eTPM: A Trusted Cloud Platform Enclave TPM Scheme Based on Intel SGX Technology
Abstract
1. Introduction
2. Related Work
3. Enclave TPM Scheme
3.1. Architecture
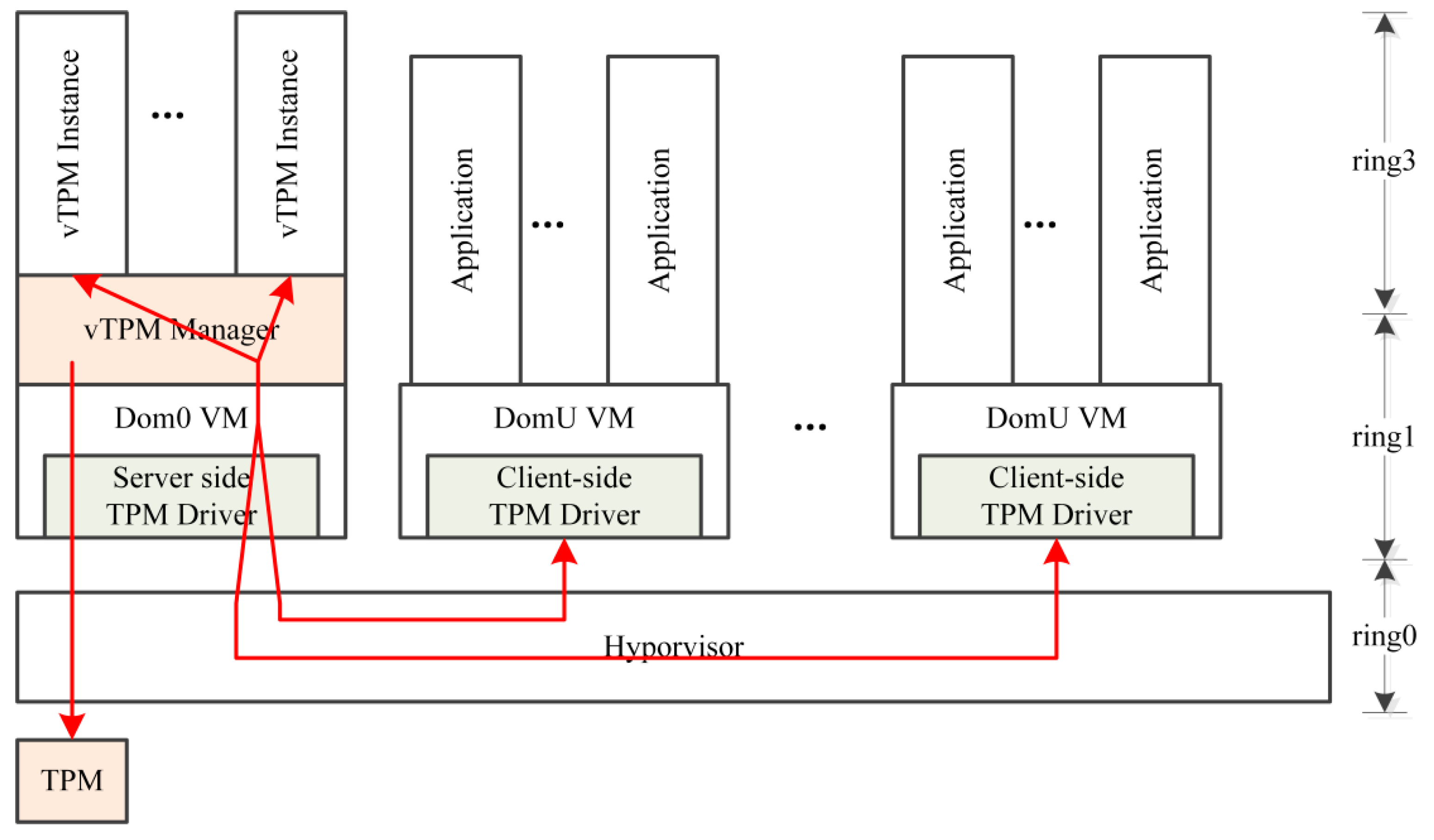
3.1.1. Enclave TPM Introduction
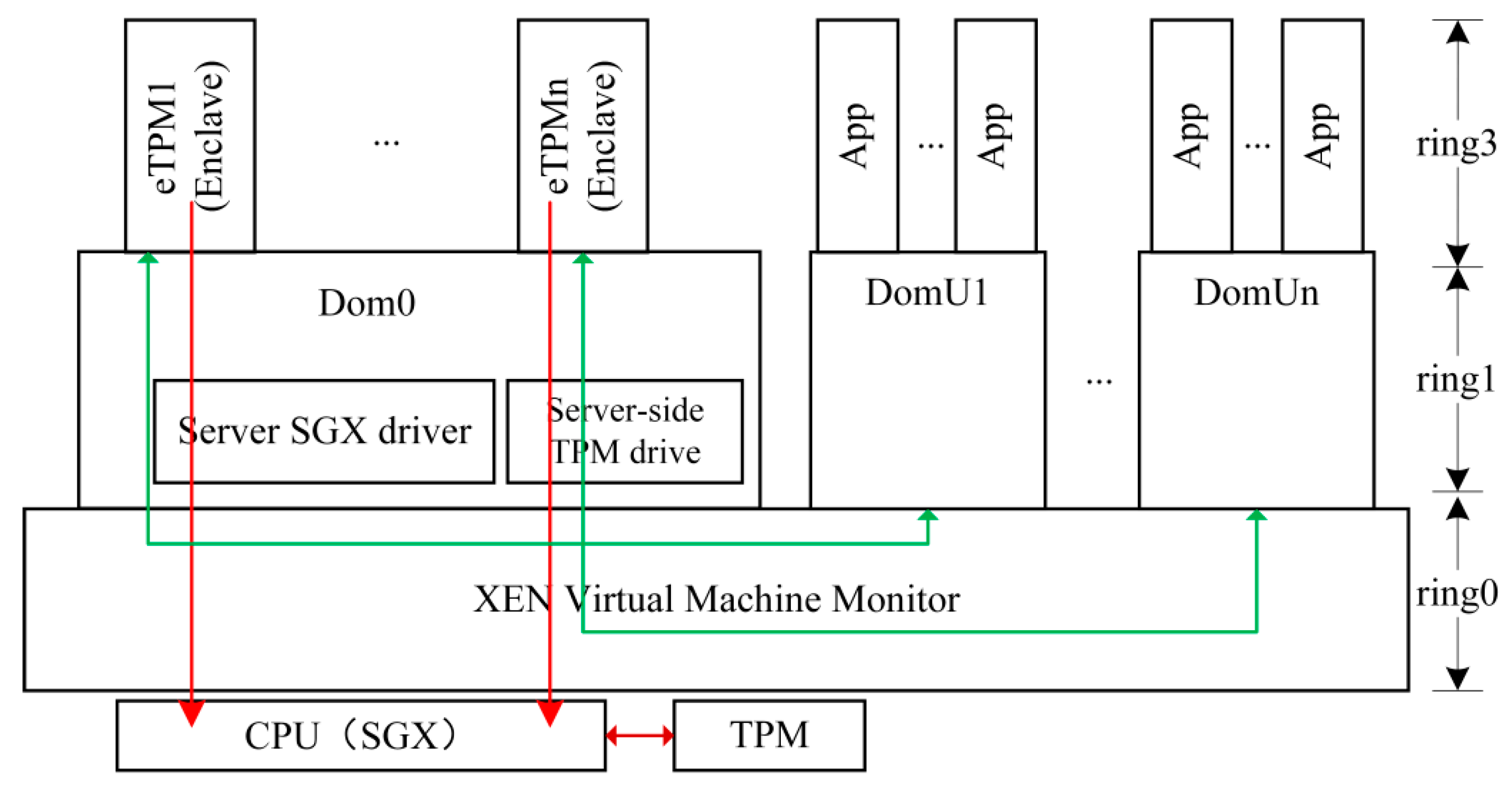
3.1.2. Enclave TPM Scheme Architecture
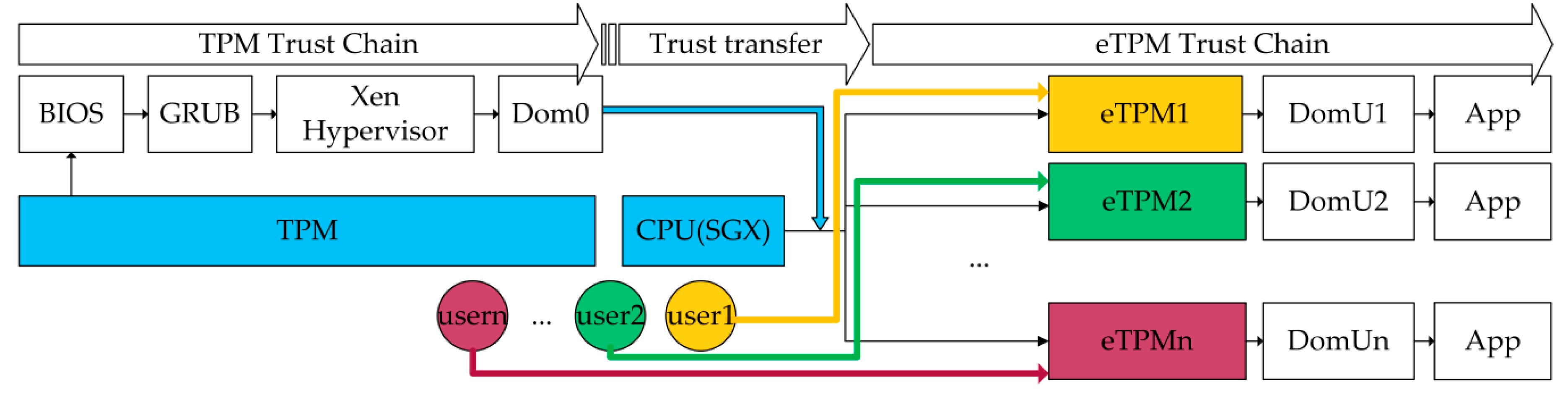
3.2. Trust Chains
- (1)
- TPM measures the components of the underlying platform and constructs the underlying platform trust chain step by step according to the order of TPM→CRTM/BIOS→GRUB→XEN Hypervisor→Dom0.
- (2)
- The eTPM runs above Dom0 and constructs the upper-level trust chain in the order of eTPM→DomU→App. For the eTPM, the Trusted Computing Base (TCB) only contains the CPU and the eTPM itself, and