Data Storage Mechanism Based on Blockchain with Privacy Protection in Wireless Body Area Network
Abstract
:1. Introduction
- (1)
- Unauthorized access: The unauthorized attackers hack into the WBAN and steal user data. Such attacks will violate users’ privacy, for example, if the attacker sells users’ information to an insurance company.
- (2)
- Tampering with the messages: The attacker modifies signals in the WBAN so that the data collector receives fake users’ data. This will affect the safety of users, for example, if the user is a patient, and the patient data received by the doctor is false data, which would lead to the wrong treatment by the doctor.
- Blockchain: We use blockchain to store the WBAN user’s data which can prevent the data from being tampered with.
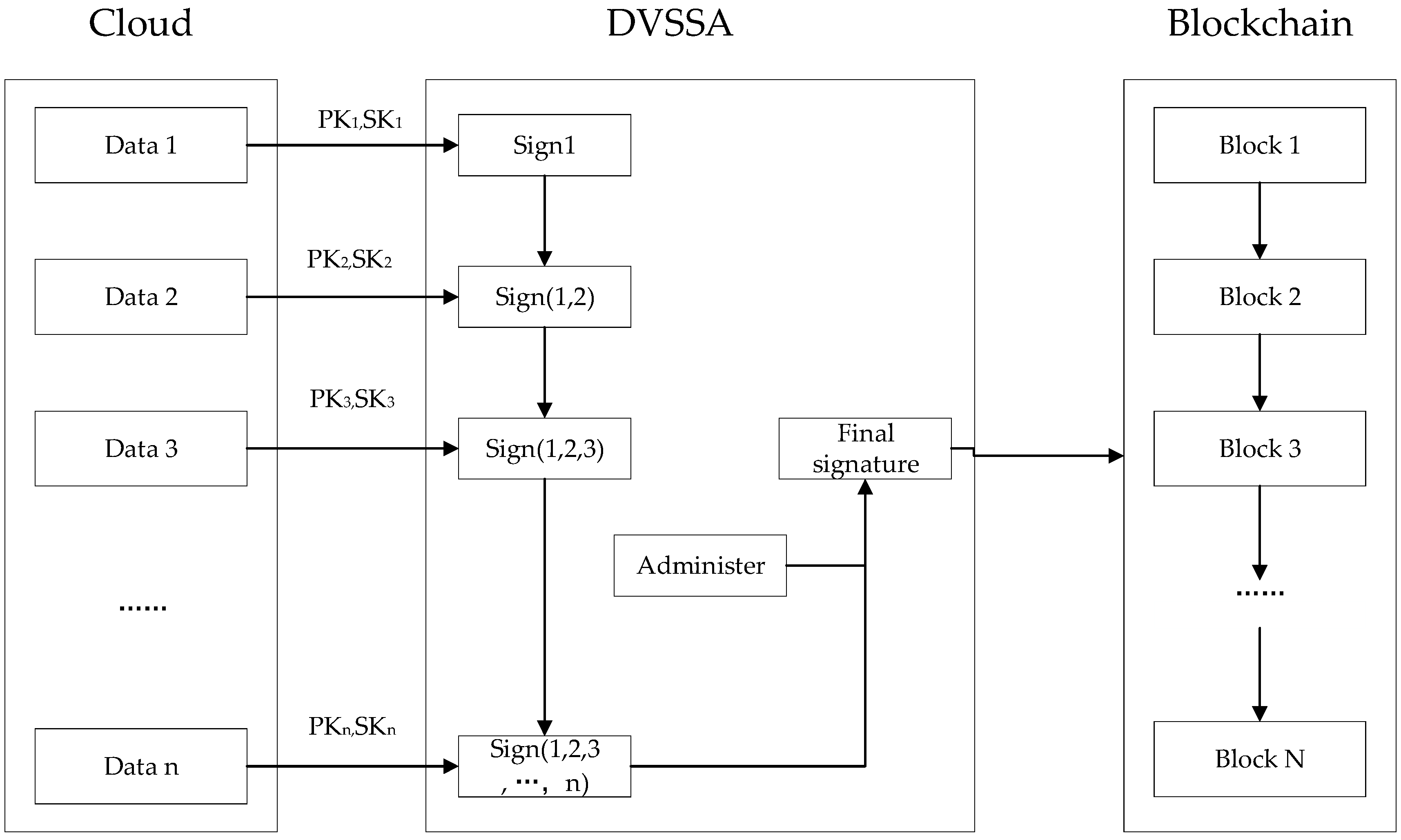
- The DVSSA scheme: We propose a sequential aggregate signature scheme with a designated verifier. It ensures that the user’s data can only be viewed by the administrator, and in other hands it can be compressed to the size of the blockchain storage space, which solves the illegal access problem.
