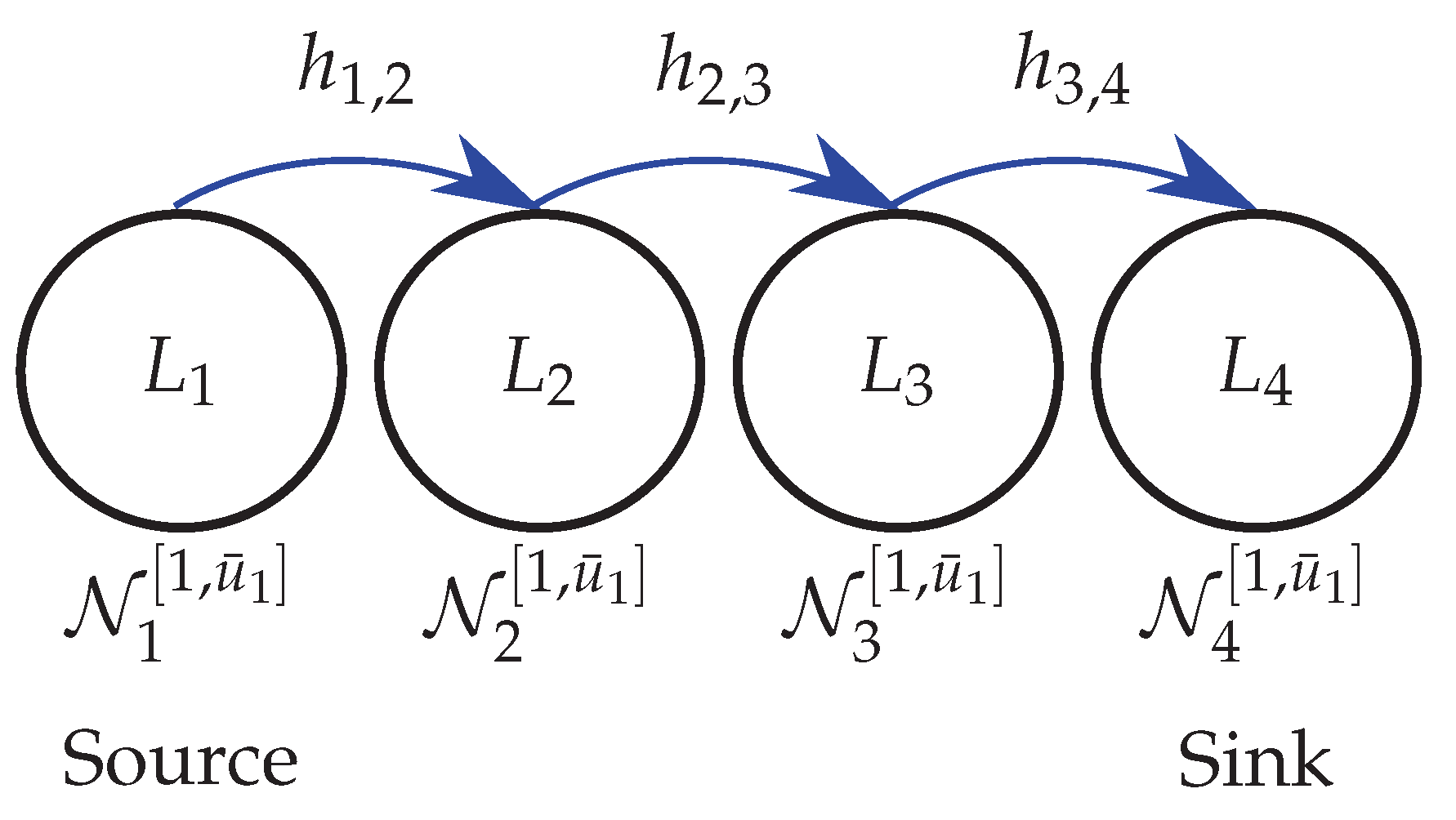
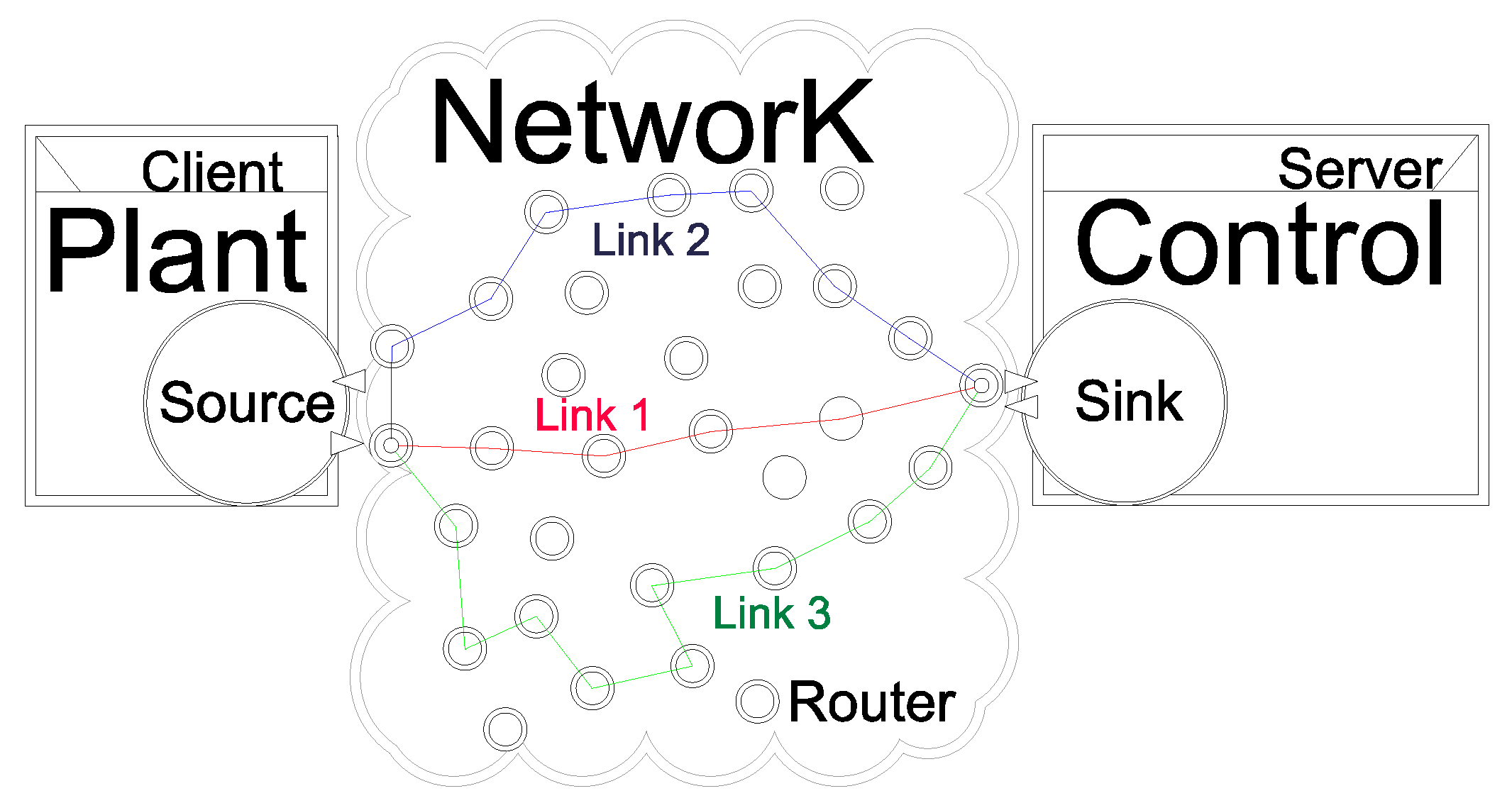
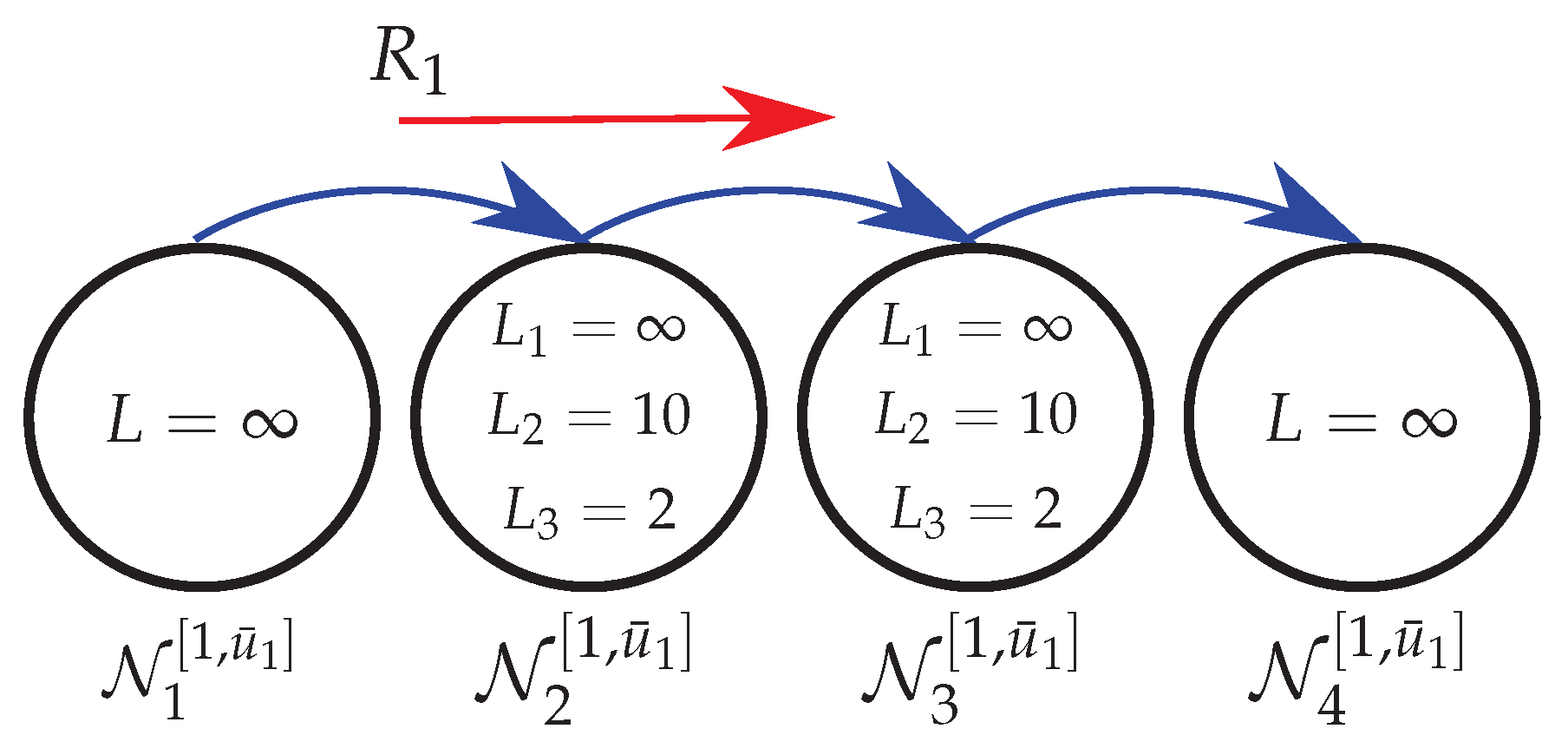
For comparison purposes, it is first designed a dynamic output-feedback controller using the classic control approach (no packet loss,
, that is,
in Equation (
15) for all routes). Applying this assumption in Lemmas 2 and 3 for the design of the controller, an
guaranteed cost of
(computed through Lemma 1 is obtained for the closed-loop system (
13). Additionally, for a full-reliable communication, the mathematical expectation of the global number of transmission
for each route
,
,
and
is, respectively, 36, 24,
and
. The value of
is computed for each route with
,
p and
N given in
Table 4. Consequently, the energy consumed by route (according to Equation (
17)) is, respectively,
J/h,
J/h,
J/h and
J/h, and the global energy consumption is
J/h.
