A Survey on Data Storage and Information Discovery in the WSANs-Based Edge Computing Systems
Abstract
1. Introduction
- We first summarize the data-storage and information-discovery schemes proposed for WSNs, and analyze why those schemes are not fit for the WSANs-based Edge computing systems. We do this because there are many similarities between the WSANs-based Edge computing systems and the WSNs-based systems.
- The existing schemes proposed for WSANs on data storage and information discovery are surveyed and compared with each other, and detail analysis on their advancements and shortcomings is also presented.
- Possible solutions are given on how to achieve high efficiency, high load balance, and perfect real-time performances at the same time for data storage and information discovery in the WSANs-based Edge computing systems.
2. Analyzing Whether the Data-Storage and Information-Discovery Schemes Proposed for WSNs Fit for WSANs
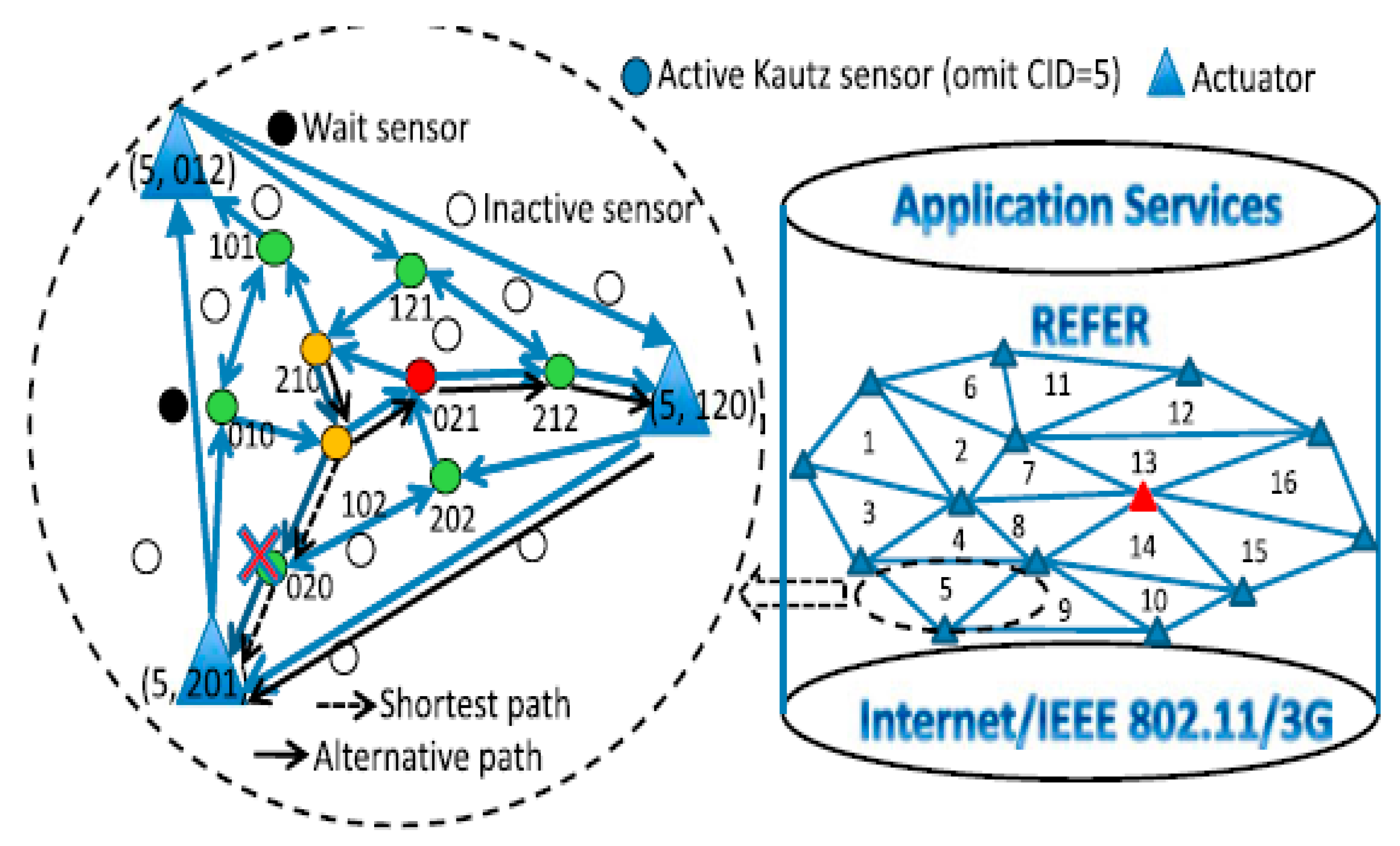
3. Analysis of the Data-Storage and Information-Discovery Schemes Proposed for WSANs
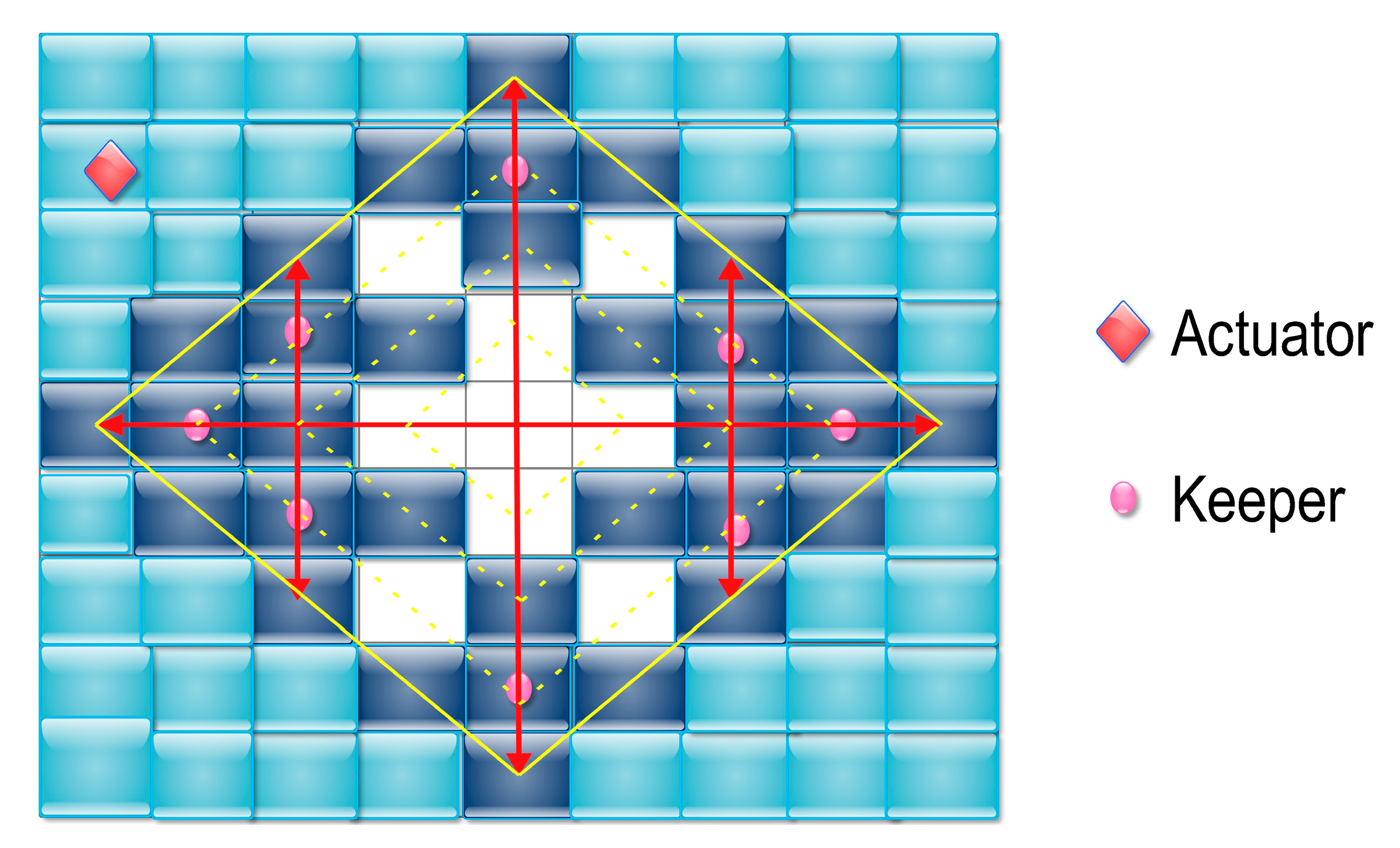
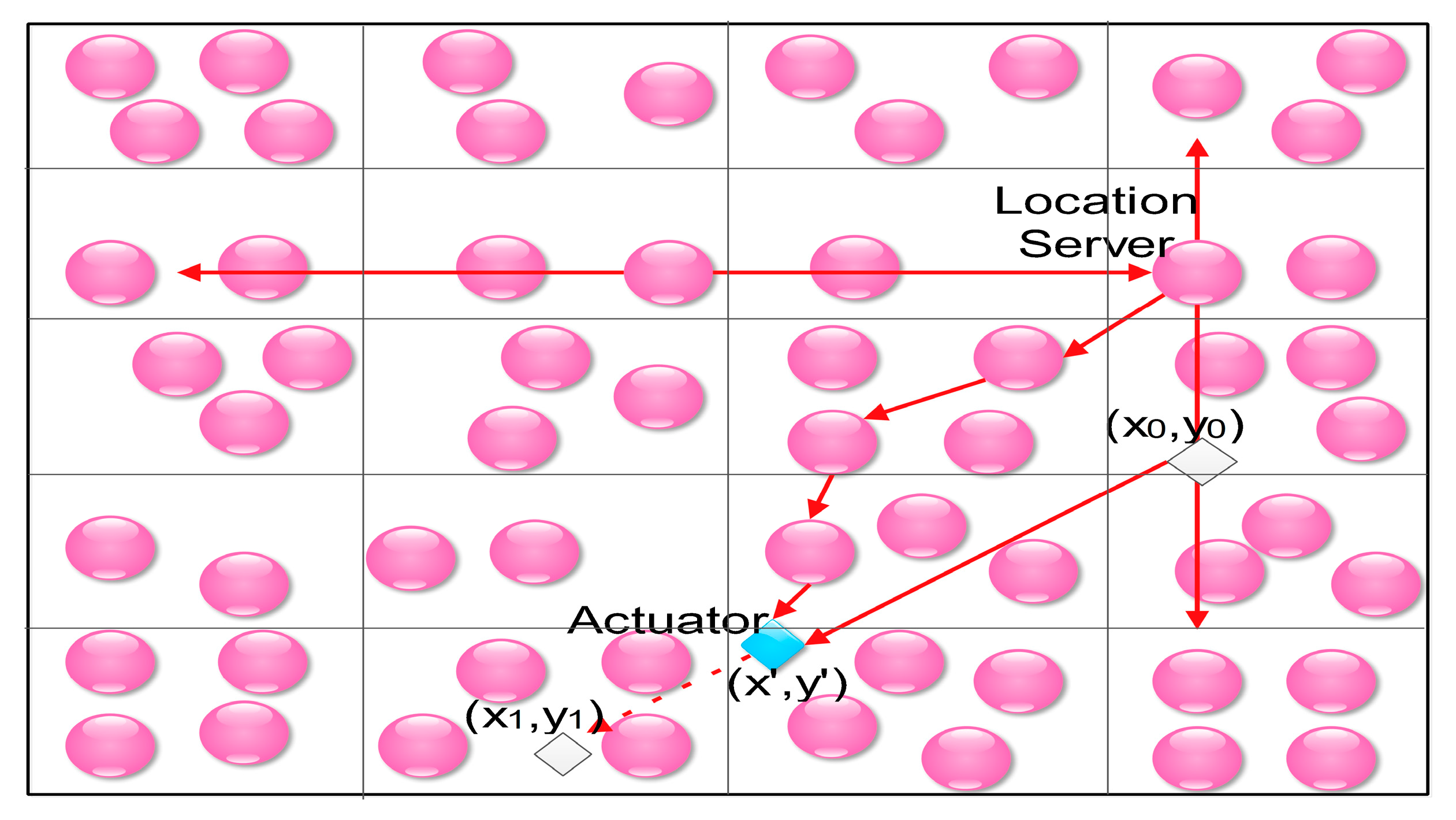
3.1. Schemes Based on the Query-Driven Model
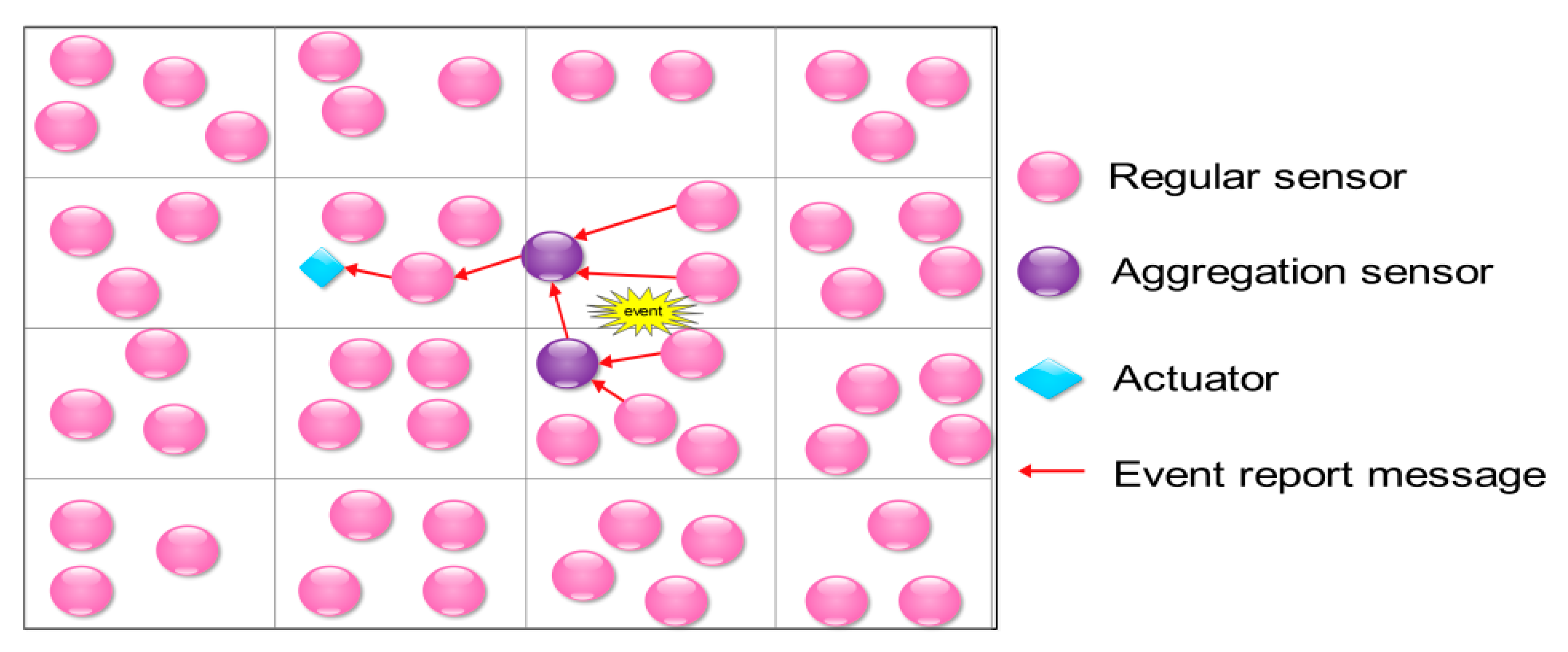
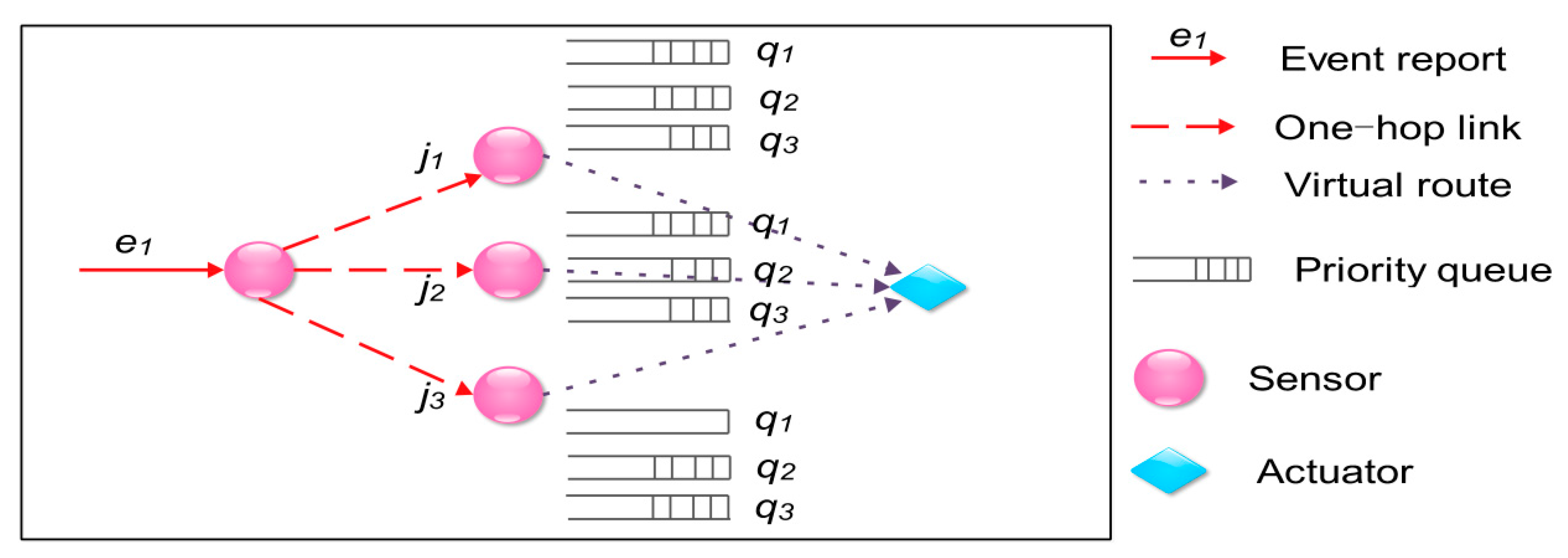
3.2. Schemes Based on the Event-Driven Model
3.3. Comprehensive Comparison and Analysis
4. Possible Solutions to Achieve the Multi-Objectives on Data Storage and Information Discovery in the WSANs-Based Edge Computing Systems
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Al-Fuqaha, A.; Guizani, M.M.; Mohammadi, M.M.; Mohammed, A.; Moussa, A. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Chen, S.; Zhao, J. The requirements, challenges, and technologies for 5G of terrestrial mobile telecommunication. IEEE Commun. Mag. 2014, 52, 36–43. [Google Scholar] [CrossRef]
