A Secure and Privacy-Preserving Navigation Scheme Using Spatial Crowdsourcing in Fog-Based VANETs
Abstract
:1. Introduction
- First, we present a model for a secure navigation scheme in fog-based VANETs, which takes advantage of vehicular cloud and fog computing to make up for the limitation of the previous VANET-based navigation system.
- Second, we construct a specific scheme that can support real-time navigation service to drivers in a congested area. In this way, drivers can quickly find an available route, and, moreover, gasoline and the time wasted in traffic congestion can be reduced. By using the spatial crowdsourcing, the real-time road conditions can be updated in time in fog-based VANETs. Meanwhile, the vehicle performing the crowdsourcing task can get a reasonable reward. Performance analysis shows that the real-time navigation service supported by the proposed scheme is effective.
2. System Model and Design Goal
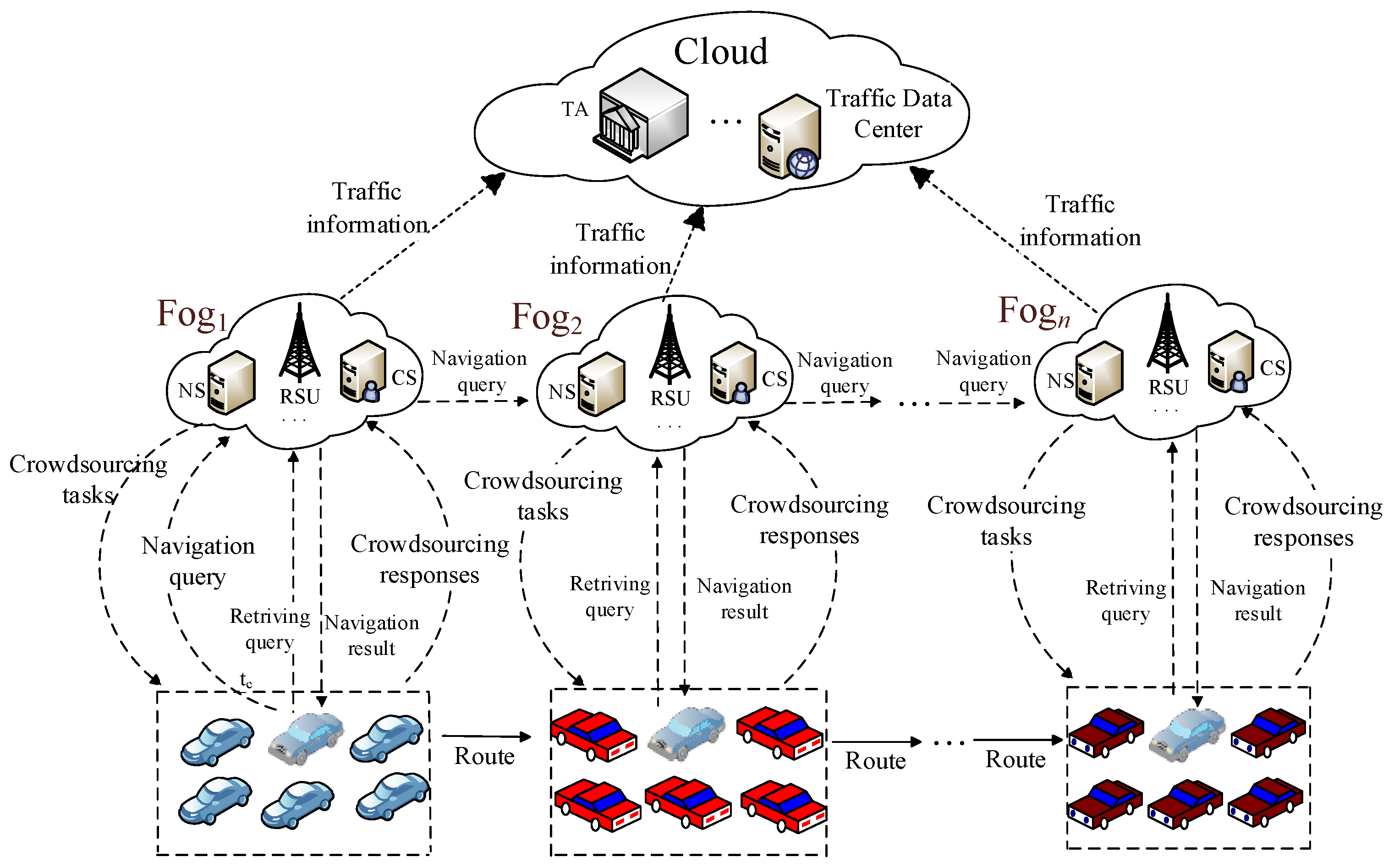
2.1. System Model
- TA is trusted and the public agency. For example, the transportation authorities with administrative rights can take on the role of the TA. It is responsible for the registration of fog nodes and vehicles deployed in fog-based VANETs, issuing anonymous credentials and tracing the vehicles’ identity in case of rewarding purpose for spatial crowdsourcing, sending fake traffic information for uncongested driving experience, etc.
