Abstract
With the growth of the urban population, the rapid development of smart cities has become the focus of urban regional development. Smart medical care is an indispensable part of smart city construction, which promotes the development of the medical industry. However, the security of data and timely service are the current problems faced by intelligent medical systems. Based on the public key encryption with filtered equality test and identity-based cryptography, an identity-based encryption with the filtered equality test (IBE-FET) is proposed for smart healthcare, in which a data receiver can use the private key and the message set to generate a warrant and send it to the cloud server. A cloud server can verify the equality between ciphertexts without decryption and check whether the encrypted message belongs to the same message set. Furthermore, the security analysis shows that the proposed scheme satisfies one-way security against the chosen identity and ciphertext attack in the random oracle model under the computational bilinear Diffie-Hellman assumption. The performance comparison shows that the scheme is feasible and practical in real life.
1. Introduction
The concept of the smart city (SC) [1] emerges in the context in which the current global power supply and consumption trends are socially, environmentally and economically unsustainable. It refers to an urban transformation which, with the use of the latest information and communications technologies (ICT), improves cities’ efficiency. Currently, more and more people live in cities and every person uses more than five devices to access the Internet. Thus, the various embedded devices are integrated with urban infrastructure to optimize daily life of citizens.
Recently, with the rapid development of the Internet of Things (IoT) [2] and ICT, the applications of the smart city [3] are on the rise, which can enhance the life quality of citizens. Representative smart city applications are given in Figure 1, which benefit the city and people in a variety of aspects: economy, education, healthcare, and living. Meanwhile, the smart city has a new, complete level of effectiveness, sustainability and efficiency.
Figure 1.
Representative smart city applications.
The main goal of the smart city is to greatly improve quality of life. Nevertheless, the security and privacy problems are of great importance to the users in the smart city [4,5,6]. Progress in the IoT and cloud computing technology is driving the development of smart systems to support and improve healthcare system. However, the current healthcare system is faced with a series of challenges in providing low cost health care services. Besides, it is difficult for patients in some areas to obtain a timely healthcare services due to poor medical conditions. As a result, smart healthcare [7,8] has emerged recently as the key component of a new generation healthcare network. The so-called smart healthcare is to improve the efficiency of biomedical systems and healthcare infrastructures through various entities and technologies, including smart sensors, wearable devices, ICT and more [9].
In the smart healthcare system, patients are paying more and more attention to the security of private information. Zhang et al. [10,11,12,13] has done in-depth research and proposed privacy-preserving access control systems by adopting attribute-based encryption techniques to improve the security of smart healthcare. However, the techniques are complex and unfeasible in practice. To save storage space and protect the user’s privacy, the sensitive information must be stored in the untrusted healthcare cloud servers in an encrypted form. However, given some ciphertexts, no one can distinguish the relationships among the ciphertexts without decryption. Searchable encryption (SE) [14,15,16] is a practical and promising solution to this problem. To provide the capability for searching in the ciphertexts, the public key encryption with keyword search (PKE-KS) schemes [17,18,19,20,21,22] were proposed, which is one practical implementation of SE. However, the PKE-KS schemes have one weakness that the ciphertexts are generated by the same public keys and therefore it is not applicable to some scenarios. To solve this problem, the public key encryption with equality test (PKE-ET) schemes [23,24,25,26,27,28,29,30,31] were put forward, which allowed equality tests made on the ciphertexts by different public keys as well as the same public keys. To alleviate the storage cost of certificates, identity-based encryption with equality test (IBE-ET) schemes [32,33] were proposed. Along with research, to make fine-grained authorization more flexible and inspired by the idea of attribute-based encryption, the attribute-based encryption with equality test (ABE-ET) schemes [34,35,36,37] were presented.
To provide more flexible equality testing to satisfy different requirements, Huang et al. presented the public key encryption with filtered equality test (PKE-FET) schemes [38,39], in which only a few selected message sets can be equality tested. An authorized user can determine not only whether two ciphertexts contain the same plaintext (without decryption) but also whether the plaintext belongs to the message set.
In this paper, we integrate the identity-based cryptography [40] into PKE-FET to propose a new concept of identity-based encryption with the filtered equality test (IBE-FET) for smart healthcare. A practical application scenario using IBE-FET is shown in Figure 2.
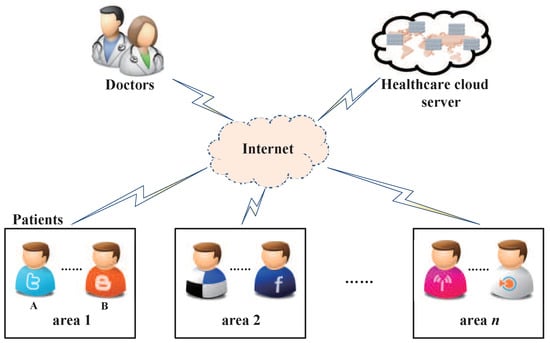
Figure 2.
A practical application scenario of identity-based encryption with filtered equality test (IBE-FET).
In the smart healthcare system, there are three parties: doctors, the healthcare cloud server (HCS) and patients, where the patients are distributed in different areas. To ensure the privacy of patients, the sensitive data is encrypted during transmission. It is desired that the healthcare providers optimize the distribution of family doctors, and thus they need to search for the encrypted information. With the assumption that patients A and B with the same symptoms belong to area 1, A encrypts his privacy information (symptom and area) under the identity and the doctor’s identity , and transmits the tuple to HCS. Additionally, A generates a warrant and transmits to HCS. B transmits and to HCS in the same way. Upon obtaining these data, the HCS could determine and search whether A and B are distributed in the same areas and have the same symptom. However, there is no knowledge what the real areas and symptom are. Then, the HCS sends the search result to the patients A and B, respectively, which allows them to share their medical experience with each other. Most important of all, the HCS can investigate the cause of the disease and arrange family doctors reasonably to improve the efficiency of healthcare. The above scenario can be extended to multi-user scenarios. For instance, more patients can get the warrant and send it to the HCS along with the requests and obtain feedback, indicating whether there are any patients belonging to the same area who have the same symptom features.
