Intrusion Detection and Prevention in CoAP Wireless Sensor Networks Using Anomaly Detection
Abstract
:1. Introduction
2. Security and Intrusion Detection in the IoT
2.1. Security in the Context of Internet-Integrated Sensor Networks
2.2. Intrusion Detection Approaches on the Internet
2.3. Intrusion Detection on the IoT
3. Anomaly-Based Intrusion Detection in Internet-Integrated CoAP WSN
3.1. Considered Approach
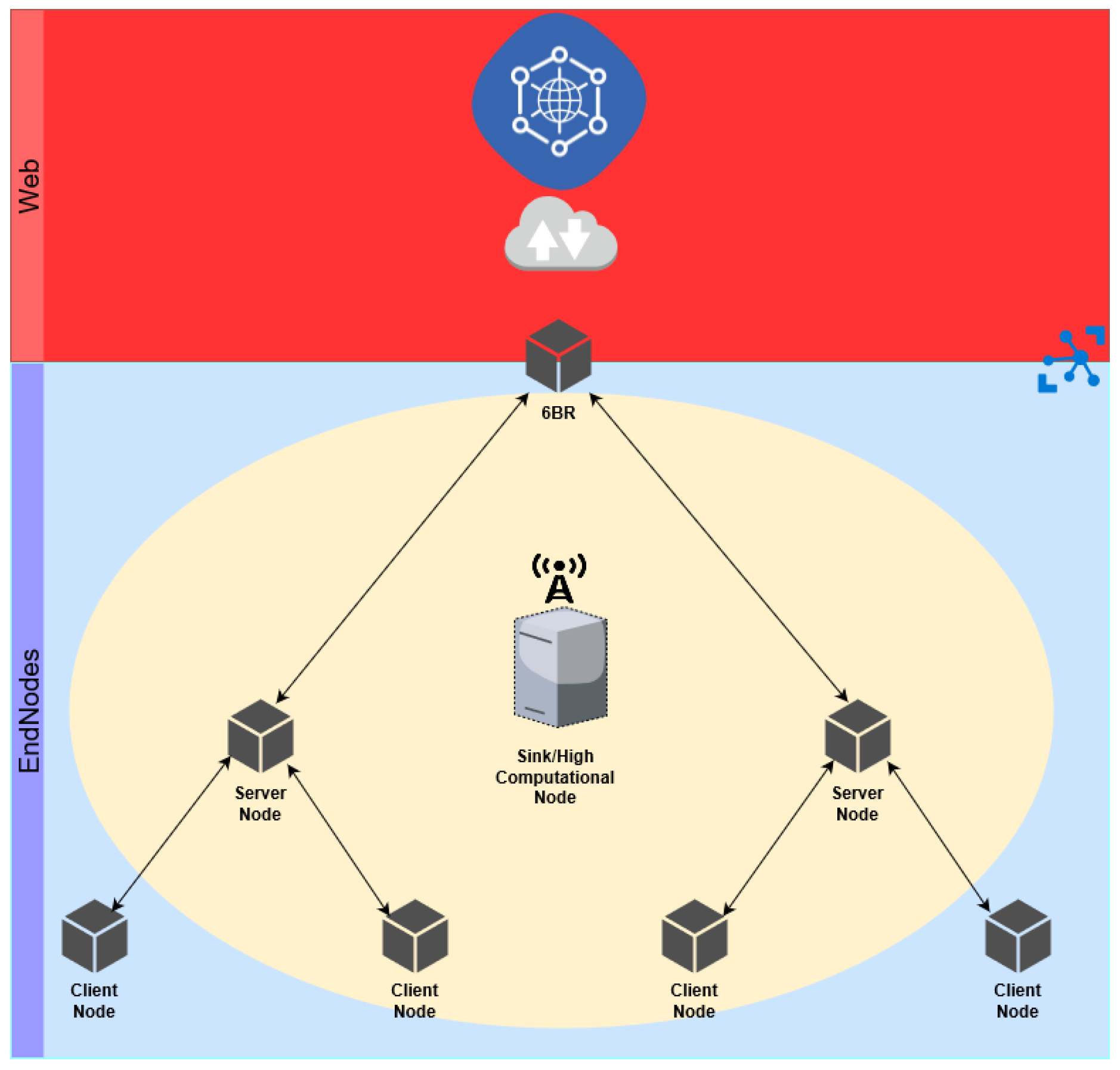
- System network architecture: we adopt a centralized approach, with the goal of detecting attacks subverting the client-server model of CoAP in the range of the system detecting communications.