6.3.1. Energy Saving Protocol—Trade-Off Approach—L Unique
In this section, a dynamic output-feedback controller is designed considering the case where
L is fixed
. The maximum value of
L was chosen equal to 30 because the probability of successful transmission between the source and sink (
) for each fragment of
and
tends to 1 for
, which provides the same performance of the classic control design. The minimum value of
L can not be zero, since in this case the system would operate in open-loop (null control signal). Thus, the minimum value of
L was set to
, ensuring a closed-loop operation. Using these assumptions in Lemmas 2 and 3 for the design of the Markovian controller, one has the results depicted in
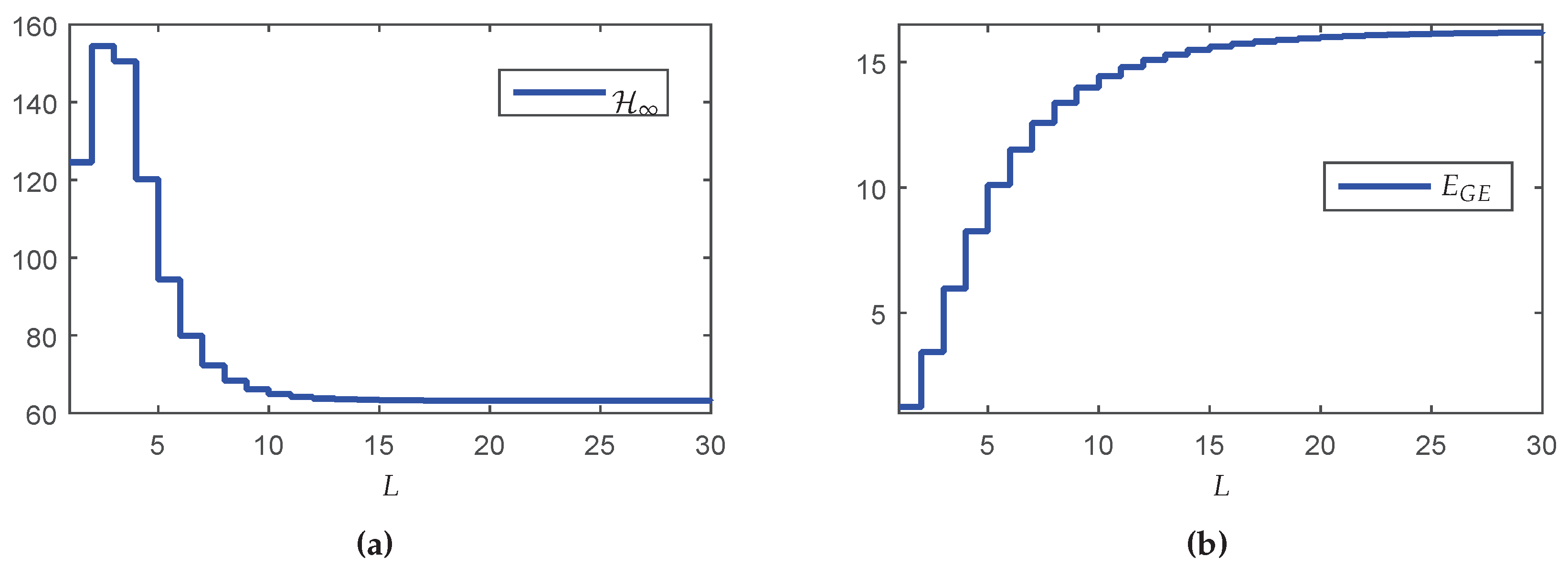
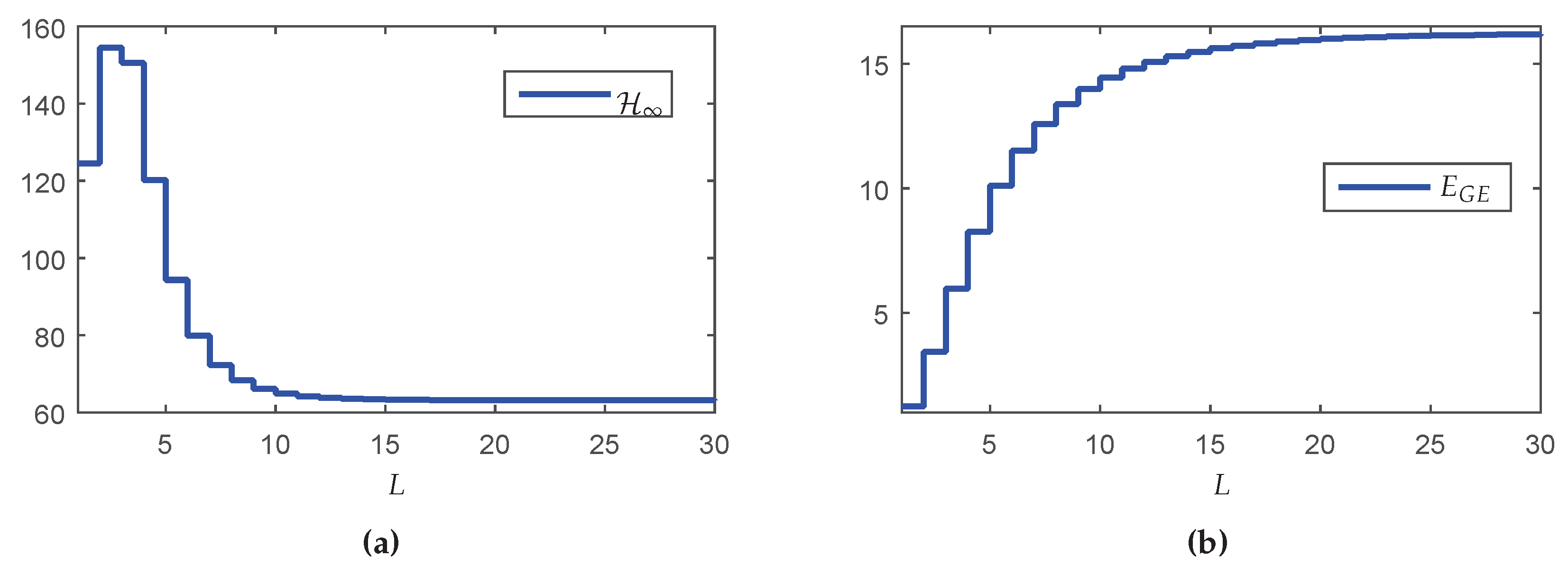
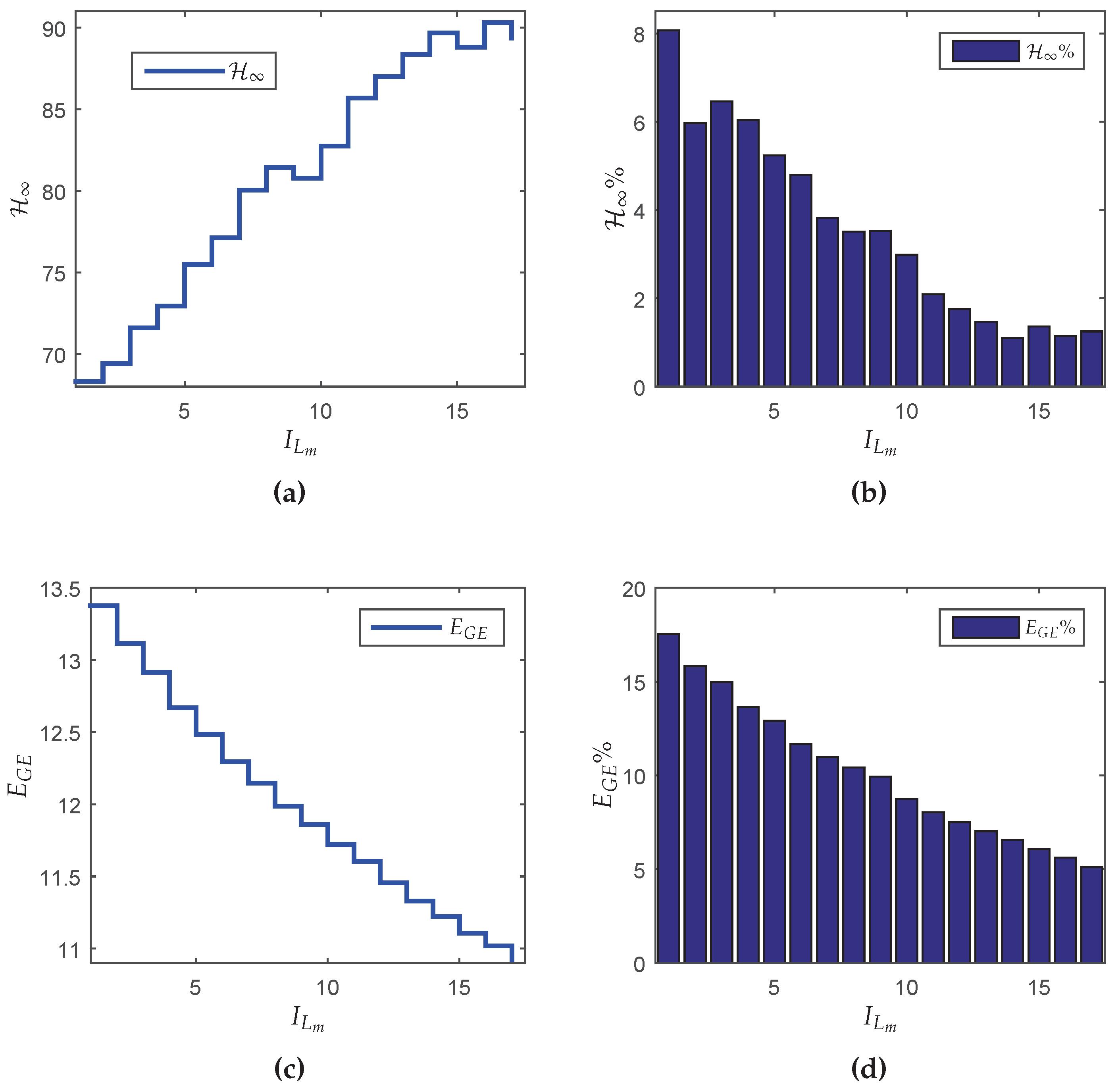
Figure 5a, which shows the
guaranteed costs of the closed-loop system in terms of the maximum number of transmissions
L.
Although counterintuitive, note that the performance in terms of the
norm for
is better than the result for
. A possible reason is that the synthesis of the controller was made in two steps (observer design + state-feedback control design). Although each step of design provides the optimal result, even for the partially mode-dependent and mode-independent cases, the joint behavior is not necessarily optimal (conservative). On the other hand, the global energy consumption increases monotonically as
L grows (see
Figure 5b), meaning that any reduction of
L implies in resource saving. To evidence how this saving occurs,
Table 5 shows some performance measurements variables (defined in
Section 5.1). Besides the performance indexes
,
,
,
and
norm, it is also presented
and
, representing the criteria computed in the node with highest consumption (
). In this example, the first node (without considering the Source and sink) was the worst one.
Observe that when , the increment in the norm in comparison with the classical case is , however, the increment in the energy saving is about twice bigger: . On the other hand, for it is possible to obtain a more expressive energy saving: , nevertheless the norm is greater than the classical case. Although provides greater energy savings, the trade-off relationship between the norm and energy savings is negative. Even so, this choice can be attractive depending on the criterion adopted by the designer.
Knowing that the node with highest energy consumption is the node closest to the source belonging to the route with the lowest probability per hop (
), one has that the critical node is
. Another information obtained from
Table 5 is that the variation in the global energy consumption (
) in function of
L does not present a linear relationship with the variation in the energy consumption of the critical node (
).