2. Related Work
2.1. Wireless Body Area Network
2.1.1. Network Architecture
2.1.2. Wireless Communication Technique in WBAN
2.1.3. Management System and Database
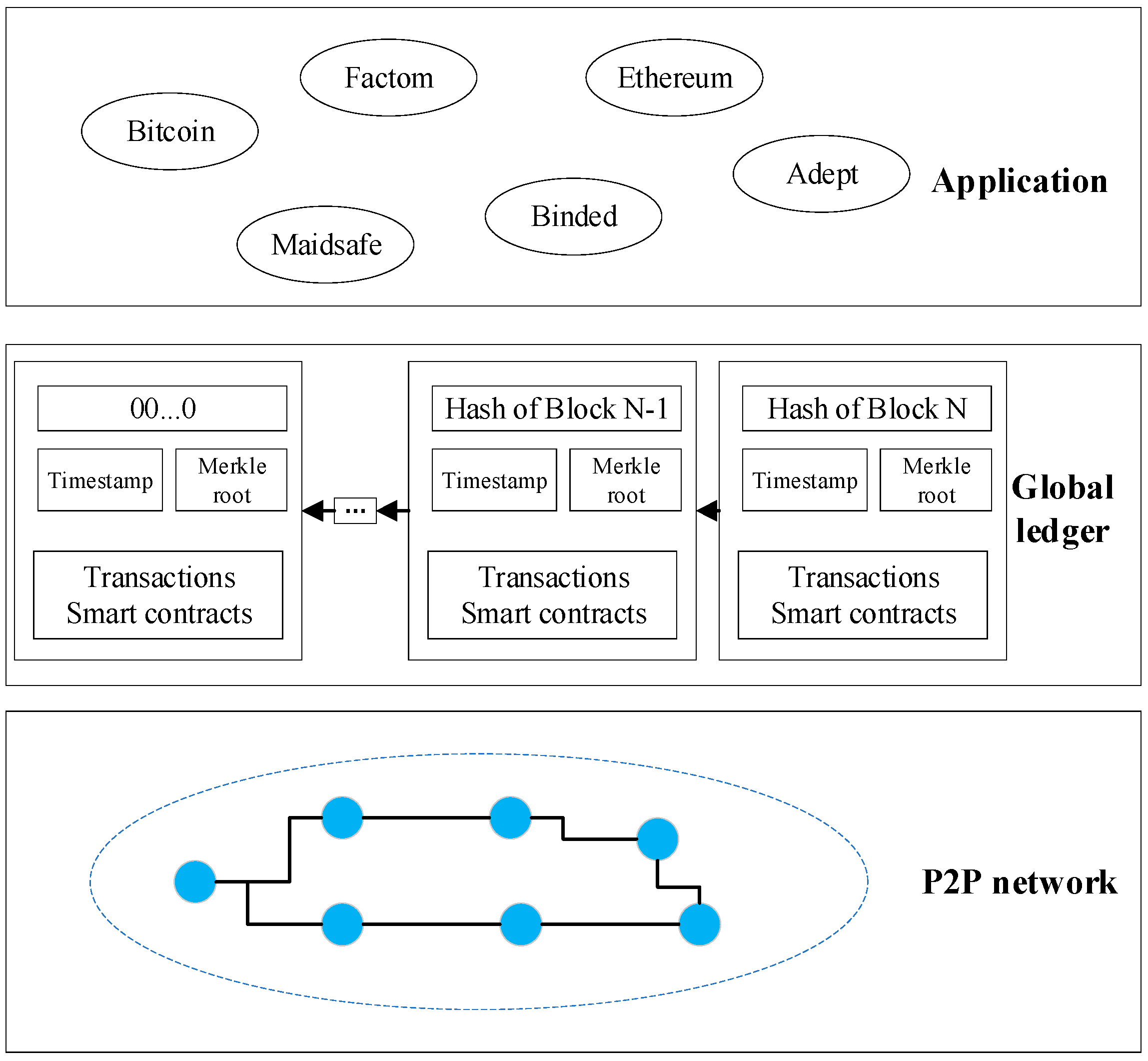
2.2. Blockchain
2.2.1. Structure of Blockchain
2.2.2. Key Characteristics of the Blockchain
- (1)
- Autonomy: One important feature of blockchain is that there is no separate entity control or control network. In the public settings, any node can sign and publish transactions, and if they are accepted, the blockchain will check other nodes in their decentralized network at any time. In addition, everyone can join the consensus process to extend new blocks to the blockchain.
- (2)
- Distributed: A blockchain system is built on a P2P network to which the source node broadcasts each signed single row of transactions. The adjacent peer then validates these incoming transactions: the valid transaction is forwarded further, and the invalid transaction is discarded. Eventually, these transactions can be extended to the entire P2P network. The system can process notifications and synchronizes networks for newly generated blocks.
- (3)
- Non-tampering: All valid blocks and transactions recorded in the global ledger are virtually immutable due to the need for validation by other nodes and traceability of changes. Furthermore, the entire global ledger is synchronized between blockchain nodes according to a consensus mechanism, giving users greater confidence in the authenticity and accuracy of the data in the blockchain.
- (4)
- Contractual: The process of consensus (for example, mining or voting) depends on the state of the data in question. The consensus is reached through the implementation of rules, i.e., the blockchain of the smart contract, for example, does not have any central authorization. The rules defined by these codes ensure that actions in any currency are executed promptly and correctly without human intervention.
3. Problem Statement
3.1. Security Requirements of WBAN
- Data confidentiality: In WBAN, data confidentiality is one of the most important problems; it can protect the user from data leaks. In medical applications, when the node collects and sends sensitive information to the coordinator, the enemy can eavesdrop on some key information in the communication, which will reveal the patient’s privacy. This kind of eavesdropping may bring serious damage to the patient. The traditional method is to encrypt the data and then retransmit to ensure the communication security of the external sensor node and the network coordinator, and only allow the receiver to be authorized to decrypt the WBAN node, but this is difficult to implement for the sensor node with poor computational performance.