- Networking type: as is common in sensor network communication environments, a wireless hierarchical model is considered, with IEEE 802.15.4 at the link layer (supporting hop-by-hop communications), and 6LoWPAN, RPL and CoAP at the higher layers.
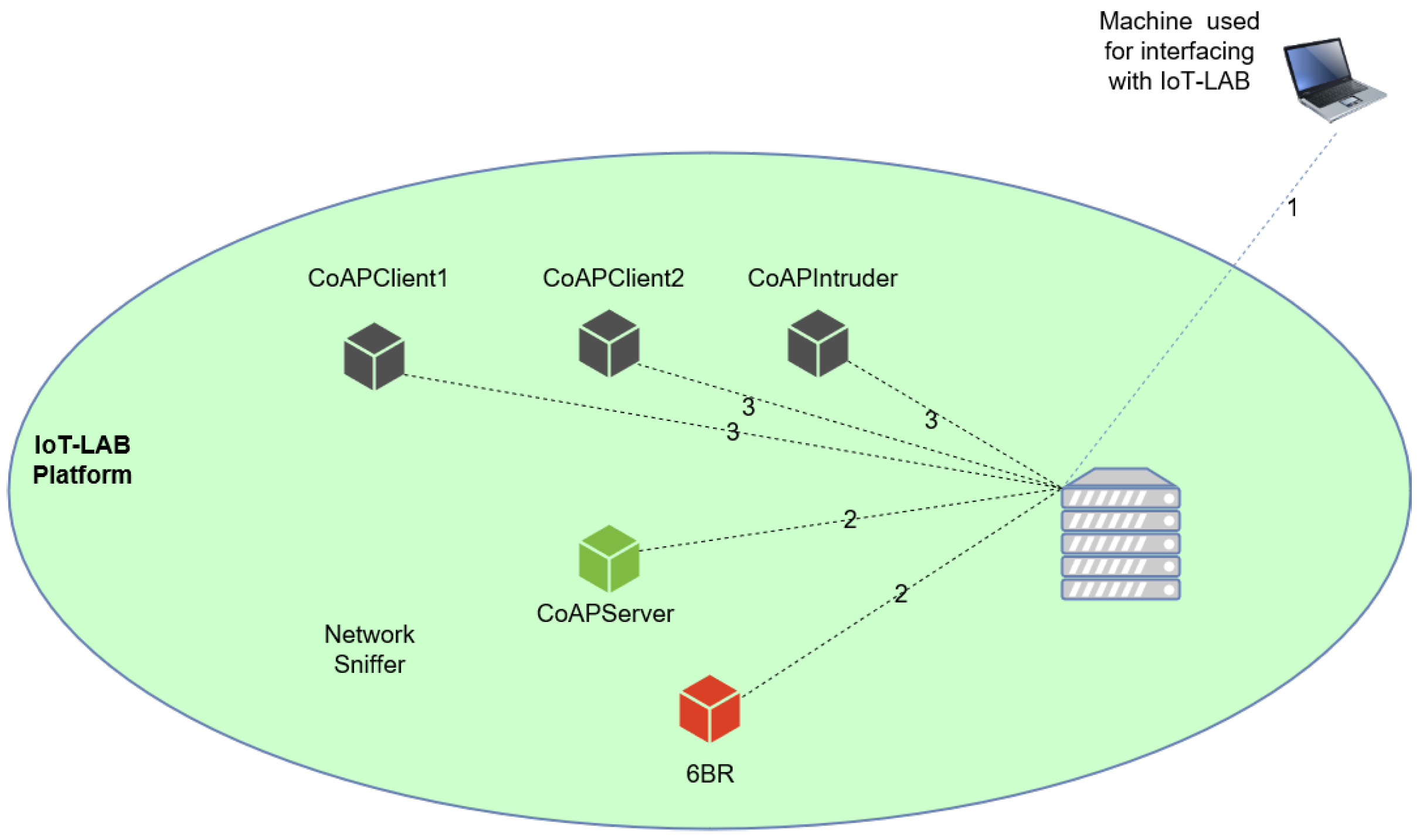
- Collection component: For traffic collection, we use an agent, in particular an IoT-LAB sniffer node capable of capturing the traffic in a specific location of the network.