- The cloud is a set of interconnected computing resources. The cloud provides centralized navigation services for drivers, e.g., Google Map.
- Fog node is a highly virtualized computing system, which is deployed at the edge of networks, e.g., banks, bus terminals, shopping halls, etc. Similar to a lightweight cloud server, fog node is equipped with the on-board large volume data storage, computers and wireless communication facility [12]. In our fog-based VANETs, the fog node consists of navigation servers (NS) and crowdsourcing servers (CS) and conventional RSU, which are in charge of releasing crowdsourcing tasks, computing the optimal path for the querying vehicles, and rewarding the crowdsourcing contributors.
- Vehicles are equipped with irreplaceable and temper-proof OBU device, which enables performing some simple computations, communicating with other vehicles and fog nodes, and these vehicles have a small amount of read-only memory. In our model, OBU is required to generate real-time navigation query, traffic information reports for spatial crowdsourcing tasks, result retrieving query.
2.2. Design Goal
- Real-time path navigation: With the guidance of the fog nodes, a vehicle can conveniently find the optimal path to the desired destination.
- Authentication: Only legitimate entities should take part in the fog-based VANETs. Fog nodes and vehicles should be able to prove themselves by using certificates or credentials. In addition, the origin of the messages should be authenticated to prevent against the impersonation and message forgery attacks. Meanwhile, the identity of the crowdsourcing contributor should be authenticated to get the reward. In addition, only a legitimate subscriber that has service access rights should be able to get navigation service.
- Confidentiality: the navigation query, traffic information report, and navigation result should be kept confidential from eavesdroppers who will illegally use the navigation information for their own purposes.
- Conditional privacy preservation: the real identity of the querying vehicle and the crowdsourcing vehicle should be kept secret. Although the location and destination would be exposed to fog nodes, the adversary can neither link a navigaiton query to a specific vehicle nor identify two navigation queries from the same vehicle. However, once an exceptional event occurs, the fog nodes can learn the vehicles’ real identifier with the help of TA.
3. Preliminaries
3.1. Bilinear groups
- for all , and , ;
- for and , ;
- the map e is efficiently computable.
3.2. Message-Locked Encryption
- On input , the parameter generation algorithm returns a public parameter P.
- On input P and a message M, the key-generation algorithm returns a message-derived key .
- On input , the encryption algorithm returns a ciphertext .
- On input and a ciphertext C, the decryption algorithm returns .
- On input , the tag generation algorithm returns a tag .
3.3. Randomized Signatures
- : given a security parameter k, this algorithm outputs public parameter . These bilinear groups must be of type 3.
- : selects and , computes , and sets as and as .
- : picks a random to compute a signature .
- : parses as and checks whether and are both satisfied. If it is the positive case, it outputs 1, and 0 otherwise.
