An Effective and Secure Key Management Protocol for Message Delivery in Autonomous Vehicular Clouds
Abstract
1. Introduction
2. Related Work
3. Proposed Vehicular Networks Architecture
3.1. Problem Statement and Solution Objectives
3.1.1. Time-Consumption
3.1.2. Cost-Effectiveness
3.1.3. Verification
3.1.4. Anonymity
3.1.5. Confidentiality
3.1.6. Light Weight
3.2. Cloud Model
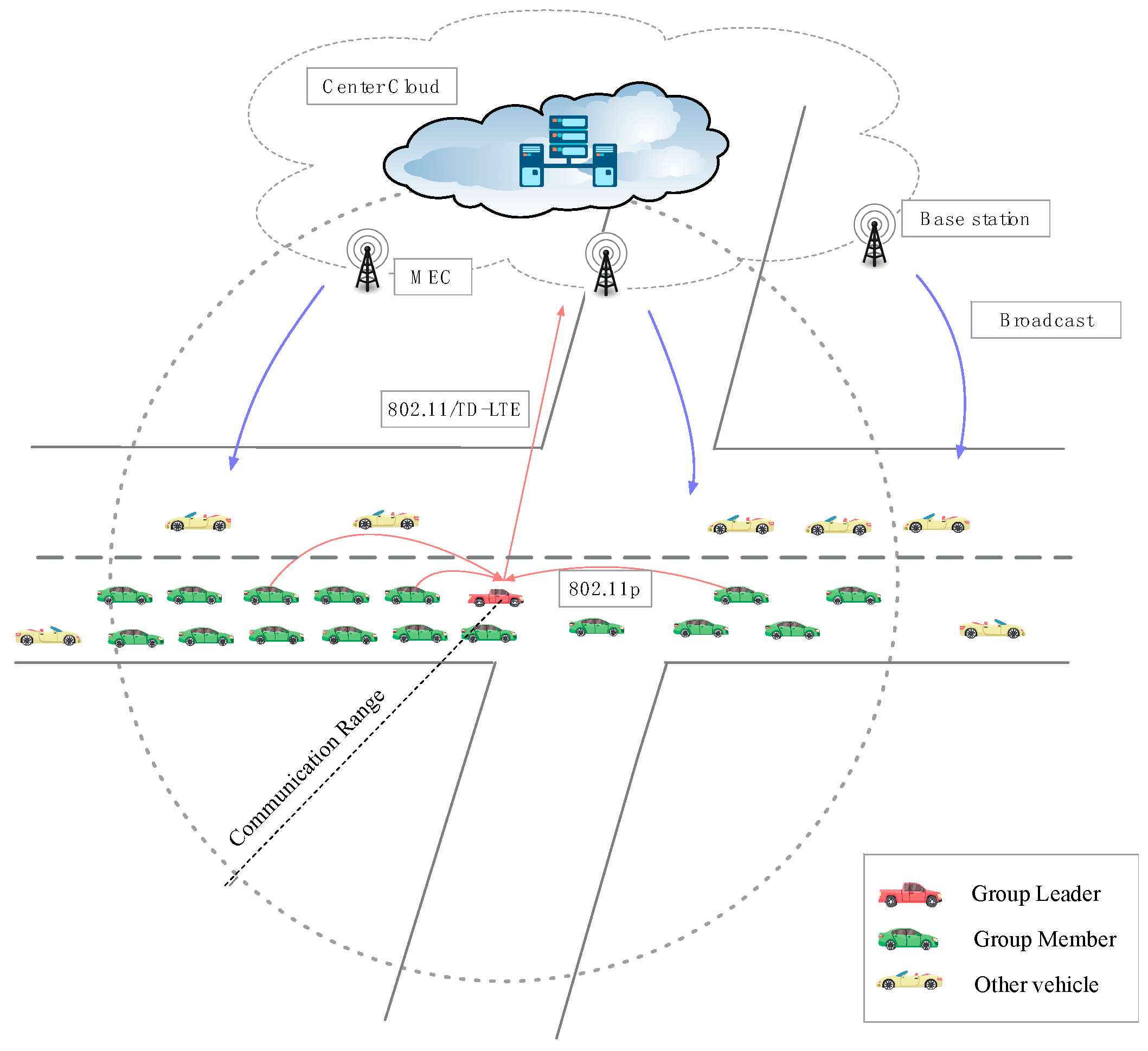
- Autonomous Vehicular Cloud: A mobile cloud consists of a large number of mobile sensor nodes played by autonomous vehicles and a set of aggregation-and-forwarding nodes, namely subgroup leaders (GLs). Each GL aggregates the data from the other vehicle nodes in its subgroup and forwards to the CC. The vehicles provide under-utilized resources and in return they receive the welfare from the central cloud for services [35]. Vehicles in the vicinal communication range select the GL by the method [36] which acts as the gateways. All vehicles in VCs are divided into many subgroups that are administered by their respective GLs. The vehicles can access the resources from cloud servers by vehicle to cloud communication (V2C) and other vehicles by vehicle to vehicle (V2V) communication. As a self-organized group of cooperative vehicles, they can lengthen the communication durability within its own communication range. The decentralized architecture can make less cost of the central cloud and reach an effective implement and key delivery.
- Central Cloud: A central cloud has many more resources and is mainly used for registration, complicated computation, massive data storage, and global decisions [1]. The central cloud provides services for vehicles. Here, mobile edge computing (MEC) implemented at the base stations (BS) is useful in reducing latency and improving localized user experience [37]. Delay-sensitive services are executed and delivered much faster due to the close proximity of end users to the MEC infrastructure [38].
- Private Key Generator (PKG): The PKG included in the CC is a trusted party that generates partial private keys to users. The PKG is fully trusted by all parties in the network and cannot be compromised.
4. Proposed Protocol
4.1. Types of Keys
- The Secret Key between the PKG and a Vehicle: Each vehicle shares a unique individual key with the PKG. For example, if a vehicle wants to transmit the sensitive data to the CC directly bypassing the GL, or if it fails to communicate with the GLs, the node can encrypt the information using the secret key and send it to the CC. In addition, it is convenient for the CC to calculate the group key via .
- Group Key: We consider all the authorized vehicles as one large group, in which all registered vehicles share one secret key. The group key is mainly used for broadcasting traffic messages without obtaining by other illegal vehicles, and also it can exclude the compromised node from the group easily through changing the group key. Only the CC can update the key when a vehicle leaves or joins the group.
- Subgroup Key: In the cluster-based structure, the pool of members is categorized into small groups called subgroups, which can minimize the computation complexity in the key updating phase and achieve a secure key delivery. All vehicles in a subgroup share one key, named subgroup key, which is mainly used for securing broadcast messages, such as sensitive commands or the change of member status in one subgroup. Only the GL can update the subgroup key when the member joins or leaves the subgroup.
- Secret Key between the GL and the Vehicle: The function of constructing the secret key between the GL and the vehicle is to calculate the subgroup key for them. It is a secure way to deliver the secret key by key agreement instead of generating it by the GL itself.
