Abstract
This paper investigated the throughput performance of a secondary user (SU) for a random primary user (PU) activity in a realistic experimental model. This paper proposed a sensing and frame duration of the SU to maximize the SU throughput under the collision probability constraint. The throughput of the SU and the probability of collisions depend on the pattern of PU activities. The pattern of PU activity was obtained and modelled from the experimental data that measure the wireless local area network (WLAN) environment. The WLAN signal has detected the transmission opportunity length (TOL) which was analyzed and clustered into large and small durations in the CTOL model. The performance of the SU is then analyzed and compared with static and dynamic PU models. The results showed that the SU throughput in the CTOL model was higher than the static and dynamic models by almost 45% and 12.2% respectively. Furthermore, the probability of collisions in the network and the SU throughput were influenced by the value of the minimum contention window and the maximum back-off stage. The simulation results revealed that the higher contention window had worsened the SU throughput even though the channel has a higher number of TOLs.
1. Introduction
Dynamic spectrum access (DSA) is one of the cognitive radio (CR) technologies, and it is used to utilise the spectrum proficiently. The purpose of DSA is to use the primary user (PU) channel that is sparsely occupied by other temporary users such as the secondary users (SU). Opportunistic spectrum access (OSA) or commonly known as the spectrum overlay is one of the DSA schemes which has the best compatibility with the static PU transmission [1]. Accordingly, the OSA enables the SU to access a channel when the PU is detected as an idle state through the spectrum sensing process (SSP). Previous studies [2,3,4] have reported that the longer sensing duration has reduced not only the collision probability but also introduced a time overhead that decreases the SU throughput. Hence, this study intended to investigate the compromise between the increment of SU throughput and the reduction of the interference to understand the fundamental performance of the CR network.
Spectrum opportunities or also known as the transmission opportunity length (TOL) can be detected using spectrum sensing and may influence the SU performance. In [2] the length of contention phase in small-scale-backoff-based of MAC protocol (SMAC) has been studied. The SU will not interfere during the contention phase but only can use the remaining period to transmit data. The remaining period is considered to be TOL for SU to transmit data. The longer TOL may increase more chances of the SU to access a channel compared to the smaller TOL. According to [2,4], TOL durations provide a variable impact in the performance of SU throughput and interference to the PU. Therefore, the strategy that is used to access the channel should consider analyzing the length of TOL from the PU activity patterns to obtain a better SU performance.
The behavior of the SU networks is influenced by the spectrum occupancy patterns in PU networks [5]. Hence, the accuracy of the PU activity model is considered to be an important factor. The PU activity durations are usually modelled as an exponential distribution of random variables in [6,7,8,9]. According to several empirical measurement studies [10,11,12,13] on the time duration of PU activity, it is not exponentially distributed in the actual system [6]. Moreover, the prior spectrum usage models that have been widely used are based on several assumptions which have not been validated by empirical evidence [14,15].
In this study, the PU activity is obtained from the real-time experimental or measurement data. This study has used an experimental setup for a wireless local area network (WLAN) to measure the TOL in the system in which WLAN is emulated as a PU to represent the random PU activity. Furthermore, an empirical model based on the primary user traffic for opportunistic access (EM-PuO) is introduced as an empirical model of the PU channel usage pattern. The model offers access to the SU based on a realistic wireless environment, where the PU activity pattern is modelled based on an actual WLAN environment. Besides that, energy detection is used to detect the PU and extract the TOL. The TOL is clustered into two categories which are small and large, and the first order of the Markov model is used to obtain the PU activity pattern based on the clustering of the TOL. The main contributions of this paper are summarized as follows:
- EM-PuO model: The PU activity traffic pattern model is designed based on a realistic (i.e., real-time) wireless environment which is WLAN. The EM-PuO is an empirical model of the measured WLAN signal. This model presents a temporal characterization of the detection TOL which approaching the real situation as it was constructed by the experiment in a wireless environment. This empirical model will be used to demonstrate the SU access strategy in the CTOL model.
- Clustering TOL model: A new SU access strategy from clustering the durations of TOL. The TOLs in the EM-PuO model was analyzed and then classified into two types of TOL which are large and small. The CTOL model is designed using a Markov model that formulated the two states using the clustered TOLs. The probability of collision and the SU throughput were investigated using CTOL model by considering the dynamic PU traffic.
2. Related Work
It was known that several spectrum access techniques used mathematical models such as Markov decision process (MDP) [16], queuing theoretic [17], and game theoretic [18]. A multiple access strategy with cooperative relays was proposed in [17,19,20] where the SUs were modelled as a separate queuing system. A coalitional game theoretic approach is presented in [18,21], while Jiang et al. in [22] proposed a joint spectrum sensing and access framework that used evolutionary game theory. The other spectrum or channel access technique is using rendezvous scheme which does not rely on the common control channel (CCC) to control messages before starting data transmission. According to [23,24] this approach can overcome the dense in the CR network.
