Minimizing Delay and Transmission Times with Long Lifetime in Code Dissemination Scheme for High Loss Ratio and Low Duty Cycle Wireless Sensor Networks
Abstract
:1. Introduction
2. Related Work
2.1. Research on Delay Optimization
2.2. Research on Transmission Times
2.3. Research on Reliability
3. Networks Model and Problem Statement
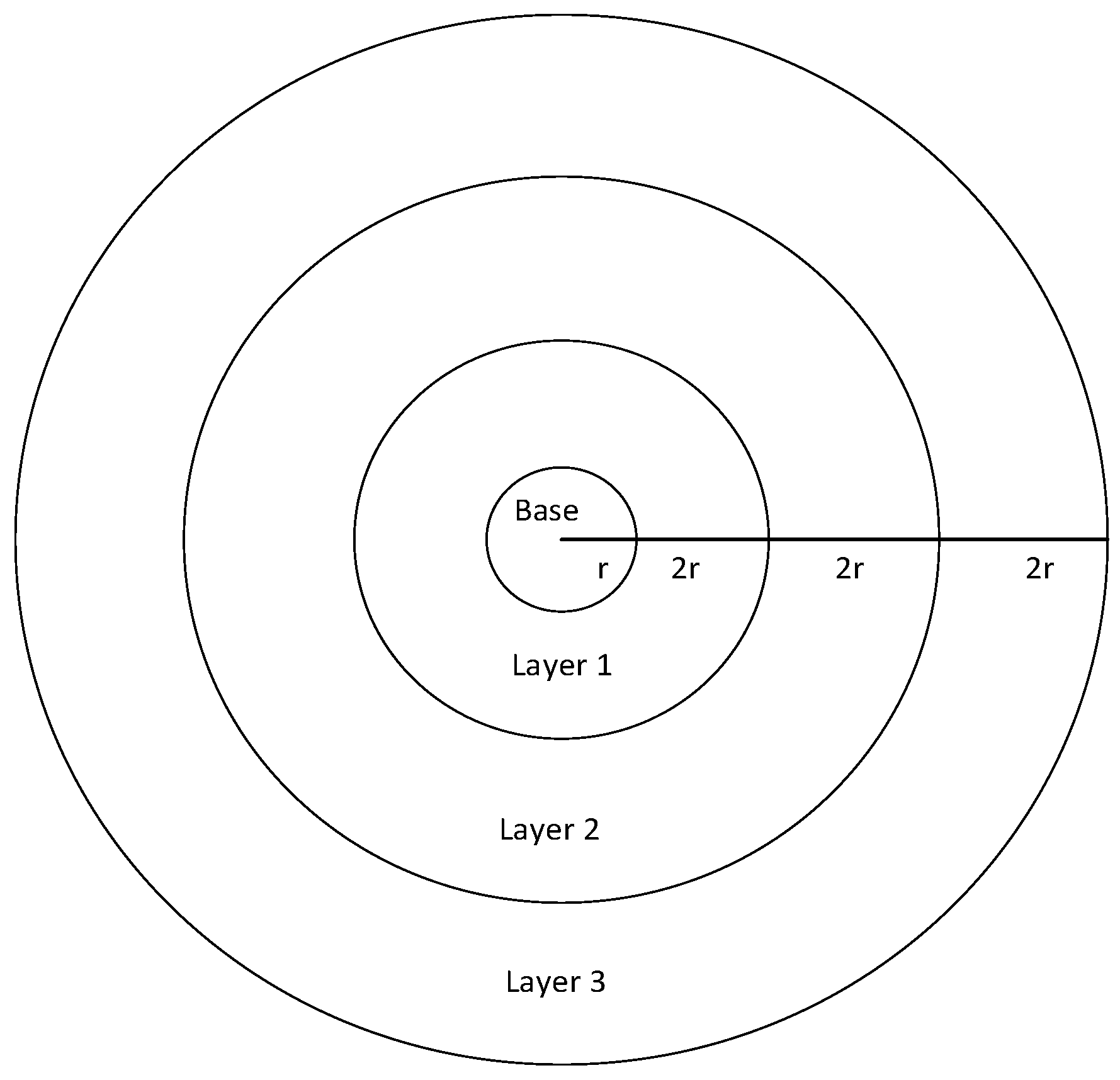
3.1. Networks Model
3.2. Problem Statement
4. Minimum Delay Scheme Design
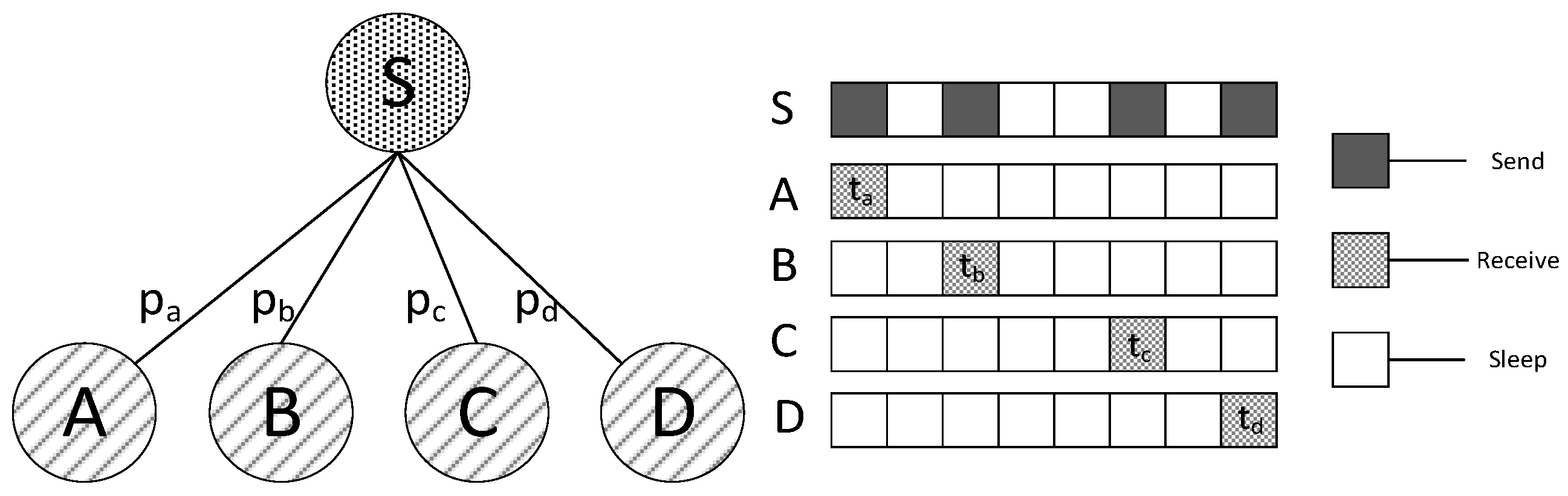
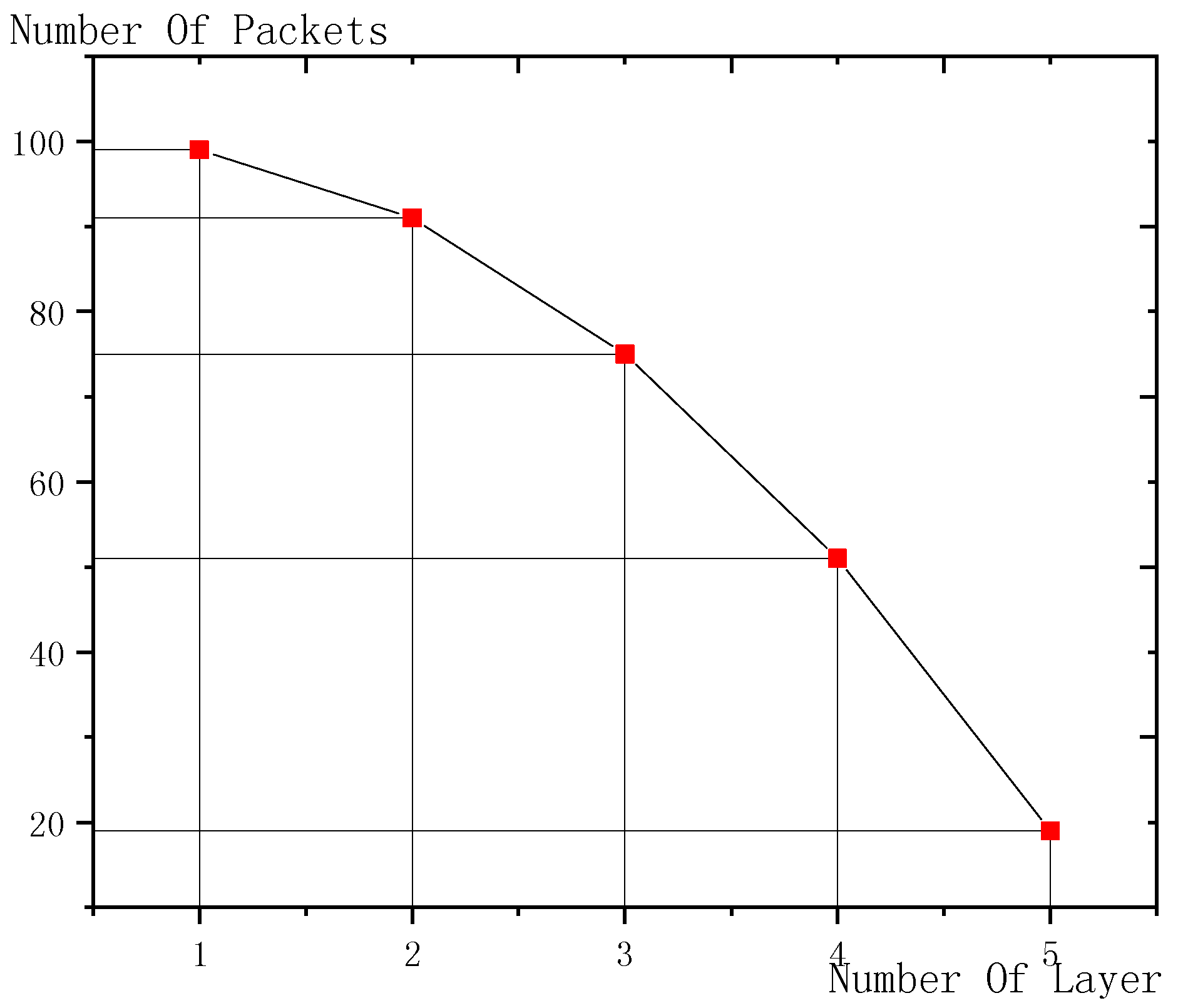
4.1. Research Motivation
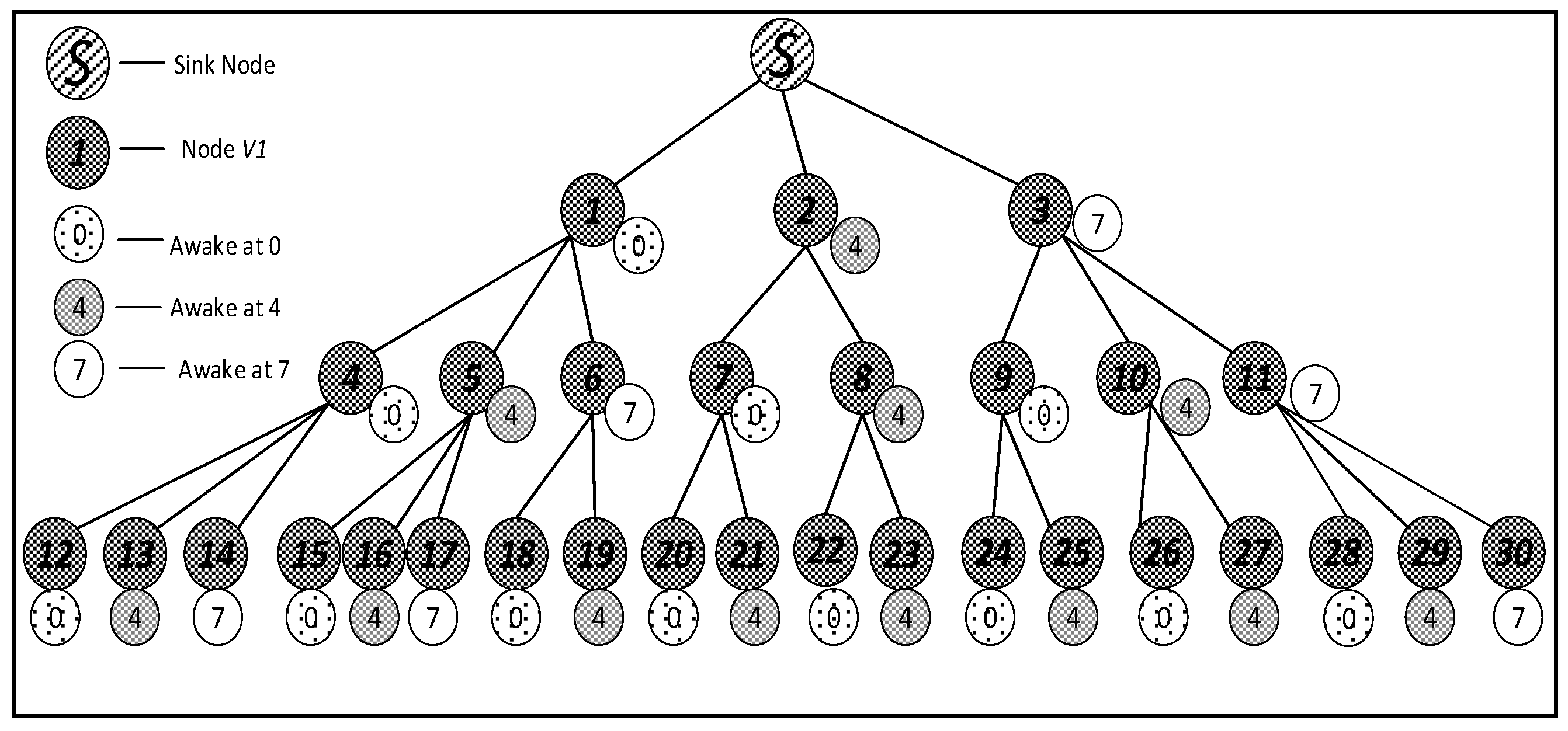
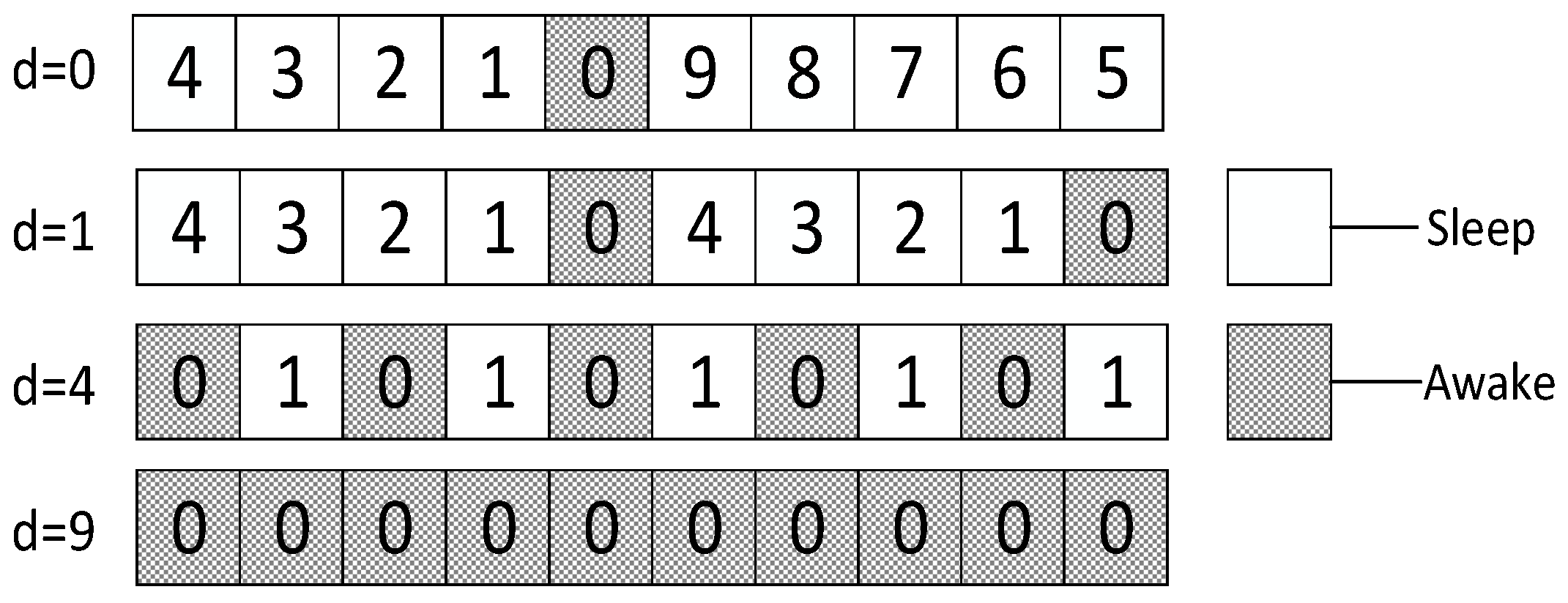
4.2. IFAS, BTAS, AAPS Schemes Design
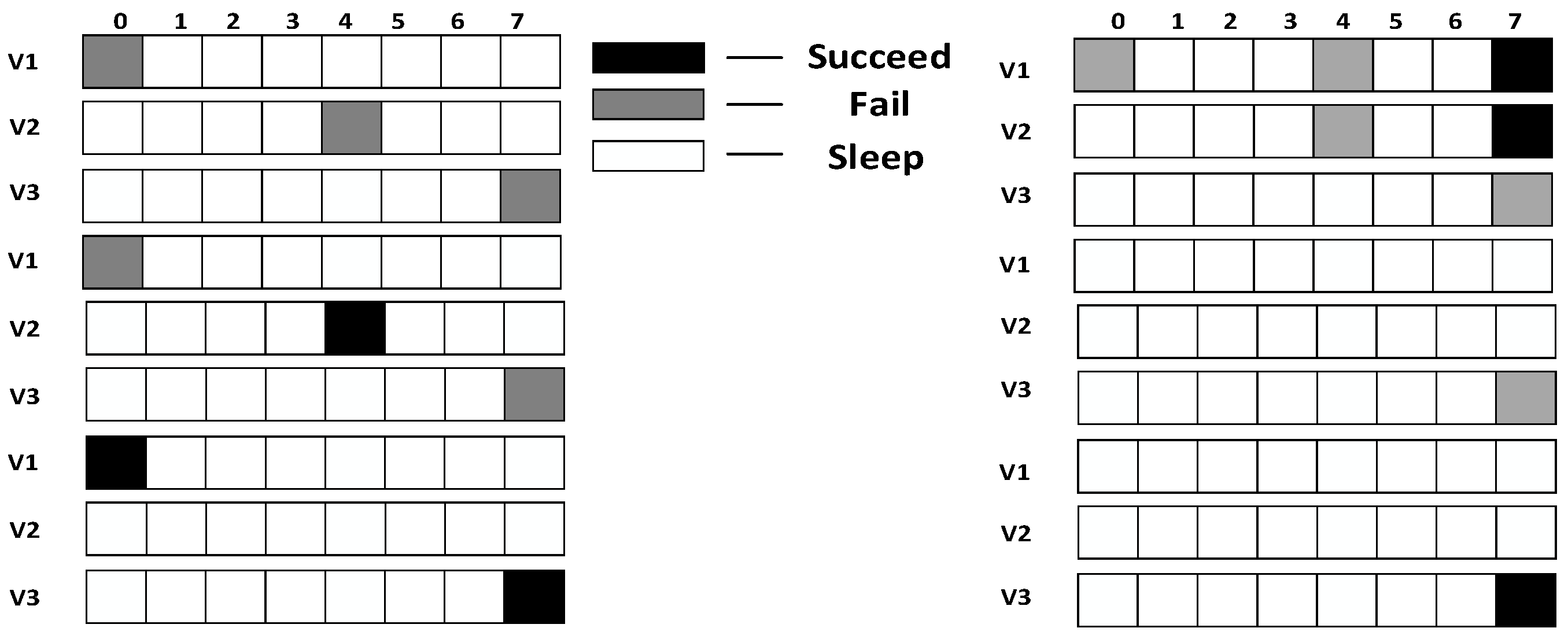
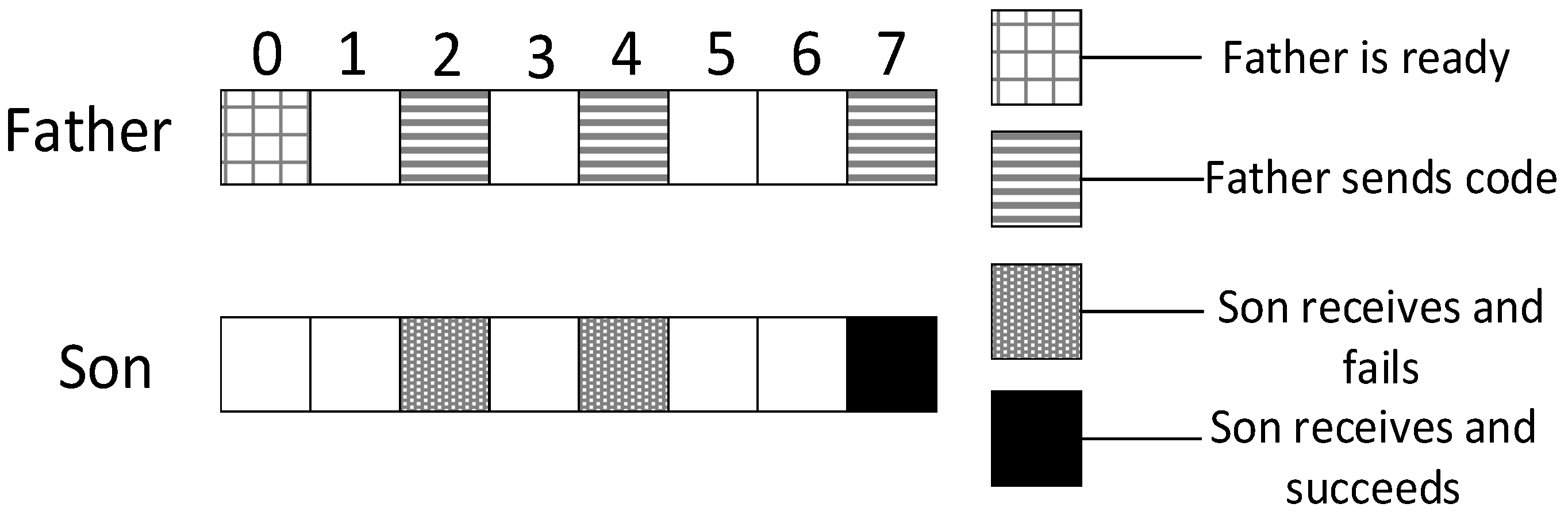
- The transmission times to this son node reaches
- Receive ACK from the son node
- The transmission times to this son node reaches
- Receive ACK from all the son nodes
- The packet is received successfully
- It senses nothing at its own slot
| Algorithm 1 Initialize father node under IFAS scheme |
| 1: Son_Count = 0 2: For each node of Do 3: Add this node’s awake slot to father node’s sending slot list 4: Son_Count = Son_Count + 1 5: End for |
| Algorithm 2 Initialize son nodes under IFAS scheme |
| 1: For each node of Brother_Nodes Do 2: If this brother node’s awake slot > own awake slot then 3: add this brother node’s awake slot to receiving slot list 4: End if 5: End for |
| Algorithm 3 Broadcast data packet under IFAS scheme |
| 1: Success_Count = 0 2: While Success_Count < Son_Count Do 3: wait until the next slot in sending slot list 4: broadcast data packet 5: For each node of Do 6: If this node receives successfully then 7: Success_Count= Success_Count + 1 8: End if 9: End for 10: End while |
| Algorithm 4 Receive data packet under IFAS scheme |
| 1: Success_Flag = 0, Receive_Flag = 0 2: While Receive_Flag==0 Do 3: wait until own slot 4: If this node receives successfully then 5: Success_Flag = 1, Receive_Flag = 1 6: End if 7: Else if this node receives unsuccessfully then 8: Success_Flag = 0, Receive_Flag = 1 9: End else 10: End while 11: While Success_Flag==0 Do 12: wait until the next slot in receiving slot list 13: If this node receives successfully then 14: Success_Flag = 1 15: End if 16: End while |
- The transmission times to this son node reaches
- Receive ACK from all the son nodes
- The packet is received successfully
- It senses nothing at its own slot
| Algorithm 5 Initialize father node under BTAS scheme |
| 1: Son_Count = 0 2: For each node of Do 3: Add this node’s awake slot to father node’s sending slot list 4: Son_Count = Son_Count + 1 5: End for |
