1. Introduction
The vision of the Internet of Things (IoT) promises to bring wireless connectivity to anything ranging from tiny static sensors to vehicles and unmanned aerial vehicles (UAVs) [
1,
2,
3]. Meanwhile, short packets are the typical form of traffic generated by sensors and exchanged in machine-type communications [
4]. In these scenarios, the Shannon capacity, which assumes the infinite blocklength, is no longer achievable. In comparison to the Shannon capacity regime, reference [
5] developed a pioneering framework and identified a tight bound of the channel coding rate at the finite blocklength regime, which presents many new research opportunities with a wide range of applications.
The IoT can offer many benefits for daily life; however, machine-type communications, such as vehicle to vehicle communication and UAV communication among others, can be illegally used (e.g., by criminals or terrorists), which is difficult to monitor, thus presenting new challenges with respect to public security [
6]. Thus, legitimate eavesdropping by legitimate parties should be necessary to effectively discover and prevent the information transmitted between the suspicious users. Further, proactive eavesdropping has recently attracted much interest in research as an approach to improve eavesdropping performance.
1.1. Related Works
Conventional wireless security studies generally assume wireless communication is rightful, i.e., the eavesdropper is treated as an adversary, and aim to preserve their confidentiality and prevent malicious eavesdropping [
7,
8]. In the presence of a malicious eavesdropper, the network of point-to-point [
7], relaying [
8,
9], multi-user [
10,
11], and cognitive radio [
12] were investigated. In contrast, legitimate eavesdropping or wireless information surveillance is a paradigm shift of wireless security, where the monitor is regarded as a legitimate eavesdropper.
In general, there are two approaches for wireless information surveillance, including passive eavesdropping and proactive eavesdropping. With passive eavesdropping, the legitimate monitor only listens to the wireless channels of the suspicious users. This approach can’t change the eavesdropping performance. However, proactive eavesdropping can generally improve the eavesdropping performance via jamming or relaying. Note that there is not much research on the legitimate proactive eavesdropping in the literature, where the legitimate monitor eavesdrops a single suspicious link [
13,
14,
15,
16,
17,
18,
19,
20,
21], multiple suspicious links [
22,
23], or a suspicious relaying link [
24,
25,
26]. A legitimate surveillance scenario where a legitimate monitor aimed to eavesdrop a point-to-point suspicious communication link via jamming [
13] and cognitive jamming [
14,
15] was investigated, and the eavesdropping rate at the legitimate monitor was studied. In [
16], the author studied the legitimate surveillance system consisting of two legitimate monitors. In [
17,
18], the legitimate monitor was equipped with multiple antennae and acted as a fake relay to eavesdrop the suspicious transmitter–receiver pair. In [
19,
20,
21], the author studied a new spoofing approach to change the communicated information of the suspicious link. The work in [
22] investigated the wireless surveillance of multiple suspicious links, and maximized weighted sum eavesdropping rate of multiple suspicious links. The work in [
23] studied the wireless surveillance of multiple suspicious communication links and proposed a cooperative eavesdropping scheme. The eavesdropping rate [
24], the eavesdropping mode [
25], and the eavesdropping non-outage probability [
26] were studied where the legitimate monitor aims to eavesdrop a suspicious relaying communication link.
1.2. Contributions and Organizations
As a common point, all the above studies are under the Shannon capacity regime, where the length of the block is assumed to be infinite. The Shannon capacity is not achievable when the information transmitted in short packets. To our best knowledge, there is no research on the legitimate proactive eavesdropping under the finite blocklength regime. Therefore, this paper analyzes the performance of a legitimate surveillance system via proactive eavesdropping at the finite blocklength regime. In the system, there is a suspicious transmitter-receiver pair, which may be two stationary UAVs etc, and a legitimate monitor. The legitimate monitor operates in a full-duplex mode with simultaneous information reception and relaying. The main contributions are summarized as follows.
In this paper, under the finite blocklength regime, we analyze the channel coding rate of the eavesdropping link and the suspicious link. Meanwhile, we find that the legitimate monitor can still eavesdrop the information sent by the suspicious transmitter as the blocklength decreases, even when the eavesdropping is failed under the Shannon capacity regime. Moreover, we define a metric called the effective eavesdropping rate and analyze the monotonicity. From the analysis of monotonicity, the existence of a maximum effective eavesdropping rate for moderate or even high signal-to-noise (SNR) is verified. Finally, numerical results are provided and discussed. In the simulation, we also find that the maximum effective eavesdropping rate slowly increases with the blocklength, and the increment is almost negligible when the blocklength reaches a relatively large value.
