1. Introduction
According to the World Health Organization, 100 million people die in traffic accidents worldwide annually, accounting for economic losses of
$500 billion [
1]. Therefore, safe transportation has become one of the most important global issues. Recently, intelligent transportation systems (ITSs) have been used to enable significant improvements in performance, traffic flow, and the efficiency of passenger and goods transportation [
2]. Moreover, an ITS ensures more comfortable travel for passengers by providing infotainment along the road. The ITS targets utilization of ubiquitous sensing and wireless networking capabilities for intelligent management of the transportation system [
3]. The vehicular ad hoc network (VANET) is one important segment of an ITS, which furnishes the quality and effectiveness of safety messages in future transportation systems. A VANET consists of a set of special vehicles and roadside units (RSUs). VANETs employ dedicated short-range communications (DSRC) for vehicle-to-vehicle (V2V) and vehicle-to-RSU (V2R) communications. V2V communications-based applications broadcast within a one-hop neighborhood. For instance, each vehicle periodically broadcasts information about its position, speed, heading, acceleration, turn signal status, and so on, to all vehicles within its one-hop neighborhood [
4] in order to announce precrash sensing, blind spot warnings, emergency electronic brake lights, and cooperative forward collision avoidance. Similarly, an RSU periodically broadcasts V2R communications–based applications, such as curve speed warnings and traffic signal violation warnings, to all approaching vehicles, plus information related to traffic signal status and timing, road surface types, weather conditions, and so on [
5]. The main properties of VANETs are variable network density, large-scale networks, a predictable mobility model, and rapid topology changes. Therefore, compared with other networks, VANETs have high rates of topology change, restrictions on vehicle movements due to road structures, and availability of ample energy sources and processing power. On the other hand, in wireless sensor networks (WSNs), energy consumption is a very important issue, and is considered a vital mechanism in most protocols.
In Wireless Access in Vehicular Environments (WAVE), the DSRC spectrum is divided into seven 10 MHz channels: one control channel (CCH) and six service channels (SCHs). The CCH is used for exchanging high-priority safety applications and network management, whereas SCHs mainly support non-safety information and entertainment applications. VANET applications have different quality of service (QoS) requirements, such as transmission delay and bandwidth. First, safety-related applications are related to the safety of people on the road, such as emergency braking, blind spot warnings, and precrash sensing. Hence, safety-related applications require reliable and fast broadcasting mechanisms, and each vehicle must periodically broadcast information like location, speed, and acceleration [
5,
6]. One such application is the beacon packet containing the vehicles location, speed, and acceleration [
5,
6], which is broadcast periodically by each vehicle. Second, traffic management services consist of intersection management, delay warnings, road congestion prevention, toll collection, and cooperative adaptive cruise control. Third, user-oriented services provide information, advertisements, and entertainment for passengers while traveling. User-oriented services have two basic applications: Internet connectivity and peer-to-peer applications [
7,
8]. However, safety services require both fast access and low delay, whereas user-oriented services require large bandwidth [
9]. We briefly summarize the requirements for different applications in
Table 1.
Media access control (MAC) plays an important role in supporting efficient broadcast services and in satisfying requirements for VANET applications. Many MAC protocols have been proposed to provide high-throughput systems for service applications and to guarantee strict transmission delays for safety applications. There are three main schemes, depending on the channel access method used: contention-based media access, such as IEEE 802.11p [
12]; contention-free media access, such as TDMA-based MAC protocols; and hybrids of the two methods. First, contention-based MAC protocols allow the vehicles to access the channel randomly when they have data to transmit. However, the collision probability is high when the network load is high. In addition, they cannot guarantee QoS requirements for critical road safety applications. Unlike contention-based MAC protocols, contention-free MAC protocols allow each vehicle to access a channel by following a schedule of time slot frequency bands or code sequences [
9]. To do so, they require a strict synchronized scheme between vehicles. In the same two-hop neighbor set that contention-free MAC protocols can support, the packets are transmitted without collisions. The major issues of contention-free and contention-based MAC protocols are as follows:
Contention-free protocols require a global positioning system (GPS) to support location and time information, which is used to synchronize the communicating vehicles. In addition, the high mobility of vehicles can affect the performance of these protocols.
Contention-free protocols cannot satisfy QoS requirements for real-time applications. When the vehicle density is high, these protocols provide poor performance.
To enhance QoS requirements and reduce the number of packet collisions, hybrid MAC protocols were proposed to try to combine these two mechanisms into a single architecture. Such an architecture includes two periods on the access channel: a random access period and a contention-free access period. The contention-free access period is used to transmit safety packets to all nodes without collisions by using TDMA-based access schemes. The contention-free access period is used to exchange WAVE service announcements, acknowledgments, and responses to service (WSA/ACK/RES) and piggyback service information and the identities of SCHs to be used. Moreover, nodes create a channel access schedule by broadcasting HELLO packets in the contention-free access period.
The performance of single-channel MAC protocols, such as IEEE 802.11p [
12], degrades quickly with an increase in vehicle density. This is because of high contention and collisions due to the increase in the number of vehicles, and, hence, the number of transmissions. Thus, multi-channel MAC protocols based on IEEE 802.11p and IEEE 1609.4 standards have higher performance than that of single-channel MAC protocols in every key performance indicator [
13]. Furthermore, the multi-channel MAC protocol supports not only reliable transmission packets with low latency but also provides maximum throughput for non-safety applications. Many multi-channel MAC protocols have been proposed for efficiency and reliability [
14,
15,
16]. IEEE 1609.4 [
14] is considered a default multi-channel MAC standard in the family of IEEE 1609 standards for VANETs. In [
14], the standard was developed to efficiently coordinate channel access on the CCH and SCHs, called a globally synchronized channel coordination scheme, based on coordinated universal time (UTC). The channel time is divided into synchronization intervals with a fixed length of 100 ms. It consists of a CCH interval (CCHI) and an SCH interval (SCHI) each with a length of 50 ms. This scheme allows safety and non-safety application packets to be transmitted on different channels without missing important packets on the CCH. However, IEEE 1609.4 cannot utilize all SCH resources during the CCH interval.