| Algorithm 6 Initialize son nodes under BTAS scheme |
| 1: After_Slots_Count = 0,Active_Slot = m 2: For each node of Brother_Nodes Do 3: If this brother node’s awake slot > own awake slot then 4: add this brother node’s awake slot to receiving slot list 5: After_Slots_Count = After_Slots_Count + 1 6: End if 7: End for 8:If After_Slots_Count==0 then 9: For each node of Brother_Nodes Do 10: If this brother node’s awake slot < Active_Slot then 11: Active_Slot = this brother node’s awake slot 12: End if 13: End for 14: Add Active_Slot to awake slot list 15:End if 16:Add own slot to awake slot list |
| Algorithm 7 Broadcast data packet under BTAS scheme |
| 1:Success_Count = 0 2:While Success_Count < Son_Count Do 3: wait until the next slot in sending slot list 4: broadcast data packet 5: For each node of Do 6: If this node receives successfully then 7: Success_Count = Success_Count + 1 8: End if 9: End for 10: End while |
| Algorithm 8 Receive data packet under BTAS scheme |
| 1: Success_Flag = 0,Receive_Flag = 0 2:While Receive_Flag==0 Do 3: wait until next slot in awake slot list 4: If this node receives successfully then 5: Success_Flag = 1, Receive_Flag = 1 6: End if 7: Else if this node receives unsuccessfully then 8: Success_Flag = 0, Receive_Flag = 1 9: End else 10:End while 11: While Success_Flag==0 Do 12: wait until the next slot in receiving slot list 13: If this node receives successfully then 14: Success_Flag = 1 15: End if 16:End while |
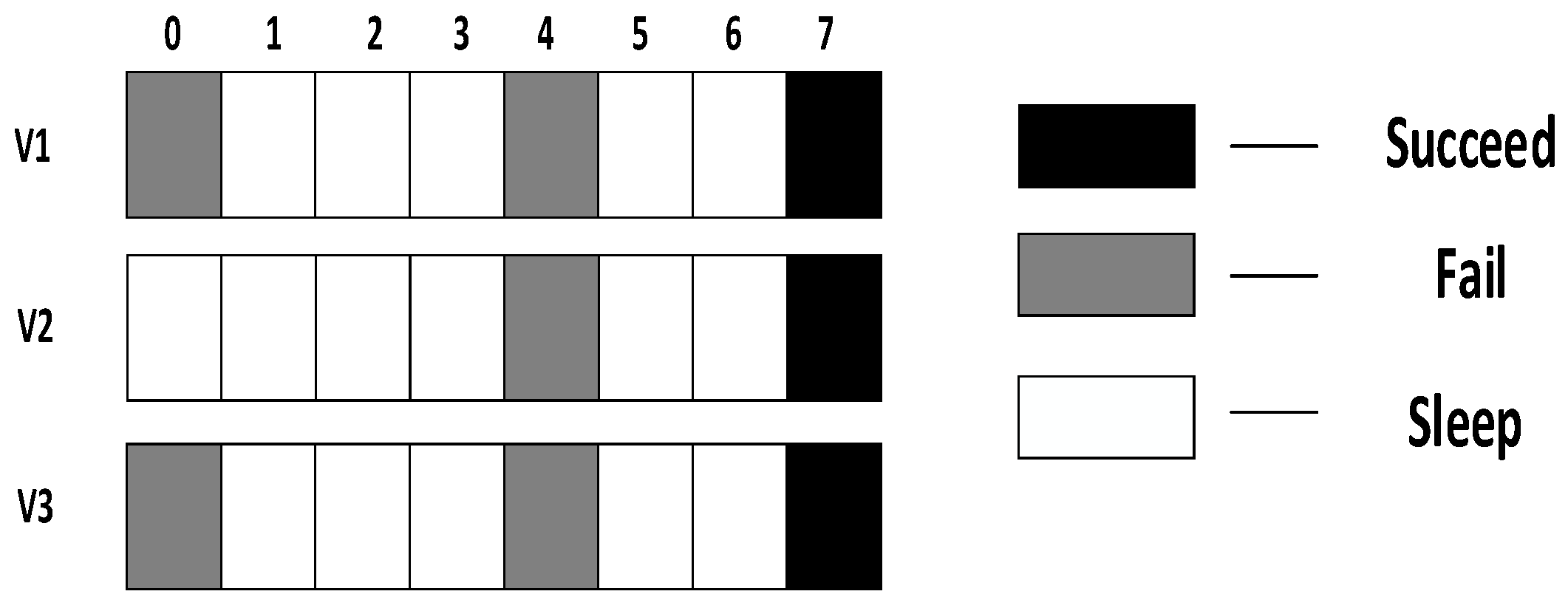
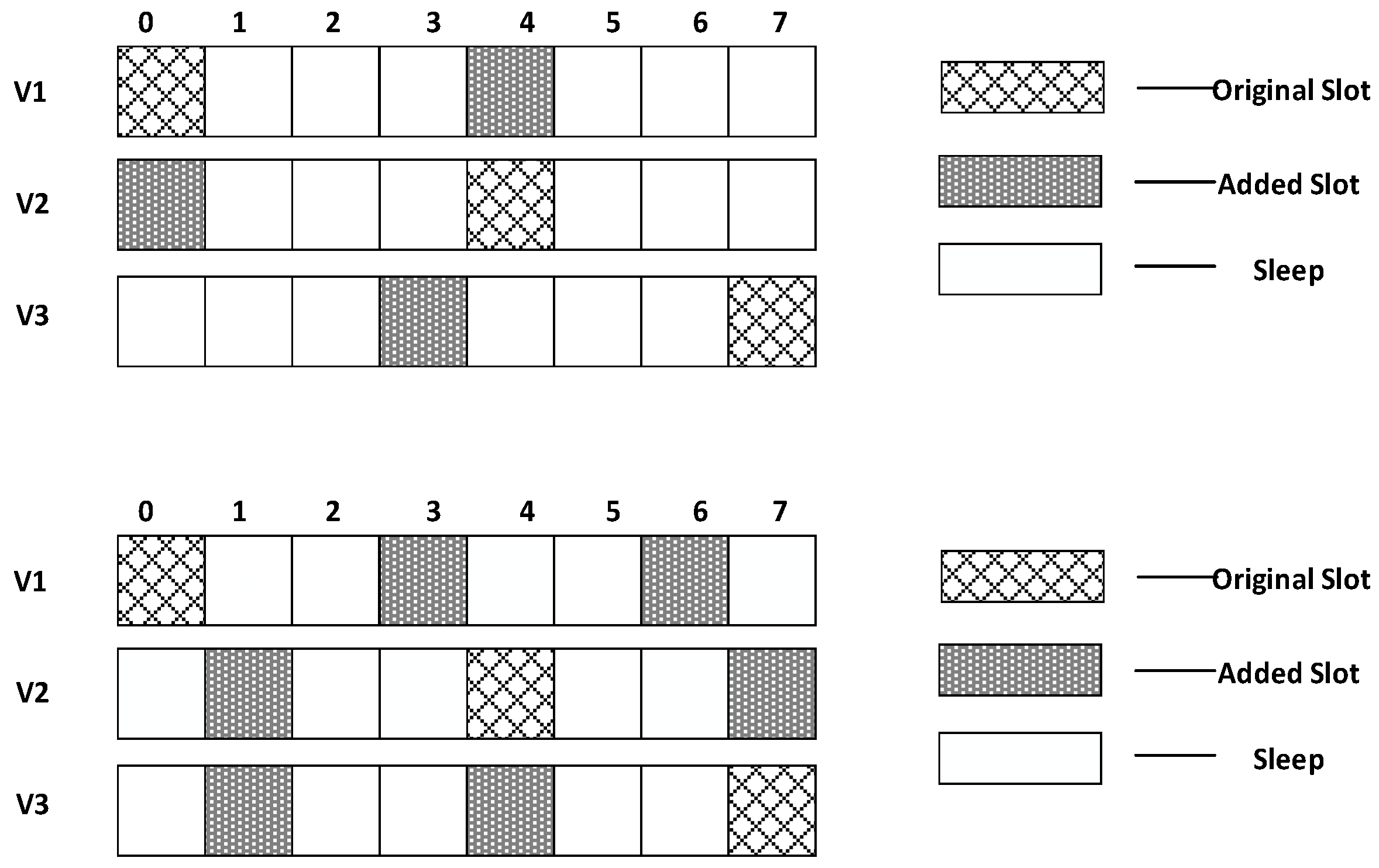
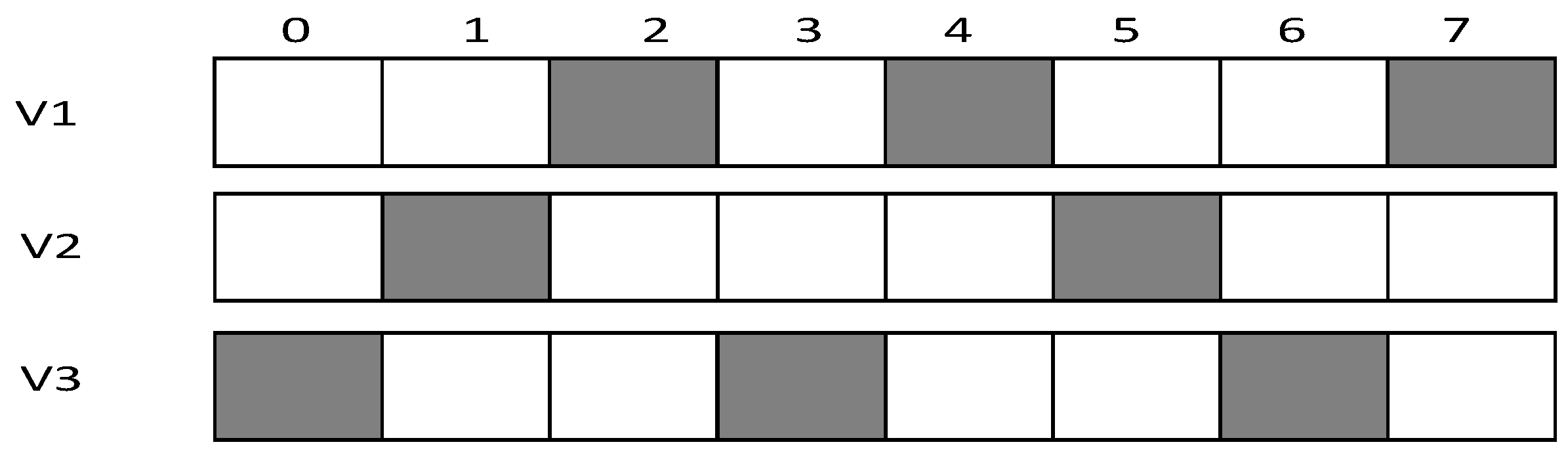
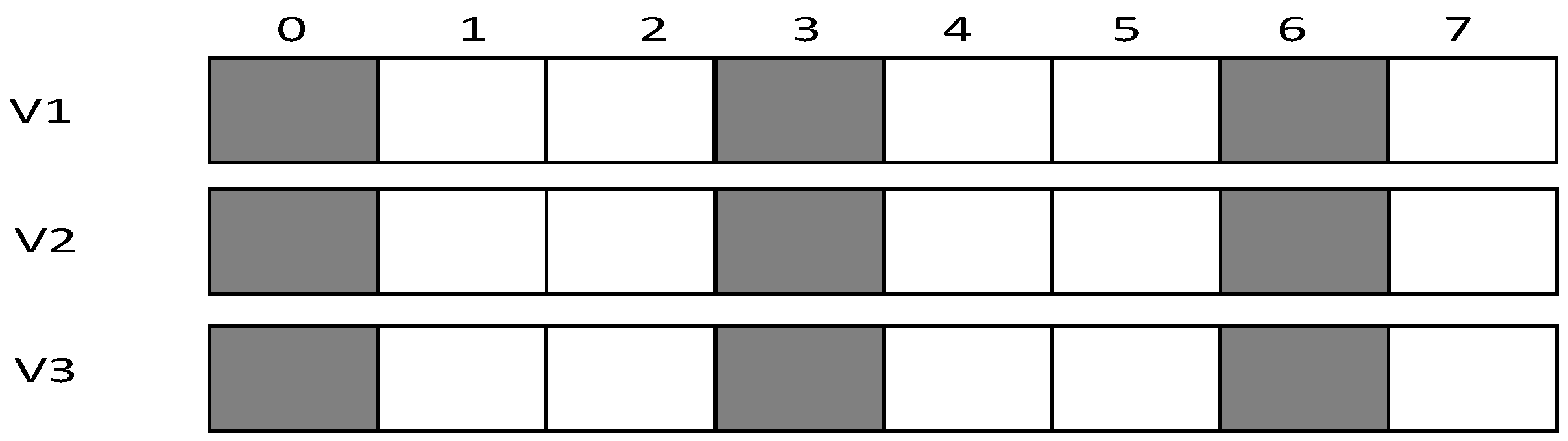
- Calculate the number of sleeping slots,
- Update to average number of sleeping slots,
- Starting from the slot randomly generated by the son node itself, it first adds a slot with a gap of , then adds another slot with a gap of ⎡⎤ and so on, until the number of added slot reaches. If the node has reached the end of the cycle, then it will continue adding slots from the beginning of the cycle.
- The transmission times to this son node reaches
- Receive ACK from all the son nodes
- The packet is received successfully
- It senses nothing at one of its own slots
| Algorithm 9 Initialize father node under AAPS scheme |
| 1: Son_Count = 0 2: For each node of Do 3: For each awake slot of this node Do 4: Add this slot to father node’s sending slot list 5: End for 6: Son_Count = Son_Count + 1 7: End for |
| Algorithm 10 Initialize son nodes under AAPS scheme |
