PRISER: Managing Notification in Multiples Devices with Data Privacy Support
Abstract
1. Introduction
2. Related Work
- Reference;
- Solution Name and Year;
- If the implementation makes use of the user’s location;
- Whether the implementation determines privacy preferences or implements actions to maintain private data;
- Compares whether the notification solution makes use of multiple devices, being more than one mobile device or another smart device;
- Informs whether the proposed solution is applied directly to the user’s mobile device through an application;
- Informs whether the solution uses human participation to verify the relevance and manual adjustments in the context of notification management.
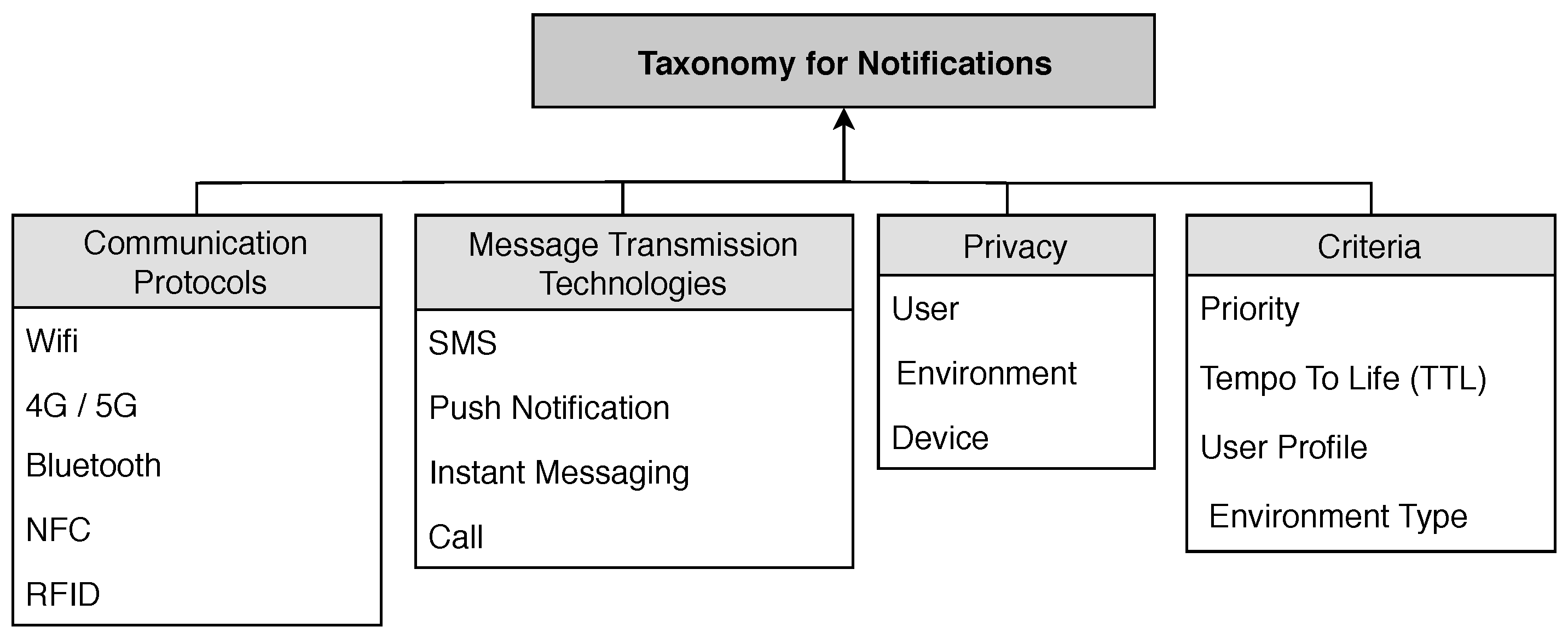
3. Taxonomy
3.1. Communication Protocols
- Wi-Fi: Widely-used wireless network technology with high bandwidth. Wi-Fi is still used to estimate location in relation to your access point in location-based-systems [37];
- Mobile Data (4G/5G): Mobile data 4G and in the future 5G;
- Bluetooth: It supports a lot of connected equipment, at a low range with an efficient energy management;
- NFC: Used for payments and short-distance communication, used for authentication in environments being an alternative to the use of traditional keys;
- RFID: It is used for short and long-range communications. Also for authenticating the location of a device or user and sending notifications to users in intelligent environments.
3.2. Message Transmission Technologies
- SMS: Short Message Service (SMS) is a service available in digital cellular phones that allows the sending of short messages (up to 160 characters) between these devices and between other ones that use the GSM interface;
- Push Notifications: Push notifications that appear in the foreground on users’ devices at random times, causing outages. Generally generated from previously-installed applications [16];
- Instant Messaging: Messages through applications, with the evolution of device programming, the number of applications for this purpose grows;
- Call: Phone-to-phone calls.
3.3. Privacy
- User: Defining the user as the center of custom alerts notification services, needing to have location contexts and well-defined individual information such as their preferences;
- Environment: The environment that the user accesses or requests access to, controlling privileges parameters in comparison to the profile;
- Device: Refers to the device that the user utilizes, from an M2M communication and using the connectivity standards defined in Section 3.1.