The rest of this paper is organized as follows. The system model and assumptions are described in
Section 2.
Section 3 analyzes the performance of the legitimate surveillance system at finite blocklength. Numerical results are presented in
Section 4. Finally, the paper is concluded in
Section 5.
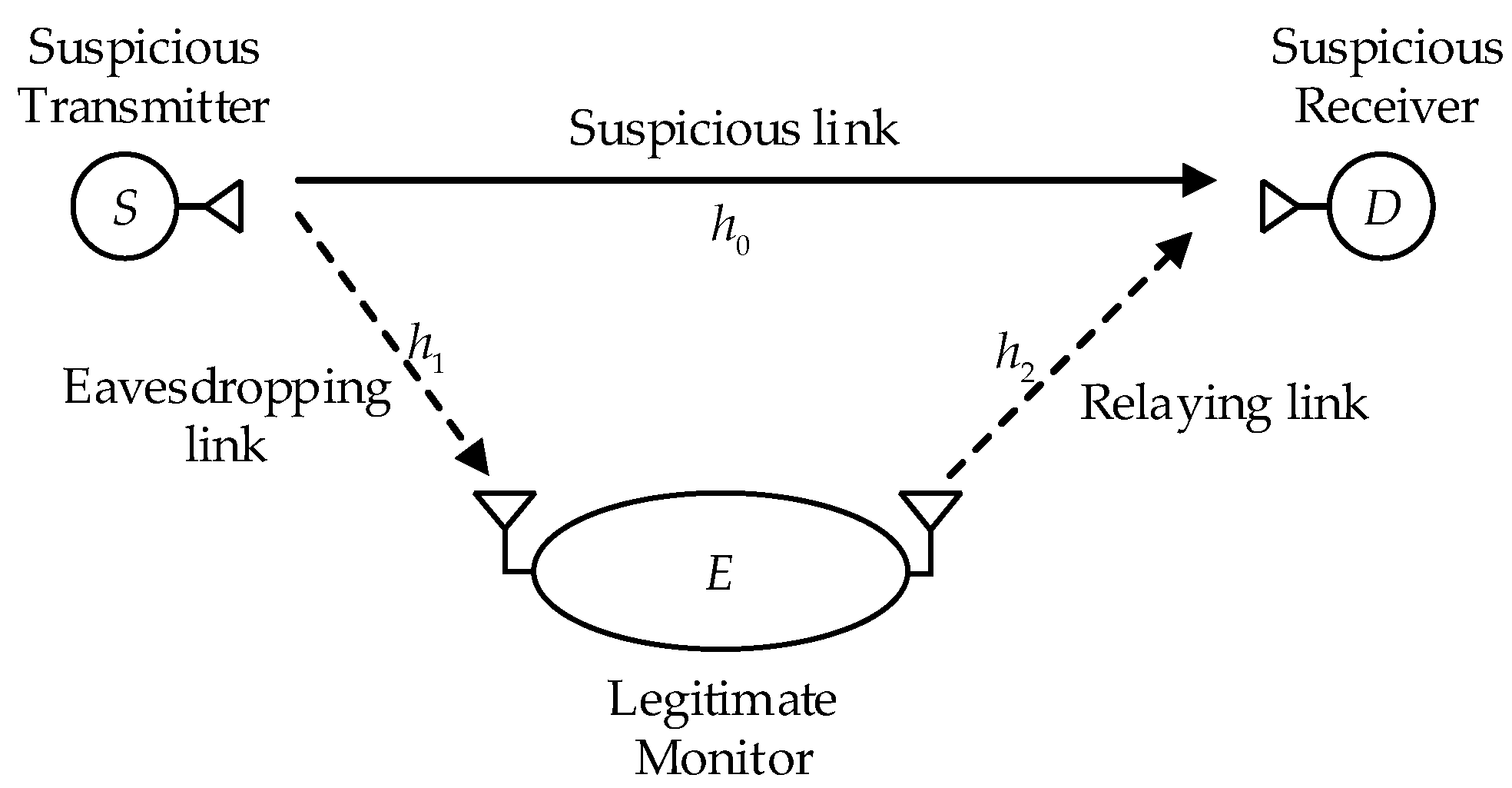
2. System Model and Assumptions
As shown in
Figure 1, we consider a legitimate surveillance system consisting of a suspicious transmitter-receiver pair (i.e.,
S-
D) and a full-duplex legitimate monitor
E.
