Frame Transmission Efficiency-Based Cross-Layer Congestion Notification Scheme in Wireless Ad Hoc Networks
Abstract
:1. Introduction
2. Wireless Channel Congestion Detection
- (1)
- Retransmission counter: There exists a correlation between the number of RTS (Request to Send) retransmissions and channel congestion extent at the MAC layer [16,17]. In [4], when the number of RTS retransmissions is greater than two, the wireless channel will be deemed as congested, and the TCP sender will decrease its sending rate. Though this method is very easy to deploy, the number of RTS retransmissions is not able to describe the congestion state accurately.
- (2)
- Frame Service Delay (FSD): The frame service delay is the interval from the time that the MAC layer begins to sense the channel for data transmission to the time that the acknowledgment is received successfully, which includes collision time and transmission time [18]. The greater the service delay is, the higher the probability of network congestion is. However, the hops that the flows are traveling through and the frame size greatly affect the service delay. Subsequently, the threshold value of the service delay is difficult to determine, resulting in the inaccuracy of congestion estimation.
- (3)
3. Definition and Theory Analysis
3.1. Definition
3.2. Theory Analysis
- (1)
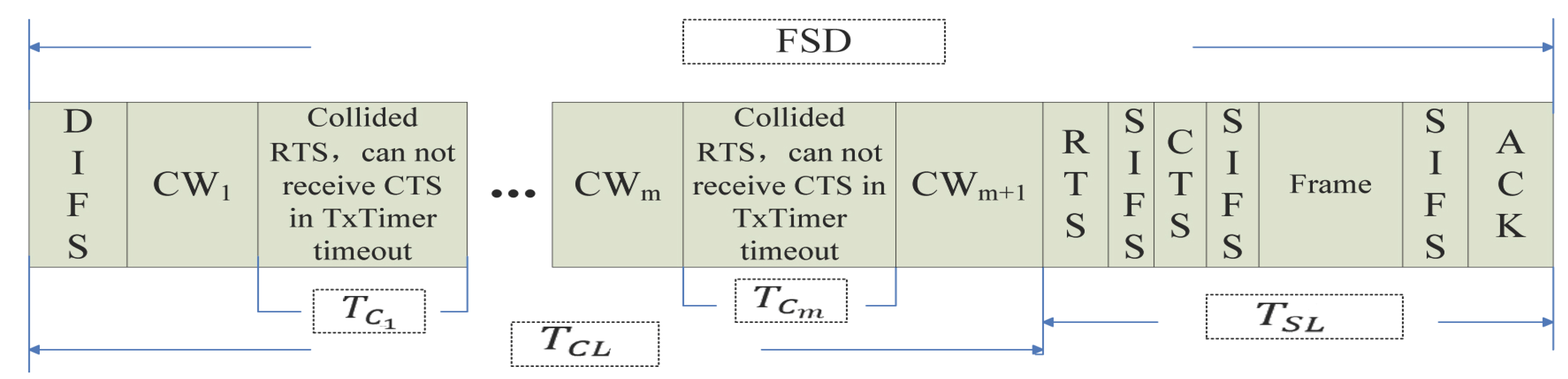
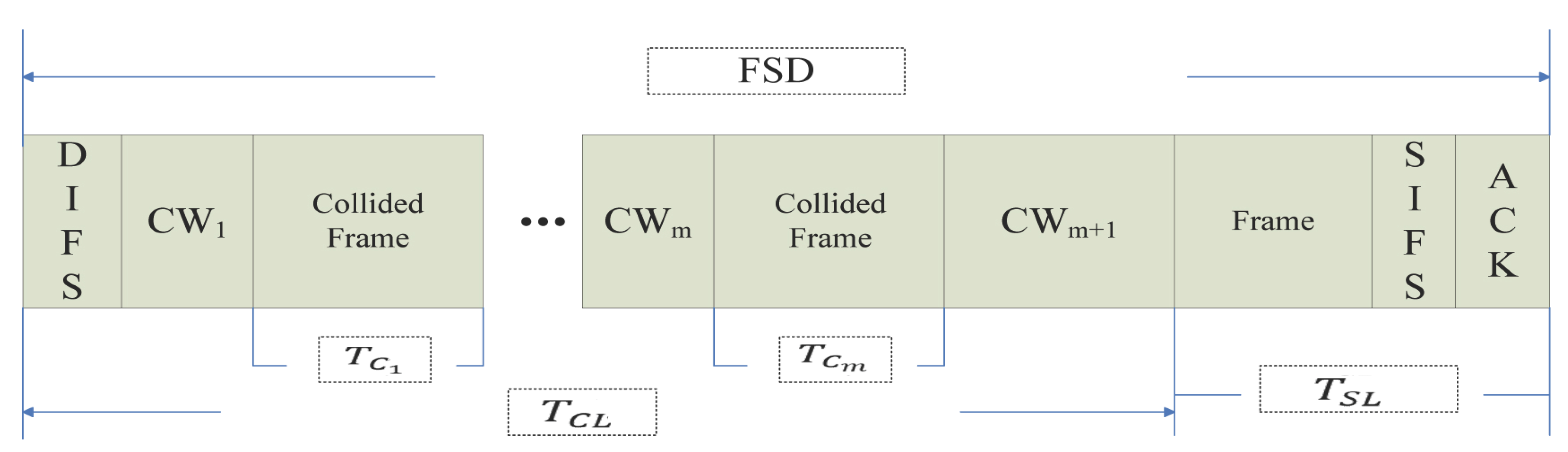
- The numerical value of : As we can see in Figure 1 and Figure 2, the time that a frame is successfully transmitted with the RTS/CTS mechanism is:where is the time of the data frame transmission. The time that a frame is successfully transmitted while using the basic access mechanism is:According to the system parameters, is 10 s. The lengths of RTS, CTS and ACK are 160 bits, 112 bits and 112 bits, respectively. Thus, is determined by the size of the data frame and is independent of the number of collisions, that is = . If the size of the data frame is determined, will be a constant value.
- (2)
- The numerical value of : The numerical value of is:where:where is the total time of congestion. is the time of each congestion. is the time of congestion waiting. N is the number of collisions, and the range of N is period [1, m], where m is the maximum number of collisions.
4. Protocol Design
| { |
| // calculating total transmission time (including data packet, ACK delay and propagation delay) |
| ; |