- Data collection: data collection is centralized, given that the capture of the network traffic is performed in a specific node of the network.
- Data type: We store the captured wireless network traffic in the pcap (Packet Capture) format.
- Time of detection: in our implementation it is currently performed off-line.
- Granularity: in our current implementation we adopt a periodic (batch) approach to traffic capturing.
- Detection discipline: we consider the state-based and stimulating evaluation disciplines, since the IDS reports if a node is in the normal or compromised state. We identify the former as “NORMAL” throughout the article, and the latter as “INTRUSION”.
- Processing strategy: we adopt a centralized approach to processing the gathered data and to detect attacks.
- Detection methodology: as previously discussed, we currently consider, implement and evaluate anomaly-based CoAP intrusion detection in the context of the proposed framework.
3.2. System Architecture
3.3. Misbehavior Detection
- Label 1—Refers to CoAP requests sent to a CoAP server at a rate above a particular threshold, thus traducing an attack which we subsequently designate as “DoS FREQ”;
- Label 2—Refers to CoAP acknowledgements sent to a CoAP server when no corresponding CoAP requests exists, which we subsequently designate as “DoS ACK”;
- Label 3—Refers to requesting resources that are not supported (available) by the CoAP server, which we subsequently designate as “WRONG URI”;
- Label 4—Refers to sending requests to a CoAP server with an invalid ACCEPT option, which we subsequently designate as “WRONG ACCEPT”.
3.4. Learning Methodology
4. Experimental Evaluation
4.1. Implementation and Automation of the Experiments
4.2. Features Considered
4.2.1. Features for Information from IEEE 802.15.4
- —Frame length.
- —Frame counter.
- —Guaranteed Time Slot (GTS) descriptor count.
- —GTS Length.
- —Link Quality Indicator (LQI) correlation value.
- —Frame length.
- —GTS length.
- —Frame counter.
- —Key sequence counter.
4.2.2. Features for Information from 6LoWPAN
- —Datagram size.
- —Message fragment count.
- —Length.
- —Hop limit.
- —Hop limit.
- —Hops left.
- —Header length.
- —Reassembled 6LoWPAN length.
- —Length.
4.2.3. Features for Information from IPv6
- —Flow label.
- —Fragment count.
- —Hop limit.
- —Compartment length.
- —Payload length.
- —Length.
- —Sender rank.
- —Payload length.
- —Reassembled IPv6 length.
- —Length.
- —Element length.
- —Length.
- —Total length.
4.2.4. Features for Information from CoAP
- —Encoded block size.
- —Options length.
- —Options extended length.
- —Max-age.
- —Token length.
- —Status code.
4.3. Evaluation Strategy
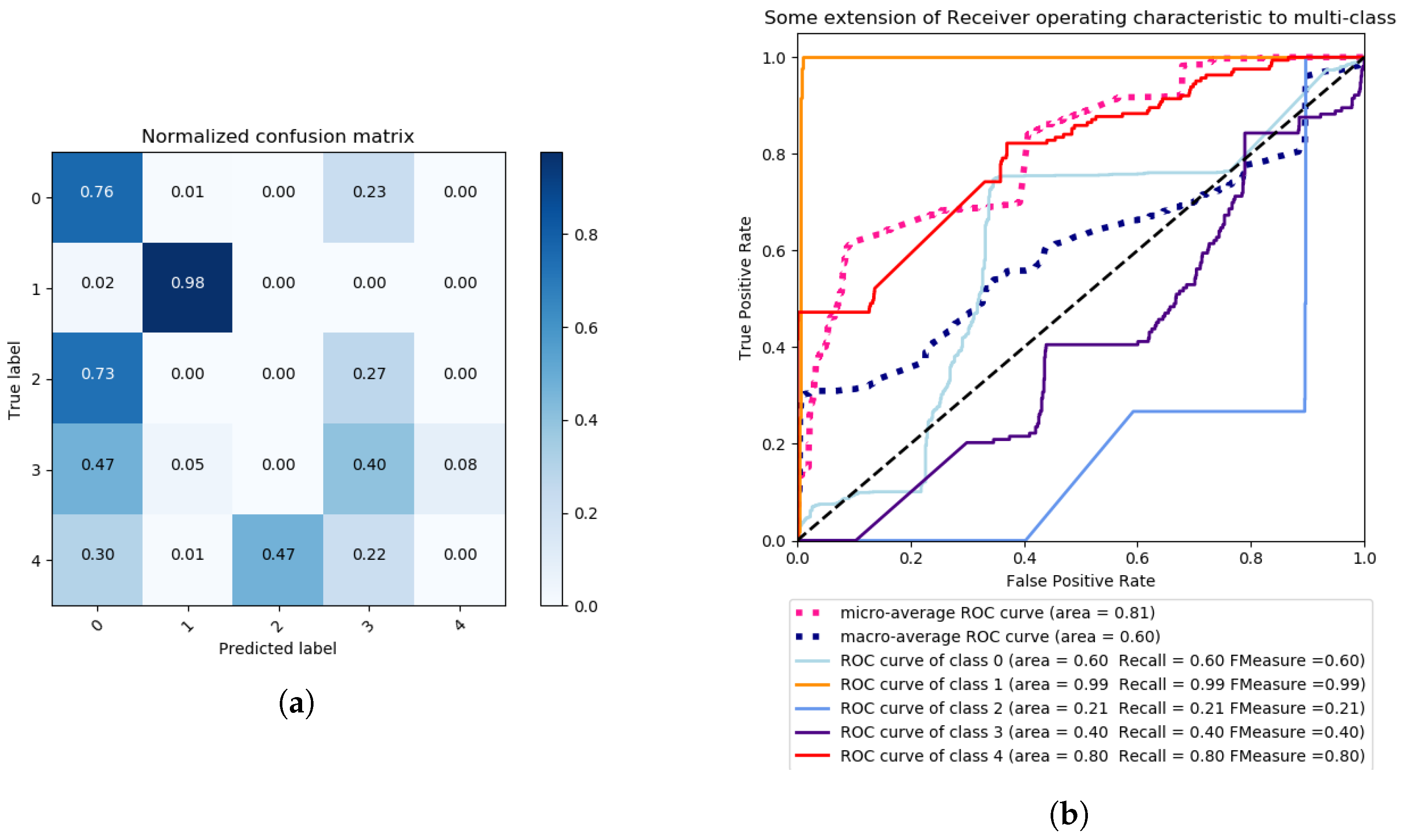
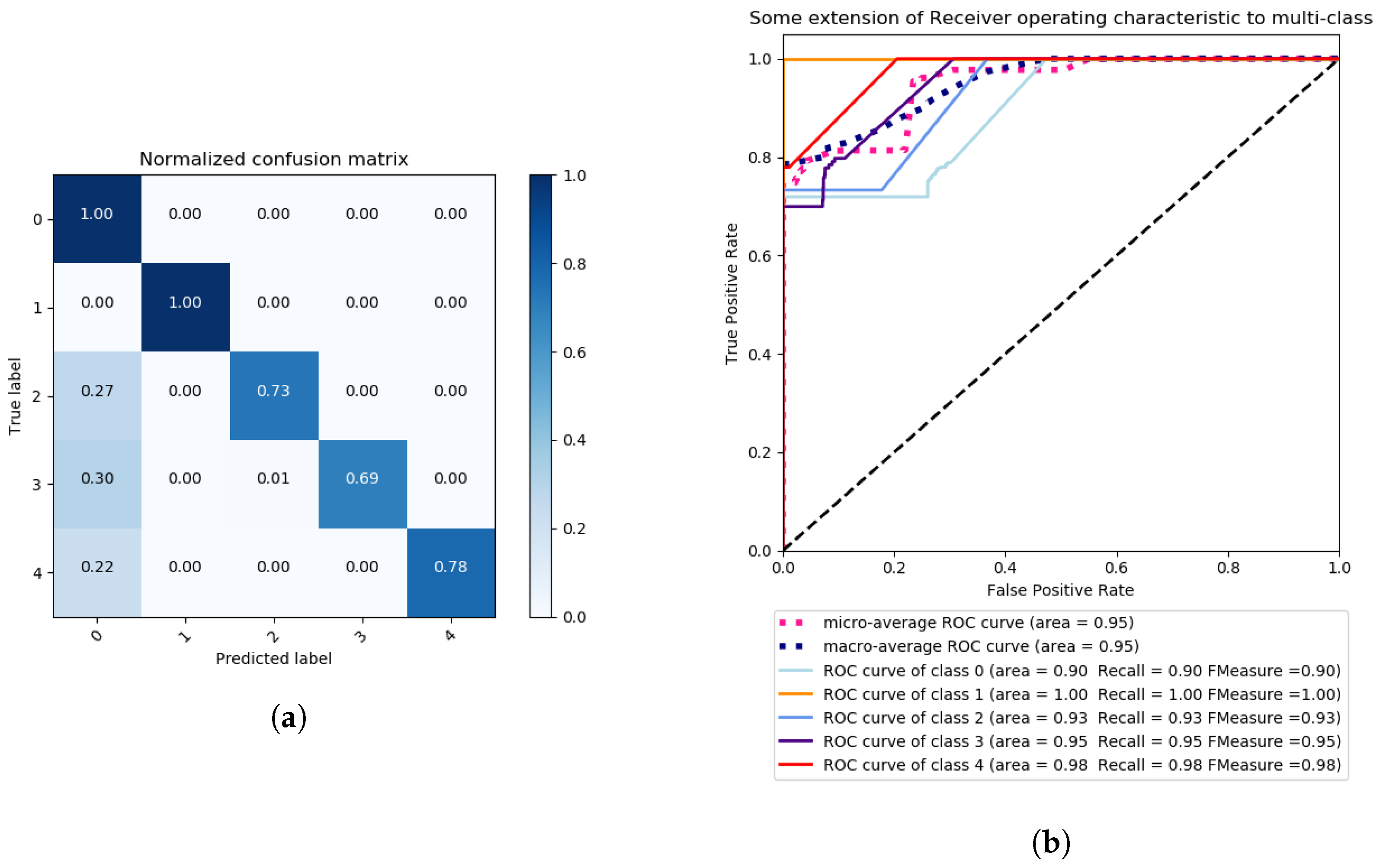
4.4. A Multi-Class Problem Approach
4.5. A Binary Class Problem Approach
5. Conclusions and Future Work
Author Contributions
Conflicts of Interest
References
- Palattella, M.R.; Accettura, N.; Vilajosana, X.; Watteyne, T.; Grieco, L.A.; Boggia, G.; Dohler, M. Standardized protocol stack for the internet of (important) things. IEEE Commun. Surv. Tutor. 2013, 15, 1389–1406. [Google Scholar] [CrossRef]
