1. Introduction
Security problems have always been of great importance in wireless communication. Traditionally, the transmitted data is encrypted by the keys to assurance the security. However, the commonly used cryptographic mechanisms have several main shortcomings, such as the difficulty in distributing the key over a public medium and the high computational complexity in wireless sensor networks (WSNs).
Recently, physical layer security has attracted much attention. It could enhance the security of wireless communication against eavesdroppers by exploiting the physical characteristics of wireless channels without encryption keys [
1]. The definition of secrecy capacity is the maximum rate of secret information sent from the user to its destination in the presence of eavesdroppers [
2,
3,
4]. It equals to the channel capacity difference between the main channel and the eavesdropper channel. However, to achieve the security, the channel condition limitation must be satisfied for networks without relays. The limitation is that the security can be achieved only when the main channel (source to–relay channel) is better than the eavesdropper channel (source to eavesdropper channel) [
5]. To break through the limitation, the cooperative relay, which helps to improve the main channel condition, has recently been used as a practical technology to provide secret transmission [
3,
4,
5,
6,
7].
Many kinds of approaches have been proposed in light of the physical-layer security under the cooperative communication framework, such as relay strategies and relay selection schemes. For relay strategies, amplify-and-forward (AF) and decode-and-forward (DF) are the most commonly used strategies [
8,
9,
10,
11]. For relay selection schemes, single-relay selection (SRS) and multi-relay selection (MRS) schemes are proposed to improve the secrecy capacity based on the signal-to-noise ratio (SNR) at the destination [
12,
13,
14]. These relay selection schemes all require a centralized controller and are not suitable for the practical networks.
The characteristic of self-organization is of great importance to the distributed WSNs and cannot be realized by the traditional MRS schemes. Thus, game theory has attracted much attention in WSNs. Game theory, a highly appealing mathematical tool, has been used to design algorithms for cooperation and competition scenarios in wireless networks. It has also been applied to the physical-layer security for relay selection and power optimization [
15,
16,
17,
18,
19,
20,
21,
22,
23,
24]. In relay selection schemes, the distributed coalitional game has been studied in wireless networks, where users can self-organize into disjointed coalitions and maximize the secrecy capacity of each user [
15,
16,
17]. The work in [
18,
19] solves the problem of multi-relay selection via a distributed algorithm based on the political coalition formation game and offers a network sum-rate performance/stability tradeoff. Furthermore, in power optimization, an efficient power-allocation protocol based on the coalition formation scheme is proposed in [
20]. It achieves a significant reduction in power consumption and an improvement in payoff for transmitter nodes. A distributed coalition formation algorithm applied to a cognitive radio (CR) network utilizes the power of secondary users to interfere with the eavesdroppers in order to improve the primary user’s secrecy capacity [
21]. In [
22], a two-level decentralized approach based on game theory is proposed to solve the relay selection and resource allocation problems of the D2D networks. In this approach, D2D pairs and relays can form and swap coalitions, and the system capacity can be enhanced significantly. The nontransferable coalition formation game has been employed in [
23] for relay selection in cooperative networks with energy harvesting relays, and it can approach the empirical bounds of the capacity very closely. Furthermore, coalition game theory is also utilized in [
24] to select the optimal relay pairs for improving the secure key generation rate in D2D communications with nontrusted relays.
Compressive sensing (CS) has recently been widely used in wireless communication and signal processing. The CS could capture and represent the compressible signals at a rate far below the Nyquist rate, and the information could be retrieved from a small number of linear measurements [
25,
26,
27]. The CS method has been studied as a physical layer security strategy of wireless networks in many research works. In [
28,
29], CS is used in a wireless network with one source node, one receiver, and one eavesdropper, and the measurement matrix is used as an encryption key to achieve the computational secrecy. Furthermore, authors in [
30,
31] considered the keyless PHY-layer secrecy scenario. The measurement matrix in [
31] is the encryption key to encode the source’s signal, and the secrecy is ensured. Those studies indicate that the measurement matrix can be used to achieve the physical-layer security without the channel state information of eavesdroppers.
However, the networks of the above studies are based on the point-to-point (one source and one destination) communication scenario, and due to the decentralized property of the WSNs, the CS methods in [
28,
29,
30,
31] are not directly applicable to the WSNs [
32]. In [
33], authors firstly utilize the CS-AF (compressed sensing amplify and forward) scheme in WSNs. It indicates that the channel matrix from sources to relays can be used as the secure measurement matrix to achieve security. The results show that the probability of recovery of the eavesdroppers under the CS-AF scheme can be arbitrarily small; or equivalently, in terms of physical security, the CS-AF scheme can dramatically enhance the protection against eavesdropper. However, the influences of relays are not considered.
The main contributions are as follows:
- (1)
We propose a CCS-AF (cooperative compressed sensing amplify and forward) scheme for physical layer security in wireless sensor network, in which relays amplify and forward the received combined sources’ signals. We find that secrecy capacity is not proportional to the number of relays and the secrecy capacity is also sensitive to the source–relay distances.
- (2)
The max-coalition order is newly defined to guide the coalition formation, which is different from the traditional ‘Pareto order’. It is used to optimize the whole network utility instead of the individual utility.
- (3)
A coalitional formation algorithm for multi-relay selection is proposed to find the optimal coalition structure to achieve the maximum secrecy capacity. The simulation results show that the proposed algorithm can improve the secrecy capacity compared with the circumstance with all relays. Furthermore, the distributed algorithm confers to the relays self-organization and self-optimization properties.