3.4. Group Signatures
4. Proposed Secure and Privacy-Preserving Navigation Scheme
4.1. System Setting
- chooses m random numbers, as the short-life private keys and computes the corresponding public keys for for the travel;
- for each short-life public key , computes the self-delegated certificate as follows:
- −
- randomly choose , , , , compute as follows: , , mod q, , , ;
- −
- compute and where mod q; mod q; mod q; and the certificate of is .
- −
- anyone can check the validity of by computing: ;;;and check whether holds.
- installs and for into the read-only memory of the OBUs.
4.2. Real-Time Navigation Querying
- utilize to encrypt by randomly choosing , and compute , , ;
- select randomly to compute the randomized signture , and the hush function , , and output the group signature ;
- finally, send the navigation query Q to the fog node , where .
- Decode by computing ;
- verify the validity of the signature by computingand checking whether the hash holds. If not, returns failure and aborts; Otherwise, it checks the routing table to find the next fog node, denoted as , according to the destination .
- randomly chooses to compute , , ;
- finally, forwards the query to .
4.3. Spatial Crowdsourcing
- randomly choose a short-life public key from the for stored in its OBU;
- generate a traffic information report including the current location, current time, driving speed and the road condition;
- randomly choose to calculate the randomized signature , the hash , and ;
- encrypt the traffic information report by using a message-lock encryption algorithm. Choose to compute , the tag , , and ;
- finally, returns the crowdsourcing response to .
- decode the crowdsourcing response by computing , , and the tag ;
- check whether the equation holds. If not, reject the . Otherwise, it compares the tag with the element in the tag table . If there exists a tag in the tag table satisfying , which means the same traffic information report has been stored in the database, will reject the . Otherwise, it verifies the signature by computingand checking whether the equation holds. If not, returns failure and aborts; otherwise, it keeps in its database;
- rewards the contributor based on the short-life public key ;
- can compute the optimal path by using Dijkstra’s algorithm in its coverage area;