4.2. Types of Information
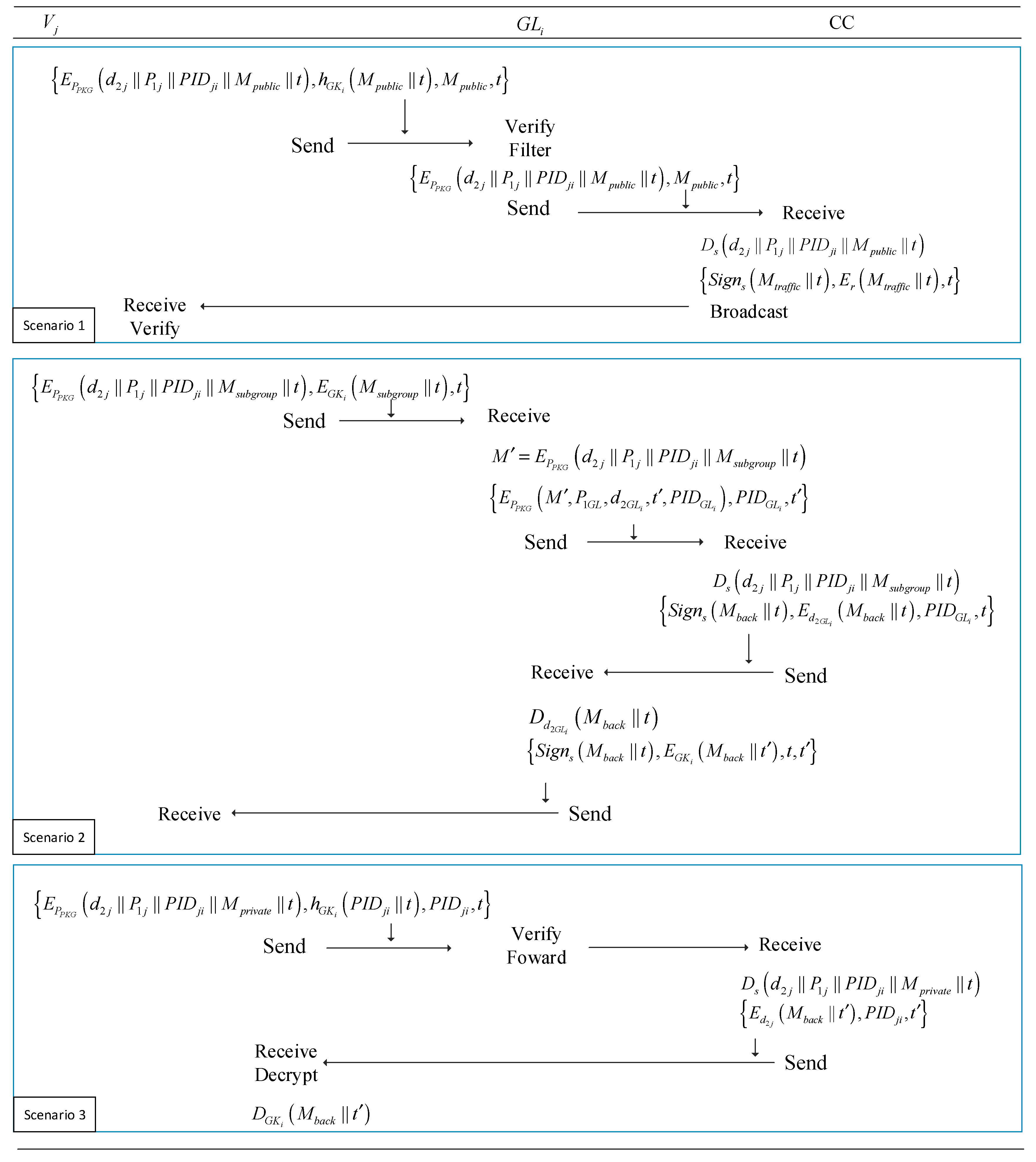
- Public traffic information: This kind of traffic information collected by vehicular nodes and analyzed by the central cloud aims to help vehicles take intelligent decisions and enhance security and quality of driving. These traffic messages based on related services and applications include real time traffic information, intelligent decision hint, localizing events and emergency warning etc.
- Private custom information: This type of information is related to the privacy of drivers, such as parking space booking, infotainment, electronic logging, service spot detection, specific route navigation and some other sensitive data. The different service requirements should be encrypted to protect from being eavesdropped.
- Group sharing information: This type of information used to be shared with all members in one subgroup, such as the private change of member status, updating subgroup keys and subgroup services etc. This kind of information should be acquired by the subgroup members rather than others.
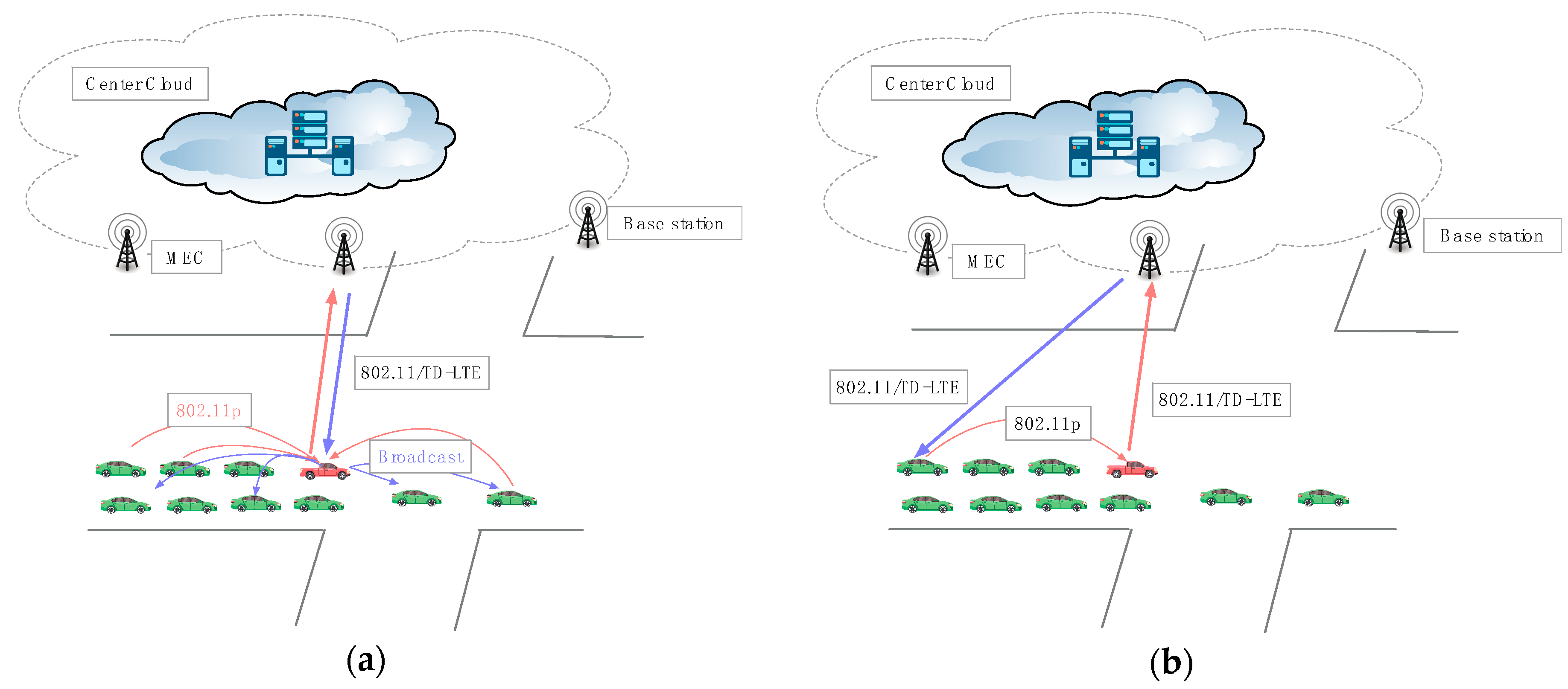
4.3. Types of Transmitting
4.4. The Details of the Protocol
4.4.1. System Setup
4.4.2. Registration
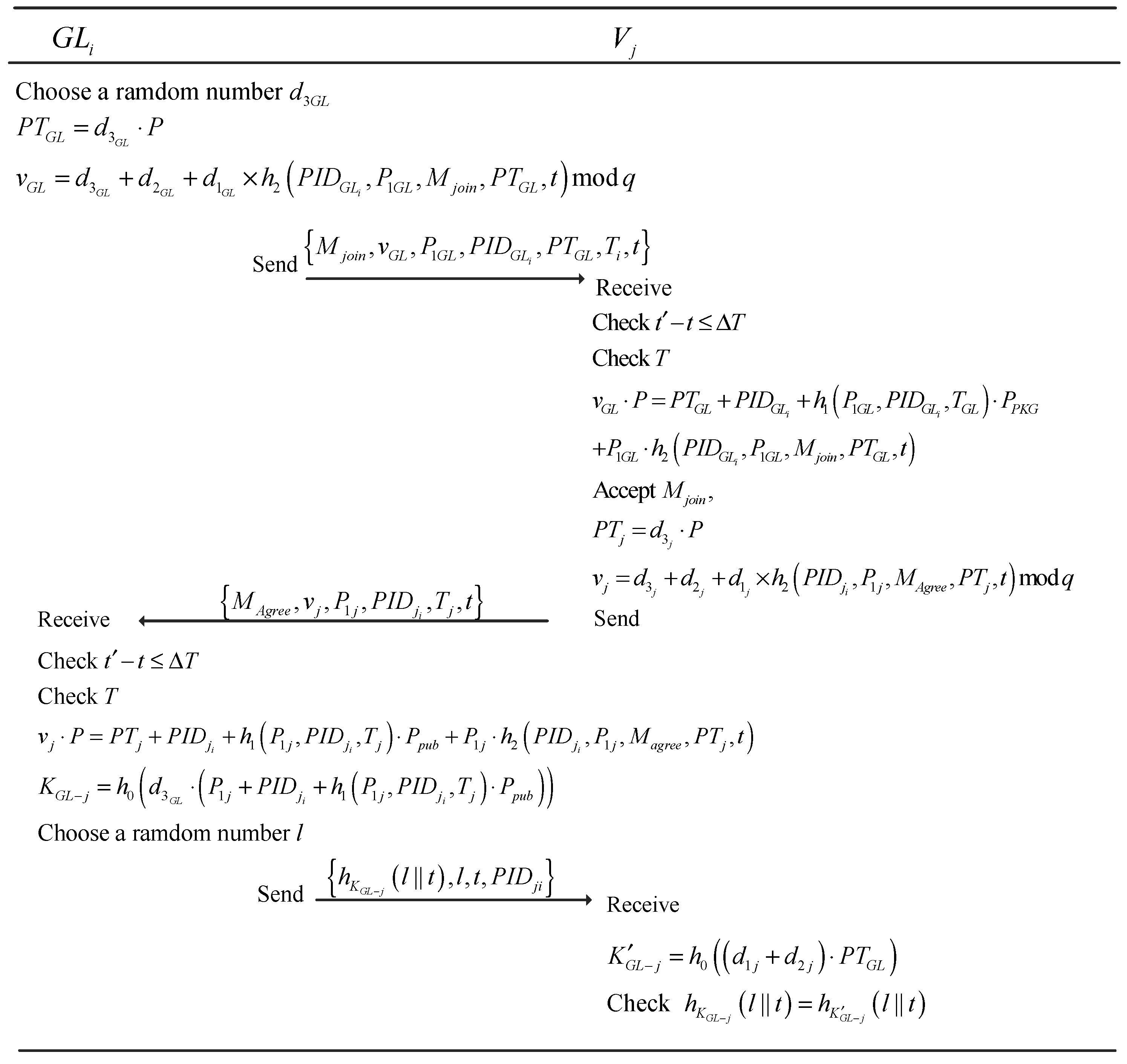
4.4.3. Subgroup Formation and Pairwise Key Generation
- Validate the freshness of by checking , where indicates the valid time interval.
- checks the expiration time of .
- checks the equation:
4.4.4. Subgroup Key Generation
- Find such that
- Select a random element as the subgroup key and compute:
4.4.5. Group Key Generation
- Find such that
- Select a random element as the subgroup key and compute:
4.4.6. Data Transmission
4.4.7. Key Updating
5. Security Analysis
5.1. Resistance to Replay Attack
5.2. Message Tampering/Fabrication/Alteration Attack
5.3. Backward Secrecy
5.4. Forward Secrecy
5.5. Insider Attacks
5.6. Traceability
5.7. Conditional Privacy
5.8. Resistance to Black-Hole Attacks
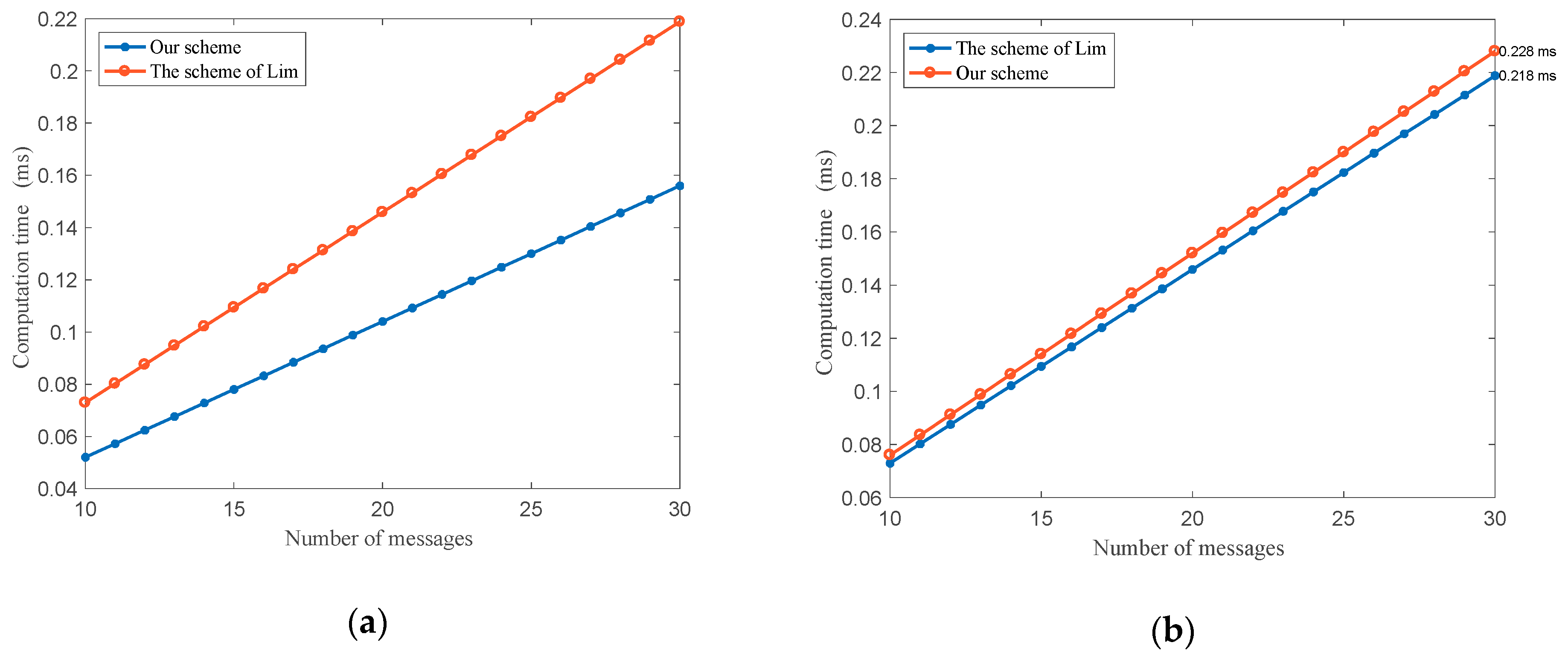
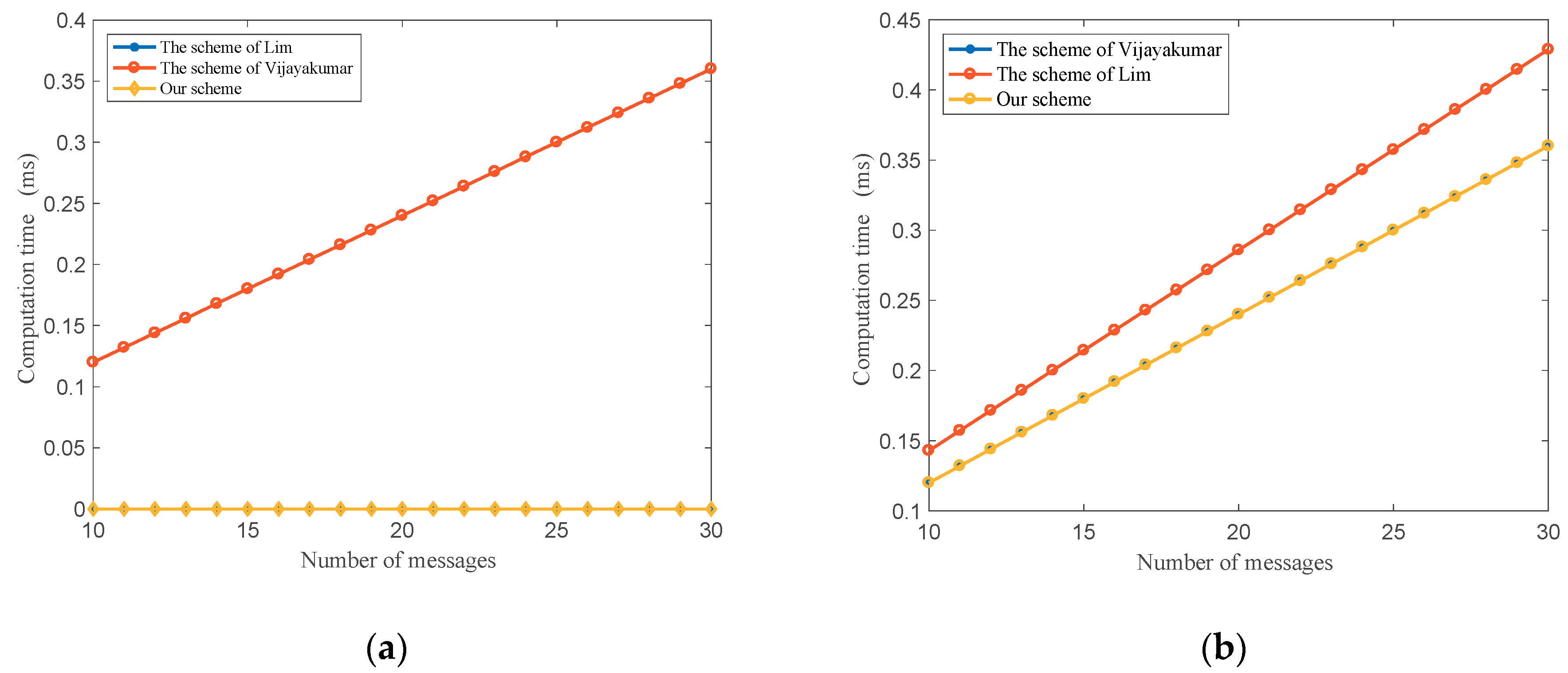
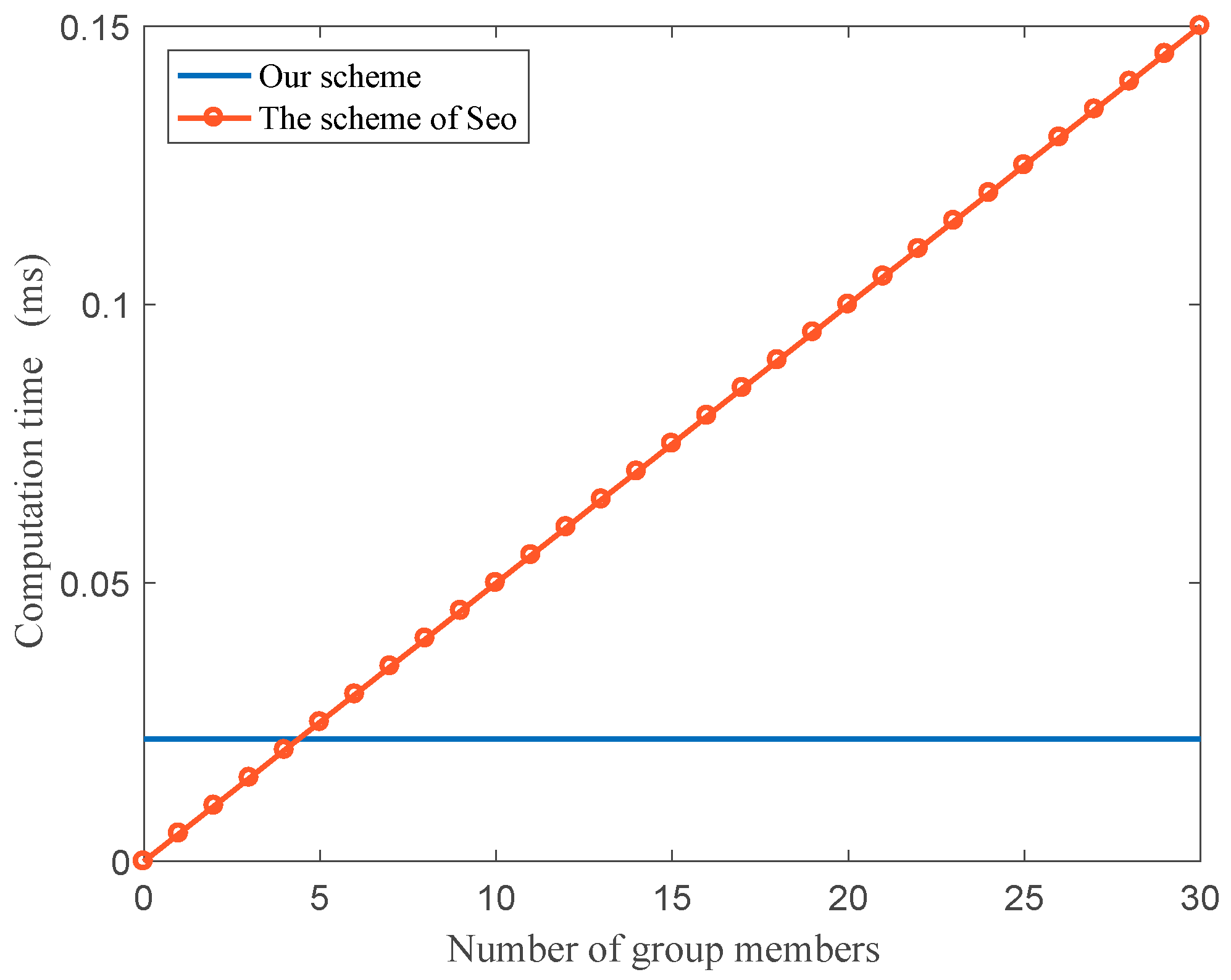
6. Comparison with Related Work
6.1. Communication Overhead
6.1.1. Information Transmitting Process
