Modeling and Deploying IoT-Aware Business Process Applications in Sensor Networks
Abstract
:1. Introduction
- We extend the graphic model and machine-readable model consisting of the XML Schema Definition (XSD) specification of BPMN 2.0, which could formally describe the elements in an extended XML document, making it able to support the direct modeling of a sensor device.
- We propose a novel deploying algorithm based on dynamic consistent hashing (DCH) to solve the problem of dynamic load balancing and access efficiency in the heterogeneous sensor networks. On this basis, the overall performance has been significantly improved.
- We qualitatively and quantitatively analyze the proposed approach. In addition, the work presented in this paper has been implemented through an actual development system.
2. Related Works
2.1. Modeling for the IoT-aware Business Process Applications
2.2. Deploying Algorithms for the Discrete IoT Applications
2.3. Summary of Related Works
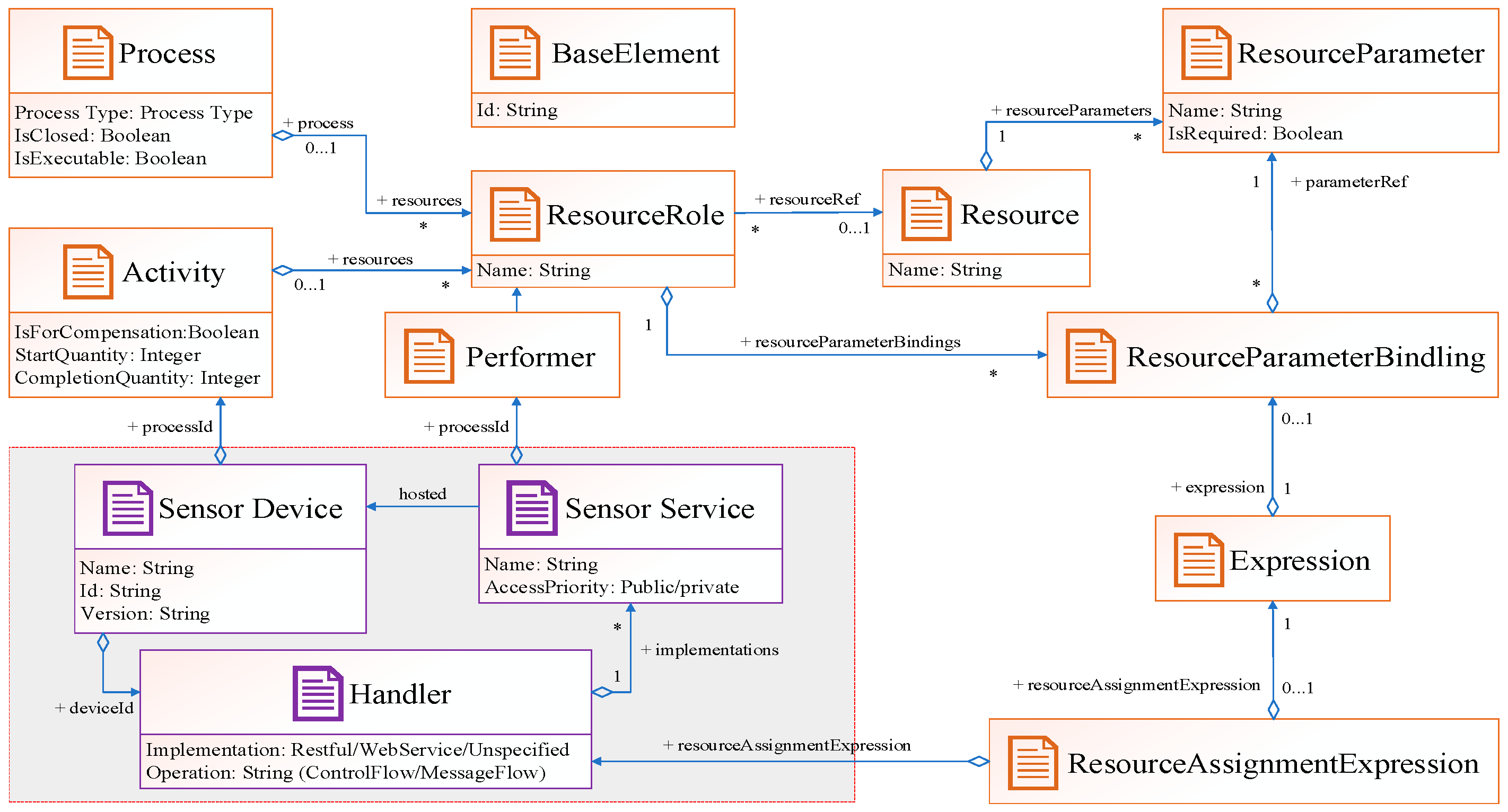
3. The Resource-Oriented Modeling Specification
3.1. The Graphic Model
3.2. The Machine-Readable Model
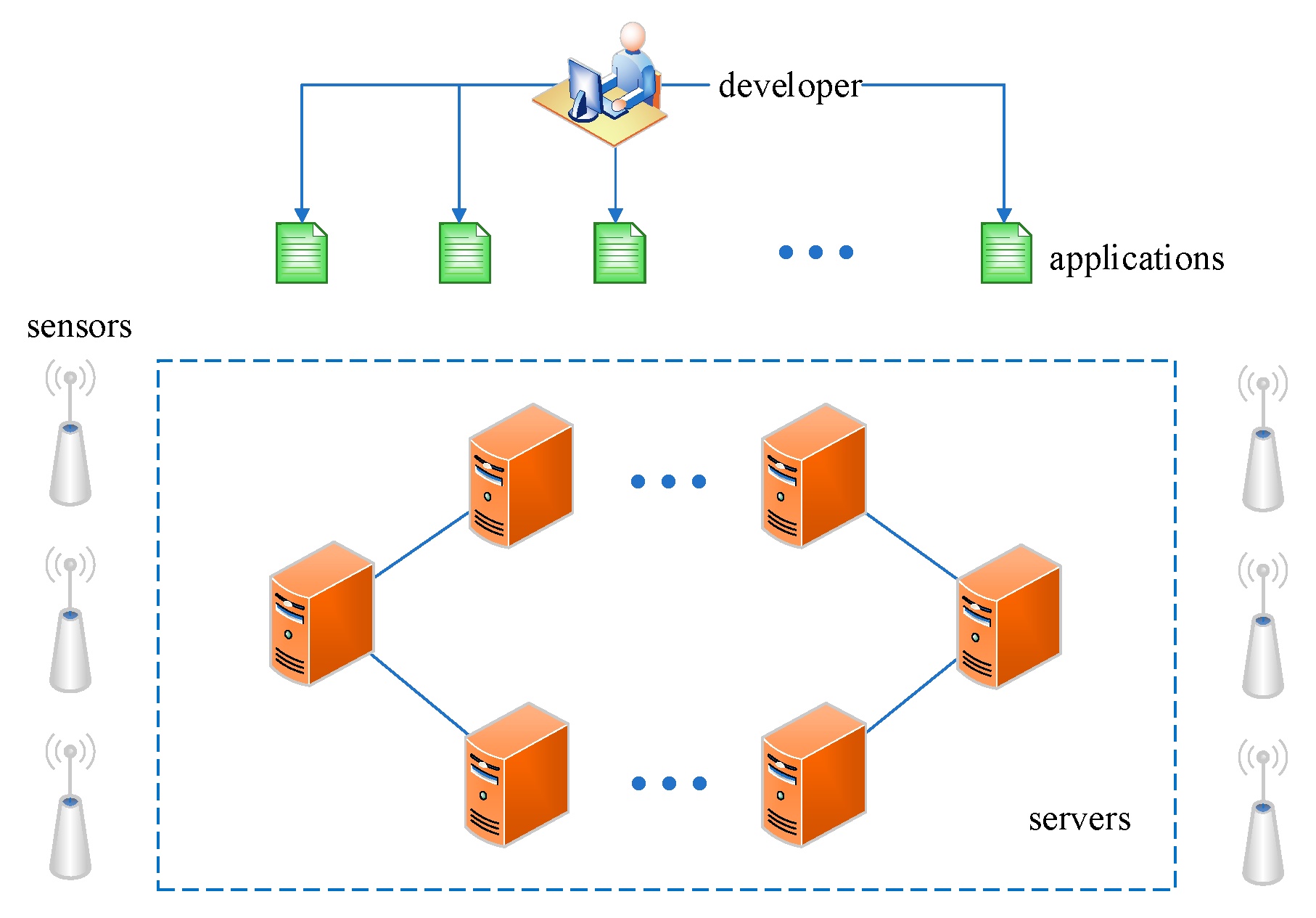
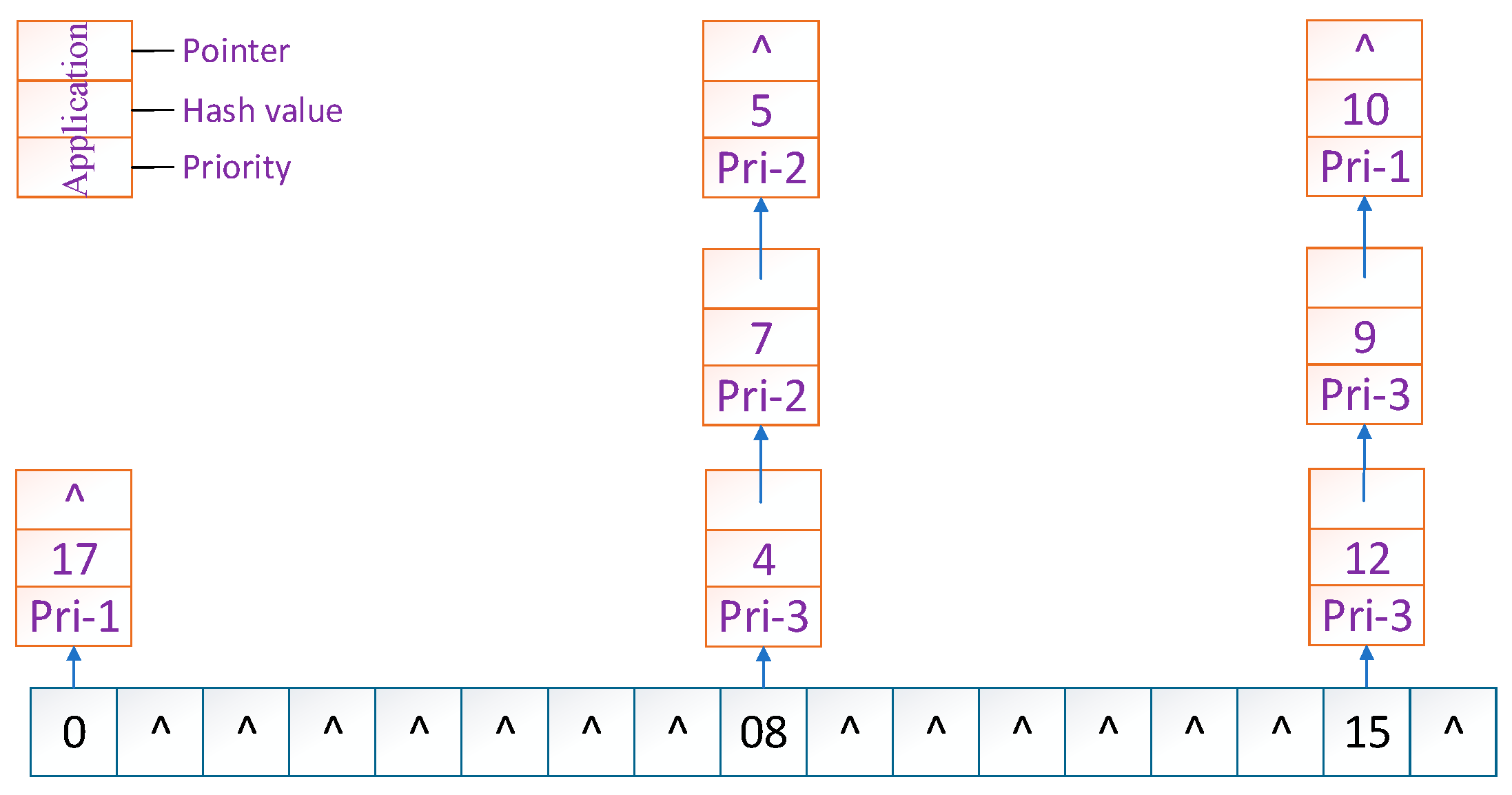
4. A DCH-Based Deploying Algorithm in the Heterogeneous Sensor Networks