| 1:Max_Interval = 0, Min_Interval = 0, d = NumberOfAddedSlots, i = 0 2:Min_Interval = (m − d − 1)/(d + 1) 3:If (m − d − 1)mod(d + 1)==0 then 4: Max_Interval = Min_Interval 5:End if 6:Else 7: Max_Interval = Min_Interval + 1 8:End else 9:While i < d Do 10: If i mod 2==0 then 11: Add (OwnSlot + Min_Interval + 1) to awake slot list 12: End if 13: Else 14: Add (OwnSlot + Max_Interval + 1) to awake slot list 15: End else 16: i = i + 1 17:End while 18:For each node of Brother_Nodes Do 19: For each awake slot of this brother node Do 20: add this awake slot to receiving slot list 21: End for 22:End for |
| Algorithm 11 Broadcast data packet under AAPS scheme |
| 1:Success_Count = 0 2:While Success_Count < Son_Count Do 3: wait until the next slot in sending slot list 4: broadcast data packet 5: For each node of Do 6: If this node receives successfully then 7: Success_Count = Success_Count + 1 8: End if 9: End for 10: End while |
| Algorithm 12 Receive data packet under AAPS scheme |
| 1: Success_Flag = 0,Receive_Flag = 0 2:While Receive_Flag==0 Do 3: wait until next slot in awake slot list 4: If this node receives successfully then 5: Success_Flag = 1, Receive_Flag = 1 6: End if 7: Else if this node receives unsuccessfully then 8: Success_Flag = 0, Receive_Flag = 1 9: End else 10:End while 11: While Success_Flag==0 Do 12: wait until the next slot in receiving slot list 13: If this node receives successfully then 14: Success_Flag = 1 15: End if 16:End while |
5. Parameter Optimization and Performance Analysis
5.1. Calculations of Energy and the Number of Slots that Can Be Added
5.2. Delay Calculation
6. Experiment Results and Performances Comparison
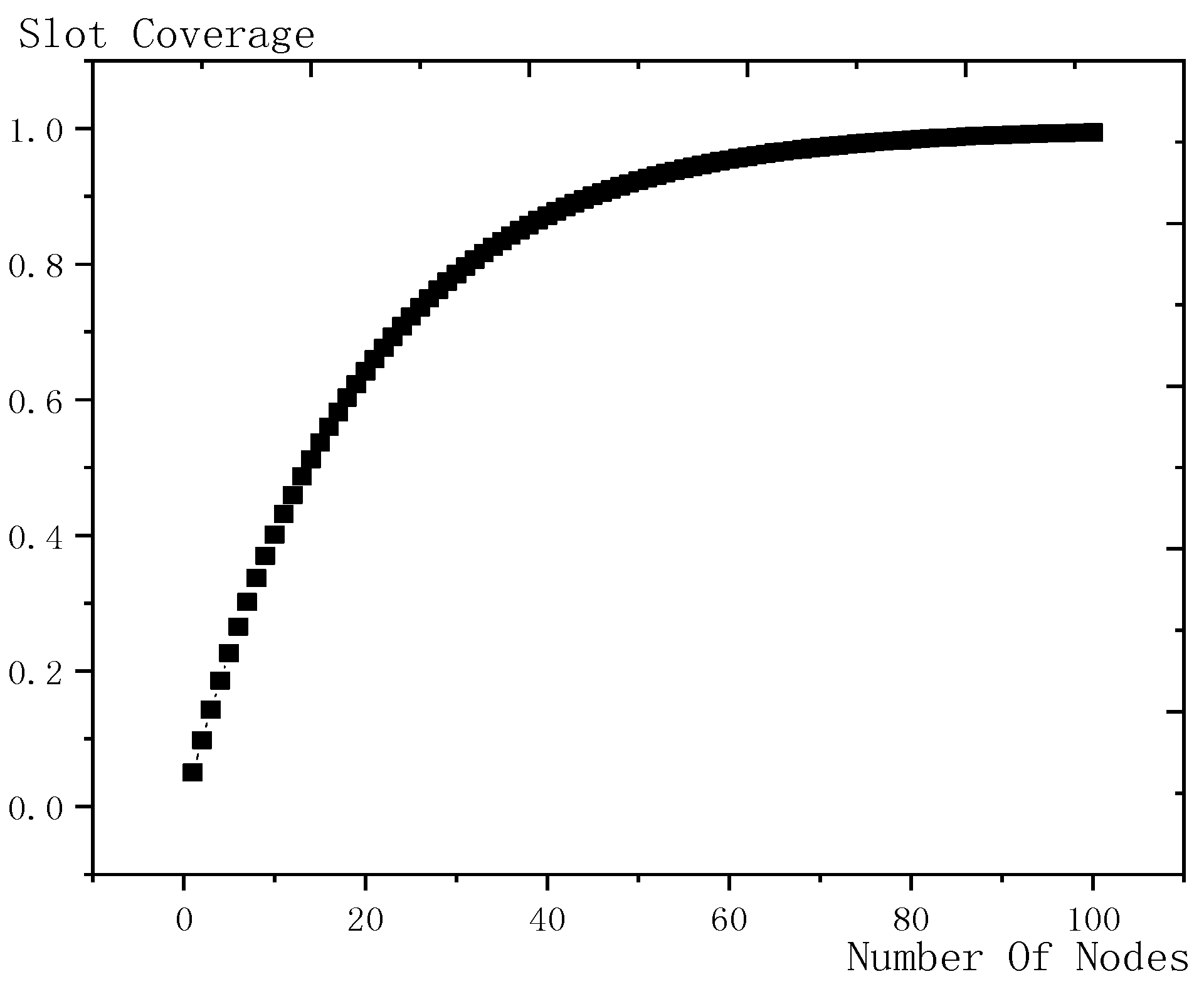
6.1. Diffusion Speed Comparison
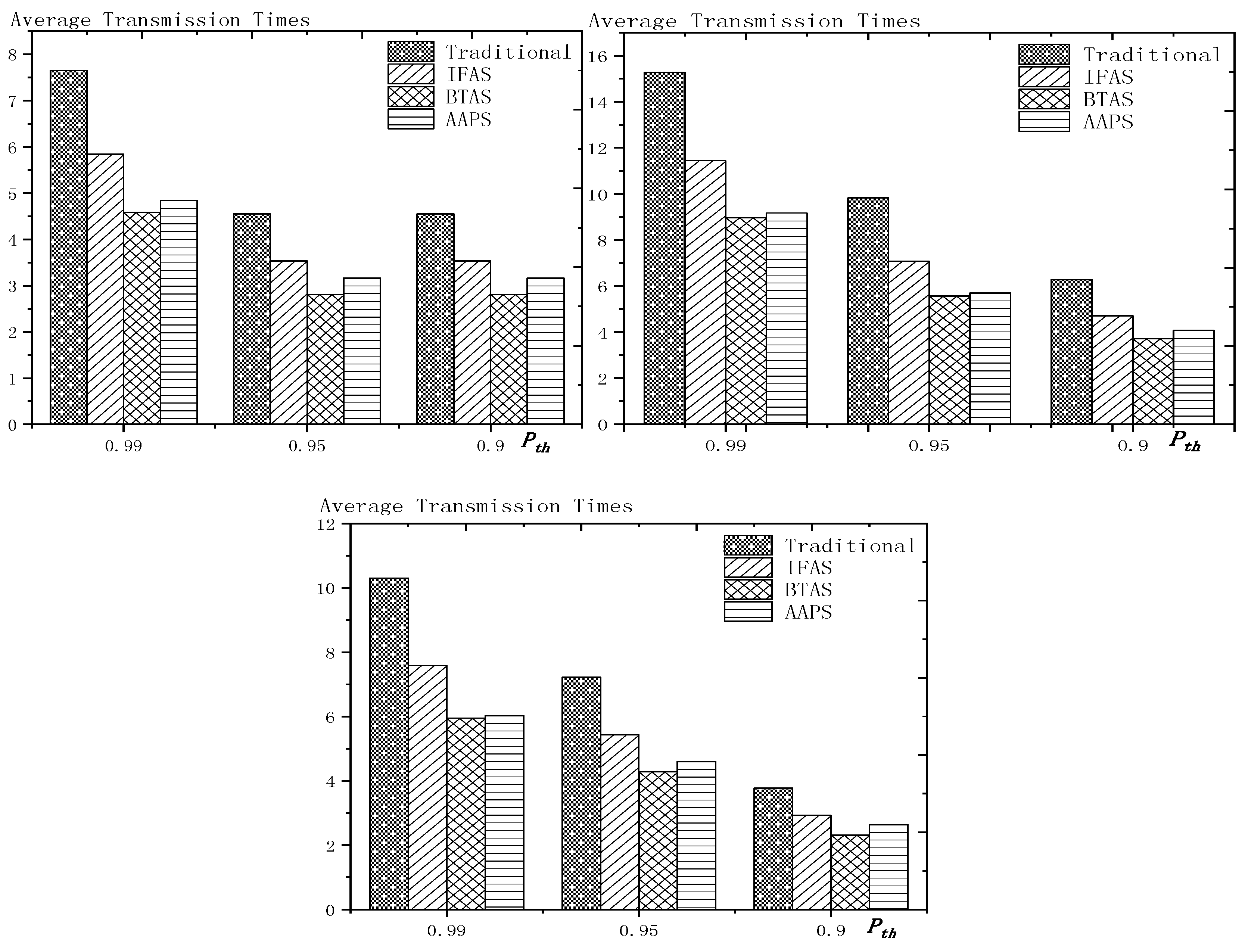
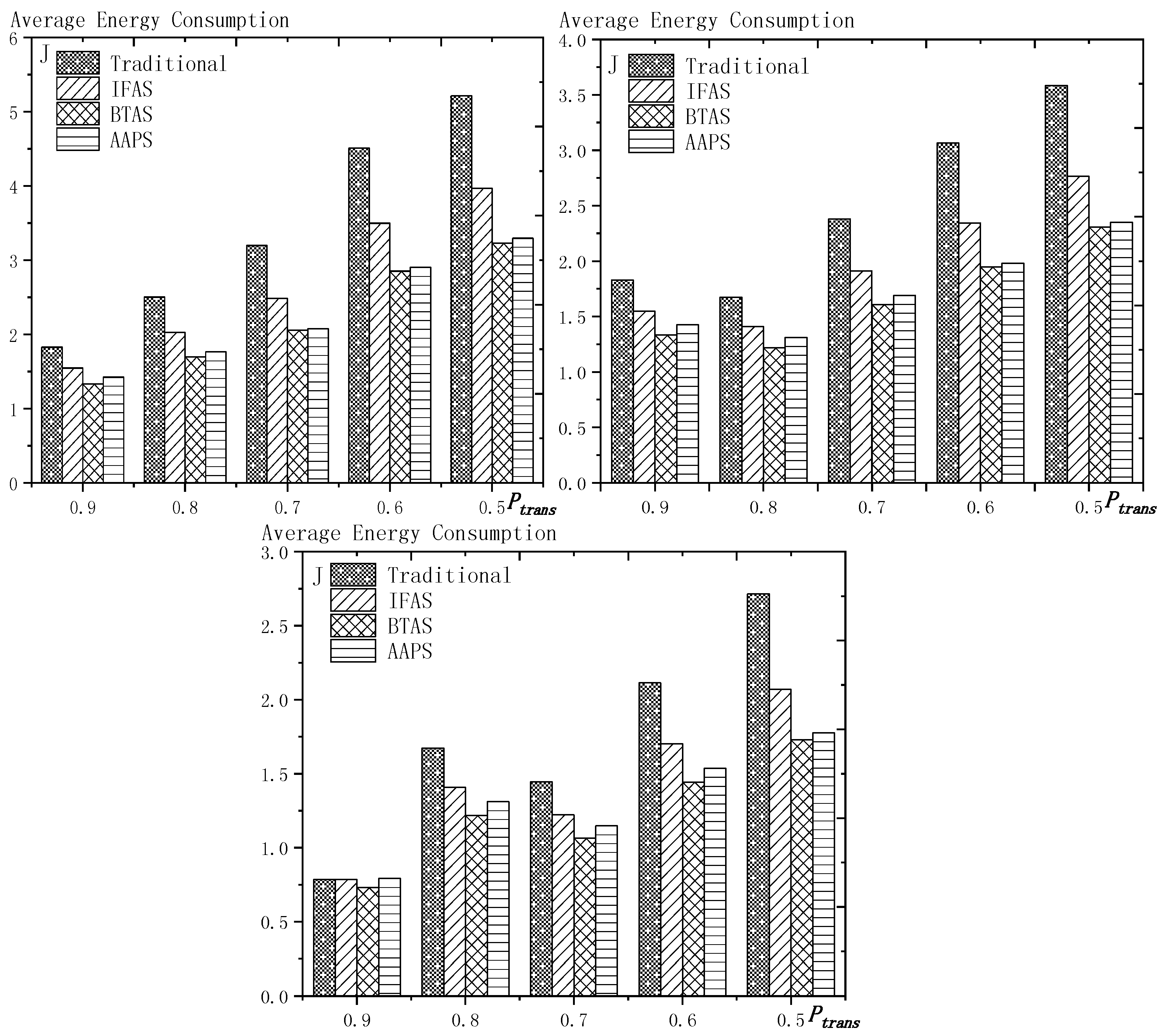
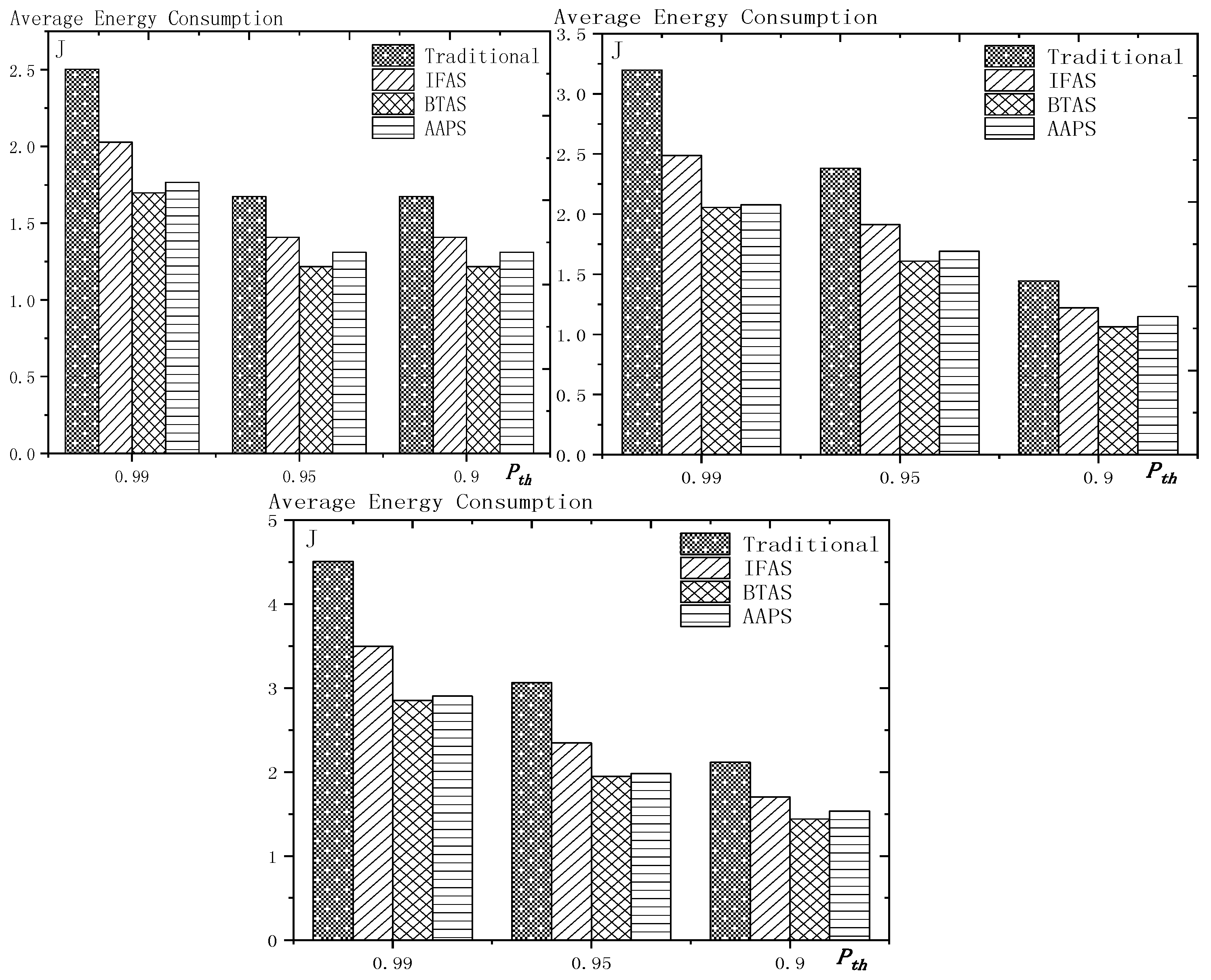
6.2. Transmission Times and Energy Consumption Comparison
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- González-Briones, A.; Chamoso, P.; De La Prieta, F.; Demazeau, Y.; Corchado, J.M. Agreement Technologies for Energy Optimization at Home. Sensors 2018, 18, 1633. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.; Ning, Z.; Wang, L. Offloading in Internet of Vehicles: A Fog-enabled Real-time Traffic Management System. IEEE Trans. Ind. Inform. 2018, 14, 4568–4578. [Google Scholar] [CrossRef]
- Yang, C.; Shi, Z.; Han, K.; Zhang, J.; Gu, Y.; Qin, Z. Optimization of Particle CBMeMBer Filters for Hardware Implementation. IEEE Trans. Veh. Technol. 2018, 67, 9027–9031. [Google Scholar] [CrossRef]