the CPU will measure and verify the integrity of the eTPM during its initialization. The eTPM protected by the SGX may be considered as security at runtime. The system architecture consists of two roots of trust, TPM and eTPM, which constitutes to the platform’s underlying trust chain and platform’s upper-level trust chain respectively. In order to transfer trust from underlying platform to up-level platform, the eTPM internal verification module verifies the measurement result of the TPM trust chain and feeds back the verification result only to the VM. This method also avoids the problem of leakage of underlying platform privacy caused by users’ acquisition of underlying platform measurement data.
- (3)
- Each user can configure and extend eTPM instance and control the VMs according to their security requirements. And eTPM authentication mechanism which establishes the trust between users and eTPMs is described in detail in Section 4.4.
3.3. User-Specific Feature
4. Enclave TPM
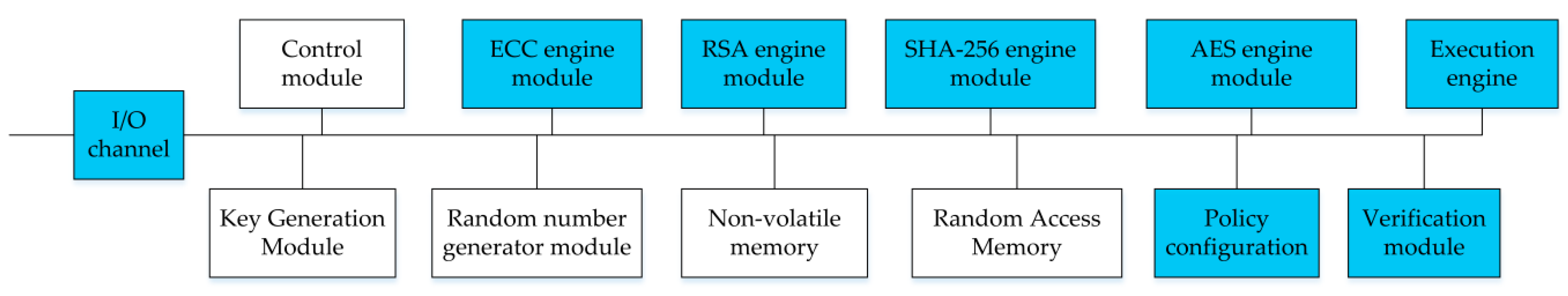
4.1. Enclave TPM Functions
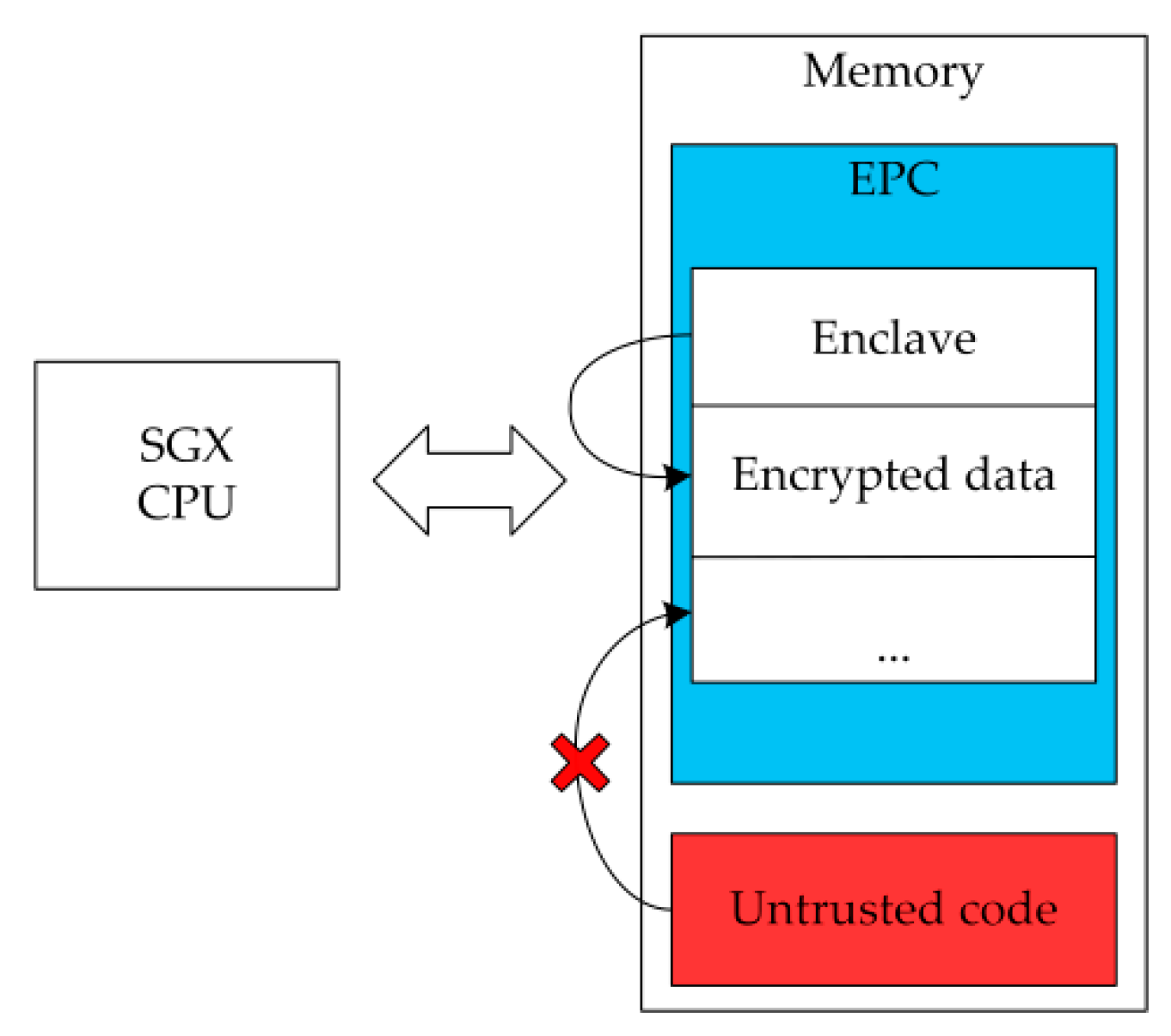
4.2. Enclave TPM Memory Isolation Mechanism
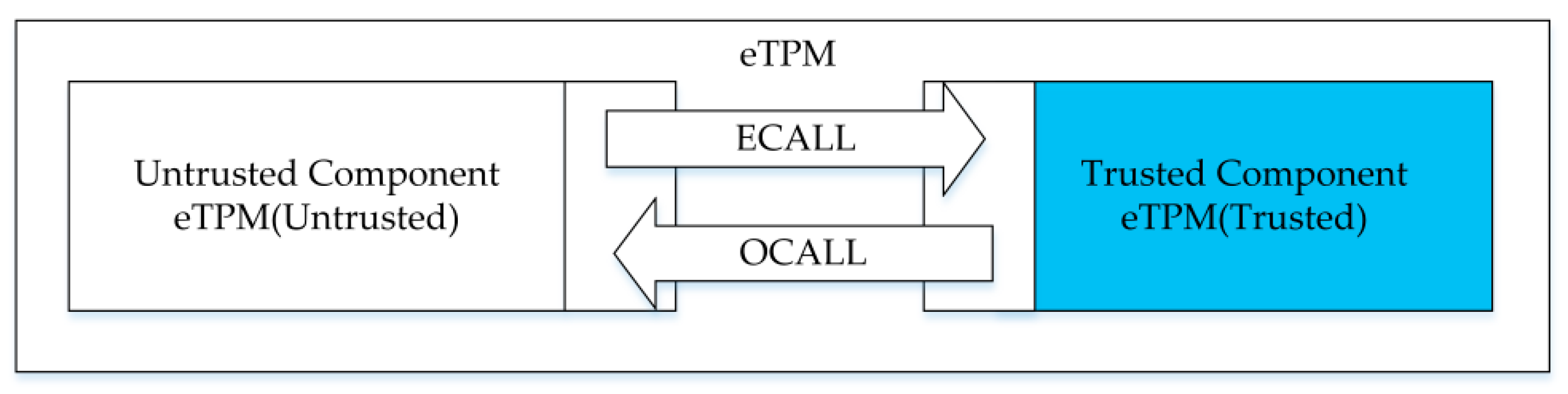
4.3. Enclave TPM Interaction Interface Designs
4.3.1. Enclave TPM Internal Interaction Interfaces
4.3.2. Enclave TPM Main Function Call
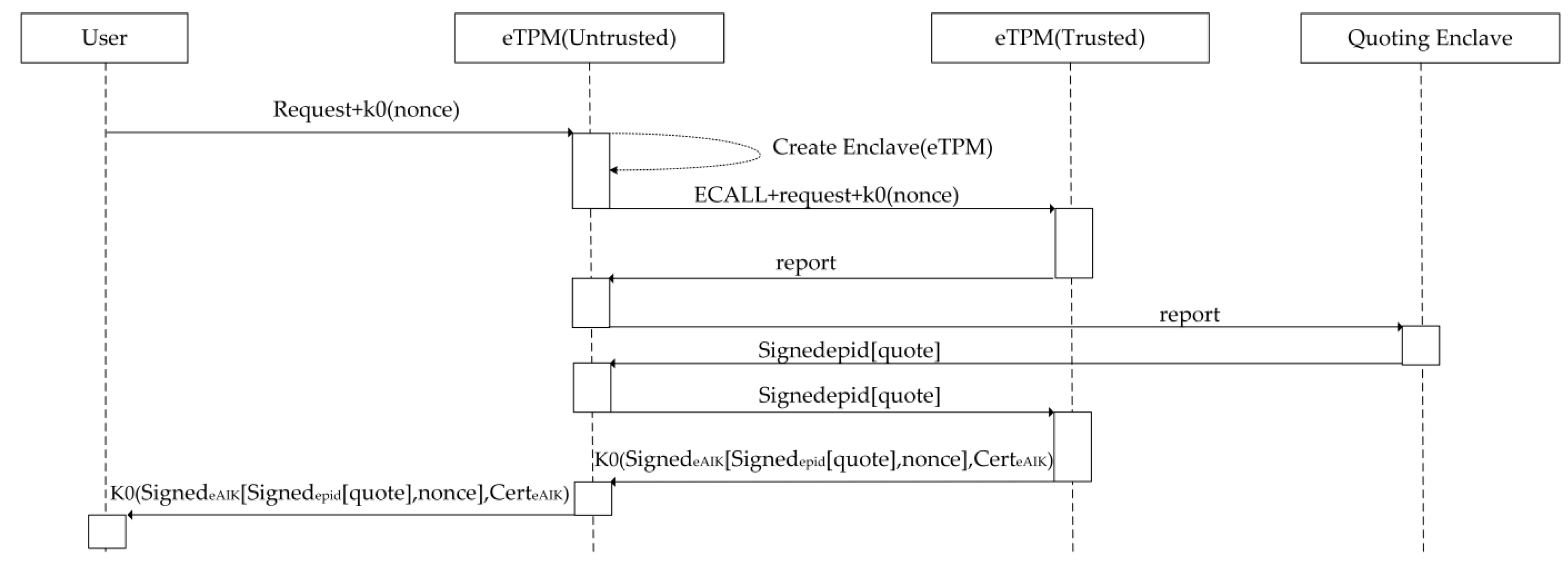
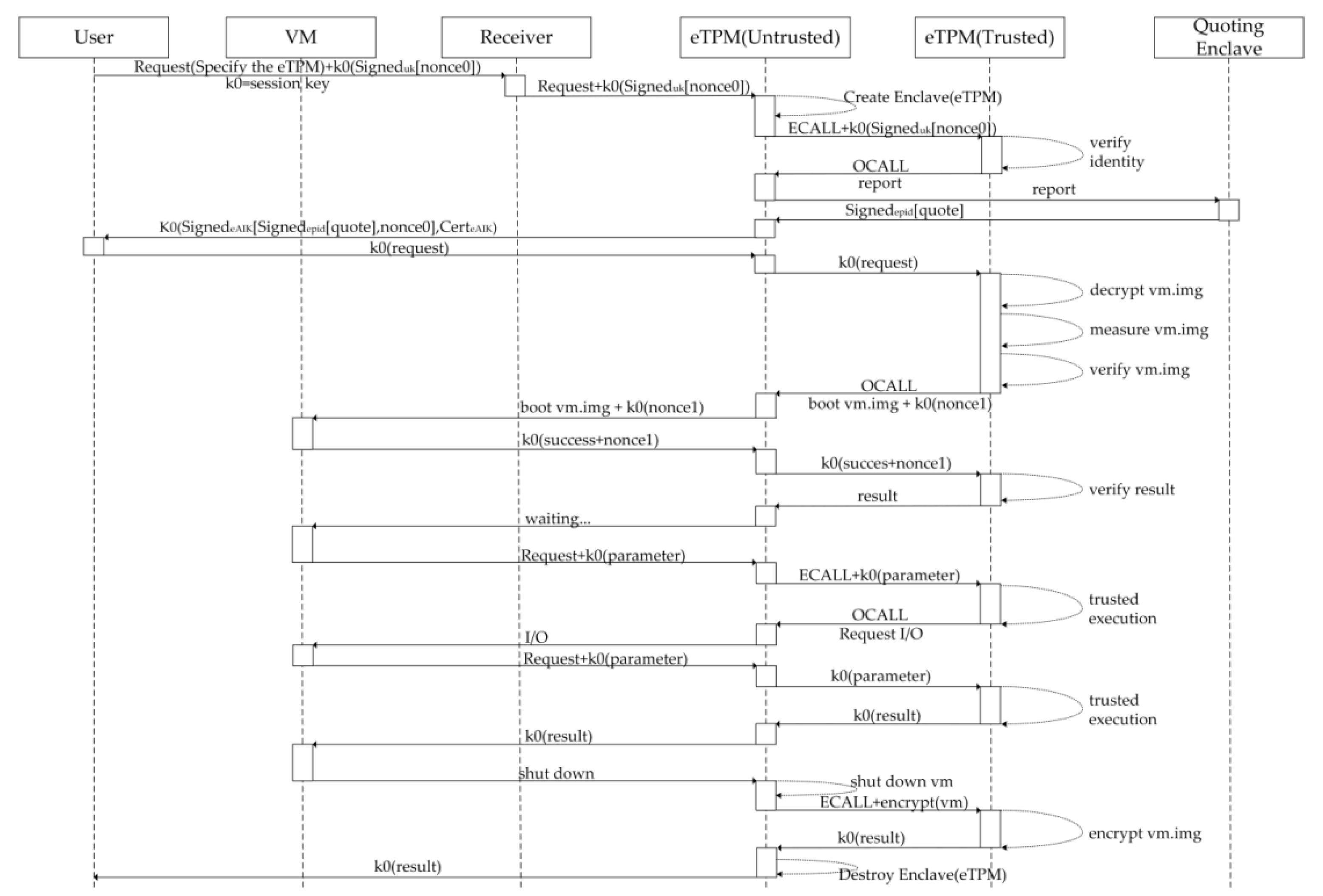
4.4. Enclave TPM’s Integrity
- (1)
- User request: The user sends the request and random number ‘nonce’ to eTPM(Untrusted).