- Han, T.; Ge, X.; Wang, L.; Kwak, K.S.; Han, Y.; Liu, X. 5G converged cell-less communications in smart cities. IEEE Commun. Mag. 2017, 55, 44–50. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Taleb, T.; Dutta, S.; Ksentini, A.; Lqbal, M.; Flinck, H. Mobile edge computing potential in making cities smarter. IEEE Commun. Mag. 2017, 55, 38–43. [Google Scholar] [CrossRef]
- Xu, Y.; Chen, X.; Liu, A.; Hu, C.A. Latency and Coverage Optimized Data Collection Scheme for Smart Cities Based on Vehicular Ad-hoc Networks. Sensors 2017, 17, 888. [Google Scholar] [CrossRef] [PubMed]
- Curiac, D.I. Towards wireless sensor, actuator and robot networks: Conceptual framework, challenges and perspectives. J. Netw. Comp. Appl. 2016, 63, 14–23. [Google Scholar] [CrossRef]
- Alves, M.; Pirmez, L.; Rossetto, S.; Delicato, F.; de Farias, C.; Pires, P.; dosSantos, I.; Zomaya, A. Damage prediction for wind turbines using wireless sensor and actuator networks. J. Netw. Comp. Appl. 2017, 80, 123–140. [Google Scholar] [CrossRef]
- Kan, Y.; Akerberg, J.; Gidlund, M.; Bjorkman, M. Realization and measurements of industrial wireless sensor and actuator networks. In Proceedings of the 2015 IEEE International Conference on Automation Science and Engineering, Gothenburg, Sweden, 24–28 August 2015; pp. 131–137. [Google Scholar]
- Sales, N.; Remedios, O.; Arsenio, A. Wireless sensor and actuator system for smart irrigation on the cloud. In Proceedings of the 2nd IEEE World Forum on Internet of Things, Milan, Italy, 14–16 December 2015; pp. 693–698. [Google Scholar]
- Zhou, J.; Chungui, L.; Zhang, Z. Intelligent transportation system based on SIP/ZigBee architecture. In Proceedings of the 2011 International Conference on Image Analysis and Signal Processing, Wuhan, China, 21–23 October 2011; pp. 405–409. [Google Scholar]
