Centralized Duplicate Removal Video Storage System with Privacy Preservation in IoT
Abstract
:1. Introduction
1.1. Related Work
1.2. Our Contribution
- We present a method of secure video deduplication with privacy preservation that enables users to remove the encrypted duplicated data with the help of the server. According to the chunk level, two secure systems are proposed: a file-level deduplication system and block-level deduplication system.
- We adopt symmetric encryption and convergent encryption in file-level and block-level deduplication systems to prevent statistical information leakage.
- We apply the SGX technique in the block-level deduplication system to guarantee privacy security.
2. Preliminaries
2.1. Symmetric Encryption
2.2. Convergent Encryption
2.3. Intel SGX Background
- Isolation: Aims to put the data and program into the enclave; they can not be read or modified by any other external process.
- Sealing: Every SGX processor has a hardware-resident key which is called the Root Seal Key. When an enclave is created, it can derive a key from the Root Seal Key called the Seal Key, and the key is used to encrypt or authenticate data and store it in untrusted memory. Sealed data can be recovered by the same enclave on the same platform even after the enclave has been destroyed. However, the Seal Key cannot derived from different enclaves on the same platform or enclaves on a different platform.
- Attestation: There are two forms of attestation: local and remote. Local attestation is between two enclaves on the same platform. They can derive a shared key for authentication because they share the same Root Seal Key. Remote attestation is to generate a report that can be verified by a remote party.
3. Problem Formulation
3.1. The Entities
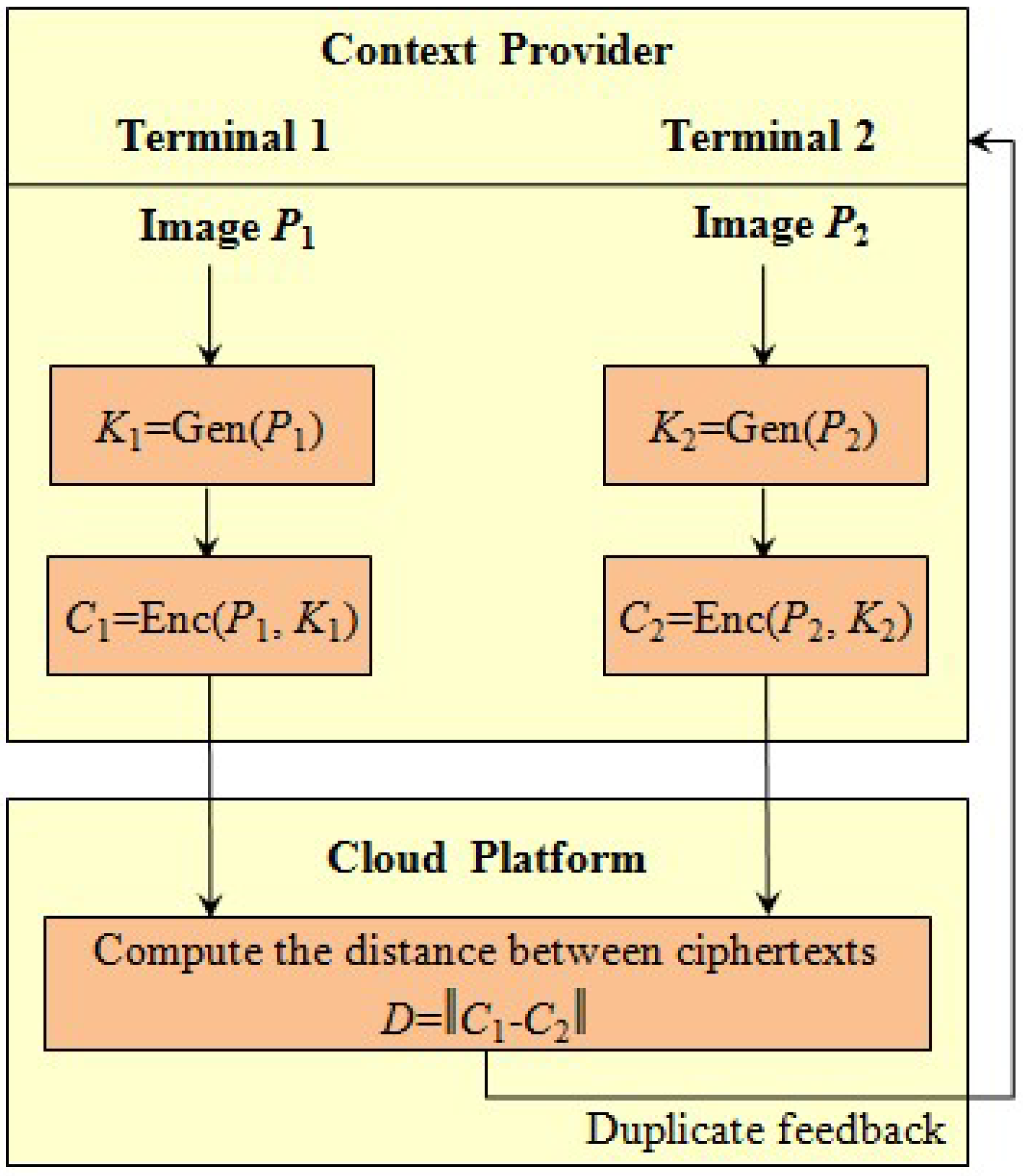
- Context provider: The entities which collect data and transmit them with other end-terminals or the remote server on the Internet host. The common context providers include the sensor node, RFID reader and so on. In most cases, the end terminals in IoT are limited in terms of both storage and computation resources.
- Remote server: The entity which hosts with a large capability of data storage and computational power. The users can store their data on the remote server and exploit its capability to accomplish computational tasks with abundant resources.