3.4. Criteria
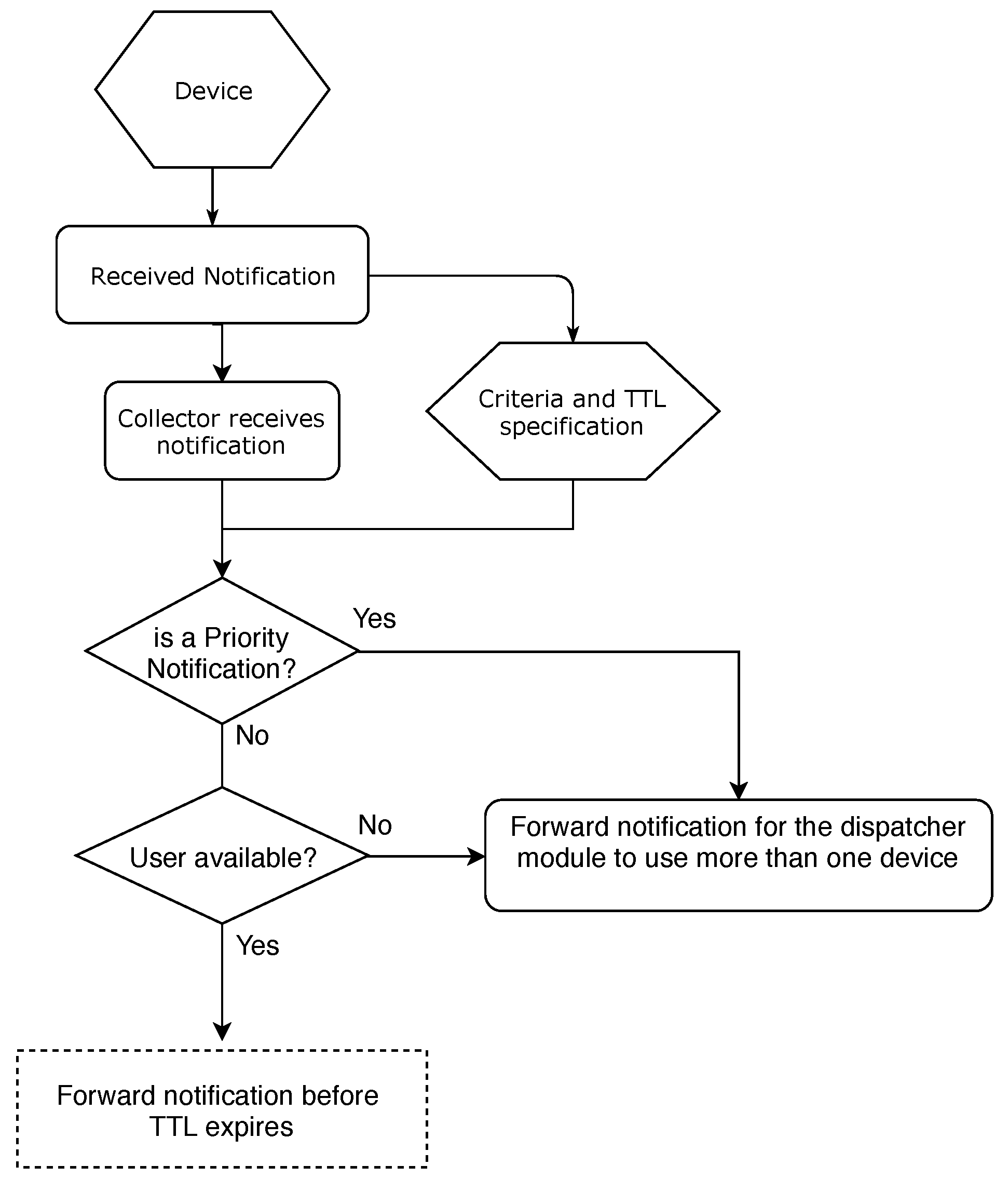
- Priority: The priority is directly related to the notification priority. An example of a high-priority notification would be a climate alert, which should reach the attention of the user, warning of a possible phenomenon;
- Time To Life (TTL): Time that a notification becomes inefficient since there is no time for delivery of it. A notification with a short lifetime and not sent with the proper priority loses its sense of notification. Likewise, it prevents the sending devices from carrying old messages for a long time [38];
- User Profile: Defines the limitations for each user. Reference [9] defined that for each environment a user profile type is assigned according to its location and attribution to the user. This environment is according to shift, day, week, month related;