Besides, the IBE-FET scheme can also be applied to the smart grid system [41,42], which contains electricity suppliers, a power system cloud server and users. To protect the privacy and enhance the power quality of users, the privacy information (e.g., power consumers and location) is generally transmitted in encrypted form. Based on IBE-FET, the power system cloud server can determine and search whether there are any users belonging to the same area that have the same feature (e.g., power flow and peak loading). Then, they send the search result to the electricity suppliers for improvement of the power distribution and optimization of the power flow.
1.1. Our Contributions
This paper proposes an identity-based encryption with the filtered equality test (IBE-FET). The main contributions are summarized as follows:
- Based on secret sharing and bilinear pairing, an IBE-FET scheme is proposed, which does not use the certificate verification to solve the problems of certificate management.
- The security analysis indicates that the IBE-FET scheme is one-way secure against the chosen identity and ciphertext attack (OW-ID-CCA) based on the computational bilinear Diffie-Hellman assumption in the random oracle model.
- The performance analysis shows that the IBE-FET scheme achieves the function of a filtered equality test and a higher efficiency in terms of communication cost than the related scheme [39], and therefore the proposed scheme is more suitable for smart healthcare systems.
1.2. Organization
The organization of this paper is as follows: We will briefly discuss related work in Section 2 and review some preliminaries in Section 3; in Section 4, we introduce the framework of IBE-FET; a concrete IBE-FET scheme is put forward in Section 5; Section 6 proposes a formal security proof; comparison and performance evaluations are described in Section 7; and Section 8 concludes this paper.
2. Related Works
The concept of public key encryption with the keyword search (PKE-KS) was first put forward by Boneh et al. [17]. In PKE-KS, each user can use their private key to generate a token for a keyword and send the token to the tester. Upon receiving the token, the tester can determine the equality of ciphertexts. Then, some interesting extension schemes [18,19,20,21,22] were proposed to satisfy various requirements.
PKE-KS aims at testing the keyword’s equality using a given trapdoor. However, it is not suitable for an equality test on ciphertexts by different public keys. In order to solve this problem, Yang et al. [23] proposed public key encryption with the equality test (PKE-ET). The so-called “equality test (ET)” refers to an authorized user who can verify the equality of two ciphertexts encrypted by different public keys, while the decryption keeps unavailable. However, in the PKE-ET scheme, anyone has the ability to execute the equality test without any authorization. As a fundamental security service, the authorization mechanism becomes increasingly important in modern smart system. The hierarchical key assignment techniques [43,44,45,46] were presented, which can provide fine-grained authentication and access control for the user. In order to mitigate the potential vulnerabilities and protect the user’s privacy, Tang et al. [24] integrated the fine-grained authorization mechanism into PKE-ET. In this scheme, two users require cooperation to generate the token by running the authorization algorithm and send this token to the tester, with the tester authorized to verify the equality between the ciphertexts. In addition, Tang et al. [25] introduced the concept of coarse-grained authorization scheme, in this system, every user independently generates the token by running the authorization algorithm and sends it to the tester, who executes the equality test from their ciphertexts. In 2012, Tang [26] expanded [24] to a two-proxy agents setting, where two proxies require cooperation to perform the equality test. Lu et al. [27] introduced a stronger security model for PKE-ET to meet the different demands. In 2015, the public key encryption with the delegated equality test scheme (PKE-DET) was proposed by Ma et al. [28] and in this scheme every user can generate the delegation token independently for the cloud server. Different from PKE-DET, Huang et al. [29] introduced an efficient public key encryption with the authorized equality test (PKE-AET), a provision of two kinds of warrants (recipient warrants and ciphertext warrants) and allowance of the authorized users to use warrants to execute the equality test on two ciphertexts encrypted by different public keys. To satisfy various requirements, the public key encryption supporting equality test and flexible authorization (PKE-ET-FA) was proposed by Ma et al. [30]. In this scheme, four types of authorization were presented to strengthen the user privacy protection. However, it is inefficient due to using bilinear pairings. In 2016, Lin et al. [31] proposed an efficient PKE-ET-FA scheme without using bilinear pairing, which was more suitable for practice. In order to solve the certificate management problem, the identity-based encryption with equality test (IBE-ET) [32,33] was presented. To determine the equality of two ciphertexts encrypted under different access policies, the attribute-based encryption with equality test schemes (ABE-ET) [34,35,36,37] were put forward.
For making the equality test more flexible, based on bilinear pairing and secret sharing, Huang et al. [38,39] proposed the public key encryption with the filtered equality test (PKE-FET). In these schemes, the receiver selects n messages as a set , and then the receiver can use a private key and to generate the warrant w and sends this warrant to someone, who can execute the equality test without decryption.
The PKE-FET scheme needs certification authority to ensure the authenticity of public keys; however, it is worth noting that the problems of certificate management arise. Accordingly, inspired by the concept of identity-based cryptography [40,47,48], we presented an identity-based encryption with the filtered equality test scheme (IBE-FET), simplifying the certificate management of PKE-FET.
3. Preliminaries
This section introduces some preliminaries, including bilinear pairing, secret sharing and security assumption.
3.1. Bilinear Pairing
Let , be two cyclic groups of prime order q, and g is a generator of . is a bilinear pairing if the following three properties hold:
- Bilinearity: For all and , where .
- Non-degeneracy: .
- Computability: It is an efficient algorithm to compute for all .
3.2. Secret Sharing
The idea of secret sharing is introduced in [49], with a secret value k assigned to n users. A trusted party holds k and randomly picks numbers form t points on a 2-dimensional plane, which are . According to these points, there is only one polynomial function with degree determined. Then, the trusted party computes the points for user , in which all the points satisfy . By distributing these points, it formalizes a t-out-of-n secret sharing scheme. Therefore, as for any t or more than t users, it can reconstruct the polynomial function and obtain the secret value k by computing , but if less than t users, it cannot rebuild the secret value k.
3.3. Assumption
Computational Bilinear Diffie-Hellman (CBDH) Problem: Let g be the generator of and be chosen at randomly. Given a tuple , the task of CBDH problem is to compute .
The probability of the algorithm in solving the CBDH problem is defined as
Computational Bilinear Diffie-Hellman (CBDH) Assumption: The CBDH assumption holds if for any polynomial-time algorithm solves the CBDH problem with the negligible probability.