6.3.2. Energy Saving Protoco—Second Method: L Variable
In the first method, the value of
L is fixed and the resulting performance, for instance the robustness against exogenous inputs, is always worse than the one provided by the classic case. In the second method, the value (per node) of
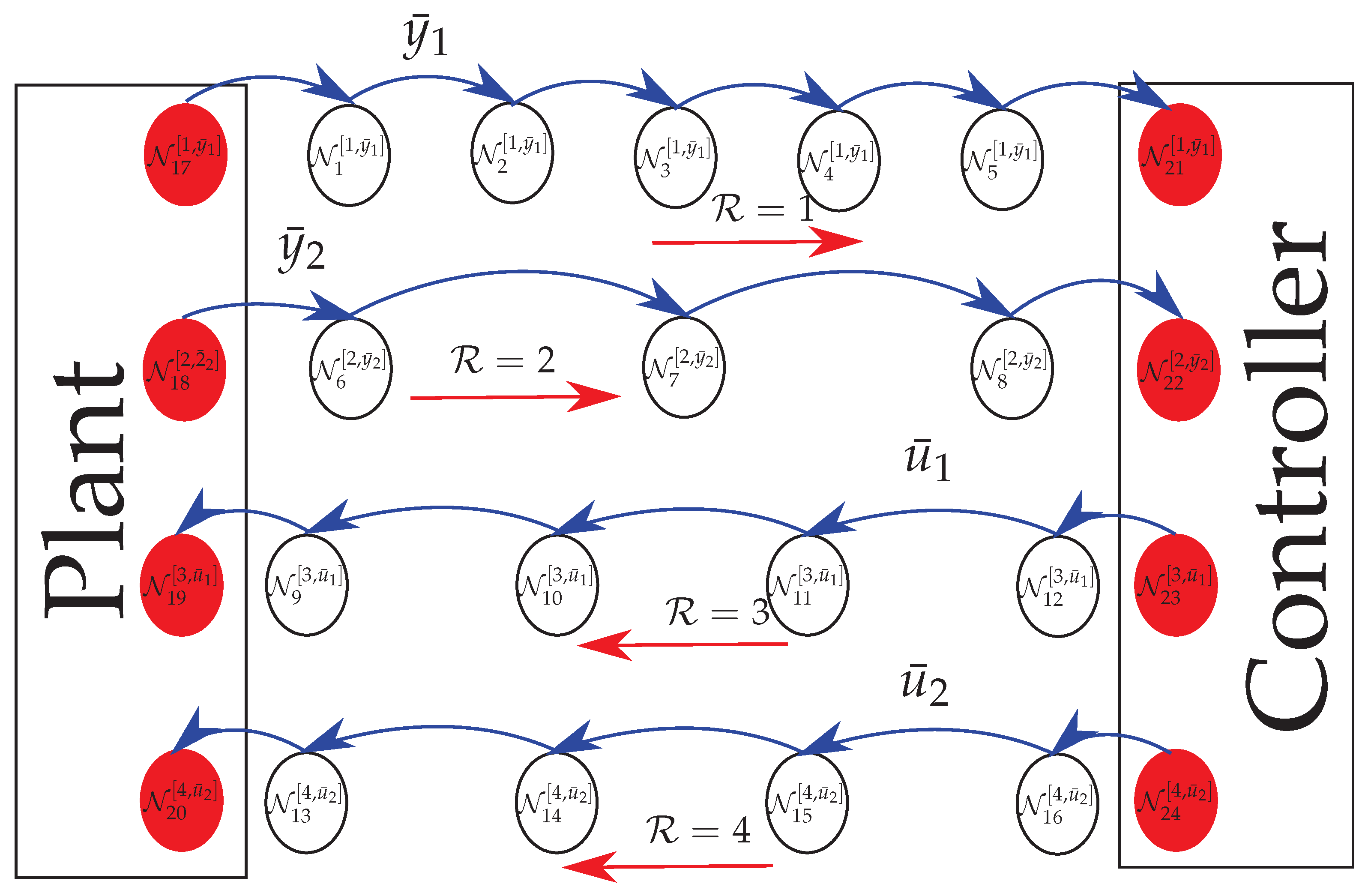
depends exclusively on the battery energy levels, which are time-varying. In the network presented in
Figure 4, the nodes that change their maximum number of transmissions
L over time are
, while nodes
always operate in
because they (nodes connected to the sensors and actuators) are assumed to have unlimited energy. The proposed method starts with a full-reliable communication (
), providing the best performance in terms of
norm. The vector
starts with a norm value of
and an global energy consumption for the entire network equal to
J and gradually declines to the value of
for all nodes with a performance of
and a energy consumption
J/h.
Table 6 exhibits the probabilities of successful transmission between the source and sink (Pr
, Pr
, Pr
, and Pr
) associated with each measurement or control input signal (
,
,
, and
) for each new setting of the network. More precisely,
Table 6 shows the sequence where the nodes change from
to
, such that column
U indicates the node that is changing in the current time interval and column
indicates the order of each setting in terms of
.
By imposing a one-way exchange sequence (from to and never the opposite), the network under investigation can operate only in distinct settings, such that the change in the value of L is made via an alarm signal sent to the controller. Observe that the exchange sequence by node is supposedly done according to the battery consumption of each node (The selection of the switching sequence is merely illustrative. To determine an optimized switching sequence for a real network is outside the scope of investigation of the present work).
Figure 6a shows the
guaranteed costs of the closed-loop system computed for each transition probability matrix
associated to a new network setting
respecting the exchange order indicated by
in
Table 6. Note that the guaranteed costs do not increase monotonically. As explained before, the reason for this fact is that the design conditions are not optimal, that is, the performance index is not directly associated with the increase of the probabilities.
Figure 6b shows the values of the mathematical expectation of the global number of transmissions
by route computed according with Lemma 4. Since the greater the number of transmissions, the greater the energy consumption, observe that the route associated with the highest resource consumption is
, that also contains the critical network node. Finally,
Figure 6c exhibits the energy consumption
for each exchange interval
, that is monotonic decreasing, meaning that the greater the number of devices operating in the resource savings working mode (finite
L), the greater are the savings in the global energy consumption of the network.
As conclusion, note that the main advantage of this method is that, at first, the performance is optimized (minimum in terms of norm, that is equivalent to the classical case since ) and over time, although the performance is deteriorated, the energy saving is gradually increased, augmenting the equipment life span.