4.1. Basic Deploying Algorithm
4.2. Deploying Algorithm for Common Cases
4.3. Deploying Algorithm for Special Cases
| Algorithm 1 DCH-based deploying algorithm in the heterogeneous sensor networks. |
| Input: The IP address queue of servers Q1 = (IP1, IP2, …, IPn) and the naming queue of applications Q2 = (AP1, AP2, …, APn) |
| Output: The deploying results of the applications Q3 |
| Conduct an hash circle that consisted of 2^32 nodes |
| for Q1 is not empty do |
| If (the elements in Q1 are adjacent) then |
| Conduct the operation i = hash (IP)%(2^32) for every element in Q1 |
| else |
| Conduct the virtual node X.a = hash (IP#1)%(2^32) for node X |
| Conduct the virtual node X.b = hash (IP#2)%(2^32) for node X |
| Map the server to hash circle according to the remainder i |
| for Q2 is not empty do |
| Conduct the operation j = hash (name+timestamp)%(2^32) for every element |
| Map the application to hash circle according to the remainder j |
| Access the nodes of applications in clockwise direction in hash circle |
| if (!hash circle.containsKey ()) then |
| Deploy the application to the current server |
| if (newNode.getPriority() > currentNode.getPriority()) then |
| Link the new node before the current node |