- Data integrity: The confidentiality of the data does not guarantee that the data will not be tampered with. After the data is stolen by the opponent, it can be tampered or destroyed by adding or reducing data segments, and then the data will be sent to the network coordinator. Vital information can be compromised, which can be very dangerous to users. The data integrity mechanism ensures that the data transmitted between BSN and BSNC (Body sensors network coordinators) is not changed by the adversary. The sender uses a one-way algorithm to compute the MAC frame, generates the integrity code for the frame, and sends it attached to the packet. The receiver uses the same process to calculate the MAC frame and compares the calculated result with the one given by the sender, to judge whether the data was maliciously tampered with in the sending process.
- Data authentication: Data authentication is necessary for medical and non-medical applications. It enables the BSN and BSNC to verify that data is sent by trusted sensor nodes. This prevents hostile parties from sending false messages to trick BSN and BSNC data authentication.
- Data freshness: The freshness of the data can prevent the retransmission attack. The hostile party may capture the frame in the transmission process and resend the data after a period of delay to achieve the purpose of confusing the BSNC.
3.2. Possible Security Threats and Attacks on WBAN
3.3. Security Solution for WBAN
4. System Model
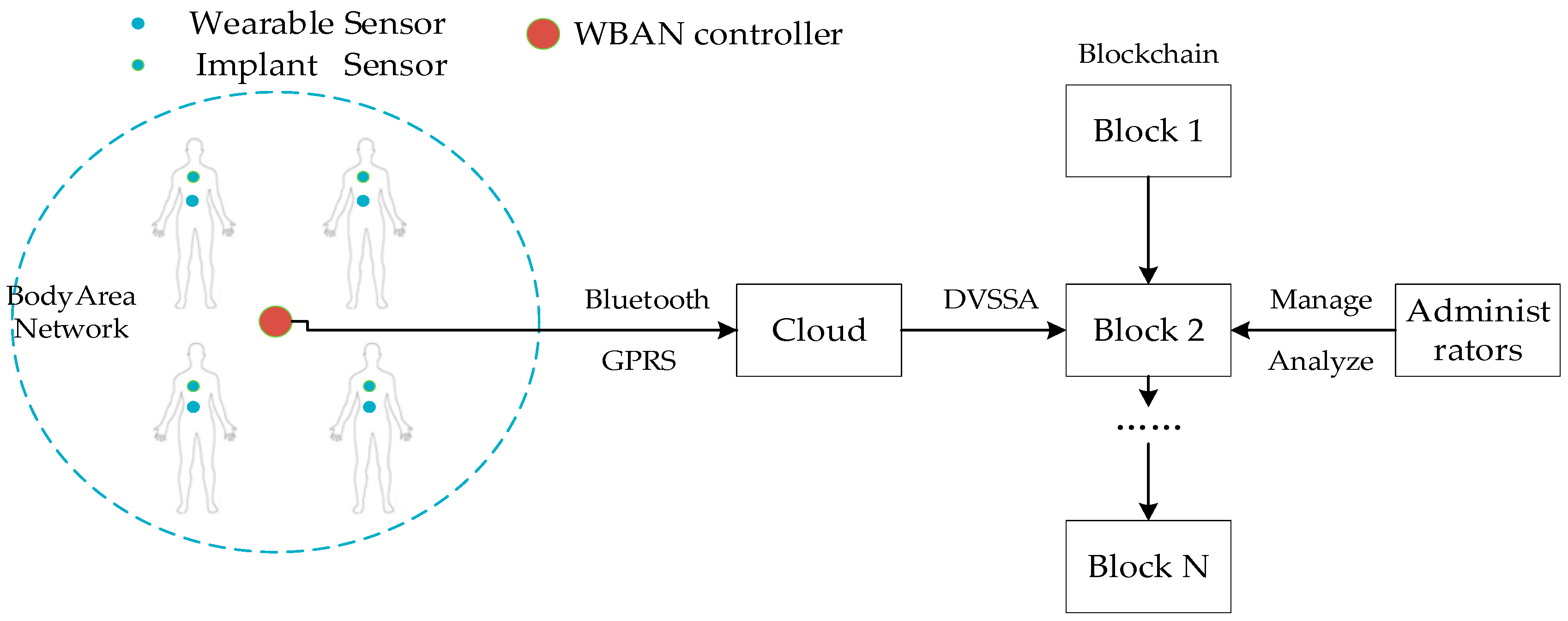
4.1. WBAN Model
- (1)
- WBAN: the WBAN consists of a WBAN controller and several (implantable or wearable) devices. These devices are often sensors that monitor important body parameters or movements and control the body by providing life support, visual/auditory feedback, and so forth. The WBAN device communicates with the WBAN controller directly or through multi-hop communication. The WBAN controller communicates not only with the WBAN device but also with Cloud. Also, the close-range WBAN controller can form a self-organizing network using a wireless personal area network (WPAN) technology.
- (2)
- External administrator: external entities are mainly doctors or hospitals that we called administrators. Administrators can view the data of WBAN users stored in the blockchain and manage and analyze the data.