4. Framework of IBE-FET
The system model, syntax and security model are described in the following sections.
4.1. System Model
The system model of IBE-FET includes four parts: private key generator (PKG), sender (patient), receiver (doctor) and the cloud server, as illustrated in Figure 3. All ciphertexts are generated by the senders under the receiver’s identity and stored in the cloud server. The PKG’s task is to generate the private keys for the users (senders and receivers) secretly. To compare the ciphertexts, the receiver generates the corresponding warrant using its private key and the message set, sending it to the cloud server; wherein the warrant denotes the trapdoor of authentication. As a result, with the warrant, the cloud server is able to verify the equality between the ciphertexts without decryption and check whether the message belongs to the message set. The work of each part is described in more details below:
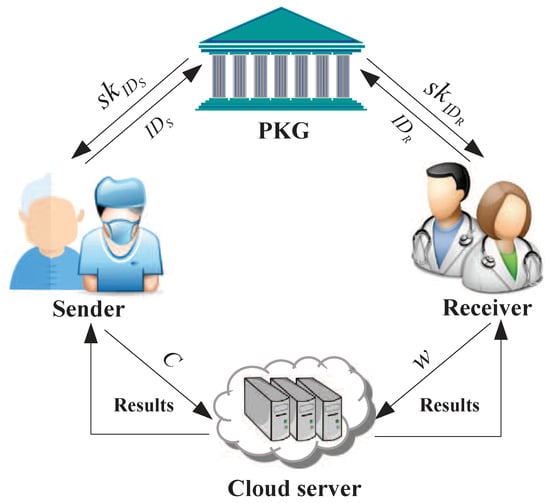
Figure 3.
System model for IBE-FET.
- PKG: It is responsible for generating the master key and the private key , and then keeps by itself and sends to the sender and receiver through a secure way.
- Sender (patient): The sender encrypts their private date under the receiver’s identity to generate the ciphertext C and stores it in the cloud server.
- Receiver (doctor): Upon receiving the private key from PKG, the receiver generates the warrant w and sends it to the cloud server. It is noted that the receiver can use the private key to decrypt the ciphertext at any time.
- Cloud server: With the warrant, the cloud server is in charge of executing the filtered equality test and returns a query result.
The detail data flow of the filtered equality test (FET) is described in Figure 4.
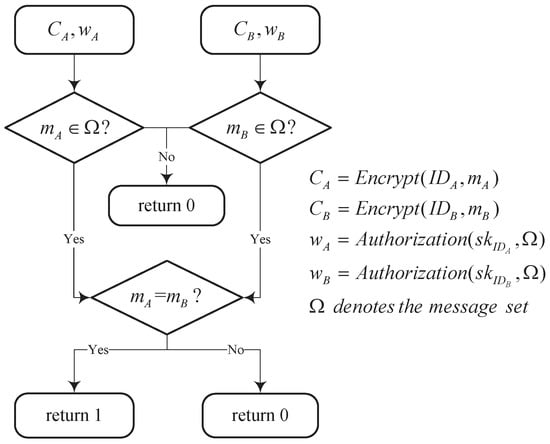
Figure 4.
Flow chart of FET.
4.2. Syntax
The IBE-FET scheme consists of the following six algorithms: setup, extract, encrypt, decrypt, authorization and filtered equality test. Let denote message space and denote the message set.
Setup: Taking a security parameter k as input, this algorithm outputs the master key and the system parameters .
Extract: Taking the master key and the identity as input, this algorithm outputs the private key .
Encrypt: Taking the system parameters , the plaintext and the identity as input, this algorithm outputs the ciphertext C.
Decrypt: Taking the system parameters , the ciphertext C and the private key as input, this algorithm outputs the corresponding plaintext m.
Authorization: Taking the system parameters , the identity , the private key and the message set as input, this algorithm outputs the warrant .
Filtered equality test: Taking the system parameters , the ciphertexts and , the warrants and as input, this algorithm returns 1 if , and . Otherwise, it returns 0.
For the property of consistency, the following conditions must be satisfied.
Correctness: When is generated by the Extract algorithm given , then, for all , .
Perfect consistency: When and are generated by the Authorization algorithm given , and , then, for all , and , the filtered equality test algorithm must return 1.
Computational soundness: When and are generated by the Authorization algorithm given , and , then, for all , and , the probability that the filtered equality test algorithm returns 1 is negligible.
4.3. Security Model
The security of IBE-FET needs to satisfy one-way security against the chosen identity and ciphertext attack (OW-ID-CCA), which is defined by an interactive game between a challenger and an adversary .
Setup: generates the master key and the system parameters by running the Setup algorithm. Then sends to and keeps by itself.
Phase 1: makes the following queries for polynomial number of times.
- Hash H queries: submits a query, then returns a random value to .
- Private key queries: submits the identity to , then runs the Extract algorithm and returns the private key to .
- Decryption queries: submits the identity and the ciphertext to , then runs the Extract algorithm to obtain and runs the Decrypt algorithm to return the plaintext to .
- Authorization queries: submits the identity and the message set to , then runs the Extract algorithm to obtain and runs the Authorization algorithm to return the warrant to .
Challenge: submits a challenge identity to , where does not appear in private key queries in Phase 1. randomly chooses a plaintext and sets be the challenge ciphertext. Finally, sends to .
Phase 2: Similar to Phase 1.
- Hash H queries: responds as in Phase 1.
- Private key queries: If , responds as in Phase 1. Otherwise, returns ⊥.
- Decryption queries: If , responds as in Phase 1. Otherwise, returns ⊥.
- Authorization queries: responds as in Phase 1.
Guess: outputs a guess and wins the above game if .
The advantage of winning the above game is defined as
Definition 1.
The IBE-FET scheme is OW-ID-CCA security if for any adversaries , is negligible.
Next, the security of the public key encryption (PKE) scheme (which will be mentioned later) needs to satisfy one-way security against the chosen ciphertext attack (OW-CCA), which is defined by an interactive game between a challenger and an adversary .
Setup: generates the private key and the system parameters by running the Setup algorithm. Then sends to and keeps by itself.