S transmits information to
D during
n channel uses, in this way, we consider that each block spans over
n channel uses. We assume that both
S and
D are unaware of the presence of
E and the decode-and-forward (DF) relaying is adopted by
E. If
E decodes the block received from
S successfully, it forwards the block to
D, which aims to enhance eavesdropping the suspicious link.
S and
D are each equipped with a single antenna, and
E is equipped with two antennae, one for eavesdropping (receiving) and the other for relaying (transmitting).
S can adaptively adjust its transmission rate. The self-interference from the relaying antenna to the eavesdropping antenna at the legitimate monitor is assumed to be perfectly cancelled by using advanced analog and digital self-interference cancellation methods [
13]. DF can be assumed here as in [
8,
27]. In addition,
E can act as a fake relay and thus obtain the channel state information and the symbol format of the suspicious link, and synchronize with
S and
D [
19,
20].
We consider a Rayleigh quasi-static block-fading channel [
28], where fading process is considered to be constant over the transmission of a block and independently and identically distributed from block to block. Let
,
and
denote channel coefficients from the suspicious transmitter to the suspicious receiver, from the suspicious transmitter to the eavesdropping antenna of the legitimate monitor, and from the relaying antenna of the legitimate monitor to the suspicious receiver, respectively. The corresponding channel gains are defined as
,
and
. In addition, we assume that
E perfectly knows the channel state information of all links, which can be obtained by utilizing the methods given in the literature [
14,
17,
19,
20].
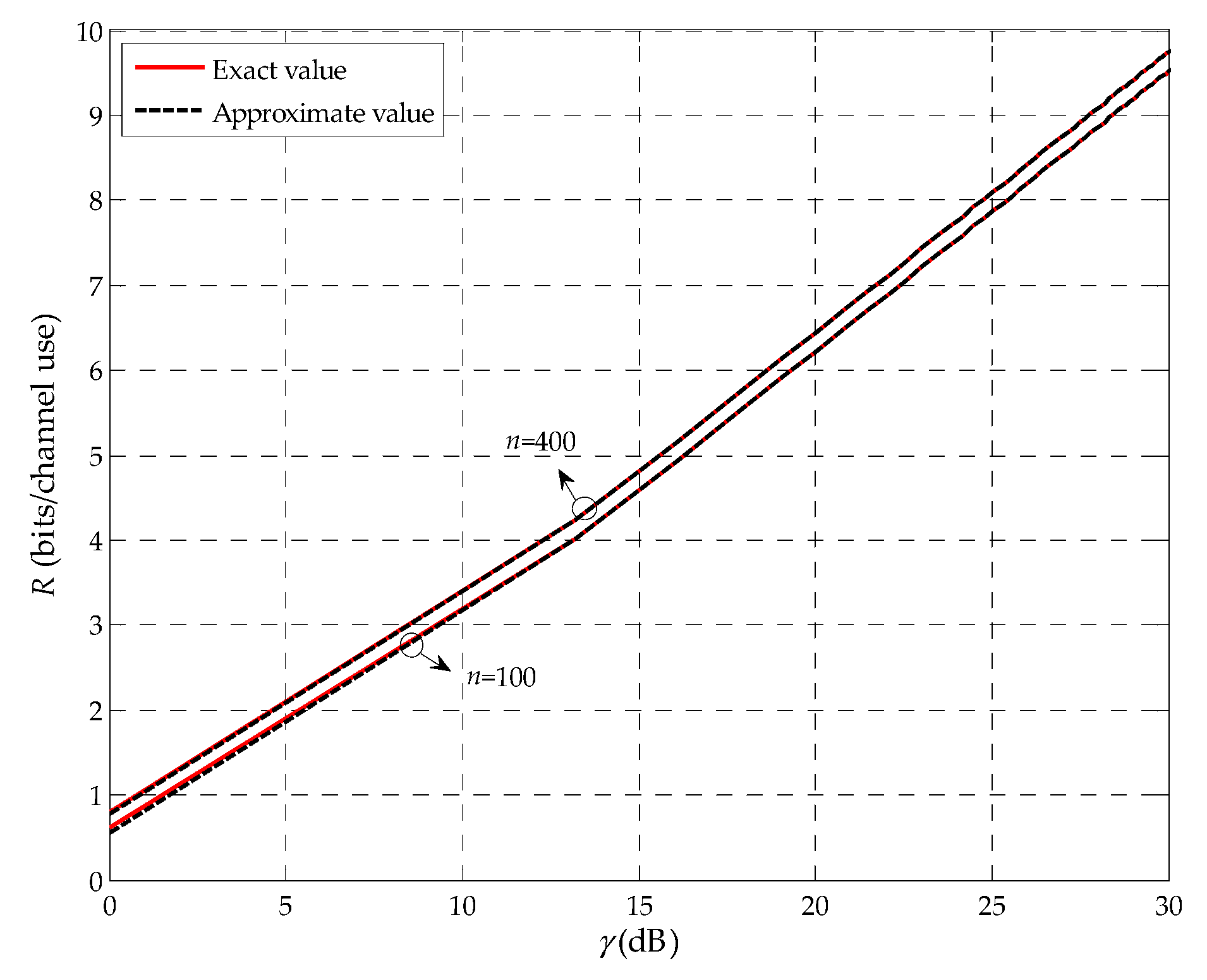
Channel Coding Rate for Finite Blocklength
For a given decoding error probability
, the channel coding rate
R (in bits per channel use) with blocklength
n is [
28,
29]
where
is the inverse
Q-function and as usual the
Q-function is given by
. In addition,
is Shannon capacity function of the SNR
. Note that Equation (1) is a very tight approximation when
, i.e., the difference from the exact value can be neglected [
28,
29]. Thus, we consider
in this paper and use equal sign in Equation (1). Based on the above results,
R can be transformed into
Equivalently, for a given channel coding rate