- choose , to calculate , and . Finally, the navigation result for is .
4.4. Navigation Result Retrieval
4.5. Identity Revocation
5. Security Analysis
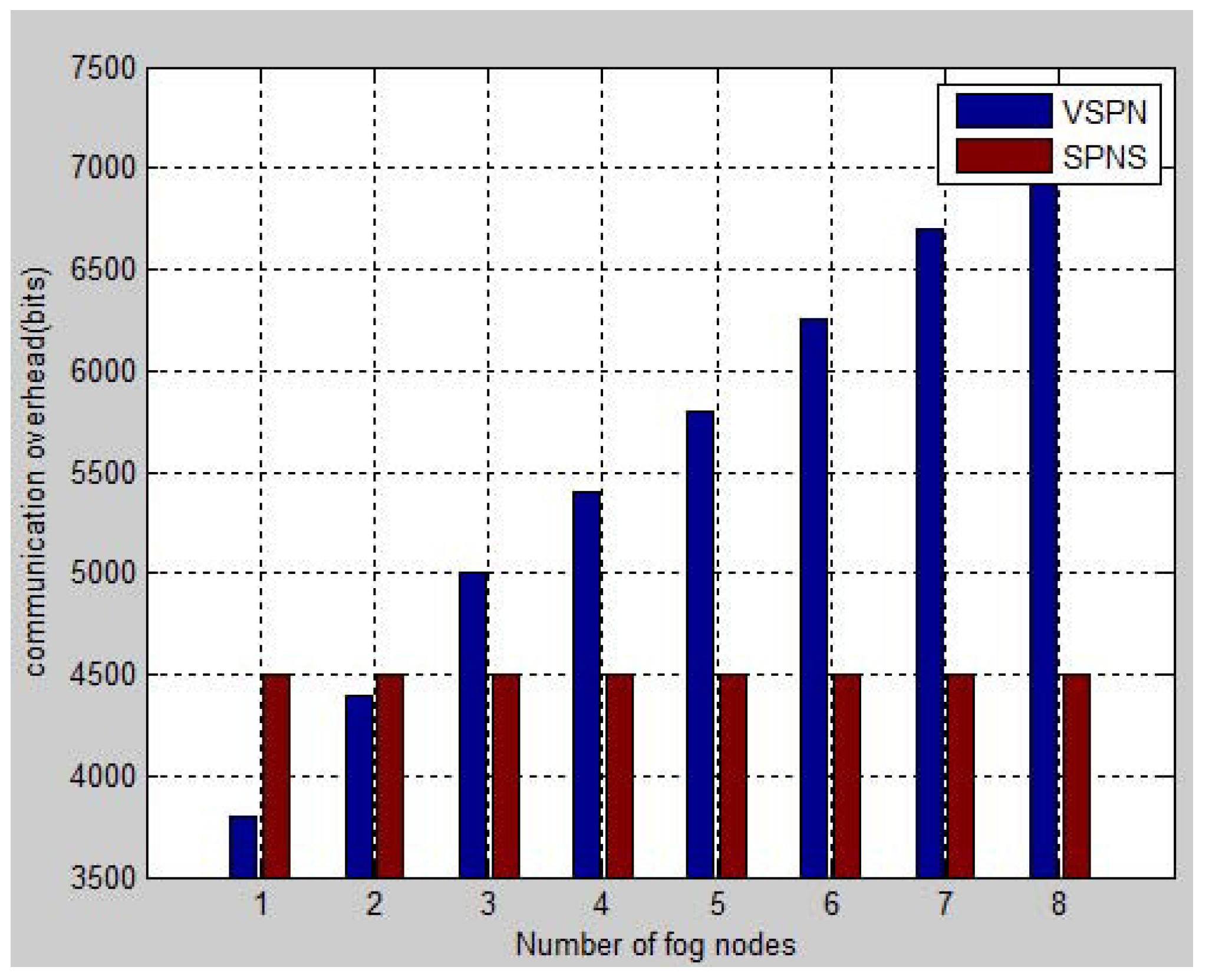
6. Performance Analysis
7. Related Works
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Zheng, J.R. Beijing tops domestic list for traffic congestion. China Daily, 27 August 2015. [Google Scholar]
- Global Positioning System Standard Positioning Service Signal Specification; Navtech GPS Supply: Springfield, VA, USA, 1995.
- Autonavi Navigation. Available online: http://www.autonavi.com/ (accessed on 17 March 2017). (In Chinese).
- Olariu, S.; Hristov, T.; Yan, G. The Next Paradigm Shift: From Vehicular Networks to Vehicular Clouds; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2013; pp. 645–700. [Google Scholar]
- Yan, G.; Wen, D.; Olariu, S.; Weigle, M.C. Security challenges in vehicular cloud computing. IEEE Trans. Intell. Transp. Syst. 2013, 14, 284–294. [Google Scholar] [CrossRef]
- Yu, R.; Zhang, Y.; Gjessing, S.; Xia, W. Toward cloud-based vehicular networks with efficient resource management. IEEE Netw. 2013, 27, 48–55. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog Computing and Its Role in the Internet of Things; Edition of the MCC Workshop on Mobile Cloud Computing; ACM: Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar]
- Lin, X.; Sun, X.; Ho, P.H.; Shen, X. GSIS: A secure and privacy-preserving protocol for vehicular communications. IEEE Trans. Veh. Technol. 2007, 56, 3442–3456. [Google Scholar]
- Lin, X.; Sun, X.; Wang, X.; Ho, P.H.; Shen, X. TSVC: Timed efficient and secure vehicular communications with privacy preserving. IEEE Trans. Wirel. Commun. 2009, 7, 4987–4998. [Google Scholar] [CrossRef]
- Lin, X.; Lu, R.; Zhang, C.; Ho, P.H.; Shen, X. Security in vehicular ad hoc networks. IEEE Commun. Mag. 2008, 46, 88–95. [Google Scholar]
- Lu, R.; Lin, X.; Zhu, H.; Ho, P.H.; Shen, X. A novel anonymous mutual authentication protocol with provable link-layer location privacy. IEEE Trans. Veh. Technol. 2009, 58, 1454–1466. [Google Scholar]
- Luan, T.H.; Gao, L.; Li, Z.; Xiang, Y.; Wei, G.; Sun, L. Fog computing: Focusing on mobile users at the edge. arXiv, 2015; arXiv:1502.01815. [Google Scholar]
