Identity-Based Encryption with Filtered Equality Test for Smart City Applications
Abstract
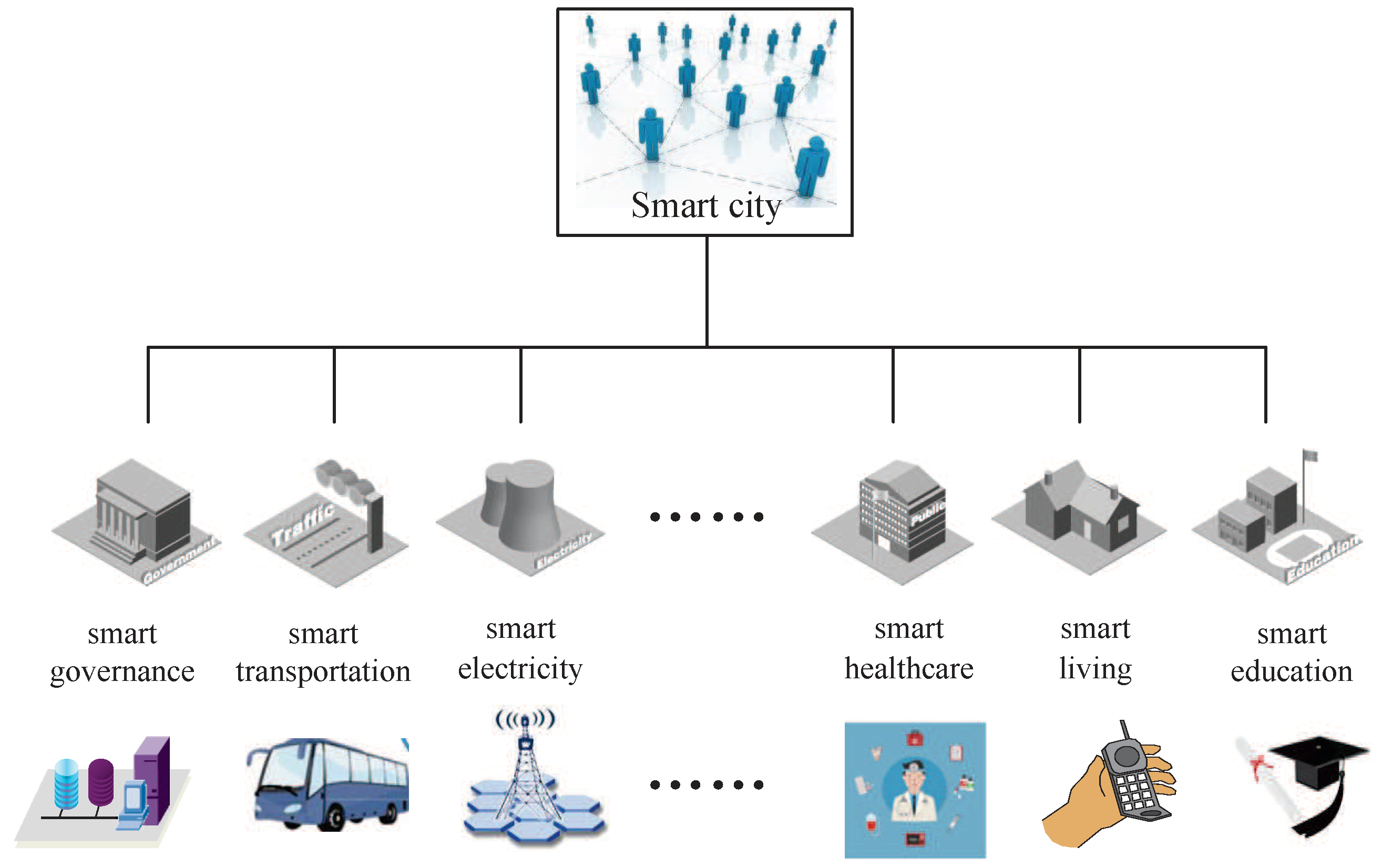
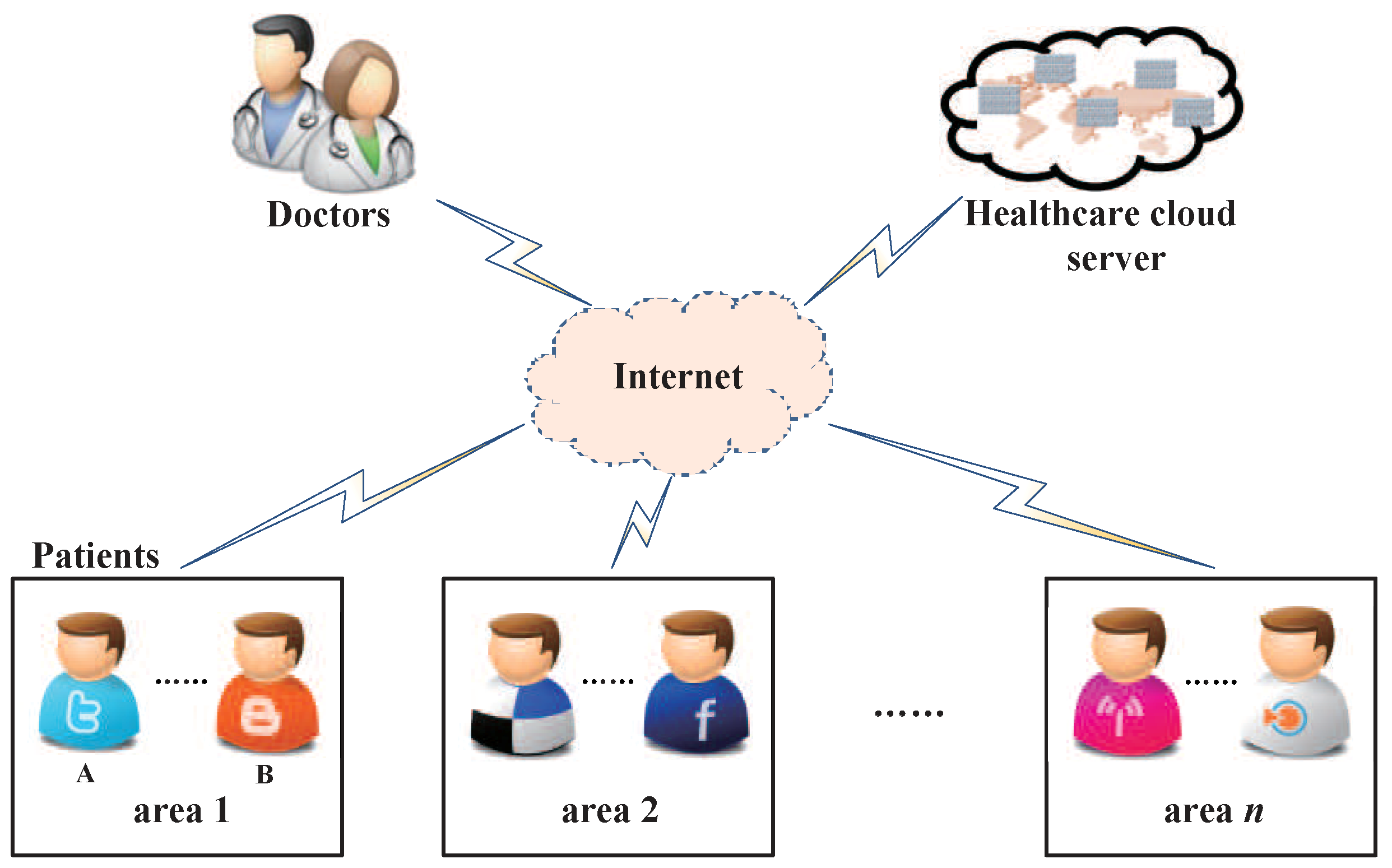
1. Introduction
1.1. Our Contributions
- Based on secret sharing and bilinear pairing, an IBE-FET scheme is proposed, which does not use the certificate verification to solve the problems of certificate management.
- The security analysis indicates that the IBE-FET scheme is one-way secure against the chosen identity and ciphertext attack (OW-ID-CCA) based on the computational bilinear Diffie-Hellman assumption in the random oracle model.