This paper focuses on the multichannel hybrid media access control schemes, which are based on draft IEEE 802.11p and IEEE 1609.4 standards. Our contributions are as follows.
We investigate the existing hybrid MAC protocols and discuss their benefits and limitations.
We propose a modified announcement packet to reduce payload size of a packet transmitted in the TDMA period.
We use a Markov chain and a stochastic process to establish the number of initial time slots in both the TDMA period and on the SCHs under the condition of saturated traffic load.
We analyze the trade-off between time slot selection in both the TDMA period and on the SCHs under a saturated traffic load condition.
We optimize time slot selection on the SCHs and on the CCH under a saturated throughput condition.
The analysis results show that the number of neighbors has little effect on the establishment of the number of time slots in both TDMA periods and SCHs under a saturated throughput condition.
The rest of this paper is organized as follows.
Section 2 gives a short survey of hybrid MAC protocols in VANETs.
Section 3 describes the modified announcement packet in detail.
Section 4 discusses a theoretical analysis of establishing the number of time slots in both the TDMA period and on the SCHs under a condition of saturated traffic load. The performance evaluation is presented in
Section 5.
Section 6 gives conclusions to this paper.
2. Related Works
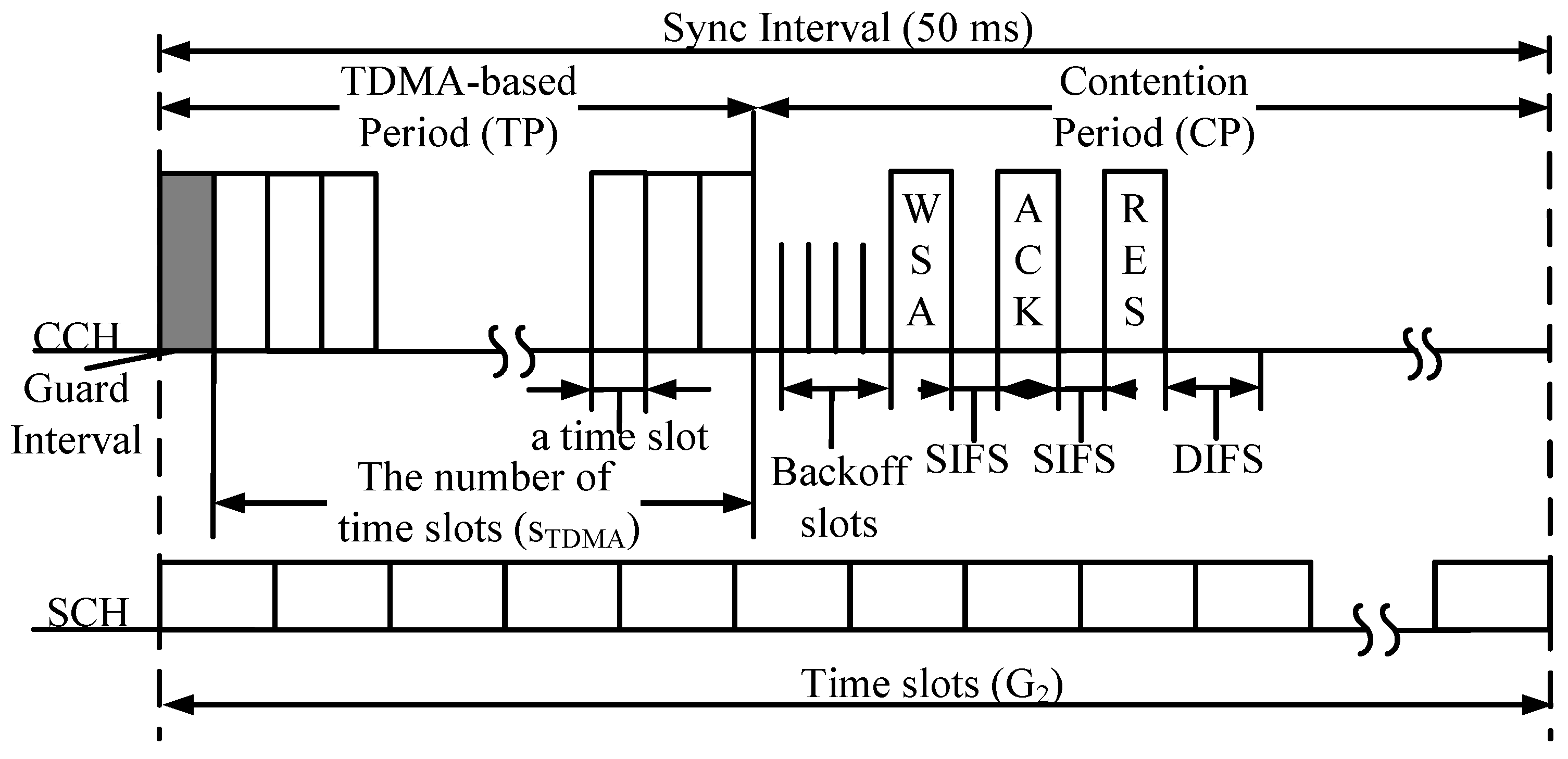
The multi-channel MAC protocol under consideration consists of TDMA periods and CSMA periods (called contention periods in this paper), as shown in
Figure 1. In the TDMA period, each node has to broadcast its information, including safety applications, in its time slot. In the CSMA period, a node that has a non-safety packet will attempt to exchange WSA/ACK/RES messages and piggyback service information and the identities of SCHs to be used. There are two main schemes to reserve time slots in the TDMA period: the self-organization scheme, and broadcasting a HELLO packet in the CSMA period. Nevertheless, a node that wants to occupy a time slot has to know its two-hop neighbor information by receiving packets about their reserved time slots. This is because a node will obtain full information about its two-hop neighbors, and it can then choose an available time slot without any access collision (Access collision is defined as the collision happening when more than two nodes occupy the same time slot in the same two-hop neighborhood [
4].). Therefore, a new node will broadcast its packet in its chosen time slot under the self-organization scheme. Otherwise, it broadcasts its HELLO packet during the contention-based period.