| else Link the new node after the current node |
| else Deploy the application to the server 0 |
| return The deploying results of the applications Q3 |
5. Experiment Results
6. Implementation and Discussion
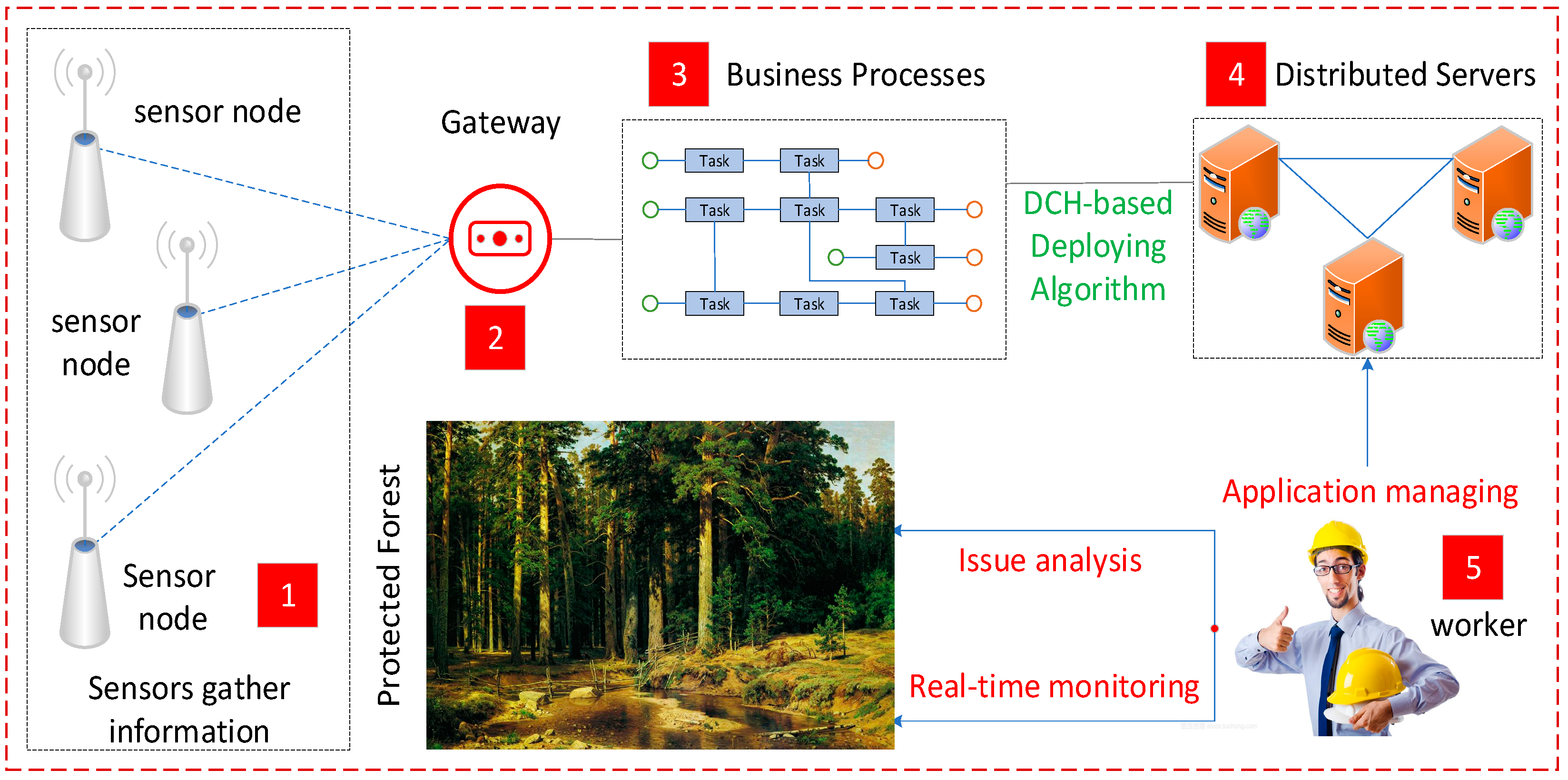
7. Case Study
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Bedi, G.; Venayagamoorthy, G.K. Internet of Things (IoT) Sensors for Smart Home Electric Energy Usage Management. In Proceedings of the IEEE International Conference on Information and Automation for Sustainability, Galle, Sri Lanka, 16–19 December 2016. [Google Scholar]
- Kim, D.Y.; Jung, M. Data Transmission and Network Architecture in Long Range Low Power Sensor Networks for IoT. Wirel. Personal Commun. 2017, 93, 119–129. [Google Scholar] [CrossRef]
- Appel, S.; Kleber, P.; Frischbier, S.; Freudenreich, T.; Buchmann, A. Modeling and execution of event stream processing in business processes. Inf. Syst. 2014, 46, 140–156. [Google Scholar] [CrossRef]
- Ruiz-Fernandez, D.; Marcos-Jorquera, D.; Gilart-Iglesias, V.; Vives-Boix, V.; Ramirez-Navarro, J. Empowerment of Patients with Hypertension through BPM, IoT and Remote Sensing. Sensors 2017, 17, 2273. [Google Scholar] [CrossRef]
