Public Key-Based Authentication and En-Route Filtering Scheme in Wireless Sensor Networks
Abstract
:1. Introduction
2. Related Works
3. System and Threat Models
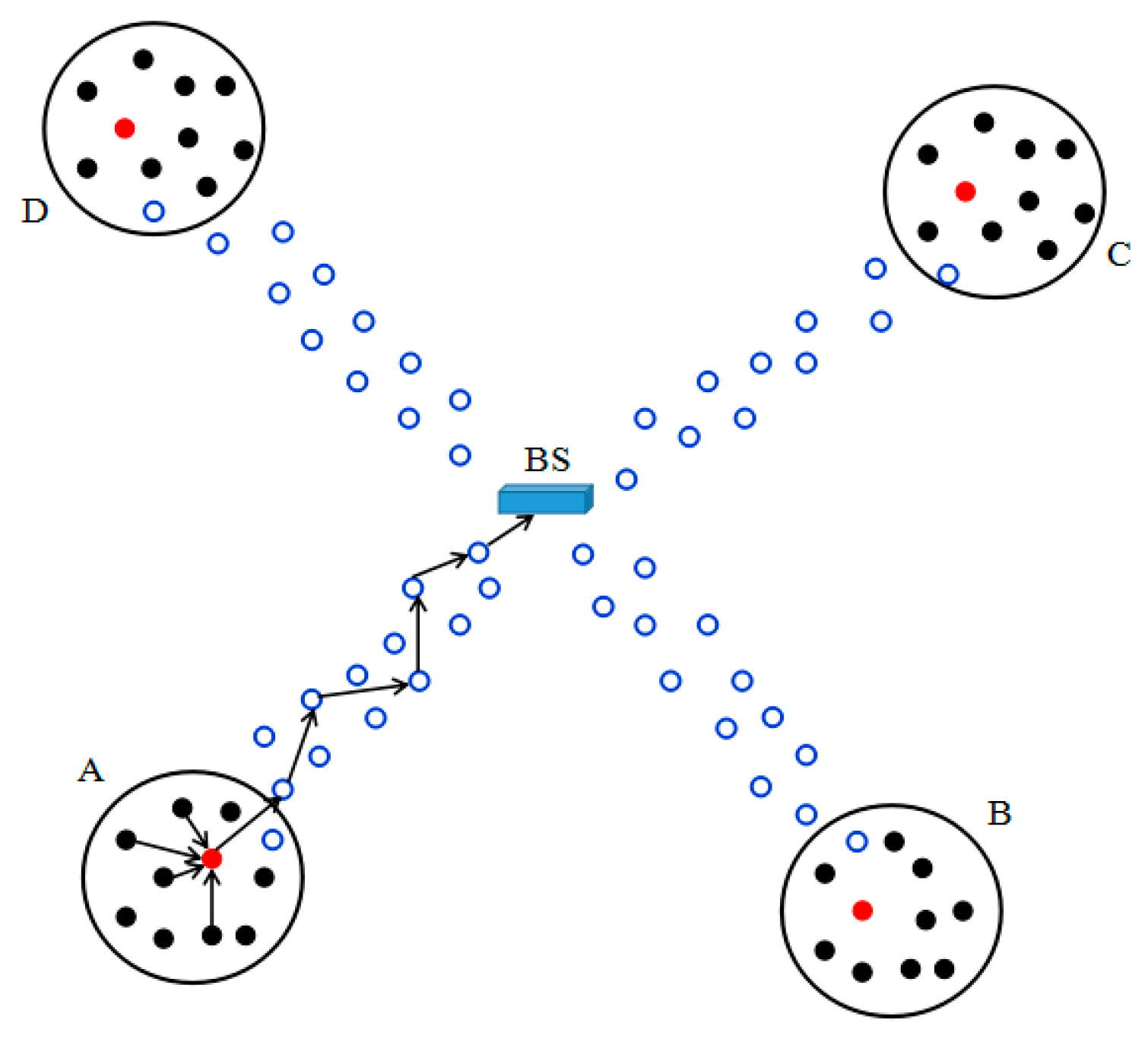
3.1. System Model
3.2. Threat Models
- False report injection attack [5]. The adversary might control the compromised nodes to inject forged event reports, which might cause false alarms as well as the exhaustion of the constrained resources of the network.
- Report disruption attack [6]. The compromised sensor node might contribute invalid endorsement to the event report. As a result, the report of a real event will be dropped by some forwarding node or the BS. Additionally, the compromised sensor node might refuse to participate in report generation, thus the CH cannot collect enough legitimate endorsements for the event report. Furthermore, if a CH node is compromised, it might refuse to send out the signed event report or send out an event report with an illegitimate signature, resulting in the real event not being reported to the BS.
- Selective forwarding attack [6]. The compromised forwarding node might selectively drop the legitimate reports, which will severely damage data availability and disrupt the event report service.
4. The Proposed Scheme
4.1. Scheme Overview
4.1.1. Design of Mechanism for Filtering False Report
4.1.2. Design of Mechanism for Resisting Report Disruption Attacks
4.1.3. Design of Mechanism for Resisting Selective Forwarding Attacks
4.1.4. Design of Mechanism for Malicious Nodes Detection and Isolation
- During the report generation phase, if a participating node vj refuses to provide kjP or a partial signature, or provides an incorrect partial signature, then each cluster node will deduct 0.2 from TVj, and vj will be substituted.