- (2)
- Initialize the eTPM: The eTPM(Untrusted) creates and initializes the eTPM(Trusted). During the initialization process, the CPU verifies the integrity and identity of the eTPM itself.
- (3)
- Attestation: The session key ‘k0’ is agreed in advance between the user and the eTPM. And ‘eAIK’ is eTPM’s signing key. eTPM(Untrusted) executes an ECALL instruction to enter eTPM(Trusted) and then forwards request and a random number encrypted by k0 to eTPM(Trusted). Then the remote attestation report issued by eTPM(Trusted), are forwarded to the platform signing component QE by the eTPM(Untrusted). QE authenticates the report, converts the report to ‘quote’, and signs the ‘quote’ with EPID, then sends it back to eTPM(Trusted) through eTPM(Untrusted). Then eTPM(Trusted) signs the quote signed by EPID and random number ‘nonce’ with eAIK, and encrypts them and eAIK certificate together with k0, and then sends them to the user through eTPM(Untrusted). The user can verify the eTPM after receiving the ‘quote’, eAIK certificate and ‘nonce’.
4.5. Enclave TPM Binding Relationships
4.5.1. Identity Binding
4.5.2. Data Binding
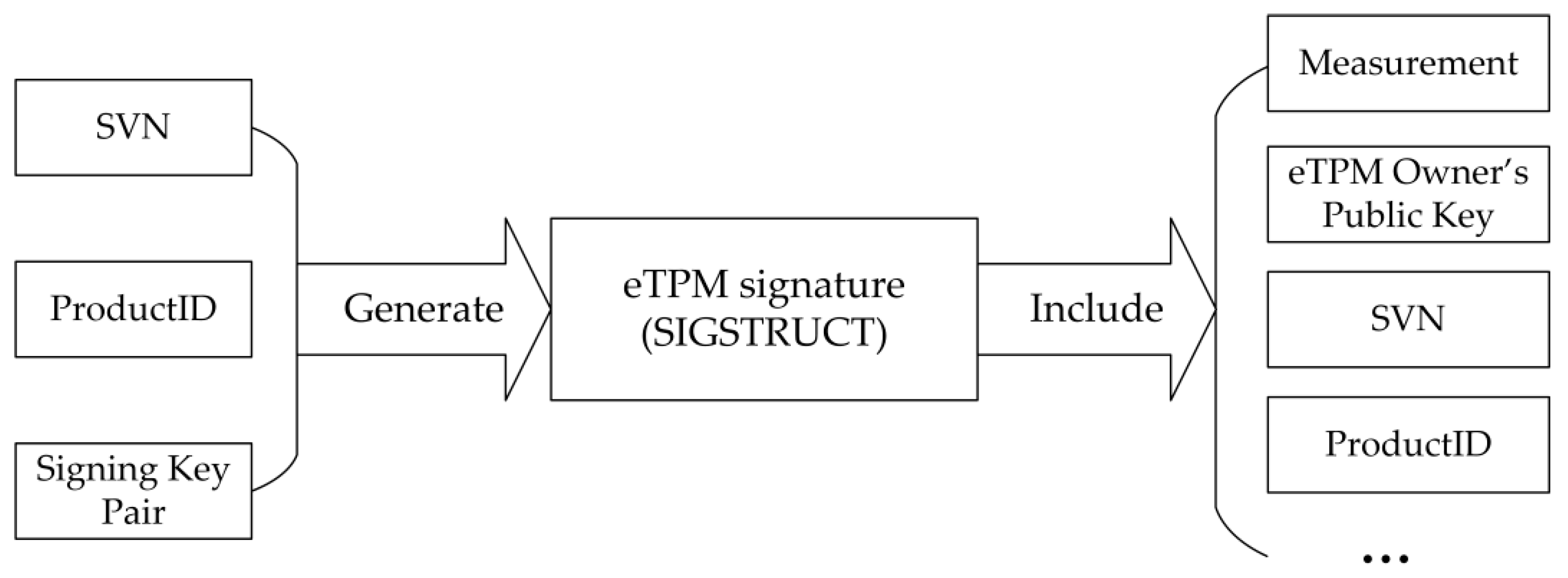
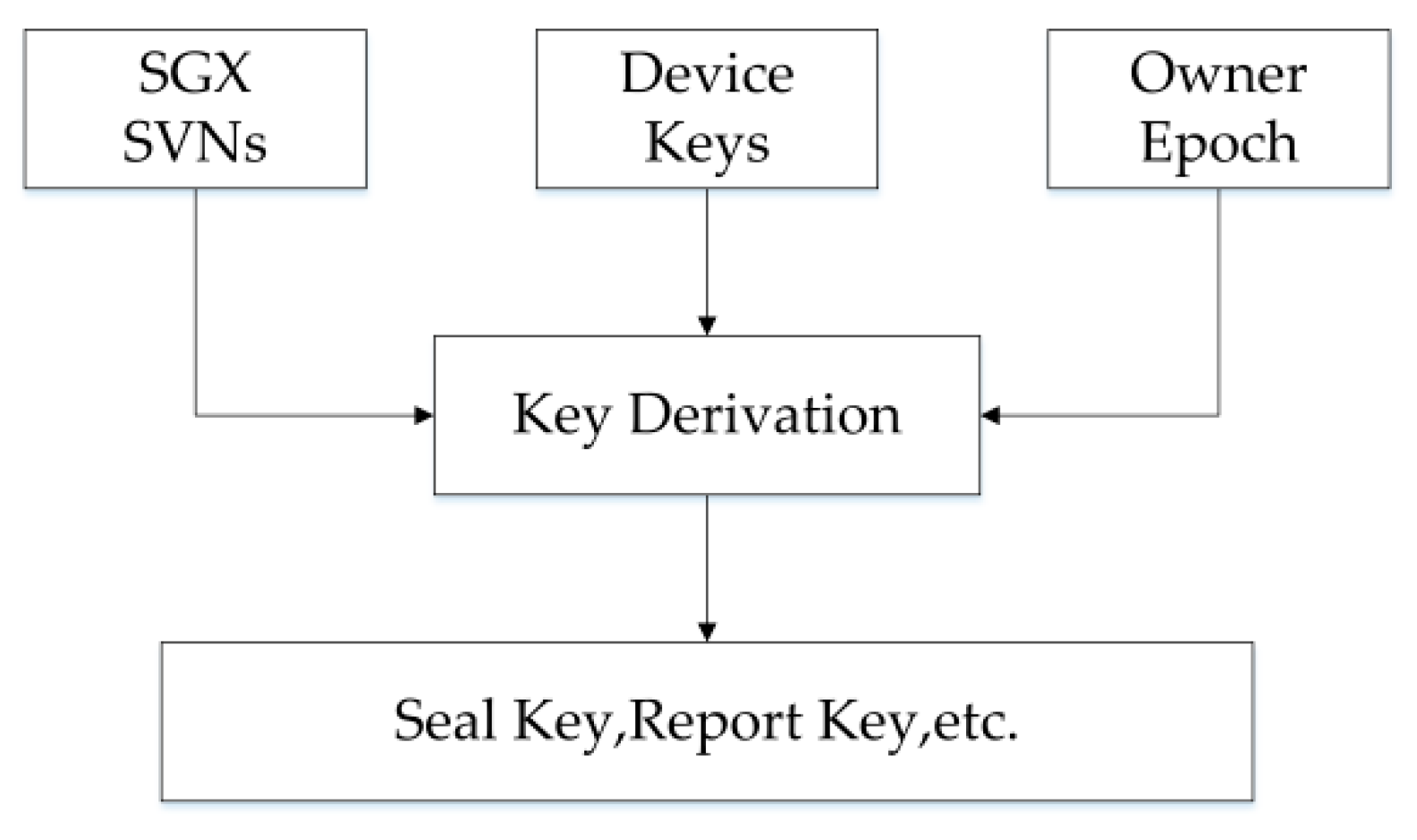
4.6. Enclave TPM Key Management
4.6.1. Key Derivation
4.6.2. Cryptographic Algorithm
4.7. Enclave TPM Trusted Execution
5. Experiments and Analysis
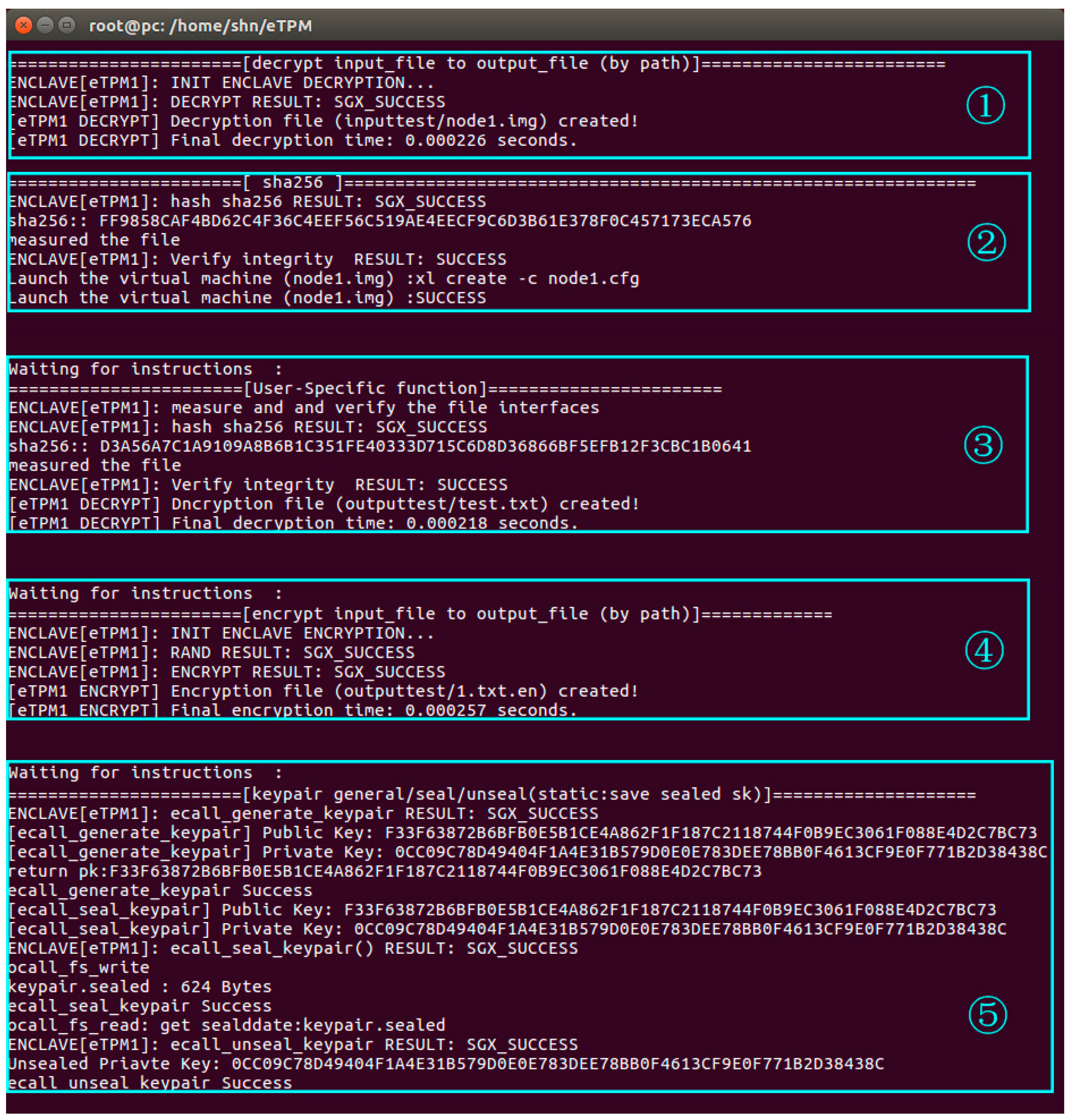
5.1. Enclave TPM Effectiveness
- (1)
- The eTPM firstly decrypts the image of the VM ‘node1’.
- (2)
- The eTPM1 measures the image of node1 and that the measured values match the reference values. Then node1 is launched and a random number ‘nonce1’ encrypted by the session key ‘K0’ is sent to node1.
- (3)
- After node1 is launched, a session with the eTPM1 is established and then a message that indicates VM launched successfully is sent to eTPM1 by node1. When eTPM1 receives this feedback message, it changes into the state of ‘waiting for instructions’.
- (4)
- eTPM1 encrypts the file according to the request of encrypting a file.