Phase 1: makes the following queries for polynomial number of times.
- Hash H queries: submits a query, then returns a random value to .
- Decryption queries: submits the ciphertext to , then runs the Decrypt algorithm and returns the plaintext to .
Challenge: randomly chooses a challenge plaintext and runs the Encrypt algorithm to obtain the challenge ciphertext . Finally, sends to .
Phase 2: Similar to Phase 1.
- Hash H queries: responds as in Phase 1.
- Decryption queries: If , responds as in Phase 1. Otherwise, returns ⊥.
Guess: outputs a guess and wins the above game if .
The advantage of wining the above game is defined as
Definition 2.
The PKE scheme is OW-CCA security if, for any adversaries , is negligible.
5. The Proposed Scheme
In this section, a detailed construction of IBE-FET is proposed.
- Setup: Given a security parameter k, the PKG executes as follows:
- (1)
- Chooses a bilinear pairing: , where and are two cyclic groups with prime order q, g is a generator of .
- (2)
- Randomly picks and computes , , , , .
- (3)
- Chooses four one-way hash functions , , , , where is the length of the message and is the length of .
The system parameters are and the master key are . - Extract: Given the identity and the master key , PKG computes and the private key .
- Encrypt: Given the message m and the identity , the sender executes as follows:
- (1)
- Randomly chooses .
- (2)
- Computes , , ,,,,.
The ciphertext is , where . - Decrypt: Given the ciphertext C and the private key , the receiver executes as follows:
- (1)
- Computes and .
- (2)
- Verifiesfor all . If holds, it outputs m. Otherwise, it outputs ⊥.
- Authorization: Given the message set and the private key , the receiver performs the following steps:
- (1)
- Computes a n-degree polynomial function and obtains the coefficient .
- (2)
- Computes for all and sends the warrant to the cloud server.
- Filtered equality test: Given two ciphertexts and , two warrants and , the cloud server executes as follows:
- (1)
- Computes and .
- (2)
- Checks whether or not. It outputs 1 if , which means , and . Otherwise, it outputs 0.
Correctness: The decryption algorithm computes
Then, let , it checks both and for all . It is straightforward that the correctness holds along with the decryption algorithm.
Perfect consistency: On input and , the filtered equality test algorithm obtains by computing
If , we have , therefore . Similarly, if , we can obtain . If , then . The filtered equality test algorithm outputs 1.
Computational soundness: For any and , by the inference of consistency, and will be computed as and , respectively. If , then , this is because is a collision resistant function. Hence the probability that the filtered equality test algorithm returns 1 is negligible. The computational soundness holds.
6. Security Proof
In this section, based on CBDH assumption, the proposed IBE-FET scheme is proved to be OW-ID-CCA security in the random oracle model. The detail of security proof is shown in Figure 5. Using the same method [32,33,40], we prove the security of the proposed scheme in two steps. We first show that an OW-ID-CCA attack on IBE-FET can be converted to an OW-CCA attack on PKE, then, we show that PKE is OW-CCA secure if the DBDH assumption holds.
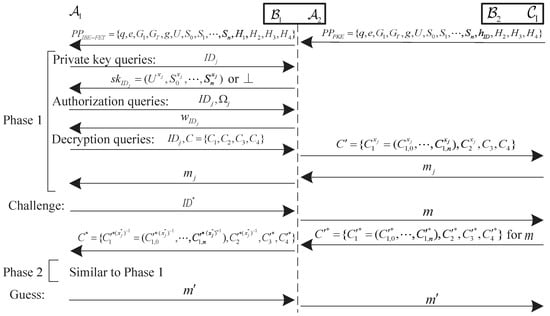
Figure 5.
The security proof of IBE-FET.
Theorem 1.
Supposing there is an OW-ID-CCA adversary that is able to break the proposed scheme with a non-negligible probability ε, then there exists an algorithm that solves the CBDH problem with the probability at least , where is the number of the private key queries, is the number of the authorization queries, is the number of the decryption queries and is the number of queries, is the length of the message and is the length of .
Proof.
Theorem 1 is proved based on the following Theorem 2 and Theorem 3. □
To prove Theorem 1, we must convert the OW-ID-CCA attack on an IBE-FET scheme to an OW-CCA attack on a PKE scheme. A related PKE scheme is described below.
- Setup: Given a security parameter k, the system executes as follows:
- (1)
- Chooses a bilinear pairing: , where and are two cyclic groups with prime order q, g is a generator of .
- (2)
- Randomly picks , and computes , , , , .
- (3)
- Chooses three one-way hash functions: , , , where is the length of the message and is the length of .
The system parameters are and the pravate key are . - Encrypt: Given the message m, the sender executes as follows:
- (1)
- Randomly chooses .
- (2)
- Computes , , , , , .
The ciphertext is , where . - Decrypt: Given the ciphertexts C and the private key , the receiver works as follows:
- (1)
- Computes and .
- (2)
- Verifiesfor all . If holds, it outputs m. Otherwise, it outputs ⊥.
Theorem 2.
Supposing there is an OW-ID-CCA adversary that is able to break the proposed IBE-FET scheme with a non-negligible probability , then there exists an OW-CCA adversary that can break the PKE scheme with the probability at least , where is the number of the private key queries, is the number of the authorization queries and is the number of the decryption queries.
Proof.
In order to convert an OW-ID-CCA attack on IBE-FET to an OW-CCA attack on PKE, we can construct a simulator to execute the game between and . □
Initialization: runs the Setup algorithm of PKE and returns the system parameters to . interacts with as follows.
Setup: chooses a hash function and returns the system parameters to . For the quickly respond and consistency, maintains an initially empty list of tuples .
Phase 1: makes the following queries.
- Hash queries: submits a query on , checks the list and performs as below:
- -
- If contains , responds with previous value to .
- -
- If doesn’t contain , based on the Coron’s technology [50], tosses a coin that yield 0 with probability and 1 with probability . randomly chooses . If , computes . If , computes . Finally, adds the tuple to the list and returns to .
- Private key queries: submits a private key query on , makes the hash query on to obtain the corresponding tuple .
- -
- If , returns to .
- -
- If , returns ⊥.