- During the report generation phase, if the CH node vi refuses to broadcast X(R), or maliciously accuses any participating node of not providing kjP or a partial signature, or providing an incorrect partial signature, or vi refuses to send out the signed report, or sends out a report with an incorrect cluster signature, then each cluster node will deduct 0.2 from TVi, and a new CH node will be selected to regenerate a signed event report.
- If a forwarding node vt detects a false report sent by vk, then vt will deduct 0.1 from TVk.
- If a forwarding node vt maliciously refuses to forward the report from vk, then vk will deduct 0.1 from TVt.
- If a cluster node vk transmits a forged report with an incorrect cluster signature to the forwarding node vt, then vt and each cluster node will deduct 0.1 from TVk.
4.2. Deployment and Initialization
4.3. Report Generation
- ①
- Compute σjP (i.e., σjP = (xjljd + kj)P = xjljdP + kjP);
- ②
- Compute xjljdP + kjP by using xjP stored locally and kjP received from vIDj in Step 1;
- ③
- Compare the results in ① and ②. When the result in ① is equal to that in ②, σj is considered to be correct, otherwise σj is considered to be incorrect.
| Algorithm 1. Processing of SUBMSG Message |
| /*Upon a cluster node vx receiving a SUBMSG message from the CH node vIDi*/ flg = false; // flg records whether the accusation in the SUBMSG message is true. if (rcd = 0) if (the z nodes to be substituted did not send their kjP to vIDi) flg = true; else if (rcd = 1) if (the z nodes to be substituted did not provide their σj or provided incorrect σj) flg = true; if (flg = false) Perform Algorithm 3 to substitute vIDi; else { for (each node vIDm to be substituted) { TVIDm = TVIDm − 0.2; if (TVIDm < TTv && NAIDm < Nc/2) { Broadcast an ALARM message for vIDm; vx, and each cluster node that hears the ALARM message, executes Algorithm 2; } }//end for if (the number of trusted non-participating cluster nodes < z) { Fail_flag = true; // Report generation fails. Cancel the timer TRG; } else { Select the z trusted non-participating cluster nodes, whose IDs are closer to hv than the others, to participate in report generation; if (vx is a new participating node) { Pick kx in [1, q − 1] and send kxP to vIDi; Compute σx after receiving X(R); Send σx to vIDi; } else if (vx is a participating node that has not been substituted) { Recompute σx after receiving X(R); Send σx to vIDi; } } } |
| Algorithm 2. Processing of ALARM Message |
| /*Upon a cluster node vx receiving an ALARM message for vy broadcast by node vz*/ if (it is the first ALARM message sent by vz for vy) NAy = NAy + 1; if (NAy ≥ Nc/2) { Delete vy from the trusted neighbor list; Add vy into the isolation list; } |
4.4. Report Forwarding and En-Route Filtering
| Algorithm 3. Substitution of Cluster Head |
| /*Substitution of the cluster head vIDi on a cluster node vx*/ TVIDi = TVIDi − 0.2; if (TVIDi < TTv && NAIDi < Nc/2) { Broadcast an ALARM message for vIDi; vx, and each cluster node that hears the ALARM message, executes Algorithm 2; } Reset the timer TRG; Select the trusted non-participating cluster node, whose ID is closer to hv than the others (vt for example), to substitute vIDi; Select the current participating node whose ID is closest to hv (vm for example) as the new CH; if (vx is exactly vm) { if (vt does not provide ktP) Perform the proposed substitution scheme in Step 5; else {// vx has stored the kjP of the other participating nodes when they sent kjP to vIDi. Compute R and broadcast X(R); Receive and verify each new σj; if (some current participating nodes do not provide their new σj or provide incorrect σj) Perform the proposed substitution scheme in Step 5; } } else if (vx is exactly vt) { Pick kx in [1, q − 1] and send kxP to vm; Compute σx after receiving X(R) from vm; Send σx to vm; } else if (vx is a participating node that has not been substituted) { Recompute σx after receiving X(R) from vm; Send σx to vm; } |
- S1.
- Check if vt has stored the pubic key QCID of cluster CID; otherwise, drop the report and go to S5.
- S2.
- Check the freshness of the report with the help of te in the report; otherwise, drop the report and go to S5.
- S3.
- When vt is a neighbor of the CH node vIDch, vt verifies the legitimacy of vIDch’s location LIDch stored locally by checking that d(Le, LIDch) ≤ Rs. Otherwise, vt drops the report and goes to S5.
- S4.
- Compute d = H(e||V), R = σP − dQCID, and C = ENC−1(X(R), e), where ENC−1 denotes a decryption operation. Then, check that the {IDch, Le} abstracted from C are the same as those in the report; otherwise, drop the report and go to S5.
- S5.
- When the report is dropped, vt deducts 0.1 from TVk. When TVk falls below TTv, vt deletes vk from the trusted neighbor list and adds it into the isolation list.
- S6.
- When the report passes all the above checks, vt sends the report to the next hop by using the proposed forwarding routing protocol.
4.5. Report Verification on the Base Station
- First, it checks the freshness of the report with the help of te.