There are two types of PU activity models that are used as references: (1) the first model is a static PU model, which is a detection model, and it assumes that the PU is either present or absent during the SU frame duration [4,25]; and (2) the second model is known as the dynamic PU model, which is a cross-layer approach indicating the PU’s traffic model based on its arrival and departure time [2,4,26]. The dynamic PU model is designed to demonstrate a realistic situation where the PU may randomly arrive or depart from the channel at any time.
The trade-off between the sensing and SU throughput was investigated to get a better quality of sensing time without degrading the achievable throughput. The quality of sensing can be improved by increasing the sensing period, but it will affect the SU throughput as a result of fixing the overall frame duration. The sensing-throughput trade-off was studied in [27,28] by assuming that the PU is static, while the dynamic PU traffic was addressed in [2,4,26].
3. System Model
The system model is an ad hoc network consisting of a pair of primary transmitters, and the primary destination shares a channel with a pair of SUs. The SUs communicate with each other using direct transmission by identifying the spectrum holes via spectrum sensing. The flow of the CTOL system can be categorized into five main parts. The parts are included the measurement of WLAN signal and detection, modelled the EM-PuO, and clustered the TOL and performance evaluation. Figure 1 shows the sequence of the parts.
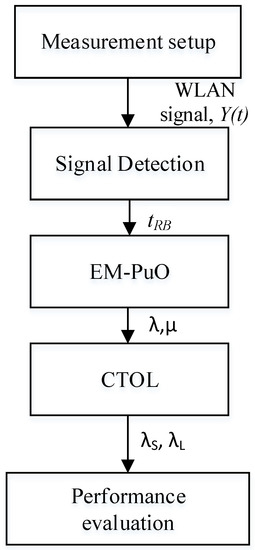
Figure 1.
Flow chart of the CTOL system.
The SU frame structure is divided into two segments which are sensing time, and data transmission time, , as shown in Figure 2. The frame duration is equal to , and the total number of samples in a frame is denoted as . It is assumed that the SU operation occurs within one frame and the energy detection is performed during the sensing period. According to the Nyquist theorem, the sampling interval is set as , where is the channel bandwidth and is the total number of samples.
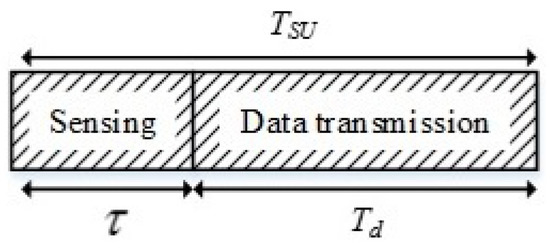
Figure 2.
Secondary user (SU) frame structure.
3.1. Measurement Setup
An experimental setup measures the WLAN signal to demonstrate a random PU activity that resembles a real-time wireless environment. There are two stations (STAs) and an access point (AP1) in the experiment. The two STAs are identified as STA1 and STA2, which are connected to AP1 through a wired and wireless LAN, respectively. Both STA1 and STA2 share a significant amount of the data (i.e., file) through AP1. STA2 retrieves the data file from STA1 using the MS Windows file sharing facility. The large data file is used to avoid the download process from being completed during the measurement process. Therefore, the resultant traffic via the access to the WLAN is considered to be full-buffering. Table 1 shows the specification of the WLAN system in the experiment. The detecting antenna (DA) has discovered a packet in the system, which is a wireless LAN Omni-antenna. The DA is connected to a real-time spectrum analyzer, SA2600 (Techtronic, SW Karl Braun Drive, OR, USA), to display the spectral activities of the system in an indoor real-time environment. The measurement antenna is located near STA1 and AP1 to maintain the power of the signal. As a result, the setup can avoid false alarms and misdetections. Figure 3 shows the structure of the experimental setup.

Table 1.
The Specifications of the WLAN system.

Figure 3.
The experimental setup of the WLAN networks.
3.2. The Detection of the WLAN (802.11) Signal
The detected signal of the wireless network is observed from AP1 and displayed in the SA2600 spectrum analyzer, which is then saved for offline processing and analysis. The displayed signal is emulated as PU activity in a channel, and the parameters of the signal detector are listed in Table 2.

Table 2.
Parameters of Signal detector.