- Transmission channel: The entity which is set up to exchange data between the terminals or between the terminal and the remote server. In IoT, the transmission channels are usually public with barely any secure protection, such as the wireless channels.
3.2. System Goals
3.2.1. Deduplication
3.2.2. Privacy Preservation
4. System Implementation
4.1. File-Level Deduplication System with Privacy Preservation
4.2. Block-Level Deduplication System with Privacy Preservation
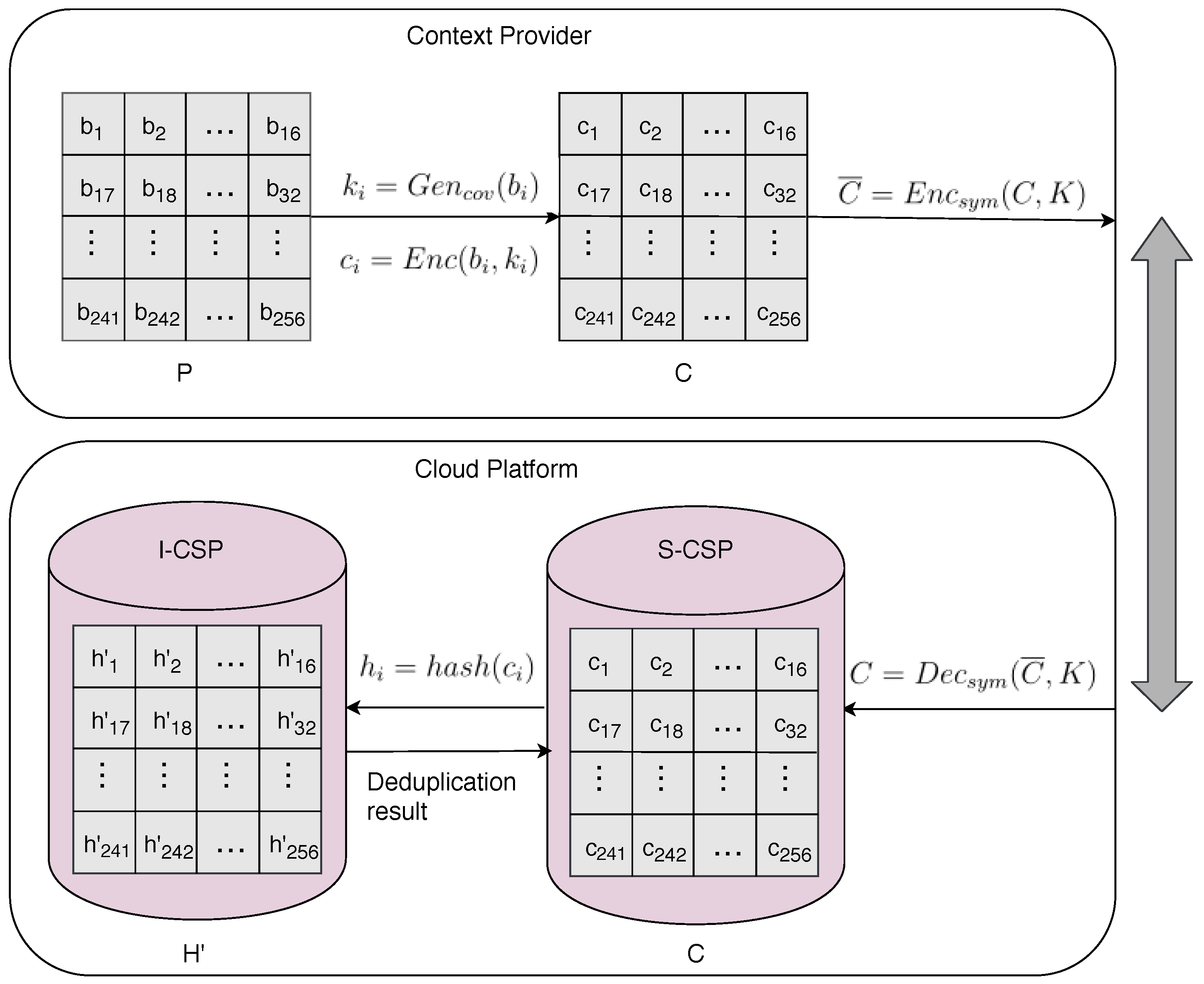
4.2.1. Block-Level Deduplication System Based on Convergent Encryption
4.2.2. Secure Block-Level Deduplication System Using SGX
5. System Evaluation
6. Conclusions
Author Contributions
Acknowledgements
Conflicts of Interest
References
- Shen, J.; Wang, C.; Li, T.; Chen, X.; Huang, X.; Zhan, Z.-H. Secure data uploading scheme for a smart home system. Inf. Sci. 2018, 453, 186–197. [Google Scholar] [CrossRef]
- Shen, J.; Gui, Z.; Ji, S.; Shen, J.; Tan, H.; Tang, Y. Cloud-aided lightweight certificateless authentication protocol with anonymity for wireless body area networks. J. Netw. Comput. Appl. 2018, 106, 117–123. [Google Scholar] [CrossRef]
- Cai, Z.; Yan, H.; Li, P.; Huang, Z.A.; Gao, C. Towards secure and flexible ehr sharing in mobile health cloud under static assumptions. Clust. Comput. 2017, 20, 2415–2422. [Google Scholar] [CrossRef]
- Zhang, Y.; Zheng, D.; Li, Q.; Li, J.; Li, H. Online/offline unbounded multi-authority attribute-based encryption for data sharing in mobile cloud computing. Secur. Commun. Netw. 2016, 9, 3688–3702. [Google Scholar] [CrossRef]
- Shen, J.; Zhou, T.; Chen, X.; Li, J.; Susilo, W. Anonymous and traceable group data sharing in cloud computing. IEEE Trans. Inf. Forensics Secur. 2018, 13, 912–925. [Google Scholar] [CrossRef]
- Li, J.; Chen, X.; Chow, S.S.M.; Huang, Q.; Wong, D.S.; Liu, Z. Multi-authority fine-grained access control with accountability and its application in cloud. J. Netw. Comput. Appl. 2018, 112, 89–96. [Google Scholar] [CrossRef]
- Li, B.; Huang, Y.; Liu, Z.; Li, J.; Tian, Z.; Yiu, S.M. Hybridoram: Practical oblivious cloud storage with constant bandwidth. Inf. Sci. 2018. [Google Scholar] [CrossRef]