- Celtek, S.A.; Soy, H. An application of building automation system based on wireless sensor/actuator networks. In Proceedings of the 9th International Conference on Application of Information and Communication Technologies, Rostov-on-Don, Russia, 14–16 October 2015; pp. 450–453. [Google Scholar]
- Ghatak, S.; Bose, S.; Roy, S. Intelligent wall mounted wireless fencing system using wireless sensor actuator network. In Proceedings of the 2014 International Conference on Computer Communication and Informatics (ICCCI 2014), Coimbatore, India, 3–5 January 2014; pp. 1–5. [Google Scholar]
- Kułakowski, P.; Calle, E.; Marzo, J.L. Performance study of wireless sensor and actuator networks in forest fire scenarios. Int. J. Commun. Syst. 2013, 26, 515–529. [Google Scholar] [CrossRef]
- Tang, J.; Liu, A.; Zhao, M.; Wang, T. An Aggregate Signature Based Trust Routing for Data Gathering in Sensor Networks. Secur. Commun. Netw. 2018, 6328504. [Google Scholar] [CrossRef]
- Chen, X.; Xu, Y.; Liu, A. Cross Layer Design for Optimizing Transmission Reliability, Energy Efficiency, and Lifetime in Body Sensor Networks. Sensors 2017, 17, 900. [Google Scholar] [CrossRef] [PubMed]
- Ma, F.; Liu, X.; Liu, A.; Zhao, M.; Huang, C.; Wang, T. A Time and Location Correlation Incentive Scheme for Deeply Data Gathering in Crowdsourcing Networks. Wirel. Commun. Mob. Comput. 2018, 2018, 8052620. [Google Scholar] [CrossRef]
- Gonizzi, P.; Ferrari, G.; Gay, V.; Laguay, J. Data dissemination scheme for distributed storage for IoT observation systems at large scale. Inf. Fusion 2015, 22, 16–25. [Google Scholar] [CrossRef]
- Maia, G.; Guidoni, D.; Viana, A.; Aquino, A.; Mini, R.; Loureiro, A. A distributed data storage protocol for heterogeneous wireless sensor networks with mobile sinks. Ad Hoc Netw. 2013, 11, 1588–1602. [Google Scholar] [CrossRef]