The active and idle states of the channel are extracted from the experimental data based on the energy detection which is the preferred approach in many prior studies due to its simplicity and relevance in processing the measurement power [14,29,30]. The energy detection compares the received signal energy in a certain channel to a correctly established decision threshold. The hypotheses model of the detection technique is defined as:
where , with is the sample of Gaussian white noise, and , with are the samples of the PU signals. The indicates that the spectrum bands are detected as being idle, and indicates that the PU occupies a channel.
The SU data transmission is activated based on the spectrum sensing result, where the SU will be transmitted during while remaining silent during . The threshold for the targeted and is formulated as [31]:
where and are the target detection probability and false alarm probability, whereas is the noise variance, is the signal to noise ratio, and is the number of samples.
Figure 4 illustrates the number of idle period () detected with three different thresholds which are , and . In Figure 4a the number of detected is 78, which is the lowest among the other threshold decisions. For Figure 4b,c, the number of detected is the same which is equal to 156. The received signal is then compared with the correctly established threshold value, which is . The threshold value is chosen since it allows the received signal sense higher numbers of compared to the threshold value of , in addition to allow detection of longer idle times, compared to the threshold of .
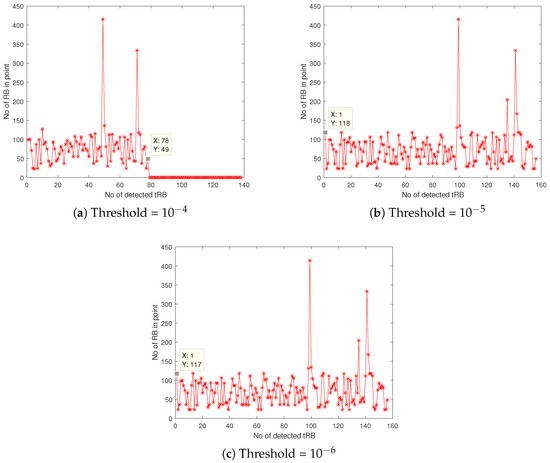
Figure 4.
The number of idle times detected with different threshold values: (a) , (b) and (c) .
4. Primary User Traffic Model Based on the Empirical Model: EM-PuO Design
The PU activity model is based on a real-time experimental data. An experimental setup to measure the TOL of a WLAN is employed in Section 3.1. The extracted TOL from the WLAN signal is analyzed and modelled as EM-PuO. The EM-PuO is the empirical measurement data of the PU, which is emulated by the WLAN system as random PU activity for SU opportunistic transmission. The modelled EM-PuO is used to determine the realistic spectrum occupancy of the PU channels based on the actual measurement of the WLAN system.
4.1. Analysis of the Detected WLAN (802.11) Signal
The obtained signal is analyzed according to the MAC protocol of the IEEE 802.11a standard. The signal includes the data packet, short inter-frame spacing (SIFS), ACK, and stop period, . The is a space that consists of distributed coordination function spacing (DIFS), and the random back-off time (). Figure 5 shows the analyzed WLAN signal. In the standard transmission data packet, the appearance of SIFS indicates the end of the data packet, and the ACK signal is sent by AP1 to acknowledge the received packet.
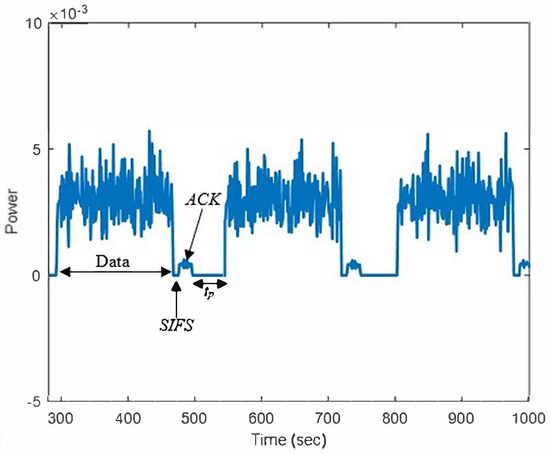
Figure 5.
The analysed WLAN signal using the spectrum analyzer.
The appearances of the data series and SIFS, ACK, and DIFS spaces thereby indicate that the channel is busy and is known as . While running the random back-off time, the channel is identified as (PU ‘off’state). The states of and are expressed as given by the following equations:
where is time for random back-off.
In this system, the PU also performs sensing to detect the wireless access. If there is any access detected during , the countdown of the back-off is immediately stopped. During measurement, the SU transmitter and receiver are configured to communicate through a short-range communication with minimum signal power. Even though the SU signal is low, it still produces harmful interference to PU due to the close distance between the SU transmitter and PU receiver. In this situation, the PU could not detect any access in the system but suffers from the hidden node terminal interference. In order to avoid this problem, the SU is only used to exploit the spectrum during the back-off period, .