- Tan, W.; Fan, Y.S.; Zhou, M.C. A petri net-based method for compatibility analysis and composition of web services in business process execution language. IEEE Trans. Autom. Sci. Eng. 2009, 6, 94–106. [Google Scholar] [CrossRef]
- Darzanos, G.; Dramitinos, M.; Stamoulis, G.D. Coordination Models for 5G Multi-Provider Service Orchestration: Specification and Assessment. In International Conference on the Economics of Grids, Clouds, Systems, and Services; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Martins, P.V.; Zacarias, M. Business Process and Practice Alignment Meta-model. Procedia Comput. Sci. 2015, 64, 314–323. [Google Scholar] [CrossRef]
- Mijares, H.; Marizé, D.; Bonillo, R. Theoric model for the specification and management of the business process, based on the use of big data and Internet of Things (IoT). In Proceedings of the 2017 12th Iberian Conference on Information Systems and Technologies (CISTI), Lisbon, Portugal, 21–24 June 2017. [Google Scholar]
- Schulte, S.; Janiesch, C.; Venugopal, S. Elastic Business Process Management: State of the art and open challenges for BPM in the cloud. Future Gener. Comput. Syst. 2015, 46, 36–50. [Google Scholar] [CrossRef]
- Liu, C.F.; Li, Q.; Zhao, X.H. Challenges and opportunities in collaborative business process management: Overview of recent advances and introduction to the special issue. Inf. Syst. Front. 2014, 11, 201–209. [Google Scholar] [CrossRef]