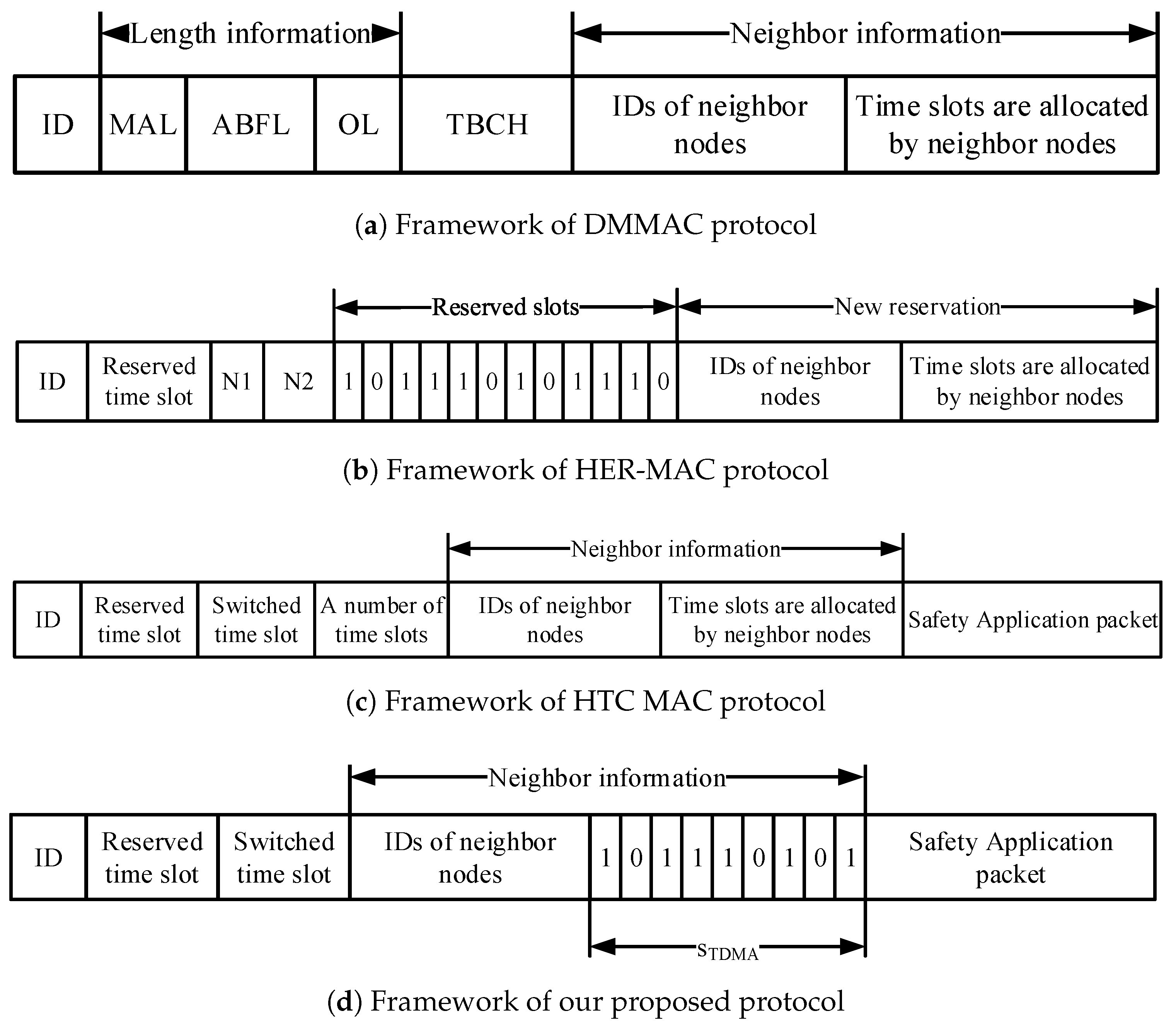
Therefore, to provide full two-hop information on neighborhood vehicles for a target node, hybrid MAC protocols have been proposed in various frameworks to broadcast in the TDMA period of each time slot, as shown in
Figure 2.