- Ding, Z.; Ota, K.; Liu, Y.; Zhang, N.; Zhao, M.; Song, H.; Liu, A.; Cai, Z. Orchestrating Data as Services based Computing and Communication Model for Information-Centric Internet of Things. IEEE Access 2018, 6, 38900–38920. [Google Scholar] [CrossRef]
- Shi, Z.; Zhou, C.; Gu, Y.; Goodman, N.A.; Qu, F. Source estimation using coprime array: A sparse reconstruction perspective. IEEE Sens. J. 2017, 17, 755–765. [Google Scholar] [CrossRef]
- Ren, Y.; Liu, W.; Liu, Y.; Xiong, N.; Liu, A.; Liu, X. An Effective Crowdsourcing Data Reporting Scheme to Compose Cloud-based Services in Mobile Robotic Systems. IEEE Access 2018. [Google Scholar] [CrossRef]
- Zhao, D.; Chin, K.; Raad, W. Approximation algorithms for broadcasting in duty cycled wireless sensor networks. Wirel. Netw. 2014, 20, 2219–2236. [Google Scholar] [CrossRef]
- Hu, X.; Cheng, J.; Zhou, M.; Hu, B.; Jiang, X.; Guo, Y.; Bai, K.; Wang, F. Emotion-aware cognitive system in multi-channel cognitive radio ad hoc networks. IEEE Commun. Mag. 2018, 56, 180–187. [Google Scholar] [CrossRef]
- Hou, W.; Ning, Z.; Hu, X.; Guo, L.; Deng, X.; Yang, Y.; Kwok, R.Y. On-Chip Hardware Accelerator for Automated Diagnosis Through Human-Machine Interactions in Healthcare Delivery. IEEE Trans. Autom. Sci. Eng. 2018, 1–12. [Google Scholar] [CrossRef]
- Zhou, H.; Xu, S.; Ren, D.; Huang, C.; Zhang, H. Analysis of event-driven warning message propagation in vehicular ad hoc networks. Ad Hoc Netw. 2017, 55, 87–96. [Google Scholar] [CrossRef]
- Duc, T.L.; Le, D.T.; Zalyubovskiy, V.V.; Kim, D.S.; Choo, H. Level-based approach for minimum-transmission broadcast in duty-cycled wireless sensor networks. Pervasive Mobile Comput. 2016, 27, 116–132. [Google Scholar] [CrossRef]
- Zhu, H.; Xiao, F.; Sun, L.; Wang, R.; Yang, P. R-TTWD: Robust device-free through-the-wall detection of moving human with WiFi. IEEE J. Sel. Areas Commun. 2017, 35, 1090–1103. [Google Scholar] [CrossRef]
- Liu, X.; Liu, A.; Deng, Q.; Liu, H. Large-scale Programing Code Dissemination for Software Defined Wireless Networks. Comput. J. 2017, 60, 1417–1442. [Google Scholar] [CrossRef]
- Liu, X.; Liu, Y.; Liu, A.; Yang, L. Defending On-Off Attacks using Light Probing Messages in Smart Sensors for Industrial Communication Systems. IEEE Trans. Ind. Inform. 2018, 14, 3801–3811. [Google Scholar] [CrossRef]
- Yu, S.; Liu, X.; Liu, A.; Xiong, N.; Cai, Z.; Wang, T. Adaption Broadcast Radius based Code Dissemination Scheme for Low Energy Wireless Sensor Networks. Sensors 2018, 18, 1509. [Google Scholar] [CrossRef] [PubMed]