- Environment Type: The parameter definitions used were based on environments with public, private and restricted location characteristics.
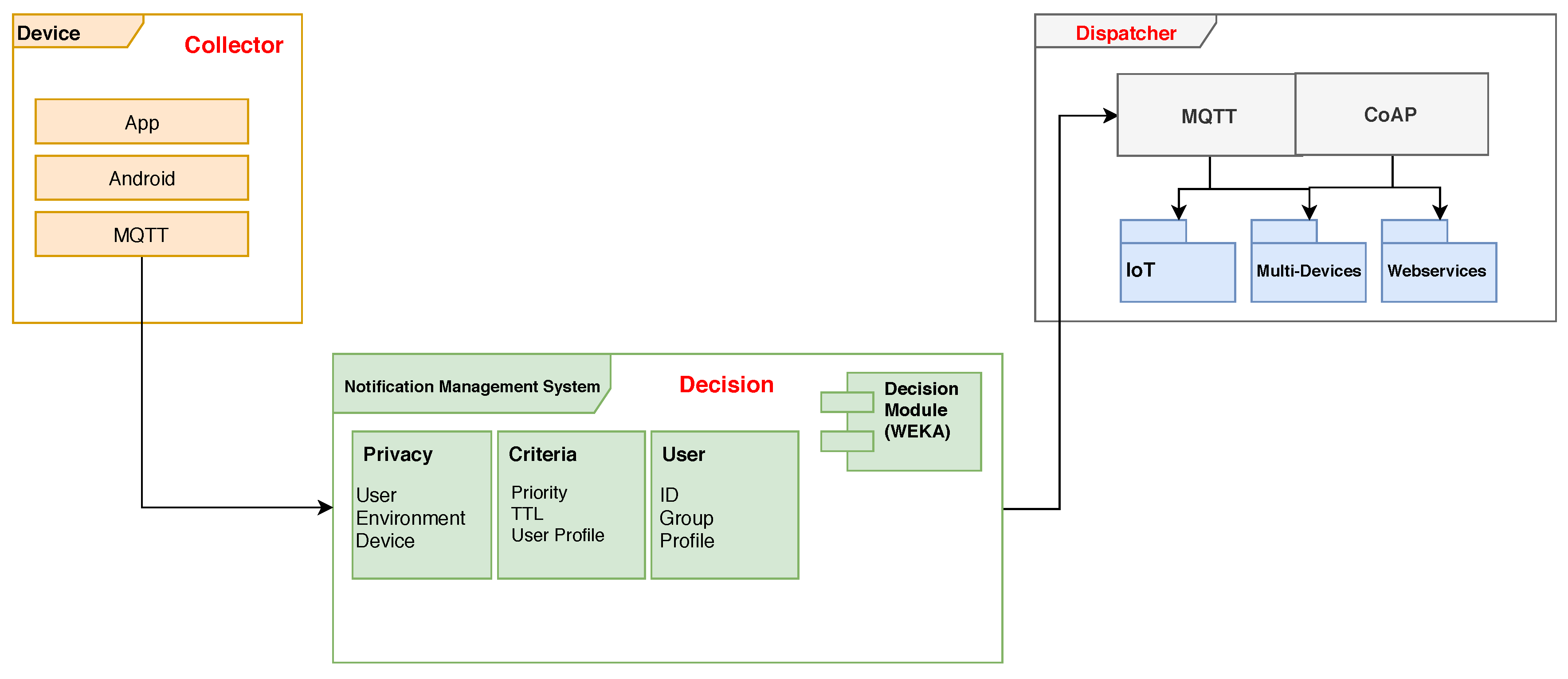
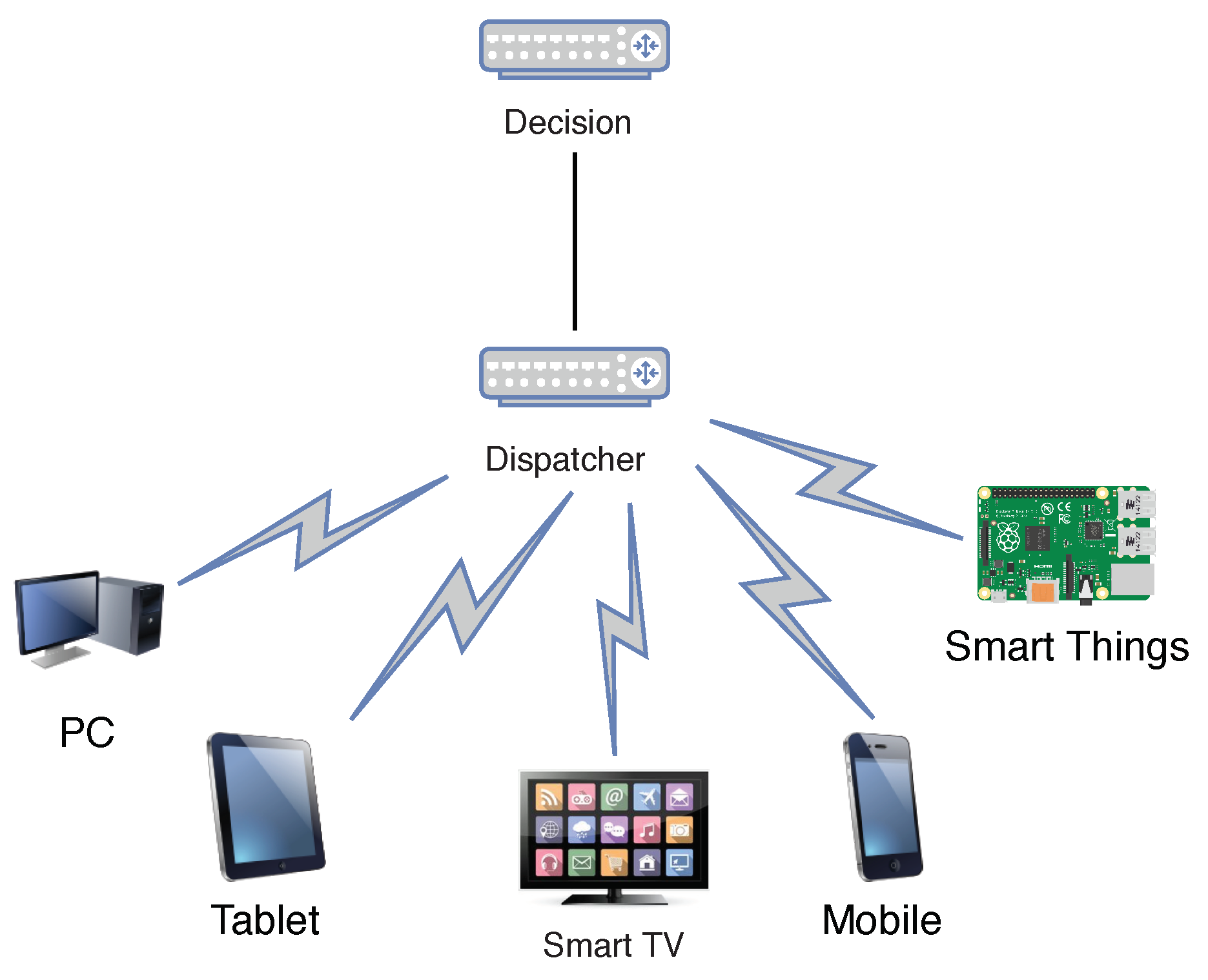
4. Priser
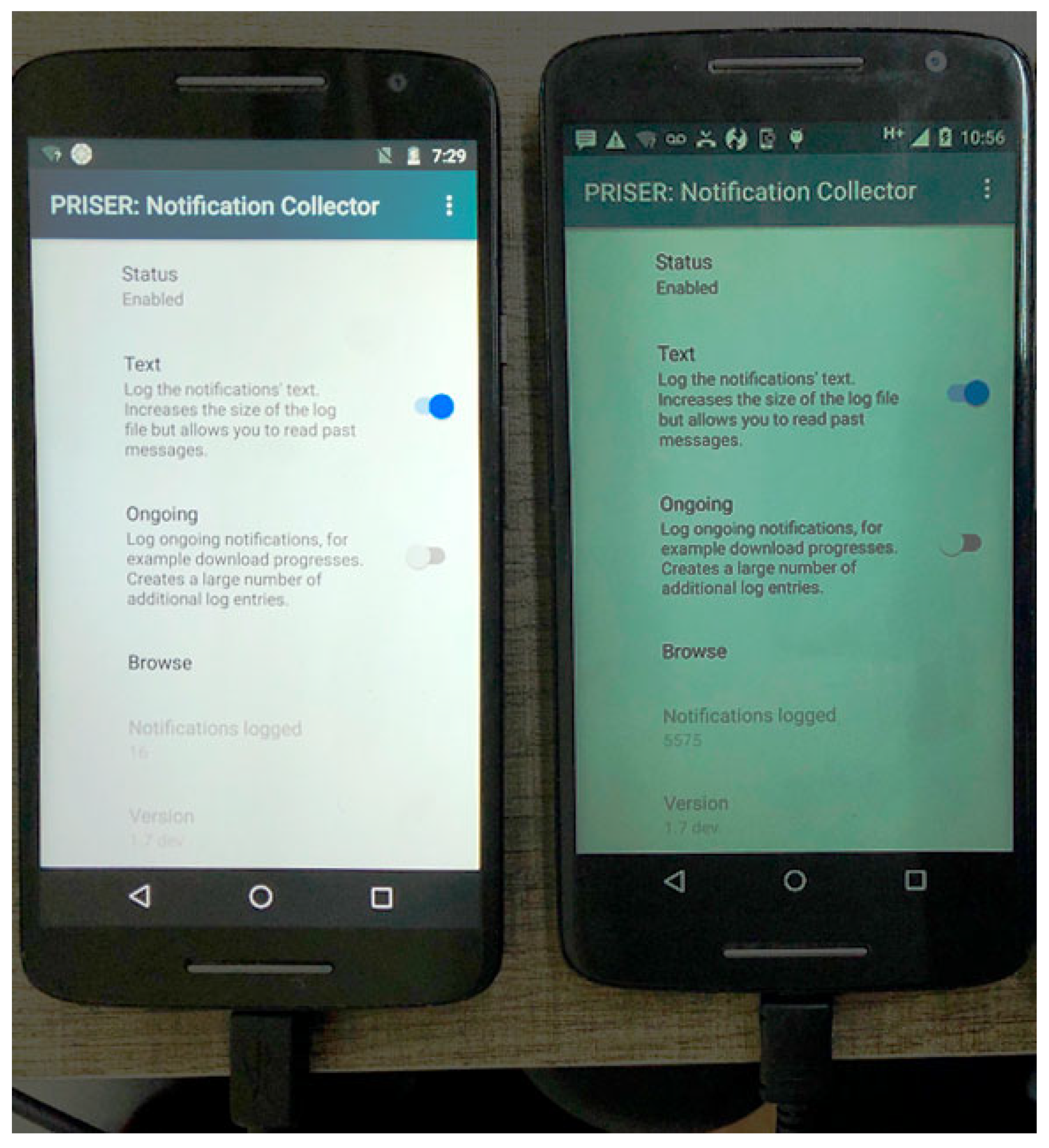
4.1. Notification Collector Module
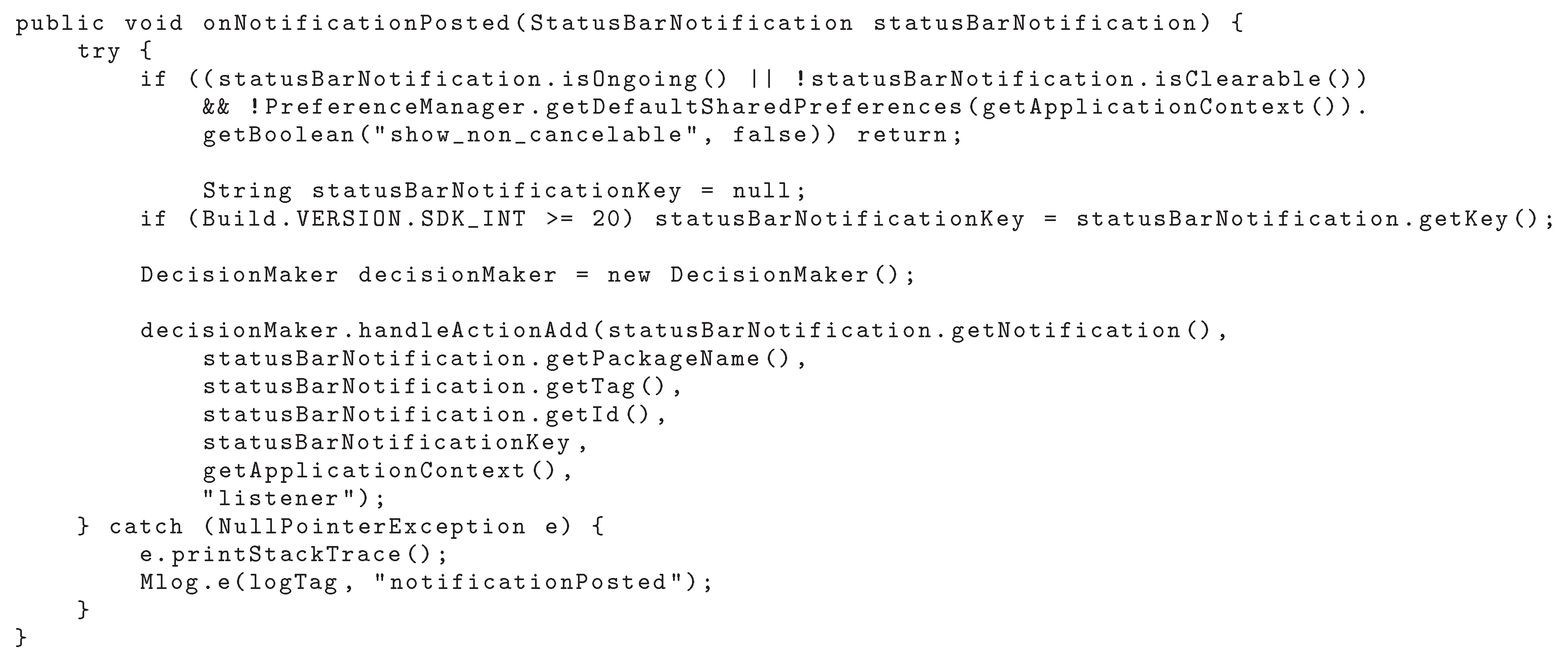
4.2. Decision Module
4.3. Dispatcher Module
4.4. Scenarios
- Access control In an access control scenario, the smart home system recognizes visitors at the doorway and sends a notification to the user. For this, it should be possible to adapt the system to the environment used. An