6.3.3. Energy Saving Protoco—Third Method: Mixed Problem
Although associated with the optimal performance in terms of the
norm, the implementation of a full-reliable communication is unfavorable with respect the energy consumption. Depending on the network and the dynamic system to be controlled, to allow a small packet loss percentage may provide a significant decrease in the use of network resources and a proportionally smaller decrease in the performance. A similar problem was discussed in [
6,
7,
8,
13], concerning filtering design through semi-reliable networks. The main goal in those works is to keep a positive trade-off between the norm degradation and the energy savings, denoted by
and defined in
Section 5.1 of this paper. To employ the mixed energy saving protocol approach, first it is necessary to determine the initial finite value of
L. By setting the maximum number of transmissions of all the network nodes to the same fixed and finite value of
L, it is possible to compute the resulting value of
(based on the results of
Section 6.3.1, see
Figure 7). Since the mixed approach does not include the case
and aiming to use values associated with positive trade-off, two distinct finite values of
L were chosen:
and
, that is
. The initial value was chosen
since it results in the maximum trade-off
, and the energy savings work mode was fixed in
to allow a better comparison with the second approach, where the finite maximum number of transmissions was also 5. To compute the number of distinct network settings (in this case, the same as the previous method:
, as shown in
Table 7), first it is necessary to identify which nodes change the maximum number of transmissions
L over time (
), and which nodes always operate in fixed
(
) because they are connected to the sensors and actuators with unlimited energy.
Figure 8 shows the results of the third method in terms of the
performance and the global energy consumption
, and also a comparison with the results obtained by the second approach. Observe, for instance, that for
, all the nodes of the network are using
, corresponding to the performance presented in
Table 5 for column
. Similarly to the second method,
Figure 8a shows that the
norm does not increase monotonically.
Figure 8b illustrates the percentage augmentation of the
norm for each network setting when compared with the value obtained by the second method:
where
and
respectively represent the
norm of the closed-loop system computed by the second approach (energy by node approach) and the third approach (mixed approach) for each network setting indexed by
.
On the other hand,
Figure 8c shows that the global energy consumption
decreases monotonically with the augmentation of the number of devices operating in the energy saving work mode. Analogously to what was done for the
norm,
Figure 8b illustrates the percentage augmentation of
for each network setting when compared with the value obtained by the second method:
where
and
respectively represent the global energy consumption associated with the second approach (energy by node approach) and with the third approach (mixed approach) for each network setting indexed by
.
6.3.4. Energy Saving Protocol: Application Guidelines and the Comparison of the Three Approaches
Before comparing the performance and energy consumption provided by the three proposed methods, a summarized sequence of operations that must be performed to apply the proposed energy saving protocol is described, step-by-step, in what follows.
The output-feedback controller is designed considering the classical control theory (full-reliable network, , ) and the optimal value for the norm of the closed-loop system is calculated;
The designer chooses a maximum value for the norm degradation (when compared with the optimum norm computed in step 1: ), which may be considered acceptable within the project specifications;
Consider the implementation of the first and most simple heuristic procedure of energy saving protocol: Trade-off approach (
L fixed and unique), named
in this section. Choose a maximum number of allowed transmissions (
L) and determine the associated transition probability matrix to finally compute the controllers and the
closed-loop norm (using Lemmas 2 and 3) and the network global energy consumption (
from Equation (
23));
If the norm degradation (rate between the norm obtained with packet loss and the one using the classical approach, without loss, ) satisfies the performance required by the designer, it is possible to reduce the value of L, implying a more accentuated reduction in the energy consumption. Otherwise, a value of L greater than the previous one must be chosen (increasing the network reliability and consequently the probability of successful transmissions) to satisfy the maximum norm degradation determined by the designer in step 2;
Assuming the new value of L set in step 4, the third and fourth steps are repeated such that the maximum number of allowed transmissions converge to a minimum value () that simultaneously respects the norm degradation criterion and maximizes the energy savings (best trade-off achieved).
Considering the implementation of the second heuristic method of energy saving protocol (
L variable from
∞ to a fixed and finite value), named
in this section, it is known, from the results obtained for
(steps 1 to 5), the minimum value of
L common to all network nodes which does not violate the criterion of norm degradation imposed by the designer. Also knowing that in the second heuristic (
), each network node assumes
a priori the value
and then the maximum number of allowed transmissions converges to
(except the nodes connected to the sensors or actuators, red circles in
Figure 4), it is enough to compute all the different combinations of network settings (
Table 6), and the corresponding transition probability matrices, stabilizing controllers,
closed-loop norm (
Figure 6a), norm degradation
, and network global energy consumption (
Figure 6c). Observe that
can be less efficient in terms of energy consumption than
because the network nodes operate, during a certain time-window, in full-reliable working mode. However, it is more efficient in terms of
performance because the network nodes operate, during a certain time-window, close to the optimal solution.
Finally, for the implementation of the third heuristic method of energy saving protocol (
L variable inside a set of values fixed and finite), named
in this section, besides determining a maximum value for the
norm degradation (as done for
and
), the designer must also set the maximum global energy consumption by choosing an upper bound for the maximum number of allowed transmissions for each node (
). This value of
L can be chosen based on the results of energy consumption obtained for
, since the network starts its operation in a certain configuration with a finite and fixed value of
L common to all nodes, such that it does not violate the norm degradation criterion imposed by the designer, and also allows an acceptable
performance. Similarly to
, knowing that each node assumes
a priori the value
and then converges to
(except the nodes connected to the sensors or actuators, red circles in
Figure 4, that remain fixed in
), it is sufficient to compute all the different combinations of network settings (
Table 7), and the corresponding transition probability matrices, stabilizing controllers,
closed-loop norm (
Figure 8a), norm degradation
, and network global energy consumption (
Figure 8c).