- Next, it checks that d (Le, LIDch) ≤ Rs, where LIDch is the location of vIDch stored in the BS.
- It then verifies the cluster signature in the report using the pubic key QCID of cluster CID. It first computes d = H(e||V), R = σP − dQCID, and C = ENC−1(X(R), e), then checks that the {IDch, Le} abstracted from C are the same as those in the report.
5. Performance Analysis
5.1. Security Analysis
5.2. Overhead Analysis
5.2.1. Communication Overhead
5.2.2. Storage Overhead
6. Performance Evaluation
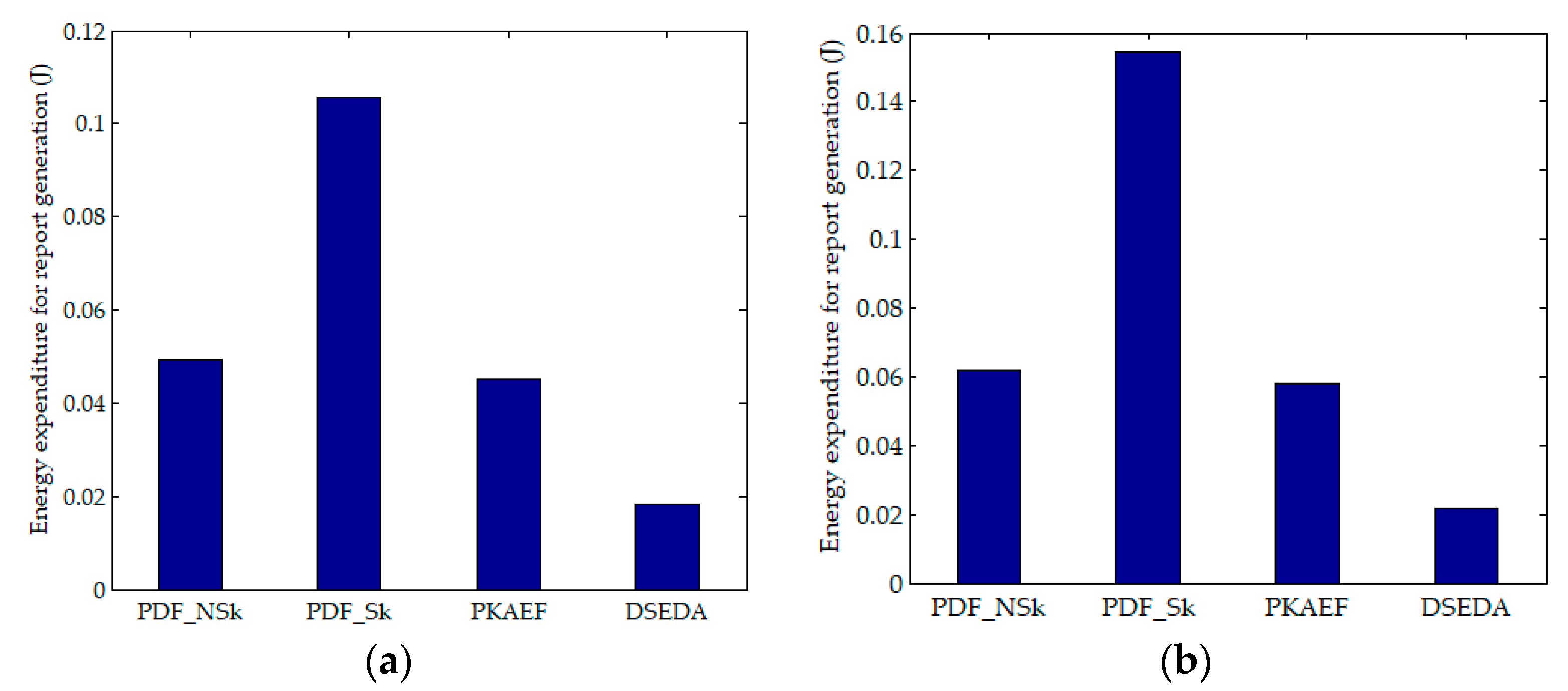
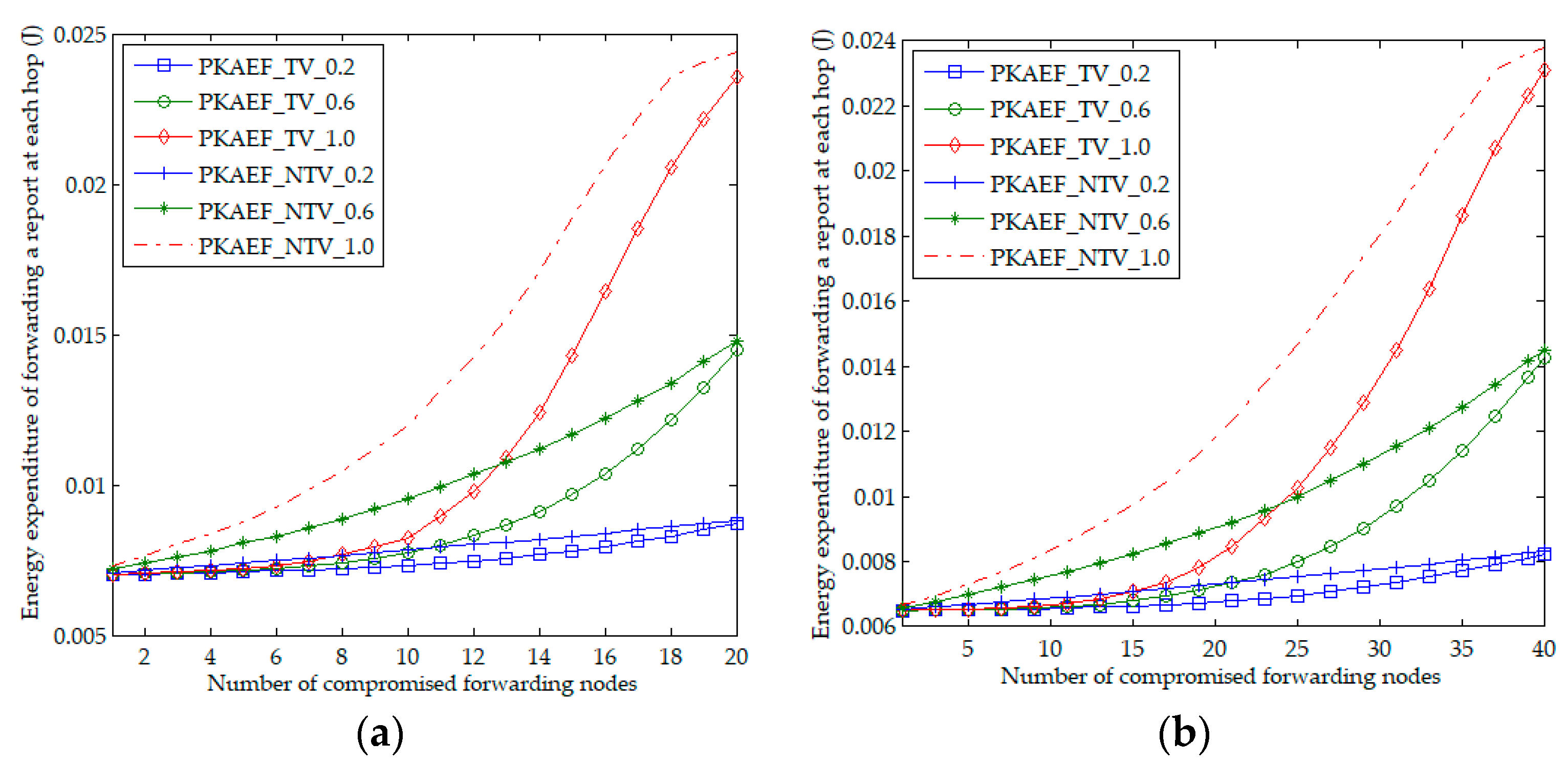
6.1. Energy Expenditure for Report Generation
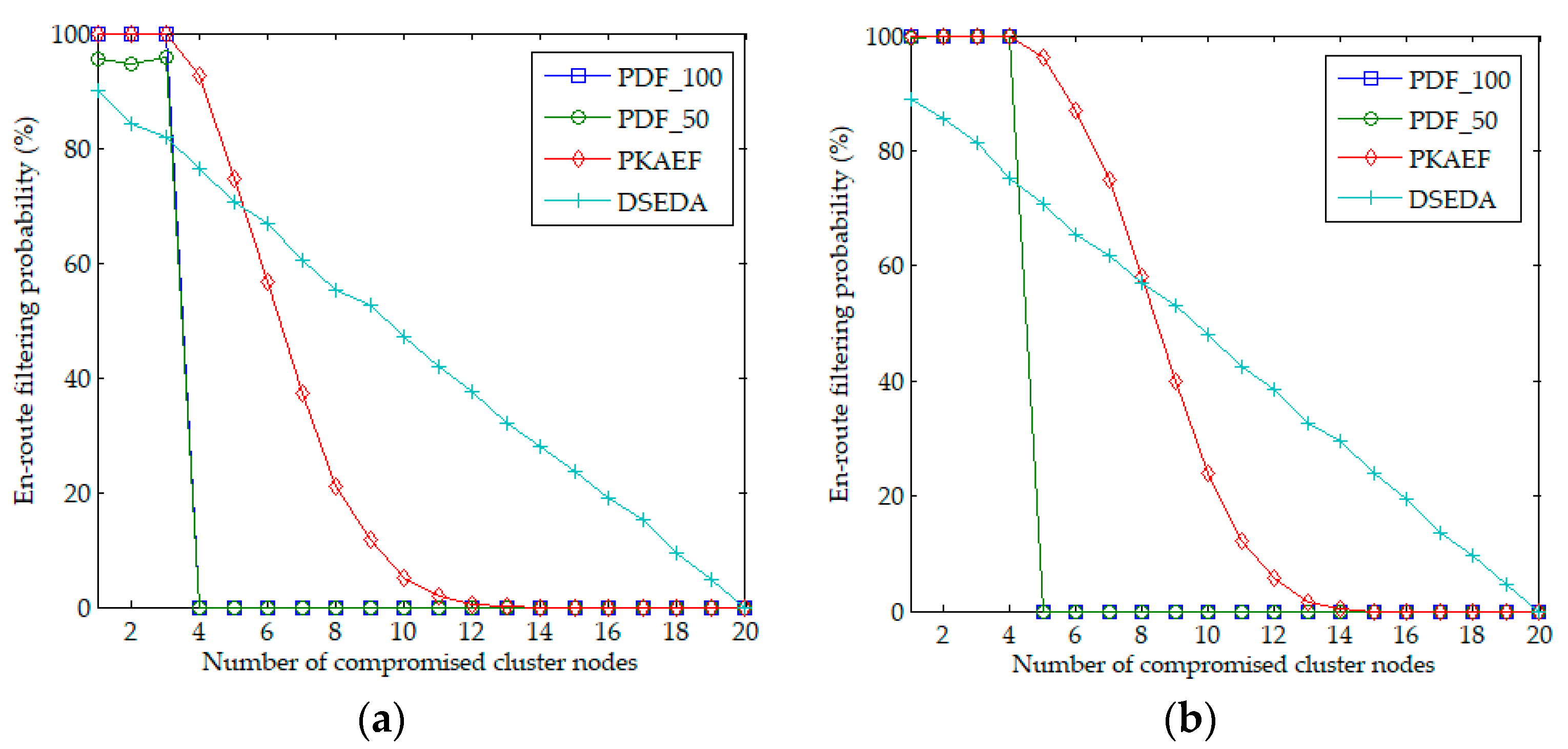
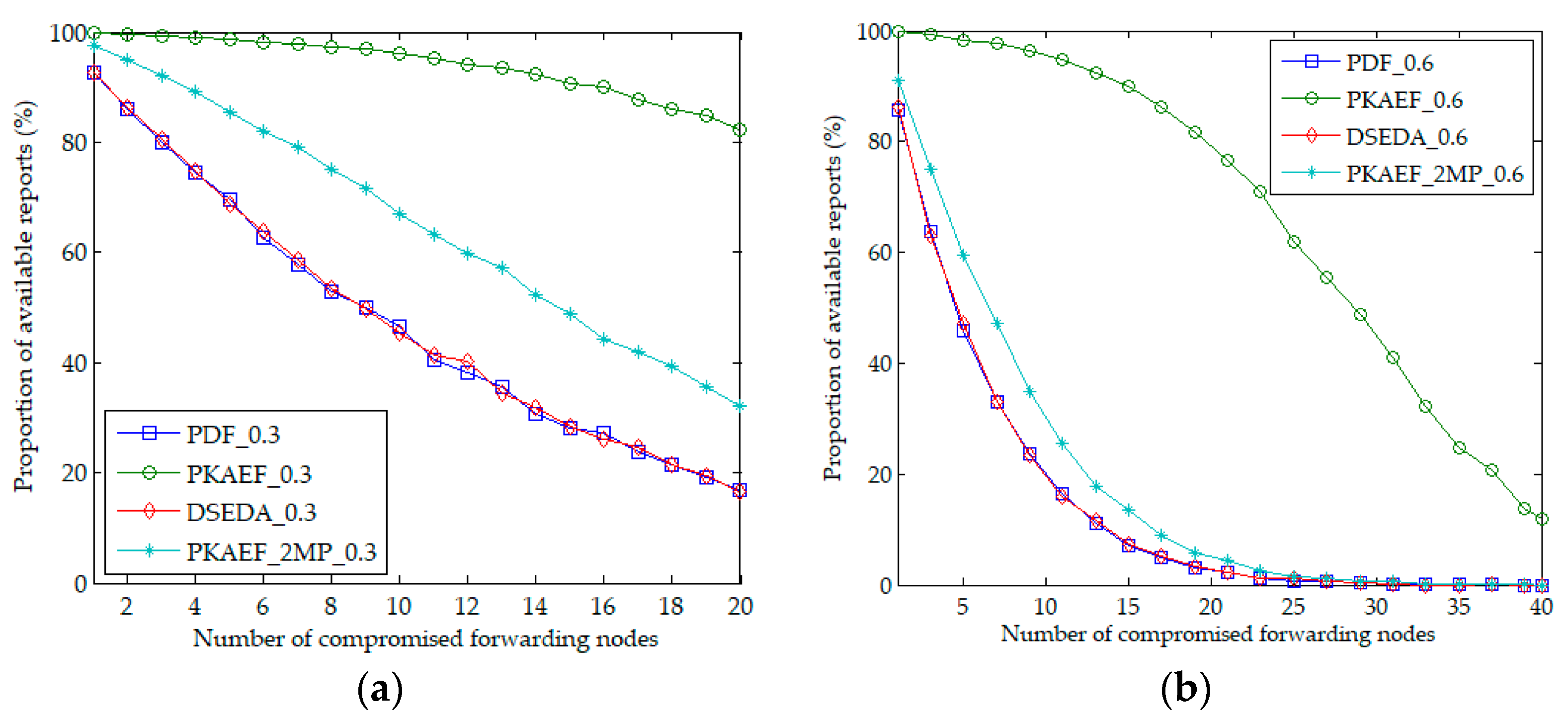
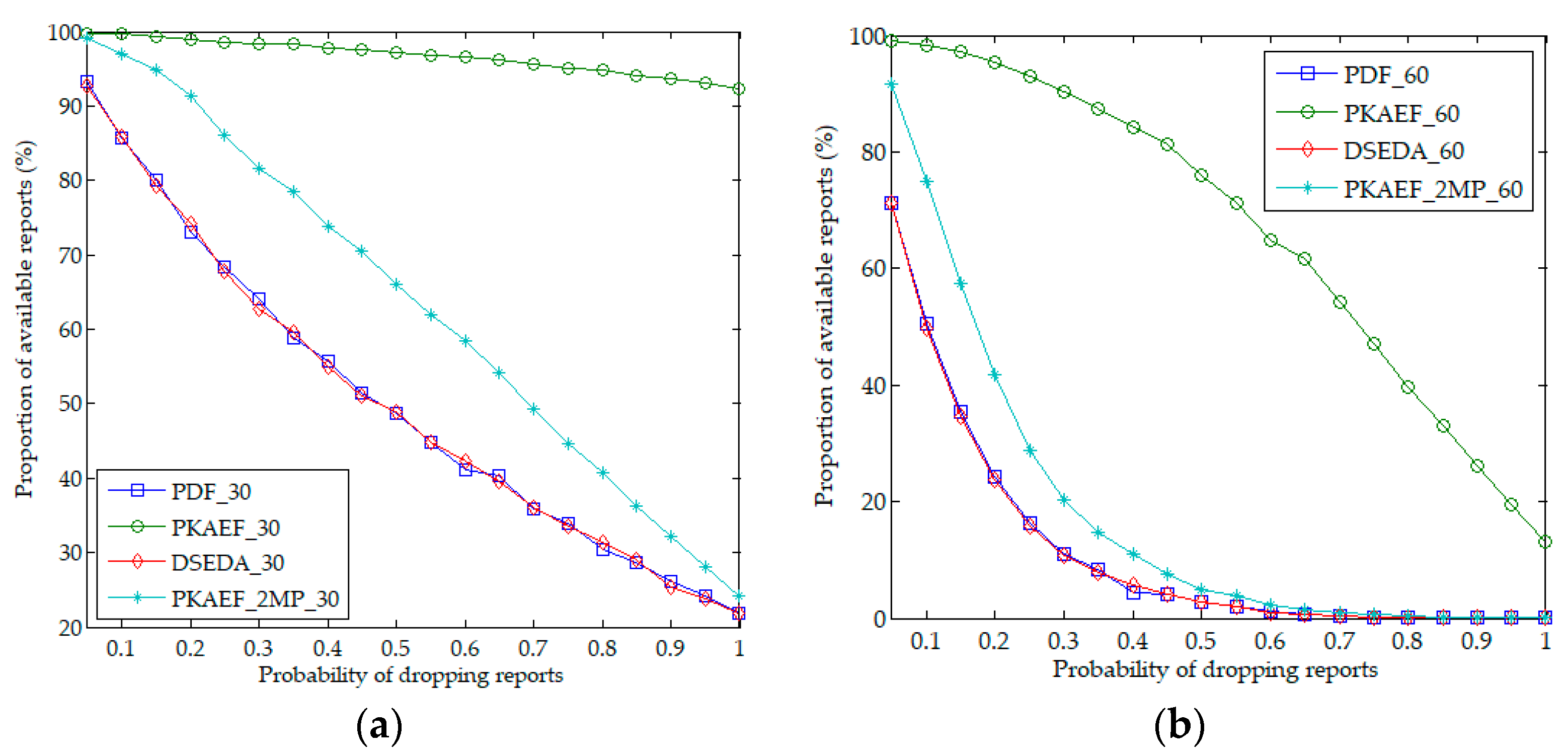
6.2. Performance of False Report Filtering
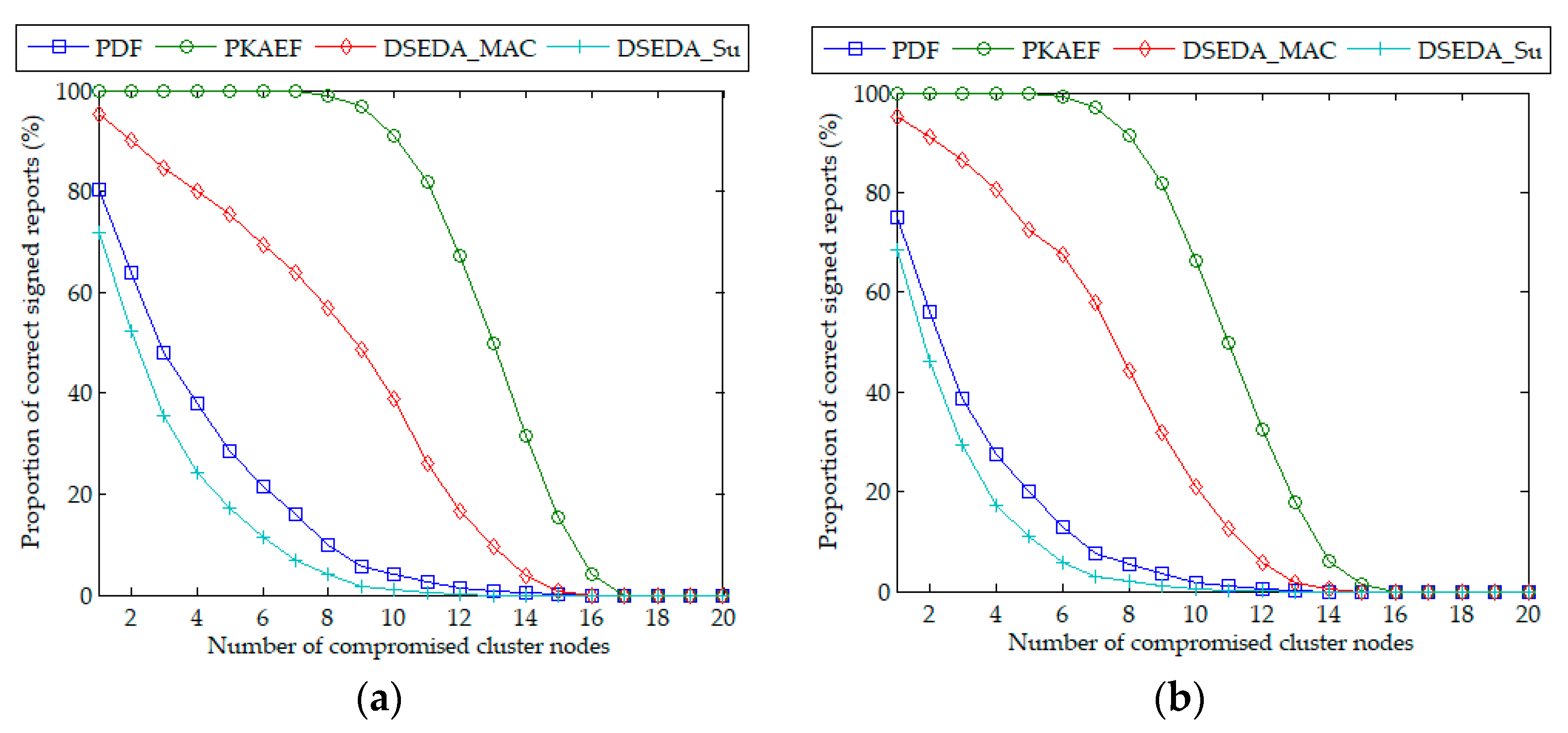
6.3. Resilience to Report Disruption Attacks
6.4. Resilience to Selective Forwarding Attacks
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ferng, H.W.; Khoa, N.M. On security of wireless sensor networks: A data authentication protocol using digital signature. Wirel. Netw. 2017, 23, 1–19. [Google Scholar] [CrossRef]
- Zhou, Q.; Yang, G.; He, L. An efficient secure data aggregation based on homomorphic primitives in wireless sensor networks. IJDSN 2014, 7, 1–11. [Google Scholar] [CrossRef]