- Montenegro, G.; Kushalnagar, N.; Hui, J.; Culler, D. Transmission of IPv6 Packets Over IEEE 802.15.4 Networks. Available online: https://tools.ietf.org/html/rfc4944 (accessed on 25 July 2018).
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.P.; Alexander, R. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks. Available online: http://www.rfc-editor.org/info/rfc6550 (accessed on 25 July 2018).
- Bormann, C.; Castellani, A.P.; Shelby, Z. Coap: An application protocol for billions of tiny internet nodes. IEEE Int. Comput. 2012, 16, 62–67. [Google Scholar] [CrossRef]
- Dunkels, A.; Gronvall, B.; Voigt, T. Contiki-a lightweight and flexible operating system for tiny networked sensors. In Proceedings of the 29th Annual IEEE International Conference on Local Computer Networks, Tampa, FL, USA, 16–18 November 2004; pp. 455–462. [Google Scholar]
- FIT IOT-LAB. Iot Experimentation at a Large Scale. Available online: https://www.iot-lab.info/ (accessed on 9 February 2018).
- Howitt, I.; Gutierrez, J.A. IEEE 802.15.4 low rate—wireless personal area network coexistence issues. In Proceedings of the 2003 IEEE Wireless Communications and Networking (WCNC 2003), New Orleans, LA, USA, 16–20 March 2003; Volume 3, pp. 1481–1486. [Google Scholar]
- Nieminen, J.; Savolainen, T.; Isomaki, M.; Patil, B.; Shelby, Z.; Gomez, C. Ipv6 Over Bluetooth(r) Low Energy. Available online: http://www.rfc-editor.org/info/rfc7668 (accessed on 25 July 2018).
