A Continuous Object Boundary Detection and Tracking Scheme for Failure-Prone Sensor Networks
Abstract
:1. Introduction
2. Background
2.1. Continuous Object Tracking in Wireless Sensor Networks
2.2. Voronoi Diagram and Node Failure in Continuous Object Tracking
3. Related Work
3.1. Continuous Object Boundary Detection and Tracking
3.2. Detection and Recovery of Node Failure
4. Proposed Scheme
4.1. Network Model
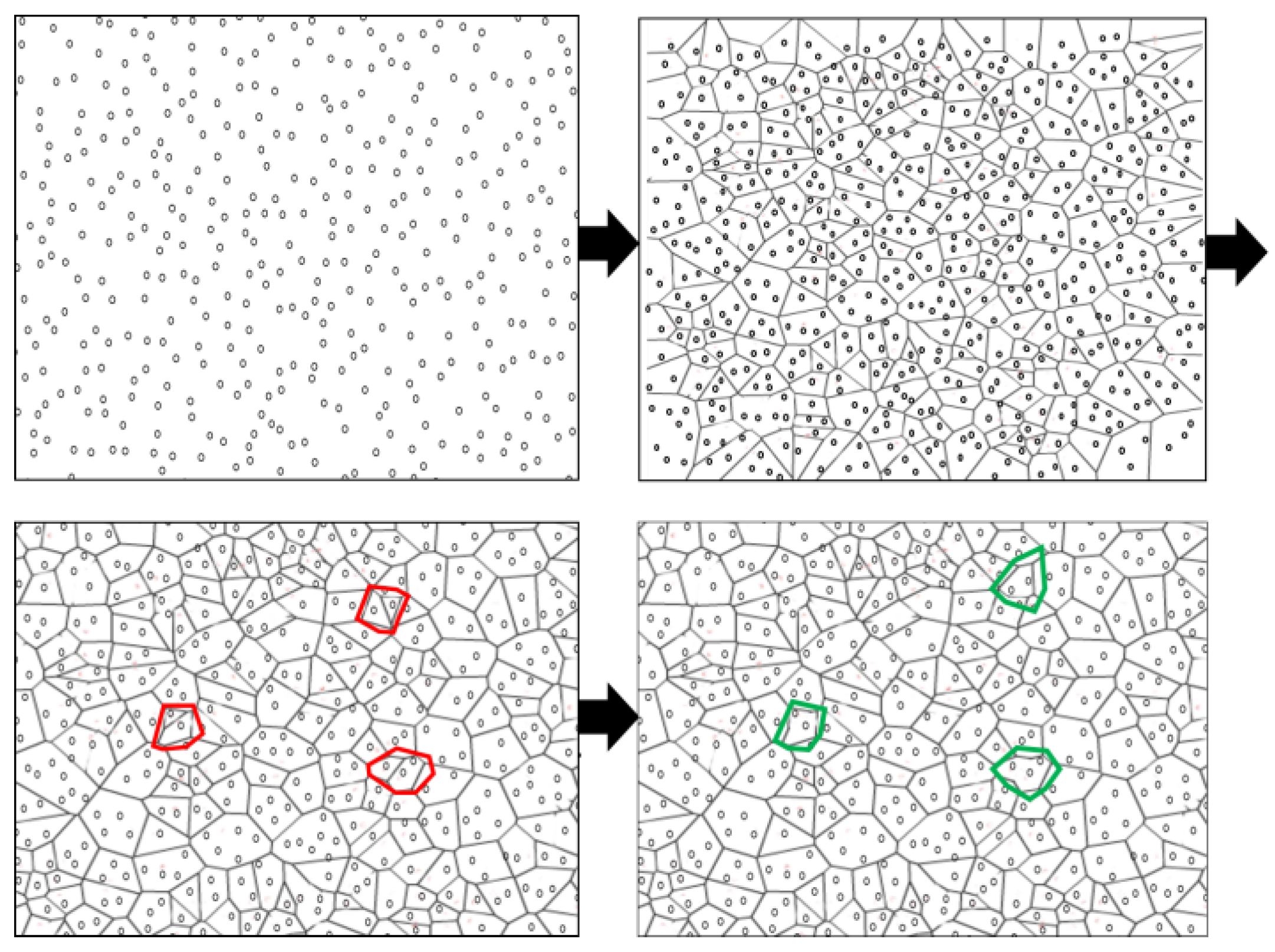
4.2. Post-Deployment Network Clustering Using a Voronoi Diagram
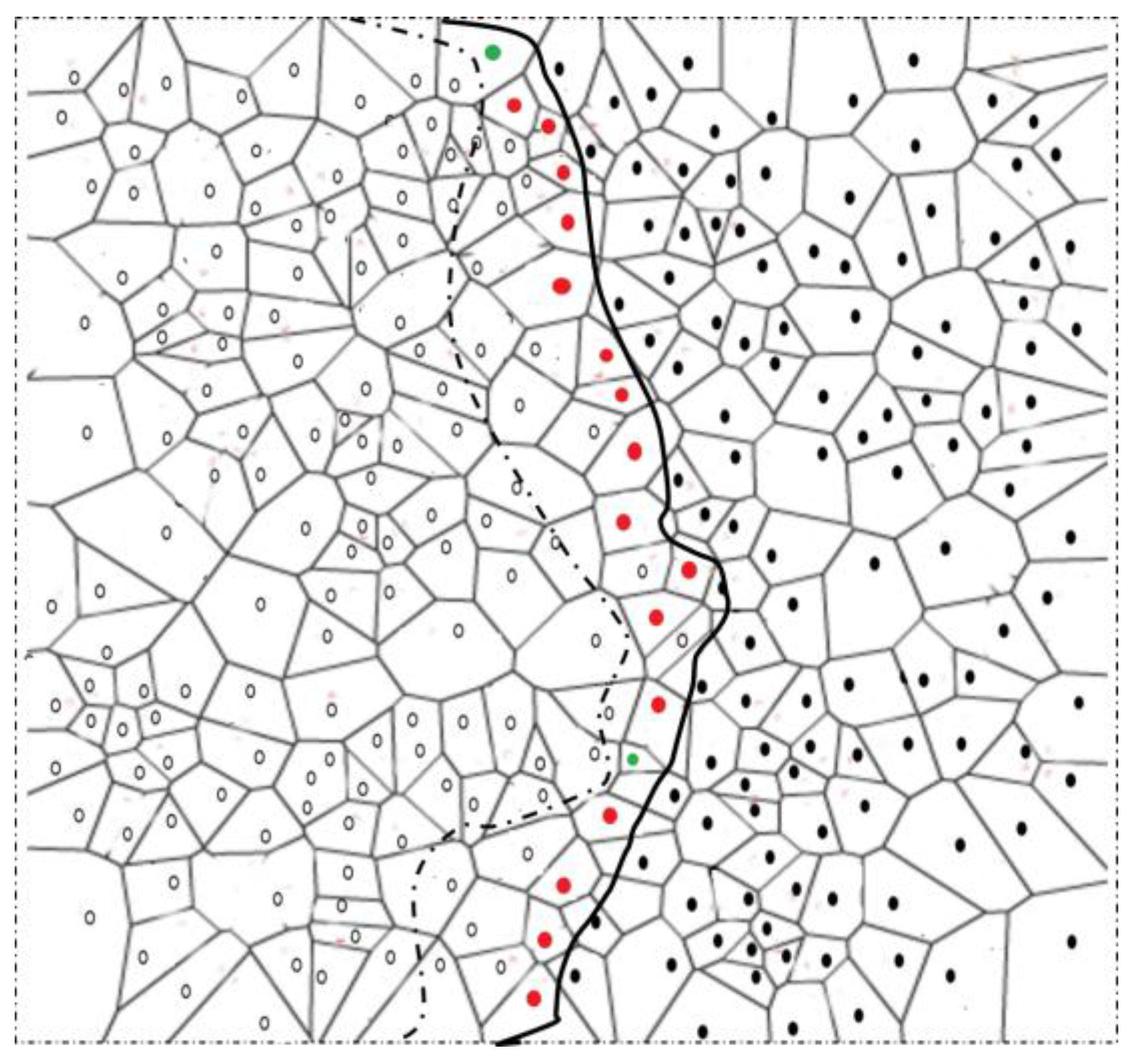
4.3. Continuous Object Detection and Tracking
| Algorithm 1 Algorithm for Boundary detection and BN selection |
| Input: Node u detects a change in its detection status |