6.1.2. Key Updating
6.2. Transmission Overhead
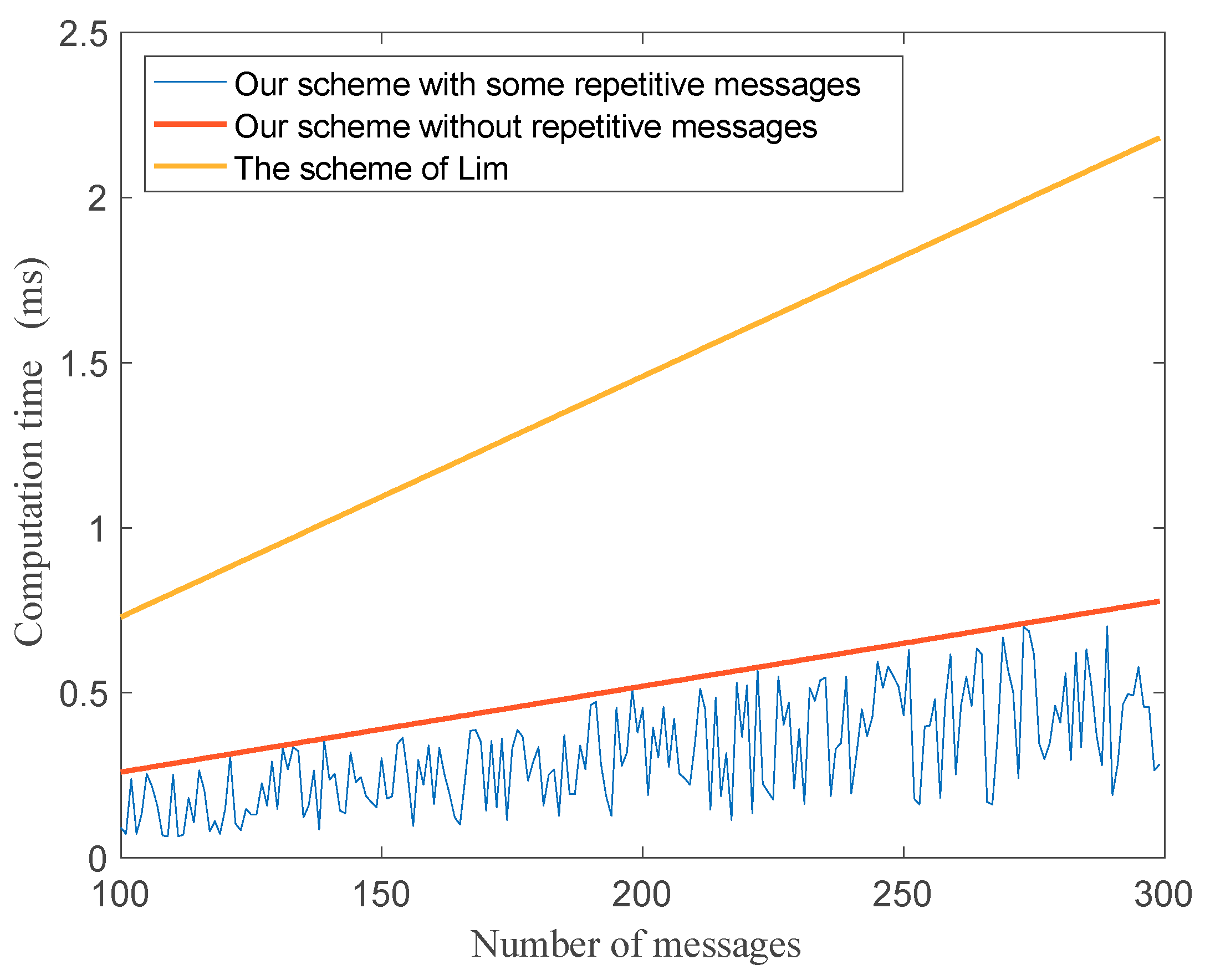
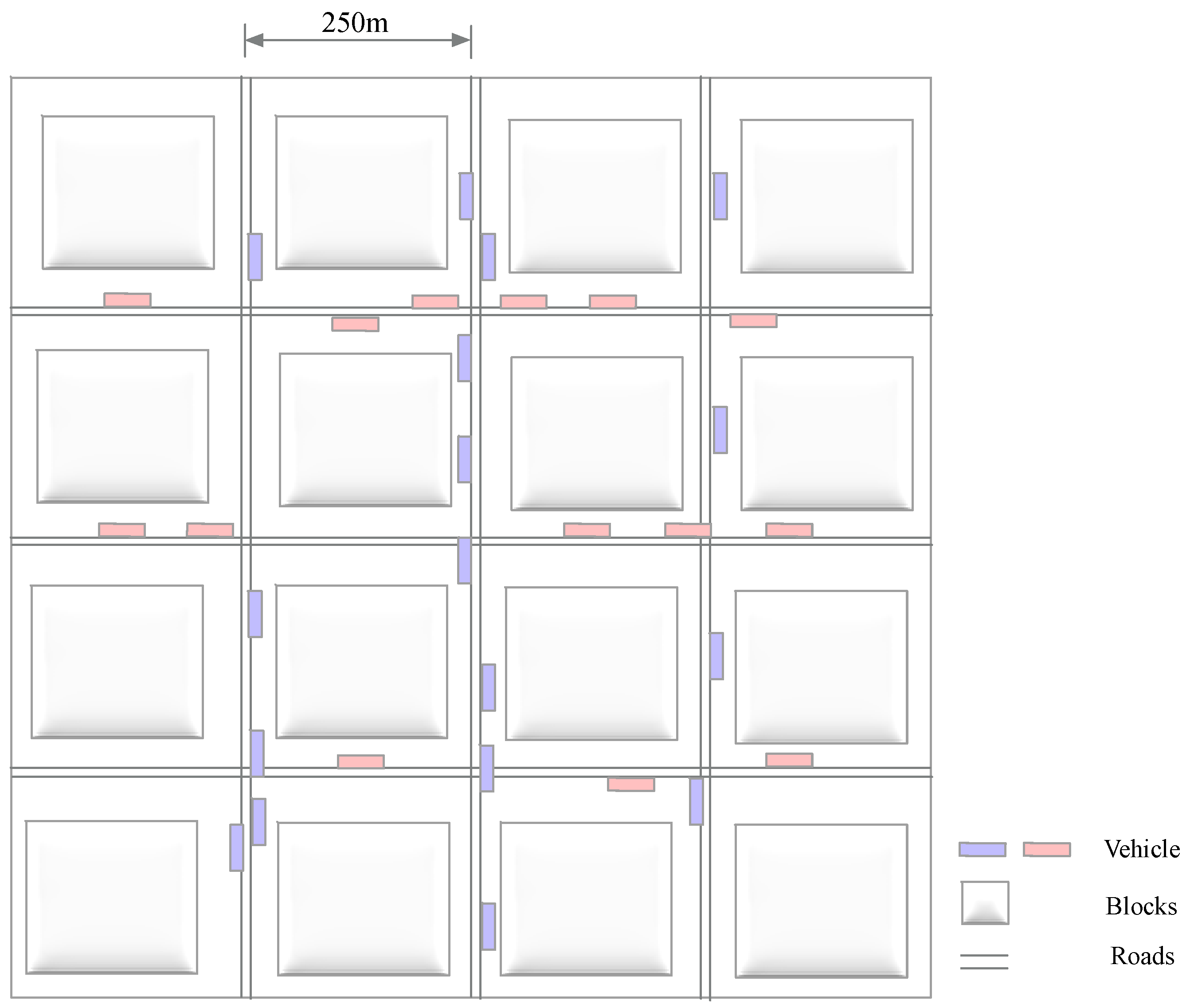
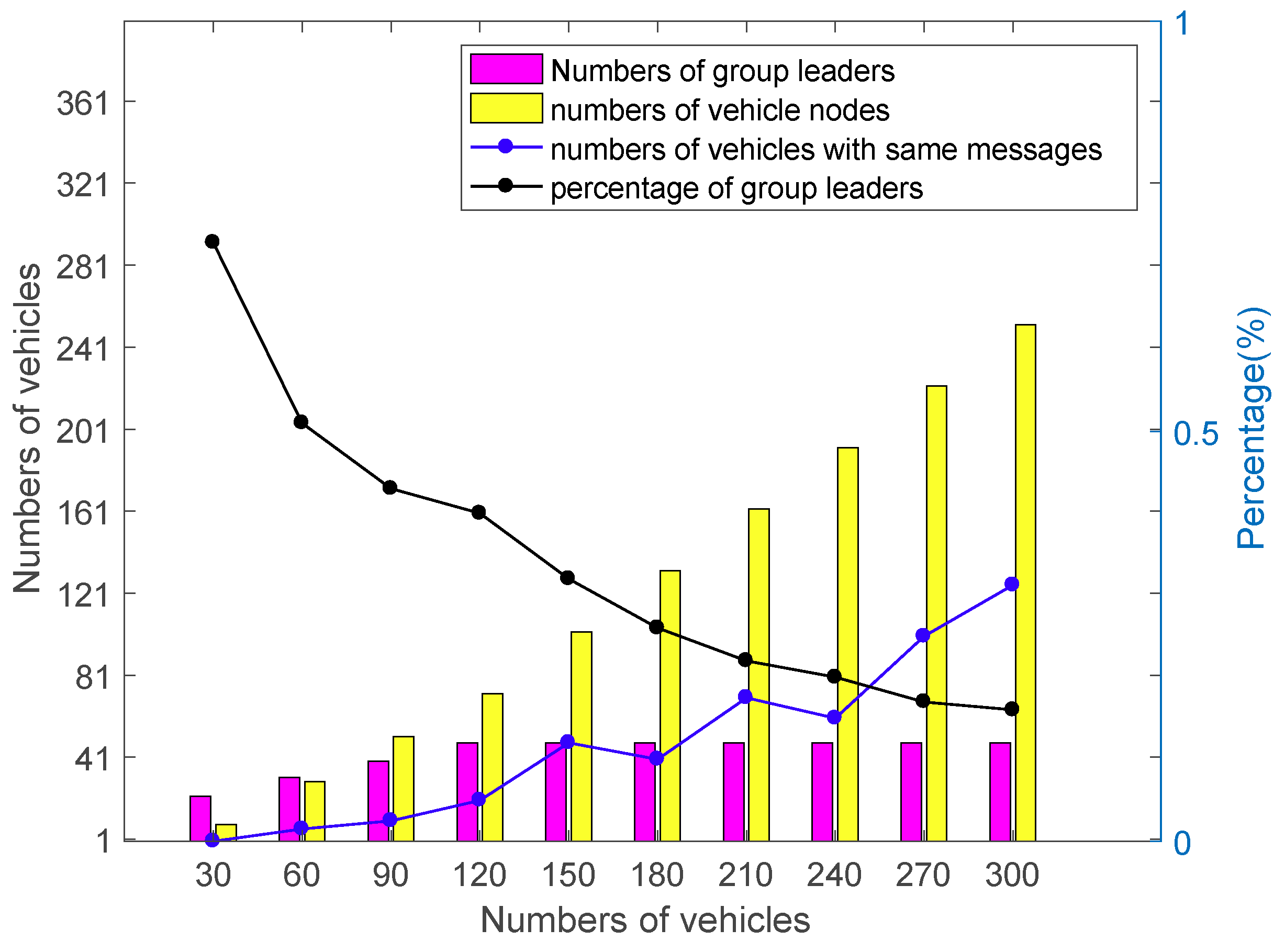
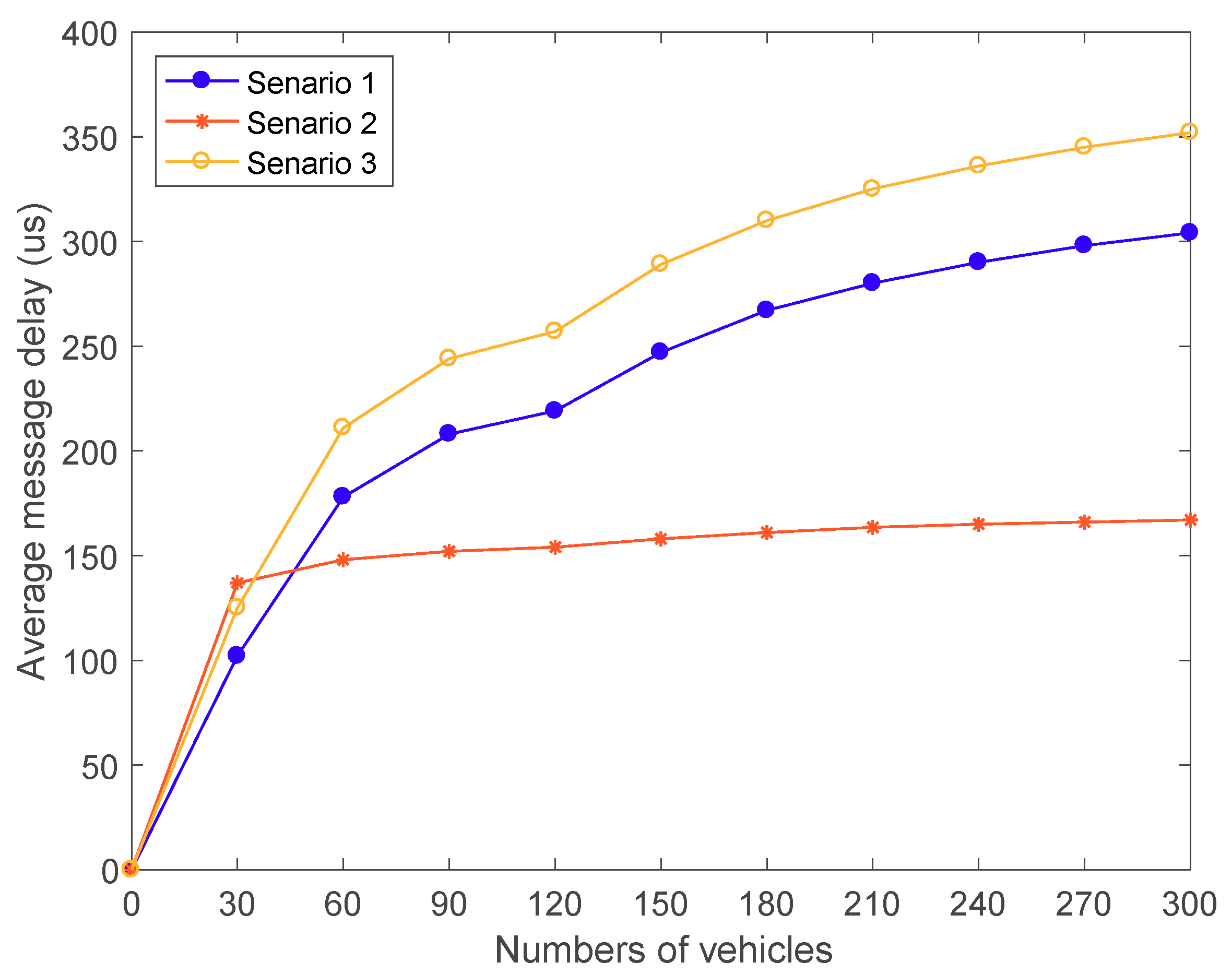
7. Simulation
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Yu, R.; Zhang, Y.; Gjessing, S.; Xia, W. Toward cloud-based vehicular networks with efficient resource management. IEEE Netw. 2013, 27, 48–55. [Google Scholar] [CrossRef]
- Kong, Q.; Lu, R.; Zhu, H.; Alamer, A.; Lin, X. A Secure and Privacy-Preserving Incentive Framework for Vehicular Cloud on the Road. In Proceedings of the Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Ahmed, Z.E.; Saeed, R.A.; Mukherjee, A. Challenges and Opportunities in Vehicular Cloud Computing. In Vehicular Cloud Computing for Traffic Management and System; Grover, J., Vinod, P., Eds.; IGI Global: Hershey, PA, USA, 2018; pp. 57–74. ISBN 13 9781522539810. [Google Scholar]
- Olariu, S.; Eltoweissy, M.; Younis, M. Towards autonomous vehicular clouds. EAI Endorsed Trans. Mob. Commun. Appl. 2011, 11, e2. [Google Scholar] [CrossRef]
- Alamer, A.; Deng, Y.; Lin, X. Secure and privacy-preserving task announcement in vehicular cloud. In Proceedings of the International Conference on Wireless Communications and Signal Processing, Nanjing, China, 11–13 October 2017; pp. 1–6. [Google Scholar]
- Lim, K. Secure and Authenticated Message Dissemination in Vehicular ad hoc Networks and an Incentive-Based Architecture for Vehicular Cloud. Ph.D. Thesis, University of Kentucky, Lexington, KY, USA, 2016. [Google Scholar]
- Yan, G.; Wen, D.; Olariu, S.; Weigle, M.C. Security challenges in vehicular cloud computing. IEEE Trans. Intell. Transp. Syst. 2013, 14, 284–294. [Google Scholar] [CrossRef]
- Rajeshwari, P. A Survey on Security challenges in Vehicular cloud computing. Int. J. Sci. Res. Educ. 2016, 4, 4848–4853. [Google Scholar] [CrossRef][Green Version]
- Ahmad, I.; Noor, R.M.; Ali, I.; Qureshi, M.A. The Role of Vehicular Cloud Computing in Road Traffic Management: A Survey. In Proceedings of the International Conference on Future Intelligent Vehicular Technologies, Islamabad, Pakistan, 17–19 October 2017; pp. 123–131. [Google Scholar]