- (3)
- Cloud: cloud servers can provide the function of cloud storage service. Users can easily access data at anytime and anywhere through any internet-connected device connected to the cloud. More importantly, the cloud server cluster has a large number of storage resources, which can provide infinite storage space for the edge networks with limited resources.
4.2. Cloud-Blockchain Model
4.2.1. The Advantage of Blockchain Storage
4.2.2. The Defect of Blockchain Storage
4.2.3. Our Solution
4.3. Data Validation Model
5. Sequential Aggregate Signature with Designated Verifier
5.1. Preliminaries
5.1.1. Bilinear Pairings
- Bilinear: ∀, there is .
- Non-degeneracy: .
- Computability: There is an efficient algorithm to compute .
5.1.2. Bilinear Diffie-Hellman Problem (BDH)
5.1.3. Sequential Aggregate Signature Model
5.2. Our Scheme
5.3. Security Proof
- Setup. B First, get Pk = () of the challenger, then set the public parameter , public key , initializes the list of keys and sets it to an empty set.
- Certification Queries. The adversary A provides a key pair and adaptability requires public key authentication. B checks the validity of the key pair and adds it to the key list.
- Signature Queries. The adversary A provides the message chain , the sequential aggregate signature under the public key and a new message M and public key , then B execute the signature query as follows:
- (1)
- Check the validity of the signature , and check that each component of exists in the key list.
- (2)
- Ask the signature oracle to get the of M, and the signed public keys is .
- (3)
- For each message , run DVSSAggSign algorithm to get the sequential aggregate signature for the designated verifier about the message , and send it to A.
- Output. The adversary A outputs the forged sequential aggregate signature for the specific verifier about the message chain . The public key is . We assume that , the forgery process of algorithm B is as follows:
- (1)
- B first runs the sequential aggregate validation algorithm for the designated verifier, then verifies the validity of the signature and at the same time confirms that the challenge public key must be in the and must not have been questioned by adversary A about the signature oracle.
- (2)
- In , , retrieve the private key from the key list , then compute:
- (3)
- Output the about .Furthermore, we can prove the correctness of of which is forged by the algorithm B:
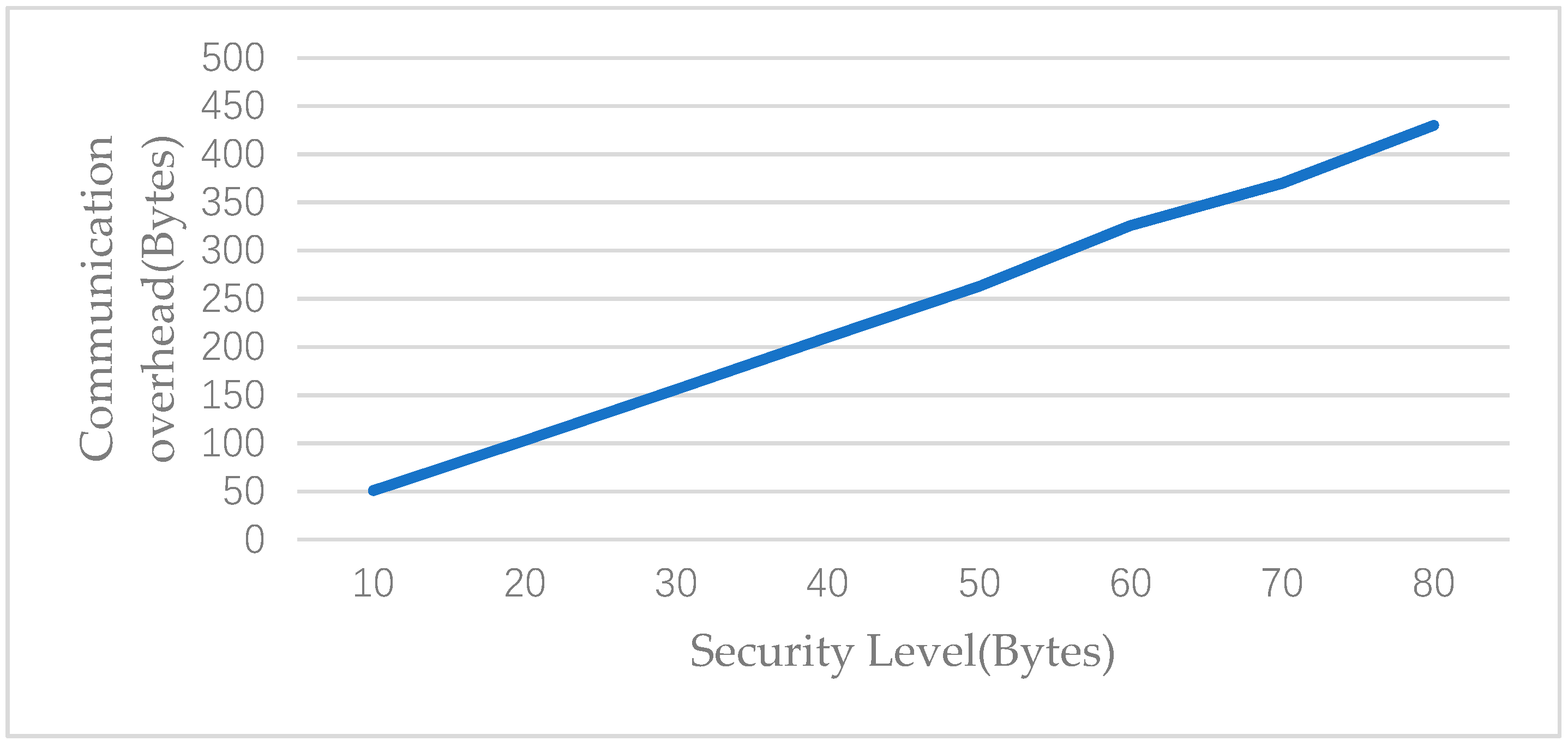
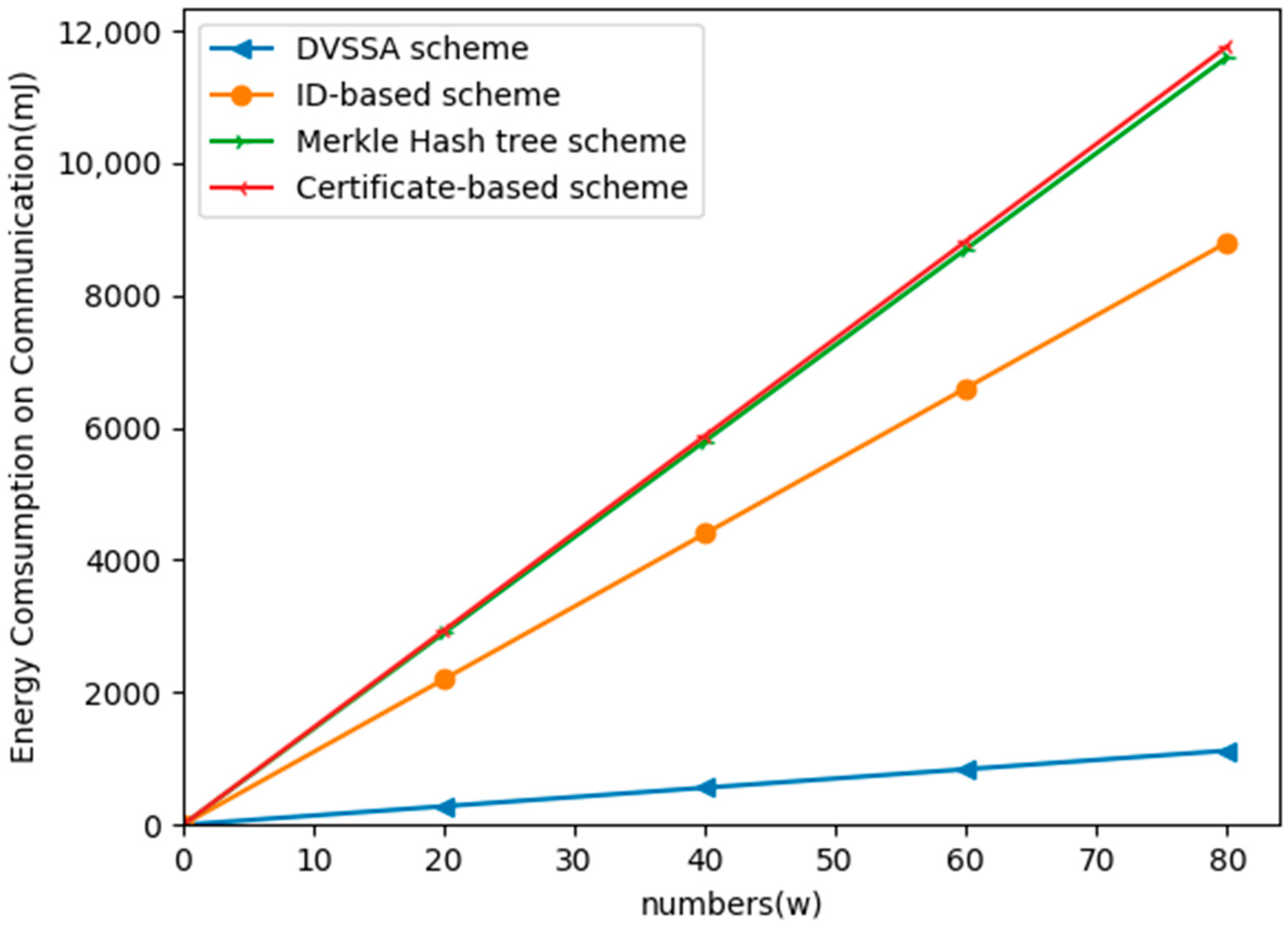
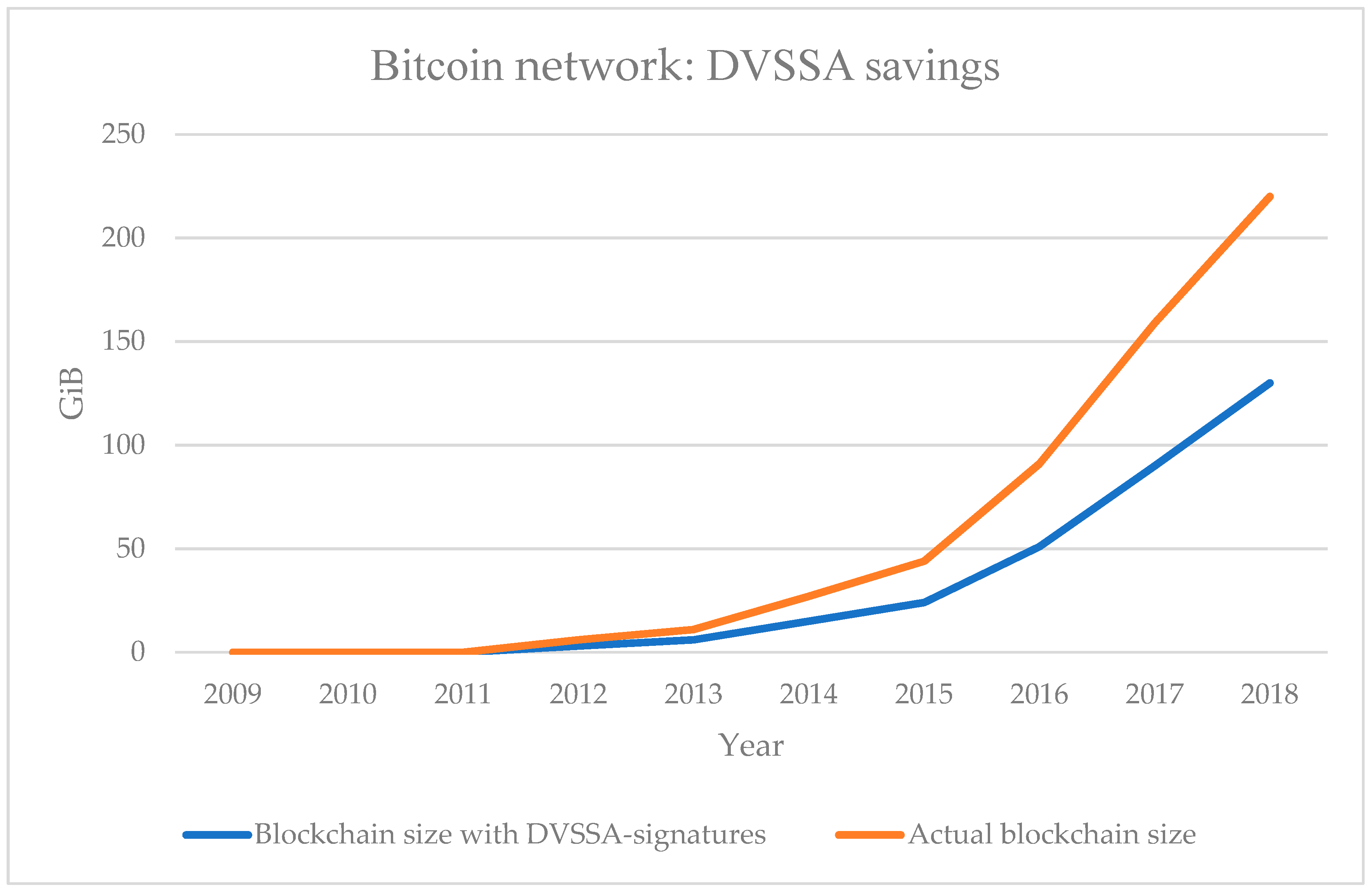
6. Experiment
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Arvind, D.K.; Bates, A. The speckled golfer. In Proceedings of the BodyNets 2008, Tempe, AZ, USA, 13–15 March 2008. [Google Scholar]