- Decryption queries: submits a decryption query on and , makes the hash query on to obtain the corresponding tuple .
- -
- If , obtains and decrypts C using .
- -
- If , obtains and computes . Then sets . Note that the IBE-FET decryption of C using is the same as the PKE decryption of using because and for any . makes the decryption query on to and returns the response of to .
- Authorization queries: submits an authorization query on and the message set , makes the private key query on to obtain . Then runs the authorization algorithm and returns the warrant to .
Challenge: chooses the challenge identity and returns it to . Here, does not appear in the private key queries of Phase 1. Then makes the hash query on to get the tuple and executes as follows:
- If , returns ⊥.
- If , randomly chooses and returns a PKE challenge ciphertext on to . Then returns to .
Phase 2: makes queries as done in Phase 1.
- Private key queries: If , responds as in Phase 1. Otherwise, returns ⊥.
- Decryption queries: If , responds as in Phase 1. Otherwise, returns ⊥.
- Authorization queries: responds as in Phase 1.
Guess: outputs a guess for . outputs a guess for .
We define the following three events:
- : aborts in the private key query during Phase 1 or Phase 2.
- : aborts in the challenge phase.
- : aborts in the decryption query in Phase 2.
Thus, we have
Clearly, can obtain the maximized when . The probability that does not abort is at least . Therefore, the advantage of is at least .
Theorem 3.
Supposing there is an OW-CCA adversary that is able to break the PKE scheme with a non-negligible probability , then there exists an algorithm that solves the CBDH problem with the probability at least , where is the number of queries and is the number of the decryption queries, is the length of the message and is the length of .
Proof.
Let represent the advantage of in the OW-CCA security game. According to schemes [23,24,25,26,27,28,29,30,31], this theorem is proved by performing a series of games. Let denote the event that in Game i . We define the Game 0 to be the real security game against the adversary in Definition 2. Then, we can modify the last game in an indistinguishable way to obtain the next game. The adversary has no advantage unconditionally in last game, thus he can make the queries many times, then the event will happen in the next game. Since each game is indistinguishable from the next, to prove the real security game, we can show that the probability of an event is negligible if the DBDH assumption holds. The detailed process is shown as follows. □
Game 0:
1. Initial phase: generates and by running the Setup algorithm, then computes . Finally, returns the system parameters to . For the quickly respond and consistency, maintains an initially empty list of tuples .
2. Query phase: works as follows:
- Hash queries: makes a hash query on , checks the list and performs as follows.
- -
- If includes , returns to .
- -
- If doesn’t include , selects a random sting and returns to .
- Decryption queries: makes a decryption query on C, returns m to by running the decryption algorithm using the private key.
3. Challenge phase: For any , randomly chooses and computes , and defines the challenge ciphertexts
as follows:
,
,
,
.
4. Output phase: outputs a guess for .
Thus, the advantage of winning in Game 0 is
Game 1:
1. Initial phase: responds as in Game 0.
2. Query phase: works as follows:
- Hash queries: makes a hash query on , checks the list and performs as follows.
- -
- If includes . When , defines as and returns to ; otherwise, returns to .
- -
- If doesn’t include , selects a random sting and returns to .
- Decryption queries: responds a decryption query as in Game 0.
3. Challenge phase: For any , randomly chooses , and computes , and defines the challenge ciphertexts
as follows:
,
,
,
.
4. Update phase: adds the tuple to the list .
5. Output phase: outputs a guess for .
Compared to Game 0, the value of is replaced by a random value in Game 1. According to the random oracle model, the advantage of winning in Game 1 is identical to Game 0. Thus
Game 2:
1. Initial phase: responds as in Game 1.
2. Query phase: works as follows:
- Hash queries: makes a hash query on , checks the list and performs as follows.
- -
- If includes . When , returns ⊥. Define this event as ; otherwise, returns to .
- -
- If does not include , selects a random sting and returns to .
- Decryption queries: makes a decryption query on C. If C is equal to the challenge ciphertext except , returns ⊥. Otherwise, responds as in Game 1.
3. Challenge phase: For any , randomly chooses , and computes , and defines the challenge ciphertexts
as follows:
,
,
,
.
4. Update phase: adds the tuple to the list .
5. Output phase: outputs a guess for .
Compared to Game 1, the value of is replaced by a random value in Game 2. According to the random oracle model, if the event does not occur, Game 2 is the same as Game 1. Therefore
Now, we proof the event occurs with negligible probability
Claim 1.
Event occurs with negligible probability in Game 2 if the CBDH problem is intractable.
Proof.
Assume the event occurs in Game 2 with a non-negligible probability , we can construct an algorithm that can compute with a non-negligible probability when receiving a random CBDH problem instance . □
randomly selects , , and computes . The system parameters are {}. Then, calculates , , and as the challenge ciphertexts and adds into the list . Finally, returns and the challenge ciphertexts to . makes the following queries:
- Hash queries: responds as in Game 2.
- Decryption queries: makes a decryption query on C. If , , , , returns ⊥. Otherwise, searches the list to get and computes , . If and are hold for all , returns to .
If the following two cases holds, can solve the CBDH problem:
- has never made a hash query on before a decryption query on . In this case, returns ⊥. If C is a valid ciphertext, it means guesses the value of correctly. Thus the probability is .
- The event occurs in the hash queries. It means that the list includes the tuple . The probability is .
Let to be event that the ciphertext is valid when returns ⊥ in the case 1. Then we have
Let to be event in case 2 that obtains as a solution of the CBDH problem. If does not occur and appears in the list with the probability at least . So
Then
So, we obtain
According to the assumption, if is non-negligible, the advantage is non-negligible. The proof of Claim 1 is completed.
Claim 2.
Event occurs with negligible probability in Game 2 if the CBDH problem is intractable.
Proof.
Assume the event occurs in Game 2 with a non-negligible probability , we can construct an algorithm that can compute with a non-negligible probability when receiving a random CBDH problem instance . □
randomly selects , , , and computes . The system parameters are {}. Then, calculates , , and as the challenge ciphertexts and adds into the list . And returns and the challenge ciphertexts to .
interacts with as Game 2.