- Sookhak, M.; Gani, A.; Buyya, R. A survey on vehicular cloud computing. J. Netw. Comput. Appl. 2014, 40, 325–344. [Google Scholar]
- Wan, J.; Zhang, D.; Zhao, S.; Yang, L. Context-aware vehicular cyber-physical systems with cloud support: Architecture, challenges, and solutions. Commun. Mag. IEEE 2014, 52, 106–113. [Google Scholar] [CrossRef]
- Chi, W.D.; Ru, L.I.; Fan, P.F. Research on the Checkpoint Server Selection Strategy Based on the Mobile Prediction in Autonomous Vehicular Cloud. In Proceedings of the International Conference on Service Science, Technology and Engineering, Suzhou, China, 14–15 May 2016; pp. 262–267. [Google Scholar]
- Hussain, R.; Son, J.; Eun, H.; Kim, S.; Oh, H. Rethinking Vehicular Communications: Merging VANET with cloud computing. In Proceedings of the IEEE International Conference on Cloud Computing Technology and Science, Bristol, UK, 2–5 December 2013; pp. 606–609. [Google Scholar]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless Public Key Cryptography; Springer: Berlin, Germany, 2003; pp. 452–473. [Google Scholar]
- Diffie, W.; Hellman, M.E. New directions in cryptography. IEEE Trans. Inf. Theor. 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Aloqaily, M.; Kantarci, B.; Mouftah, H.T. A Generalized Framework for Quality of Experience (QoE)-Based Provisioning in a Vehicular Cloud. In Proceedings of the IEEE International Conference on Ubiquitous Wireless Broadband, Montreal, QC, Canada, 4–7 October 2015; pp. 1–5. [Google Scholar]
- Aloqaily, M.; Ridhawi, I.A.; Kantraci, B.; Mouftah, H.T. Vehicle as a resource for continuous service availability in smart cities. In Proceedings of the IEEE the 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications, Montreal, QC, Canada, 8–13 October 2017; pp. 1–6. [Google Scholar]
- Sáchez-García, J.; García-Campos, J.M.; Gutiérrez, D.; Toral, S.; Barrero, F. On-siteDriverID: A Secure Authentication Scheme based on Spanish eID Cards for Vehicular Ad Hoc Networks. Future Gener. Comput. Syst. 2016, 64, 50–60. [Google Scholar] [CrossRef]