- Granjal, J.; Monteiro, E.; Silva, J.S. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Le, A.; Loo, J.; Lasebae, A.; Aiash, M.; Luo, Y. 6LoWPAN: A study on QoS security threats and countermeasures using intrusion detection system approach. Int. J. Commun. Syst. 2012, 25, 1189–1212. [Google Scholar] [CrossRef]
- Shelby, Z.; Hartke, K.; Bormann, C. The Constrained Application Protocol (CoAP). Available online: http://www.rfc-editor.org/info/rfc7252 (accessed on 25 July 2018).
- Liao, H.J.; Lin, C.H.R.; Lin, Y.C.; Tung, K.Y. Intrusion detection system: A comprehensive review. J. Netw. Comput. Appl. 2013, 36, 16–24. [Google Scholar] [CrossRef]
- Can, O.; Sahingoz, O.K. A survey of intrusion detection systems in wireless sensor networks. In Proceedings of the 2015 6th International Conference on Modeling, Simulation, and Applied Optimization (ICMSAO), Istanbul, Turkey, 27–29 May 2015; pp. 1–6. [Google Scholar]
- Aljawarneh, S.; Aldwairi, M.; Yassein, M.B. Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. J. Comput. Sci. 2018, 25, 152–160. [Google Scholar] [CrossRef]
- Gai, K.; Qiu, M.; Tao, L.; Zhu, Y. Intrusion detection techniques for mobile cloud computing in heterogeneous 5G. Secur. Commun. Netw. 2016, 9, 3049–3058. [Google Scholar] [CrossRef]
- Kasinathan, P.; Pastrone, C.; Spirito, M.A.; Vinkovits, M. Denial-of-Service detection in 6LoWPAN based Internet of Things. In Proceedings of the 2013 IEEE 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Lyon, France, 7–9 October 2013; pp. 600–607. [Google Scholar]
- Oliveira, L.M.L.; Rodrigues, J.J.P.C.; de Sousa, A.F.; Lloret, J. Denial of Service Mitigation Approach for IPv6-enabled Smart Object Networks. Concurr. Comput. Pract. Exp. 2013, 25, 129–142. [Google Scholar] [CrossRef]
- Suricata. Home Page. Available online: https://suricata-ids.org/ (accessed on 9 February 2018).
- Raza, S.; Wallgren, L.; Voigt, T. SVELTE: Real-time intrusion detection in the Internet of Things. Ad Hoc Netw. 2013, 11, 2661–2674. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Miorandi, D.; Coen-Porisini, A. REATO: REActing to Denial of Service attacks in the Internet of Things. Comput. Netw. 2018, 137, 37–48. [Google Scholar] [CrossRef]
- Sellami, L.; Idoughi, D.; Baadache, A. Intrusions Detection System Based on Ubiquitous Network Nodes. arXiv, 2014; arXiv:1407.7715. [Google Scholar]
- Roesch, M. Snort: Lightweight intrusion detection for networks. Lisa 1999, 99, 229–238. [Google Scholar]
- Cho, E.J.; Kim, J.H.; Hong, C.S. Attack Model and Detection Scheme for Botnet on 6LoWPAN. Management Enabling the Future Internet for Changing Business and New Computing Services; Hong, C.S., Tonouchi, T., Ma, Y., Chao, C.S., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 515–518. [Google Scholar]
- Gupta, A.; Pandey, O.J.; Shukla, M.; Dadhich, A.; Mathur, S.; Ingle, A. Computational intelligence based intrusion detection systems for wireless communication and pervasive computing networks. In Proceedings of the 2013 IEEE International Conference on Computational Intelligence and Computing Research, Enathi, India, 26–28 December 2013; pp. 1–7. [Google Scholar]
- Pongle, P.; Chavan, G. Real time intrusion and wormhole attack detection in internet of things. Int. J. Comput. Appl. 2015, 121, 9. [Google Scholar] [CrossRef]
- Summerville, D.H.; Zach, K.M.; Chen, Y. Ultra-lightweight deep packet anomaly detection for Internet of Things devices. In Proceedings of the 2015 IEEE 34th International Performance Computing and Communications Conference (IPCCC), Nanjing, China, 14–16 December 2015; pp. 1–8. [Google Scholar]
- Saeed, A.; Ahmadinia, A.; Javed, A.; Larijani, H. Intelligent Intrusion Detection in Low-Power IoTs. ACM Trans. Int. Technol. 2016, 16, 27. [Google Scholar] [CrossRef]
- FIT IOT-LAB. M3 Open Node. Available online: https://www.iot-lab.info/hardware/m3/ (accessed on 16 February 2018).