- Castiglione, A.; D’Arco, P.; Santis, A.D.; Russo, R. Secure group communication schemes for dynamic heterogeneous distributed computing. Future Gener. Comput. Syst. 2017, 74, 313–324. [Google Scholar] [CrossRef]
- Jan, M.; Nanda, P.; Usman, M.; He, X.J. PAWN: A payload-based mutual authentication scheme for wireless sensor networks. Concurr. Comput. Pract. Exp. 2017, 29, 1–10. [Google Scholar] [CrossRef]
- Jeba, S.V.A.; Paramasivan, B. Energy efficient multipath data transfer scheme to mitigate false data injection attack in wireless sensor networks. Comput. Electr. Eng. 2013, 39, 1867–1879. [Google Scholar] [CrossRef]
- Yu, H.; He, J. Authentication and en-route data filtering for wireless sensor networks in the internet of things scenario. Int. J. Grid Distrib. Comput. 2013, 6, 1–12. [Google Scholar]
- Zhang, Y.; Liu, W.; Lou, W.; Fang, Y. Location-based compromise-tolerant security mechanisms for wireless sensor networks. IEEE J. Sel. Area Commun. 2006, 24, 247–260. [Google Scholar] [CrossRef]
- Yang, X.; Lin, J.; Moulema, P.; Yu, W.; Fu, X.; Zhao, W. A novel en-route filtering scheme against false data injection attacks in cyber-physical networked systems. In Proceedings of the 2012 IEEE 32nd International Conference on Distributed Computing Systems, Macau, China, 18–21 June 2012; pp. 92–101. [Google Scholar]