| // recording the current time |
| bt = now; |
| ; //st is the beginning time for transmitting. |
| if // threshold is a given value. |
| set CE bit to 1; // mark ECN bit |
| } |
5. Performance Evaluation
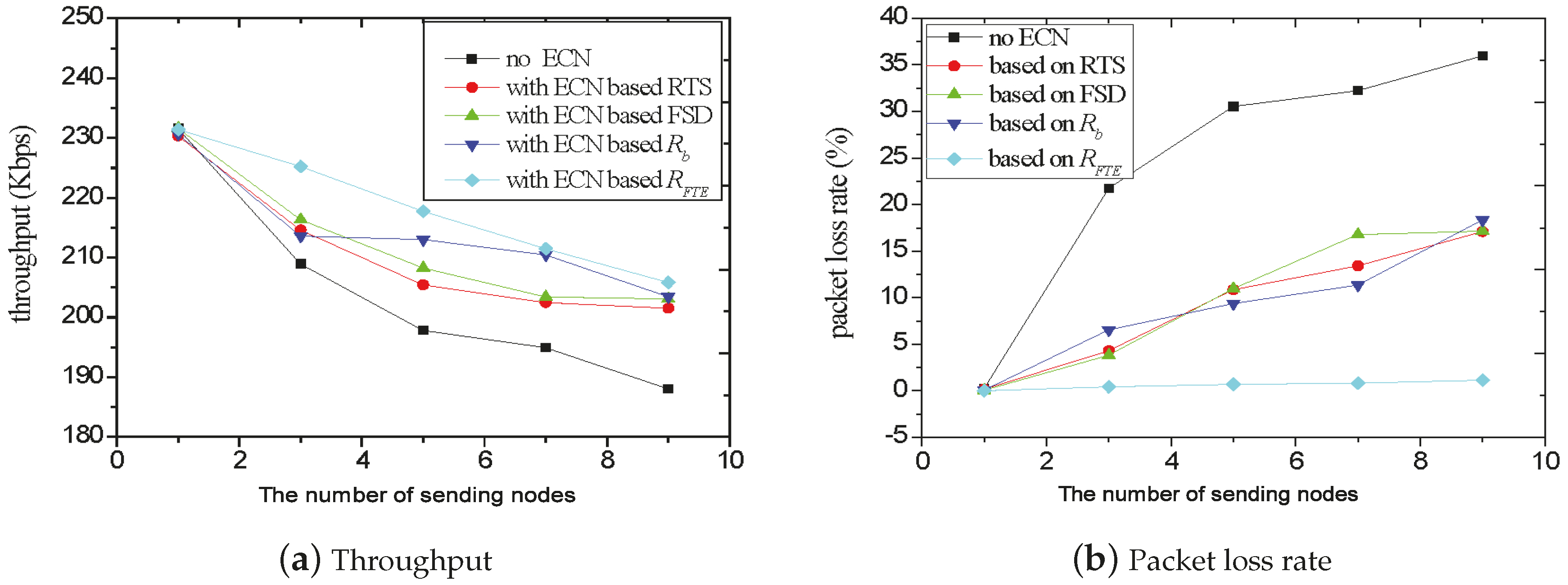
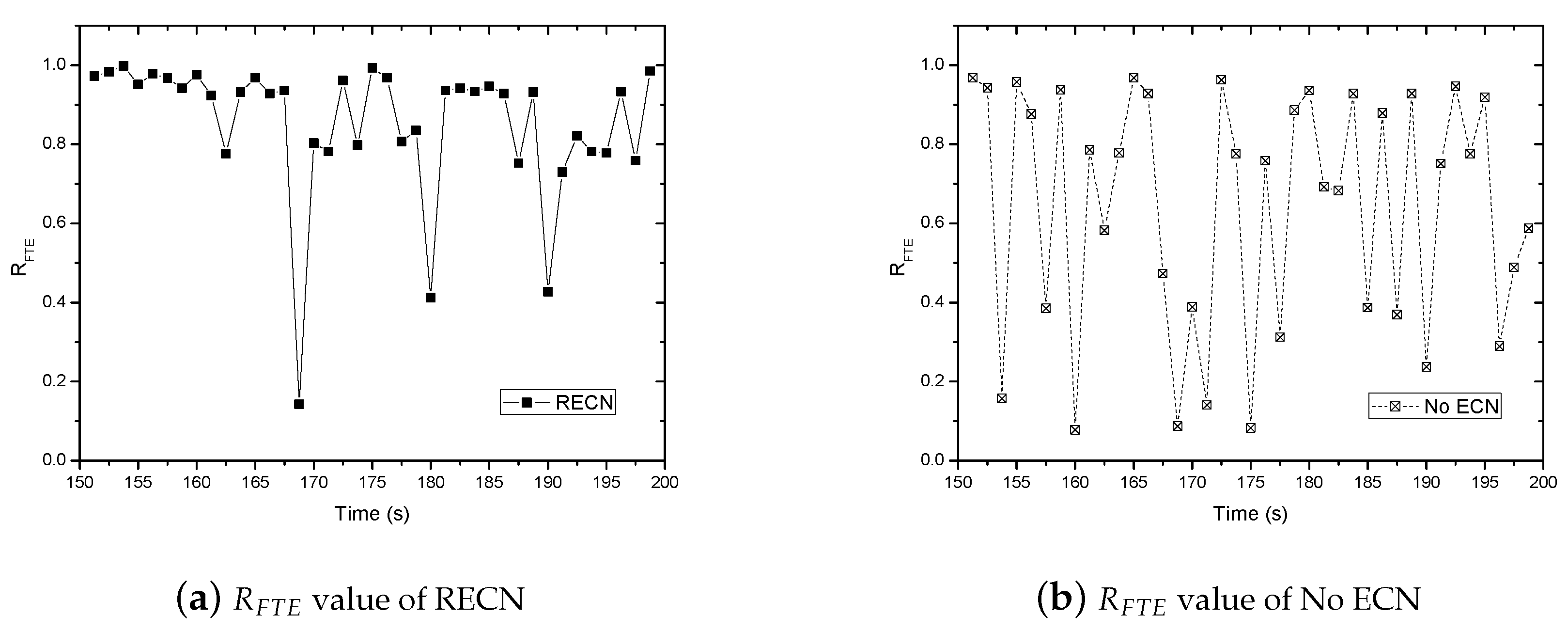
5.1. Comparison with Other Metrics
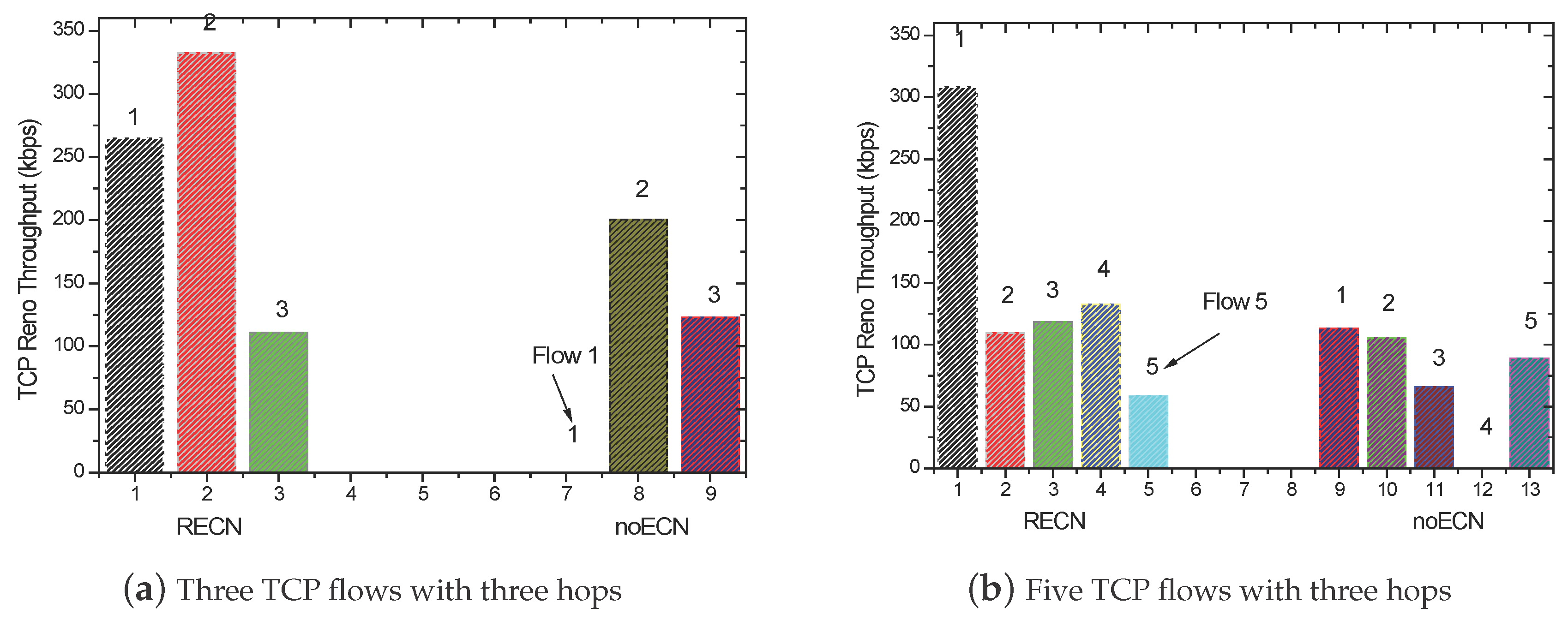
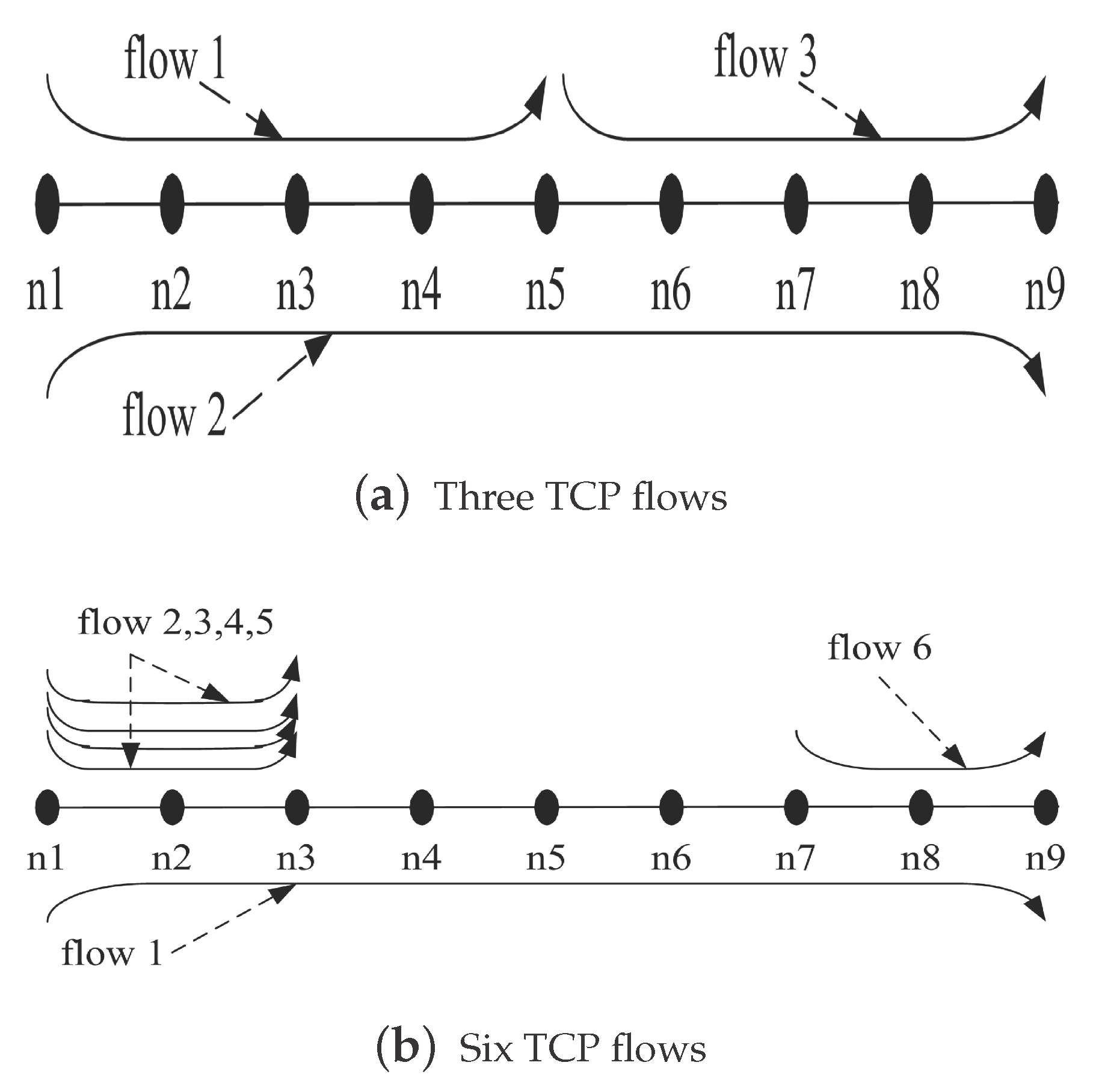
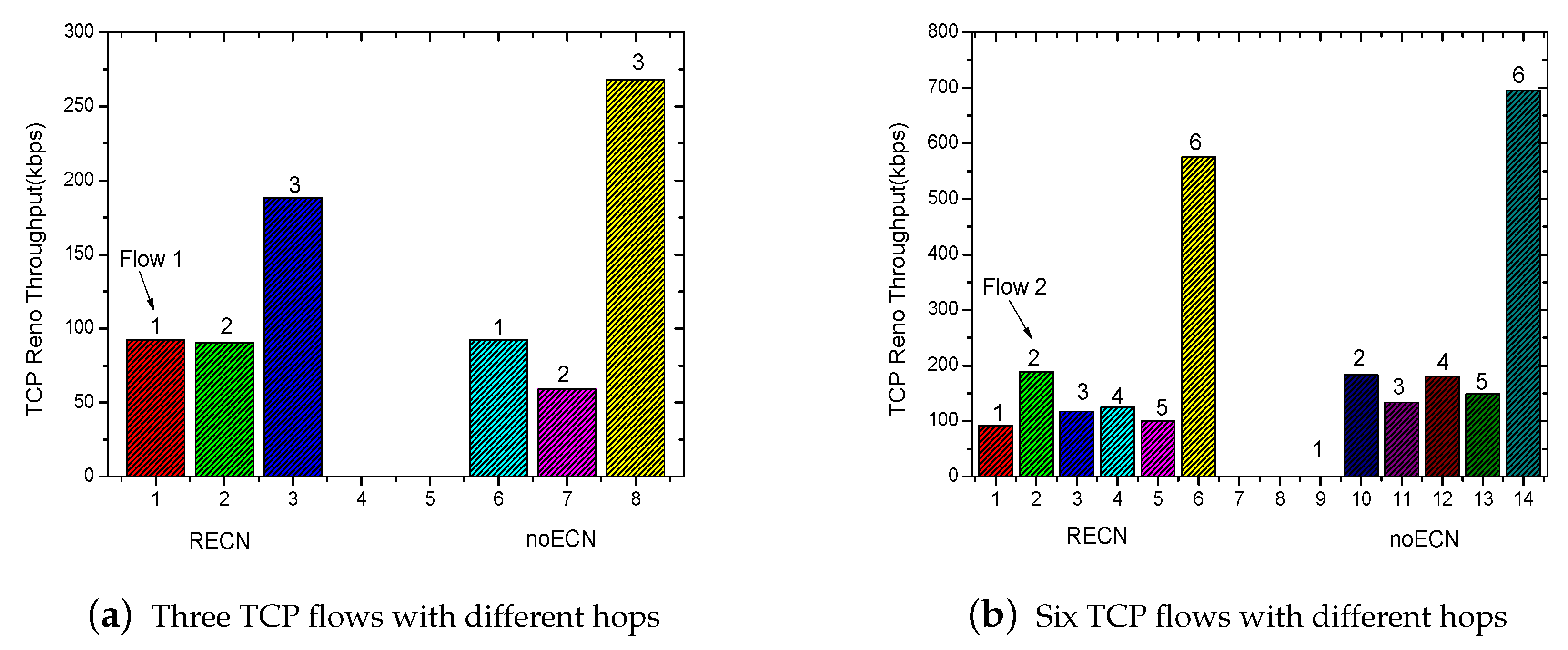
5.2. TCP Throughput
5.3. Fairness Analysis
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Yan, G.; Wang, J. Survey of TCP improvement over multi-hop wireless and wired hybrid networks. J. Comput. Res. Develop. 2009, 46, 738–746. [Google Scholar]
- Fu, Z.; Zrefos, P.; Luo, H.; Lu, S.; Zhang, L.; Gerla, M. The impact of multihop wireless channel on TCP throughput and loss. In Proceedings of the IEEE INFOCOM 2003. Twenty-Second Annual Joint Conference of the IEEE Computer and Communications Societies, San Francisco, CA, USA, 30 March–3 April 2003; Volume 3, pp. 1744–1753. [Google Scholar]
- Zhang, X.; Dai, Z.; Zhu, H. Channel reservation based on contention and interference in wireless ad hoc networks. In Proceedings of the IEEE International Conference on Computer Communication and Networks, Honolulu, HI, USA, 3–6 February 2014; pp. 1–8. [Google Scholar]