- Zhou, C.; Gu, Y.; He, S.; Shi, Z. A robust and efficient algorithm for coprime array adaptive beamforming. IEEE Trans. Veh. Technol. 2018, 67, 1099–1112. [Google Scholar] [CrossRef]
- Liu, X.; Liu, Y.; Xiong, N.; Zhang, N.; Liu, A.; Shen, H.; Huang, C. Construction of Large-scale Low Cost Deliver Infrastructure using Vehicular Networks. IEEE Access 2018, 6, 21482–21497. [Google Scholar] [CrossRef]
- Zhou, H.; Wang, H.; Li, X.; Leung, V. A Survey on Mobile Data Offloading Technologies. IEEE Access 2018, 6, 5101–5111. [Google Scholar] [CrossRef]
- Li, T.; Tian, S.; Liu, A.; Liu, H.; Pei, T. DDSV: Optimizing Delay and Delivery Ratio for Multimedia Big Data Collection in Mobile Sensing Vehicles. IEEE Internet Things J. 2018. [Google Scholar] [CrossRef]
- Ju, X.; Liu, W.; Zhang, C.; Liu, A.; Wang, T.; Xiong, N.; Cai, Z. An Energy Conserving and Transmission Radius Adaptive Scheme to Optimize Performance of Energy Harvesting Sensor Networks. Sensors 2018, 18, 2885. [Google Scholar] [CrossRef] [PubMed]
- Xu, X.; Zhang, N.; Song, H.; Liu, A.; Zhao, M.; Zeng, Z. Adaptive Beaconing based MAC Protocol for Sensor based Wearable System. IEEE Access 2018, 6, 29700–29714. [Google Scholar] [CrossRef]
- Zhang, J.; Hu, X.; Ning, Z.; Ngai, E.; Zhou, L.; Wei, J.; Cheng, J.; Hu, B. Energy-latency Trade-off for Energy-aware Offloading in Mobile Edge Computing Networks. IEEE Internet Things J. 2018, 5, 2633–2645. [Google Scholar] [CrossRef]
- Liu, Z.; Tsuda, T.; Watanabe, H.; Ryuo, S.; Iwasawa, N. Data driven cyber-physical system for landslide detection. Mobile Netw. Appl. 2018, 1–12. [Google Scholar] [CrossRef]
- Zhou, H.; Ruan, M.; Zhu, C.; Leung, V.; Xu, S.; Huang, C. A Time-ordered Aggregation Model-based Centrality Metric for Mobile Social Networks. IEEE Access 2018, 6, 25588–25599. [Google Scholar] [CrossRef]
- Li, T.; Xiong, N.; Gao, J.; Song, H.; Liu, A.; Zeng, Z. Reliable Code Disseminations through Opportunistic Communication in Vehicular Wireless Networks. IEEE Access 2018. [Google Scholar] [CrossRef]
- Nguyen, P.; Ji, Y.; Liu, Z.; Vu, H.; Nguyen, K. Distributed hole-bypassing protocol in WSNs with constant stretch and load balancing. Comput. Netw. 2017, 129, 232–250. [Google Scholar] [CrossRef]
- Xiao, F.; Xie, X.; Li, Z.; Deng, Q.; Liu, A.; Sun, L. Wireless Networks Optimization via Physical Layer Information for Smart Cities. IEEE Netw. 2018, 32, 88–93. [Google Scholar] [CrossRef]
- Wang, T.; Zhang, G.; Liu, A.; Bhuiyan, M.Z.A.; Jin, Q. A Secure IoT Service Architecture with an Efficient Balance Dynamics Based on Cloud and Edge Computing. IEEE Internet Things J. 2018. [Google Scholar] [CrossRef]