- Li, J.; Yu, L.; Gao, H.; Xiong, S. Grouping-enhanced resilient probabilistic en-route filtering of injected false data in WSNs. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 881–889. [Google Scholar]
- Wang, J.; Liu, Z.; Zhang, S.; Zhang, X. Defending collaborative false data injection attacks in wireless sensor networks. Inf. Sci. 2014, 254, 39–53. [Google Scholar] [CrossRef]
- Ren, K.; Lou, W.; Zhang, Y. LEDS: Providing location-aware end-to-end data security in wireless sensor networks. IEEE Trans. Mob. Comput. 2008, 7, 585–598. [Google Scholar] [CrossRef]
- Yi, C.; Yang, G.; Dai, H.; Liu, L.; Chen, Y. Efficient geographical information-based en-route filtering scheme in wireless sensor networks. KSII Trans. Internet Inf. Syst. 2018, 12, 4183–4204. [Google Scholar] [CrossRef]
- Su, M.N.; Cho, T.H. Context-aware architecture for probabilistic voting-based filtering scheme in sensor networks. IEEE Trans. Mob. Comput. 2017, 16, 2751–2763. [Google Scholar]
- Duan, M.J.; Xu, J. An efficient location-based compromise-tolerant key management scheme for sensor networks. Inf. Process. Lett. 2011, 111, 503–507. [Google Scholar] [CrossRef]
- Malan, D.J.; Welsh, M.; Smith, M.D. A public-key infrastructure for key distribution in tinyos based on elliptic curve cryptography. In Proceedings of the SECON 2004, Santa Clara, CA, USA, 4–7 October 2004; pp. 71–80. [Google Scholar]