R, the decoding error probability
can be given by
3. Performance at Finite Blocklength
In this section, under the finite blocklength regime, we first analyze the performance of the legitimate surveillance system in terms of the channel coding rate of the eavesdropping link and the suspicious link in comparison with the Shannon capacity regime. Afterwards, we define a metric called the effective eavesdropping rate and analyze the monotonicity. From the analysis of monotonicity, the existence of a maximum effective eavesdropping rate for moderate or even high SNR is also verified.
3.1. Analysis of Channel Coding Rate
According to Equation (2), the channel coding rate of the eavesdropping link can be obtained as
where
,
is the SNR at
E,
is the transmit power at
S,
is the power of noise at
E, and
is the decoding error probability at
E. Likewise, the effective channel coding rate of the suspicious link can be obtained as
where
,
is the effective SNR at
D,
is the transmit power at
E,
is the power of noise at
D, and
is the decoding error probability at
D.
E can act as a fake relay and alter the effective channel of the suspicious link from
S to
D [
17]. Thus, we use effective channel coding rate, which includes the suspicious link and the relaying link.
results from the error probability of each link and is given by
where
and
are the decoding error probabilities of the suspicious link and the relaying link, respectively.
Since
, it is straightforward to know that
. Thus, we immediately have
. Besides we consider that
, in this way, we have
. In summary, we can obtain as follows
It can be known that when . So according to Equation (3), . In this way, we immediately have . Thus, we can derive from Equation (7).
When , we can obtain . But, we consider is more reasonable. The reasons mainly include the following: decreases as the transmission rate of E decreases; decreases as the transmit power of E increases; meanwhile, as the transmit power of E increases, increases. Overall, can be controlled at a very small value by reducing the transmission rate of E or increasing the transmit power of E.
In general, under the Shannon capacity regime, the Shannon capacity of the eavesdropping link is
, accordingly, the effective Shannon capacity of the suspicious link is
, as in [
17]. Next, we give the following proposition.