- Wang, X.; Ning, Z.; Zhou, M.C.; Hu, X.; Wang, L.; Hu, B.; Kwok, R.Y.K.; Guo, Y. A Privacy-Preserving Message Forwarding Framework for Opportunistic Cloud of Things. IEEE Internet Things J. 2018. [Google Scholar] [CrossRef]
- Ning, Z.; Huang, J.; Wang, X. Vehicular fog computing: Enabling real-time traffic management for smart cities. IEEE Wirel. Commun. 2018. [Google Scholar] [CrossRef]
- Huang, M.; Liu, Y.; Zhang, N.; Xiong, N.; Liu, A.; Zeng, Z.; Song, H. A Services Routing based Caching Scheme for Cloud Assisted CRNs. IEEE Access 2018, 6, 15787–15805. [Google Scholar] [CrossRef]
- Liu, X.; Liu, W.; Liu, Y.; Song, H.; Liu, A.; Liu, X. A Trust and Priority based Code Updated Approach to Guarantee Security for Vehicles Network. IEEE Access 2018. [Google Scholar] [CrossRef]
- Liu, Q.; Liu, A. On the hybrid using of unicast-broadcast in wireless sensor networks. Comput. Electr. Eng. 2017. [Google Scholar] [CrossRef]
- Li, X.; Liu, A.; Xie, M.; Xiong, N.; Zeng, Z.; Cai, Z. Adaptive Aggregation Routing to Reduce Delay for Multi-Layer Wireless Sensor Networks. Sensors 2018, 18, 751. [Google Scholar] [CrossRef] [PubMed]
- Li, Z.; Xiao, F.; Wang, S.; Pei, T.; Li, J. Achievable Rate Maximization for Cognitive Hybrid Satellite-Terrestrial Networks with AF-Relays. IEEE J. Sel. Areas Commun. Spec. Issue Adv. Satell. Commun. 2018, 26, 304–313. [Google Scholar] [CrossRef]
- Liu, X. Node deployment based on extra path creation for wireless sensor networks on mountain roads. IEEE Commun. Lett. 2017, 21, 2376–2379. [Google Scholar] [CrossRef]
- Chen, X.; Pu, L.; Gao, L.; Wu, W.; Wu, D. Exploiting massive D2D collaboration for energy-efficient mobile edge computing. IEEE Wirel. Commun. 2017, 24, 64–71. [Google Scholar] [CrossRef]
- Fang, S.; Cai, Z.; Sun, W.; Liu, A.; Liu, F.; Liang, Z.; Wang, G. Feature Selection Method Based on Class Discriminative Degree for Intelligent Medical Diagnosis. CMC: Comput. Mater. Contin. 2018, 55, 419–433. [Google Scholar]
- Xiao, F.; Chen, L.; Sha, C.; Sun, L.; Wang, R.; Liu, A.X.; Ahmed, F. Noise Tolerant Localization for Sensor Networks. IEEE/ACM Trans. Netw. 2018, 26, 1701–1714. [Google Scholar] [CrossRef]
- Huang, M.; Liu, A.; Zhao, M.; Wang, T. Multi Working Sets Alternate Covering Scheme for Continuous Partial Coverage in WSNs. Peer-to-Peer Netw. Appl. 2018, 1–15. [Google Scholar] [CrossRef]
- Liu, A.; Zhao, S. High performance target tracking scheme with low prediction precision requirement in WSNs. Int. J. Ad Hoc Ubiquitous Comput. 2017. Available online: http://www.inderscience.com/info/ingeneral/forthcoming.php?jcode=ijahuc (accessed on 23 May 2018).