- Wang, L.; Liu, G.; Sun, L. A Secure and Privacy-Preserving Navigation Scheme Using Spatial Crowdsourcing in Fog-Based VANETs. Sensors 2017, 17, 668. [Google Scholar] [CrossRef] [PubMed]
- Otoum, S.; Kantarci, B.; Mouftah, H. Adaptively Supervised and Intrusion-Aware Data Aggregation for Wireless Sensor Clusters in Critical Infrastructures. In Proceedings of the IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018. [Google Scholar]
- Lin, X.; Sun, X.; Wang, X.; Zhang, C.; Ho, P.H.; Shen, X. TSVC: Timed efficient and secure vehicular communications with privacy preserving. IEEE Trans. Wirel. Commun. 2008, 7, 4987–4998. [Google Scholar] [CrossRef]
- Cao, X.; Kou, W.; Du, X. A pairing-free identity-based authenticated key agreement protocol with minimal message exchanges. Inf. Sci. 2010, 180, 2895–2903. [Google Scholar] [CrossRef]
- Chim, T.W.; Yiu, S.M.; Hui, L.C.K.; Li, V.O.K. SPECS: Secure and privacy enhancing communications schemes for VANETs. Ad Hoc Netw. 2011, 9, 189–203. [Google Scholar] [CrossRef]
- Horng, S.J.; Tzeng, S.F.; Pan, Y.; Fan, P.; Wang, X.; Li, T.; Khan, M.K. b-SPECS+: Batch verification for secure pseudonymous authentication in VANET. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1860–1875. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W. A privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Syst. J. 2015, 9, 805–815. [Google Scholar] [CrossRef]
- Park, Y.; Sur, C.; Noh, S.W.; Rhee, K.H. Self-Controllable Secure Location Sharing for Trajectory-Based Message Delivery on Cloud-Assisted VANETs. Sensors 2018, 18, 2112. [Google Scholar] [CrossRef] [PubMed]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Lo, N.-W.; Tsai, J.-L. An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks without pairings. IEEE Trans. Intell. Transp. Syst. 2016, 17, 1319–1328. [Google Scholar] [CrossRef]
- Ming, Y.; Shen, X. PCPA: A Practical Certificateless Conditional Privacy Preserving Authentication Scheme for Vehicular Ad Hoc Networks. Sensors 2018, 18, 1573. [Google Scholar] [CrossRef] [PubMed]
- Lim, K.; Manivannan, D. An efficient protocol for authenticated and secure message delivery in vehicular ad hoc networks. Veh. Commun. 2016, 4, 30–37. [Google Scholar] [CrossRef]