Figure 2a shows fields included in a packet transmitted in the TDMA period under the dedicated multi-channel MAC (DMMAC) protocol [
15]. This consists of length information (the maximum active length (MAL) of vehicles in its one-hop area, adaptive broadcast frame length (ABFL), and the maximum ABFL within a one-hop area (OL)), TBCH (which is used when the vehicle makes its active length as short as possible), and neighbor information. To reduce the overhead of a framework using the DMMAC protocol, the hybrid efficient and reliable MAC (HER MAC) protocol [
16] uses a bitmap to represent the neighbor information, as shown in
Figure 2b.
and
are the last time slots occupied by the one-hop neighbor nodes and by all neighbor nodes, respectively. The information helps a new node know the bitmap length of its one- and two-hop neighbors. Then, the new node can broadcast a HELLO packet including its ID and a reserved time slot to its one-hop neighborhood. Moreover, this information also helps a vehicle to shorten the TDMA period by eliminating the empty time slots [
16]. However, there are many types of packets transmitted in the HER-MAC protocol. Hence, collision probability increases with an increase in the number of vehicles. The hybrid TDMA/CSMA MAC (HTC-MAC) protocol [
17] was proposed to remove HELLO and SWITCH packets during the CSMA period. As shown in
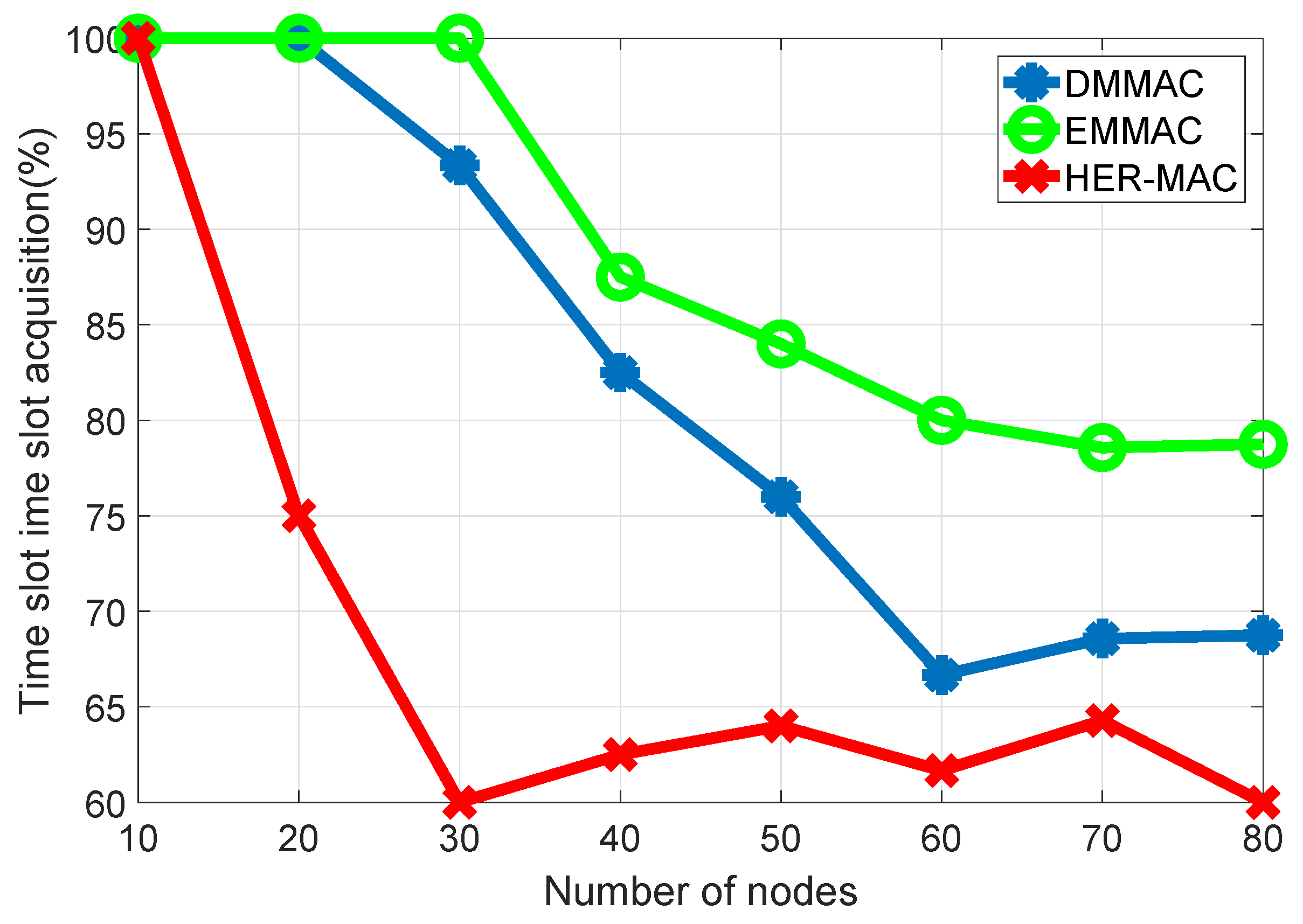
Figure 2c, a new field is added to the HTC-MAC framework to shorten the length of the TDMA period. Furthermore, HTC-MAC provides efficient time-slot acquisition by letting a new vehicle randomly choose an available time slot to broadcast the announcement (ANC) packet.
Time slot selection is an important issue for TDMA-based MAC protocols in VANETs. One of the well-known problems with TDMA-based MAC protocols, such as HER-MAC [
16] and HTC-MAC [
17], is transmission overhead when node density is high. To solve the transmission overhead problem, we propose a modified announcement packet to reduce the payload size of a packet transmitted in the TDMA period.
