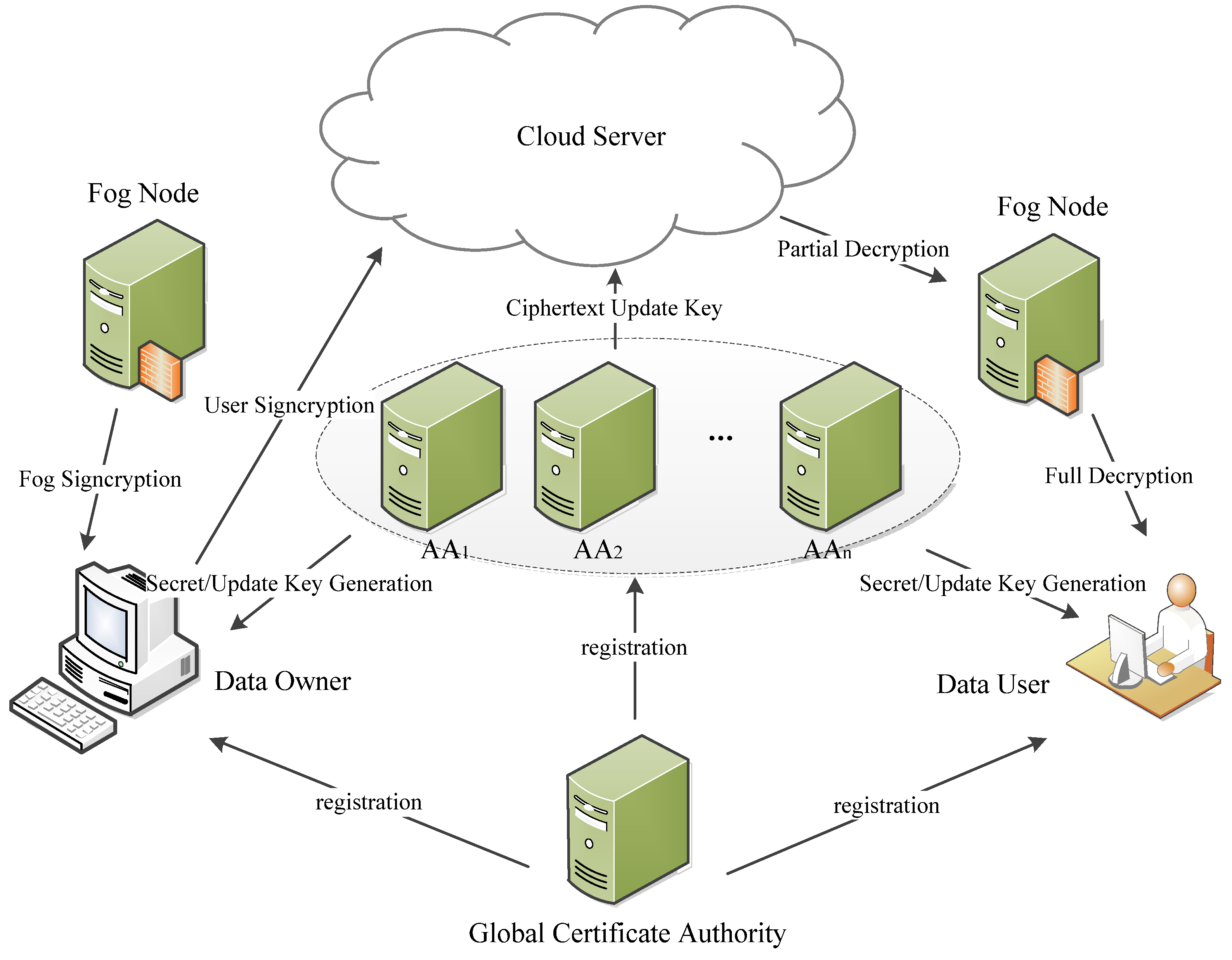
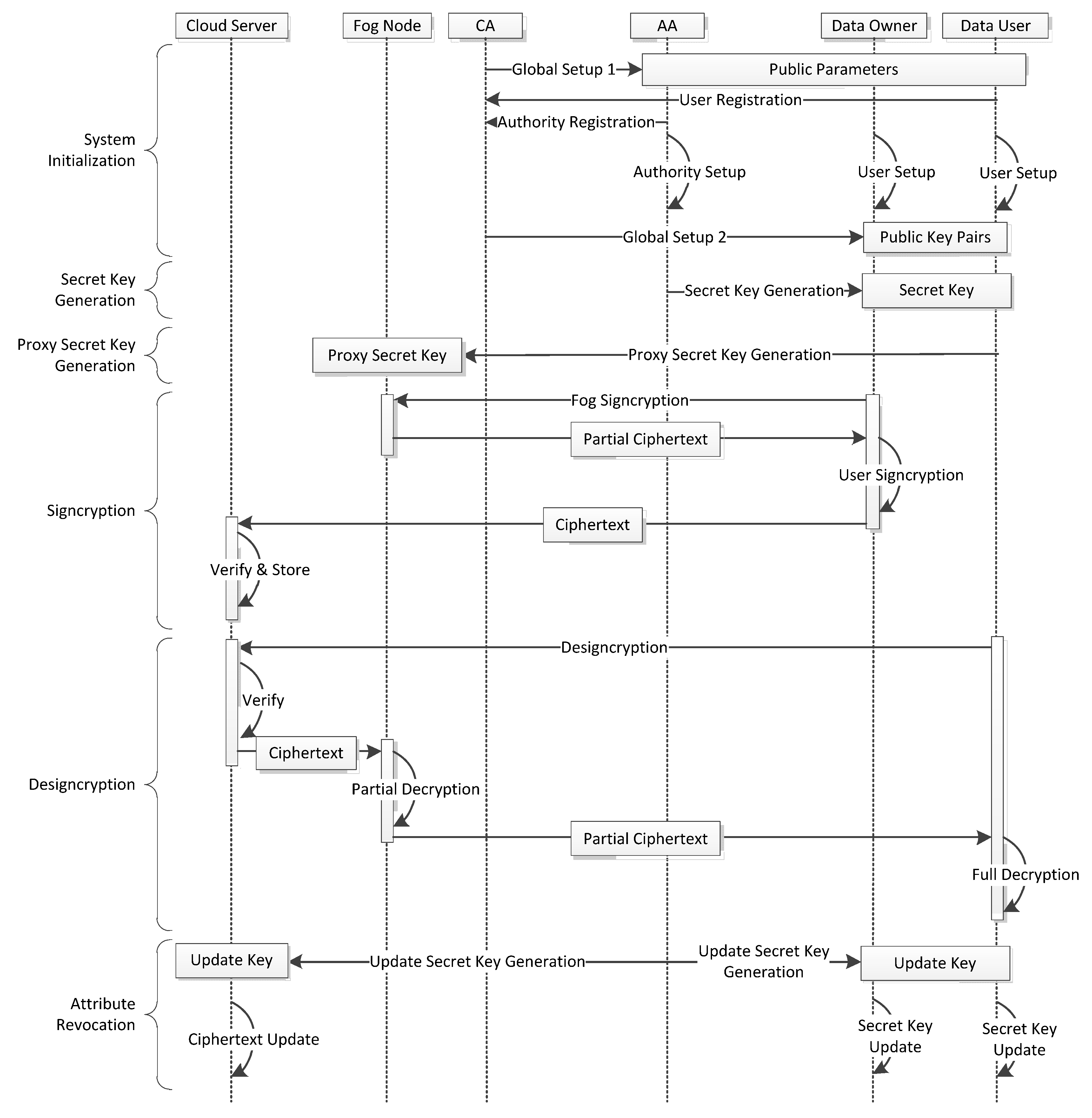
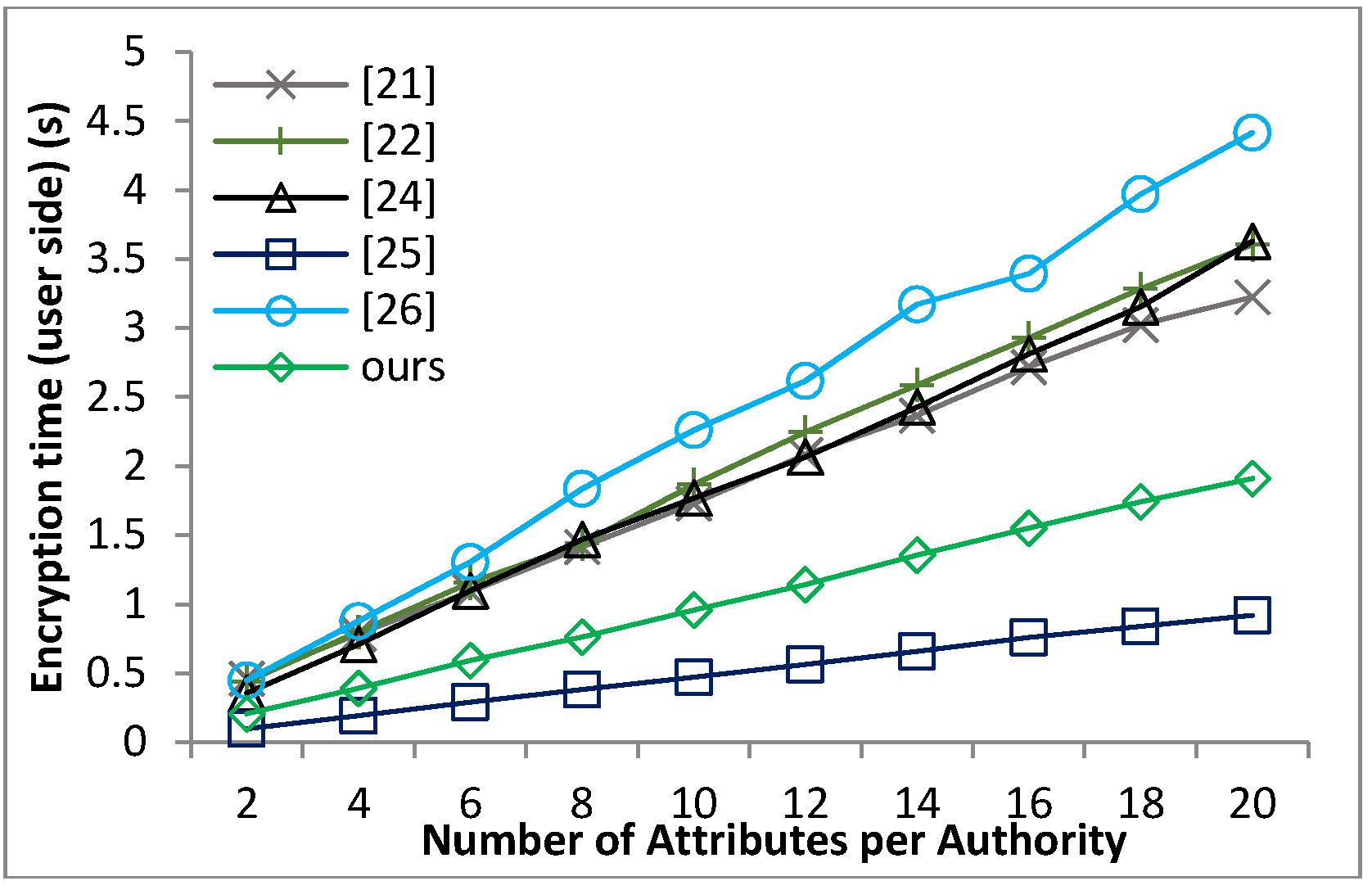
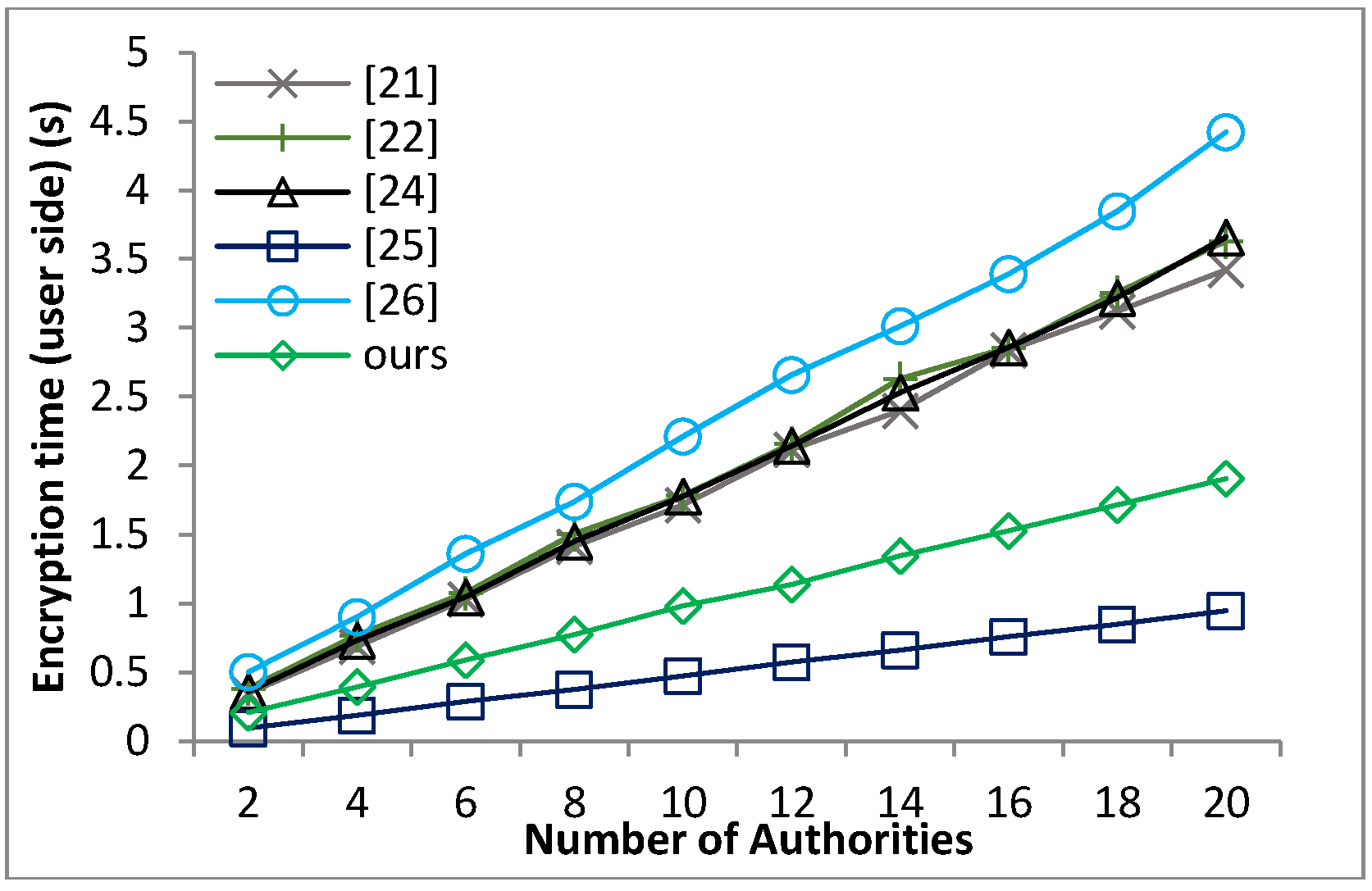
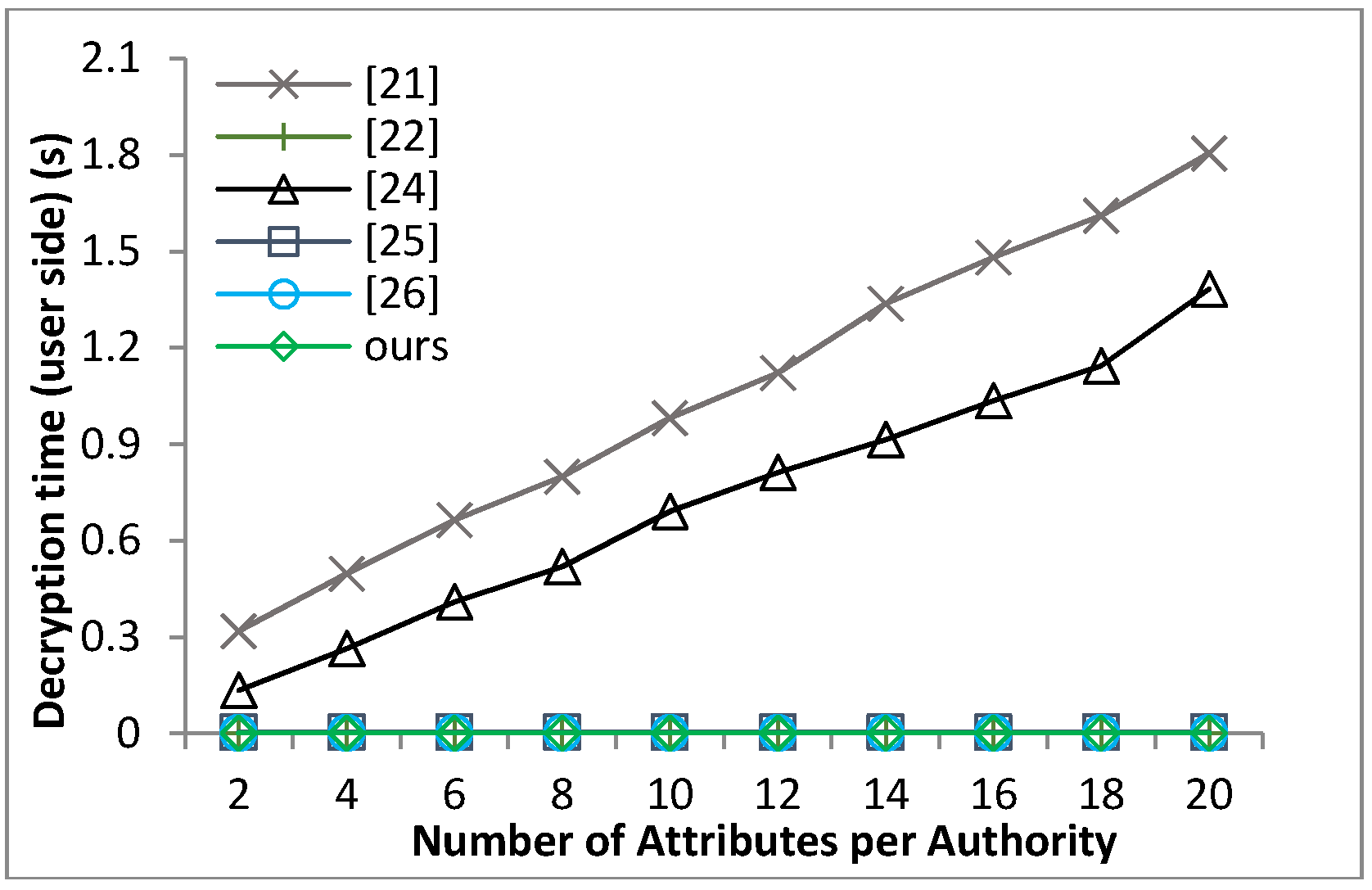
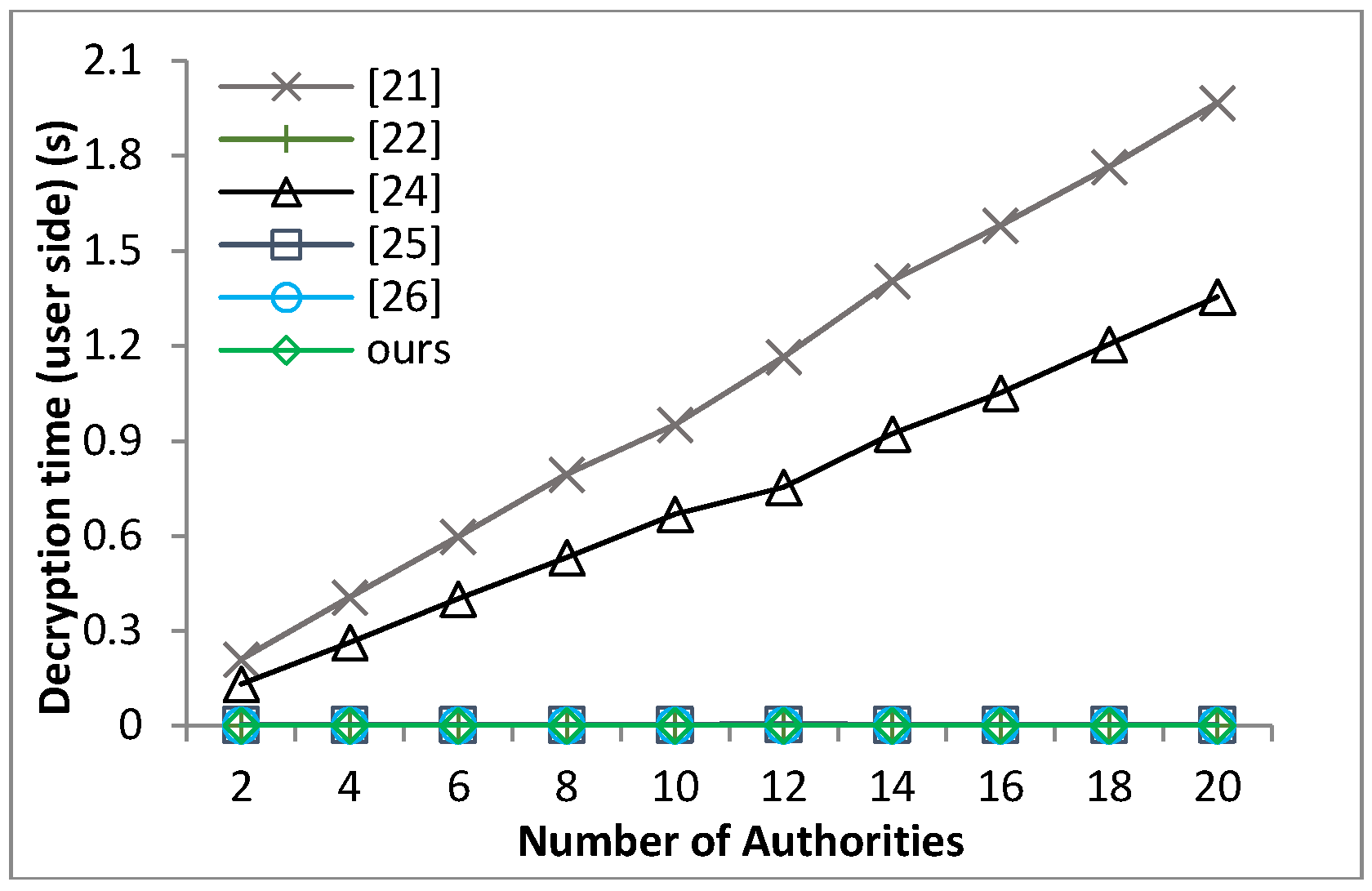
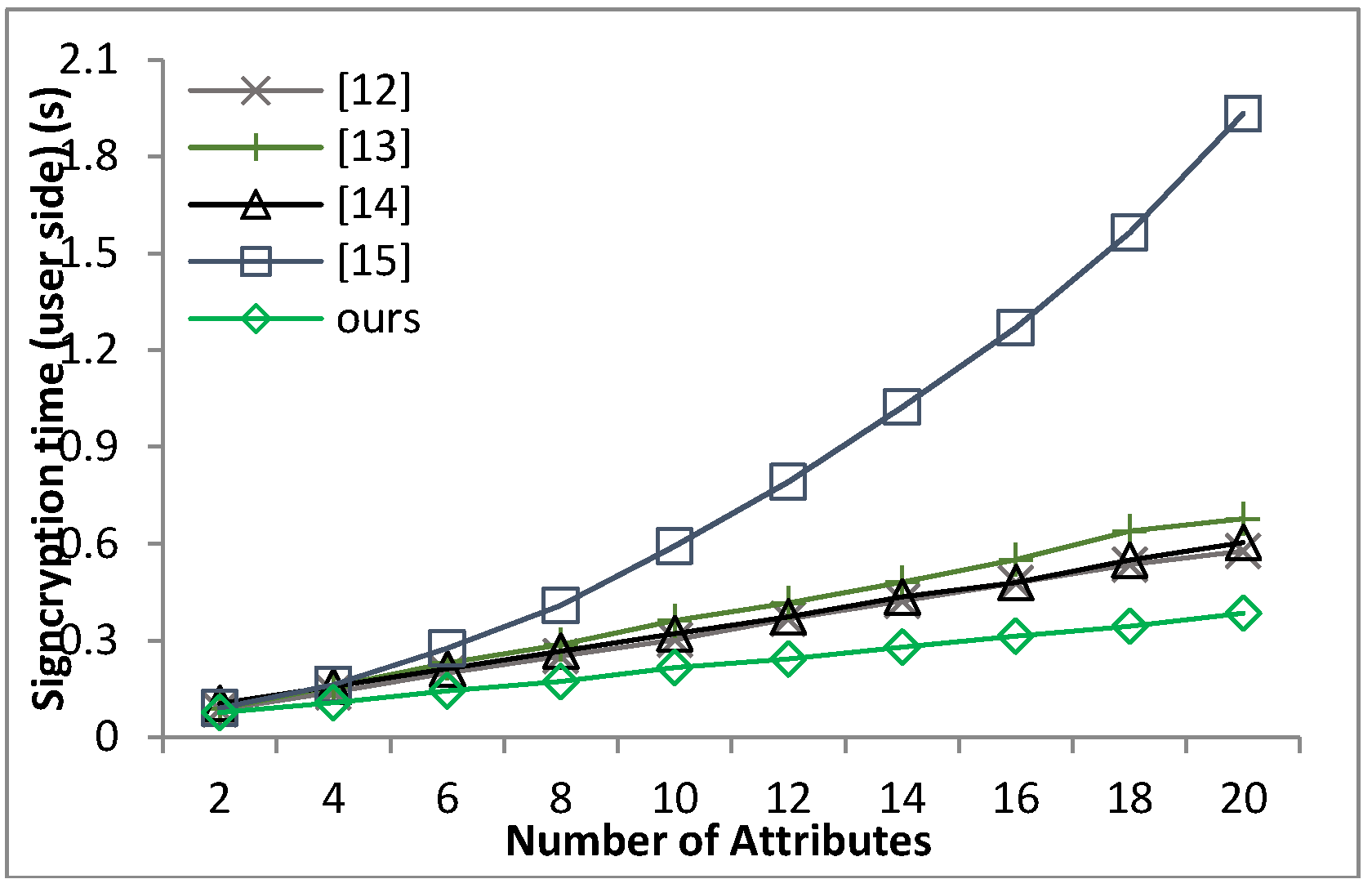
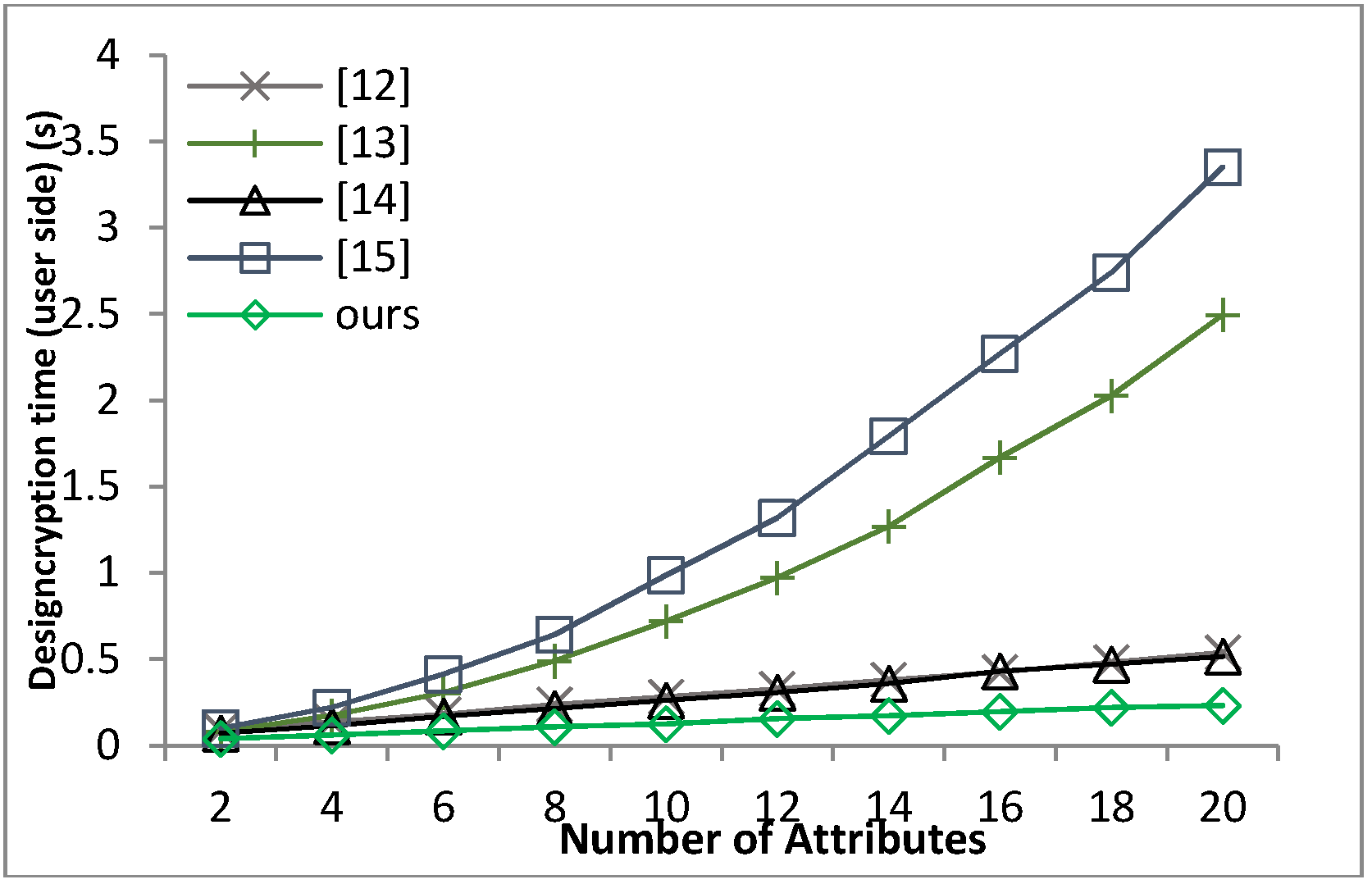
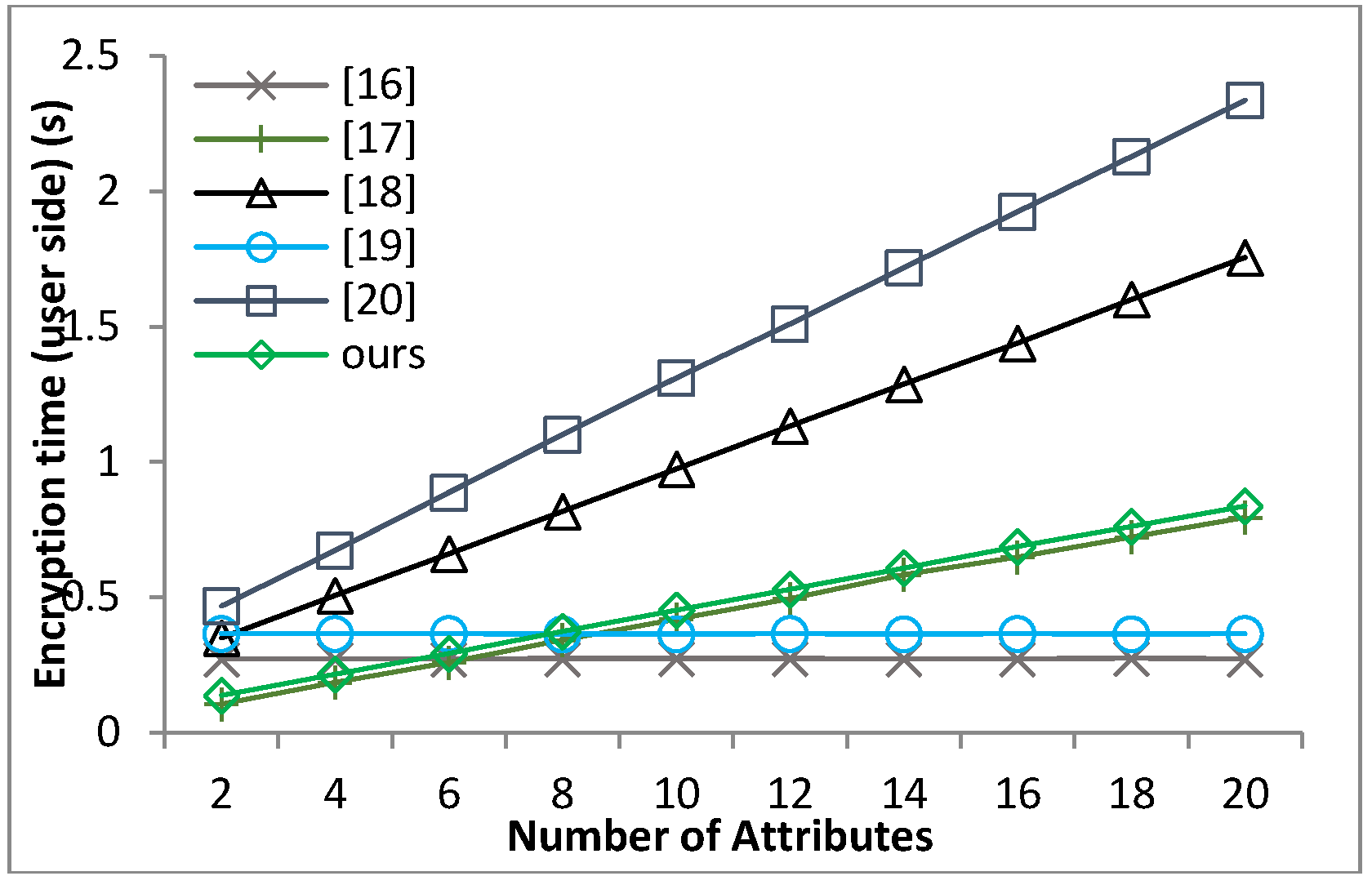
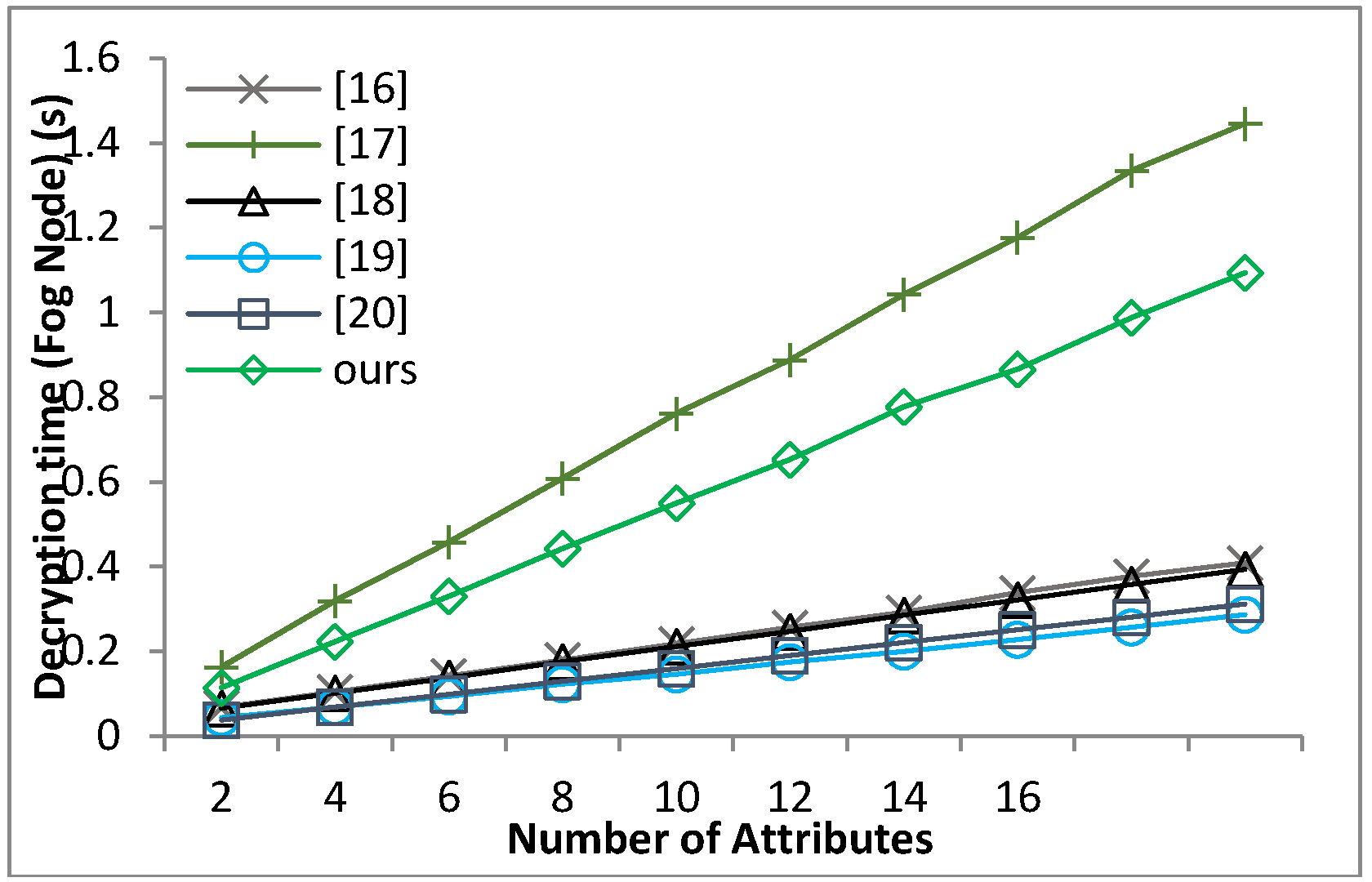
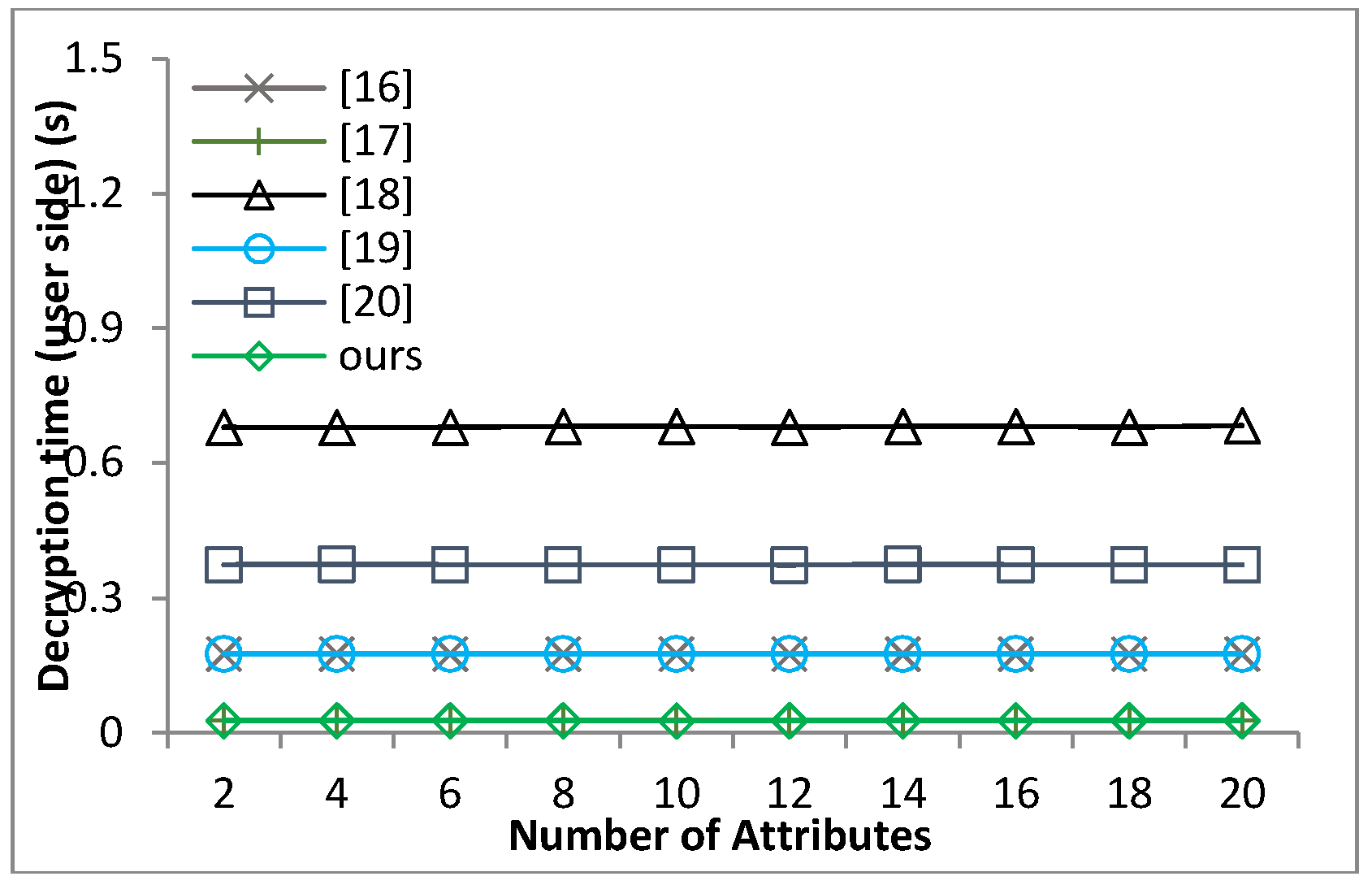
Based on the security model defined in Definition 8 and Theorem 1, we can prove that our proposed scheme