4.2. The Probability Distribution of Idle Time
Based on the extracted length of and obtained from the empirical data, a cumulative distribution function (CDF) was derived and compared to the probability of the distribution model. Notably, the exponential distribution is used to fit with the obtained empirical curves to present the duration of the idle and busy states in the statistical properties. Assuming that the exponential matches or corresponds to the idle periods, it can be defined as follows:
where the estimated of the considered exponential distribution that uses the relation is as follows:
Next, the Kolgomorov-Sminorv (KS) test is calculated as [32] for both empirical data and exponential fit to quantify the distance, :
where is empirical cdf of . After running the KS test, the and are approximately the exponential distribution random variables as and respectively.
5. Clustering Transmission Opportunity Length (CTOL) Model
The CTOL model represents the presence and absence of PU, which is similar to [2] which is based on the PU arrival and departure time. The channel occupancy contains of two states, in which represent the channel are idle and occupied, respectively. In this model, the TOLs are clustered or separated into two groups that are denoted as large TOL, and small TOL, . The is defined as idle states, while is assumed as busy in .
There are two states of SU frame structure, in which 0 represents the sensing time state while and 1 is the data transmission time. No collision will happen when the SU state is 0 and collision may occur during 1. Hence, there are four different states of PU’s traffic in the CTOL model, which are based on the channel occupancy and SU frames structure during the transmission. The four states are: (i) ; (ii) ; (iii) ; and (iv) .
5.1. CTOL Protocol Design
The duration of is a critical factor that enables the SU to access the channel. Therefore, it is important to analyze so that the throughput of the SU is enhanced without causing any harmful interferences to the PU. In the CTOL model, the detected undergoes the clustering process that is detached to the large and small idle time. The transmission opportunity length of the channel is defined as follows:
where and are large and small idle times, respectively and is the threshold values of the random back-off time. The is determined by considering the range of the total in the system and the contention window (W) value.
From the classification of , the opportunity length of the time required to access a channel is modelled using the two-state Markov model. The PU activity is modelled as based on the assumption that offers an idle channel for the access of SU. Meanwhile, is assumed not suitable for the SU transmission because it will be exposed to the interference in the channel. The mean values of and in the exponential distribution are given as and , respectively.
Additionally, the probability of the transition of time from large to large and small to large are formulated as follows:
where is the total number of and is the total number of . Meanwhile is the number of TOL transition from to , is the transition from to , is transition from to , and is the transition from to .
5.2. PU Traffic Model
A realistic PU traffic model is then developed as in [2] to analyze the detection of the PU’s signal by the SUs during spectrum sensing. The detected WLAN signal in Section 3.2 is emulated as the PU traffic pattern. The CTOL model uses the empirical data from the measured WLAN signal and analyzed them randomly. This model uses equations in [2] as references to develop the random arrival and departure times of PU. Figure 6 shows the PU’s random departure and arrival times within one frame of SU that considers the duration of and .
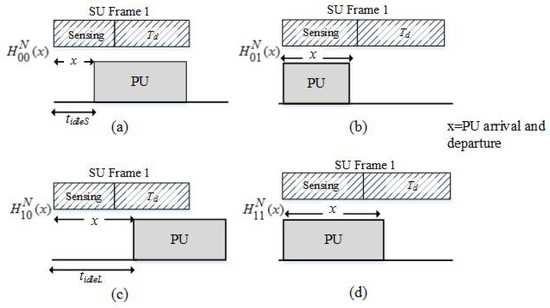
Figure 6.
The PU’s traffic model of the CTOL model.
The different scenarios of PU traffic pattern in CTOL model are indicated using the notation of . The subscript indicates the channel occupancy status, is the SU frame structure states, and represents the PU arrival and departure time. The superscript represents the new model, which is the CTOL model.
Initially, in and , the PU is absent, and the noise is only detected during the sensing period. However, the PU arrives during the xth sample of the sensing period in , and the PU signal is then detected. Meanwhile, in and , the channel is detected as busy at the beginning of SU transmission. In , the PU departs from the channel during the sensing period, while is the hypothesis that the PU is always present during the sensing period. The transition probability of the CTOL model is given by [33]:
where , , , and are the probabilities of transition between large and small states and vice-versa.
The probabilities of the hypotheses for the CTOL model were formulated from [2,4,26] as shown in Figure 5. The Equations of (16)–(19) are reformulated from [2] which incorporates the clustered TOL; and from Equation (10). The probabilities of the hypotheses are considered as the probability of small and large idle time which can be derived as follows:
where and represent the probability of and , respectively. The SU transmission rate is derived based on the hypotheses for the improved throughput [4] and can be expressed as:
The , , and are the average SNRs that considered the random arrival and departure of PU traffic.