immediate reaction is necessary, otherwise, visitors may assume that no one is at home. In an attempt to gain unauthorized access, the system user may request to be notified of any attempted improper entries;
- Environment control In the case of window control of an environment, it begins to rain while a window is open. To prevent damage to the interior of the residence, the system informs the user throught a notification. In this case, the urgency level is quite high and the user should react in the next few minutes;
- Medical Area The user must apply a medication every night. The intelligent house system detects from a schedule that it must be applied and informs the user through a notification. In this case, the user should react soon [57];
- IoT A clever vase detects that a plant needs to be watered and sends a notification. The level of urgency of this notification is quite low and you should react to it in the next few hours.
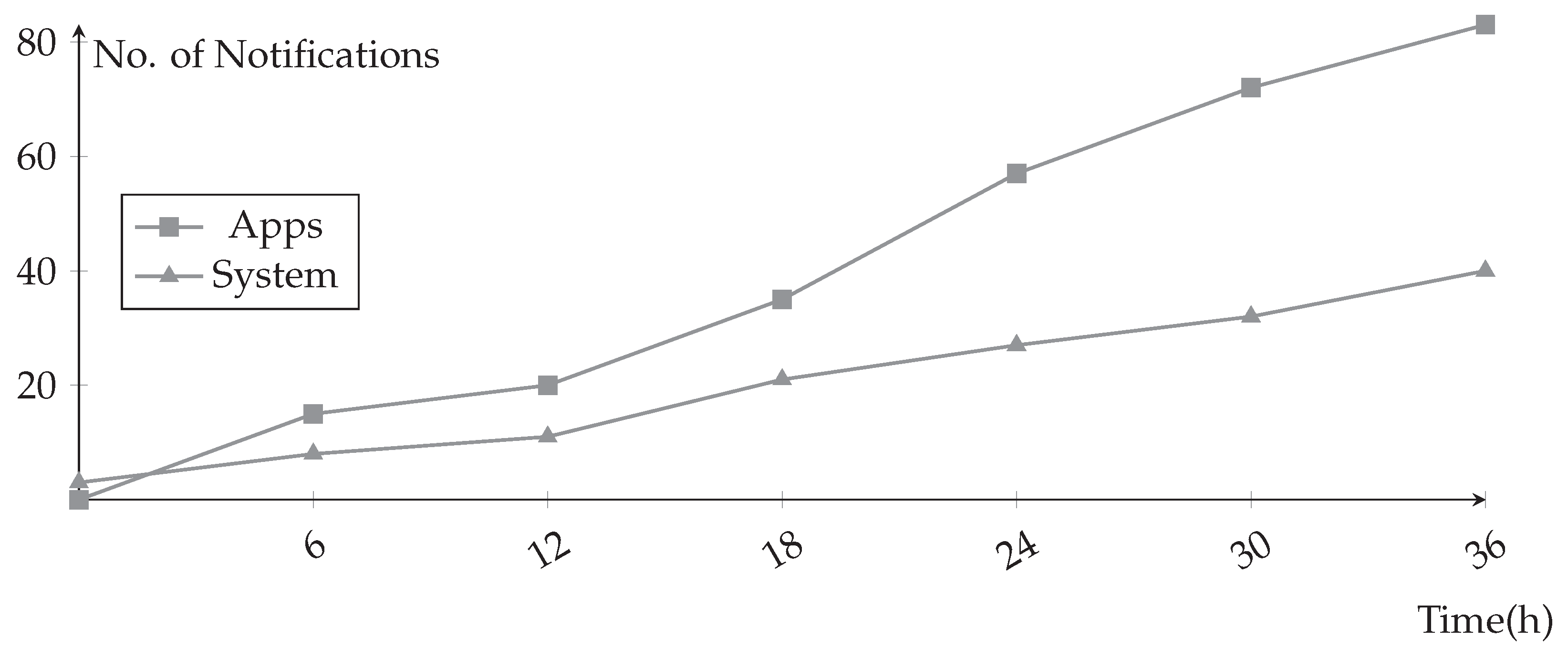
5. Prototype and Experimental Results
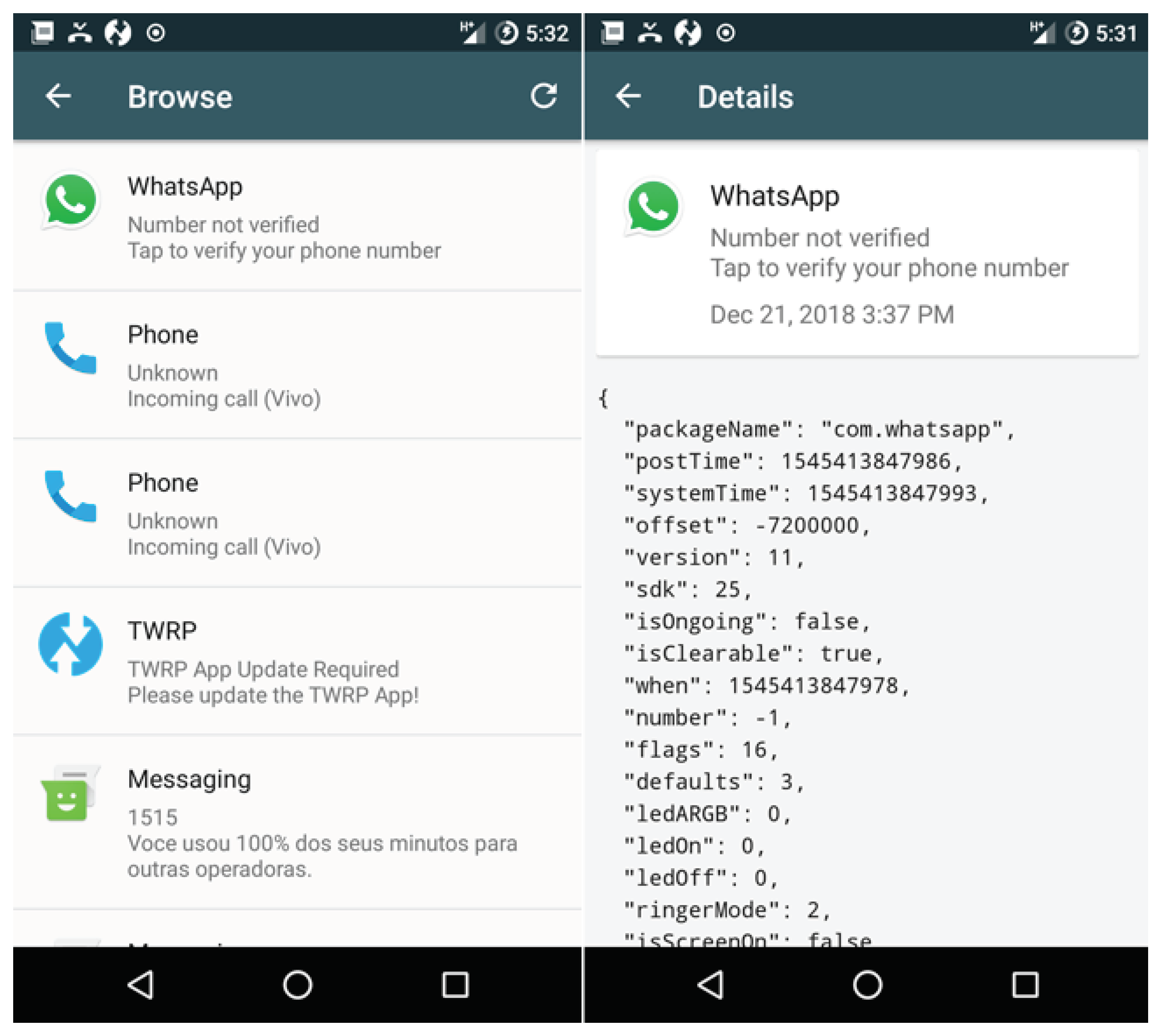
- Name of the event that originated the notification (email account, smart-thing (e.g., washing machine, SmartTV), WhatsApp, and individual users or groups);
- Event status regarding which type of notification is being sent (screen activated, screen off, and screen unlock);
- Action performed by the user (notification received, notification removed or still responded);
- Message content;
- Time and event data.