guarantees the message confidentiality under the hardness of the q-PBDHE assumption.
Proof. Assume can break our scheme, we will construct the algorithm as follows: is given with the q-PBDHE challenge instance . The challenger runs to generate the bilinear group and chooses . If , sends to ; otherwise it sends to .
. The same as defined in Definition 8. Assume is the challenge encryption access structure over all the attributes selected from the set of authorities . Assume is a matrix and .
. The adversary chooses a set consisting of the corrupted authorities, and sends to the simulator . For each uncorrupted authority , randomly chooses and implicitly sets . publishes .
Let . , where .
sends to . initializes the empty list .
For the authority , chooses and sets . Let be the set consisting of the indexes with . For the attribute where , chooses and computes , where is the th element of . If , chooses and computes . This assignment describes that for each signing attribute as the signing attributes are different from encryption attributes. sends to . For the authority , generates the public keys and secret keys of as in the real scheme and sends both the public keys and secret keys to .
Phase 1.
. adaptively queries the secret keys for the attribute set with identity to the authority . does not satisfy together with any keys that can be obtained from corrupted authorities.
checks the list that whether the entry exists. If it does, sends and to the adversary and publishes the public key and .
- (1)
Otherwise, randomly picks from and chooses a vector such that and for all since . sets , , and computes as the public key . Then computes