- The performance analysis shows that the IBE-FET scheme achieves the function of a filtered equality test and a higher efficiency in terms of communication cost than the related scheme [39], and therefore the proposed scheme is more suitable for smart healthcare systems.
1.2. Organization
2. Related Works
3. Preliminaries
3.1. Bilinear Pairing
- Bilinearity: For all and , where .
- Non-degeneracy: .
- Computability: It is an efficient algorithm to compute for all .
3.2. Secret Sharing
3.3. Assumption
4. Framework of IBE-FET
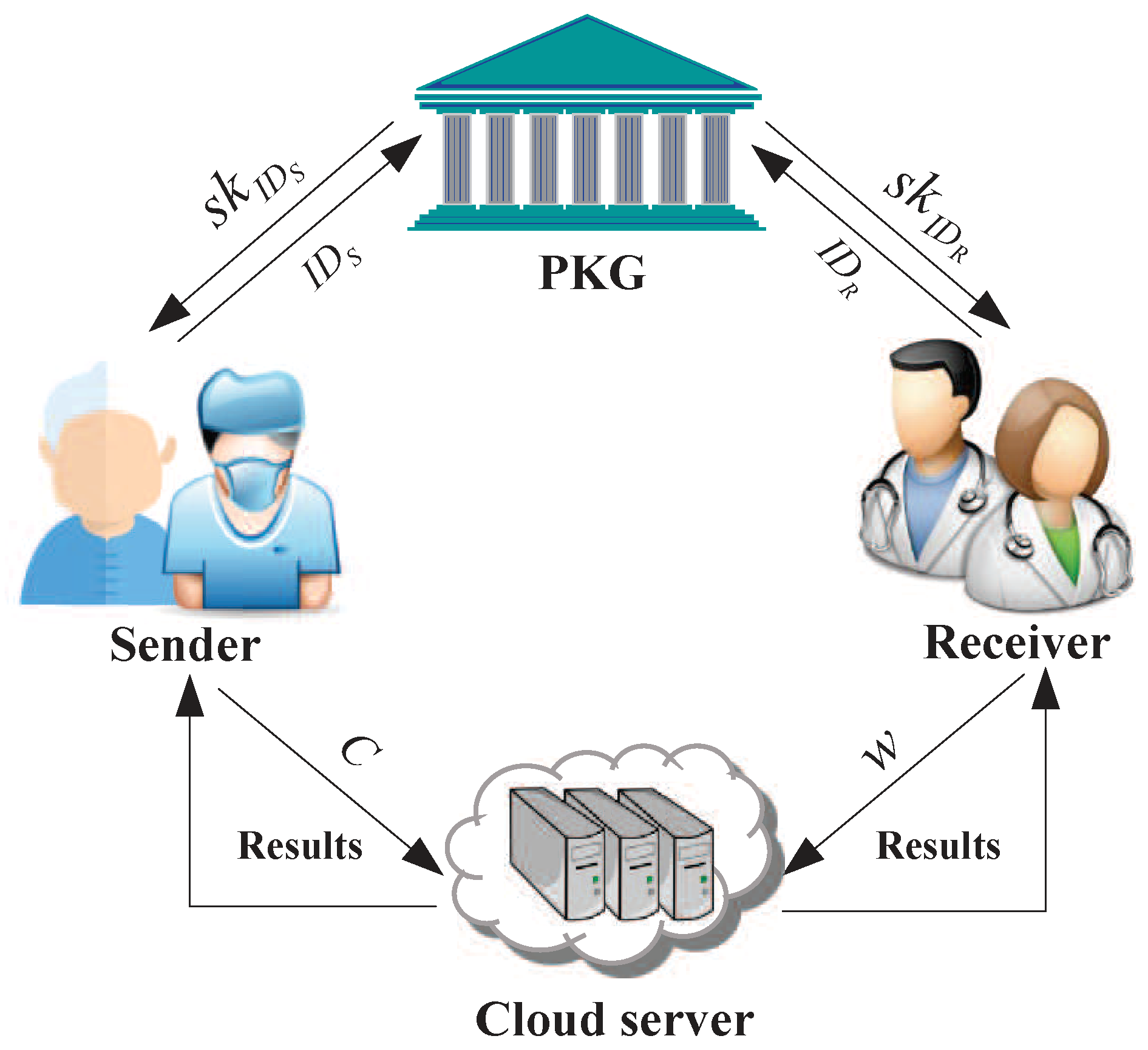
4.1. System Model
- PKG: It is responsible for generating the master key and the private key , and then keeps by itself and sends to the sender and receiver through a secure way.
