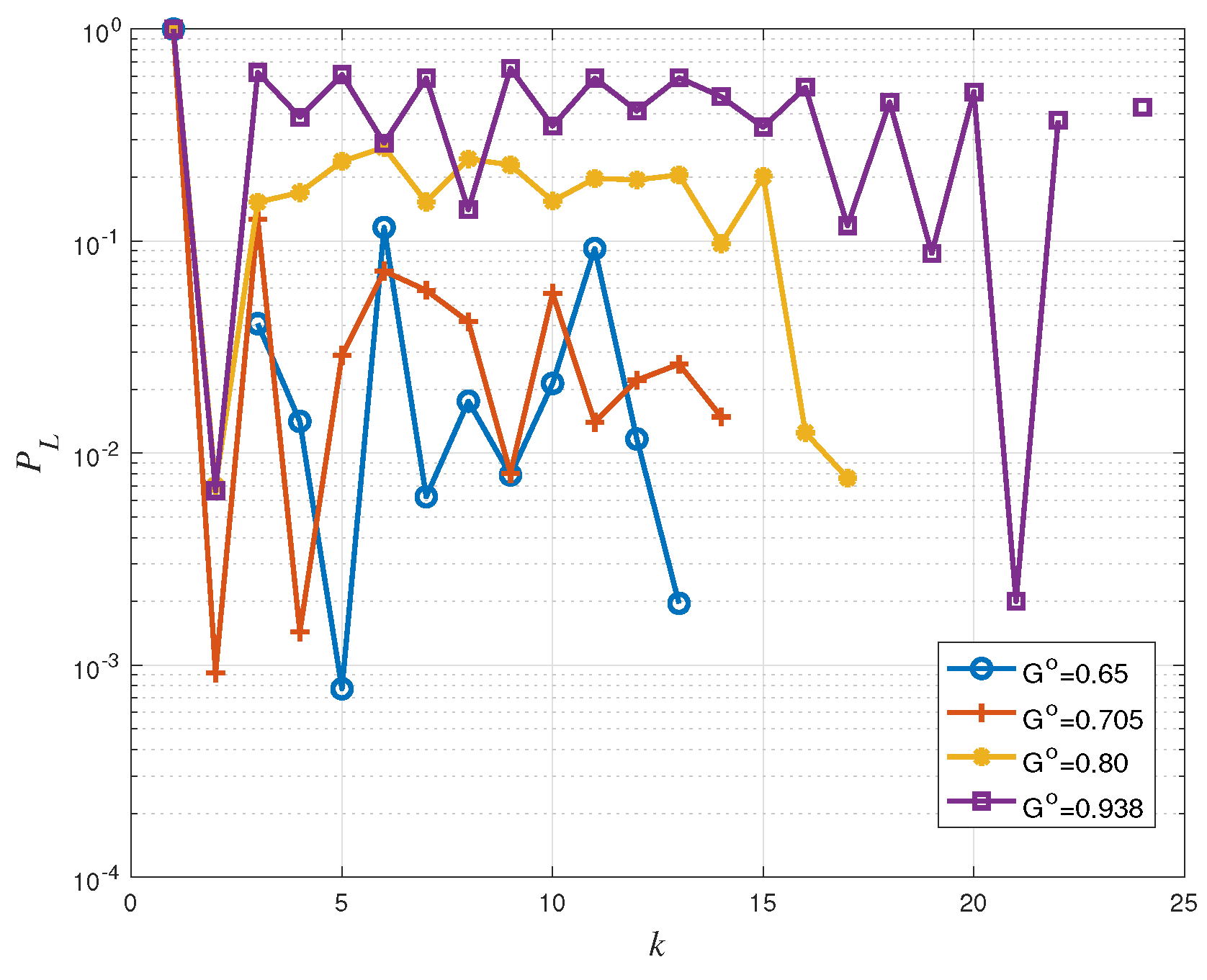
4.2. Dynamic Access Probability Simulation Results
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A. Justification and Implementation of Equation (uid44)
Appendix B. Estimation Using Collision Slots before SIC
References
- Abramson, N. The ALOHA system: Another alternative for computer communications. In Proceedings of the Fall Joint Computer Confonference, New York, NY, USA, 17–19 November 1970; pp. 281–285. [Google Scholar]
- Roberts, L.G. ALOHA packet systems with and without slots and capture. ACM SIGCOM Comput. Commun. Rev. 1975, 5, 28–42. [Google Scholar] [CrossRef]
- Casini, E.; De Gaudenzi, R.; Herrero, O.D.R. Contention resolution diversity slotted ALOHA (CRDSA): An enhanced random access scheme for satellite access packet networks. IEEE Trans. Wirel. Commun. 2007, 6, 1408–1419. [Google Scholar] [CrossRef]
- De Gaudenzi, R.; Herrero, O.D.R. Advances in random access protocols for satellite networks. In Proceedings of the 2009 International Workshop on Satellite and Space Communications, Tuscany, Italy, 9–11 September 2009; pp. 331–336. [Google Scholar]
- Liva, G. Graph-based analysis and optimization of contention resolution diversity slotted ALOHA. IEEE Trans. Commun. 2011, 59, 477–487. [Google Scholar] [CrossRef]
- Amat, A.G.; Liva, G. Finite Length Analysis of Irregular Repetition Slotted ALOHA in the Waterfall Region. IEEE Commun. Lett. 2018, 22, 886–889. [Google Scholar] [CrossRef]
- De Gaudenzi, R.; Herrero, O.D.R.; Gallinaro, G.; Cioni, S.; Arapoglou, P.D. Random access schemes for satellite networks, from VSAT to M2M: A survey. Int. J. Satellite Commun. Netw. 2018, 36, 66–107. [Google Scholar] [CrossRef]
- Alvi, S.; Durrani, S.; Zhou, X. Enhancing CRDSA with Transmit Power Diversity for Machine-Type Communication. IEEE Trans. On Vehic. Tech. 2018, 67, 7790–7794. [Google Scholar] [CrossRef]
- Paolini, E.; Liva, G.; Chiani, M. Coded slotted ALOHA: A graph-based method for uncoordinated multiple access. IEEE Trans. Inf. Theory 2015, 61, 6815–6832. [Google Scholar] [CrossRef]
- Paolini, E.; Stefanović, Č.; Liva, G.; Popovski, P. Coded random access: Applying codes on graphs to design random access protocols. IEEE Commun. Mag. 2015, 53, 144–150. [Google Scholar] [CrossRef]
- Taghavi, A.; Vem, A.; Chamberland, J.-F.; Narayanan, K.R. On the design of universal schemes for massive uncoordinated multiple access. In Proceedings of the 2016 IEEE International Symposium on Information Theory (ISIT), Barcelona, Spain, 10–15 July 2016; pp. 345–349. [Google Scholar]
- Sandgren, E.; i Amat, A.G.; Brännström, F. On frame asynchronous coded slotted ALOHA: Asymptotic, finite length, and delay analysis. IEEE Trans. Commun. 2017, 65, 691–704. [Google Scholar] [CrossRef]
- Schoute, F. Dynamic frame length ALOHA. IEEE Trans. Commun. 1983, 31, 565–568. [Google Scholar] [CrossRef]