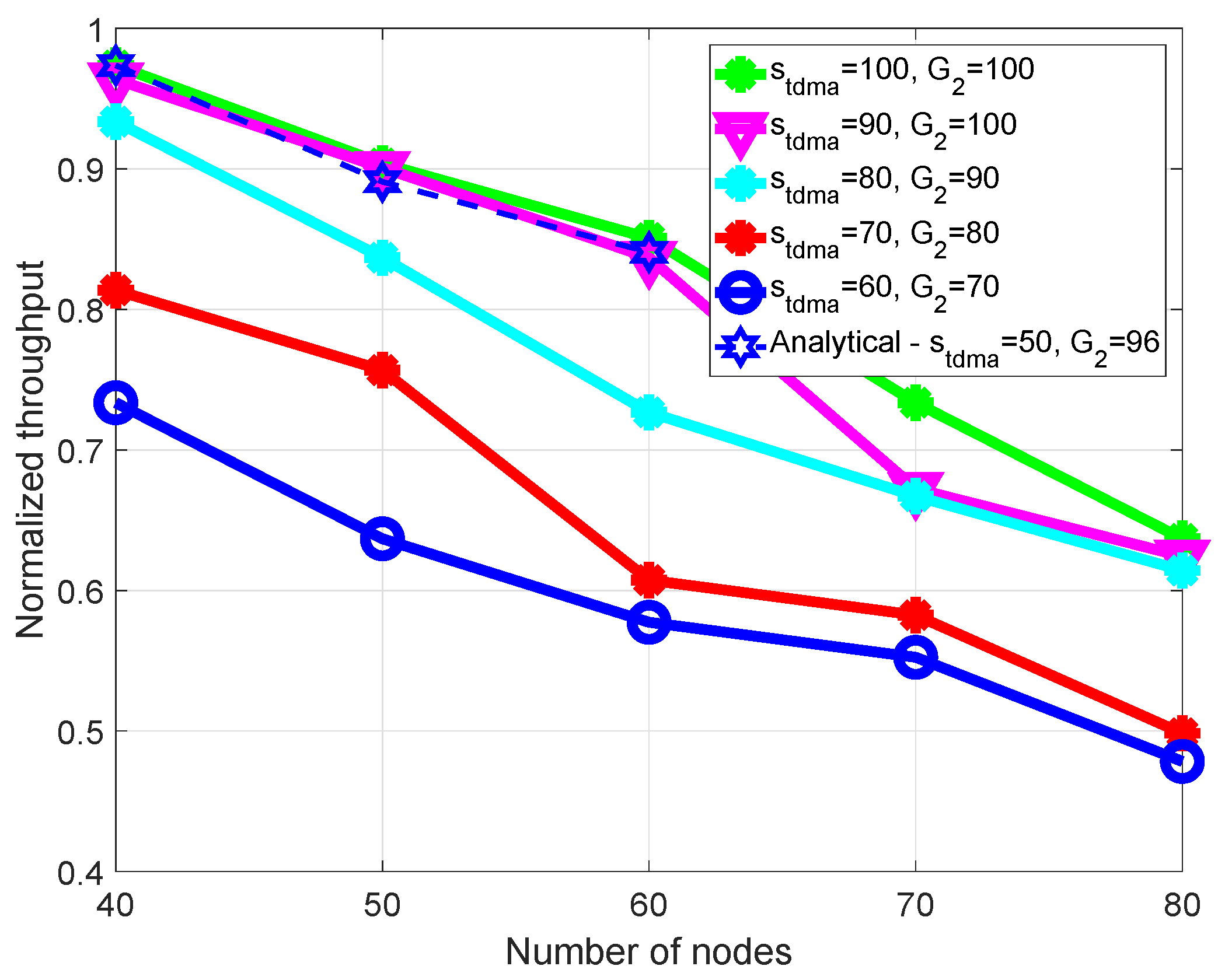
The saturation throughput of SCHs (or saturation of traffic load) is when all time slots on the SCHs are used after nodes successfully exchange WSA/ACK/RES in the CSMA period on the CCH. Time slots on the SCHs are used to transmit/receive large bandwidth–consuming applications, such as video downloads and map updates. Hence, the length of the TDMA period needs to ensure that all nodes can use sufficient bandwidth resources on the SCHs. This paper considers a way to optimize time slot selection on SCHs and on the CCH under conditions of saturation throughput and packet delay.