The rest of this paper is organized as follows: In
Section 2, a cooperative network model with multi-user and multi-relay is proposed based on CCS-AF. A brief introduction of coalitional game is shown in
Section 3, and the coalition formation algorithm is introduced in
Section 4. The results of simulations are provided and analyzed in
Section 5. Finally, conclusions are drawn in
Section 6.
2. System Model
In this section, we model a cooperative system with multiple sources and multiple relays based on CS. As shown in
Figure 1, there are
sources (
),
relays (
),
eavesdroppers (
), and one destination (
) in the network. The transmission period is divided into two time slots. In the first time slot, the source nodes send their own information to the relay nodes simultaneously. In the second time slot, some or all of the relays will be selected to amplify and forward (AF) the received combined signals to the destination. Besides, the channel state information (CSI) is known to all legitimate users.
The sparsity of the sources’ signal is denoted as
[
34]. Let
denote the source–relay channel matrix, the matrix
denote the relay–destination matrix vector, and the matrix
denote the source–eavesdropper channel matrix. The source–relay distances, relay–destination distances, and source–eavesdropper distances are represented as
,
, and
, respectively. Secrecy capacity, which is the channel capacity difference between the main channel and the eavesdropper channel, is used to measure the system security. It can be represented as
where
is the secrecy capacity,
is the capacity at destination, and
is the capacity at the eavesdropper.
2.1. CCS-AF Scheme
In the CCS-AF scheme, there are there phases, namely the sensing phase, measurement phase, and reconstruction phase.
2.1.1. Sensing Phase
In the sensing phase, only K of N source nodes whose readings are changed in a certain quantity will transmit their data to the relay nodes synchronously. Let denote the signal transmitted by the source . Thus, there are K nonzero elements and N − K zero elements in the N-dimensional sources’ signal . According to the CS theory, the number of nonzero elements in the signal is called the sparsity. Hence, the sparsity of sources’ signal is K.
2.1.2. Measurement Phase
In this CCS-AF scheme, the transmission matrix is used as the measurement matrix of CS. Modeled by the source–relay transmission matrix, the signal received at each relay is the linear combination of the sources’ signal . Furthermore, the signal is compressed from the N dimension to the M dimension through the M × N source–relay transmission matrix.
According to the CS theory, the measurement should satisfy the restricted isometry property (RIP). The transmission matrix is proved as the measurement matrix in the following part.
In the first time slot, the sources send information to relays simultaneously. The power constraints of the sources and relays are
and
, respectively. The source–relay channel matrix
is incoherent with the identity matrix, and satisfies the RIP property with a high probability as long as
, where
is the number of relays,
is a small constant,
is the sparsity, and
is the number of sources [
33]. In this paper, the number of relays
should satisfy Equation (2) [
29,
34]:
The transmission matrix
is equal to
. Besides,
is a
matrix which represents the path loss of the first time slot, and the path loss from the
th source (
) to the
th relay (
) is
. The received signal of relays is represented as
where
is an additive white Gaussian noise (AWGN) vector at relays and the variance is
.
In the second time slot, the selected relays amplify and forward the received sources’ signal to the destination
. The diagonal matrix
represents the channel between relays and the destination. The relay–destination transmission matrix is
, where
is the relay–destination path loss. Thereby, the received signal at the destination is
where
is the diagonal matrix and its entity
denotes the amplification coefficient of
, and
is the noise between relays and D and is a AWGN vector with variance
.
Equation (4) could be rewritten as
where
. The
matches the requirement of the RIP property, because the transmission matrix
satisfies the RIP property and
is a diagonal matrix. Therefore, the transmission matrix
can be used as the secure measurement matrix to encrypt the sources’ signal
.
2.1.3. Reconstruction Phase
The destination receives all the signals from the relays and can recover the sources’ signal
from
by solving the convex optimization problem:
where
is an upper bound on the magnitude of the noise and
is the reconstructed vector at
D.
It should be noted that the eavesdroppers in this model are unable to reconstruct the original signal because they have no knowledge about the measurement matrix. Thus, the eavesdropper cannot overhear the signal from the relay nodes, and the security performance is improved.
2.2. Secrecy Capacity
To calculate secrecy capacity conveniently, we use the singular value decomposition (SVD) method introduced in [
35,
36] to obtain the equivalent parallel channel. The M × N source–relay channel matrix
is transformed to a
parallel channel vector.
Let
, and then the signal at the relays can be represented by
, where
is a diagonal matrix,
and
are both unitary matrixes, and
is the conjugate transpose of
. Hence, the signal received at the relays shown in Equation (3) can be transformed as follows:
As is shown, in Equation (7c),
,
, and
. Then, bringing Equation (7c) into Equation (4), the received signal at the destination can be written as
Due to the property of the unitary matrix, the power of signals
,
, and
cannot be changed by the
and
, and we can know that
,
, and
. Thus, the signal power and the noise power could be formulated as follows:
where
indicates the
th parallel Gaussian channel and
is the
th diagonal entry of
.
Then, the channel capacity
of the main channel is
where
and
are the noise powers of the two time slots, respectively.
The signal received by the eavesdropper
could be expressed as
where
is the transmission vector between the sources and eavesdropper
and
is the noise at
. The power of the signal and the noise at
are
and
, respectively. The channel capacity from
to
is
where
is the path loss between
and
, and
is the noise at
.
Therefore, the eavesdropper channel capacity is as follows:
The secrecy capacity of the CCS-AF system can be represented as based on Equation (1).
The secrecy capacity is the channel capacity difference between the main channel and eavesdropper channel. From Equation (10), we find that when the relay number increases, the capacity obtained by each relay decreases because of the reduction of the amplification coefficient. However, the large number of relays can improve the secrecy capacity. Thus, there exists a certain relay number that maximizes the secrecy capacity. Meanwhile, the position of the relay affects the main channel condition. To obtain the maximum secrecy capacity, we proposed a coalition formation algorithm to select the relays based on coalition game theory because of the distribution property.