- Raghunathan, V.; Kumar, P.R. A counterexample in congestion control of wireless networks. Perform. Eval. 2007, 64, 399–418. [Google Scholar] [CrossRef]
- Mezzavilla, M.; Quer, G.; Zorzi, M. On the effects of cognitive mobility prediction in wireless multi-hop ad hoc networks. In Proceedings of the IEEE International Conference on Communications, Sydney, Australia, 10–14 June 2014; pp. 1638–1644. [Google Scholar]
- Zhang, X.; Yang, B.; Ma, Y. TCP congestion control based on accurate bandwidth-delay product in wireless Ad hoc networks. In Proceedings of the 23rd International Conference on Computer Communication and Networks, Shanghai, China, 4–7 August 2014; pp. 1–7. [Google Scholar]
- Kaushik, S.K.; Chahal, K.; Dhariwal, S.; Kumar, A.; Raj, P. Analysis of TCP Performance over Mobile Ad Hoc Networks with Varying Speed. In Proceedings of the 2012 International Conference on Computing Sciences, Phagwara, India, 14–15 September 2012; pp. 193–200. [Google Scholar]
- Duong, L.M.; Zitoune, L.; Véque, V. MAC-aware rate control for transport protocol in multihop wireless networks. In Proceedings of the IEEE 23rd International Symposium on Personal Indoor and Mobile Radio Communications, Sydney, Australia, 9–12 September 2012; pp. 1436–1441. [Google Scholar]