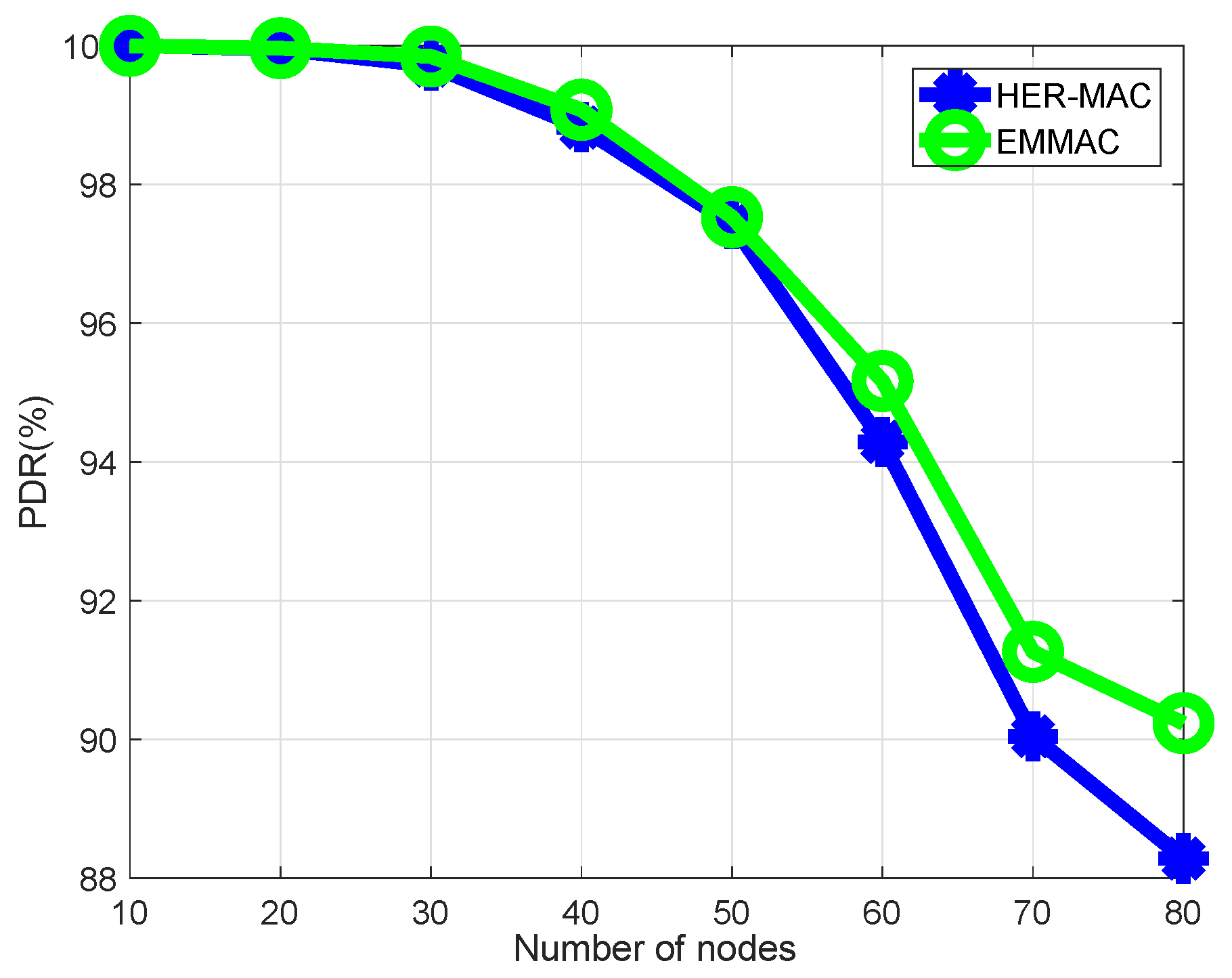
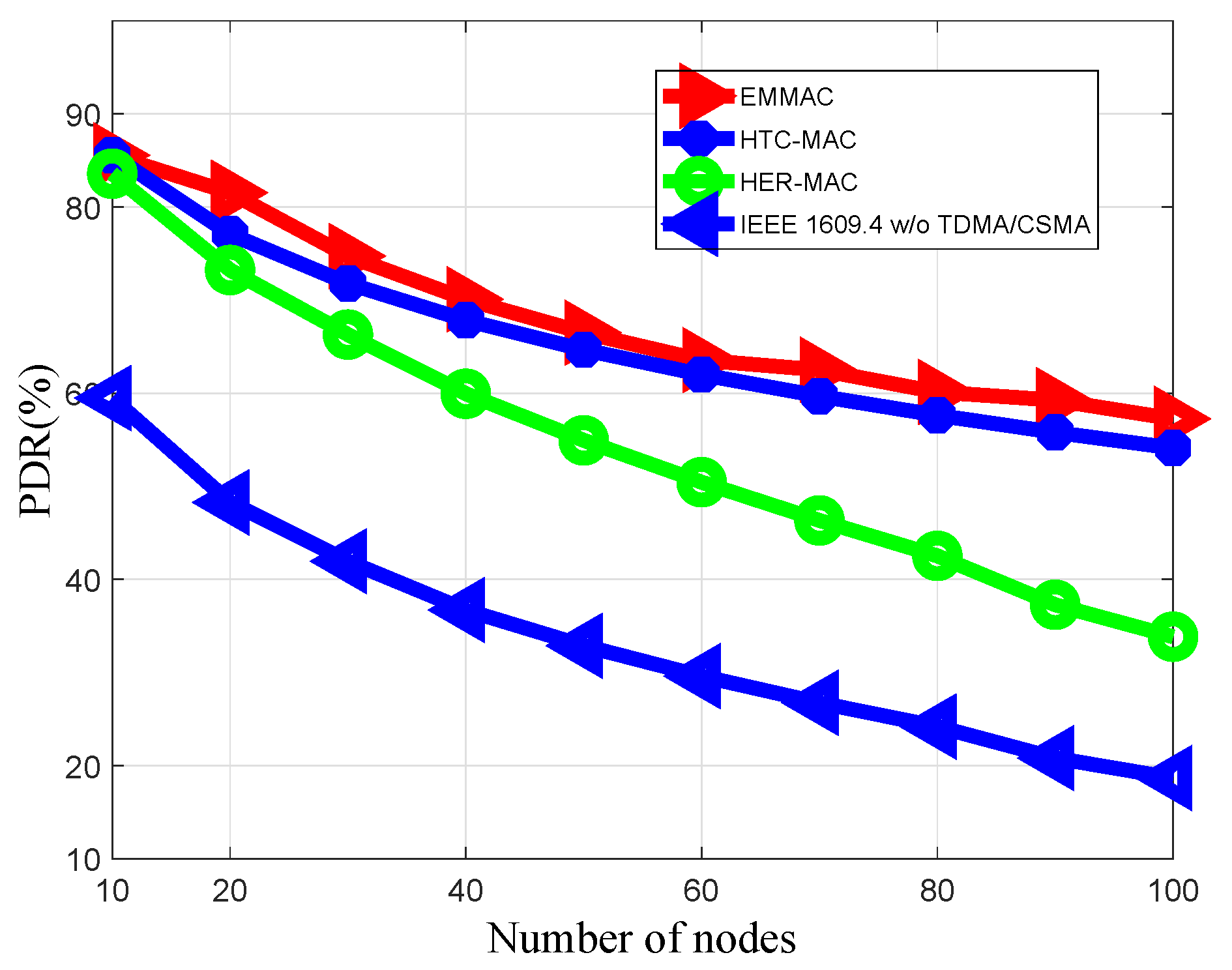
Table 2 summarizes a comparison between our proposal and the existing MAC protocols. Our proposal allows the adjustment of both TDMA and contention periods, based on vehicle density and data traffic conditions. By reducing the payload size of a packet transmitted in the TDMA period, our proposal can decrease the length of the TDMA period when vehicle density is high.