3. Coalitional Games
3.1. Coalition Game Model
In wireless networks, the coalitional game is an effective mathematical tool to enhance the PHY security and improve the performance. As is defined, a coalitional game with transferable utility (TU) is represented by a pair
, where
is the set of players and the function
is a value for each coalition. Denote
as an element in
and
as the payoff of coalition
during its time slot, and the function
is defined as follows [
15]:
where
is the gain in terms of secrecy capacity for coalition
given by (10),
is a security loss function for coalition
during the first slot, and the security loss caused by the
th (
) eavesdropper in the first slot is given by Equation (12). Let
, and then
is the secrecy capacity and acts as the measure of the wireless communication security. The cost function
is computed according to Equation (13), which is the security loss caused by eavesdroppers.
3.2. Coalition Formation
The coalitional game can be divided into two kinds of orders. One is coalition value orders, and the other is individual value orders. Coalition value orders compare the value of two collections, such as the utilitarian order, in which implies . In contrast, the individual value orders compare the individual payoff of each player, such as the Pareto order. Assuming that the collection and the collection have the same players and the payoff of a player in these two collections are denoted by and , respectively, which can be written as by Pareto order if the collection is better than the collection . In other words, is preferred to if at least one player’s utility is increased without decreasing other players’ utilities.
In this CCS-AF network, only the coalition that obtains the highest secrecy capacity can be selected, which means only the relays in the coalition with higher secrecy capacity have more chances for cooperation. If a relay cannot participate the coalition with the highest secrecy capacity, it will obtain nothing. Differently from the cases where the individual values are considered, we consider the whole coalition value, where the Pareto order is not suitable. The two coalitions are preferred to be merged into one coalition if a higher coalition value can be obtained. This merge operation makes the players in these two coalitions have more chance to win the utility. To deal with the cooperative problem, a new comparison relation rule is defined as follows.
Definition 1. Consider two collections, and , which have the same players. Then, the ‘Max-Coalition order’ is defined as .
3.3. Merge-and-Split Rule
To make sure the relays can self-organize to form the coalition, the “merge” and “split” rules are defined as below.
Merge Rule: Merge any set of coalitions
whenever the relays prefer the merged form.
Split Rule: Split any coalition
whenever the relays prefer a split form.
Based on the merge-and-split rules and the ‘Max-Coalition order’ proposed above, the relays will form a new coalition if split-and-merge operations improve the secrecy capacity; otherwise, they keep the original coalition.
4. Coalition Formation Algorithm
In this CCS-AF network, some of the relays could form a coalition to maximize the system secrecy capacity based on the newly defined Max-Coalition order. Coalitions would like to merge if the merging forms a preferred coalition. It is implied that a group of relays will sign an agreement to merge into a larger coalition if the coalition yielded by the merge has larger secrecy capacity. Similarly, a coalition should split if the splitting can form a preferred coalition. At the beginning, relays are noncooperative nodes and the coalition structure is
. Therefore, the first operation should be merging. Based on merge-and-split rules and ‘Max-Coalition order’, the coalition formation algorithm is shown in
Table 1. The coalition formation algorithm needs to know the transmission matrix to calculate the secrecy capacity of the possible coalition and decide whether to form this possible coalition. This requires that the CSI must be accurate. If the CSI is wrong, the relays cannot obtain the accurate transmission matrix. This makes the relay node unable to calculate the security capacity of the possible coalition correctly. If the CSI error is too large, the new formed coalition based on the ‘Max-coalition order’ may have a lower secrecy capacity than the old coalition. This will make the network unable to select the best relay to obtain the highest security performance through the proposed algorithm.
In order to make the topology adaptive to the relays’ dynamic location, the coalition formation algorithm is repeated periodically during the network operation. There are three stages in the algorithm: neighbor discovery, secrecy capacity calculation, and the iterative coalition formation. After these three stages, the topology is stable and the appropriate coalition will be selected.
In the neighbor discovery stage (stage 1), each coalition surveys the environment and finds the possible neighbor coalition to cooperate with. In the secrecy capacity calculation stage (stage 2), the coalition calculates the secrecy capacity periodically. Then, the iterative formation process begins (stage 3). In this stage, relays determine whether to merge with other coalitions to form a new coalition or sign a split agreement to break the current coalition. If the merge operation can yield a new coalition which has a larger secrecy capacity than coalitions and , coalitions and in will merge based on the Max–Coalition order: the two coalitions and will form a new coalition, . This is mainly because merging brings a long-term secrecy capacity improvement of this network. The merging operation will stop if there is not a better merge form. After merging, the coalitions are about to split based on the split rule. If coalitions can find a better split form through the Max-Coalition order, the relays in those coalitions will sign the split agreement to form a new coalition, . This is because splitting improves the secrecy capacity of the network. The network will repeat the merge-and-split operations until the highest secrecy capacity has been obtained. The coalition which can obtain the highest system secrecy capacity is selected to help sources transmit the information. Under this circumstance, the coalition is stable and relays have no incentive to merge or split to form a new coalition.