- Ye, J.; Wang, J.; Liu, Q.; Luo, Y. An Improved TCP with Cross-layer Congestion Notification over Wired/Wireless Hybrid Networks. In Proceedings of the 9th International Conference for Young Computer Scientists, Hunan, China, 18–21 November 2008; pp. 368–373. [Google Scholar]
- Yue, P.; Wen, A.J.; Zhao, R.Q.; Liu, Z.J. Frame service delay analysis of IEEE 802.11 MAC protocol and its application in congestion control. J. Xidian Univ. 2008, 3, 5. [Google Scholar]
- Feng, K.T.; Lin, J.S.; Lei, W.N. Design and Analysis of Adaptive Receiver Transmission Protocols for Receiver Blocking Problem in Wireless Ad Hoc Networks. IEEE Trans. Mob. Comput. 2013, 12, 1651–1668. [Google Scholar] [CrossRef]
- Liu, Y.; Li, V.O.K.; Leung, K.C.; Zhang, L. Performance Improvement of Topology-Transparent Broadcast Scheduling in Mobile Ad Hoc Networks. IEEE Trans. Veh. Technol. 2014, 63, 4594–4605. [Google Scholar] [CrossRef]
- Tuan, N.M.; Nakagawa, K.; Watabe, K. A Method at Link Layer to Improve the Fairness in Multi-hop Wireless Ad Hoc Networks. In Proceedings of the Sixth ACM International Symposium on Information and Communication Technology, Cape Town, South Africa, 7–10 December 2015; pp. 135–142. [Google Scholar]