- Shao, M.; Zhu, S.; Zhang, W.; Cao, G.; Yang, Y. pDCS: Security and privacy support for data-centric sensor networks. IEEE Trans. Mob. Comput. 2009, 8, 1023–1038. [Google Scholar] [CrossRef]
- Ren, Y.; Oleshchuk, V.; Li, F. Optimized secure and reliable distributed data storage scheme and performance evaluation in unattended WSNs. Comput. Commun. 2013, 36, 1067–1077. [Google Scholar] [CrossRef]
- Talari, A.; Rahnavard, N. CStorage: Decentralized compressive data storage in wireless sensor networks. Ad Hoc Netw. 2016, 37, 475–485. [Google Scholar] [CrossRef]
- Albano, M.; Chessa, S. Replication vs. Erasure coding in data centric storage for wireless sensor networks. Comput. Netw. 2015, 77, 42–55. [Google Scholar] [CrossRef]
- Shen, H.; Zhao, L.; Li, Z. A distributed spatial-temporal similarity data storage scheme in wireless sensor networks. IEEE Trans. Mob. Comput. 2011, 10, 982–996. [Google Scholar] [CrossRef]
- Yu, Z.; Xiao, B.; Zhou, S. Achieving optimal data storage position in wireless sensor networks. Comput. Commun. 2010, 33, 92–102. [Google Scholar] [CrossRef]
- Ma, X.; Gao, J.; Wang, W.; Wang, J. A virtual-ring-based data storage and retrieval scheme in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2012, 143, 869–876. [Google Scholar] [CrossRef]
- Liu, X.; Huang, Q.; Zhang, Y. Balancing push and pull for efficient information discovery in large-scale sensor networks. IEEE Trans. Mob. Comput. 2007, 6, 241–251. [Google Scholar]
- Lin, C.; Kuo, J.; Liu, B.; Tsai, M. GPS-free, boundary-recognition-free, and reliable double-ruling-based information brokerage scheme in wireless sensor networks. IEEE Trans. Comput. 2012, 62, 885–898. [Google Scholar]
- Liang, J.; Wang, J.; Li, T.; Chen, J. Maximum lifetime algorithm for precise data gathering based on tree in wireless sensor networks. Chin. J. Softw. 2010, 21, 2289–2303. [Google Scholar]