- Zhou, C.; Gu, Y.; Fan, X.; Shi, Z.; Mao, G.; Zhang, Y. Direction-of-arrival estimation for coprime array via virtual array interpolation. IEEE Trans. Signal Process 2018, 2018, 6425067. [Google Scholar] [CrossRef]
- Pu, L.; Chen, X.; Xu, J.; Fu, X. D2D fogging: An energy-efficient and incentive-aware task offloading framework via networks-assisted D2D collaboration. IEEE J. Sel. Areas Commun. 2016, 34, 3887–3901. [Google Scholar] [CrossRef]
- Liu, X.; Dong, M.; Ota, K.; Yang, L.T.; Liu, A. Trace malicious source to guarantee cyber security for mass monitor critical infrastructure. J. Comput. Syst. Sci. 2016, 98, 1–26. [Google Scholar] [CrossRef]
- Huang, B.; Liu, A.; Zhang, C.; Xiong, N.; Zeng, Z.; Cai, Z. Caching Joint Shortcut Routing to Improve Quality of Experiments of Users for Information-Centric Networksing. Sensors 2018, 18, 1750. [Google Scholar] [CrossRef] [PubMed]
- Li, Z.; Liu, Y.; Ma, M.; Liu, A.; Zhang, X.; Luo, G. MSDG: A Novel Green Data Gathering Scheme for Wireless Sensor Networks. Comput. Netw. 2018, 142, 223–239. [Google Scholar] [CrossRef]
- Galzarano, S.; Savaglio, C.; Liotta, A.; Fortino, G. Gossiping-based aodv for wireless sensor networks. In Proceedings of the 2013 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Manchester, UK, 13–16 October 2013; pp. 26–31. [Google Scholar]
- Li, X.; Liu, W.; Xie, M.; Liu, A.; Zhao, M.; Xiong, N.; Zhao, M.; Dai, W. Differentiated Data Aggregation Routing Scheme for Energy Conserving and Delay Sensitive Wireless Sensor Networks. Sensors 2018, 18, 2349. [Google Scholar] [CrossRef] [PubMed]
- Kim, C.; Shin, D.H. A Formal Approach to the Selection by Minimum Error and Pattern Method for Sensor Data Loss Reduction in Unstable Wireless Sensor Networks Communications. Sensors 2017, 17, 1092. [Google Scholar]
- Liu, Y.; Liu, A.; Chen, Z. Analysis and Improvement of Send-and-Wait Automatic Repeat-reQuest protocols for Wireless Sensor Networks. Wirel. Pers. Commun. 2015, 81, 923–959. [Google Scholar] [CrossRef]
- Cheng, L.; Niu, J.; Luo, C.; Shu, L.; Kong, L.; Zhao, Z.; Gu, Y. Towards minimum-delay and energy-efficient flooding in low-duty-cycle wireless sensor networks. Comput. Netw. 2018, 134, 66–77. [Google Scholar] [CrossRef]
- Li, T.; Liu, Y.; Xiong, N.; Liu, A.; Cai, Z.; Song, H. Privacy-Preserving Protocol of Sink Node Location in Telemedicine Networks. IEEE Access 2018, 6, 42886–42903. [Google Scholar] [CrossRef]
- Ning, Z.; Kong, X.; Xia, F.; Hou, W.; Wang, X. Green and Sustainable Cloud of Things: Enabling Collaborative Edge Computing. IEEE Commun. Mag. 2018. [Google Scholar] [CrossRef]
- Ren, Y.; Liu, Y.; Zhang, N.; Liu, A.; Xiong, N.; Cai, Z. Minimum-Cost Mobile Crowdsourcing with QoS Guarantee Using Matrix Completion Technique. Pervasive Mobile Comput. 2018, 49, 23–44. [Google Scholar] [CrossRef]
- Gui, J.; Deng, J. Multi-hop Relay-Aided Underlay D2D Communications for Improving Cellular Coverage Quality. IEEE Access 2018, 6, 14318–14338. [Google Scholar] [CrossRef]
- Luo, X.; Lv, Y.; Zhou, M.; Wang, W.; Zhao, W. A laguerre neural networks-based ADP learning scheme with its application to tracking control in the Internet of Things. Pers. Ubiquitous Comput. 2016, 20, 361–372. [Google Scholar] [CrossRef]
- Molina, B.; Palau, C.E.; Fortino, G.; Guerrieri, A.; Savaglio, C. Empowering smart cities through interoperable Sensor Network Enablers. In Proceedings of the 2014 IEEE International Conference on Systems, Man and Cybernetics (SMC), San Diego, CA, USA, 5–8 October 2014; pp. 7–12. [Google Scholar]
- Savaglio, C.; Fortino, G. Autonomic and cognitive architectures for the Internet of Things. In Proceedings of the International Conference on Internet and Distributed Computing Systems, Windsor, UK, 2–4 September 2015; Springer: Cham, Switzerland, 2015; pp. 39–47. [Google Scholar]
- Clark, B.N.; Colbourn, C.J.; Johnson, D.S. Unit disk graphs. Discret. Math. 1990, 86, 165–177. [Google Scholar] [CrossRef]
- Guha, S.; Khuller, S. Approximation algorithms for connected dominating sets. Algorithmica 1998, 20, 374–387. [Google Scholar] [CrossRef]
- Lim, H.; Kim, C. Flooding in wireless ad hoc networks. Comput. Commun. 2001, 24, 353–363. [Google Scholar] [CrossRef]
- Khiati, M.; Djenouri, D. BOD-LEACH: Broadcasting over duty-cycled radio using LEACH clustering for delay/power efficient dissimilation in wireless sensor networks. Int. J. Commun. Syst. 2015, 28, 296–308. [Google Scholar] [CrossRef]
- Guo, L.; Ning, Z.; Hou, W.; Hu, B.; Guo, P. Quick Answer for Big Data in Sharing Economy: Innovative Computer Architecture Design Facilitating Optimal Service-Demand Matching. IEEE Trans. Autom. Sci. Eng. 2018, 15, 1494–1506. [Google Scholar] [CrossRef]
- Pooranian, Z.; Barati, A.; Movaghar, A. Queen-bee algorithm for energy efficient clusters in wireless sensor networks. World Acad. Sci. Eng. Technol. 2011, 73, 1080–1083. [Google Scholar]
- Naranjo, P.G.V.; Shojafar, M.; Mostafaei, H.; Pooranian, Z.; Baccarelli, E. P-SEP: A prolong stable election routing algorithm for energy-limited heterogeneous fog-supported wireless sensor networks. J. Supercomput. 2017, 73, 733–755. [Google Scholar] [CrossRef]










| Symbol | Meaning | Value |
|---|---|---|
| the number of slots in a cycle | decided when computing | |
| the number of source nodes in the networks | decided when computing | |
| possibility of successful single transmission | decided when computing | |
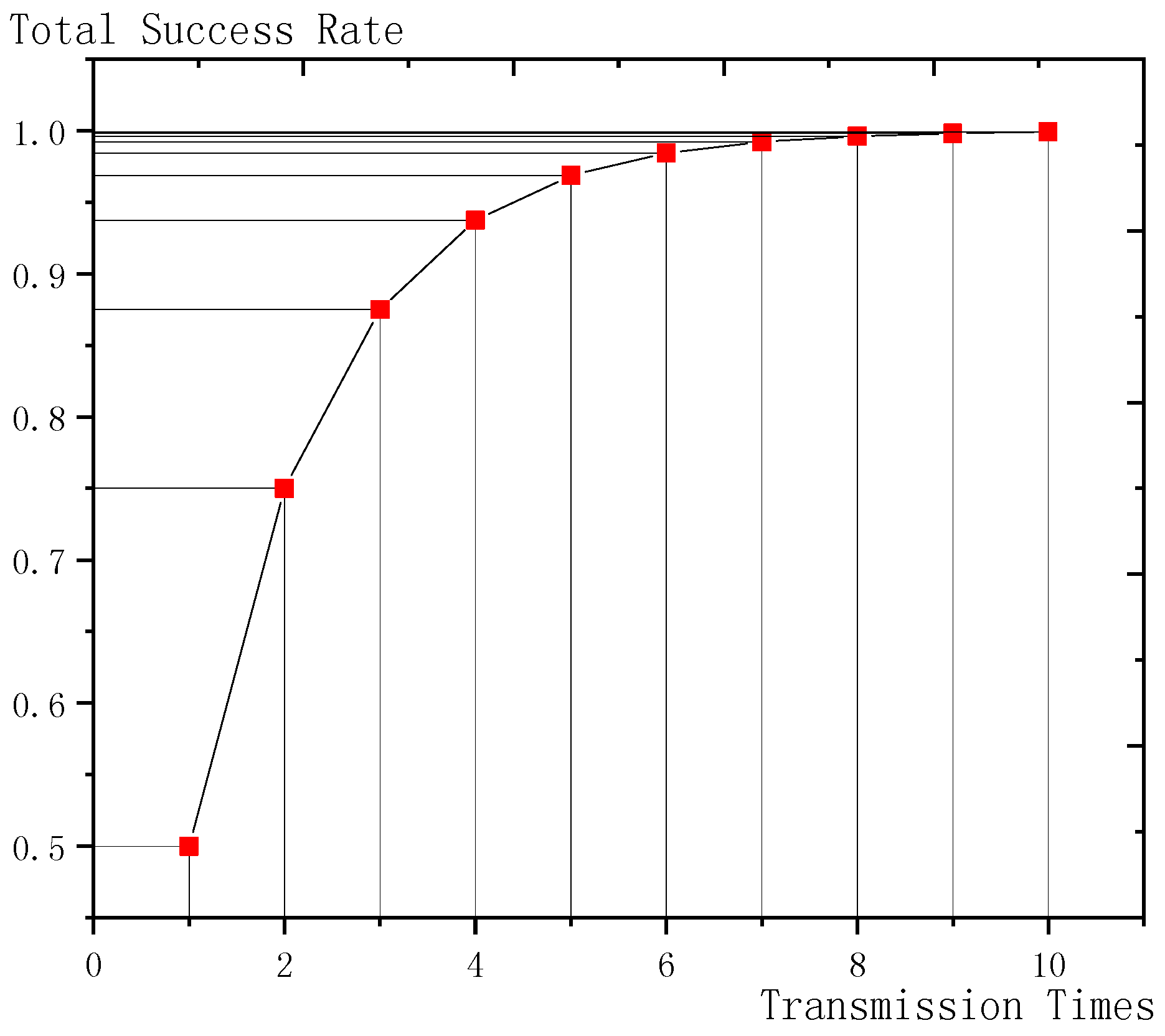
| total successful transmission possibility threshold | decided when computing | |
| maximum transmission times | decided when computing | |
| the energy required to send a packet | 0.5 J | |
| the energy required to receive a packet | 0.4 J | |
| the energy required when node wakes up to detect whether it needs to receive the packet | 0.1 J |
| 16 | 12 | 23 | 40 | 28 | 39 | 32 | 28 | 40 | 36 |
| 47 | 64 | 52 | 63 | 48 | 44 | 47 | 56 | 52 | 56 |
| 44 | 48 | 44 | 64 | 52 | 56 | 52 | 64 | 60 | 71 |