- Baker, C.R.; Armijo, K.; Belka, S.; Benhabib, M.; Bhargava, V. Wireless sensor networks for home healthcare. In Proceedings of the International Conference on Advanced Information Networking and Applications Workshops, Niagara Falls, ON, Canada, 21–23 March 2007; pp. 832–837. [Google Scholar]
- Barth, A.; Wilson, S.; Hanson, M.; Powell, H.; Unluer, D.; Lach, J. Body-coupled communication for body sensor networks. In Proceedings of the 3rd International Conference on Body Area Networks, Tempe, AZ, USA, 13–15 March 2008. [Google Scholar]
- Wang, J.; Cao, J.Y.; Ji, S.; Park, J.H. Energy efficient cluster-based dynamic routes adjustment approach for wireless sensor networks with mobile sinks. J. Supercomput. 2017, 73, 3277–3329. [Google Scholar] [CrossRef]
- Fleury, A.; Vacher, M.; Noury, N. SVM based multimodal classification of activities of daily living in health smart homes: Sensors, algorithms and first experimental results. IEEE Trans. Inf. Technol. Biomed. 2008, 14, 274–283. [Google Scholar] [CrossRef] [PubMed]
- Delgado, O.; Fuster, A.; Sierra, J.M. A lightweight authentication scheme for wireless sensor networks. Ad Hoc Netw. 2011, 9, 727–735. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Arun, K.S.; Kim, H.Y. An improved routing schema with special clustering using PSO algorithm for heterogeneous wireless sensor network. Sensors 2019, 19, 671. [Google Scholar] [CrossRef] [PubMed]
- Wang, J.; Gao, Y.; Liu, W.; Wu, W.B.; Lim, S.J. An asynchronous clustering and mobile data gathering schema based on timer mechanism in wireless sensor networks. Comput. Mater. Contin. 2019, 58, 711–725. [Google Scholar] [CrossRef]
- Li, M.; Yu, S.; Guttman, J.; Lou, W.; Ren, K. Secure ad-hoc trust initialization and key management in wireless body area networks. ACM Trans. Sens. Netw. 2013, 9, 18. [Google Scholar] [CrossRef]
- Al Ameen, M.; Liu, J.; Kwak, K. Security and privacy issues in wireless sensor networks for healthcare applications. J. Med. Syst. 2012, 36, 93–101. [Google Scholar] [CrossRef] [PubMed]
- Yin, C.Y.; Xi, J.W.; Sun, R.X.; Wang, J. Location privacy protection based on differential privacy strategy for big data in industrial internet of things. IEEE Trans. Ind. Inform. 2018, 14, 3628–3636. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.B.; He, D.B.; Wang, P. On the challenges in designing identity-based privacy-preserving authentication schemes for mobile devices. IEEE Syst. J. 2018, 12, 916–925. [Google Scholar] [CrossRef]
- He, D.B.; Neeraj, K.; Muhammad, K.; Wang, L.N.; Shen, J. Efficient privacy-aware authentication scheme for mobile cloud computing services. IEEE Syst. J. 2018, 12, 1621–1631. [Google Scholar] [CrossRef]