- Sender (patient): The sender encrypts their private date under the receiver’s identity to generate the ciphertext C and stores it in the cloud server.
- Receiver (doctor): Upon receiving the private key from PKG, the receiver generates the warrant w and sends it to the cloud server. It is noted that the receiver can use the private key to decrypt the ciphertext at any time.
- Cloud server: With the warrant, the cloud server is in charge of executing the filtered equality test and returns a query result.
4.2. Syntax
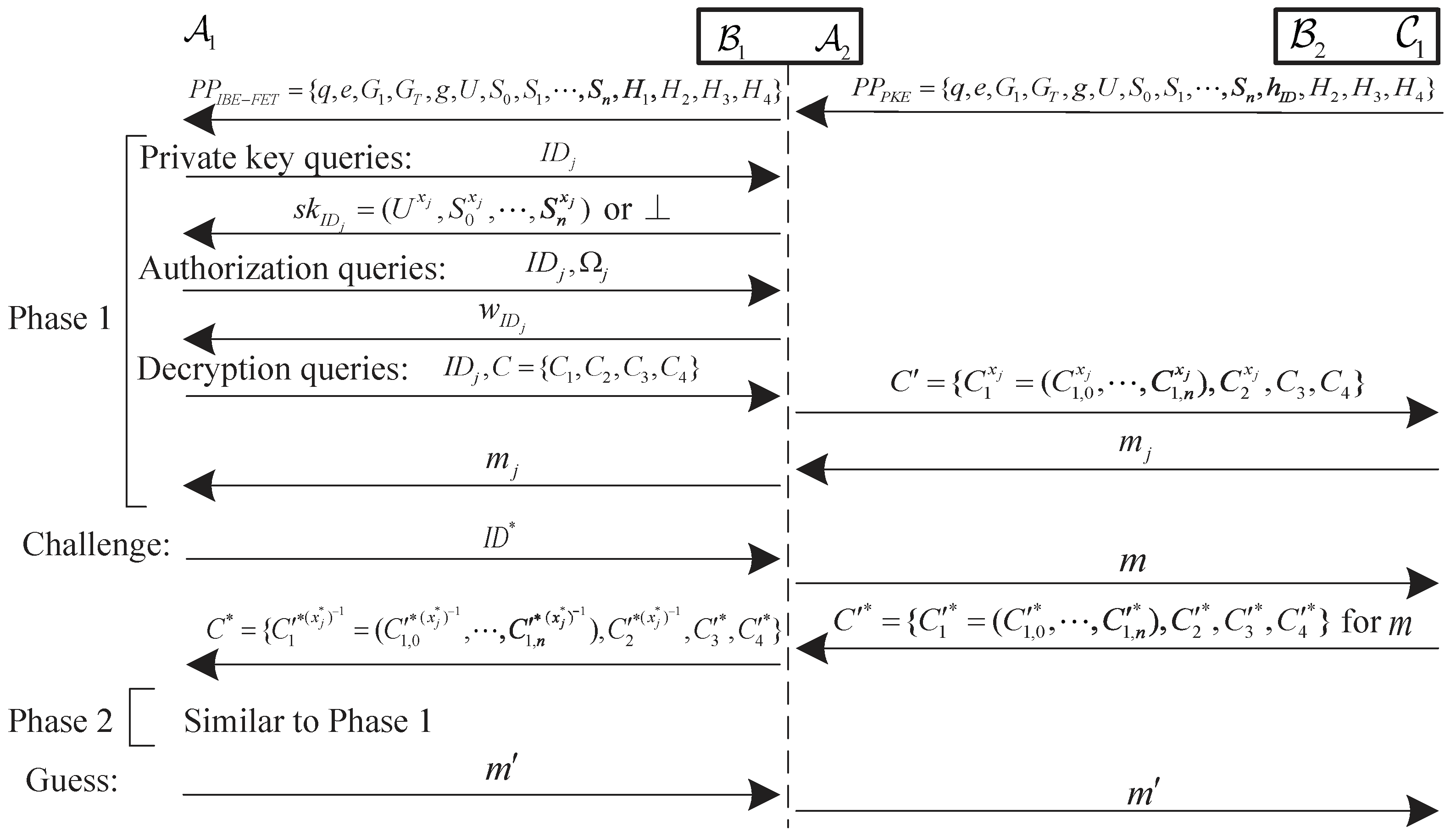
4.3. Security Model
- Hash H queries: submits a query, then returns a random value to .