3. EMMAC: Efficient Multi-Channel MAC Protocol in VANETs
Each node in VANET under consideration has one transceiver which can switch between CCH and SCHs. A node tunes to CCH to transmit two kinds of information: (1) high-priority short application (such as periodic or event driven safety messages), and beacon packet which includes the vehicle’s position, speed, and acceleration [
5] during the TDMA period; and (2) control information required for the nodes to determine which time slots they should access in SCHs in the CSMA period. In this paper, we present the modified announcement packet to reduce payload size of a packet transmitted in the TDMA period. Based on the modified announcement packets, we design an efficient multi-channel MAC protocol.
Nodes based on two-hop neighbors information adjust the length of the TDMA period. Two-hop neighbors information is collected by receiving the modified announcement packet (MANC) transmitted in the TDMA period including the time slots information. As shown in
Figure 2d, MANC packet contains six fields: (i) node ID; (ii) its reserved time slot; (iii) a switched time slot; (iv) IDs of one-hop neighbor nodes; (v) bits representing the status of time slots in the TDMA period; and (vi) safety application packet. In the bits representing the status of time slots in the TDMA period, bit 0 means free time slot status; otherwise, bit 1 represents busy time slot status. Note that the number of bits is the length of time slots in the TDMA period.
3.1. TDMA Period Adjustment Scheme
To reduce the length of the TDMA period, under the HER-MAC [
16] protocol, a switched node attempts to broadcast a SWITCH packet in the CSMA period to change its time slot. Under the DMMAC [
15] protocol, each node, based on the length of the TDMA period and the last time slot that was occupied, reduces the length of the TDMA period in the next frame. Our proposed contention-free length-adjustment scheme under the efficient multi-channel MAC (EMMAC) protocol operates as follows:
Each node successfully receives MANC packets transmitted by one-hop neighbor nodes in the previous frame. Based on these MANC packets, each node has the status of all time slots and the number of time slots in the TDMA period.
Each node considers whether it should move to an available time slot without collisions to reduce the number of time slots in the TDMA period. If a node wants to change its time slot, it will randomly choose an available time slot. Then, this node will broadcast a switched time slot included in the MANC packet in its reserved time slots.
After one period of the sync-interval (100 ms under IEEE 1609.4 [
14]), a switched node checks the MANC packets broadcast by one-hop neighbor nodes. If all neighbor nodes broadcast MANC packets including the updated information, it successfully acquires the new time slot, reducing the length of the TDMA period in the next frame.
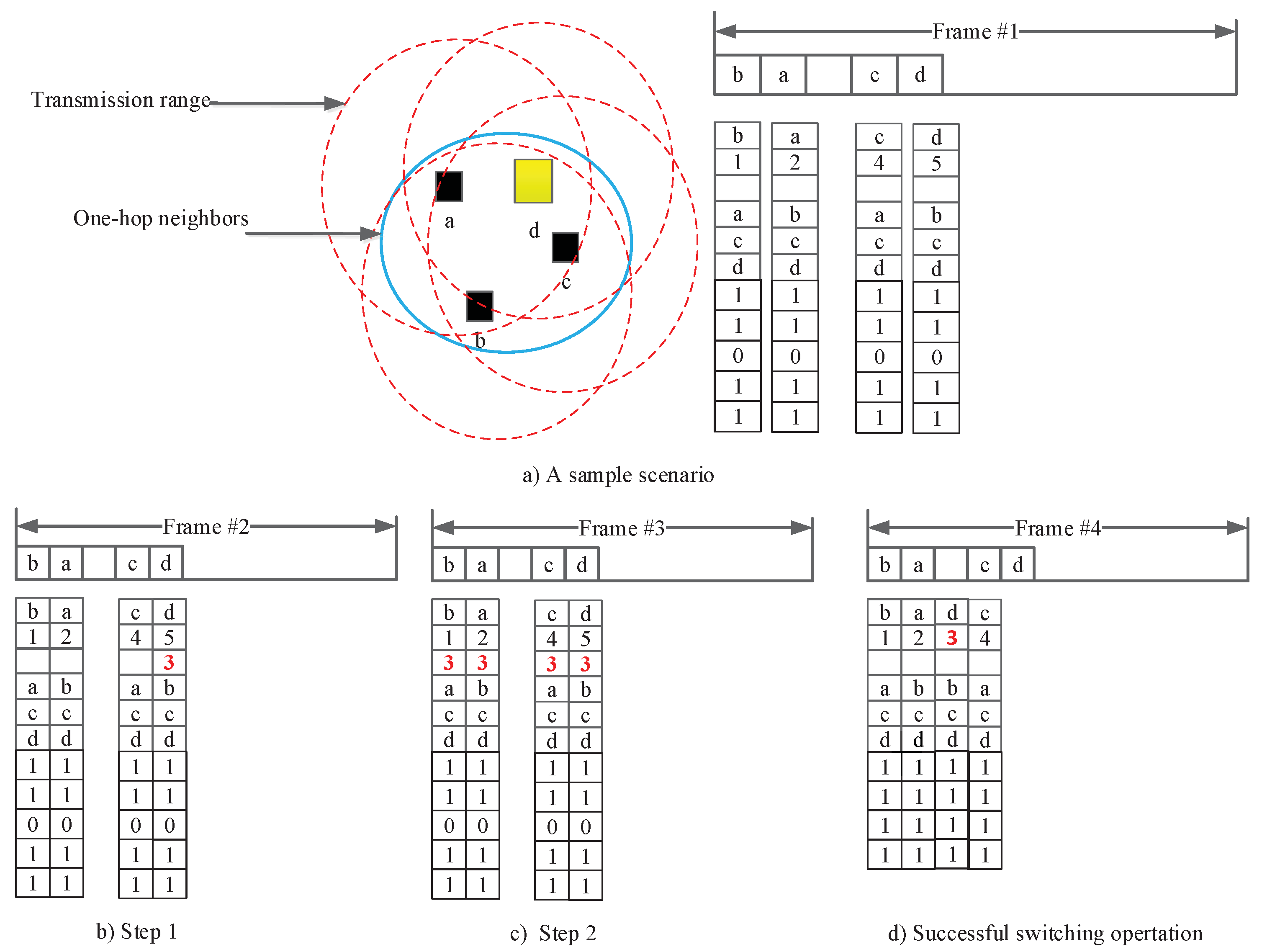
For instance, we consider one sample scenario shown in
Figure 3. Nodes
, and
d occupy time slots
, respectively.
Figure 3a shows that each node periodically broadcasts its MANC packet during its occupied time slot. After all nodes receive the MANC packets, node