- Behrendt, K.; Fodero, K. The perfect time: An examination of time-synchronization techniques. In Proceedings of the Distributech, San Diego, CA, USA, 3 January 2005. [Google Scholar]
- Galbraith, S.D.; Paterson, K.G.; Smart, N.P. Pairings for cryptographers. Discr. Appl. Math. 2008, 156, 3113–3121. [Google Scholar] [CrossRef]
- Bellare, M.; Keelveedhi, S.; Ristenpart, T. Message-Locked Encryption and Secure Deduplication. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Athens, Greece, 26–30 May 2013; Volume 7881, pp. 296–312. [Google Scholar]
- Hur, J.; Koo, D.; Shin, Y.; Kang, K. Secure Data Deduplication with Dynamic Ownership Management in Cloud Storage. IEEE Trans. Knowl. Data Eng. 2016, 28, 3113–3125. [Google Scholar] [CrossRef]
- Mao, B.; Jiang, H.; Wu, S.; Tian, L. Leveraging Data Deduplication to Improve the Performance of Primary Storage Systems in the Cloud. IEEE Trans. Comput. 2013, 25, 1775–1788. [Google Scholar]
- Yan, Z.; Wang, M.; Li, Y.; Vasilakos, A.V. Encrypted Data Management with Deduplication in Cloud Computing. IEEE Cloud Comput. 2016, 3, 28–35. [Google Scholar] [CrossRef]
- Pointcheval, D.; Sanders, O. Short randomizable signatures. In Proceedings of the CT-RSA 2016, San Francisco, CA, USA, 29 February–4 March 2016; Volume 9610, pp. 111–126. [Google Scholar]
- Camenisch, J.; Lysyanskaya, A. A signature scheme with efficient protocols. In Proceedings of the International Conference on Security in Communication Networks, Amalfi, Italy, 11–13 September 2002; pp. 268–289. [Google Scholar]
- Chaum, D.; Heyst, E.V. Group signatures. In Proceedings of the Workshop on the Theory and Application of of Cryptographic Techniques, Brighton, UK, 8–11 April 1991; Springer: Berlin/Heidelberg, Germany, 1991; pp. 257–265. [Google Scholar]
- Schnorr, C.P. Efficient Identification and Signatures for Smart Cards. In Advances in Cryptology— EUROCRYPT’89; Springer: Berlin/Heidelberg, Germany, 1990; pp. 688–689. [Google Scholar]
- Chim, T.W.; Yiu, S.M.; Hui, L.C.K.; Li, V.O. VSPN: VANET-Based Secure and Privacy-Preserving Navigation. IEEE Trans. Comput. 2014, 63, 510–524. [Google Scholar] [CrossRef]
- Scott, M. Efficient Implementation of Cryptographic pairings. Available online: http://ecrypt-ss07.rhul.ac.uk/Slides/Thursday/mscottsamos07.pdf (accessed on 5 June 2016).