The complexity of this algorithm is related to the split/merge operations. In terms of the split operation, supposing the current coalition is , the number of potential coalitions grows exponentially with the number of relays in coalition . Supposing the number of relays in the current coalition is M and the total number of relays in the network is , the number of merge trails is , and this results in the complexity of , while the real computation load is usually far below this, for the algorithm will stop when a better coalition is found. The complexity is the number of all possible merge operations under the current coalition structure, while the real computational load is the number of real operations before the merge operation stops, which means there is no other better coalition with higher secrecy capacity that can be obtained through the merge operation. Obviously, the number of real merge operations is far below the number of all possible merge operations under the current coalition structure. In other words, there is no need for the algorithm to traverse all possible situations, because the iteration of operation will stop once a better coalition is found.
5. Simulations
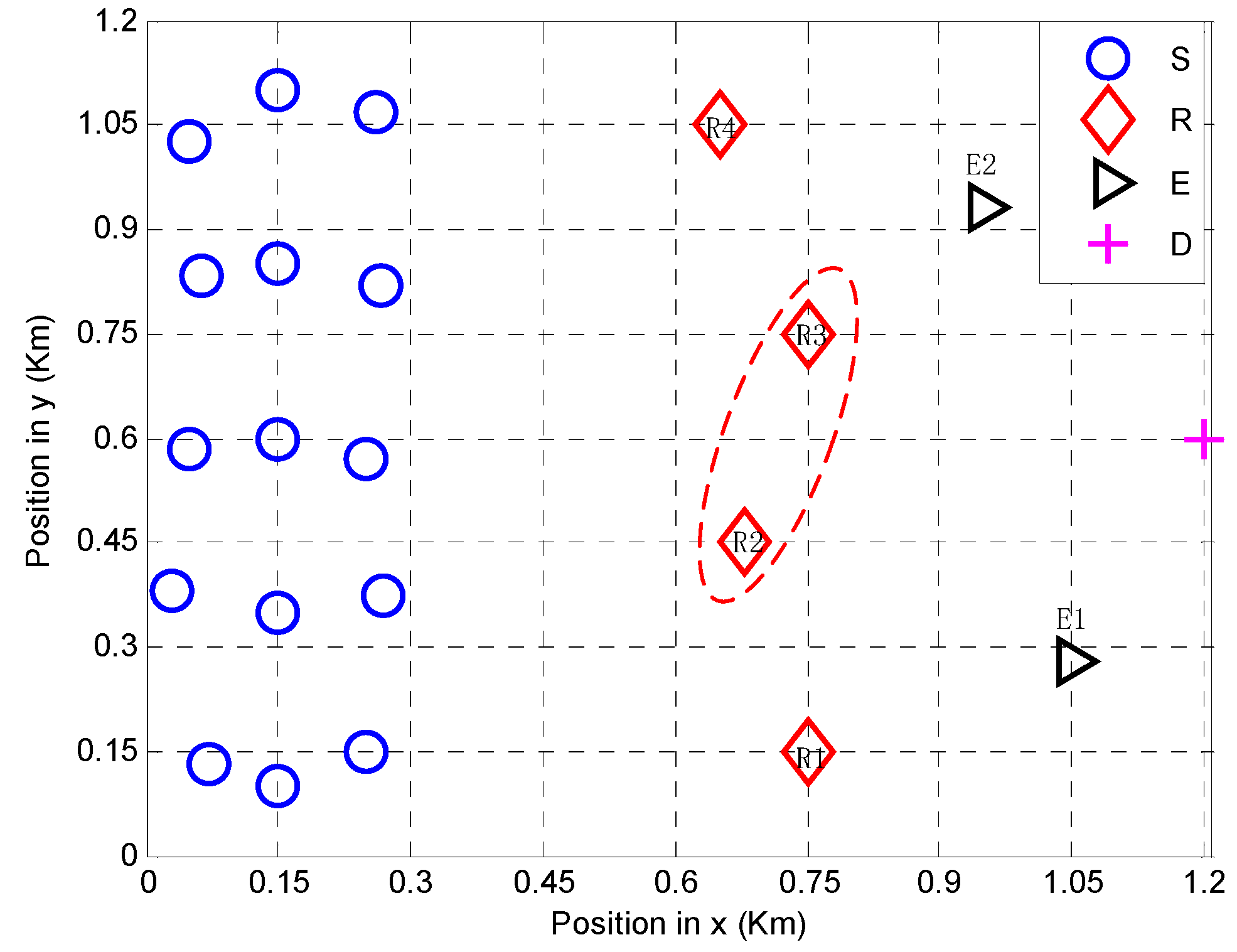
We consider a coalitional network with 15 users, four relays, two eavesdroppers, and one destination located in a square of
, as shown in
Figure 2. Sources are randomly distributed between
to
. The coordinates for the destination and eavesdroppers are set to
for
,
for
, and
for
. The path loss
is 4, the power constraints of sources and relays are
and
respectively, and both
and
are
.
5.1. Coalition Formation Process
As shown in
Figure 2, the coordinates for relays are set to
for Relay 1 (
),
for Relay 2 (
),
for Relay 3 (
), and
for Relay 4 (
). It is shown in
Figure 2 that
and
form a coalition and help sources to forward the information. The capacities of all potential coalitions and the relay utility are shown in
Table 2. The details of the coalition formation process are described below.
At first, for both Max-Coalition order and Pareto order, the relay nodes are noncooperative and each relay is a coalition. The first operation is a merge operation, and it starts with (the nearest relay from the destination), which attempts to merge with (the closest relay to ). Then, the coalition is formed. Subsequently, the coalition tries to merge with (the nearest relay to the coalition ) to form a three-relay coalition. Then, the process of Max-Coalition order and Pareto order will be described separately.