, and sets as . For the attribute such that , computes . Otherwise, . sends and to the adversary and publishes the public key and . inserts into .
. checks the list that whether the entry exists. If it does not exist, issues query to compute and , and then runs and returns to . Otherwise, directly performs and returns to .
. submits a message , signing and encryption predicts . selects a signing attribute set such that . For each , computes the secret signing key and from , and , where is an arbitrary identity. Then returns the ciphertext to .
. If or , then returns . If , aborts. If algorithm is invalid, returns .Otherwise, carries out the following steps.
Assume the encryption predicate contained in is and is the set which consists of the indexes of the authorities whose attributes are associated with rows of .
If does not satisfy the challenge encryption predicate , then can obtain and secret decryption key from , and . returns the output of to .
Otherwise, if , assume , where is the secret value chosen to generate in signcryption phase. Then for , compute . Thus can return to .
. submits two messages with the same length and signing predicate to . Assume is the set which consists of the indexes of the authorities whose attributes are associated with rows of and is a matrix. chooses . selects a signing attribute set satisfying and an arbitrary identity .
Let such that , such that . Implicitly set . Then compute the challenge ciphertext as follows:
Let and implicitly sets for all . Select , .
, .
, .
, . .
,
, where and .
Finally, sends the challenge ciphertext to .
Phase 2. Phase 1 is repeated. In this phase, cannot issue with the challenge ciphertext and attribute set such that .
. outputs his guess on . If , outputs 0 and guess that ; otherwise, outputs 1 to indicate that is a random element in .
If issues with the ciphertext satisfying , then the simulation aborts. The probability is at most . If , and does not abort, then is a valid ciphertext of . In this case, we have . If is a random element in , then is a random element and cannot obtain , namely the advantage in this case is . Therefore, the advantage of which can break the q-PBDHE assumption is at least . The runtime of is at most . □