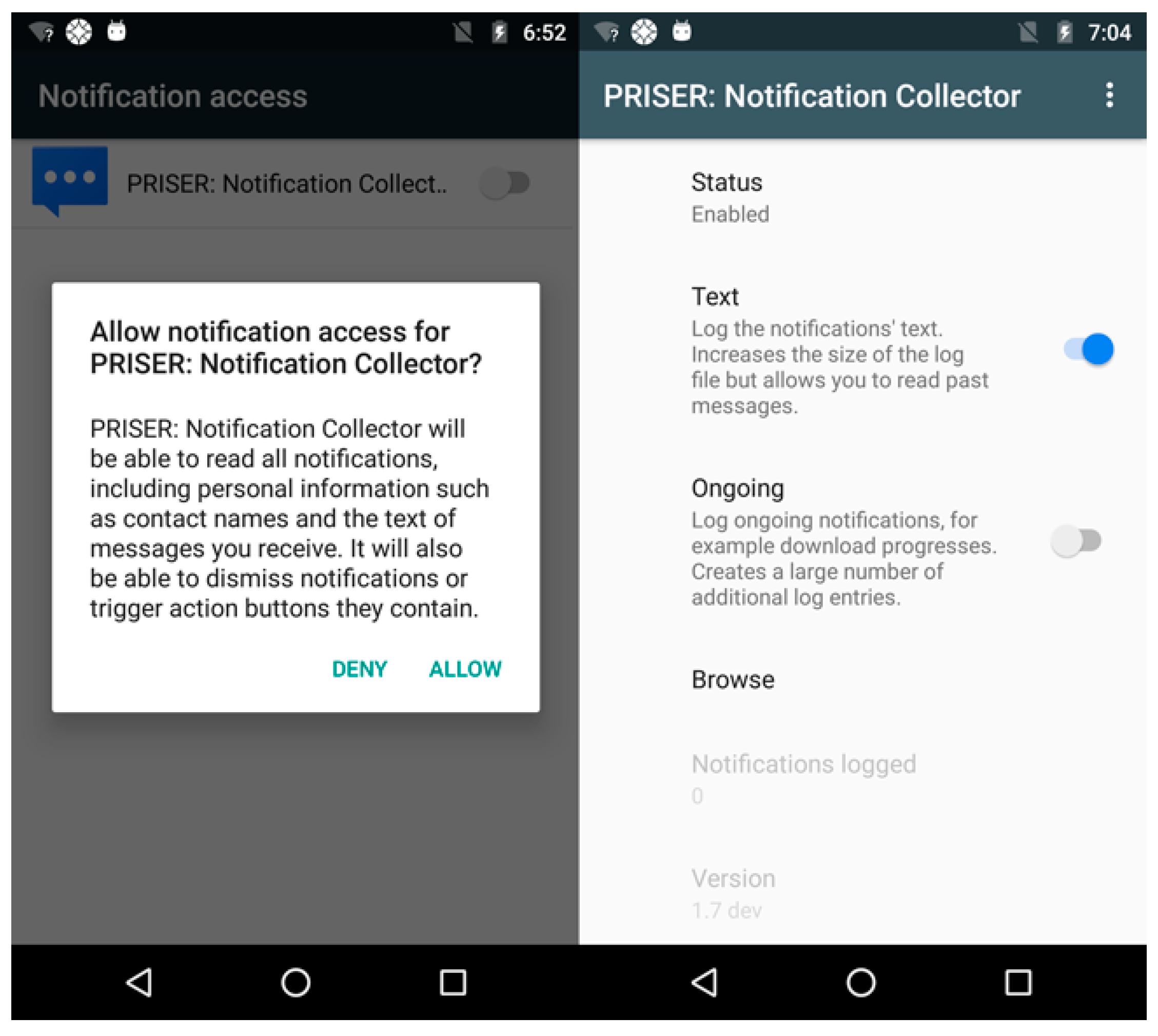
5.1. Collect and Share Method
5.2. Collect Notifications in Multiple Applications Scenario
5.3. Devices
- II Motorola Moto X Play (XT1563)
- CPU: Intel® Core i5 2.7 GHz
- RAM: 8 GB (1600 MHz)
6. Conclusions and Future Works
Author Contributions
Funding
Conflicts of Interest
References
- Goudos, S.K.; Dallas, P.I.; Chatziefthymiou, S.; Kyriazakos, S. A Survey of IoT Key Enabling and Future Technologies: 5G, Mobile IoT, Sematic Web and Applications. Wirel. Pers. Commun. 2017, 97, 1645–1675. [Google Scholar] [CrossRef]
- Elazhary, H. Internet of Things (IoT), mobile cloud, cloudlet, mobile IoT, IoT cloud, fog, mobile edge, and edge emerging computing paradigms: Disambiguation and research directions. J. Netw. Comput. Appl. 2019, 128, 105–140. [Google Scholar] [CrossRef]
- Viel, F.; Silva, L.A.; Leithardt, V.R.Q.; Zeferino, C. Internet of Things: Concepts, Architectures and Technologies. In Proceedings of the 2018 13th IEEE International Conference on Industry Applications (INDUSCON), São Paulo, Brazil, 12–14 November 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Arasteh, H.; Hosseinnezhad, V.; Loia, V.; Tommasetti, A.; Troisi, O.; Shafie-khah, M.; Siano, P. Iot-based smart cities: A survey. In Proceedings of the 2016 IEEE 16th International Conference on Environment and Electrical Engineering (EEEIC), Florence, Italy, 7–10 June 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Thakare, S.; Shriyan, A.; Thale, V.; Yasarp, P.; Unni, K. Implementation of an energy monitoring and control device based on IoT. In Proceedings of the 2016 IEEE Annual India Conference (INDICON), Bangalore, India, 16–18 December 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Ahlgren, B.; Hidell, M.; Ngai, E.C.H. Internet of Things for Smart Cities: Interoperability and Open Data. IEEE Int. Comput. 2016, 20, 52–56. [Google Scholar] [CrossRef]
- Mehrotra, A.; Pejovic, V.; Vermeulen, J.; Hendley, R.; Musolesi, M. My phone and me: Understanding people’s receptivity to mobile notifications. In Proceedings of the 2016 CHI Conference on Human Factors in Computing Systems, San Jose, CA, USA, 7–12 May 2016; pp. 1021–1032. [Google Scholar] [CrossRef]
- Weber, D. Towards smart notification management in multi-device environments. In Proceedings of the 19th International Conference on Human-Computer Interaction with Mobile Devices and Services, Vienna, Austria, 4–7 September 2017; p. 68. [Google Scholar] [CrossRef]
- Leithardt, V.; Rolim, C.; Rossetto, A.; Borges, G.; SáSilva, J.; Geyer, C. The classification of algorithms for Privacy Management in Ubiquitous Environments. In Proceedings of the 8º SBCUP-Simpósio Brasileiro de Computação Ubíqua e Pervasiva-XXXVI CSBC-Congresso da Sociedade Brasileira de Computação, Porto Alegre-RS, 6 July 2016. [Google Scholar]
- Begole, J.B.; Matsakis, N.E.; Tang, J.C. Lilsys: Sensing unavailability. In Proceedings of the 2004 ACM Conference on Computer Supported Cooperative Work, Chicago, IL, USA, 6–10 November 2006; Volume 6, pp. 511–514. [Google Scholar] [CrossRef]
- Horvitz, E.; Koch, P.; Apacible, J. BusyBody: Creating and fielding personalized models of the cost of interruption. In Proceedings of the 2004 ACM Conference on Computer Supported Cooperative Work, Chicago, IL, USA, 6–10 November 2004; Volume 6, p. 507. [Google Scholar] [CrossRef]
- Qin, Y.; Bhattacharya, T.; Kulik, L.; Bailey, J. A context-aware do-not-disturb service for mobile devices. In Proceedings of the 13th International Conference on Mobile and Ubiquitous Multimedia, Melbourne, Australia, 25–28 November 2014; pp. 236–239. [Google Scholar] [CrossRef]
- Bidargaddi, N.; Pituch, T.; Maaieh, H.; Short, C.; Strecher, V. Predicting which type of push notification content motivates users to engage in a self-monitoring app. Prevent. Med. Rep. 2018, 11, 267–273. [Google Scholar] [CrossRef] [PubMed]
- Gudla, S.K.; Bose, J. Intelligent Web Push Architecture with Push Flow Control and Push Continuity. In Proceedings of the 2016 IEEE International Conference on Web Services (ICWS), San Francisco, CA, USA, 27 June–2 July 2016; pp. 658–661. [Google Scholar] [CrossRef]
- Cho, C.; Kim, J.; Joo, Y.; Shin, J. An approach for CoAP based notification service in IoT environment. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 19–21 October 2016; pp. 440–445. [Google Scholar] [CrossRef]
- Okoshi, T.; Tsubouchi, K.; Taji, M.; Ichikawa, T.; Tokuda, H. Attention and engagement-awareness in the wild: A large-scale study with adaptive notifications. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications (PerCom), Kona, HI, USA, 13–17 March 2017; pp. 100–110. [Google Scholar] [CrossRef]
- Google — Android API Guide. Available online: https://developer.android.com (accessed on 30 November 2018).