- Liu, C.; Wu, K.; Pei, J. An energy-efficient data collection framework for wireless sensor networks by exploiting spatiotemporal correlation. IEEE Trans. Parallel Distrib. Syst. 2007, 18, 1010–1023. [Google Scholar] [CrossRef]
- Dong, M.; Ota, K.; Liu, A.; Guo, M. Joint Optimization of Lifetime and Transport Delay under Reliability Constraint Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 225–236. [Google Scholar] [CrossRef]
- Jiang, H.; Jin, S.; Wang, C. Prediction or Not? An energy-efficient framework for clustering-based data collection in wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 1064–1071. [Google Scholar] [CrossRef]
- Liu, Y.; Dong, M.; Ota, K.; Liu, A.; Guo, M. ActiveTrust: Secure and Trustable Routing in Wireless Sensor Networks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2013–2027. [Google Scholar] [CrossRef]
- Kumar, A.; Sivalingam, K.; Kumar, A. On reducing delay in mobile data collection based wireless sensor networks. Wirel. Netw. 2013, 19, 285–299. [Google Scholar] [CrossRef]
- Francesco, M.; Das, S.; Anastasi, G. Data collection in wireless sensor networks with mobile elements: A Survey. ACM Trans. Sens. Netw. 2011, 8, 7–41. [Google Scholar] [CrossRef]
- Gao, S.; Zhang, H.; Das, S. Efficient data collection in wireless sensor networks with path-constrained mobile sinks. IEEE Trans. Mob. Comput. 2011, 10, 592–608. [Google Scholar] [CrossRef]
- Khan, A.; Abdullah, A.; Anisi, M.; Bangash, J. A comprehensive study of data collection schemes using mobile sinks in wireless sensor networks. Sensors 2014, 14, 2510–2548. [Google Scholar] [CrossRef] [PubMed]
- Dhamdhere, S.; Guru, S. Robust data collection in wireless sensor networks with mobile sinks. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 4999–5002. [Google Scholar]