- Pedregosa, F.; Varoquaux, G.; Gramfort, A.; Michel, V.; Thirion, B.; Grisel, O.; Blondel, M.; Prettenhofer, P.; Weiss, R.; Dubourg, V.; et al. Scikit-learn: Machine learning in Python. J. Mach. Learn. Res. 2011, 12, 2825–2830. [Google Scholar]
- Hunter, J.D. Matplotlib: A 2D graphics environment. Comput. Sci. Eng. 2007, 9, 90–95. [Google Scholar] [CrossRef]





| Scoring Metric: accuracy | |||||||
|---|---|---|---|---|---|---|---|
| C | Kernel | Iterations | Degree (Valid on Polynomial only) | Gamma | Coef0 | Decision Function Shape | Accuracy |
| 0.957895 | ‘linear’ | 30 | 1 | 0.100000 | 0.000000 | ‘ovr’ | 0.212513 |
| 0.957895 | ‘rbf’ | 30 | 1 | 1.000000 | 0.000000 | ‘ovr’ | 0.509824 |
| 0.410526 | ‘poly’ | 30 | 2 | 0.621053 | 0.105263 | ‘ovr’ | 0.283868 |
| 0.200000 | ‘sigmoid’ | 30 | 1 | 0.194736 | 0.947368 | ‘ovr’ | 0.618408 |
| Scoring Metric: accuracy | |||||||
|---|---|---|---|---|---|---|---|
| C | Kernel | Iterations | Degree (valid on Polynomial only) | Gamma | Coef0 | Decision Function Shape | Accuracy |
| 0.452632 | ‘linear’ | 30 | 1 | 0.100000 | 0.000000 | ‘ovr’ | 0.932782 |
| 0.578947 | ‘rbf’ | 30 | 1 | 0.810526 | 0.000000 | ‘ovr’ | 0.632368 |
| 0.200000 | ‘poly’ | 30 | 1 | 0.147368 | 0.000000 | ‘ovr’ | 0.933816 |
| 0.284211 | ‘sigmoid’ | 30 | 1 | 0.100000 | 0.000000 | ‘ovr’ | 0.753361 |
| Scoring Metric: accuracy | |||||||
|---|---|---|---|---|---|---|---|
| C | Kernel | Iterations | Degree (valid on Polynomial only) | Gamma | Coef0 | Decision Function Shape | Accuracy |
| 0.200000 | ‘linear’ | 30 | 1 | 0.100000 | 0.000000 | ‘ovr’ | 0.858325 |
| 0.200000 | ‘rbf’ | 30 | 1 | 0.100000 | 0.000000 | ‘ovr’ | 0.830403 |
| 0.915790 | ‘poly’ | 30 | 3 | 0.621053 | 0.000000 | ‘ovr’ | 0.810238 |
| 0.200000 | ‘sigmoid’ | 30 | 1 | 0.9052632 | 0.315710 | ‘ovr’ | 0.927094 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Granjal, J.; Silva, J.M.; Lourenço, N. Intrusion Detection and Prevention in CoAP Wireless Sensor Networks Using Anomaly Detection. Sensors 2018, 18, 2445. https://doi.org/10.3390/s18082445
Granjal J, Silva JM, Lourenço N. Intrusion Detection and Prevention in CoAP Wireless Sensor Networks Using Anomaly Detection. Sensors. 2018; 18(8):2445. https://doi.org/10.3390/s18082445
Chicago/Turabian StyleGranjal, Jorge, João M. Silva, and Nuno Lourenço. 2018. "Intrusion Detection and Prevention in CoAP Wireless Sensor Networks Using Anomaly Detection" Sensors 18, no. 8: 2445. https://doi.org/10.3390/s18082445
APA StyleGranjal, J., Silva, J. M., & Lourenço, N. (2018). Intrusion Detection and Prevention in CoAP Wireless Sensor Networks Using Anomaly Detection. Sensors, 18(8), 2445. https://doi.org/10.3390/s18082445