- Wang, H.; Zheng, Z.; Wu, L.; Li, P. New directly revocable attribute-based encryption scheme and its application in cloud storage environment. Clust. Comput. 2017, 20, 2385–2392. [Google Scholar] [CrossRef]
- Liu, Z.; Huang, Y.; Li, J.; Cheng, X.; Shen, C. Divoram: Towards a practical oblivious ram with variable block size. Inf. Sci. 2018, 447, 1–11. [Google Scholar] [CrossRef]
- Xu, J.; Wei, L.; Zhang, Y.; Wang, A.; Zhou, F.; Gao, C.Z. Dynamic fully homomorphic encryption-based merkle tree for lightweight streaming authenticated data structures. J. Netw. Comput. Appl. 2018, 107, 113–124. [Google Scholar] [CrossRef]
- Li, T.; Li, J.; Liu, Z.; Li, P.; Jia, C. Differentially private naive bayes learning over multiple data sources. Inf. Sci. 2018, 444, 89–104. [Google Scholar] [CrossRef]
- Jiang, T.; Chen, X.; Li, J.; Wong, D.S.; Ma, J.; Liu, J.K. Towards secure and reliable cloud storage against data re-outsourcing. Future Gen. Comput. Syst. 2015, 52, 86–94. [Google Scholar] [CrossRef]
- Chen, X.; Li, J.; Weng, J.; Ma, J.; Lou, W. Verifiable computation over large database with incremental updates. IEEE Trans. Comput. 2014, 65, 3184–3195. [Google Scholar] [CrossRef]
- Zhang, X.; Tan, Y.A.; Liang, C.; Li, Y.; Li, J. A covert channel over volte via adjusting silence periods. IEEE Access 2018, 4, 1–11. [Google Scholar] [CrossRef]
- Li, C.; Li, L.Y. Optimal scheduling across public and private clouds in complex hybrid cloud environment. Inf. Syst. Front. 2017, 19, 1–12. [Google Scholar]
- Celesti, A.; Mulfari, D.; Fazio, M.; Puliafito, A.; Villari, M. Evaluating alternative daas solutions in private and public openstack clouds. Softw. Pract. Exp. 2017, 47, 1185–1200. [Google Scholar] [CrossRef]
- Miguel, R.; Aung, K.M.M. Hedup: Secure deduplication with homomorphic encryption. In Proceedings of the IEEE International Conference on Networking, Architecture and Storage, Boston, MA, USA, 6–7 August 2015; pp. 215–223. [Google Scholar]
- Lin, Q.; Yan, H.; Huang, Z.; Chen, W.; Shen, J.; Tang, Y. An id-based linearly homomorphic signature scheme and its application in blockchain. IEEE Access 2018, 6, 20632–20640. [Google Scholar] [CrossRef]
- Bolosky, W.J.; Goebel, D.; Goebel, D.; Douceur, J.R. Single instance storage in windows? In Proceedings of the Conference on Usenix Windows Systems Symposium 4, Seattle, WA, USA, 3–4 August 2000. [Google Scholar]