- Dave, B.; Buda, A.; Nurminen, A.; Framling, K. A framework for integrating BIM and IoT through open standards. Autom. Constr. 2018, 95, 35–45. [Google Scholar] [CrossRef]
- You, K.M.; Yang, W.; Han, R.S. The video collaborative localization of a Miner’s lamp based on wireless multimedia sensor networks for underground coal mines. Sensors 2015, 15, 25103–25122. [Google Scholar] [CrossRef]
- Rosa, M.L.; Dumas, M.; Uba, R. Business Process Model Merging: An Approach to Business Process Consolidation. ACM Trans. Softw. Eng. Methodol. 2013, 22, 1–42. [Google Scholar] [CrossRef]
- Smirnov, S.; Reijers, H.A.; Weske, M. Business process model abstraction: A definition, catalog, and survey. Distrib. Parallel Databases 2012, 30, 63–99. [Google Scholar] [CrossRef]
- Meyer, S.; Ruppen, A.; Magerkurth, C. Internet of Things-Aware Process Modeling: Integrating IoT Devices as Business Process Resources. In International Conference on Advanced Information Systems Engineering; Springer: Berlin/Heidelberg, Germany, 2013; pp. 84–98. [Google Scholar]
- Rosa, M.L.; van der Aalst, W.M.P.; Dumas, M.; Milani, F. Business Process Variability Modeling: A Survey. ACM Comput. Surv. 2017, 50, 2. [Google Scholar] [CrossRef]