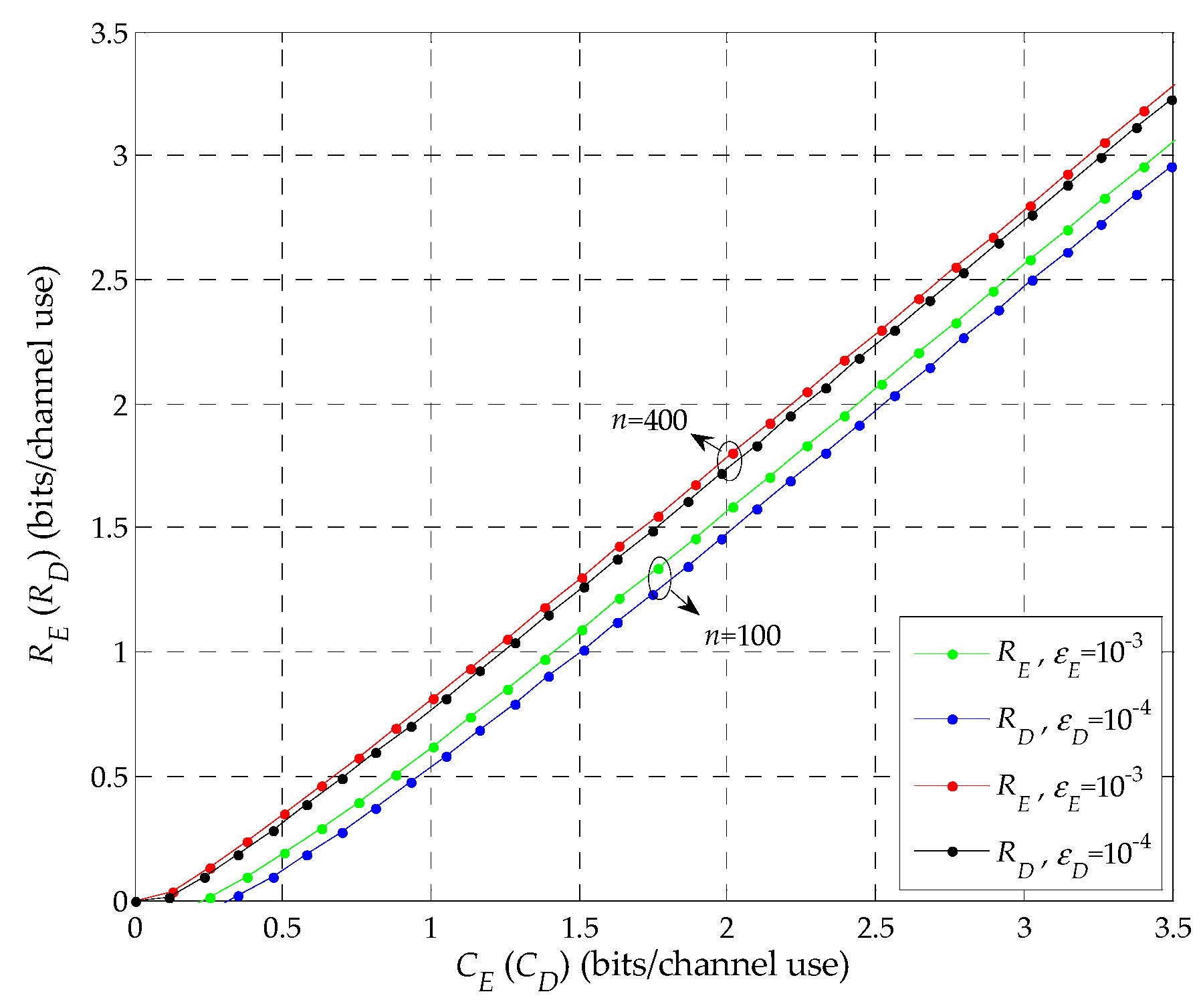
Proposition 1: when , i.e., under the finite blocklength regime, E can eavesdrop the information sent by S the same as the condition under the Shannon capacity regime.