5.3. The Probability of Collision
The probability of the collision between the SU and the PU is observed through imperfect sensing. In a real-time environment, the sensing errors can occur in spectrum sensing. The probability of the collision between SU and PU is denoted as . The spectrum sensing results might have errors that can lead to false alarms and missed detection.
This study assumed that the sensing errors such as the probability of false alarms could occur in a channel. The SU frames might collide with the PU’s transmissions if the channel is idle with the presence of PU’s transmissions during the transmission period.
From Figure 6, the conditional probability of collisions of the CTOL model can be calculated as follows:
where is the probability of false alarms.
When the sensing period increases, the probability of detection will also increase while the probability of false alarm decreases, and it is equal to .
The probability of the collision among the SUs is denoted as , which can occur if there is at least one SU that is transmitted in the same frame. The conditional collision probability between and means that the probability for the collision of the SU packet can be seen during its transmission in a channel. The conditional probability of the collision between the SUs is given as , where is the stable transmission probability at the beginning of the idle time.
The total conditional probability collision from both the SU and the PU to a packet can be derived as follows:
The stable transmission probability is formulated from [34] as:
where and represent the minimum contention window value and the maximum back-off stage, respectively. Next, let the probability of at least, an SU transmitting during the transmission be and the probability of the interference to a PU can be derived as in [2] as:
5.4. Normalized Throughput of the SU
The normalized throughput of the SU is defined as the portion of the period that the SU uses to transmit the data successfully. The throughput of the SU is calculated based on the successful SU’s transmission, which occurs when the channel is detected as idle, and the PU does not reappear during the transmission period.
As an example, let n be the number of SUs that contend in the channel, and the probability of at least one SU’s success to transmit in the channel is as follows:
By considering the SU throughput, it is formulated as [2]:
where is the frame duration, and represents the sensing duration.
6. Results and Discussions
In this section, the CTOL model is evaluated and compared to the static PU model and dynamic PU model. The probability of collisions and the SU’s throughput in the network are investigated for all of the models. The total frame duration is set to 30 ms, the bandwidth is 5 MHz, and the sampling interval is = 0.2 μs. The detection probability, , is set to 80% to restrict the interference probability to below 20%.
Figure 7 illustrate the relationships of the SU normalized throughput with the increment of the sensing durations for all of the models. These figures show the effect of the various sensing durations on the SU throughput. The sensing duration from 0.1 ms in Figure 7a is increased to 1 ms (Figure 7b) and 10 ms (Figure 7c). It shows that the CTOL model outperforms the other models due to the increment of the sensing duration. This happens because the static model needs a longer sensing duration to satisfy the detection constraint, in which is set as 0.8. The longer sensing duration improves the sensing reliability and increasing the sensing durations degrades the SU throughput. The reason for the degradation of the throughput is due to the shorter data transmission slot in the SU frames. The longer sensing duration in the frames may, shorten the data transmission time for the SU, that causes the degradation of the throughput.
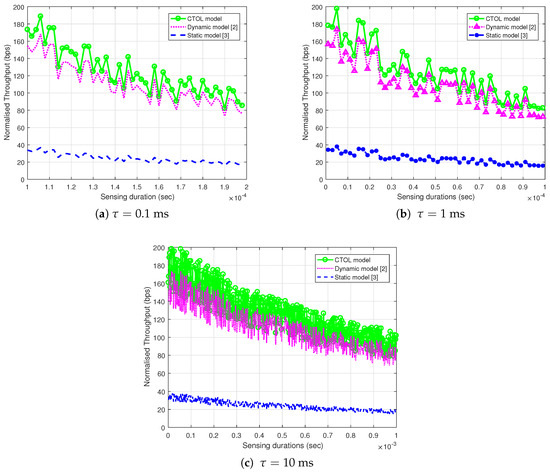
Figure 7.
The effect of sensing the duration of the normalized throughput for the secondary user when increasing the sensing time: (a) ms; (b) ms and (c) ms.
The throughput performance in the CTOL model is slightly higher by 45% and 12.2% than the other two reference models. This condition occurs because the CTOL model has analyzed the TOLs and clustered them into two separate large and small parts. Then, the SU transmitted within the two TOLs to reduce the possibility of colliding with the PU as both TOLs are idle. The fluctuation of the throughput value is caused by the random values of SU transmit power in the simulation.