- Gura, N.; Patel, A.; Wander, A.; Eberle, H.; Shantz, S.C. Comparing elliptic curve cryptography and RSA on 8-bit CPUs. Cryptogr. Hardw. Embed. Syst. 2004, 3156, 119–132. [Google Scholar]
- Geedhabhanu, S.; Latha, P. Excluding compromised node by tracing false data injected messages in wireless sensor network. In Proceedings of the ICIICT 2015, Chennai, India, 19–20 February 2015; pp. 1–5. [Google Scholar]
- Shahzad, M.K.; Cho, T.H. An energy-aware routing and filtering node (ERF) selection in CCEF to extend network lifetime in WSN. IETE J. Res. 2017, 63, 368–370. [Google Scholar] [CrossRef]
- Wang, H.; Li, Q. Achieving robust message authentication in sensor networks: A public-key based approach. Wirel. Netw. 2010, 16, 999–1009. [Google Scholar] [CrossRef]
- Anudeep, C.; Das, M.L. An improved scheme for false data filtering in wireless sensor networks. In Proceedings of the ICDCIT 2012, Bhubaneswar, India, 2–4 February 2012; pp. 62–70. [Google Scholar]
- Pintsov, L.A.; Vanstone, S.A. Postal revenue collection in the digital age. In Proceedings of the FC 2000, Anguilla, British West Indies, 20–24 February 2000; pp. 105–120. [Google Scholar]
- Certicom. Code and cipher. Certicom’s Bull. Secur. Cryptogr. 2004, 1, 1–5. [Google Scholar]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Wang, Z.; Zhang, H.; Lu, T.; Gulliver, T.A. A grid-based localization algorithm for wireless sensor networks using connectivity and RSS rank. IEEE Access 2018, 6, 8426–8439. [Google Scholar] [CrossRef]