Finally, obtains by computing
Therefore, we have
According to the assumption, if is non-negligible, the advantage is non-negligible. The proof of Claim 2 is completed.
Owing to the Equations (1)–(8), we can claim that
So, Theorem 3 has been proved.
According to Theorem 2 and Theorem 3, we can show that the proposed IBE-FET scheme satisfies OW-ID-CCA security. Assume an OW-ID-CCA adversary is able to against IBE-FET with the probability , then there the algorithm can solve the CBDH problem with the probability at least
7. Comparison and Performance Evaluation
In this section, we present the comparisons between the proposed IBE-FET scheme and the existing related schemes [23,24,25,30,32,33,39].
7.1. Comparison
The comparison for the proposed IBE-FET scheme and the related schemes [23,24,25,30,32,33,39] is given in Table 1. Let ET be the quality test, FET be the filtered quality test, ID be the identity-based and ROM be the random oracle model. Let ✓ denote “satisfy” and ✗ denote “not satisfy”.

Table 1.
Comparison.
From Table 1, it is clearly observed that scheme [39] and the proposed scheme support the filtered equality test while other schemes only provide the equality test. Schemes [32,33] and the proposed scheme adopt the identity-based cryptography which can avoid the certificate management problem, while other schemes adopt public key cryptography. With regard to security, all schemes are provably secure based on basic assumptions in the random oracle except scheme [39]. However, none of the schemes [23,24,25,30,32,33,39] could satisfy both the properties of the filtered equality test and of the identity-based one, only our scheme can do it.
7.2. Computation Cost
For computation complexity estimation, the time cost for performing the cryptographic operations is defined as follows. Let and denote the time of a scale multiplication operation and a bilinear pairing operation, respectively. The time of a map-to-point hash function operation is denoted as . Other lightweight operations (point addition, one way hash function operation) are not taken into account.
To offer the security level of 80-bit, we adopt the symmetric bilinear pairing , here is the cyclic group generated by a generator g with the order q on a super singular elliptic curve with embedding degree 2. p is 512-bit prime number and q is 160-bit Solinas prime number, which satisfy . Using the MIRACL Crypto SDK [51], the running time of the cryptographic operations are quantified. The experiment is run on an Intel Core i5-4590, 3.3GHz CPU, 8 gigabytes memory with Windows 7 environment. Table 2 lists the average execution times of cryptographic operations , , and .

Table 2.
Execution time of cryptographic operation.
Based on the experimental results, the computation cost of the proposed IBE-FET scheme and the related schemes [23,24,25,30,32,33,39] are summarized in Table 3.

Table 3.
Computation costs.
In the encryption phase, the proposed scheme needs to execute scalar multiplication operations, two bilinear pairing operations and two map-to-point hash operations; therefore, the total encryption time is ms. In the decryption phase, the proposed scheme needs to execute scalar multiplication operations, bilinear pairing operations and one map-to-point hash operation; therefore, the total decryption time is ms. In the authorization phase, the proposed scheme needs to execute scalar multiplication operations; therefore, the total authorization time is ms. In the test phase, the proposed scheme needs to execute bilinear pairing operations; therefore, the total test time is ms. From Table 3, we can arrive at the fact that the computational cost of the proposed scheme is higher than those of other schemes [23,24,25,30,32,33,39] in both encryption and decryption phases. In terms of authorization and test phases, the proposed scheme has the same computational cost as scheme [39], which is more than those of other schemes [23,24,25,30,32,33,39].
Figure 6 describes the relationship between the computational cost of the proposed scheme and the number of message n. As shown in Figure 6, the total computational cost increases linearly with the number of message in all phases. The computational cost is equal to 67.7496, 95.9209, 22.6270 and 54.4746 ms when , that is equal to 162.2096, 417.3234, 117.0870 and 281.4521 ms when , in encryption, decryption, authorization, and equation test phase of the proposed scheme, respectively. Based on the above analysis, the computational cost of the proposed scheme is feasible.

Figure 6.
Computational cost with different number of messages.
7.3. Communication Cost
We compare the communication cost of the proposed IBE-FET and those of the related schemes [23,24,25,30,32,33,39] in this section. The communication cost is represented by the size of message transmitted. The sender transmits the ciphertext to the cloud server for storing and a warrant is transmitted from the receiver to the cloud server in order to perform the filter equality test. Therefore, the communication cost is generated as a result of the communication between the sender and the cloud server and between the receiver and the cloud server. Let , , denote the sizes of the public key, ciphertext and warrant, respectively. Let be the length of the element in group , be the length of the element in group , be the element’s length of . Since the size of q is 512 bits (64 bytes), therefore the sizes of the elements in group and are 512 bits (64 bytes) and 3072 bits (384 bytes) respectively. The length of is 512 bits (64 bytes). Based on the above analysis, in the proposed scheme, the ciphertext is sent from the sender to the cloud server, where , , , . Therefore, the communication cost is . The warrant is sent from the receiver to the cloud server, where . Therefore, the communication cost is . The results of the comparison are listed in Table 4.

Table 4.
Communication costs.
From Table 4, we can see that the communication cost of schemes [23,24,25,30,32,33,39] is a fixed value, while that of the proposed scheme and scheme [39] increases linearly with the number of message n. From the above analysis, we find that when the message n is constant, the public key’s size of the proposed scheme is smaller than those of scheme [39]. As for the size of ciphertext and warrant, the communication cost of the proposed scheme is equal to that of scheme [39]. Thus, the communication cost of the proposed IBE-FET scheme is lower than that of scheme [39].
8. Conclusions
In this paper, based on bilinear pairing and secret sharing, we have presented an identity-based encryption with the filtered equality test (IBE-FET) scheme. The security analysis demonstrated that the proposed IBE-FET is OW-ID-CCA secure under the CBDH assumptions in the random oracle model. The performance evaluation and comparison indicate that the proposed IBE-FET achieves greater functionality than most previous schemes and adopts identity-based cryptography which avoids the certificate management issue effectively. In addition, the total computational cost increases linearly with the number of message n in all phases. Besides, in terms of communication cost, the proposed scheme is efficient. Therefore, the proposed IBE-FET scheme is more practical.