- Zhai, H.; Chen, X.; Fang, Y. Improving Transport Layer Performance in Multihop Ad Hoc Networks by Exploiting MAC Layer Information. IEEE Trans. Wirel. Commun. 2007, 6, 1692–1701. [Google Scholar] [CrossRef]
- Yahia, M. Enhanced congestion control for TCP fairness in ad hoc wireless networks. In Proceedings of the 7th IEEE Conference on Industrial Electronics and Applications (ICIEA), Singapore, 18–20 July 2012; pp. 669–675. [Google Scholar]
- Zhai, H.; Chen, X.; Fang, Y. How well can the IEEE 802.11 wireless LAN support quality of service? IEEE Trans. Wirel. Commun. 2005, 4, 3084–3094. [Google Scholar] [CrossRef]
- IEEE Standard Association. IEEE Standards Interpretation for IEEE Std 802.11™ —Telecommunications and Information Exchange Between Systems—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. Available online: http://standards.ieee.org/findstds/interps/802.11-2007.html (accessed on 11 July 2017).
- Hegde, M.; Kumar, P.; Vasudev, K.R.; Sowmya, N.N.; Anand, S.V.R.; Kumar, A.; Kuri, J. Experiences with a centralized scheduling approach for performance management of IEEE 802.11 wireless LANs. IEEE/ACM Trans. Netw. 2009, 21, 648–662. [Google Scholar] [CrossRef]