- Yang, S.; Adeel, U.; Tahir, Y.; Mccann, J. Practical opportunistic data collection in wireless sensor networks with mobile sinks. IEEE Trans. Mob. Comput. 2017, 16, 1420–1433. [Google Scholar] [CrossRef]
- Zhang, X.; Dai, H.; Xu, L.; Chen, G. Mobility-assisted data-gathering strategies in WSNs. Chin. J. Softw. 2013, 24, 198–214. [Google Scholar] [CrossRef]
- Sugihara, R.; Gupta, R. Path planning of data mules in sensor networks. ACM Trans. Sens. Netw. 2011, 8, 1–30. [Google Scholar] [CrossRef]
- Cuevas, Á.; Urueña, M.; Romeral, R.; Larrabeiti, D. Data centric storage technologies: Analysis and enhancement. Sensors 2010, 10, 3023–3056. [Google Scholar]
- Cuevas, Á.; Urueña, M.; Cuevas, R.; Romeral, R. Modelling data-aggregation in multi-replication data centric storage systems for wireless sensor and actuator Networks. IET Commun. 2011, 5, 1669–1681. [Google Scholar] [CrossRef]
- Cuevas, Á.; Urueña, M.; Veciana, G.; Cuevas, R.; Crespi, N. Dynamic data-centric storage for long-term storage in wireless sensor and actuator networks. Wirel. Netw. 2014, 20, 141–153. [Google Scholar] [CrossRef]
- Ngai, E.; Zhou, Y.; Lyu, M.; Liu, J. A delay-aware reliable event reporting framework for wireless sensor–actuator networks. Ad Hoc Netw. 2010, 8, 694–707. [Google Scholar] [CrossRef]
- Karimi, H.; Medhati, O.; Zabolzadeh, H.; Jamalpoor, A. Implementing a reliable, fault tolerance and secure framework in the wireless sensor-actuator networks for events reporting. Proc. Comput. Sci. 2015, 73, 384–394. [Google Scholar] [CrossRef]
- Mustafa, A.; Turgut, D. Lightweight routing with dynamic interests in wireless sensor and actuator networks. Ad Hoc Netw. 2013, 11, 2313–2328. [Google Scholar]