For Max-Coalition order, the coalition is formed successfully because the system secrecy capacity is improved from 1.4087 to 1.4583. After that, the coalition has an incentive to merge with , but this merge is impossible as the system utility decreases (). Until this moment, the merge operation is finished, for no other better coalition can be obtained by the merge operation, and the split operation begins. For the first split operation, (located in the edge of the current coalition) splits from the coalition successfully, because the split operation can enhance the secrecy capacity from 1.4583 to 1.5547. Then, the iteration process ends. Thus, the coalition is the selected coalition, and its utility is . As a result, for Max-Coalition order, the coalition cannot merge or split any further, and the final coalition structure is .
In contrast, based on Pareto order, the coalition cannot be formed. This is because the utilities of () and () cannot be improved through this merge. Then, the coalition tries to merge with , but the merge operation fails for the same reason (for and for ). For Pareto order, the coalition is selected and its utility is . It can be seen that the utility obtained by Max-Coalition order is higher than that of the Pareto order, and this result demonstrates the effectiveness of the Max-Coalition order.
5.2. The Adaption on the Relay’s Mobility
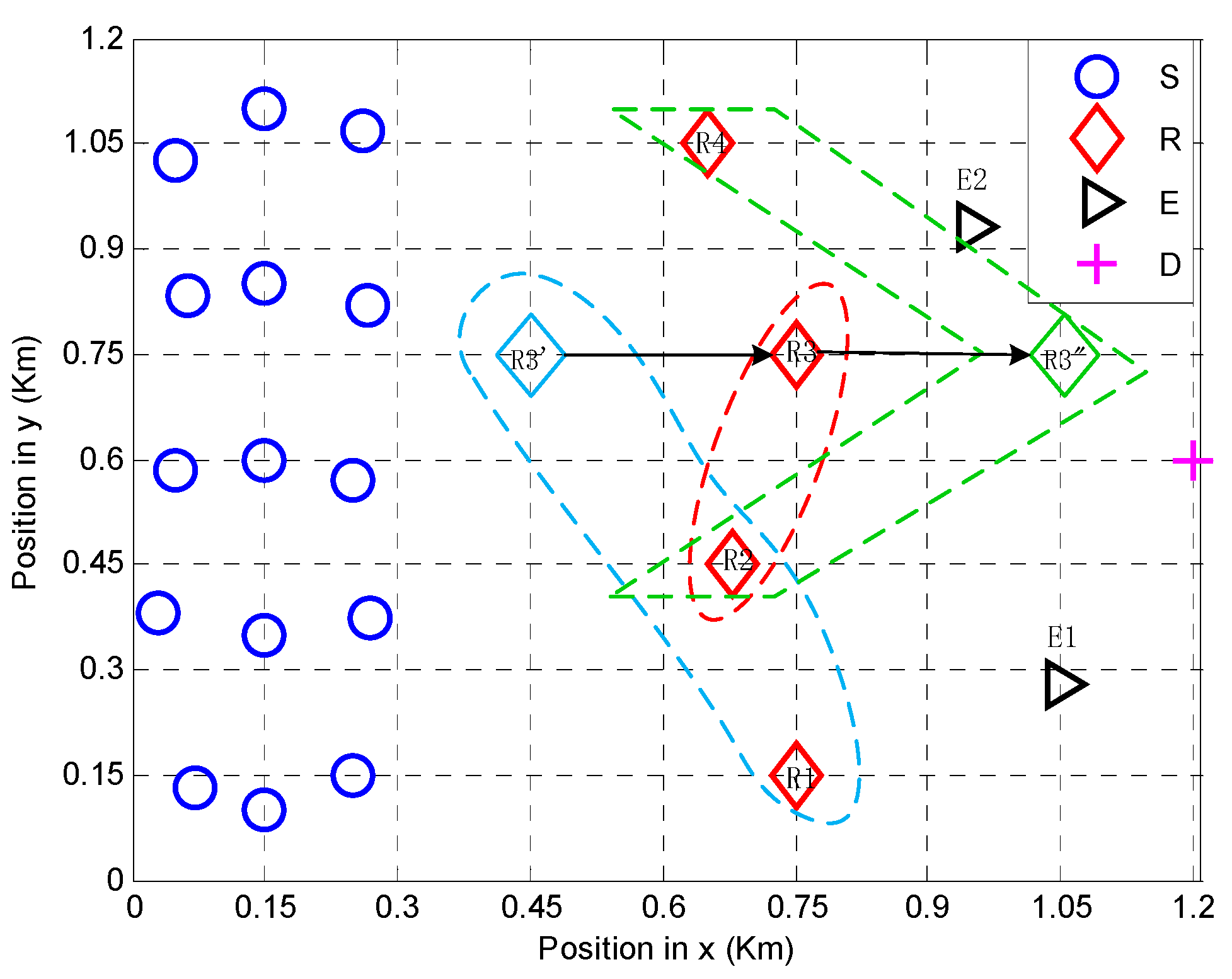
In this section, the algorithm’s ability for handling the relay’s mobility is studied. For this purpose,
in
Figure 2 is moved horizontally from
(
) to
(
). The change of the coalition structure and the performance are shown in
Figure 3 and
Figure 4, respectively.
In
Figure 3, the coalition structure changes dynamically when relay
changes its location. When relay
moves from sources to the destination,
first splits from
. When
moves close to destination,
merges and forms the coalition
.