- Bianchi, G. Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun. 2006, 18, 535–547. [Google Scholar] [CrossRef]
- Floyd, S. TCP and explicit congestion notification. ACM Sigcomm Comput. Commun. Rev. 1994, 24, 8–23. [Google Scholar] [CrossRef]
- Kim, B.C.; Choi, Y.S.; Cho, Y.Z. A New Packet Marking Strategy for Explicit Congestion Notification in the Internet. IEEE Int. Conf. Commun. 2002, 4, 2330–2334. [Google Scholar]
- Harhalakis, S.; Samaras, N.; Vitsas, V. An Experimental Study of the Efficiency of Explicit Congestion Notification. In Proceedings of the 15th Panhellenic Conference on Informatics, Kastonia, Greece, 30 September–2 October 2011; pp. 122–126. [Google Scholar]
- Dappuri, B.; Venkatesh, T.G. IEEE 802.11 DCF MAC protocol for cognitive radio networks: Cooperative basic access Vs RTS/CTS. In Proceedings of the 14th International Symposium on Communications and Information Technologies, Incheon, South Korea, 24–26 September 2014; pp. 45–50. [Google Scholar]
- VINT Project UC Berkeley/LBNL. NS2: Network Simulator. Available online: http://ee.lbl.gov/ns/#version2 (accessed on 11 July 2017).