d, which occupies the last time slot, considers a move to a new time slot to reduce the length of the TDMA period. Thus, node
d can move to time slot
, and node
d includes
in the switched time slot field of its MANC packet and broadcasts in its reserved time slot
, as shown in
Figure 3b. Each node will broadcast its MANC packet including the information of the switched time slot field,
, as shown in
Figure 3c. If node
d checks its switched time slot information in the MANC packets and all one-hop neighbors were updated, it successfully acquires the new time slot, reducing the length of the TDMA period in the next frame in
Figure 3c.
3.2. Hybrid Time Slot Acquisition Scheme
In this section, we present a scheme that is used to occupy a time slot for a new node. After one duration of the TDMA period, a new node, x, receives all packets transmitted with its one-hop neighbors’ information. From the IDLE (IDLE is defined as the channel is detected as free) time slots, node x will consider occupying a time slot in the TDMA period. There are two cases: (1) there is at least one available time slot; and (2) there are no available time slots. Depending on these cases, we present two corresponding options.
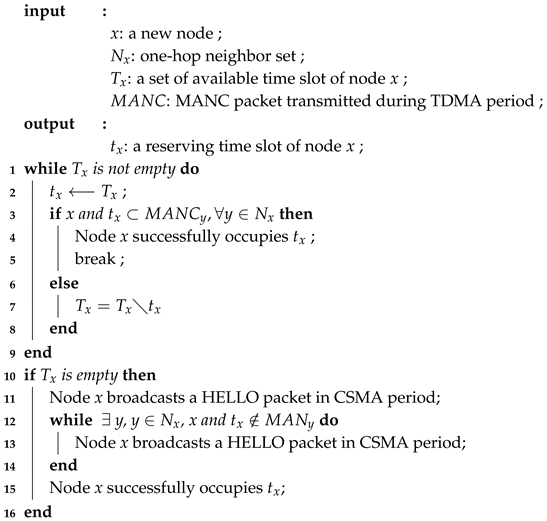
When new node x enters the network, node x has to listen for one duration to collect and store information from one-hop neighbors. The parameters are stored to determine if there is an available time slot to access. Here, we propose a hybrid time slot–acquisition scheme in Algorithm 1. Let be a set of available time slots from the nodes. Node x checks to determine the status of available time slots. If is ∅, node x will broadcast a HELLO packet in the CSMA period. Node x checks the information in the packets transmitted by neighbors in , to find out if it can successfully occupy a time slot or not. , which is the one-hop neighbor set for node x, is collected when node x enters the network.
| Algorithm 1: Hybrid time slot acquisition scheme |
![Sensors 18 03028 i001]() |
The main operations of the hybrid time slot acquisition scheme in the algorithm are as follows:
After node x receives all packets from its one-hop neighbor set, node x will find out if a time slot is available.
If there are available time slots, node x will randomly choose a time slot to occupy. In the next TDMA period, node x will broadcast its MANC packet in its reserved time slot. If all one-hop neighbors add node x’s ID and change the corresponding bit in the bitmap to 1 in their neighbor information of the MANC packets, node x successfully occupies the time slot. Otherwise, node x will choose another available time slot to occupy. If there are no remaining available time slots, node x will choose the next option.
If there are no available time slots, node x will broadcast a HELLO packet in the CSMA period. If all one-hop neighbors add node x’s ID, and change the extending time slot to in their neighbor information of the MANC packets, node x successfully occupies an extended time slot. Otherwise, node x will broadcast a HELLO packet again until it successfully occupies a time slot.