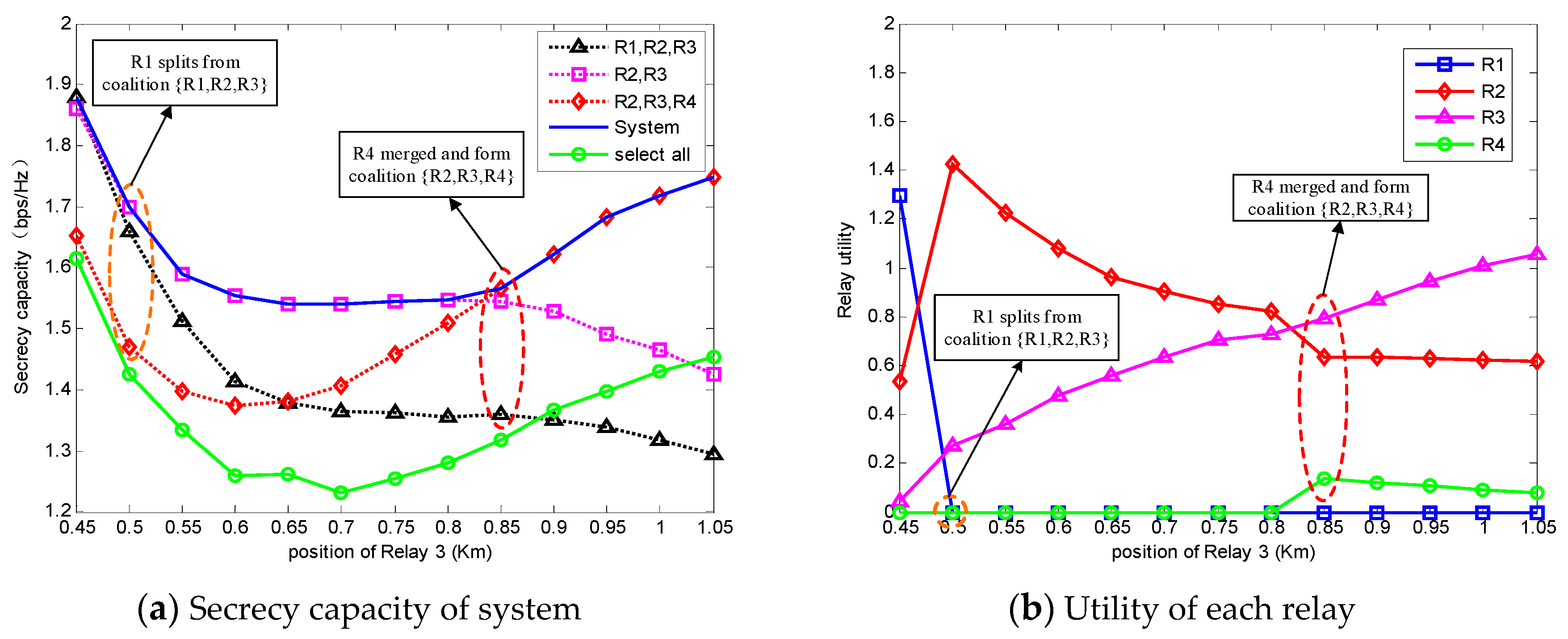
Figure 4a is the secrecy capacity of the system, and
Figure 4b is the utility of each relay accordingly. In
Figure 4a, it is obvious that the system secrecy capacity obtained by the coalition formation algorithm is much higher than the circumstance when all relays are selected. This phenomenon proves that the coalitional game algorithm improves the system security.
Obviously, the selected coalition through the coalition formation algorithm is stable based on the Max-Coalition order, because there is no relay that has an incentive to split or merge and form another coalition which can obtain a higher system secrecy capacity. Due to the fact that the algorithm prefers a higher secrecy capacity to keep the stability of the coalition, the coalition structure will change to obtain a higher capacity when
moves from
to
. We can easily know that the splitting of
at
is beneficial to both
and
from
Figure 4b, so
splits from
. During the movement of
, the utility of
is increasing, and this is because
is getting closer to the destination. After
moves at
, the system capacity starts increasing. It is clear that the merging of
increases the utility of
and the capacity of the system.
Obviously, the secrecy capacity obtained through the proposed algorithm is higher than the secrecy capacity obtained with all relays. This is because the relays can self-organize into some coalitions, and the best coalition structure will be formed after some iteration guided by the ‘Max-Coalition order’. Due to the property of the ‘Max-Coalition order’, the relays will try to form the coalitions which can obtain a higher secrecy capacity. Thus, the final formed coalition structure is the best structure and it is stable because relays cannot form another structure with a higher secrecy capacity. In the final state, the relays in the best coalition which obtains the highest system secrecy capacity will be selected to transmit the source information. Therefore, we can easily know that the selected relays have a higher ability to obtain the secrecy capacity than the other unselected relays, and the total relay power will be only allocated to these selected relays. In other words, this relay-selection algorithm can select better relays and increase the efficiency of the total relay power. Thus, the secrecy capacity is improved by the proposed algorithm.