Proof: See detailed proof of Proposition 1 in
Appendix A. The corresponding simulation is shown in
Figure 2. □
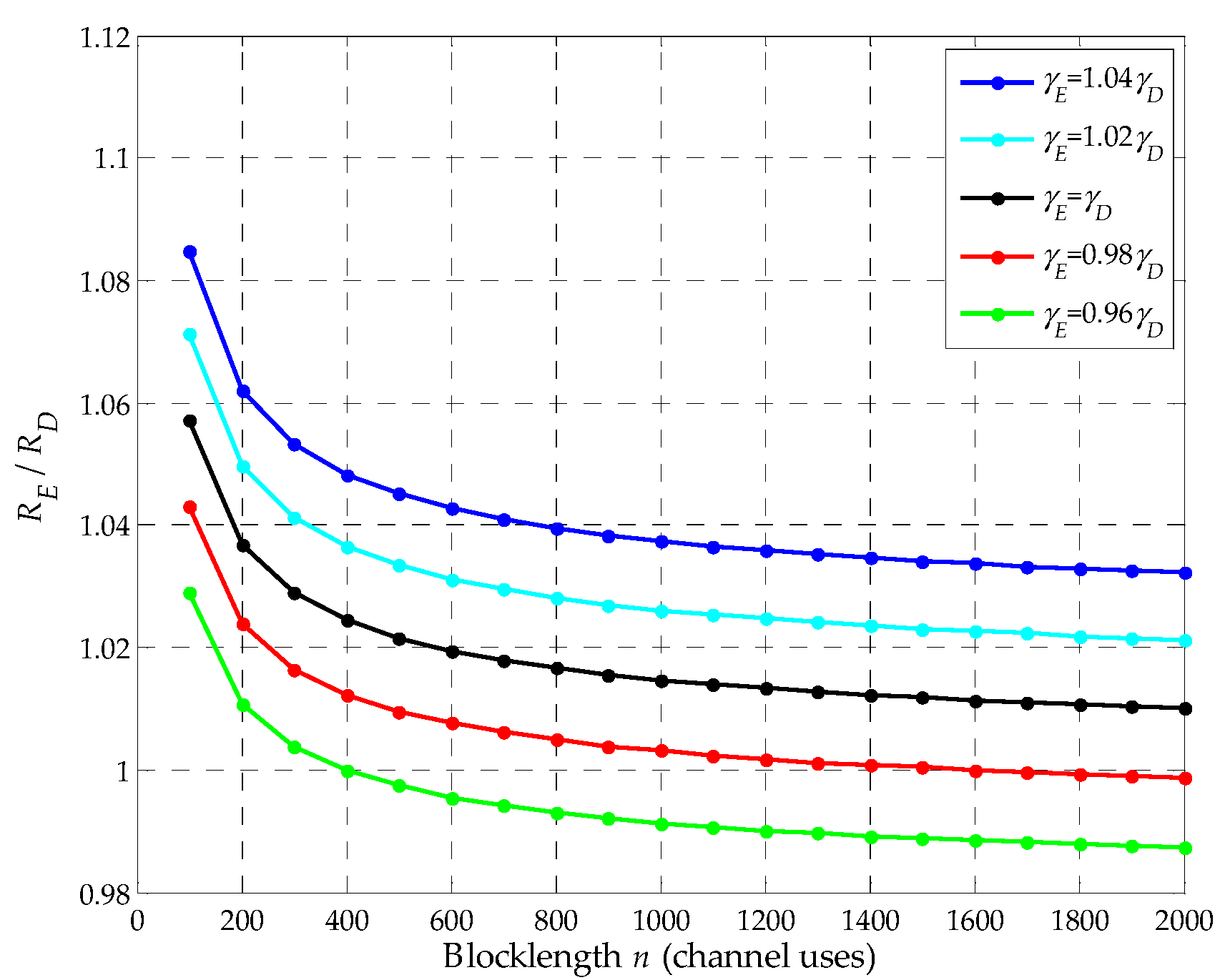
Next, we give the following proposition, which is different from the results under the Shannon capacity regime where the legitimate monitor can eavesdrop the information sent by the suspicious transmitter only when .
Proposition 2: E can still eavesdrop the information sent by S as n decreases even though in some conditions of, i.e., when n decreases,can still be achieved even in some conditions of.
Proof: Based on Equation (A1), it is known that
when
. Further, according to Equation (A1), the value of
decreases with
n because
n is in the denominator. Therefore, the value of
increases as
n decreases. In this way, in some conditions of
,
can still be achieved as
n decreases, which is investigated by simulation in
Figure 3. Thus,
E can still eavesdrop the information sent by
S as
n decreases even though in some conditions of
.□
3.2. Analysis of Effective Eavesdropping Rate
When , there is always a potential chance, such as increasing the relaying power of the legitimate monitor, to improve the eavesdropping rate by increasing until , which means that reaches the optimal value. Then, any more improvement of will lead to , which means the failure of eavesdropping. So, when the suspicious link is eavesdropped with optimal eavesdropping rate, the relation of is always realized.
Next, under the finite blocklength regime, we define a metric called effective eavesdropping rate to analyze the system performance. Mathematically, the effective eavesdropping rate is given by
where
is the eavesdropping rate, and
. According to Equation (3), we can reformulate Equation (8) as a function of
as
where
, and
. Next, we study Equation (9), for which we have the following lemma.