- Miyaji, A.; Nakabayashi, M.; Takano, S. New explicit conditions of elliptic curve traces for FR-reduction. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2001, 84, 1234–1243. [Google Scholar]
- Lu, R.; Lin, X.; Zhu, H.; Shen, X. SPARK: A new VANET-based smart parking scheme for large parking lots. In Proceedings of the IEEE INFOCOM, Rio De Janeiro, Brazil, 19–25 April 2009; pp. 1413–1421. [Google Scholar]
- Leontiadis, I.; Costa, P.; Mascolo, C. Extending access point connectivity through opportunistic routing in vehicular networks. In Proceedings of the Conference on Information Communications, San Diego, CA, USA, 14–19 March 2010; pp. 1–5. [Google Scholar]
- Liu, C.G.; Liu, I.H.; Yang, T.T.; Li, J.S. Navigation-aware association control in vehicular wireless networks. J. High Speed Netw. 2013, 19, 311–324. [Google Scholar]
- Chen, P.Y.; Guo, Y.M.; Chen, W.T. Fuel-saving navigation system in VANETs. In Proceedings of the IEEE Vehicular Technology Conference Fall, Ottawa, ON, Canada, 6–9 September 2010; pp. 1–5. [Google Scholar]
- Cho, W.; Park, Y.; Sur, C.; Rhee, K.H. An improved privacy-preserving navigation protocol in VANETs. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2013, 4, 80–92. [Google Scholar]
- Sur, C.; Park, Y.; Rhee, K.H. An efficient and secure navigation protocol based on vehicular cloud. Int. J. Comput. Math. 2016, 93, 1–20. [Google Scholar] [CrossRef]
- Ni, J.B.; Lin, X.D.; Zhang, K.; Shen, X. Privacy-Preserving Real-Time Navigation System Using Vehicular Crowdsourcing. In Proceedings of the IEEE 84th Vehicular Technology Conference (VTC2016-Fall), Montréal, QC, Canada, 18–21 September 2016. [Google Scholar]
- Gentry, C.; Silverberg, A. Hierarchical ID-Based cryptography. In Advances in Cryptology-ASIACRYPT 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 548–566. [Google Scholar]
- Chen, L.; Cheng, Z.; Smart, N.P. Identity-based key agreement protocols from pairings. Int. J. Inf. Secur. 2007, 6, 213–241. [Google Scholar] [CrossRef]
| Element | Description |
|---|---|
| N | Sequence number: records the query number that is used to distinguish different queries from the same OBU. |
| Short-life public key: If a vehicle sends a navigation query at some time, it will randomly choose a short-life public key from the sequence for stored in the OBU. This field is used to record the public key, which will be also used to reward vehicles in the spatial crowdsourcing step. | |
| Current location: records the current position of the querying vehicle on the unique Euclidean plane. | |
| Desired destination: records the destination where the querying vehicle will arrive. | |
| Current time: records the start querying time. | |
| Expired time: records the exact time after which the query is invalid, because the life-time of the navigation query is fixed. |
| Phases | TA | Fog Node | Vehicle |
|---|---|---|---|
| System setting | |||
| Querying | 0 | ||
| Crowdsourcing | 0 | ||
| Retrieving | 0 | ||
| Tracing | 0 | 0 |
| Phases | SPNS | VSPN |
|---|---|---|
| Setting | ||
| Querying | ||
| Crowdsourcing | 0 | |
| Retrieving |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, L.; Liu, G.; Sun, L. A Secure and Privacy-Preserving Navigation Scheme Using Spatial Crowdsourcing in Fog-Based VANETs. Sensors 2017, 17, 668. https://doi.org/10.3390/s17040668
Wang L, Liu G, Sun L. A Secure and Privacy-Preserving Navigation Scheme Using Spatial Crowdsourcing in Fog-Based VANETs. Sensors. 2017; 17(4):668. https://doi.org/10.3390/s17040668
Chicago/Turabian StyleWang, Lingling, Guozhu Liu, and Lijun Sun. 2017. "A Secure and Privacy-Preserving Navigation Scheme Using Spatial Crowdsourcing in Fog-Based VANETs" Sensors 17, no. 4: 668. https://doi.org/10.3390/s17040668
APA StyleWang, L., Liu, G., & Sun, L. (2017). A Secure and Privacy-Preserving Navigation Scheme Using Spatial Crowdsourcing in Fog-Based VANETs. Sensors, 17(4), 668. https://doi.org/10.3390/s17040668