- Vijayakumar, P.; Azees, M.; Kannan, A.; Deborah, L.J. Dual Authentication and Key Management Techniques for Secure Data Transmission in Vehicular Ad Hoc Networks. IEEE Trans. Intell. Trans. Syst. 2016, 17, 1015–1028. [Google Scholar] [CrossRef]
- Zheng, X.; Huang, C.T.; Matthews, M. In Chinese remainder theorem based group key management. In Proceedings of the Southeast Regional Conference, Winston-Salem, NC, USA, 23–23 March 2007; pp. 266–271. [Google Scholar]
- Zhou, J.; Ou, Y. Key Tree and Chinese Remainder Theorem Based Group Key Distribution Scheme. J. Chin. Inst. Eng. 2009, 32, 967–974. [Google Scholar] [CrossRef]
- Seo, S.H.; Won, J.; Sultana, S.; Bertino, E. Effective Key Management in Dynamic Wireless Sensor Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 371–383. [Google Scholar]
- Lim, K.; Abumuhfouz, I.M.; Manivannan, D. Secure Incentive-Based Architecture for Vehicular Cloud. In Proceedings of the International Conference Ad-hoc, Mobile, and Wireless Networks (ADHOC-NOW 2015), Athens, Greece, 29 June–1 July 2015; pp. 361–374. [Google Scholar]
- Sahoo, R.R.; Panda, R.; Behera, D.K.; Naskar, M.K. A trust based clustering with Ant Colony Routing in VANET. In Proceedings of the 3rd International Conference on Computing Communication & Networking Technologies, Maui, HI, USA, 30 January–2 February 2012; pp. 1–8. [Google Scholar]
- Tran, T.X.; Hajisami, A.; Pandey, P.; Pompili, D. Collaborative Mobile Edge Computing in 5G Networks: New Paradigms, Scenarios, and Challenges. IEEE Commun. Mag. 2017, 55, 54–61. [Google Scholar] [CrossRef]
- Ridhawi, I.A.; Aloqaily, M.; Kotb, Y.; Ridhawi, Y.A.; Jararweh, Y. A collaborative mobile edge computing and user solution for service composition in 5G systems. Trans. Emerg. Telecommun. Technol. 2018, 1, 3446–3465. [Google Scholar] [CrossRef]
- Ridhawi, I.A.; Samaan, N.; Karmouch, A. Simulator-Assisted Joint Service-Level-Agreement and Vertical-Handover Adaptation for Profit Maximization. In Proceedings of the 12th International Symposium on Applications and the Internet, Izmir, Turkey, 16–20 July 2012; pp. 74–82. [Google Scholar]