- Fang, X.; Jiang, Z.; Nan, L.; Chen, L. Noise-aware localization algorithms for wireless sensor networks based on multidimensional scaling and adaptive Kalman filtering. Comput. Commun. 2017, 101, 57–68. [Google Scholar] [CrossRef]
- Pecori, R. A comparison analysis of trust-adaptive approaches to deliver signed public keys in P2P systems. In Proceedings of the NTMS 2015, Paris, France, 27–29 July 2015; pp. 1–5. [Google Scholar]
- Abirami, E.; Padmavathy, T. Proficient key management scheme for multicast groups using group key agreement and broadcast encryption. In Proceedings of the ICICES 2017, Chennai, India, 23–24 February 2017; pp. 1–5. [Google Scholar]

| Security Performance | PKAEF | DSEDA | |
|---|---|---|---|
| Security of private key | High | Moderate | Low |
| Resilience to false report injection attacks | High | Moderate | Low |
| Resilience to report disruption attacks launched by a non-cluster head (CH) node | High | Poor | Low |
| Resilience to report disruption attacks launched by a CH node | High | Poor | Poor |
| Resilience to selective forwarding attacks | High | Poor | Poor |
| Malicious nodes detection and isolation | Yes | No | No |
| Overhead | PKAEF | DSEDA | |
|---|---|---|---|