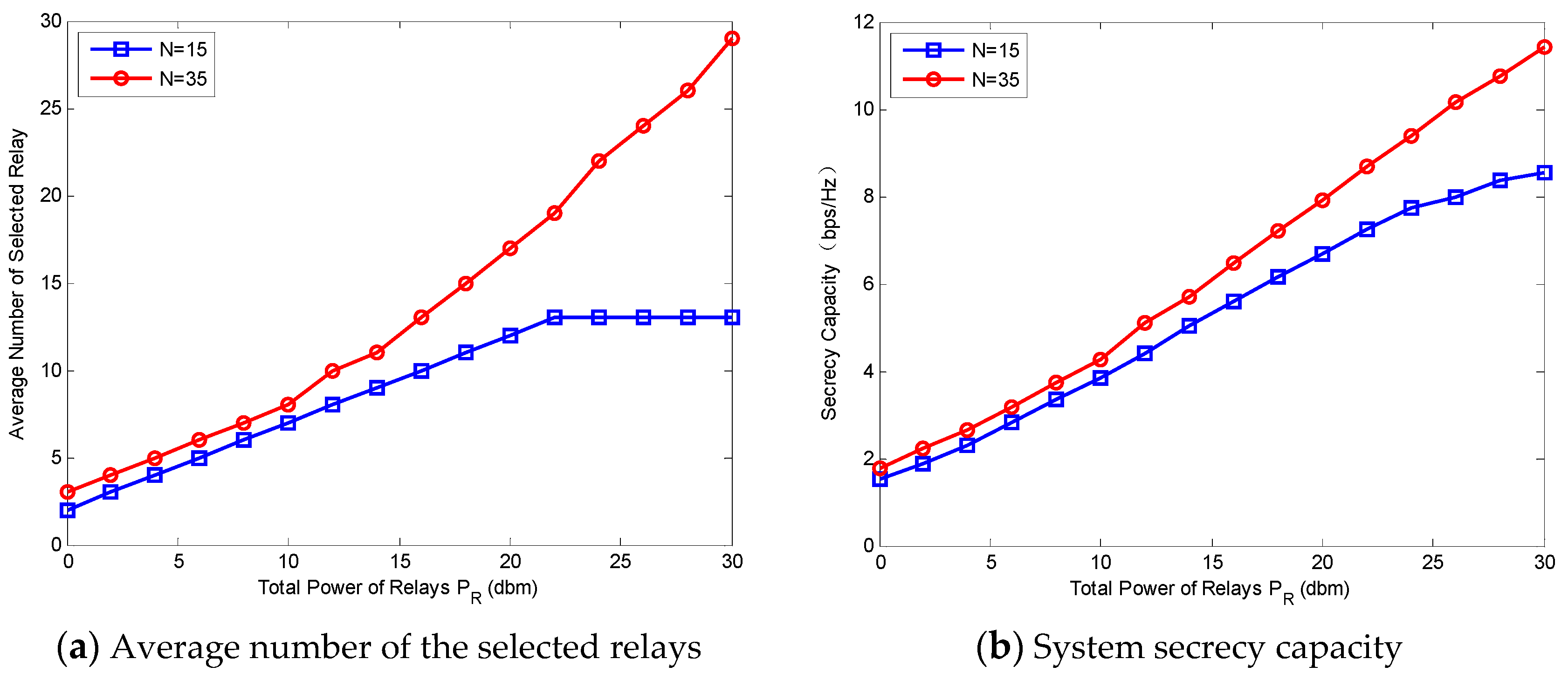
5.3. The Effect of Power on the Performance
Figure 5 shows the system performance and the average size of coalitions versus
, where the number of sources
is set to
and
, respectively. The total power of sources
and
varies from
to
.
Figure 5a is the average number of the selected relays with different
. It can be observed that the average number of selected relays increases with the increase of
. This implies that the higher
is, the more relays that have a chance to gain their utilities. Compared with the circumstance when
, especially when
is large, the number of selected relays when
is higher. When
, the number of selected relays (when
) is no more than 15; this can be explained by Equation (2).
Figure 5b demonstrates the maximum system secrecy capacity when the number of selected relays is set as in
Figure 5a. The secrecy capacity with each
increases with the increase of
. In other words, higher
results in a better system performance.