Author Contributions
Y.M. and E.W. conceived of the work, designed the concrete scheme and wrote the paper.
Acknowledgments
This work was supported in part by the Natural Science Foundation of Shaanxi Province under Grant 2018JM6081, in part by the Project of Science and Technology of Xi’an City under Grant 2017088CG/RC051(CADX002), and in part by the Fundamental Research Funds for the Central Universities, CHD, under Grant 300102249204.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Nam, T.; Pardo, T.A. Conceptualizing smart city with dimensions of technology, people, and institutions. In Proceedings of the 12th Annual International Digital Government Research Conference on Digital Government Innovation in Challenging Times, College Park, MD, USA, 12–15 June 2011; pp. 282–291. [Google Scholar]
- Yu, Y.; Li, Y.; Tian, J. Blockchain-based solutions to security and privacy issues in the Internet of Things. IEEE Wirel. Commun. 2018, 25, 12–18. [Google Scholar] [CrossRef]
- Su, K.; Jie, L.; Hongbo, F. Smart city and the applications. In Proceedings of the International Conference on Electronics, Communications and Control (ICECC), Ningbo, China, 9–11 September 2011; pp. 1028–1031. [Google Scholar]
- Ferraz, F.S.; Ferraz, C.A.G. Smart city security issues: Depicting information security issues in the role of an urban environment. In Proceedings of the 7th International Conference on Utility and Cloud Computing (UCC), London, UK, 8–11 December 2014; pp. 842–847. [Google Scholar]
- Zheng, D.; Wu, A.; Zhang, Y.; Zhao, Q. Efficient and privacy-preserving medical data sharing in Internet of Things with limited computing power. IEEE Access 2018, 6, 28019–28027. [Google Scholar] [CrossRef]
- Zhang, Y.; Yang, M.; Zheng, D.; Lang, P.; Wu, A.; Chen, C. Efficient and secure big data storage system with leakage resilience in cloud computing. Soft Comput. 2018, 22, 7763–7772. [Google Scholar] [CrossRef]
- Catarinucci, L.; De Donno, D.; Mainetti, L. An IoT-aware architecture for smart healthcare systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Demirkan, H. A smart healthcare systems framework. IT Prof. 2013, 15, 38–45. [Google Scholar] [CrossRef]
- Acampora, G.; Cook, D.J.; Rashidi, P. A survey on ambient intelligence in healthcare. Proc. IEEE 2013, 101, 2470–2494. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Y.; Zheng, D.; Deng, R.H. Security and privacy in smart health: Efficient policy-hiding attribute-based access control. IEEE Internet Things J. 2018, 5, 2130–2145. [Google Scholar] [CrossRef]
- Zhang, Y.; Lang, P.; Zheng, D.; Yang, M.; Guo, R. A secure and privacy-aware smart health system with secret key leakage resilience. Secur. Commun. Netw. 2018, 2018, 1–13. [Google Scholar] [CrossRef]
- Zhang, Y.; Deng, R.H.; Han, G. Secure smart health with privacy-aware aggregate authentication and access control in Internet of Things. J. Netw. Comput. Appl. 2018, 123, 89–100. [Google Scholar] [CrossRef]
- Zhang, Y.; Zheng, D.; Guo, R.; Lan, Q. Fine-grained access control systems suitable for resource-constrained users in cloud computing. Comput. Inf. 2018, 37, 327–348. [Google Scholar] [CrossRef]
- Abdalla, M.; Bellare, M.; Catalano, D. Searchable encryption revisited: Consistency properties, relation to anonymous IBE, and extensions. In Proceedings of the Advances in Cryptology-Crypto’05, Santa Barbara, CA, USA, 14–18 August 2005; pp. 205–222. [Google Scholar]
- Bellare, M.; Boldyreva, A.; O’Neill, A. Deterministic and efficiently searchable encryption. In Proceedings of the Advances in Cryptology-Crypto’07, Santa Barbara, CA, USA, 19–23 August 2007; pp. 535–552. [Google Scholar]
- Fuhr, T.; Paillier, P. Decryptable searchable encryption. In Proceedings of the International Conference on Provable Security, Wollongong, Australia, 1–2 November 2007; pp. 228–236. [Google Scholar]
- Boneh, D.; Di Crescenzo, G.; Ostrovsky, R. Public key encryption with keyword search. In Proceedings of the Advances in Cryptology-Crypto’04, Interlaken, Switzerland, 2–6 May 2004; pp. 506–522. [Google Scholar]
- Yau, W.C.; Heng, S.H.; Goi, B.M. Off-line keyword guessing attacks on recent public key encryption with keyword search schemes. In Proceedings of the International Conference on Autonomic and Trusted Computing (ATC), Oslo, Norway, 23–25 June 2008; pp. 100–105. [Google Scholar]
- Ibraimi, L.; Nikova, S.; Hartel, P. Public-key encryption with delegated search. In Proceedings of the International Conference on Applied Cryptography and Network Security (ACNS), Nerja, Spain, 7–10 June 2011; pp. 532–549. [Google Scholar]
- Fang, L.; Susilo, W.; Ge, C. Public key encryption with keyword search secure against keyword guessing attacks without random oracle. Inform. Sci. 2013, 238, 221–241. [Google Scholar] [CrossRef]
- Baek, J.; Safavi-Naini, R.; Susilo, W. Public key encryption with keyword search revisited. In Proceedings of the International Conference on Computational Science and Its Applications (ICCSA), Perugia, Italy, 30 June–3 July 2008; pp. 1249–1259. [Google Scholar]
- Chen, R.; Mu, Y.; Yang, G. A new general framework for secure public key encryption with keyword search. In Proceedings of the Australasian Conference on Information Security and Privacy (ACISP), Brisbane, QLD, Australia, 29 June–1 July 2015; pp. 59–76. [Google Scholar]
- Yang, G.; Tan, C.H.; Huang, Q. Probabilistic public key encryption with equality test. In Proceedings of the Cryptographers’ Track at the RSA Conference (CT-RSA), San Francisco, CA, USA, 1–5 March 2010; pp. 119–131. [Google Scholar]
- Tang, Q. Towards public key encryption scheme supporting equality test with fine-grained authorization. In Proceedings of the Australasian Conference on Information Security and Privacy (ACISP), Melbourne, VIC, Australia, 11–13 July 2011; pp. 389–406. [Google Scholar]
- Tang, Q. Public key encryption supporting plaintext equality test and user-specified authorization. Secur. Commun. Netw. 2012, 5, 1351–1362. [Google Scholar] [CrossRef]
- Tang, Q. Public key encryption schemes supporting equality test with authorization of different granularity. Int. J. Appl. Cryptogr. 2012, 2, 304–321. [Google Scholar] [CrossRef]
- Lu, Y.; Zhang, R.; Lin, D. Stronger security model for public-key encryption with equality test. In Proceedings of the International Conference on Pairing-Based Cryptography, Cologne, Germany, 16–18 May 2012; pp. 65–82. [Google Scholar]
- Ma, S.; Zhang, M.; Huang, Q. Public key encryption with delegated equality test in a multi-user setting. Comput. J. 2014, 58, 986–1002. [Google Scholar] [CrossRef]
- Huang, K.; Tso, R.; Chen, Y.C. Pke-aet: Public key encryption with authorized equality test. Comput. J. 2015, 58, 2686–2697. [Google Scholar] [CrossRef]
- Ma, S.; Huang, Q.; Zhang, M. Efficient public key encryption with equality test supporting flexible authorization. IEEE Trans. Inf. Forensics Secur. 2015, 10, 458–470. [Google Scholar] [CrossRef]
- Lin, X.J.; Qu, H.; Zhang, X. Public Key Encryption Supporting Equality Test and Flexible Authorization Without Bilinear Pairings. Cryptology ePrint Archive. 2016. Available online: http://eprint.iacr.org/2016/277 (accessed on 1 July 2019).