- Swenson, B.P.; Riley, G.F. Implementing explicit congestion notification in ns-3. In Proceedings of the 2014 Workshop on ns-3, Atlanta, GA, USA, 7 May 2014; Volume 5, pp. 1–8. [Google Scholar]
- Joy, S.; Nayak, A. SDN based ECN adaptation scheme for improving data center long flow throughput. In Proceedings of the IEEE International Conference on Communication Workshop, London, UK, 8–12 June 2015; pp. 1545–1550. [Google Scholar]
- Li, D.; Li, S.; Du, Z. Session-aware congestion control for TCP Incast in datacenter networks. In Proceedings of the 2016 IEEE Symposium on Computers and Communication, Messina, Italy, 27–30 June 2016; pp. 1227–1232. [Google Scholar]
- Silva, R.F.E.; Carpenter, P.M. Controlling Network Latency in Mixed Hadoop Clusters: Do We Need Active Queue Management? In Proceedings of the IEEE 41st Conference on Local Computer Networks, Dubai, United Arab Emirates, 7–10 November 2016; pp. 415–423. [Google Scholar]
- Lee, C.; Nakagawa, Y.; Hyoudou, K.; Kobayashi, S.; Shiraki, O.; Shimizu, T. Flow-Aware Congestion Control to Improve Throughput under TCP Incast in Datacenter Networks. In Proceedings of the IEEE 39th Annual Computer Software and Applications Conference, Taichung, Taiwan, 1–5 July 2015; pp. 155–162. [Google Scholar]

| Parameters | Setting |
|---|---|
| prop | TwoRayGround |
| mac | 802.11 |
| ifq | Drop Tail/PriQueue |
| ifqlen | 20 |
| SIFS | 10 s |
| Phy header | 192 bits |
| Mac header | 224 bits |
| RTS | 160 bits + Phy header |
| CTS, ACK | 112 bits + Phy header |
| The Number of Background Flows (UDP Flows) | 1 | 2 | 3 | 4 |
|---|---|---|---|---|
| RTS retransmission times | 1.349 | 1.688 | 2.068 | 2.109 |
| FSD (ms) | 20.234 | 21.289 | 23.560 | 24.395 |
| 0.66237 | 0.69409 | 0.71038 | 0.72191 | |
| 0.58043 | 0.57561 | 0.57334 | 0.57322 |
| TCP Flow Number | Total Throughput (kbps) | Average Value of | ||
|---|---|---|---|---|
| RECN | No ECN | RECN | No ECN | |
| 1 | 244.58 | 232.39 | 0.761 | 0.645 |
| 2 | 556.11 | 317.64 | 0.760 | 0.640 |
| 3 | 707.89 | 323.81 | 0.758 | 0.646 |
| 4 | 640.80 | 399.18 | 0.756 | 0.613 |
| 5 | 727.27 | 373.71 | 0.753 | 0.624 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, H.; Li, T.; Feng, L.; Ye, J. Frame Transmission Efficiency-Based Cross-Layer Congestion Notification Scheme in Wireless Ad Hoc Networks. Sensors 2017, 17, 1637. https://doi.org/10.3390/s17071637
He H, Li T, Feng L, Ye J. Frame Transmission Efficiency-Based Cross-Layer Congestion Notification Scheme in Wireless Ad Hoc Networks. Sensors. 2017; 17(7):1637. https://doi.org/10.3390/s17071637
Chicago/Turabian StyleHe, Huaguang, Taoshen Li, Luting Feng, and Jin Ye. 2017. "Frame Transmission Efficiency-Based Cross-Layer Congestion Notification Scheme in Wireless Ad Hoc Networks" Sensors 17, no. 7: 1637. https://doi.org/10.3390/s17071637
APA StyleHe, H., Li, T., Feng, L., & Ye, J. (2017). Frame Transmission Efficiency-Based Cross-Layer Congestion Notification Scheme in Wireless Ad Hoc Networks. Sensors, 17(7), 1637. https://doi.org/10.3390/s17071637