In Figure 8, the probability of collisions is investigated and compared to the increasing of frame duration. Then, the CTOL model is compared with the static and dynamic models. The probability of collisions in the static model shows the highest number of collisions among the other models. The static model assumed the absence and presence of the PU in the detection process. There might be the occurrence of misdetections, which will lead to a higher collision in the channel due to the imperfect sensing. Both CTOL and dynamic models use the random arrival and departure of the PU signals. These models can detect and classify the PU signals thoroughly for every sample time in the four different scenarios.
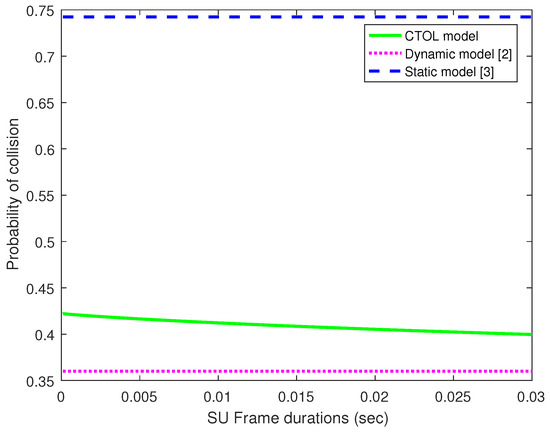
Figure 8.
The probability of collisions for the CTOL model, dynamic model, and static model.
Figure 9 shows the SU throughput in the CTOL model for the three different transmission opportunity lengths (TOLs) in the following channels: D1, D2 and D3. The SU throughput in D2 is higher than in D1 and D3, even though it has the smallest number of TOLs compared to D1. Notably, it occurs due to the value of the probability of stable transmissions , which did not only depend on the conditional probability of collisions, , and it can also be determined by the number of and . Although the numbers of TOL in D1 and D3 have a large gap, the throughput is slightly different as they have the largest contention window, .
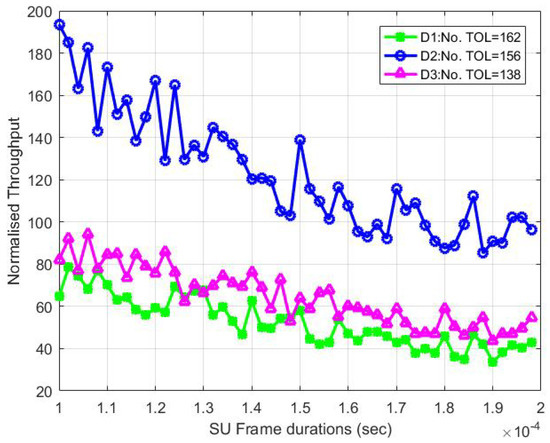
Figure 9.
The normalized throughput for the CTOL model with the different numbers of TOL.
7. Conclusions
In this paper, the access opportunity for the SU is estimated in the channel and analyzed using an experimental model that offers an accurate and realistic scenario. From the data, the CTOL model is designed to examine the spectrum hole behaviors and evaluate all of them. The CTOL model was compared between both static and dynamic models correspondingly. The proposed CTOL model improves the SU throughput by 45% and 12.2% by clustering the detected TOLs into two large and small categories. Even though the probability of collisions in the proposed CTOL model is 13.7% higher than the dynamic model, the results showed that the performance improves as the value of the probability of collision degrades and the frame duration increases. The simulation results have proven that the SU throughput in the CTOL model can perform better with fewer minimum contention windows and maximum back-off stage.
Author Contributions
All authors have made significant contributions to the paper. M.H.M. designed the CTOL conceptualization and protocol, conducted the experiments, formal analysis the results, and writing the original draft preparation. A.S. refined the protocol algorithms, edited the paper, validation and provided the funding acquisition for publication. O.T. defined the experiment set-up and validation. F.H. and R.N. contributed to the paper organization and technical writing of early versions of the manuscript. They also contributed in several rounds of critical revisions. All authors have contributed to the interpretation and discussion of the results and have read and approved the final version of the manuscript.
Funding
This research was funded by MALAYSIA MINISTRY OF HIGHER EDUCATION grant number FRGS/1/2015/TK10/UPM/02/2 and The APC was funded by Universiti Putra Malaysia.