- Private key queries: submits the identity to , then runs the Extract algorithm and returns the private key to .
- Decryption queries: submits the identity and the ciphertext to , then runs the Extract algorithm to obtain and runs the Decrypt algorithm to return the plaintext to .
- Authorization queries: submits the identity and the message set to , then runs the Extract algorithm to obtain and runs the Authorization algorithm to return the warrant to .
- Hash H queries: responds as in Phase 1.
- Private key queries: If , responds as in Phase 1. Otherwise, returns ⊥.
- Decryption queries: If , responds as in Phase 1. Otherwise, returns ⊥.
- Authorization queries: responds as in Phase 1.
- Hash H queries: submits a query, then returns a random value to .
- Decryption queries: submits the ciphertext to , then runs the Decrypt algorithm and returns the plaintext to .
- Hash H queries: responds as in Phase 1.
- Decryption queries: If , responds as in Phase 1. Otherwise, returns ⊥.
5. The Proposed Scheme
- Setup: Given a security parameter k, the PKG executes as follows:
- (1)
- Chooses a bilinear pairing: , where and are two cyclic groups with prime order q, g is a generator of .
- (2)
- Randomly picks and computes , , , , .
- (3)
- Chooses four one-way hash functions , , , , where is the length of the message and is the length of .
The system parameters are and the master key are . - Extract: Given the identity and the master key , PKG computes and the private key .
- Encrypt: Given the message m and the identity , the sender executes as follows:
- (1)
- Randomly chooses .
- (2)
- Computes , , ,,,,.
The ciphertext is , where . - Decrypt: Given the ciphertext C and the private key , the receiver executes as follows:
- (1)
- Computes and .
- (2)
- Verifiesfor all . If holds, it outputs m. Otherwise, it outputs ⊥.
- Authorization: Given the message set and the private key , the receiver performs the following steps:
- (1)
- Computes a n-degree polynomial function and obtains the coefficient .
- (2)
- Computes for all and sends the warrant to the cloud server.
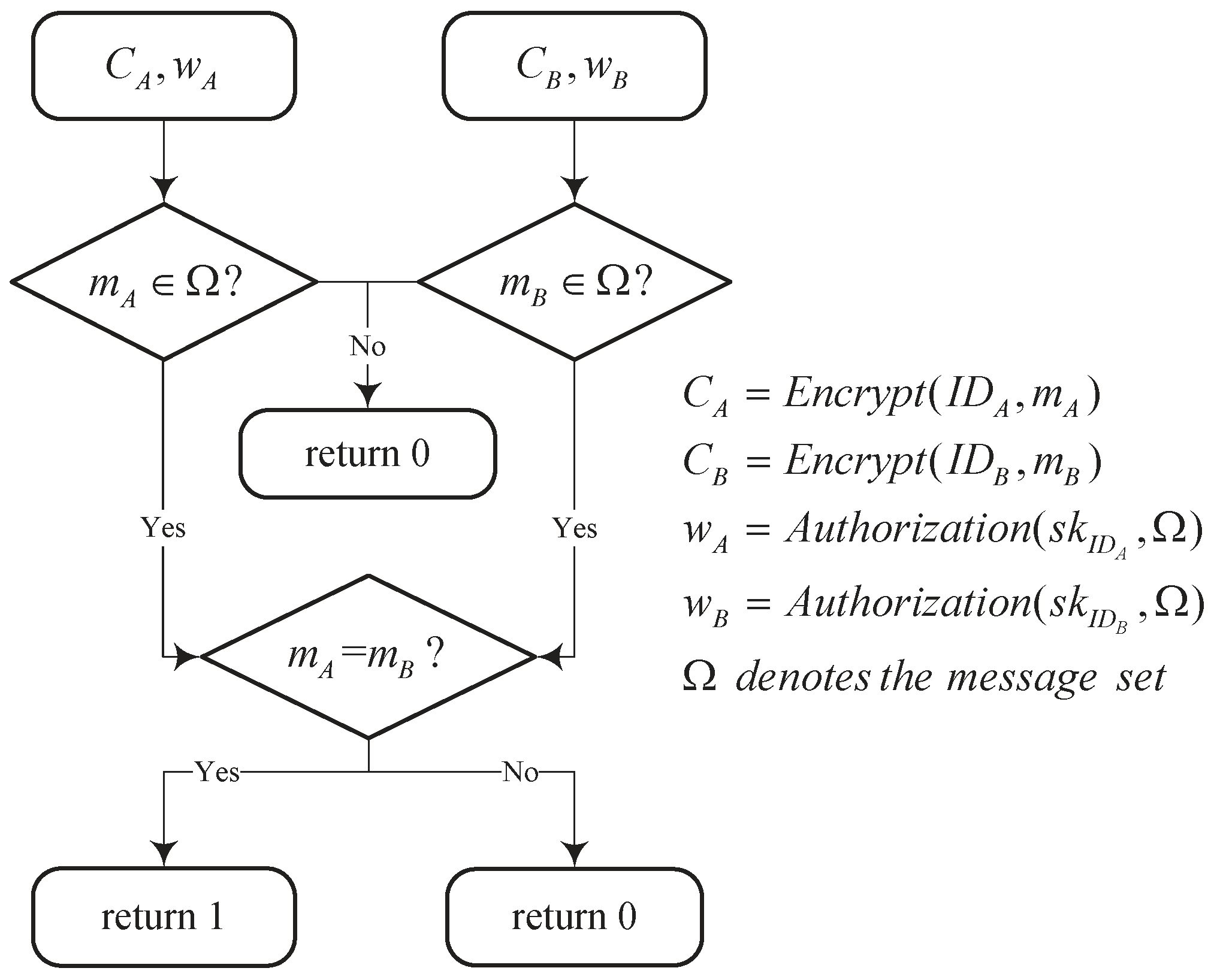
- Filtered equality test: Given two ciphertexts and , two warrants and , the cloud server executes as follows:
- (1)
- Computes and .