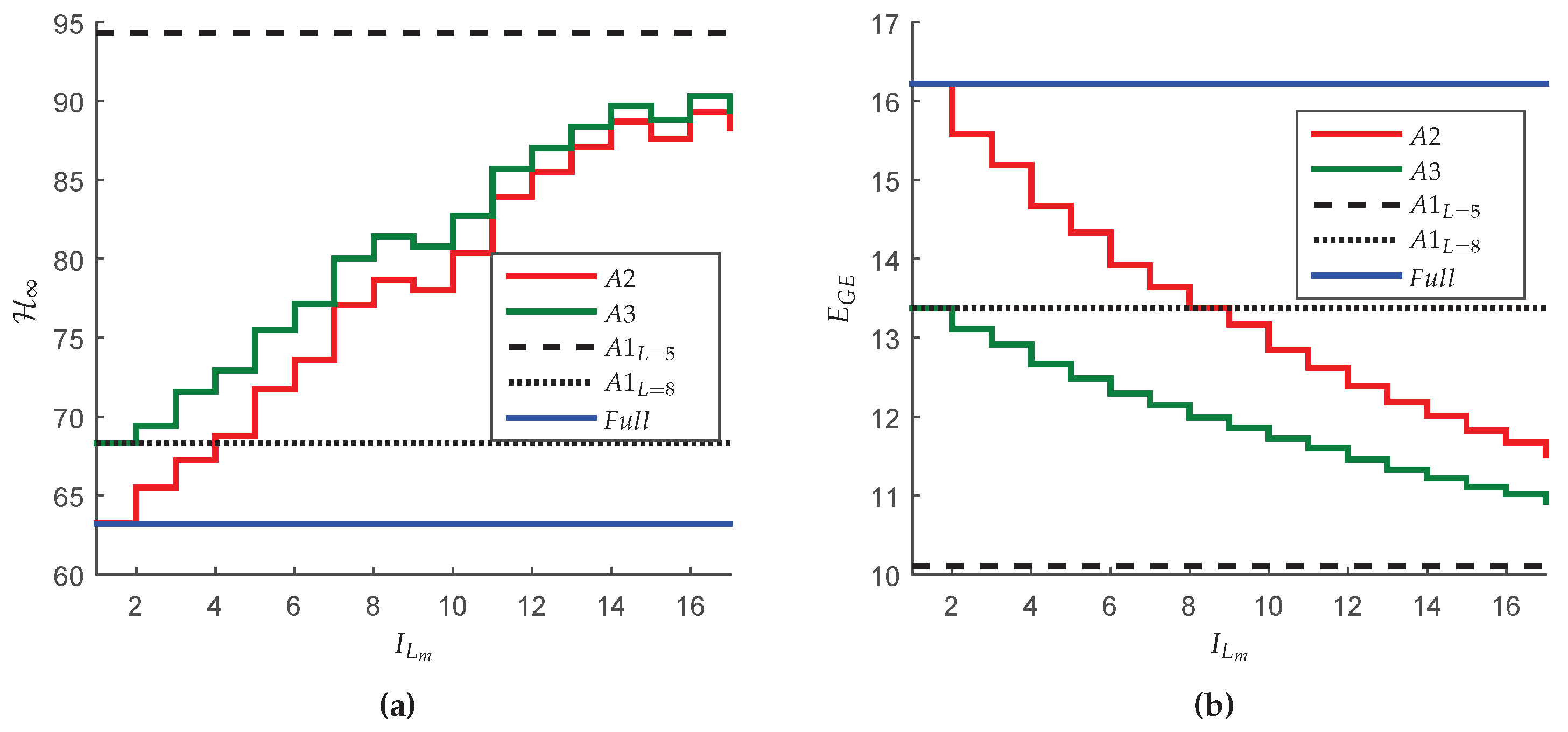
Aiming to compare both performance and energy consumption of all three approaches and their advantages with respect to the classical approach (that assumes the unrealistic hypothesis of a full-reliable network), the
closed-loop norm and the value of
obtained with each one of the methods are presented in
Figure 9. Observe in
Figure 9a that, as expected, the
norm associated with the classical approach is the optimal one and, therefore, an lower bound for the second approach (
with
), since the starting setting of the network imposes
for all nodes. Also note that, the
performance obtained for the first method (
) with
is a lower bound for the third approach (
with
), since, in this case, all the network nodes are set in
in the starting setting. Furthermore, the
results for
with
are always superior than those obtained with any other method, because, even for
with
and
with
, the nodes connected to sensors and actuators are assumed operating with unlimited energy (
for
and
for
). The same explanation can be used to justify why the
closed-loop norm provided by
is always better than the values provided by
even if all the intermediate nodes converge to
. On the other hand, it is noteworthy to mention that the features that can classify a given method as unfavorable in terms of
performance are the same that allow greater energy savings (see
Figure 9b). Note, for instance, that
tends to save less energy than
with
(because the network nodes operate, for a certain time-window, in a more reliable working mode:
) but it consumes less energy than