- Chen, W.-T. An accurate tag estimate method for improving the performance of an RFID anticollision algorithm based on dynamic frame length ALOHA. IEEE Trans. Autom. Sci. Eng. 2009, 6, 9–15. [Google Scholar] [CrossRef]
- Eom, J.-B.; Lee, T.-J. Accurate tag estimation for dynamic framed-slotted ALOHA in RFID systems. IEEE Commun. Lett. 2010, 14, 60–62. [Google Scholar] [CrossRef]
- Wu, H.; Zeng, Y. Bayesian tag estimate and optimal frame length for anti-collision ALOHA RFID system. IEEE Trans. Autom. Sci. Eng. 2010, 7, 963–969. [Google Scholar] [CrossRef]
- Zanella, A. Estimating collision set size in framed slotted ALOHA wireless networks and RFID systems. IEEE Commun. Lett. 2012, 16, 300–303. [Google Scholar] [CrossRef]
- Rivero Angeles, M.E.; Lara Rodriguez, D.; Cruz-Perez, F.A. Random-access control mechanisms using adaptive traffic load in ALOHA and CSMA strategies for EDGE. IEEE Trans. Vehic. Tech. 2005, 54, 1160–1186. [Google Scholar] [CrossRef]
- Lee, M.W.; Lee, J.K.; Lim, J.S. R-CRDSA: Reservation-Contention Resolution Diversity Slotted ALOHA for Satellite Networks. IEEE Commun. Lett. 2012, 16, 1576–1579. [Google Scholar] [CrossRef]
- Noh, H.J.; Lee, J.K.; Lim, J.S. Performance evaluation of access control for CRDSA and R-CRDSA under high traffic load. In Proceedings of the 2013 IEEE Military Communications Conference, San Diego, CA, USA, 18–20 November 2013; pp. 1365–1370. [Google Scholar]
- Sun, J.; Liu, R. Irregular Repetition Slotted ALOHA with Priority (P-IRSA). In Proceedings of the 2016 IEEE Vehicular Technology Conference (VTC Spring), Nanjing, China, 15–18 May 2016; pp. 1–5. [Google Scholar]
- Sun, J.; Liu, R.; Paolini, E. Detecting the Number of Active Users in Coded Random Access Systems. In Proceedings of the 2018 IEEE 29th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Bologna, Italy, 9–12 September 2018; pp. 1–7. [Google Scholar]
- Sun, J.; Liu, R.; Paolini, E. Detecting the Number of Active Users in IRSA Access Protocols. In Proceedings of the 2018 IEEE 29th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Bologna, Italy, 9–12 September 2018; pp. 1972–1976. [Google Scholar]
- Sun, J.; Liu, R.; Paolini, E. Unrecovered Users Distribution in Coded Random Access Systems with Erasures. In Proceedings of the 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Schmetterer, L. An introduction to combinatorial analysis by J. Riordan. Phys. Today 1959, 12, 158. [Google Scholar]
| Distribution, | |
|---|---|
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, J.; Liu, R.; Paolini, E. A Dynamic Access Probability Adjustment Strategy for Coded Random Access Schemes. Sensors 2019, 19, 4206. https://doi.org/10.3390/s19194206
Sun J, Liu R, Paolini E. A Dynamic Access Probability Adjustment Strategy for Coded Random Access Schemes. Sensors. 2019; 19(19):4206. https://doi.org/10.3390/s19194206
Chicago/Turabian StyleSun, Jingyun, Rongke Liu, and Enrico Paolini. 2019. "A Dynamic Access Probability Adjustment Strategy for Coded Random Access Schemes" Sensors 19, no. 19: 4206. https://doi.org/10.3390/s19194206