- (2)
- Checks whether or not. It outputs 1 if , which means , and . Otherwise, it outputs 0.
6. Security Proof
- Setup: Given a security parameter k, the system executes as follows:
- (1)
- Chooses a bilinear pairing: , where and are two cyclic groups with prime order q, g is a generator of .
- (2)
- Randomly picks , and computes , , , , .
- (3)
- Chooses three one-way hash functions: , , , where is the length of the message and is the length of .
The system parameters are and the pravate key are . - Encrypt: Given the message m, the sender executes as follows:
- (1)
- Randomly chooses .
- (2)
- Computes , , , , , .
The ciphertext is , where . - Decrypt: Given the ciphertexts C and the private key , the receiver works as follows:
- (1)
- Computes and .
- (2)
- Verifiesfor all . If holds, it outputs m. Otherwise, it outputs ⊥.
- Hash queries: submits a query on , checks the list and performs as below:
- -
- If contains , responds with previous value to .
- -
- If doesn’t contain , based on the Coron’s technology [50], tosses a coin that yield 0 with probability and 1 with probability . randomly chooses . If , computes . If , computes . Finally, adds the tuple to the list and returns to .
- Private key queries: submits a private key query on , makes the hash query on to obtain the corresponding tuple .
- -
- If , returns to .
- -
- If , returns ⊥.
- Decryption queries: submits a decryption query on and , makes the hash query on to obtain the corresponding tuple .
- -
- If , obtains and decrypts C using .
- -
- If , obtains and computes . Then sets . Note that the IBE-FET decryption of C using is the same as the PKE decryption of using because and for any . makes the decryption query on to and returns the response of to .
- Authorization queries: submits an authorization query on and the message set , makes the private key query on to obtain . Then runs the authorization algorithm and returns the warrant to .
- If , returns ⊥.
- If , randomly chooses and returns a PKE challenge ciphertext on to . Then returns to .
- Private key queries: If , responds as in Phase 1. Otherwise, returns ⊥.
- Decryption queries: If , responds as in Phase 1. Otherwise, returns ⊥.
- Authorization queries: responds as in Phase 1.
- : aborts in the private key query during Phase 1 or Phase 2.
- : aborts in the challenge phase.
- : aborts in the decryption query in Phase 2.
- Hash queries: makes a hash query on , checks the list and performs as follows.
- -
- If includes , returns to .
- -
- If doesn’t include , selects a random sting and returns to .
- Decryption queries: makes a decryption query on C, returns m to by running the decryption algorithm using the private key.
- Hash queries: makes a hash query on , checks the list and performs as follows.
- -
- If includes . When , defines as and returns to ; otherwise, returns to .
- -
- If doesn’t include , selects a random sting and returns to .
- Decryption queries: responds a decryption query as in Game 0.
- Hash queries: makes a hash query on , checks the list and performs as follows.
- -
- If includes . When , returns ⊥. Define this event as ; otherwise, returns to .
- -
- If does not include , selects a random sting and returns to .
- Decryption queries: makes a decryption query on C. If C is equal to the challenge ciphertext except , returns ⊥. Otherwise, responds as in Game 1.
- Hash queries: responds as in Game 2.
- Decryption queries: makes a decryption query on C. If , , , , returns ⊥. Otherwise, searches the list to get and computes , . If and are hold for all , returns to .
- has never made a hash query on before a decryption query on . In this case, returns ⊥. If C is a valid ciphertext, it means guesses the value of correctly. Thus the probability is .
- The event occurs in the hash queries. It means that the list includes the tuple . The probability is .