- Li, X.; Liu, S.P.; Wu, F.; Saru, K.; Joel, J.P. Privacy preserving data aggregation scheme for mobile edge computing assisted IoT applications. IEEE Internet Things J. 2018. [Google Scholar] [CrossRef]
- Hu, C.; Zhang, N.; Li, H. Body area network security: A fuzzy attribute-based signcryption scheme. IEEE J. Sel. Areas Commun. 2013, 31, 37–46. [Google Scholar] [CrossRef]
- Kumar, A.; Fischer, C.; Tople, S. A traceability analysis of Monero’s blockchain. In Proceedings of the International Conference on European Symposium on Research in Computer Security, Oslo, Norway, 11–15 September 2017; Springer: Berlin, Germany, 2017; pp. 153–173. [Google Scholar]
- Wang, J.; Cao, J.Y.; Sherratt, S.D.; Park, J.H. An improved ant colony optimization-based approach with mobile sink for wireless sensor networks. J. Supercomput. 2018, 74, 6633–6645. [Google Scholar] [CrossRef]
- Moser, M.; Soska, K.; Heilman, E. An empirical analysis of traceability in the Monero blockchain. In Proceedings of the 18th International Conference on Privacy Enhancing Technologies, Barcelona, Spain, 24–27 July 2018; Springer: Berlin, Germany, 2018; pp. 143–163. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: http://bitcoin.org/bitcoin.pdf (accessed on 25 May 2019).
- Ren, Y.J.; Liu, Y.P.; Ji, S.; Arun, K.; Wang, J. Incentive mechanism of data storage based on blockchain for wireless sensor networks. Mob. Inf. Syst. 2018, 2018, 6874158. [Google Scholar] [CrossRef]
- Ren, Y.J.; Leng, Y.; Cheng, Y.P.; Wang, J. Secure data storage based on blockchain and coding in edge computing. Math. Biosci. Eng. 2019, 16, 1874–1892. [Google Scholar] [CrossRef]
- Wang, J.; Ju, C.W.; Gao, Y.; Arun, K.S.; Kim, G.J. A PSO based energy efficient coverage control algorithm for wireless sensor networks. Comput. Mater. Contin. 2018, 56, 433–446. [Google Scholar]
- Polastre, J.; Szewczyk, R.; Culler, D. Telos: Enabling ultra-low power wireless research. In Proceedings of the Information Processing in Sensor Networks (IPSN 2005), Los Angeles, CA, USA, 24–27 April 2005; pp. 364–369. [Google Scholar]
- Yu, J.; Tao, D.C.; Wang, M.; Rui, Y. Learning to rank using user clicks and visual features for image retrieval. IEEE Trans. Cybern. 2015, 45, 767–779. [Google Scholar] [CrossRef] [PubMed]
- Yong, S.; Baldus, H.; Espina, J. The simulation method of the galvanic coupling intrabody communication with different signal transmission paths. IEEE Trans. Instrum. Meas. 2011, 60, 1257–1266. [Google Scholar]