Acknowledgments
The authors wish to acknowledge Universiti Teknikal Malaysia Melaka (UTeM), and the Ministry of Higher Education of Malaysia for funding the primary author’s PhD study. The Fundamental Research Grant Scheme (FRGS) obtained from the Malaysia Ministry of Higher Education entitled ‘On the Cogitation of Primary User Reappearance in Cognitive Radio Network’ (FRGS/1/2015/TK10/UPM/02/2) is also duly acknowledged.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zhang, J.; Zheng, F.C.; Gao, X.Q.; Zhu, H.B. Which Is Better for Opportunistic Spectrum Access: The Duration-Fixed or Duration-Variable MAC Frame? IEEE Trans. Veh. Technol. 2015, 64, 198–208. [Google Scholar] [CrossRef]
- Zhang, S.; Hafid, A.S.; Zhao, H.; Wang, S. Cross-layer aware joint design of sensing and frame durations in cognitive radio networks. IET Commun. 2016, 10, 1111–1120. [Google Scholar] [CrossRef]
- Liang, Y.C.; Zeng, Y.; Peh, E.C.; Hoang, A.T. Sensing-throughput tradeoff for cognitive radio networks. IEEE Trans. Wirel. Commun. 2008, 7, 1326–1337. [Google Scholar] [CrossRef]
- Tang, L.; Chen, Y.; Hines, E.L.; Alouini, M.S. Effect of primary user traffic on sensing-throughput tradeoff for cognitive radios. IEEE Trans. Wirel. Commun. 2011, 10, 1063–1068. [Google Scholar] [CrossRef]
- Lopez-Benitez, M.; Casadevall, F. Spectrum usage in cognitive radio networks: From field measurements to empirical models. IEICE Trans. Commun. 2014, 97, 242–250. [Google Scholar]
- Sibomana, L.; Zepernick, H.J.; Tran, H.; Ngoga, S.R. Packet Transmission for Multiservice Cognitive Radio Networks with Finite Buffer Capacity. In Proceedings of the 2013 19th European in Wireless Conference (EW), VDE, Guildford, UK, 16–18 April 2013; pp. 1–6. [Google Scholar]
- Jiang, C.; Chen, Y.; Liu, K.R.; Ren, Y. Renewal-theoretical dynamic spectrum access in cognitive radio network with unknown primary behavior. IEEE J. Sel. Areas Commun. 2013, 31, 406–416. [Google Scholar] [CrossRef]
- Ali, A.; Piran, M.J.; Kim, H.; Yun, J.; Suh, D.Y. PAD-MAC: Primary User Activity-Aware Distributed MAC for Multi-Channel Cognitive Radio Networks. Sensors 2015, 15, 7658–7690. [Google Scholar] [CrossRef]
- Gabran, W.; Liu, C.H.; Pawelczak, P.; Cabric, D. Primary user traffic estimation for dynamic spectrum access. IEEE J. Sel. Areas Commun. 2013, 31, 544–558. [Google Scholar] [CrossRef]
- Geirhofer, S.; Tong, L.; Sadler, B.M. Cognitive radios for dynamic spectrum access-dynamic spectrum access in the time domain: Modeling and exploiting white space. IEEE Commun. Mag. 2007, 45, 66–72. [Google Scholar] [CrossRef]
- Geirhofer, S.; Tong, L.; Sadler, B.M. Dynamic spectrum access in WLAN channels: Empirical model and its stochastic analysis. In Proceedings of the First International Workshop on Technology and Policy for Accessing Spectrum, Boston, MA, USA, 5 August 2006; p. 14. [Google Scholar]
- Stabellini, L. Quantifying and modeling spectrum opportunities in a real wireless environment. In Proceedings of the Wireless Communications and Networking Conference (WCNC), Sydney, Australia, 18–21 April 2010; pp. 1–6. [Google Scholar]
- Saleem, Y.; Rehmani, M.H. Primary radio user activity models for cognitive radio networks: A survey. J. Netw. Comput. Appl. 2013, 43, 1–16. [Google Scholar] [CrossRef]
- Lopez-Benitez, M.; Casadevall, F. Empirical time-dimension model of spectrum use based on a discrete-time Markov chain with deterministic and stochastic duty models. IEEE Trans. Veh. Technol. 2011, 60, 2519–2533. [Google Scholar] [CrossRef]
- Shi, Z.; Teh, K.C.; Li, K.H. Energy-efficient joint design of sensing and transmission durations for protection of primary user in cognitive radio systems. IEEE Commun. Lett. 2013, 17, 565–568. [Google Scholar] [CrossRef]
- Zhang, F.; Jing, T.; Huo, Y.; Ma, L. Optimal Spectrum Sensing-Access Policy in Energy Harvesting Cognitive Radio Sensor Networks. Procedia Comput. Sci. 2018, 129, 194–200. [Google Scholar] [CrossRef]