7. Comparison and Performance Evaluation
7.1. Comparison
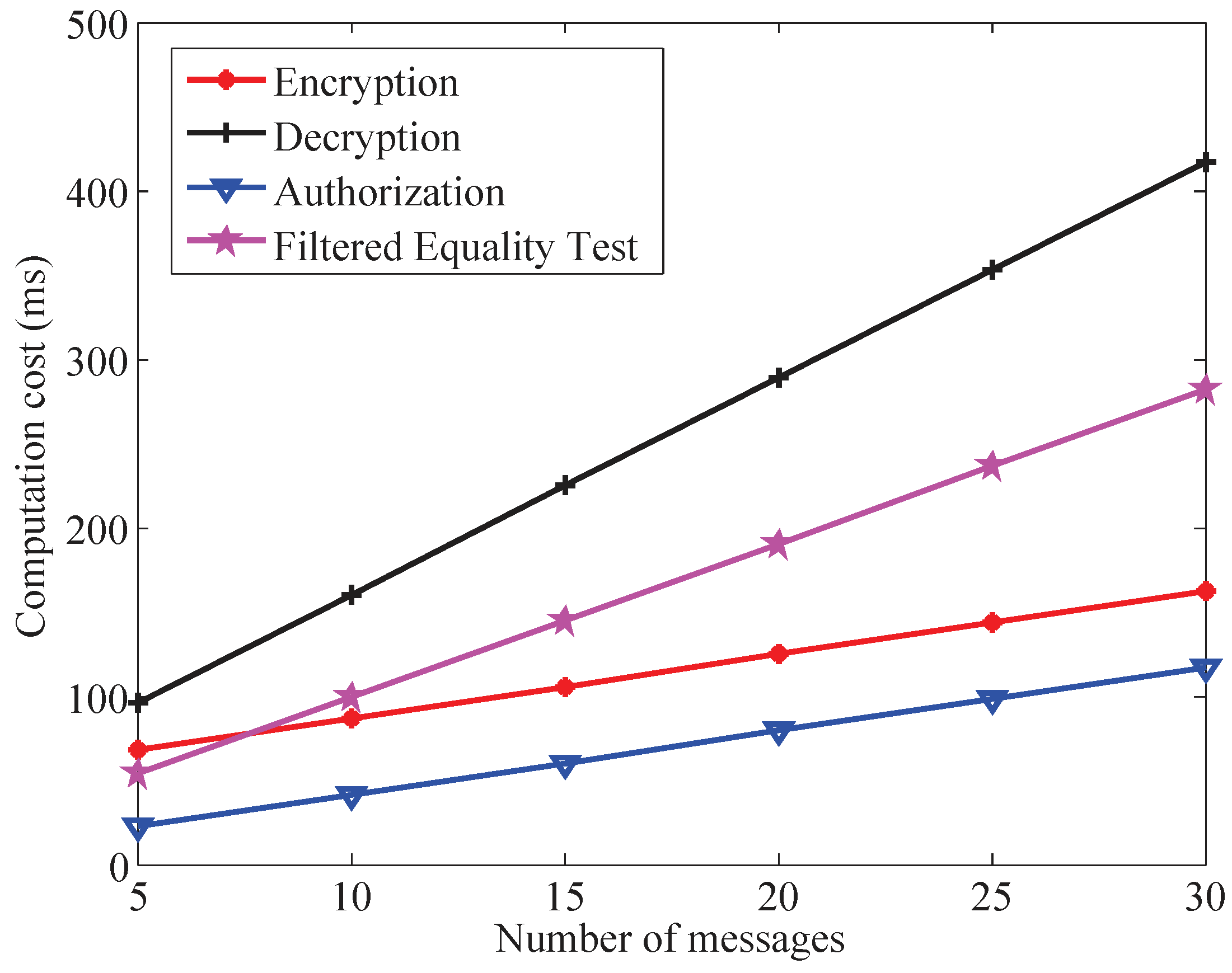
7.2. Computation Cost
7.3. Communication Cost
8. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Nam, T.; Pardo, T.A. Conceptualizing smart city with dimensions of technology, people, and institutions. In Proceedings of the 12th Annual International Digital Government Research Conference on Digital Government Innovation in Challenging Times, College Park, MD, USA, 12–15 June 2011; pp. 282–291. [Google Scholar]
- Yu, Y.; Li, Y.; Tian, J. Blockchain-based solutions to security and privacy issues in the Internet of Things. IEEE Wirel. Commun. 2018, 25, 12–18. [Google Scholar] [CrossRef]
- Su, K.; Jie, L.; Hongbo, F. Smart city and the applications. In Proceedings of the International Conference on Electronics, Communications and Control (ICECC), Ningbo, China, 9–11 September 2011; pp. 1028–1031. [Google Scholar]
- Ferraz, F.S.; Ferraz, C.A.G. Smart city security issues: Depicting information security issues in the role of an urban environment. In Proceedings of the 7th International Conference on Utility and Cloud Computing (UCC), London, UK, 8–11 December 2014; pp. 842–847. [Google Scholar]
- Zheng, D.; Wu, A.; Zhang, Y.; Zhao, Q. Efficient and privacy-preserving medical data sharing in Internet of Things with limited computing power. IEEE Access 2018, 6, 28019–28027. [Google Scholar] [CrossRef]
- Zhang, Y.; Yang, M.; Zheng, D.; Lang, P.; Wu, A.; Chen, C. Efficient and secure big data storage system with leakage resilience in cloud computing. Soft Comput. 2018, 22, 7763–7772. [Google Scholar] [CrossRef]
- Catarinucci, L.; De Donno, D.; Mainetti, L. An IoT-aware architecture for smart healthcare systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Demirkan, H. A smart healthcare systems framework. IT Prof. 2013, 15, 38–45. [Google Scholar] [CrossRef]
- Acampora, G.; Cook, D.J.; Rashidi, P. A survey on ambient intelligence in healthcare. Proc. IEEE 2013, 101, 2470–2494. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Y.; Zheng, D.; Deng, R.H. Security and privacy in smart health: Efficient policy-hiding attribute-based access control. IEEE Internet Things J. 2018, 5, 2130–2145. [Google Scholar] [CrossRef]
- Zhang, Y.; Lang, P.; Zheng, D.; Yang, M.; Guo, R. A secure and privacy-aware smart health system with secret key leakage resilience. Secur. Commun. Netw. 2018, 2018, 1–13. [Google Scholar] [CrossRef]
- Zhang, Y.; Deng, R.H.; Han, G. Secure smart health with privacy-aware aggregate authentication and access control in Internet of Things. J. Netw. Comput. Appl. 2018, 123, 89–100. [Google Scholar] [CrossRef]
- Zhang, Y.; Zheng, D.; Guo, R.; Lan, Q. Fine-grained access control systems suitable for resource-constrained users in cloud computing. Comput. Inf. 2018, 37, 327–348. [Google Scholar] [CrossRef]
- Abdalla, M.; Bellare, M.; Catalano, D. Searchable encryption revisited: Consistency properties, relation to anonymous IBE, and extensions. In Proceedings of the Advances in Cryptology-Crypto’05, Santa Barbara, CA, USA, 14–18 August 2005; pp. 205–222. [Google Scholar]
- Bellare, M.; Boldyreva, A.; O’Neill, A. Deterministic and efficiently searchable encryption. In Proceedings of the Advances in Cryptology-Crypto’07, Santa Barbara, CA, USA, 19–23 August 2007; pp. 535–552. [Google Scholar]