| 7 | 7 | 23 | 15 | 15 | 31 | 16 | 20 | 31 | 31 |
| 47 | 23 | 23 | 39 | 23 | 23 | 39 | 40 | 44 | 32 |
| 28 | 32 | 36 | 40 | 44 | 40 | 44 | 55 | 55 | 71 |
| 7 | 7 | 7 | 15 | 15 | 15 | 24 | 28 | 15 | 15 |
| 15 | 23 | 23 | 23 | 23 | 23 | 23 | 24 | 28 | 40 |
| 36 | 40 | 44 | 24 | 28 | 24 | 28 | 23 | 23 | 23 |
| 7 | 7 | 23 | 12 | 11 | 15 | 16 | 12 | 28 | 27 |
| 31 | 16 | 15 | 17 | 16 | 15 | 15 | 22 | 19 | 22 |
| 24 | 19 | 16 | 35 | 32 | 35 | 32 | 35 | 33 | 36 |
| Setting | ||
|---|---|---|
| 1 | 0.99 | 0.9 |
| 2 | 0.99 | 0.8 |
| 3 | 0.99 | 0.7 |
| Setting | ||
|---|---|---|
| 1 | 15 | 0.99 |
| 2 | 15 | 0.95 |
| 3 | 15 | 0.90 |
| Setting | ||
|---|---|---|
| 1 | 15 | 0.8 |
| 2 | 15 | 0.7 |
| 3 | 15 | 0.6 |
| IFAS (Setting 1, Setting 2, Setting 3) | BTAS (Setting 1, Setting 2, Setting 3) | AAPS (Setting 1, Setting 2, Setting 3) | |
|---|---|---|---|
| 10 | 5.36%, 10.43%, 14.56% | 20.94%, 25.88%, 29.89% | 44.51%, 49.64%, 53.89% |
| 15 | 5.29%, 10.75%, 15.24% | 12.39%, 19.24%, 24.88% | 36.19%, 42.87%, 48.56% |
| 20 | 6.01%, 11.55%, 16.08% | 15.37%, 21.68%, 26.88% | 31.60%, 38.20%, 43.74% |
| IFAS (Setting 1, Setting 2, Setting 3) | BTAS (Setting 1, Setting 2, Setting 3) | AAPS (Setting 1, Setting 2, Setting 3) | |
|---|---|---|---|
| 0.9 | 5.29%, 5.29%, 0.00% | 12.39%, 12.39%, 5.94% | 36.19%, 36.19%, 29.35% |
| 0.8 | 10.75%, 8.61%, 8.61% | 19.24%, 16.60%, 16.60% | 42.87%, 40.13%, 40.13% |
| 0.7 | 15.24%, 14.15%, 10.93% | 24.88%, 23.55%, 19.62% | 48.56%, 46.93%, 42.73% |
| 0.6 | 19.24%, 18.25%, 16.69% | 29.81%, 28.68%, 26.79% | 53.77%, 52.32%, 49.87% |
| 0.5 | 22.25%, 21.45%, 20.56% | 33.48%, 32.54%, 31.59% | 57.72%, 56.55%, 55.16% |
| IFAS (Setting 1, Setting 2, Setting 3) | BTAS (Setting 1, Setting 2, Setting 3) | AAPS (Setting 1, Setting 2, Setting 3) | |
|---|---|---|---|
| 0.99 | 10.75%, 15.24%, 19.24% | 19.24%, 24.88%, 29.81% | 42.87%, 48.56%, 53.77% |
| 0.95 | 8.61%, 14.45%, 18.25% | 16.60%, 23.55%, 28.68% | 40.13%, 46.93%, 52.32% |
| 0.90 | 8.61%, 10.93%, 16.69% | 16.60%, 19.62%, 26.79% | 40.13%, 42.73%, 49.88% |
| IFAS (Setting 1, Setting 2, Setting 3) | BTAS (Setting 1, Setting 2, Setting 3) | AAPS (Setting 1, Setting 2, Setting 3) | |
|---|---|---|---|
| 10 | 20.73%, 21.06%, 24.16% | 37.85%, 38.39%, 41.21% | 31.94%, 32.97%, 35.25% |
| 15 | 21.13%, 23.66%, 26.33% | 37.24%, 40.12%, 42.26% | 30.23%, 36.68%, 41.48% |
| 20 | 25.45%, 25.45%, 29.53% | 38.50%, 38.50%, 41.93% | 30.19%, 30.19%, 32.15% |
| IFAS (Setting 1, Setting 2, Setting 3) | BTAS (Setting 1, Setting 2, Setting 3) | AAPS (Setting 1, Setting 2, Setting 3) | |
|---|---|---|---|
| 0.9 | 21.11%, 21.11%, 0.00% | 37.24%, 37.24%, 16.09% | 30.23%, 30.23%, −2.29% |
| 0.8 | 23.66%, 22.18%, 22.18% | 40.12%, 38.20%, 38.20% | 36.68%, 30.38%, 30.38% |
| 0.7 | 26.33%, 24.73%, 22.55% | 42.26%, 40.76%, 38.59% | 41.48%, 36.36%, 29.97% |
| 0.6 | 25.16%, 27.95%, 24.95% | 41.29%, 43.39%, 40.76% | 40.00%, 42.04%, 35.14% |
| 0.5 | 26.37%, 26.47%, 28.72% | 42.08%, 41.20%, 43.93% | 40.61%, 39.83%, 41.77% |
| IFAS (Setting 1, Setting 2, Setting 3) | BTAS (Setting 1, Setting 2, Setting 3) | AAPS (Setting 1, Setting 2, Setting 3) | |
|---|---|---|---|
| 0.99 | 23.66%, 26.33%, 25.16% | 40.12%, 42.26%, 41.29% | 36.68%, 41.48%, 40.00% |
| 0.95 | 22.18%, 24.73%, 27.95% | 38.20%, 40.76%, 43.39% | 30.38%, 36.36%, 42.04% |
| 0.90 | 22.18%, 22.55%, 24.95% | 38.20%, 38.59%, 40.76% | 30.38%, 29.97%, 35.14% |
| IFAS (Setting 1, Setting 2, Setting 3) | BTAS (Setting 1, Setting 2, Setting 3) | AAPS (Setting 1, Setting 2, Setting 3) | |
|---|---|---|---|
| 10 | 15.12%, 16.91%, 20.44% | 27.61%, 30.83%, 34.87% | 23.29%, 26.47%, 29.83% |
| 15 | 15.40%, 18.97%, 22.25% | 27.16%, 32.17%, 35.71% | 22.05%, 29.41%, 35.04% |
| 20 | 20.55%, 20.55%, 25.10% | 31.09%, 31.09%, 35.64% | 24.38%, 24.38%, 27.33% |
| IFAS (Setting 1, Setting 2, Setting 3) | BTAS (Setting 1, Setting 2, Setting 3) | AAPS (Setting 1, Setting 2, Setting 3) | |
|---|---|---|---|
| 0.9 | 15.40%, 15.40%, 0.00% | 27.16%, 27.16%, 6.86% | 22.05%, 22.05%, −0.97% |
| 0.8 | 18.97%, 15.82%, 15.82% | 32.17%, 27.24%, 27.24% | 29.41%, 21.67%, 21.67% |
| 0.7 | 22.25%, 19.67%, 15.45% | 35.71%, 32.43%, 26.44% | 35.04%, 28.93%, 20.53% |
| 0.6 | 22.38%, 23.50%, 19.43% | 36.73%, 36.49%, 31.74% | 35.58%, 35.36%, 27.36% |
| 0.5 | 23.86%, 22.89%, 23.76% | 38.07%, 35.64%, 36.34% | 36.75%, 34.45%, 34.56% |
| IFAS (Setting 1, Setting 2, Setting 3) | BTAS (Setting 1, Setting 2, Setting 3) | AAPS (Setting 1, Setting 2, Setting 3) | |
|---|---|---|---|
| 0.99 | 18.97%, 22.25%, 22.38% | 32.17%, 35.71%, 36.73% | 29.41%, 35.04%, 35.58% |
| 0.95 | 15.82%, 19.67%, 23.50% | 27.24%, 32.43%, 36.49% | 21.67%, 28.93%, 35.36% |
| 0.90 | 15.82%, 15.45%, 19.43% | 27.24%, 26.44%, 31.74% | 21.67%, 20.53%, 27.36% |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qi, W.; Liu, W.; Liu, X.; Liu, A.; Wang, T.; Xiong, N.N.; Cai, Z. Minimizing Delay and Transmission Times with Long Lifetime in Code Dissemination Scheme for High Loss Ratio and Low Duty Cycle Wireless Sensor Networks. Sensors 2018, 18, 3516. https://doi.org/10.3390/s18103516
Qi W, Liu W, Liu X, Liu A, Wang T, Xiong NN, Cai Z. Minimizing Delay and Transmission Times with Long Lifetime in Code Dissemination Scheme for High Loss Ratio and Low Duty Cycle Wireless Sensor Networks. Sensors. 2018; 18(10):3516. https://doi.org/10.3390/s18103516
Chicago/Turabian StyleQi, Wei, Wei Liu, Xuxun Liu, Anfeng Liu, Tian Wang, Neal N Xiong, and Zhiping Cai. 2018. "Minimizing Delay and Transmission Times with Long Lifetime in Code Dissemination Scheme for High Loss Ratio and Low Duty Cycle Wireless Sensor Networks" Sensors 18, no. 10: 3516. https://doi.org/10.3390/s18103516
APA StyleQi, W., Liu, W., Liu, X., Liu, A., Wang, T., Xiong, N. N., & Cai, Z. (2018). Minimizing Delay and Transmission Times with Long Lifetime in Code Dissemination Scheme for High Loss Ratio and Low Duty Cycle Wireless Sensor Networks. Sensors, 18(10), 3516. https://doi.org/10.3390/s18103516