- Chang, Z.; Ristaniemi, T.; Han, Z. Queueing game for spectrum access in cognitive radio networks. IEEE Commun. Lett. 2015, 19, 2017–2020. [Google Scholar] [CrossRef]
- Rawat, D.B.; Shetty, S.; Raza, K. Game theoretic dynamic spectrum access in cloud-based cognitive radio networks. In Proceedings of the 2014 IEEE International Conference on Cloud Engineering (IC2E), Boston, MA, USA, 11–14 March 2014; pp. 586–591. [Google Scholar]
- El-Sherif, A.A.; Kwasinki, A.; Sadek, A.K.; Liu, K.R. Content-aware multiple access protocol for cooperative packet speech communications. IEEE Trans. Wirel. Commun. 2009, 8, 995–1005. [Google Scholar] [CrossRef]
- Li, D.; Youyun, X.; Xinbing, W.; Guizani, M. Coalitional Game Theoretic Approach for Secondary Spectrum Access in Cooperative Cognitive Radio Networks. IEEE Trans. Wirel. Commun. 2011, 10, 844–856. [Google Scholar] [CrossRef]
- Saad, W.; Han, Z.; Zheng, R.; Hjørungnes, A.; Basar, T.; Poor, H.V. Coalitional games in partition form for joint spectrum sensing and access in cognitive radio networks. IEEE J. Sel. Top. Signal Process. 2012, 6, 195–209. [Google Scholar] [CrossRef]
- Jiang, C.; Chen, Y.; Gao, Y.; Liu, K.R. Joint spectrum sensing and access evolutionary game in cognitive radio networks. IEEE Trans. Wirel. Commun. 2013, 12, 2470–2483. [Google Scholar] [CrossRef]
- Al-Mqdashi, A.; Sali, A.; Abdel-Rahman, M.J.; Noordin, N.K.; Hashim, S.J.; Nordin, R. Efficient rendezvous schemes for fast-varying cognitive radio ad hoc networks. Trans. Emerg. Telecommun. Technol. 2017, 28, e3217. [Google Scholar] [CrossRef]
- Abdel-Rahman, M.J.; Rahbari, H.; Krunz, M. Multicast rendezvous in fast-varying DSA networks. IEEE Trans. Mob. Comput. 2015, 14, 1449–1462. [Google Scholar] [CrossRef]
- Liang, Y.C.; Zeng, Y.; Hoang, A.T. Sensing-Throughput Tradeoff for Cognitive Radio Networks. IEEE Trans. Wirel. Commun. 2008, 7, 326–1337. [Google Scholar]
- Kalamkar, S.S.; Banerjee, A. On the effect of primary user traffic on secondary throughput and outage probability under Rayleigh flat fading channel. In Proceedings of the International Conference Signal Process and Communication, SPCOM 2014, Bangalore, India, 15 December 2014; pp. 1–6. [Google Scholar]
- Soltanmohammadi, E.; Orooji, M.; Naraghi-Pour, M. Improving the Sensing–Throughput Tradeoff for Cognitive Radios in Rayleigh Fading Channels. IEEE Trans. Veh. Technol. 2013, 62, 2118–2130. [Google Scholar] [CrossRef]
- Sharkasi, Y.F.; McLernon, D.C.; Ghogho, M.; Zaidi, S.A.R. On spectrum sensing, secondary and primary throughput, under outage constraint with noise uncertainty and flat fading. In Proceedings of the 2013 IEEE 24th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), London, UK, 8–11 September 2013; pp. 927–931. [Google Scholar]
- Trivedi, U.B.; Dalal, U.D. Energy Detection Based Sensing and Primary User Traffic Classification for Cognitive Radio. World Acad. Sci. Eng. Technol. Int. J. Electr. Comput. Energy Electron. Commun. Eng. 2016, 2016, 749–754. [Google Scholar]
- Wang, J.W.; Adriman, R. Analysis of Opportunistic Spectrum Access in Cognitive Radio Networks using Hidden Markov Model with State Prediction. EURASIP J. Wirel. Commun. Netw. 2015, 2015, 10. [Google Scholar] [CrossRef]
- Weidling, F.; Datla, D.; Petty, V.; Krishnan, P.; Minden, G.J. A framework for RF spectrum measurements and analysis. In Proceedings of the First IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN 2005), Baltimore, MD, USA, 8–11 November 2005; pp. 573–576. [Google Scholar]
- Press, W.H.; Teukolsky, S.A.; Vetterling, W.T.; Flannery, B.P. Numerical Recipes: The Art of Scientific Computing, 3rd ed.; Cambridge University Press: Cambridge, UK, 2007. [Google Scholar]
- Papoulis, A.; Pillai, S.U. Probability, Random Variables, and Stochastic Processes, 4th ed.; McGraw- Hill, Inc.: Boston, MA, USA, 2002. [Google Scholar]
- Bianchi, G. Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar] [CrossRef]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).