- Falck, T.; Baldus, H.; Espina, J. Plug’n play simplicity for wireless medical body sensors. Mob. Netw. Appl. 2007, 12, 143–153. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Yin, X.; Li, F.; Kim, H.Y. An enhanced PEGASIS algorithm with mobile sink support for wireless sensor networks. Wirel. Commun. Mob. Comput. 2018, 2018, 9472075. [Google Scholar] [CrossRef]
- Yin, Y.Y.; Song, A.H.; Gao, M.; Xu, Y.S.; Wang, S.P. QoS prediction for web service recommendation with network location-aware neighbor selection. Int. J. Softw. Eng. Knowl. Eng. 2016, 26, 611–632. [Google Scholar] [CrossRef]
- Yu, J.; Yang, X.K.; Gao, F.; Tao, D.C. Deep multimodal distance metric learning using click constraints for image ranking. IEEE Trans. Cybern. 2017, 47, 4014–4024. [Google Scholar] [CrossRef]
- Jia, G.Y.; Han, G.J.; Jiang, J.F.; Rodrigues, J.P.C. PARS: A scheduling of periodically active rank to optimize power efficiency for main memory. J. Netw. Comput. Appl. 2015, 58, 327–336. [Google Scholar] [CrossRef]
- Liang, X.; Li, X.; Shen, Q.; Lu, R.; Lin, X.; Shen, X.; Zhuang, W. Exploiting prediction to enable secure and reliable routing in wireless body area networks. In Proceedings of the IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 388–396. [Google Scholar]
- Tu, Y.; Lin, Y.; Wang, J.; Kim, J.U. Semi-supervised learning with generative adversarial networks on digital signal modulation classification. Comput. Mater. Contin. 2018, 55, 243–254. [Google Scholar]
- Zeng, D.J.; Dai, Y.; Li, F.; Sherratt, R.S.; Wang, J. Adversarial learning for distant supervised relation extraction. Comput. Mater. Contin. 2018, 55, 121–136. [Google Scholar]
- Kim, E.; Park, S.; Cha, J. Improved performance of UWB system for wireless body area networks. IEEE Trans. Consum. Electron. 2010, 56, 1373–1379. [Google Scholar] [CrossRef]
- Yin, Y.Y.; Chen, L.; Xu, Y.S.; Wan, J.; Zhang, H.; Mai, Z.D. QoS prediction for service recommendation with deep feature learning in edge computing environment. Mob. Netw. Appl. 2019. [Google Scholar] [CrossRef]
- Yin, Y.Y.; Chen, L.; Xu, Y.S.; Wan, J. Location-aware service recommendation with enhanced probabilistic matrix factorization. IEEE Access 2018, 6, 62815–62825. [Google Scholar] [CrossRef]
- Zhang, J.L.; Wan, J.; Li, F.F.; Mao, J.; Zhuang, L. Efficient sparse matrix-vector multiplication using cache oblivious extension quadtree storage format. Future Gener. Comput. Syst. 2016, 54, 490–500. [Google Scholar] [CrossRef]
- Gao, Y.; Wang, J.; Wu, W.B.; Sangaiah, A.K.; Lim, S.-J. A hybrid method for mobile agent moving trajectory scheduling using ACO and PSO in WSNs. Sensors 2019, 19, 3. [Google Scholar] [CrossRef]
- Zhang, Y.; Dolmans, G. Priority-guaranteed MAC protocol for emerging wireless body area networks. Ann. Telecommun. 2010, 66, 229–241. [Google Scholar] [CrossRef]