- Li, C.; Zhang, X.; Wang, H.; Li, D. An Enhanced Secure Identity-Based Certificateless Public Key Authentication Scheme for Vehicular Sensor Networks. Sensors 2018, 18, 194. [Google Scholar] [CrossRef] [PubMed]
- Ding, C.; Pei, D.; Salomaa, A. Chinese Remainder Theorem. World Sci. 2005, 70, 224. [Google Scholar]
- Otoum, S.; Kantarci, B.; Mouftah, H.T. In Hierarchical trust-based black-hole detection in WSN-based smart grid monitoring. In Proceedings of the IEEE International Conference on Communications, Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
| Keys | Functions |
|---|---|
| The secret key between a vehicle and the PKG |
|
| Group key |
|
| The pairwise key between the GL and the vehicle |
|
| Subgroup key |
|
| Contents | Security level | Keys | |
|---|---|---|---|
| Public traffic information | Real time traffic information, Intelligent decision hint, Localizing events, Emergency warning etc. | Access with all authorized vehicles | Group key, Subgroup key. |
| Private custom information | Parking space, Infotainment, Electronic logging, vService spot detection, Specific route navigation etc. | Encryption Only access with one specified vehicle | Subgroup key, Secret key . |
| Group sharing information | Private change of member status, Updating subgroup keys, Subgroup services etc. | Encryption Access with all members in one subgroup. | Subgroup key, Secret key . |
| Symbol | Descriptions | Symbol | Descriptions |
|---|---|---|---|
| A k-bit prime number | A secret key of a user | ||
| A finite field with elements | The secret key between a vehicle and the PKG | ||
| An Elliptic Curve over a finite field , , | A public key of a user | ||
| An additive group with the order | The pairwise key between the GL and the vehicle | ||
| The order of the group | A subgroup key | ||
| The point generator of the group | A public key of the PKG | ||
| The pseudo identity of a user | A timestamp | ||
| The real identity of a user | Exclusive-OR operation | ||
| A group key | Message concatenation operation | ||
| A private key of the PKG |
| Operation | Execution Time (Microsecond) |
|---|---|
| 2.6 | |
| 4.5 | |
| 2.3 | |
| 5 | |
| 12 | |
| 0.01 |
| Method | Communication Overhead | Result (byte) | ||
|---|---|---|---|---|