| Communication overhead for report generation | ** | *** | * |
| Communication overhead for forwarding a report | * | * | ** |
| Key storage overhead | *** | **/**** | * |
| Parameter | In Scenario 1 | In Scenario 2 |
|---|---|---|
| Communication range Rc | 80 m | 80 m |
| Sensing range Rs | 40 m | 40 m |
| T in DSEDA | 5 | 6 |
| t | 4 | 5 |
| Power consumption of transmitting 1 byte | 16.25 uJ | 16.25 uJ |
| Power consumption of receiving 1 byte | 12.5 uJ | 12.5 uJ |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yi, C.; Yang, G.; Dai, H.; Liu, L.; Li, N. Public Key-Based Authentication and En-Route Filtering Scheme in Wireless Sensor Networks. Sensors 2018, 18, 3829. https://doi.org/10.3390/s18113829
Yi C, Yang G, Dai H, Liu L, Li N. Public Key-Based Authentication and En-Route Filtering Scheme in Wireless Sensor Networks. Sensors. 2018; 18(11):3829. https://doi.org/10.3390/s18113829
Chicago/Turabian StyleYi, Chuanjun, Geng Yang, Hua Dai, Liang Liu, and Ning Li. 2018. "Public Key-Based Authentication and En-Route Filtering Scheme in Wireless Sensor Networks" Sensors 18, no. 11: 3829. https://doi.org/10.3390/s18113829
APA StyleYi, C., Yang, G., Dai, H., Liu, L., & Li, N. (2018). Public Key-Based Authentication and En-Route Filtering Scheme in Wireless Sensor Networks. Sensors, 18(11), 3829. https://doi.org/10.3390/s18113829