Lemma 1: Under the finite blocklength regime, the effective eavesdropping rate is monotonically increasing over and monotonically decreasing over for moderate or even high SNR, where is the eavesdropping rate that maximizes the effective eavesdropping rate .
Base on the proof of Lemma 1, we prove that there exists a maximum effective eavesdropping rate,
, corresponding to
. However, unfortunately, the general closed-form for
cannot be derived. Therefore, it is investigated by simulation in
Figure 4. Furthermore, we consider the optimal eavesdropping rate
, where
is the channel coding rate of the suspicious link with no relaying power. Here, we first simply explain it as follows. We consider the eavesdropping rate
. First, consider the case when
. In this case, the legitimate monitor should use a positive relaying power to facilitate the eavesdropping, such that the effective channel coding rate
of the suspicious link is improved from
to
, thus, we have
and the optimal effective eavesdropping rate
. Next, consider
. In this case, we have
, which means that no relaying is required for the legitimate monitor to obtain its optimal effective eavesdropping rate.
4. Numerical Results
Next, we present numerical results obtained by simulations for the considered legitimate surveillance system. We consider the Rayleigh quasi-static block-fading channel and set the channel coefficients , and to be independent circularly symmetric complex Gaussian random variables with mean zero and variance 1. Here, the transmit powers are normalized over the receiver noise powers such that we can set the noise powers at E and D to be . Unless otherwise stated, we set the transmit power at S as dB. We assume that the transmit power is large enough to facilitate the eavesdropping.
In
Figure 2,
with
and
with
are shown for given blocklength
n and error probability
. Here, the transmit power
is set to be 2 dB. Without loss of generality,
n is set to be 100 and 400 channel uses,
and
are set to be 10
−3 and 10
−4, respectively. As shown in the figure, when
, it is clear that
. Meanwhile, we can note that
increases with
, and that
also increases with
. For example, when
n is 400 channel uses, for
,
, while for
and
,
, so
when
. Thus, under the finite blocklength regime,
E can eavesdrop the information sent by
S the same as the condition under the Shannon capacity regime, which is in line with Proposition 1.
In
Figure 3, we plot the ratio of
and
with
n when
,
,
,
and
, where
and
represent some conditions of
. We set
and
to be 10
−3 and 10
−4, respectively. As shown in the figure, we can note that when
,
and
decreases with
n. Meanwhile, in comparison to
,
can still be larger than or equal to 1 when
and
as shown in the figure. For example, when
, the blocklengths