| Vijayakumar’s Scheme | 256 + 256 + 1344 + 256 + 32 + 32 = 2176 bits = 272 bytes | 272 | ||
| Lim’s Scheme | One hop | 256 + 256 + 256 + 32 + 32 = 832 bits = 104 bytes | 104 | |
| N hops | 104 + 121n bytes | 104 + 121n | ||
| Yang’s Scheme | 512 + 256 + 512 + 512 + 32 + 512 + 512 = 2848 bits = 356 bytes | 356 | ||
| Our Scheme | Scenario 1 | V2G | 256 + 512 + 512 + 256 + 32 + 256 + 256 + 32 = 2112 bits = 264 bytes | 264 |
| G2C | 256 + 512 + 512 + 256 + 32 + 256 + 32 = 1856 bits = 232 bytes | 232 | ||
| Scenario 2 | V2G | 256 + 512 + 512 + 256 + 32 +256 + 32 + 32 = 1888 bits = 236 bytes | 236 | |
| G2C | 256 + 512 + 512 + 256 + 32 + 512 + 32 = 2112 bits = 264 bytes | 264 | ||
| G2V | 256 + 256 + 32 + 32 + 32 = 608 bits = 76 bytes | 76 | ||
| Scenario 3 | V2G | 256 + 512 + 512 + 256 + 32 + 256 +512 +32 = 2368 bits = 296 bytes | 296 | |
| G2C | 256 + 512 + 512 + 256 + 32 + 512 + 32 = 2112 bits = 264 bytes | 264 | ||
| Parameters | Values |
|---|---|
| Simulation area | |
| Wireless protocol | 802.11 p |
| Channel bit rate | 6 Mbs |
| Numbers of vehicles | (30, 60, 90, 120, 150, 180, 210, 240, 270, 300) |
| Vehicles speed | 30–70km/h |
| Simulation time | 100 s |
| Radio coverage | 250 m |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, C.; Ji, S.; Zhang, X.; Wang, H.; Li, D.; Liu, H. An Effective and Secure Key Management Protocol for Message Delivery in Autonomous Vehicular Clouds. Sensors 2018, 18, 2896. https://doi.org/10.3390/s18092896
Li C, Ji S, Zhang X, Wang H, Li D, Liu H. An Effective and Secure Key Management Protocol for Message Delivery in Autonomous Vehicular Clouds. Sensors. 2018; 18(9):2896. https://doi.org/10.3390/s18092896
Chicago/Turabian StyleLi, Congcong, Shouwen Ji, Xi Zhang, Haiping Wang, Dongfeng Li, and Huiyong Liu. 2018. "An Effective and Secure Key Management Protocol for Message Delivery in Autonomous Vehicular Clouds" Sensors 18, no. 9: 2896. https://doi.org/10.3390/s18092896
APA StyleLi, C., Ji, S., Zhang, X., Wang, H., Li, D., & Liu, H. (2018). An Effective and Secure Key Management Protocol for Message Delivery in Autonomous Vehicular Clouds. Sensors, 18(9), 2896. https://doi.org/10.3390/s18092896