- Shen, H.; Li, Z. A Kautz-based wireless sensor and actuator network for real-time, fault-tolerant and energy-efficient transmission. IEEE Trans. Mob. Comput. 2016, 15, 1–16. [Google Scholar] [CrossRef]
- Kakarla, J.; Majhi, B.; Battula, R. Comparative analysis of routing protocols in wireless sensor–actuator networks: A review. Int. J. Wirel. Inf. Netw. 2015, 22, 220–239. [Google Scholar] [CrossRef]
- Mo, L.; Cao, X.; Chen, J.; Sun, Y. Collaborative estimation and actuation for wireless sensor and actuator networks. IFAC Proc. Vol. 2014, 47, 5544–5549. [Google Scholar] [CrossRef]
- Zeng, Y.; Li, D.; Vasilakos, A. Real-time data report and task execution in wireless sensor and actuator networks using self-aware mobile actuators. Comput. Commun. 2013, 36, 988–997. [Google Scholar] [CrossRef]
- Konstantopoulos, C.; Pantziou, G.; Venetis, I.; Gavalas, D. Efficient event handling in wireless sensor and actuator networks: An on-line computation approach. J. Netw. Comput. Appl. 2016, 75, 181–199. [Google Scholar] [CrossRef]
- Yi, J.; Shi, W.; Tang, Y.; Xu, L. A dynamic task scheduling for wireless sensor and actuator networks. Chin. J. Electron. 2010, 38, 1239–1244. [Google Scholar]
- Xu, Z.; Chen, C.; Guo, Y.; Guan, X. Ballooning: An agent-based search strategy in wireless sensor and actuator networks. IEEE Commun. Lett. 2011, 15, 944–946. [Google Scholar] [CrossRef]
- Xu, Z.; Chen, C.; Cheng, B.; Guan, X. Sharing mobility strategy improves location service in wireless sensor and actuator networks. IEEE Commun. Lett. 2012, 16, 858–861. [Google Scholar]
- Bettstetter, C.; Hartenstein, H.; Pérezcosta, X. Stochastic properties of the random waypoint mobility model. Wirel. Netw. 2004, 10, 555–567. [Google Scholar] [CrossRef]
- Bose, P.; Morin, P.; Stojmenovi’c, I.; Urrutia, J. Routing with guaranteed delivery in ad hoc wireless networks. Wirel. Netw. 2001, 7, 609–616. [Google Scholar] [CrossRef]