- Lin, C.C.; Yang, J.W. Cost-Efficient Deployment of Fog Computing Systems at Logistics Centers in Industry 4.0. IEEE Trans. Ind. Inform. 2018, 14, 4603–4611. [Google Scholar] [CrossRef]
- Senouci, M.R.; Mellouk, A.; Assnoune, K. Localized Movement-Assisted SensorDeployment Algorithm for HoleDetection and Healing. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1267–1277. [Google Scholar] [CrossRef]
- Jiang, P.; Wang, X.; Jiang, L. Node Deployment Algorithm Based on Connected Tree for Underwater Sensor Networks. Sensors 2015, 15, 16763–16785. [Google Scholar] [CrossRef] [PubMed]
- Kim, B.K.; Kang, J.Y.; Lee, D.H. A New Hash Algorithm Exploiting Triple-state Bucket Directory for Flash Storage Devices. IEEE Trans. Consum. Electron. 2016, 62, 398–404. [Google Scholar] [CrossRef]
- Liang, T.Y.; Li, Y.J. A Location-Aware Service Deployment Algorithm Based on K-Means for Cloudlets. Mob. Inf. Syst. 2017, 2017. [Google Scholar] [CrossRef]
- Hwang, G.; Lee, J.; Park, J.; Chang, T.W. Developing performance measurement system for Internet of Things and smart factory environment. Int. J. Prod. Res. 2017, 55, 2590–2602. [Google Scholar] [CrossRef]
- Available online: http://www.jbpm.org/ (accessed on 30 December 2018).