- Quinlan, S.; Dorward, S. Venti: A new approach to archival storage. In Proceedings of the 1st USENIX conference on File and Storage Technologies (FAST 2), Monterey, CA, USA, 28–30 January 2002; pp. 89–101. [Google Scholar]
- Zhu, B.; Li, K.; Patterson, R.H. Avoiding the disk bottleneck in the data domain deduplication file system. In Proceedings of the 1st USENIX conference on File and Storage Technologies (FAST 2008), San Jose, CA, USA, 26–29 February 2008; Volume 8, pp. 1–14. [Google Scholar]
- Liu, J.; Asokan, N.; Pinkas, B. Secure deduplication of encrypted data without additional independent servers. In Proceedings of the ACM Sigsac Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 874–885. [Google Scholar]
- Ng, W.K.; Wen, Y.; Zhu, H. Private data deduplication protocols in cloud storage. In Proceedings of the 27th Annual ACM Symposium on Applied Computing, Trento, Italy, 26–30 March 2012; pp. 441–446. [Google Scholar]
- Bellare, M.; Keelveedhi, S.; Ristenpart, T. Dupless: Server-aided encryption for deduplicated storage. In Proceedings of the Usenix Conference on Security, Washington, DC, USA, 14–16 August 2013; pp. 179–194. [Google Scholar]
- Puzio, P.; Molva, R.; Onen, M.; Loureiro, S. Block-level de-duplication with encrypted data. Open J. Cloud Comput. 2014, 1, 10–18. [Google Scholar]
- Chen, R.; Mu, Y.; Yang, G.; Guo, F. Bl-mle: Block-level message-locked encryption for secure large file deduplication. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2643–2652. [Google Scholar] [CrossRef]
- Litwin, W.; Jajodia, S.; Schwarz, T. Privacy of data outsourced to a cloud for selected readers through client-side encryption. In Proceedings of the ACM Workshop on Privacy in the Electronic Society, Chicago, IL, USA, 17 October 2011; pp. 171–176. [Google Scholar]
- Li, J.; Chen, X.; Li, M.; Li, J.; Lee, P.P.C.; Lou, W. Secure deduplication with efficient and reliable convergent key management. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1615–1625. [Google Scholar] [CrossRef]
- Gonzlez-Manzano, L.; Orfila, A. An efficient confidentiality-preserving proof of ownership for deduplication. J. Netw. Comput. Appl. 2015, 50, 49–59. [Google Scholar] [CrossRef]