- Pryss, R.; Geiger, P.; Schickler, M.; Schobel, J.; Reichert, M. The AREA Framework for Location-Based Smart Mobile Augmented Reality Applications. Int. J. Ubiquitous Syst. Pervasive Netw. (JUSPN) 2017, 9, 13–21. [Google Scholar] [CrossRef]
- Li, L.; Katangur, A.K.; Karuturi, N.N. SmartNotify: An Intelligent Location Based Notification System Using Users’ Activities and Points of Interests. Int. J. Adv. Pervasive Ubiquitous Comput. (IJAPUC) 2018, 10, 37–50. [Google Scholar] [CrossRef]
- Sahni, Y.; Cao, J.; Shen, J. Challenges and Opportunities in Designing Smart Spaces. In Internet of Everything; Springer: Cham, Switzerland, 2018; pp. 131–152. [Google Scholar]
- Ahmed, E.; Yaqoob, I.; Gani, A.; Imran, M.; Guizani, M. Internet-of-things-based smart environments: State of the art, taxonomy, and open research challenges. IEEE Wirel. Commun. 2016, 23, 10–16. [Google Scholar] [CrossRef]
- Tilak, S.; Abu-Ghazaleh, N.B.; Heinzelman, W. A taxonomy of wireless micro-sensor network models. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2002, 6, 28–36. [Google Scholar] [CrossRef]
- Tory, M.; Moller, T. Rethinking visualization: A high-level taxonomy. In Proceedings of the IEEE Symposium on Information Visualization, Austin, TX, USA, 10–12 October 2004; pp. 151–158. [Google Scholar] [CrossRef]
- Heurix, J.; Zimmermann, P.; Neubauer, T.; Fenz, S. A taxonomy for privacy enhancing technologies. Comput. Secur. 2015, 53, 1–17. [Google Scholar] [CrossRef]
- Kubitza, T.; Voit, A.; Weber, D.; Schmidt, A. An IoT infrastructure for ubiquitous notifications in intelligent living environments. In Proceedings of the 2016 ACM International Joint Conference on Pervasive and Ubiquitous Computing Adjunct-UbiComp’16, Heidelberg, Germany, 12–16 September 2016; pp. 1536–1541. [Google Scholar] [CrossRef]
- Naik, A.; Shahnasser, H. A Taxonomy on Accountability and Privacy Issues in Smart Grids. In IOP Conference Series: Earth and Environmental Science; IOP Publishing: Bristol, UK, 2017; Volume 73. [Google Scholar]
- Okoshi, T.; Nakazawa, J.; Tokuda, H. Attelia: Sensing User’s Attention Status on Smart Phones. In Proceedings of the 2014 ACM International Joint Conference on Pervasive and Ubiquitous Computing: Adjunct Publication, Seattle, WA, USA, 13–17 September 2014; pp. 139–142. [Google Scholar] [CrossRef]
- Pielot, M.; de Oliveira, R.; Kwak, H.; Oliver, N. Didn’T You See My Message?: Predicting Attentiveness to Mobile Instant Messages. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Toronto, ON, Canada, 26 April–1 May 2014; pp. 3319–3328. [Google Scholar] [CrossRef]
- Liu, S.; Jiang, Y.; Striegel, A. Face-to-face proximity estimationusing bluetooth on smartphones. IEEE Trans. Mob. Comput. 2014, 13, 811–823. [Google Scholar] [CrossRef]
- Sahami Shirazi, A.; Henze, N.; Dingler, T.; Pielot, M.; Weber, D.; Schmidt, A. Large-scale Assessment of Mobile Notifications. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Toronto, ON, Canada, 26 April–1 May 2014; pp. 3055–3064. [Google Scholar] [CrossRef]
- Pan, Z.; Liang, X.; Zhou, Y.C.; Ge, Y.; Zhao, G.T. Intelligent Push Notification for Converged Mobile Computing and Internet of Things. In Proceedings of the 2015 IEEE International Conference on Web Services, New York, NY, USA, 27 June–2 July 2015; pp. 655–662. [Google Scholar] [CrossRef]
- Corno, F.; Russis, L.D.; Montanaro, T. A context and user aware smart notification system. In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 645–651. [Google Scholar]
- Fraser, K.; Yousuf, B.; Conlan, O. A context-aware, info-bead and fuzzy inference approach to notification management. In Proceedings of the 2016 IEEE 7th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 20–22 October 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Zhang, S.; Choo, K.K.R.; Liu, Q.; Wang, G. Enhancing Privacy through Uniform Grid and Caching in Location-Based Services; Elsevier: Amsterdam, The Netherlands, 2017. [Google Scholar]
- Weber, D.; Voit, A.; Henze, N. Notification Log: An Open-Source Framework for Notification Research on Mobile Devices. In Proceedings of the 2018 ACM International Joint Conference and 2018 International Symposium on Pervasive and Ubiquitous Computing and Wearable Computers, Singapore, 8–12 October 2018; pp. 1271–1278. [Google Scholar] [CrossRef]
- Resmini, A.; Rosati, L. Pervasive Information Architecture: Designing Cross-Channel User Experiences, 1st ed.; Morgan Kaufmann Publishers Inc.: San Francisco, CA, USA, 2011. [Google Scholar]
- He, S.; Chan, S.H.G. Wi-Fi fingerprint-based indoor positioning: Recent advances and comparisons. IEEE Commun. Surv. Tutor. 2016, 18, 466–490. [Google Scholar] [CrossRef]
- Rolim, C.; Rossetto, A.; Leithardt, V.; Borges, G.; Geyer, C.; dos Santos, T.; Souza, A. Situation awareness and computational intelligence in opportunistic networks to support the data transmission of urban sensing applications. Comput. Netw. 2016, 111, 55–70. [Google Scholar] [CrossRef]
- Aloi, G.; Caliciuri, G.; Fortino, G.; Gravina, R.; Pace, P.; Russo, W.; Savaglio, C. Enabling IoT interoperability through opportunistic smartphone-based mobile gateways. J. Netw. Comput. Appl. 2017, 81, 74–84. [Google Scholar] [CrossRef]
- Church, K.; de Oliveira, R. What’s up with whatsapp?: Comparing mobile instant messaging behaviors with traditional SMS. In Proceedings of the 15th International Conference on Human-Computer Interaction with Mobile Devices and Services, Munich, Germany, 27–30 August 2013; pp. 352–361. [Google Scholar] [CrossRef]