- Cheng, Y.Y.; Zhao, S.; Cheng, B.; Chen, J.L. A Resource Oriented Modeling Approach for the Internet of Things: A Business Process Perspective. Models 2017, 2019, 465–467. [Google Scholar]
- Monica, L.C.; Pablo, V.G.; Adolfo, C.M.; Fredy, K.R.; Raul, S.B. Methodology for auditing the resources allocation of critical maintenance activities. DYNA 2014, 89, 89–974. [Google Scholar] [CrossRef]
- Cristina, C.; Manuel, R.; Antonio, R.C. A template-based approach for responsibility management in executable business processes. Enterp. Inf. Syst. 2018, 12, 550–586. [Google Scholar] [CrossRef]
- Cheng, Y.Y.; Zhao, S.; Cheng, B.; Hou, S.L.; Shi, Y.L.; Chen, J.L. Modeling and Optimization for Collaborative Business Process Towards IoT Applications. Mob. Inf. Syst. 2018, 2018. [Google Scholar] [CrossRef]
- Ostrensky, A.; Horodesky, A.; Faoro, H.; Balsanelli, E.; Sfeir, M.Z.T.; Cozer, N.; Pie, M.R.; Pont, G.D.; Westphal, G.G.C. Metagenomic evaluation of the effects of storage conditions on the bacterial microbiota of oysters Crassostrea gasar (Adanson, 1757). J. Appl. Microbiol. 2018, 125, 1435–1443. [Google Scholar] [CrossRef]
- Zhao, J.; Wang, X.X.; Li, X.Y.; Jia, S.Y.; Peng, Y.Z. Combining partial nitrification and post endogenous denitrification in an EBPR system for deep-level nutrient removal from low carbon/nitrogen (C/N) domestic wastewater. Chemosphere 2018, 210, 19–28. [Google Scholar] [CrossRef] [PubMed]
- Pontarelli, S.; Reviriego, P.; Mitzenmacher, M. EMOMA: Exact Match in One Memory Access. IEEE Trans. Knowl. Data Eng. 2018, 30, 2120–2133. [Google Scholar] [CrossRef]
- Lv, Y.M.; Ng, W.W.Y.; Zeng, Z.Q.; Yeung, D.S.; Chan, P.P.K. Asymmetric Cyclical Hashing for Large Scale Image Retrieval. IEEE Trans. Multimedia 2015, 17, 1225–1235. [Google Scholar] [CrossRef]
- Hua, H.E.; Lin, C.; Zhao, Z. Modeling and performance analysis of Hadoop fair scheduling using deterministic and stochastic Petri net. Int. J. Comput. Appl. Technol. 2015, 54, 154–160. [Google Scholar]
- Yu, W.Y.; Yan, C.G.; Ding, Z.J.; Jiang, C.J.; Zhou, M.C. Modeling and validating E-commerce business process based on Petri nets. IEEE Trans. Syst. Man Cybern. Syst. 2013, 44, 327–341. [Google Scholar] [CrossRef]
- Available online: https://www.activiti.org/ (accessed on 30 December 2018).















| Attribute Name | Description |
|---|---|
| name: string | The descriptive name of the element. |
| operations: Operation [1, ..., *] | The operations that define the Interface. An Interface has at least one Operation. |
| callableelement: Callableelement [0, ..., *] | The CallableElements that use this Interface. |
| implementationRef: Element [0, ..., 1] | This attribute allows to reference a concrete artifact in the underlying implementation technology representing that interface. |
| <xsd: element name = “interface” type = “Interface” Group = “baseElement”/> |
| <xsd: complexType name = “tInterface”> |
| <xsd: complexContent> |
| <xsd: extension base = “tBaseElement”> |
| <xsd: sequence> |
| <xsd: element ref = “operation” minOccurs = “1” maxOccurs = “10”/> |
| </xsd: sequence> |
| <xsd: attribute name = “Qname” type = “xsd: string” use = “required”/> |
| <xsd: attribute name = “Qname” type = “xsd: string” use = “optional”/> |
| </xsd: extension> |
| </xsd: complexContent> |
| </xsd: complexType> |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cheng, Y.; Zhao, S.; Cheng, B.; Chen, X.; Chen, J. Modeling and Deploying IoT-Aware Business Process Applications in Sensor Networks. Sensors 2019, 19, 111. https://doi.org/10.3390/s19010111
Cheng Y, Zhao S, Cheng B, Chen X, Chen J. Modeling and Deploying IoT-Aware Business Process Applications in Sensor Networks. Sensors. 2019; 19(1):111. https://doi.org/10.3390/s19010111
Chicago/Turabian StyleCheng, Yongyang, Shuai Zhao, Bo Cheng, Xiwei Chen, and Junliang Chen. 2019. "Modeling and Deploying IoT-Aware Business Process Applications in Sensor Networks" Sensors 19, no. 1: 111. https://doi.org/10.3390/s19010111
APA StyleCheng, Y., Zhao, S., Cheng, B., Chen, X., & Chen, J. (2019). Modeling and Deploying IoT-Aware Business Process Applications in Sensor Networks. Sensors, 19(1), 111. https://doi.org/10.3390/s19010111