- Koo, D.; Hur, J. Privacy-preserving deduplication of encrypted data with dynamic ownership management in fog computing. Future Gen. Comput. Syst. 2017, 78, 739–752. [Google Scholar] [CrossRef]
- Li, X.; Li, J.; Huang, F. A secure cloud storage system supporting privacy-preserving fuzzy deduplication. Soft Comput. 2016, 20, 1437–1448. [Google Scholar] [CrossRef]
- Li, J.; Li, Y.K.; Chen, X.; Lee, P.P.; Lou, W. A hybrid cloud approach for secure authorized deduplication. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 1206–1216. [Google Scholar] [CrossRef]
- Li, J.; Chen, X.; Huang, X.; Tang, S.; Xiang, Y.; Hassan, M.M.; Alelaiwi, A. Secure distributed deduplication systems with improved reliability. IEEE Trans. Comput. 2015, 64, 3569–3579. [Google Scholar] [CrossRef]
- Chen, Q.; Yang, L.; Zhang, D.; Shen, Y.; Huang, S. Face deduplication in video surveillance. Int. J. Pattern Recognit. Artif. Intell. 2017, 32, 1856001. [Google Scholar] [CrossRef]
- Li, Y.; Xia, K. Fast video deduplication via locality sensitive hashing with similarity ranking. In Proceedings of the International Conference on Internet Multimedia Computing and Service, Xi’an, China, 19–21 August 2016; pp. 94–98. [Google Scholar]
- Rashid, F.; Miri, A.; Woungang, I. Proof of storage for video deduplication in the cloud. In Proceedings of the IEEE International Congress on Big Data, New York, NY, USA, 27 June–2 July 2015; pp. 499–505. [Google Scholar]
- Douceur, J.R.; Adya, A.; Bolosky, W.J.; Dan, S.; Theimer, M. Reclaiming space from duplicate files in a serverless distributed file system. Microsoft Res. 2002, 617–624, 617–624. [Google Scholar]
- Anderson, P.; Zhang, L. Fast and secure laptop backups with encrypted de-duplication. In Proceedings of the International Conference on Large Installation System Administration, San Jose, CA, USA, 7–12 November 2010; pp. 1–8. [Google Scholar]
- Mckeen, F.; Alexandrovich, I.; Berenzon, A.; Rozas, C.V.; Shafi, H.; Shanbhogue, V.; Savagaonkar, U.R. Innovative instructions and software model for isolated execution. In Proceedings of the International Workshop on Hardware and Architectural Support for Security and Privacy, Tel-Aviv, Israel, 23–24 June 2013; pp. 1–8. [Google Scholar]
- Intel Software Guard Extensions Programming Reference. 2016. Available online: https://software.intel.com/en-us/sgx (accessed on 4 June 2018).