(because no network node operates in full-reliable working mode when using
).
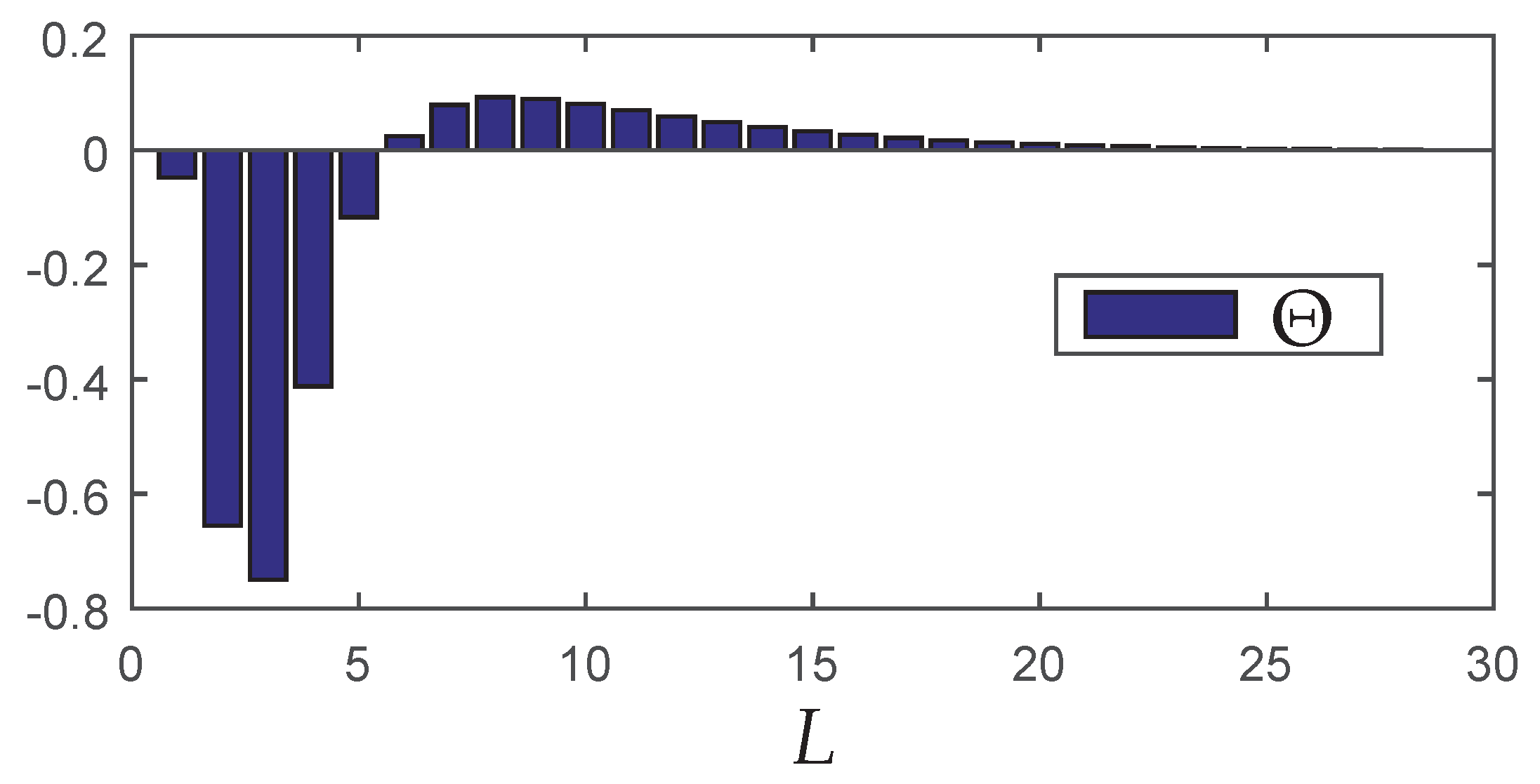
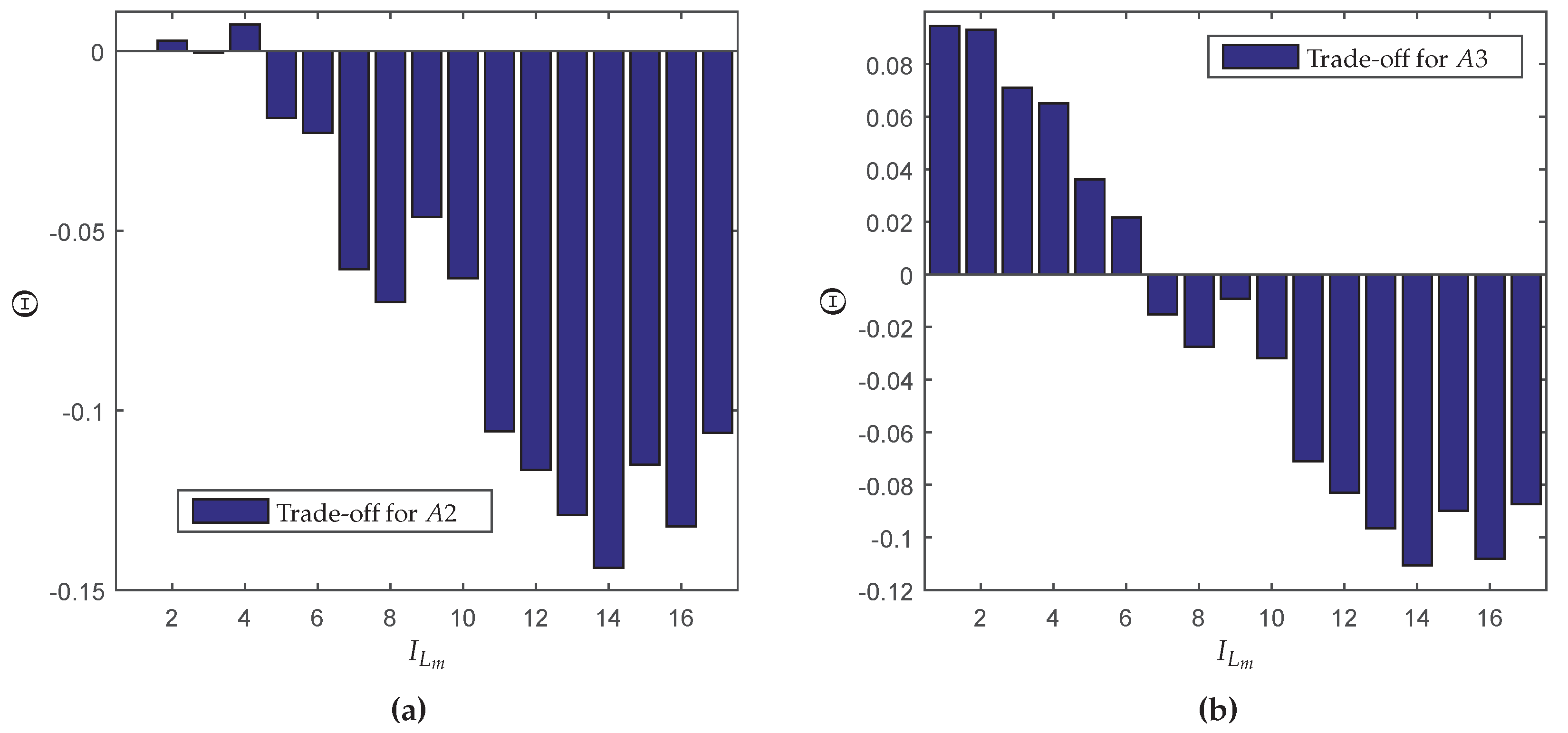
To evaluate how much better is
with
than
with
or
with
, the trade-off index (
) is presented in
Figure 10 for each distinct network setting indexed by
. First, note that by employing
with
, the trade-off is negative (see
Figure 7). By employing
, there are only two network settings that present a positive trade-off, since, in a large time-window, several nodes are maintained in full-reliable working mode. On the other hand, when using
, there are six network settings that present a positive trade-off and even when negative, the trade-off associated to
is better than the other methods.
In short, note that the third approach always produces better results in terms of energy savings than the second method, which starts from the setting similar to the classical control case. Furthermore, when compared with the first method, the third approach seems to be more flexible, allowing to operate on distinct energy saving working modes, among which there are some with better performance indexes.
 such that , . The matrices of filter (4) designed in the case (state-observer filter) can be synthesized by solving a set of LMI conditions presented in [21] and reproduced in the sequence for convenience.
such that , . The matrices of filter (4) designed in the case (state-observer filter) can be synthesized by solving a set of LMI conditions presented in [21] and reproduced in the sequence for convenience.