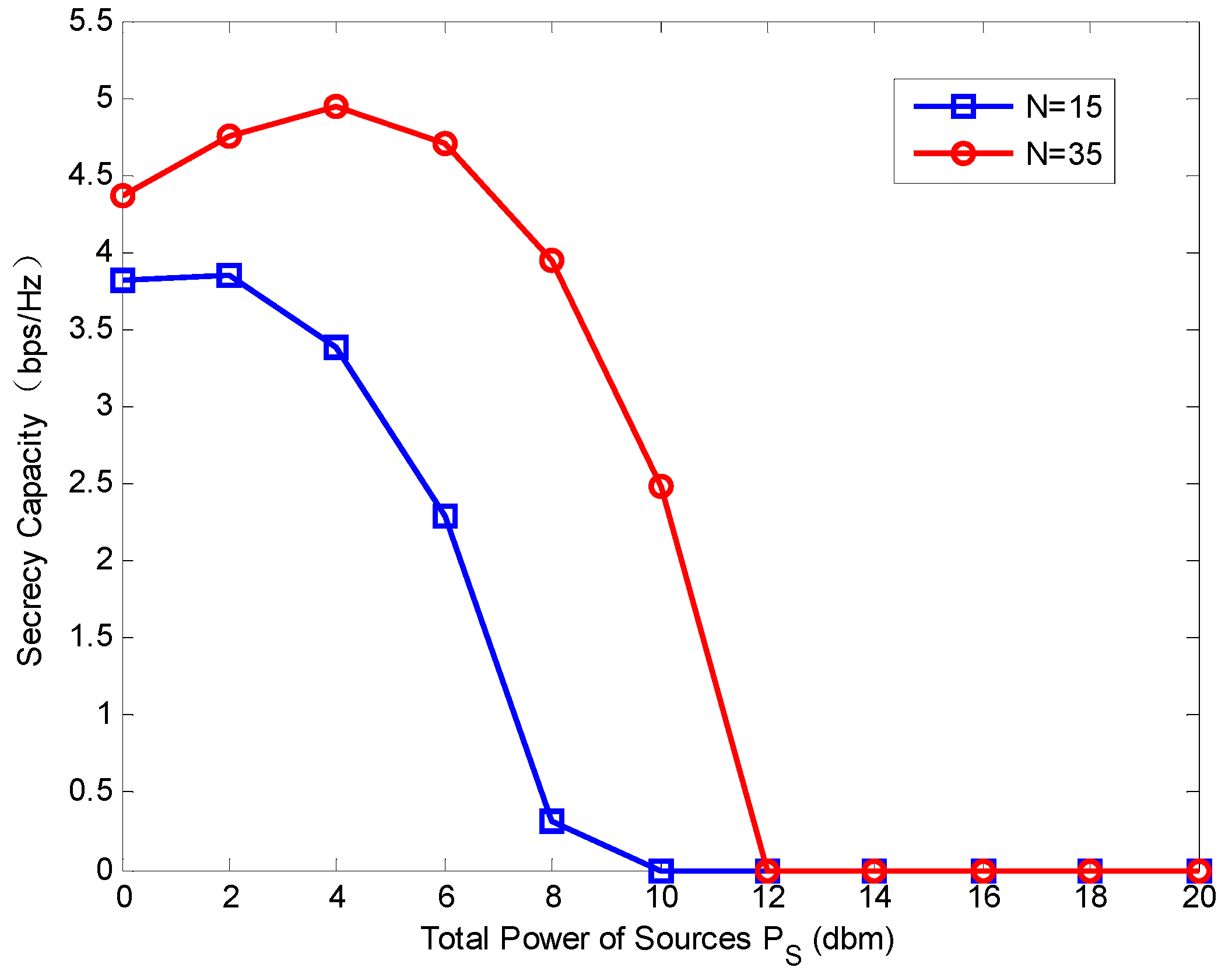
Figure 6 represents the secrecy capacity versus
where the number of sources
is set to
and
, respectively. The total power of relays
and
varies from
to
. The secrecy capacity is first increased and then decreased along with the increasing of the
. When
is larger than a certain value, the secrecy capacity will drop to zero (for
and
, the certain values of
are
and
, respectively). This means the too-large
has a negative effect on the system security. This phenomenon can be explained by
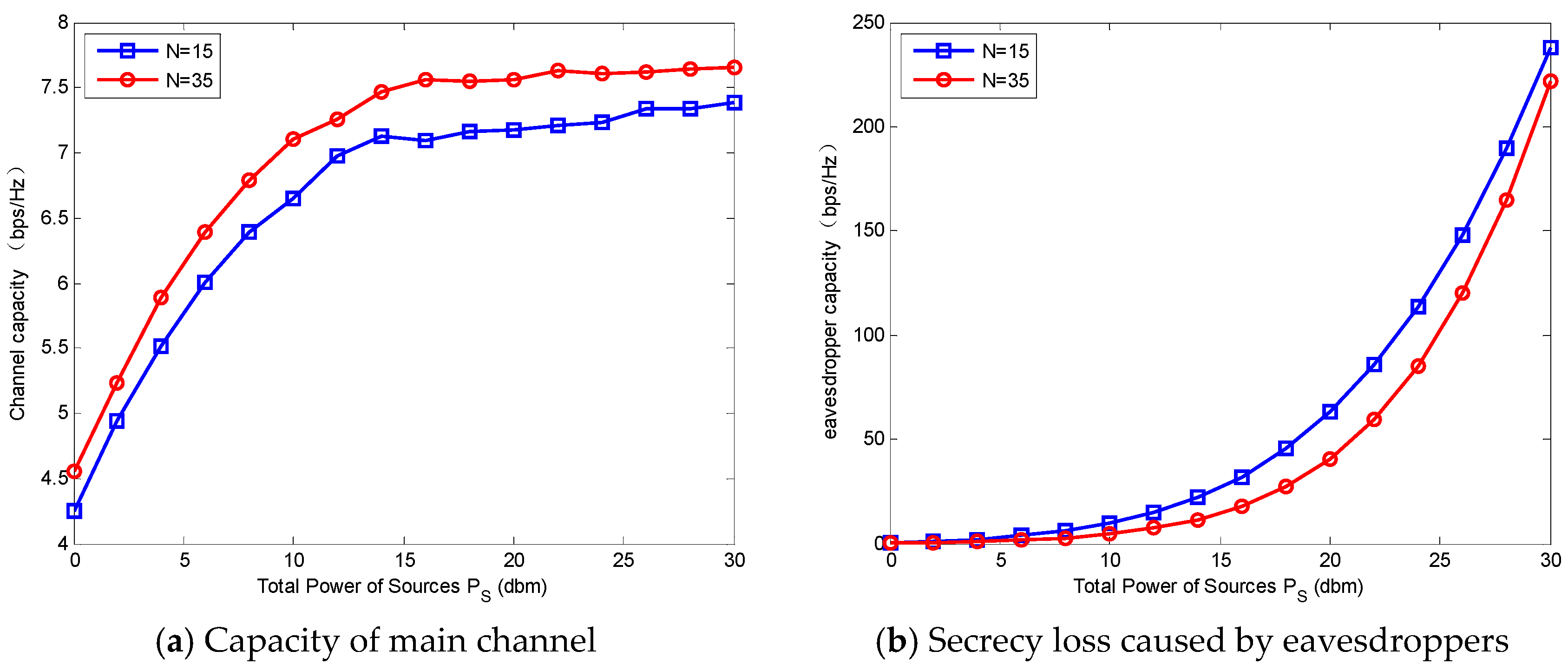
Figure 7a,b. When
increases, the channel capacity goes up first and then stays steady at the point about
. While the secrecy loss caused by eavesdroppers increases slowly at first, and at the point about
, it goes up rapidly. In other words, when
is larger than a certain value, the increase of eavesdropper capacity is much faster than that of the channel capacity. Thus, the large
degrades the secrecy capacity.