- Cohn, J.M.; Finn, P.G.; Nair, S.P.; Panikkar, S.B.; Pureswaran, V.S. Autonomous Decentralized Peer-to-peer Telemetry. U.S. Patent Application No. 20170310747A1, 26 October 2017. [Google Scholar]
- Feng, Q.; He, D.B.; Zeadally, S.K.; Muhammad, K.K. A survey on privacy protection in blockchain system. J. Netw. Comput. Appl. 2019, 126, 45–58. [Google Scholar] [CrossRef]
- Ren, K.; Lou, W.; Zeng, K.; Moran, P.J. On broadcast authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2007, 6, 4136–4144. [Google Scholar] [CrossRef]
- Wander, A.; Gura, N.; Eberle, H.; Gupta, V.; Shantz, S. Energy analysis of public-key cryptography for wireless sensor networks. In Proceedings of the PerCom, Kauai Island, HI, USA, 8–12 March 2005. [Google Scholar]

| Security Threats: | Security Requirements | Possible Solutions |
|---|---|---|
| Unverified or unauthorized access | Verified or authorized access | Random key distribution Public key encryption |
| Information leakage | Confidentiality | Link layer or network layer encryption Access control |
| Tampering with message | Integrity | Type a secure hash function A digital signature |
| Denial-of-service attack (DoS) | Usability | Intrusion detection Redundant routing |
| Node capture, damaged nodes | The resilience of the damaged node | Consistency checking and node undo tamper-proof |
| Routing attacks | Secure Routing | Security routing protocol |
| Intrusions and advanced security attacks | Security group management, intrusion detection | Secure group communication, intrusion detection |
| The Schemes | Total Size | Energy Consumption (mJ) |
|---|---|---|
| DVSSA scheme | P = 30 bytes | 13.52 W |
| Certificate-based scheme | N = 512 | 146.99 W |
| Merkle hash tree scheme | N = 512 | 144.56 W |
| ID-based scheme | N = 512 | 111.02 W |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ren, Y.; Leng, Y.; Zhu, F.; Wang, J.; Kim, H.-J. Data Storage Mechanism Based on Blockchain with Privacy Protection in Wireless Body Area Network. Sensors 2019, 19, 2395. https://doi.org/10.3390/s19102395
Ren Y, Leng Y, Zhu F, Wang J, Kim H-J. Data Storage Mechanism Based on Blockchain with Privacy Protection in Wireless Body Area Network. Sensors. 2019; 19(10):2395. https://doi.org/10.3390/s19102395
Chicago/Turabian StyleRen, Yongjun, Yan Leng, Fujian Zhu, Jin Wang, and Hye-Jin Kim. 2019. "Data Storage Mechanism Based on Blockchain with Privacy Protection in Wireless Body Area Network" Sensors 19, no. 10: 2395. https://doi.org/10.3390/s19102395
APA StyleRen, Y., Leng, Y., Zhu, F., Wang, J., & Kim, H.-J. (2019). Data Storage Mechanism Based on Blockchain with Privacy Protection in Wireless Body Area Network. Sensors, 19(10), 2395. https://doi.org/10.3390/s19102395