n of the red and green curves are respectively around 1400, 400 channel uses, thus,
n decreases. So even in some conditions of
,
E can still eavesdrop the information sent by
S as
n decreases, which demonstrates proposition 2.
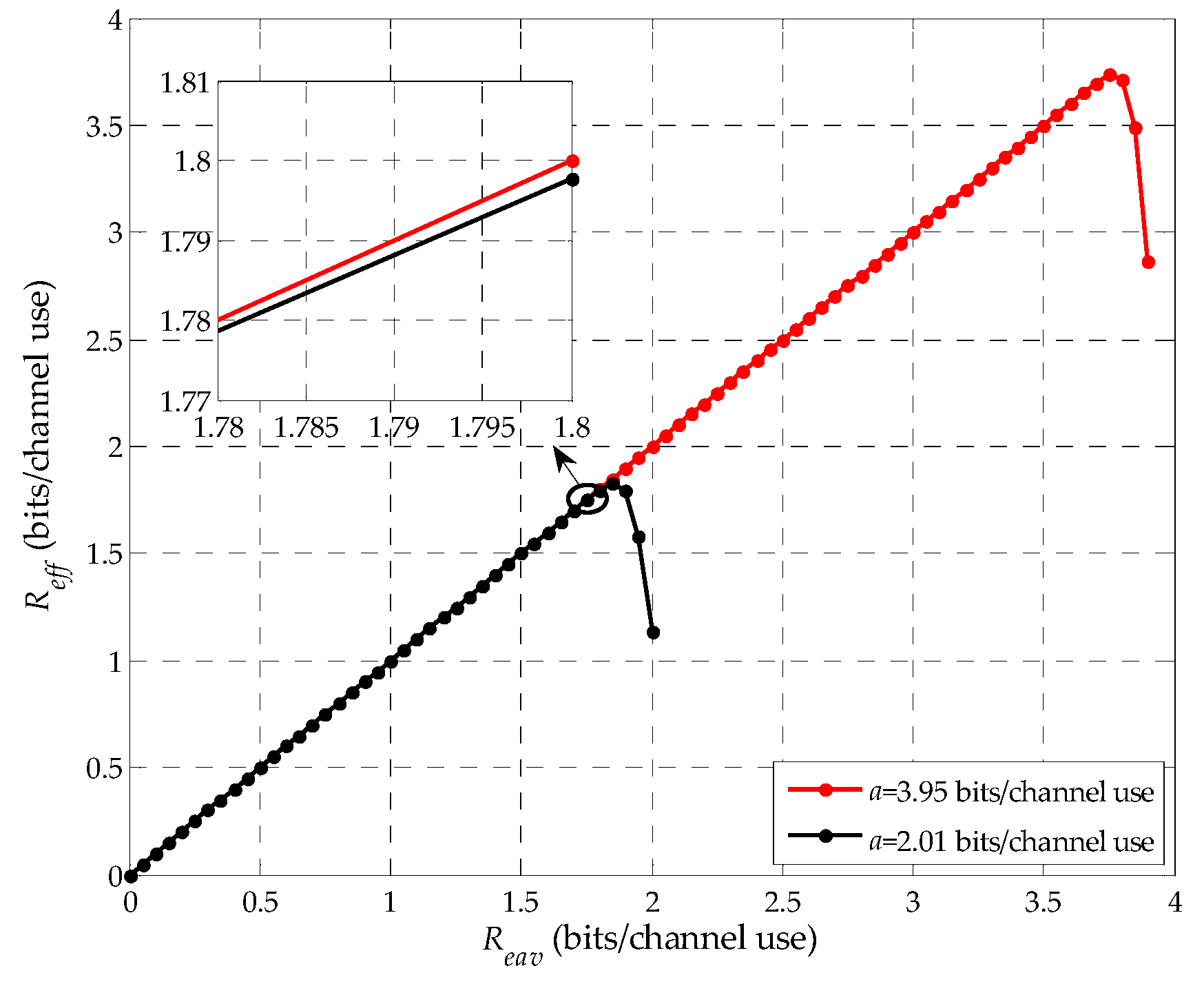
Figure 4 shows the effective eavesdropping rate
with the eavesdropping rate
at
E given in Equation (9). Here, the results are obtained when
a is 2.01 and 3.95 bits per channel use, thus, we can obtain that
is 4.81 dB and 11.6 dB, which are supposed to moderate SNRs. Without loss of generality, we set
n to be 400 channel uses. As shown in the figure, we can note that
is first monotonically increasing and then monotonically decreasing and there is a maximum value of the eavesdropping rate,
, which is corresponding to the maximum value of the effective eavesdropping rate,
. For example,
is around 3.7 when
is 11.6 dB. Moreover, we can also note that
is larger when
is 11.6 dB compared with
is 4.81 dB. Thus, for a given blocklength
,
increases with
for the same
. So far, the Lemma 1 is demonstrated by simulation.
In
Figure 5, we plot the maximum effective eavesdropping rate
with the blocklength
n. Here, corresponding to
Figure 4, the results are obtained when
a is 2.01 and 3.95 bits per channel use. As show in
Figure 5, we can clearly note that
increases with
n. We can also note that the increments of the curves are almost negligible when
n reaches a relatively large value. For example, the increment of the red curve is very small in the range of 1500 channel uses to 2000 channel uses. Moreover, it is easy to see that
increases with
a, thus,
increases with
.
5. Conclusions
In this paper, under the finite blocklength regime, we analyze the performance of a legitimate proactive eavesdropping system, which consists of a suspicious transmitter–receiver pair and a legitimate monitor. We consider that the legitimate monitor operates in a full-duplex mode with simultaneous information reception and relaying. Moreover, we analyze the channel coding rate of the eavesdropping link and the suspicious link. We find that the legitimate monitor can still eavesdrop the information sent by the suspicious transmitter as the blocklength decreases, even when the eavesdropping is failed under the Shannon capacity regime. Furthermore, we define a metric called effective eavesdropping rate and analyze the monotonicity. From the analysis of monotonicity, the existence of a maximum effective eavesdropping rate for moderate or even high SNR is verified. Finally, numerical results are provided and discussed. In the simulation, we also find that the maximum effective eavesdropping rate slowly increases with the blocklength, and the increment is almost negligible when the blocklength is relatively large.