- (5)
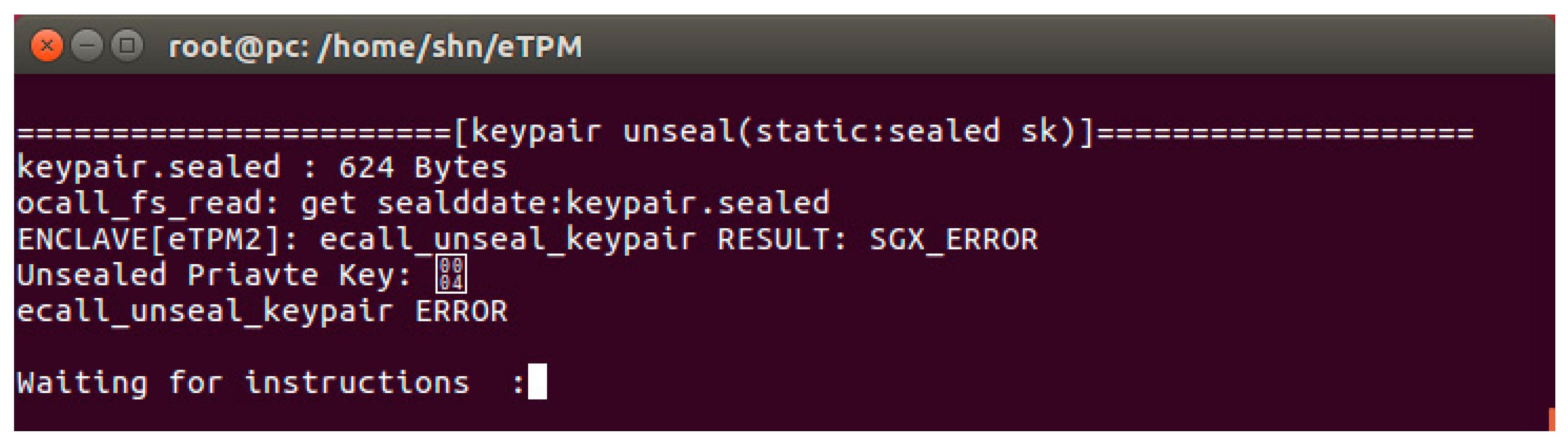
- eTPM1 generates, seals, and unseals a key pair according to the request.
5.2. Enclave TPM Security
5.2.1. Protocol Security
- (1)
- is a message, If.
- (2)
- is a message, ifare messages.is any n-dimensional function.
- (3)
- is a message ifis a formula.
- (1)
- is a formula, ifis a primitive proposition.
- (2)
- andare formulae(Includes other propositions connected byand), ifandare formulae.
- (3)
- andare formulae, ifis a principal andis a formula.
- (4)
- ,,,andare formulae, ifis a principal andis a message.
- (5)
- ,andare formulae, ifis a principal andis a key.
- (1)
- is an instantiation of an axiom;
- (2)
- is an assumption;
- (3)
- can be derived from some of the preceding formulae by using MP or Nec rules.
- (1)
- Believing:
- A0
- A1
- (2)
- Receiving:
- A7
- A8
- A9
- (3)
- Seeing:
- A10
- (4)
- Freshness:
- A18
- P1
- P2
- P3
- P4
- P5
- P6
- P7
- P8
- P9
- P10
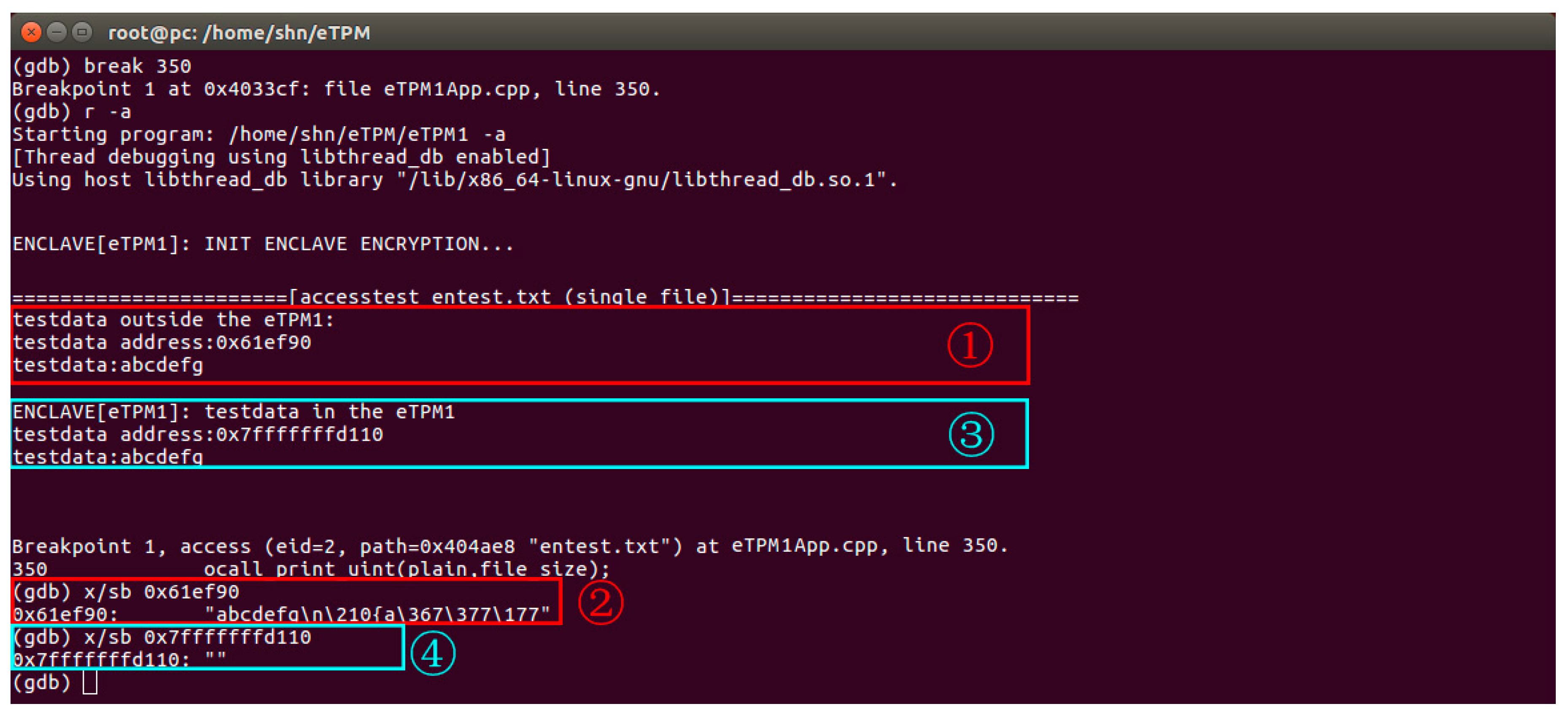
5.2.2. Memory Security
5.2.3. Data Security
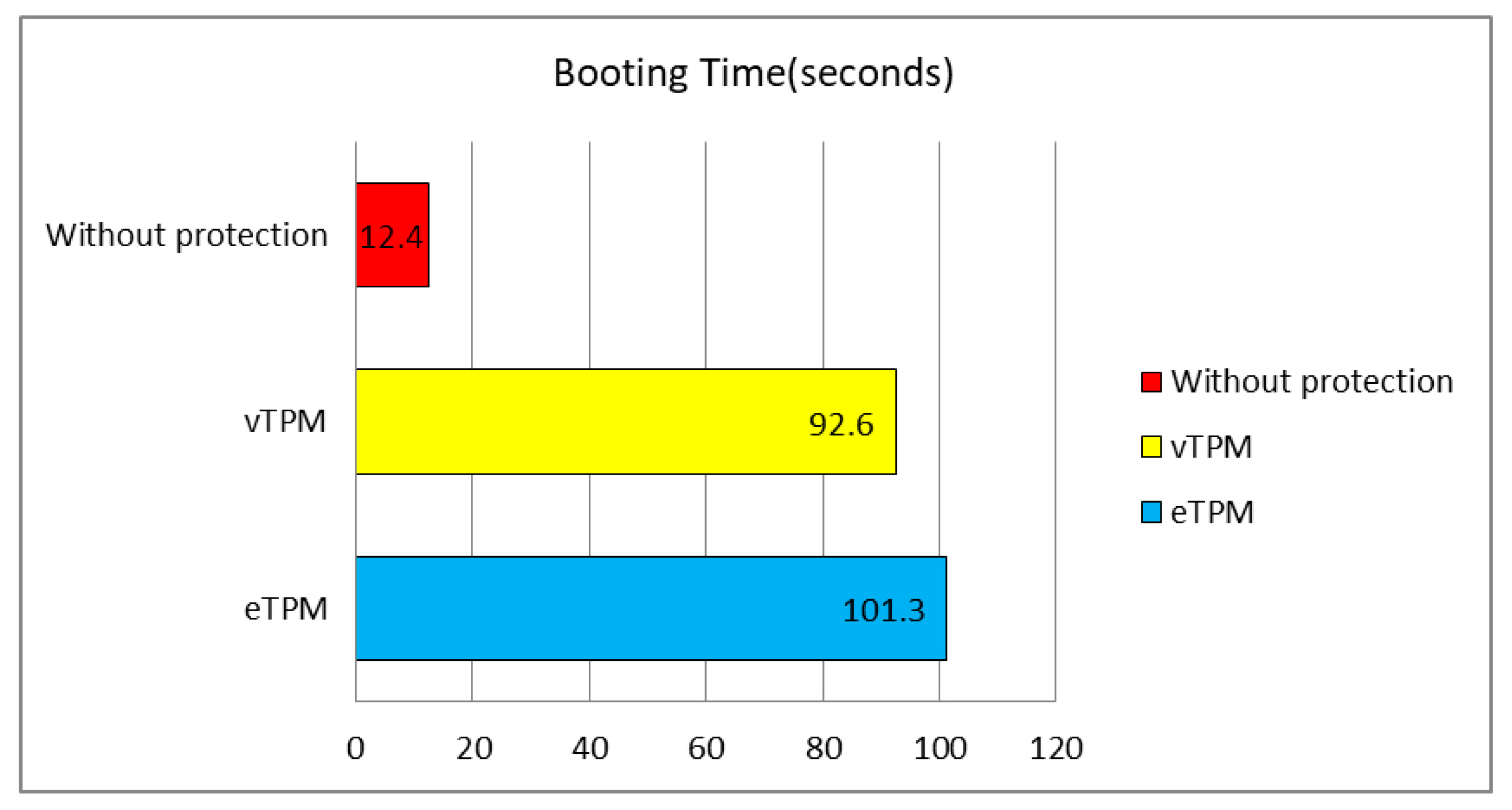
5.3. Enclave TPM Availability
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Mell, P.; Grance, T. The NIST Definition of Cloud Computing; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2011. [Google Scholar]
- Chen, Y.; Paxson, V.; Katz, R.H. What’s New about Cloud Computing Security; University of California, Berkeley Report No. UCB/EECS-2010-5 August; University of California: Oakland, CA, USA, 2010; Volume 20, p. 2010-5. [Google Scholar]
- Ristenpart, T.; Tromer, E.; Shacham, H.; Savage, S. Hey, you, get off of my cloud: Exploring information leakage in third-party compute clouds. In Proceedings of the 16th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009; pp. 199–212. [Google Scholar]
- Jiang, J.; Han, G.; Shu, L.; Chan, S.; Wang, K. A trust model based on cloud theory in underwater acoustic sensor networks. IEEE Trans. Ind. Inform. 2017, 13, 342–350. [Google Scholar] [CrossRef]
- Kaufman, L.M. Data security in the world of cloud computing. IEEE Secur. Priv. 2009, 7, 61–64. [Google Scholar] [CrossRef]
- Khalil, I.M.; Khreishah, A.; Azeem, M. Cloud computing security: A survey. Computers 2014, 3, 1–35. [Google Scholar] [CrossRef]
- Liu, Y.; Sun, Y.; Ryoo, J.; Rizvi, S.; Vasilakos, A.V. A survey of security and privacy challenges in cloud computing: Solutions and future directions. J. Comput. Sci. Eng. 2015, 9, 119–133. [Google Scholar] [CrossRef]
- Coppolino, L.; D’antonio, S.; Mazzeo, G.; Romano, L. Cloud security: Emerging threats and current solutions. Comput. Electr. Eng. 2017, 59, 126–140. [Google Scholar] [CrossRef]
- Martin, A. The Ten-Page Introduction to Trusted Computing; Computing Laboratory, Oxford University: Oxford, UK, 2008; p. 49. [Google Scholar]
- Achemlal, M.; Gharout, S.; Gaber, C. Trusted platform module as an enabler for security in cloud computing. In Proceedings of the IEEE 2011 Conference on Network and Information Systems Security (SAR-SSI), La Rochelle, France, 18–21 May 2011; pp. 1–6. [Google Scholar]