- Warren, I.; Meads, A.; Srirama, S.; Weerasinghe, T.; Paniagua, C. Push notification mechanisms for pervasive smartphone applications. IEEE Pervasive Comput. 2014, 13, 61–71. [Google Scholar] [CrossRef]
- Rusu, D.; Vert, S. City Alerts: Smart City Notification Platform Based on Public Open Data. Sci. Bull. Politech. Univ. Timisoara Trans. Electron. Commun. 2014, 59, 21–26. [Google Scholar]
- Acer, U.; Mashhadi, A.; Forlivesi, C.; Kawsar, F. Energy Efficient Scheduling for Mobile Push Notifications. In Proceedings of the 12th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, Coimbra, Portugal, 22–24 July 2015. [Google Scholar] [CrossRef]
- Zhang, J. Emergency Notification on Mobile Devices-Concern and Personalised Notification. Ph.D. Thesis, University of Canterbury, Christchurch, New Zealand, 2017. [Google Scholar]
- Künzler, F.; Kramer, J.N.; Kowatsch, T. Efficacy of mobile context-aware notification management systems: A systematic literature review and meta-analysis. In Proceedings of the 2017 IEEE 13th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Rome, Italy, 9–11 October 2017; pp. 131–138. [Google Scholar] [CrossRef]
- Trihinas, D.; Pallis, G.; Dikaiakos, M.D. ADMin: Adaptive monitoring dissemination for the Internet of Things. In Proceedings of the IEEE INFOCOM 2017—IEEE Conference on Computer Communications, Atlanta, GA, USA, 14 May 2017; pp. 1–9. [Google Scholar] [CrossRef]
- Wei, E.J.; Chan, A.T. CAMPUS: A middleware for automated context-aware adaptation decision making at run time. Pervasive Mob. Comput. 2013, 9, 35–56. [Google Scholar] [CrossRef]
- Faragher, R.; Harle, R. Location fingerprinting with bluetooth low energy beacons. IEEE J. Sel. Areas Commun. 2015, 33, 2418–2428. [Google Scholar] [CrossRef]
- Bai, S.Y.; Chiu, C.C.; Hsu, J.C.; Leu, J.S. Campus-wide wireless indoor positioning with hybrid iBeacon and Wi-Fi system. In Proceedings of the 2017 6th International Symposium on Next Generation Electronics (ISNE), Keelung, Taiwan, 23–25 May 2017; pp. 1–2. [Google Scholar] [CrossRef]
- Solove, D.J. A Taxonomy of Privacy. Univ. Pa. Law Rev. 2006, 86, 457–470. [Google Scholar] [CrossRef]
- Eckhoff, D.; Wagner, I. Privacyp in the Smart City; Applications, Technologies, Challenges and Solutions. IEEE Commun. Surv. Tutor. 2017, 20, 489–516. [Google Scholar] [CrossRef]
- Langheinrich, M.; Schaub, F. Privacy in Mobile and Pervasive Computing. Synth. Lect. Mob. Pervasive Comput. 2018, 10, 1–139. [Google Scholar] [CrossRef]
- de Araujo, J.P.; Arantes, L.; Duarte, E.P.; Rodrigues, L.A.; Sens, P. VCube-PS: A causal broadcast topic-based publish/subscribe system. J. Parallel Distrib. Comput. 2019, 125, 18–30. [Google Scholar] [CrossRef]
- MÜller, H.; Kazakova, A.; Heuten, W.; Boll, S. Supporting Efficient Task Switching in a Work Environment with a Pervasive Display. In Proceedings of the 5th ACM International Symposium on Pervasive Displays, Oulu, Finland, 20–26 June 2016; pp. 13–19. [Google Scholar] [CrossRef]
- Altosaar, M.; Vertegaal, R.; Sohn, C.; Cheng, D. AuraOrb: Social Notification Appliance. In Proceedings of the CHI’06 Extended Abstracts on Human Factors in Computing Systems, Montréal, QC, Canada, 22–27 April 2006; pp. 381–386. [Google Scholar] [CrossRef]
- Weber, D.; Mayer, S.; Voit, A.; Ventura Fierro, R.; Henze, N. Design Guidelines for Notifications on Smart TVs. In Proceedings of the ACM International Conference on Interactive Experiences for TV and Online Video, Chicago, IL, USA, 22–24 June 2016; pp. 13–24. [Google Scholar] [CrossRef]
- Santos, J.; Rodrigues, J.J.; Silva, B.M.; Casal, J.; Saleem, K.; Denisov, V. An IoT-based mobile gateway for intelligent personal assistants on mobile health environments. J. Netw. Comput. Appl. 2016, 71, 194–204. [Google Scholar] [CrossRef]


| Work | Solution | User Location | Privacy | Multiple Devices | User App | Human Intervention |
|---|---|---|---|---|---|---|
| [27] | Attelia (2014) | X | X | |||
| [28] | Message Monitor (2014) | X | X | X | X | |
| [29] | Face-to-Face (2014) | X | X | X | ||
| [30] | Desktop Notifications (2014) | X | X | X | X | |
| [31] | Intelligent Push (2015) | X | X | |||
| [32] | Notification Collector (2015) | X | X | X | ||
| [33] | NAbsMobile (2016) | X | X | X | X | |
| [34] | No name (2017) | X | X | X | ||
| [19] | Smartnotify (2018) | X | X | |||
| [35] | Notification Log (2018) | X | X | X | X | |
| This Work | PRISER (2019) | X | X | X | X |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Silva, L.A.; Leithardt, V.R.Q.; Rolim, C.O.; González, G.V.; Geyer, C.F.R.; Silva, J.S. PRISER: Managing Notification in Multiples Devices with Data Privacy Support. Sensors 2019, 19, 3098. https://doi.org/10.3390/s19143098
Silva LA, Leithardt VRQ, Rolim CO, González GV, Geyer CFR, Silva JS. PRISER: Managing Notification in Multiples Devices with Data Privacy Support. Sensors. 2019; 19(14):3098. https://doi.org/10.3390/s19143098
Chicago/Turabian StyleSilva, Luis Augusto, Valderi Reis Quietinho Leithardt, Carlos O. Rolim, Gabriel Villarrubia González, Cláudio F. R. Geyer, and Jorge Sá Silva. 2019. "PRISER: Managing Notification in Multiples Devices with Data Privacy Support" Sensors 19, no. 14: 3098. https://doi.org/10.3390/s19143098
APA StyleSilva, L. A., Leithardt, V. R. Q., Rolim, C. O., González, G. V., Geyer, C. F. R., & Silva, J. S. (2019). PRISER: Managing Notification in Multiples Devices with Data Privacy Support. Sensors, 19(14), 3098. https://doi.org/10.3390/s19143098