- Li, J.; Liu, X. An important aspect of big data: Data usability. J. Comput. Res. Dev. 2013, 50, 1147–1162. [Google Scholar]
- Ota, K.; Dong, M.; Gui, J.; Liu, A. QUOIN: Incentive Mechanisms for Crowd Sensing Networks. IEEE Netw. Mag. 2018. [Google Scholar] [CrossRef]

| Systems | Energy Efficiency | Real-Time Support | Load Balance | Fault Tolerance | Actuator Movement Support |
|---|---|---|---|---|---|
| Traditional data-centric WSANs [42] | high | × | bad | bad | √ |
| Long-term storage WSANs [44] | high | × | good | good | √ |
| Delay-aware WSANs [45] | high | √ | good | good | × |
| Ballooning [54] | low | √ | good | good | √ |
| MLS [55] | low | √ | good | good | √ |
| LRP-QS [47] | high | √ | good | good | × |
| REFER (REal-time, Fault-tolerant and EneRgy-efficient WSAN) [48] | high | √ | good | good | × |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ma, X.; Liang, J.; Liu, R.; Ni, W.; Li, Y.; Li, R.; Ma, W.; Qi, C. A Survey on Data Storage and Information Discovery in the WSANs-Based Edge Computing Systems. Sensors 2018, 18, 546. https://doi.org/10.3390/s18020546
Ma X, Liang J, Liu R, Ni W, Li Y, Li R, Ma W, Qi C. A Survey on Data Storage and Information Discovery in the WSANs-Based Edge Computing Systems. Sensors. 2018; 18(2):546. https://doi.org/10.3390/s18020546
Chicago/Turabian StyleMa, Xingpo, Junbin Liang, Renping Liu, Wei Ni, Yin Li, Ran Li, Wenpeng Ma, and Chuanda Qi. 2018. "A Survey on Data Storage and Information Discovery in the WSANs-Based Edge Computing Systems" Sensors 18, no. 2: 546. https://doi.org/10.3390/s18020546
APA StyleMa, X., Liang, J., Liu, R., Ni, W., Li, Y., Li, R., Ma, W., & Qi, C. (2018). A Survey on Data Storage and Information Discovery in the WSANs-Based Edge Computing Systems. Sensors, 18(2), 546. https://doi.org/10.3390/s18020546