- Berger, S.; Goldman, K.A.; Perez, R.; Sailer, R.; Doorn, L. Vtpm: Virtualizing the Trusted Platform Module. In Proceedings of the 15th Conference on Usenix Security Symposium, Vancouver, BC, Canada, 31 July–4 August 2006; pp. 305–320. [Google Scholar]
- Yan, Q.; Han, J.; Li, Y.; Deng, R.H.; Li, T. A software-based root-of-trust primitive on multicore platforms. In Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, Hong Kong, China, 22–24 March 2011; pp. 334–343. [Google Scholar]
- Riad, K. Multi-authority trust access control for cloud storage. In Proceedings of the IEEE 2016 4th International Conference on Cloud Computing and Intelligence Systems (CCIS), Beijing, China, 17–19 August 2016; pp. 429–433. [Google Scholar]
- Garfinkel, T.; Pfaff, B.; Chow, J.; Rosenblum, M.; Boneh, D. Terra: A virtual machine-based platform for trusted computing. In Proceedings of the Nineteenth ACM Symposium on Operating Systems Principles, Bolton Landing, NY, USA, 19–22 October 2003; pp. 193–206. [Google Scholar]
- Takemura, C.; Crawford, L.S. The Book of Xen; No Starch Press: San Francisco, CA, USA, 2009. [Google Scholar]
- Xue, H.; Qing, S.; Zhang, H. XEN virtual machine technology and its security analysis. Wuhan Univ. J. Nat. Sci. 2007, 12, 159–162. [Google Scholar] [CrossRef]
- Garfinkel, T.; Rosenblum, M.; Dan, B. Flexible OS support and applications for trusted computing. In Proceedings of the Conference on Hot Topics in Operating Systems, Lihue, HI, USA, 18–21 May 2003; p. 25. [Google Scholar]
- Wojtczuk, R.; Rutkowska, J.; Tereshkin, A. Xen 0wning Trilogy; Invisible Things Lab: Las Vegas, NV, USA, 2008. [Google Scholar]
- Anati, I.; Gueron, S.; Johnson, S.; Scarlata, V. Innovative technology for CPU based attestation and sealing. In Proceedings of the 2nd International Workshop on Hardware and Architectural Support for Security and Privacy, Tel-Aviv, Israel, 23–24 June 2013; ACM: New York, NY, USA, 2013. [Google Scholar]
- McKeen, F.; Alexandrovich, I.; Berenzon, A.; Rozas, C.V.; Shafi, H.; Shanbhogue, V.; Savagaonkar, U.R. Innovative instructions and software model for isolated execution. In Proceedings of the 2nd International Workshop on Hardware and Architectural Support for Security and Privacy, Tel-Aviv, Israel, 23–24 June 2013; p. 10. [Google Scholar]
- Hoekstra, M.; Lal, R.; Pappachan, P.; Phegade, V.; Del Cuvillo, J. Using innovative instructions to create trustworthy software solutions. In Proceedings of the 2nd International Workshop on Hardware and Architectural Support for Security and Privacy, Tel-Aviv, Israel, 23–24 June 2013; p. 11. [Google Scholar]
- Intel Inc. Intel Software Guard Extensions. Available online: https://software.Intel.com/en-us/SGX (accessed on 21 August 2018).
- Intel Inc. Intel Software Guard Extensions Reference. Available online: https://software.Intel.com/sites/default/files/332680-002.pdf (accessed on 21 August 2018).