- Zhao, X.; Zhang, Y.; Wu, Y.; Chen, K. Liquid: A scalable deduplication file system for virtual machine images. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1257–1266. [Google Scholar] [CrossRef]
- Yang, C.; Zhang, M.; Jiang, Q.; Zhang, J.; Li, D.; Ma, J.; Ren, J. Zero knowledge based client side deduplication for encrypted files of secure cloud storage in smart cities. Pervasive Mob. Comput. 2017, 41, 243–258. [Google Scholar] [CrossRef]
- Wang, M.; Li, W.; Wang, X. Transferring a generic pedestrian detector towards specific scenes. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Providence, RI, USA, 16–21 June 2012; pp. 3274–3281. [Google Scholar]



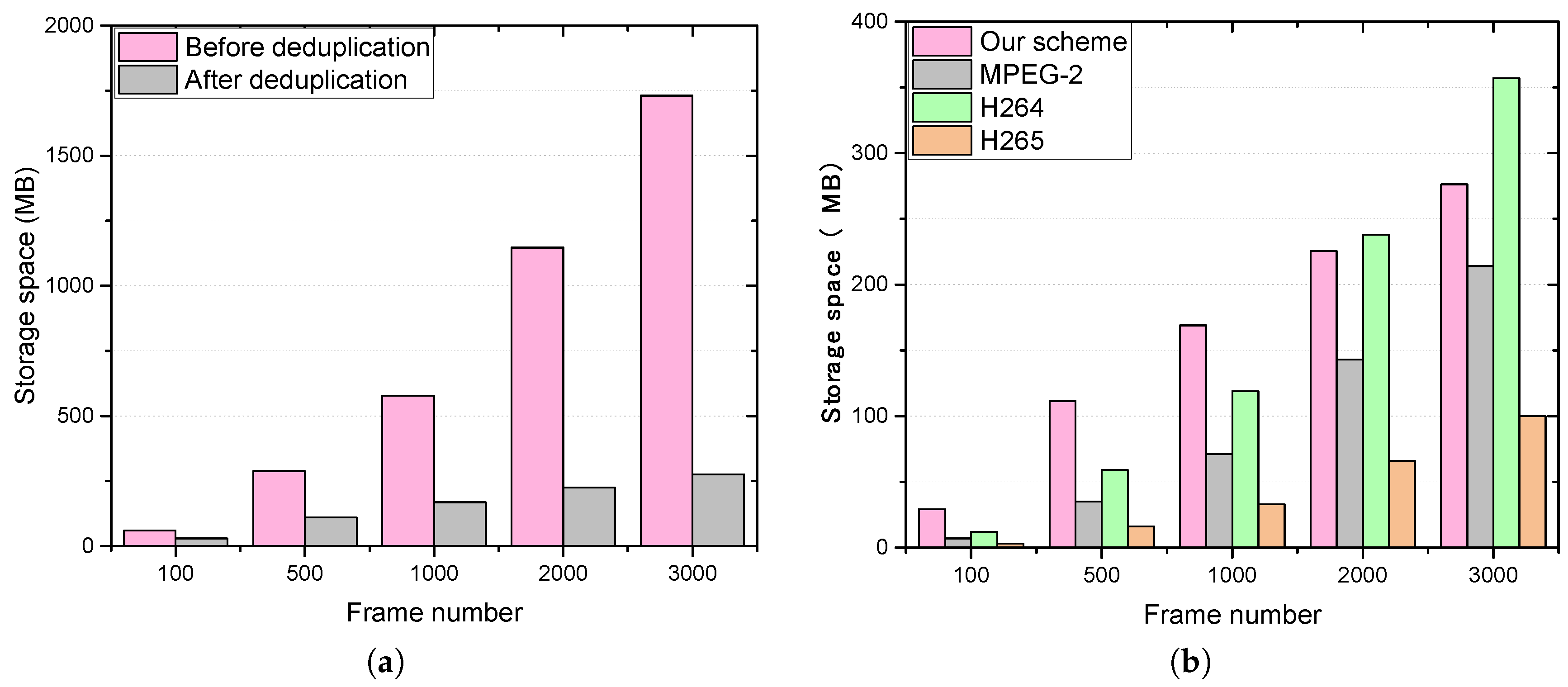
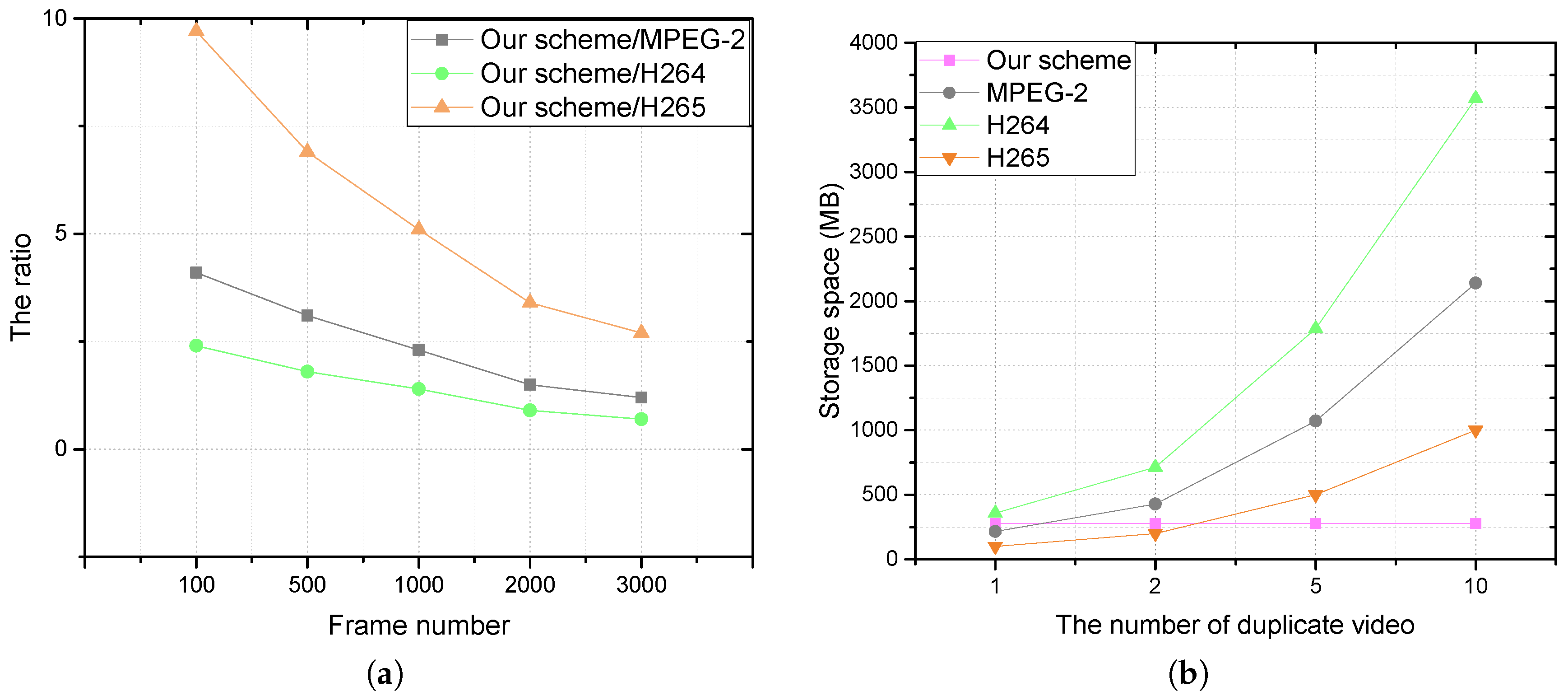
| Frame number | 100 | 500 | 1000 | 2000 | 3000 |
| Block number | 25,600 | 128,000 | 256,000 | 512,000 | 768,000 |
| Duplicated number | 13,101 | 78,875 | 181,108 | 411,352 | 645,410 |
| Deduplication ratio | 51% | 61.61% | 70.75% | 80.34% | 84.04% |
| Required storage space | 49% | 38.48% | 29.25% | 19.66% | 15.96% |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yan, H.; Li, X.; Wang, Y.; Jia, C. Centralized Duplicate Removal Video Storage System with Privacy Preservation in IoT. Sensors 2018, 18, 1814. https://doi.org/10.3390/s18061814
Yan H, Li X, Wang Y, Jia C. Centralized Duplicate Removal Video Storage System with Privacy Preservation in IoT. Sensors. 2018; 18(6):1814. https://doi.org/10.3390/s18061814
Chicago/Turabian StyleYan, Hongyang, Xuan Li, Yu Wang, and Chunfu Jia. 2018. "Centralized Duplicate Removal Video Storage System with Privacy Preservation in IoT" Sensors 18, no. 6: 1814. https://doi.org/10.3390/s18061814
APA StyleYan, H., Li, X., Wang, Y., & Jia, C. (2018). Centralized Duplicate Removal Video Storage System with Privacy Preservation in IoT. Sensors, 18(6), 1814. https://doi.org/10.3390/s18061814