- Fuhr, T.; Paillier, P. Decryptable searchable encryption. In Proceedings of the International Conference on Provable Security, Wollongong, Australia, 1–2 November 2007; pp. 228–236. [Google Scholar]
- Boneh, D.; Di Crescenzo, G.; Ostrovsky, R. Public key encryption with keyword search. In Proceedings of the Advances in Cryptology-Crypto’04, Interlaken, Switzerland, 2–6 May 2004; pp. 506–522. [Google Scholar]
- Yau, W.C.; Heng, S.H.; Goi, B.M. Off-line keyword guessing attacks on recent public key encryption with keyword search schemes. In Proceedings of the International Conference on Autonomic and Trusted Computing (ATC), Oslo, Norway, 23–25 June 2008; pp. 100–105. [Google Scholar]
- Ibraimi, L.; Nikova, S.; Hartel, P. Public-key encryption with delegated search. In Proceedings of the International Conference on Applied Cryptography and Network Security (ACNS), Nerja, Spain, 7–10 June 2011; pp. 532–549. [Google Scholar]
- Fang, L.; Susilo, W.; Ge, C. Public key encryption with keyword search secure against keyword guessing attacks without random oracle. Inform. Sci. 2013, 238, 221–241. [Google Scholar] [CrossRef]
- Baek, J.; Safavi-Naini, R.; Susilo, W. Public key encryption with keyword search revisited. In Proceedings of the International Conference on Computational Science and Its Applications (ICCSA), Perugia, Italy, 30 June–3 July 2008; pp. 1249–1259. [Google Scholar]
- Chen, R.; Mu, Y.; Yang, G. A new general framework for secure public key encryption with keyword search. In Proceedings of the Australasian Conference on Information Security and Privacy (ACISP), Brisbane, QLD, Australia, 29 June–1 July 2015; pp. 59–76. [Google Scholar]
- Yang, G.; Tan, C.H.; Huang, Q. Probabilistic public key encryption with equality test. In Proceedings of the Cryptographers’ Track at the RSA Conference (CT-RSA), San Francisco, CA, USA, 1–5 March 2010; pp. 119–131. [Google Scholar]
- Tang, Q. Towards public key encryption scheme supporting equality test with fine-grained authorization. In Proceedings of the Australasian Conference on Information Security and Privacy (ACISP), Melbourne, VIC, Australia, 11–13 July 2011; pp. 389–406. [Google Scholar]
- Tang, Q. Public key encryption supporting plaintext equality test and user-specified authorization. Secur. Commun. Netw. 2012, 5, 1351–1362. [Google Scholar] [CrossRef]
- Tang, Q. Public key encryption schemes supporting equality test with authorization of different granularity. Int. J. Appl. Cryptogr. 2012, 2, 304–321. [Google Scholar] [CrossRef]
- Lu, Y.; Zhang, R.; Lin, D. Stronger security model for public-key encryption with equality test. In Proceedings of the International Conference on Pairing-Based Cryptography, Cologne, Germany, 16–18 May 2012; pp. 65–82. [Google Scholar]
- Ma, S.; Zhang, M.; Huang, Q. Public key encryption with delegated equality test in a multi-user setting. Comput. J. 2014, 58, 986–1002. [Google Scholar] [CrossRef]
- Huang, K.; Tso, R.; Chen, Y.C. Pke-aet: Public key encryption with authorized equality test. Comput. J. 2015, 58, 2686–2697. [Google Scholar] [CrossRef]
- Ma, S.; Huang, Q.; Zhang, M. Efficient public key encryption with equality test supporting flexible authorization. IEEE Trans. Inf. Forensics Secur. 2015, 10, 458–470. [Google Scholar] [CrossRef]
- Lin, X.J.; Qu, H.; Zhang, X. Public Key Encryption Supporting Equality Test and Flexible Authorization Without Bilinear Pairings. Cryptology ePrint Archive. 2016. Available online: http://eprint.iacr.org/2016/277 (accessed on 1 July 2019).