- Schuster, F.; Costa, M.; Fournet, C.; Gkantsidis, C.; Peinado, M.; Mainar-Ruiz, G.; Russinovich, M. VC3: Trustworthy data analytics in the cloud using SGX. In Proceedings of the 2015 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 17–21 May 2015; pp. 38–54. [Google Scholar]
- Chang, R.; Jiang, L.; Chen, W.; Xie, Y.; Lu, Z. A trust enclave-based architecture for ensuring run-time security in embedded terminals. Tsinghua Sci. Technol. 2017, 22, 447–457. [Google Scholar] [CrossRef]
- Yan, F.; Yu, Z.; Zhang, L.; Zhao, B. Vtse: A solution of sgx-based vtpm secure enhancement. Adv. Eng. Sci. 2017, 49, 133–139. [Google Scholar]
- Trusted Computing Group: Trusted Platform Module (tpm) Specifications. Technical Report. 2006. Available online: https://www.trustedcomputinggroup.org/specs/TPM (accessed on 23 August 2018).
- Stumpf, F.; Benz, M.; Hermanowski, M.; Eckert, C. An approach to a trustworthy system architecture using virtualization. In Proceedings of the International Conference on Autonomic and Trusted Computing, Hong Kong, China, 11–13 July 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 191–202. [Google Scholar]
- Shi, Y.; Zhao, B.; Yu, Z.; Zhang, H. A security-improved scheme for virtual TPM based on KVM. Wuhan Univ. J. Nat. Sci. 2015, 20, 505–511. [Google Scholar] [CrossRef]
- Rongyu, H.; Shaojie, W.; Lu, J. A User-specific Trusted Virtual Environment for Cloud Computing. Inf. Technol. J. 2013, 12, 1905–1913. [Google Scholar] [CrossRef][Green Version]
- Fortino, G.; Fotia, L.; Messina, F.; Rosaci, D.; Sarn, G.M. Forming Groups in the Cloud of Things Using Trust Measures. In Proceedings of the International Symposium on Intelligent and Distributed Computing, Bilbao, Spain, 15–17 October 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 298–308. [Google Scholar]
- Messina, F.; Pappalardo, G.; Comi, A.; Fotia, L.; Sarn, G.M.L.; Rosaci, D. Combining reputation and QoS measures to improve cloud service composition. Int. J. Grid Util. Comput. 2017, 8, 142. [Google Scholar] [CrossRef]
- Iyengar, A.; Kundu, A.; Sharma, U.; Zhang, P. A Trusted Healthcare Data Analytics Cloud Platform. In Proceedings of the IEEE International Conference on Distributed Computing Systems, Vienna, Austria, 2–5 July 2018; pp. 1238–1249. [Google Scholar]
- Baumann, A.; Peinado, M.; Hunt, G. Shielding Applications from an Untrusted Cloud with Haven. ACM Trans. Comput. Syst. 2014, 33, 1–26. [Google Scholar] [CrossRef]
- Arnautov, S.; Trach, B.; Gregor, F.; Knauth, T.; Martin, A.; Priebe, C.; Lind, J.; Muthukumaran, D.; O’keeffe, D.; Stillwell, M. SCONE: Secure Linux Containers with Intel SGX. In Proceedings of the OSDI, Savannah, GA, USA, 2–4 November 2016; pp. 689–703. [Google Scholar]
- Fetzer, C.; Mazzeo, G.; Oliver, J.; Romano, L.; Verburg, M. Integrating Reactive Cloud Applications in SERECA. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August 29–1 September 2017; pp. 1–8. [Google Scholar]
- Brenner, S.; Hundt, T.; Mazzeo, G.; Kapitza, R. Secure Cloud Micro Services Using Intel SGX. In Proceedings of the IFIP International Conference on Distributed Applications and Interoperable Systems, Neuchâtel, Switzerland, 19–22 June 2017; pp. 177–191. [Google Scholar]
- Arthur, W.; Challener, D. A Practical Guide to TPM 2.0: Using the Trusted Platform Module in the New Age of Security; Apress: Lanham, MD, USA, 2015. [Google Scholar]
- Syverson, P.F.; Oorschot, P.C.V. On Unifying Some Cryptographic Protocol Logics. In Proceedings of the IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–18 May 1994; p. 14. [Google Scholar]
- Syverson, P. A Unified Cryptographic Protocol Logic; NRL Chaos Report; NRL: Washington, DC, USA, 1996. [Google Scholar]
| Functions | Configuration | Description |
|---|---|---|
| Measurement and verification | Standard configuration | Measure and verify the integrity of components |
| Static protection | Standard configuration | Encrypt storage OS image, data |
| Dynamic protection | Standard configuration | Temporary data security processing |
| Components bootstrap | User self-configuration | Component bootstrap order limit |
| Personalized requirement s | User-specific | Such as access control policies |
| Function Name | Interaction Interface | Cryptographic Library Interface | Description |
|---|---|---|---|
| ecall_encrypt/ecall_decrypt | ECALL | sgx_rijndael128GCM_encrypt/sgx_rijndael128GCM_decrypt | Performs a 128 bit key size Rijndael AES-GCM encryption/decryption operation |
| eacll_generater and | ECALL | sgx_read_rand | Generates a random number inside the enclave. |
| ecall_hash | ECALL | sgx_sha256_msg | Performs a standard SHA256 hash of the input data buffer. |
| ecall_sealdata/ecall_unsealdata | ECALL | sgx_seal_data/sgx_unseal_data | Use AES-GCM to seal/unseal the input data |
| ecall_ecckeypair | ECALL | sgx_ecc256_create_key_pair | Generates a private/public key pair on the ECC curve. |
| ecall_rsasign/ecall_rsaverify | ECALL | sgx_rsa3072_sign/sgx_rsa3072_verify | Calculates/Verify the digital signature for a given data set based on the RSA 3072 private/public key. |
| ecall_aesctrencyrpt/ecall_aesctrdecrypt | ECALL | sgx_aes_ctr_encrypt/sgx_aes_ctr_decrypt | Performing 128-bit Rijndael AES-CTR encryption/decryption |
| ecall_report | ECALL | sgx_create_report | Create a cryptographic report that describes the contents of the calling enclave. |
| ecall_generatekey | ECALL | sgx_get_key | Generates a 128-bit secret key using the input information. |
| ocall_output | OCALL | / | Output the execution result |
| ocall_instructions | OCALL | / | Transfer instructions |
| Trusted Execution | Description |
|---|---|
| Verify the integrity of the underlying platform | Get the TPM’s measurement values for the underlying platform and verify them in the eTPM, to connect trust chains. |
| Measure and verify data | Measure and verify user’s data within eTPM |
| Seal/unseal data | Seal/unseal user’s sensitive data or keys so that the data or keys can only be unsealed in the user’s eTPM. |
| Encrypt/decrypt data | Use the key algorithm provided by eTPM to encrypt/decrypt user’s data so that data can be securely stored on the hard disk. |
| User-specific trusted execution | Users can expand eTPM according to their own needs, add specific functions. |
| Symbol | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| meaning | believes | says | said | received | equals | sees/has | fresh() | implies | controls |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, H.; He, R.; Zhang, Y.; Wang, R.; Ip, W.H.; Yung, K.L. eTPM: A Trusted Cloud Platform Enclave TPM Scheme Based on Intel SGX Technology. Sensors 2018, 18, 3807. https://doi.org/10.3390/s18113807
Sun H, He R, Zhang Y, Wang R, Ip WH, Yung KL. eTPM: A Trusted Cloud Platform Enclave TPM Scheme Based on Intel SGX Technology. Sensors. 2018; 18(11):3807. https://doi.org/10.3390/s18113807
Chicago/Turabian StyleSun, Haonan, Rongyu He, Yong Zhang, Ruiyun Wang, Wai Hung Ip, and Kai Leung Yung. 2018. "eTPM: A Trusted Cloud Platform Enclave TPM Scheme Based on Intel SGX Technology" Sensors 18, no. 11: 3807. https://doi.org/10.3390/s18113807
APA StyleSun, H., He, R., Zhang, Y., Wang, R., Ip, W. H., & Yung, K. L. (2018). eTPM: A Trusted Cloud Platform Enclave TPM Scheme Based on Intel SGX Technology. Sensors, 18(11), 3807. https://doi.org/10.3390/s18113807