- Ma, S. Identity-based encryption with outsourced equality test in cloud computing. Inf. Sci. 2016, 328, 389–402. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Choo, K.R. Efficient and secure identity-based encryption scheme with equality test in cloud computing. Future Gener. Comput. Syst. 2017, 73, 22–31. [Google Scholar] [CrossRef]
- Zhu, H.; Wang, L.; Ahmad, H.; Niu, X. Key-policy attribute-based encryption with equality test in cloud computing. IEEE Access 2017, 5, 20428–20439. [Google Scholar] [CrossRef]
- Wang, Q.; Peng, L.; Xiong, H.; Sun, J. Ciphertext-policy attribute-based encryption with delegated equality test in cloud computing. IEEE Access 2017, 6, 760–771. [Google Scholar] [CrossRef]
- Liao, Y.; Chen, H.; Li, F.; Jiang, S.; Zhou, S.; Mohammed, R. Insecurity of a key-policy attribute based encryption scheme with equality test. IEEE Access 2018, 6, 10189–10196. [Google Scholar] [CrossRef]
- Sun, J.; Bao, Y.; Nie, X.; Xiong, H. Attribute-hiding predicate encryption with equality test in cloud computing. IEEE Access 2018, 6, 31621–31629. [Google Scholar] [CrossRef]
- Huang, K.; Chen, Y.C.; Tso, R. Semantic secure public key encryption with filtered equality test pke-fet. In Proceedings of the 12th International Joint Conference on E-Business and Telecommunications (ICETE), Colmar, France, 20–22 July 2015; pp. 327–334. [Google Scholar]
- Huang, K.; Tso, R.; Chen, Y.C. Somewhat semantic secure public key encryption with filtered-equality-test in the standard model and its extension to searchable encryption. J. Comput. Syst. Sci. 2017, 89, 400–409. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. In Proceedings of the Advances in Cryptology-Crypto’01, Santa Barbara, CA, USA, 19–23 August 2001; pp. 213–229. [Google Scholar]
- Amin, S.M.; Wollenberg, B.F. Toward a smart grid: Power delivery for the 21st century. IEEE Power Energy Mag. 2005, 3, 34–41. [Google Scholar] [CrossRef]
- Heydt, G.T. The next generation of power distribution systems. IEEE Trans. Smart Grid. 2010, 1, 225–235. [Google Scholar] [CrossRef]
- Alderman, J.; Farley, N.; Crampton, J. Tree-based cryptographic access control. In Proceedings of the 22nd European Symposium on Research in Computer Security (ESORICS), Oslo, Norway, 11–15 September 2017; pp. 47–64. [Google Scholar]
- Alderman, J.; Crampton, J.; Farley, N. A framework for the cryptographic enforcement of information flow policies. In Proceedings of the 22nd ACM on Symposium on Access Control Models and Technologies (SACMAT), Indianapolis, IN, USA, 21–23 June 2017; pp. 143–154. [Google Scholar]
- Castiglione, A.; De Santis, A.; Masucci, B. Supporting dynamic updates in storage clouds with the Akl-Taylor scheme. Inf. Sci. 2017, 387, 56–74. [Google Scholar] [CrossRef]
- Castiglione, A.; De Santis, A.; Masucci, B. Key indistinguishability versus strong key indistinguishability for hierarchical key assignment schemes. IEEE Trans. Dependable Secur. Comput. 2016, 13, 451–460. [Google Scholar] [CrossRef]
- Yu, Y.; Ho Au, M.; Ateniese, G.; Huang, X.; Susilo, W.; Dai, Y.; Min, G. Identity-based remote data integrity checking with perfect data privacy preserving for cloud storage. IEEE Trans. Inf. Forensics Sec. 2017, 12, 767–778. [Google Scholar] [CrossRef]
- Li, Y.; Yu, Y.; Susilo, W.; Min, G.; Ni, J.; Choo, R. Fuzzy identity-based data integrity auditing for reliable cloud storage systems. IEEE Trans. Dependable Secur. Comput. 2019, 16, 72–83. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Coron, J.S. On the exact security of full domain hash. In Proceedings of the Advances in Cryptology-Crypto’00, Santa Barbara, CA, USA, 20–24 August 2000; pp. 229–235. [Google Scholar]
- Ltd, S.S. Multi Precision Integer and Rational Arithmetic Cryptographic Library (MIRACL). 2019. Available online: http://www.certivox.com/miracl/ (accessed on 1 July 2019).
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).