- Ma, S. Identity-based encryption with outsourced equality test in cloud computing. Inf. Sci. 2016, 328, 389–402. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Choo, K.R. Efficient and secure identity-based encryption scheme with equality test in cloud computing. Future Gener. Comput. Syst. 2017, 73, 22–31. [Google Scholar] [CrossRef]
- Zhu, H.; Wang, L.; Ahmad, H.; Niu, X. Key-policy attribute-based encryption with equality test in cloud computing. IEEE Access 2017, 5, 20428–20439. [Google Scholar] [CrossRef]
- Wang, Q.; Peng, L.; Xiong, H.; Sun, J. Ciphertext-policy attribute-based encryption with delegated equality test in cloud computing. IEEE Access 2017, 6, 760–771. [Google Scholar] [CrossRef]
- Liao, Y.; Chen, H.; Li, F.; Jiang, S.; Zhou, S.; Mohammed, R. Insecurity of a key-policy attribute based encryption scheme with equality test. IEEE Access 2018, 6, 10189–10196. [Google Scholar] [CrossRef]
- Sun, J.; Bao, Y.; Nie, X.; Xiong, H. Attribute-hiding predicate encryption with equality test in cloud computing. IEEE Access 2018, 6, 31621–31629. [Google Scholar] [CrossRef]
- Huang, K.; Chen, Y.C.; Tso, R. Semantic secure public key encryption with filtered equality test pke-fet. In Proceedings of the 12th International Joint Conference on E-Business and Telecommunications (ICETE), Colmar, France, 20–22 July 2015; pp. 327–334. [Google Scholar]
- Huang, K.; Tso, R.; Chen, Y.C. Somewhat semantic secure public key encryption with filtered-equality-test in the standard model and its extension to searchable encryption. J. Comput. Syst. Sci. 2017, 89, 400–409. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. In Proceedings of the Advances in Cryptology-Crypto’01, Santa Barbara, CA, USA, 19–23 August 2001; pp. 213–229. [Google Scholar]
- Amin, S.M.; Wollenberg, B.F. Toward a smart grid: Power delivery for the 21st century. IEEE Power Energy Mag. 2005, 3, 34–41. [Google Scholar] [CrossRef]
- Heydt, G.T. The next generation of power distribution systems. IEEE Trans. Smart Grid. 2010, 1, 225–235. [Google Scholar] [CrossRef]
- Alderman, J.; Farley, N.; Crampton, J. Tree-based cryptographic access control. In Proceedings of the 22nd European Symposium on Research in Computer Security (ESORICS), Oslo, Norway, 11–15 September 2017; pp. 47–64. [Google Scholar]
- Alderman, J.; Crampton, J.; Farley, N. A framework for the cryptographic enforcement of information flow policies. In Proceedings of the 22nd ACM on Symposium on Access Control Models and Technologies (SACMAT), Indianapolis, IN, USA, 21–23 June 2017; pp. 143–154. [Google Scholar]
- Castiglione, A.; De Santis, A.; Masucci, B. Supporting dynamic updates in storage clouds with the Akl-Taylor scheme. Inf. Sci. 2017, 387, 56–74. [Google Scholar] [CrossRef]
- Castiglione, A.; De Santis, A.; Masucci, B. Key indistinguishability versus strong key indistinguishability for hierarchical key assignment schemes. IEEE Trans. Dependable Secur. Comput. 2016, 13, 451–460. [Google Scholar] [CrossRef]
- Yu, Y.; Ho Au, M.; Ateniese, G.; Huang, X.; Susilo, W.; Dai, Y.; Min, G. Identity-based remote data integrity checking with perfect data privacy preserving for cloud storage. IEEE Trans. Inf. Forensics Sec. 2017, 12, 767–778. [Google Scholar] [CrossRef]
- Li, Y.; Yu, Y.; Susilo, W.; Min, G.; Ni, J.; Choo, R. Fuzzy identity-based data integrity auditing for reliable cloud storage systems. IEEE Trans. Dependable Secur. Comput. 2019, 16, 72–83. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Coron, J.S. On the exact security of full domain hash. In Proceedings of the Advances in Cryptology-Crypto’00, Santa Barbara, CA, USA, 20–24 August 2000; pp. 229–235. [Google Scholar]
- Ltd, S.S. Multi Precision Integer and Rational Arithmetic Cryptographic Library (MIRACL). 2019. Available online: http://www.certivox.com/miracl/ (accessed on 1 July 2019).
| Schemes | ET | FET | ID | ROM | Security | Assumption |
|---|---|---|---|---|---|---|
| [23] | ✓ | ✗ | ✗ | ✓ | OW-CCA | CDH |
| [24] | ✓ | ✗ | ✗ | ✓ | OW-CCA,IND-CCA | CDH,DDH |
| [25] | ✓ | ✗ | ✗ | ✓ | OW-CCA,IND-CCA | CDH |
| [30] | ✓ | ✗ | ✗ | ✓ | OW-CCA,IND-CCA | CONF,CDH |
| [32] | ✓ | ✗ | ✓ | ✓ | OW-ID-CCA | CDH |
| [33] | ✓ | ✗ | ✓ | ✓ | OW-ID-CCA | CBDH |
| [39] | ✓ | ✓ | ✗ | ✗ | IND-CCA | SXDH |
| The proposed scheme | ✓ | ✓ | ✓ | ✓ | OW-ID-CCA | CBDH |
| Cryptographic Operation | Execution Time |
|---|---|
| Scalar multiplication | 3.7770 |
| Bilinear pairing | 9.0791 |
| Map-to-point hash function | 9.7052 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ming, Y.; Wang, E. Identity-Based Encryption with Filtered Equality Test for Smart City Applications. Sensors 2019, 19, 3046. https://doi.org/10.3390/s19143046
Ming Y, Wang E. Identity-Based Encryption with Filtered Equality Test for Smart City Applications. Sensors. 2019; 19(14):3046. https://doi.org/10.3390/s19143046
Chicago/Turabian StyleMing, Yang, and Erxiu Wang. 2019. "Identity-Based Encryption with Filtered Equality Test for Smart City Applications" Sensors 19, no. 14: 3046. https://doi.org/10.3390/s19143046
APA StyleMing, Y., & Wang, E. (2019). Identity-Based Encryption with Filtered Equality Test for Smart City Applications. Sensors, 19(14), 3046. https://doi.org/10.3390/s19143046