| Output: Strong and normal BNs are selected |
| 1. Node u sends its detection status to one-hop neighbors v. |
| 2. if there is a change in the detection status of v, then |
| 3. send a status message to one-hop neighbors w. |
| 4. if the detection status of w is changed, then |
| 5. v send detection status of w to u |
| 6. if the detection status of both v and w is changed then |
| 7. u becomes strong BN |
| 8. else |
| 9. u becomes normal BN |
| 10. else |
| 11. a no-change message is sent back to node u. |
| 12. else |
| 13. u withdraws to become a BN |
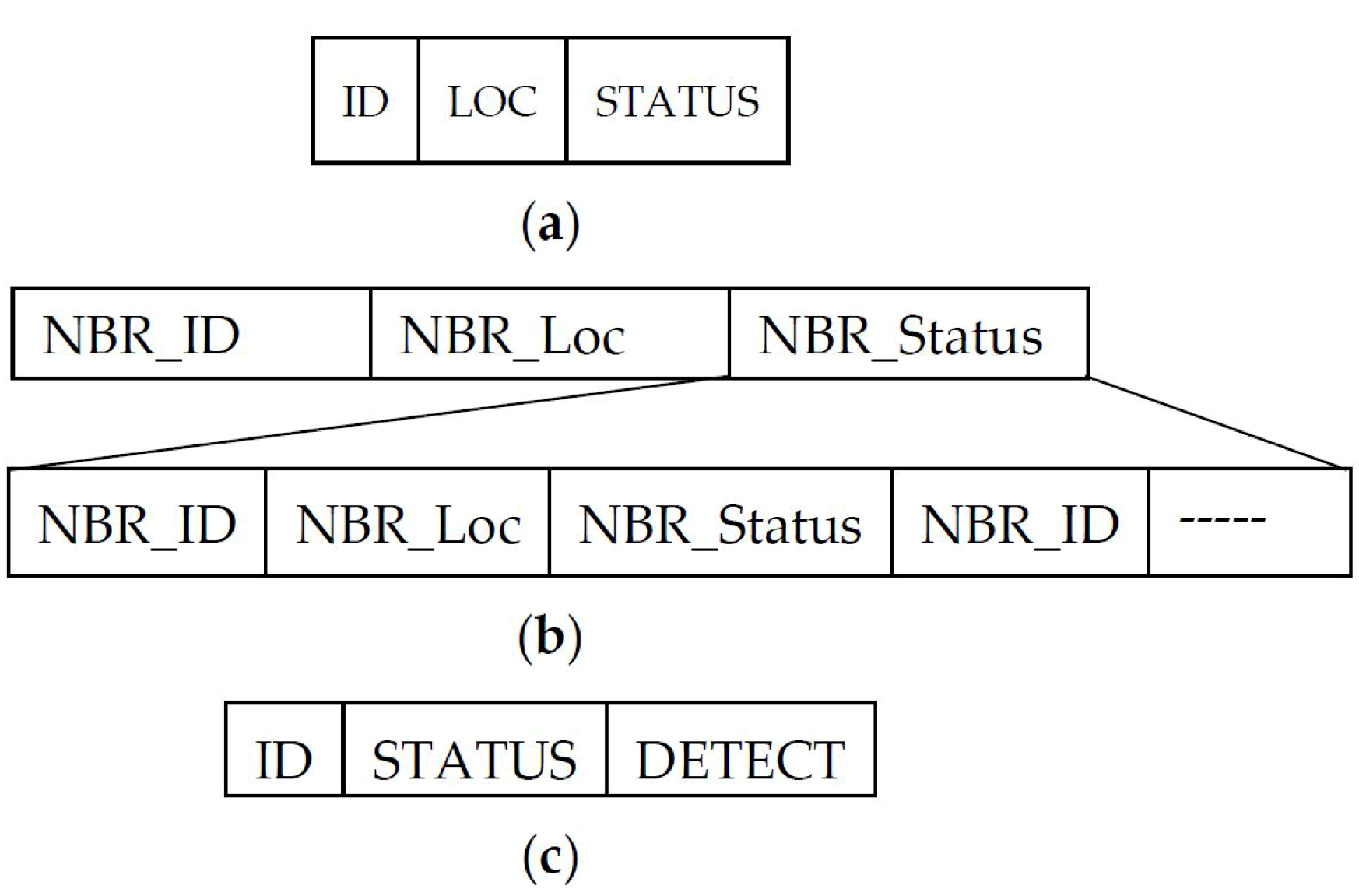
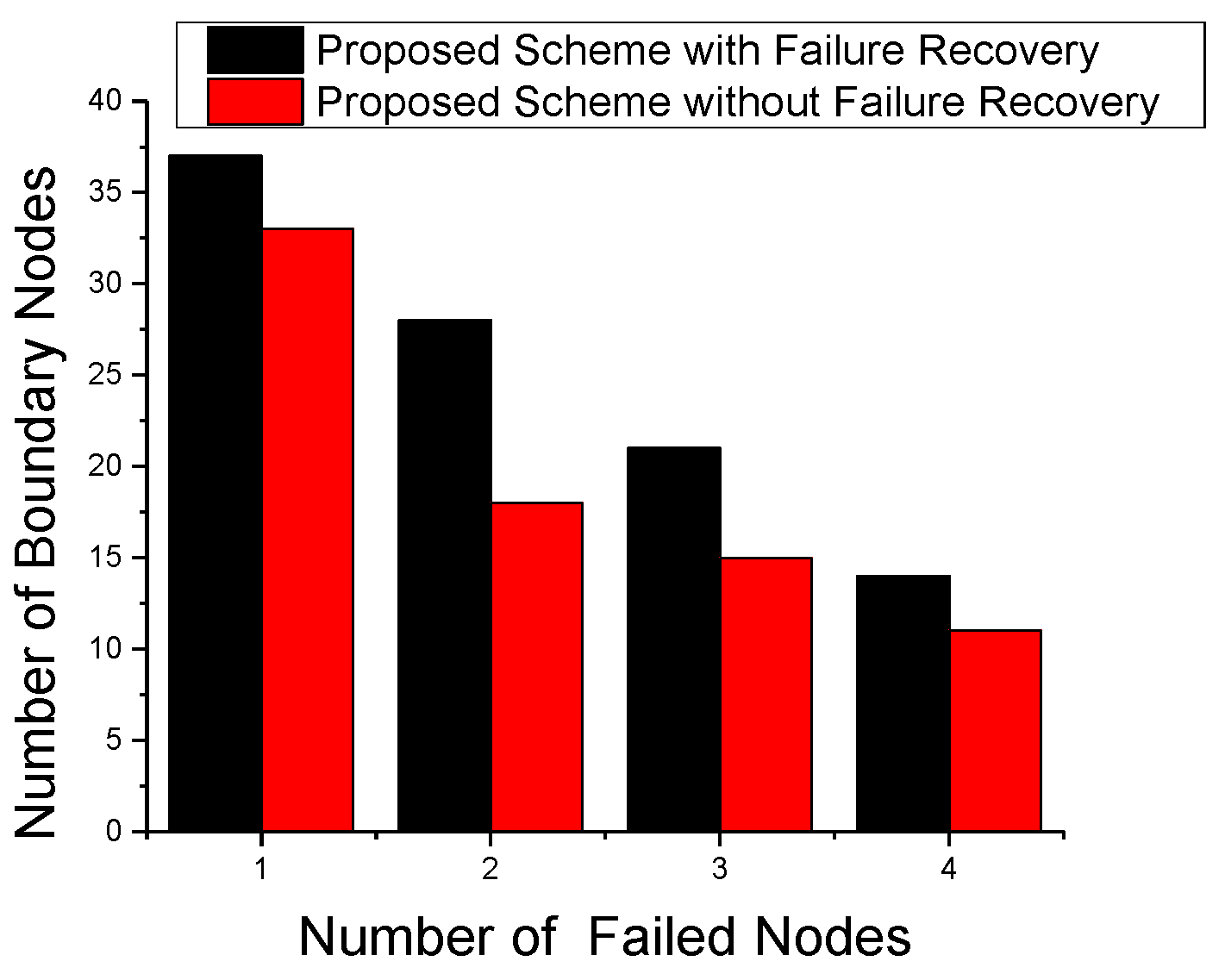
4.4. Failure Detection and Recovery
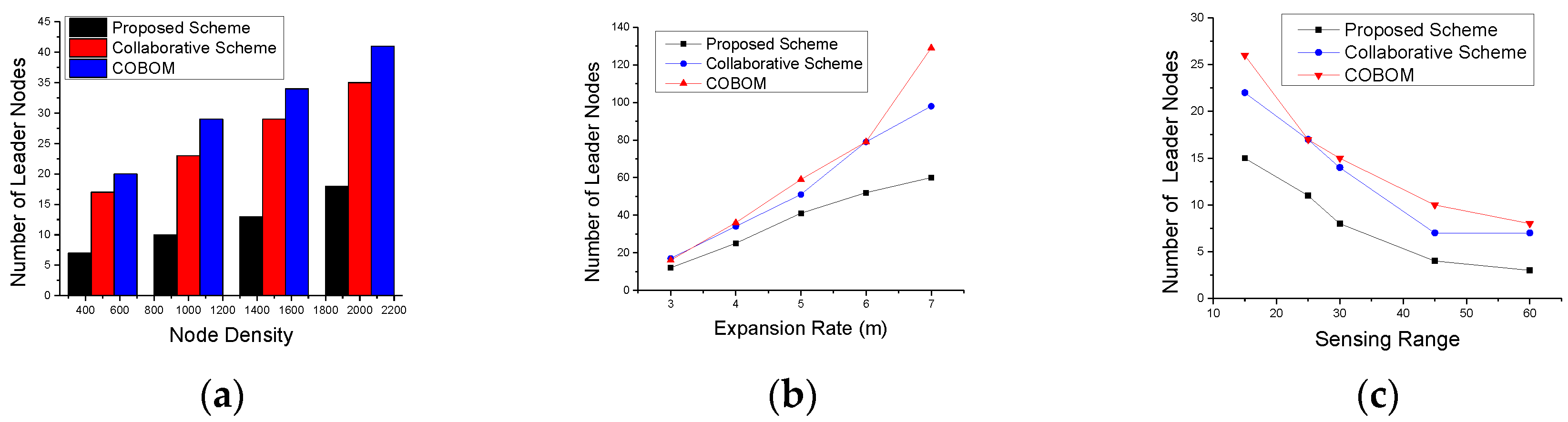
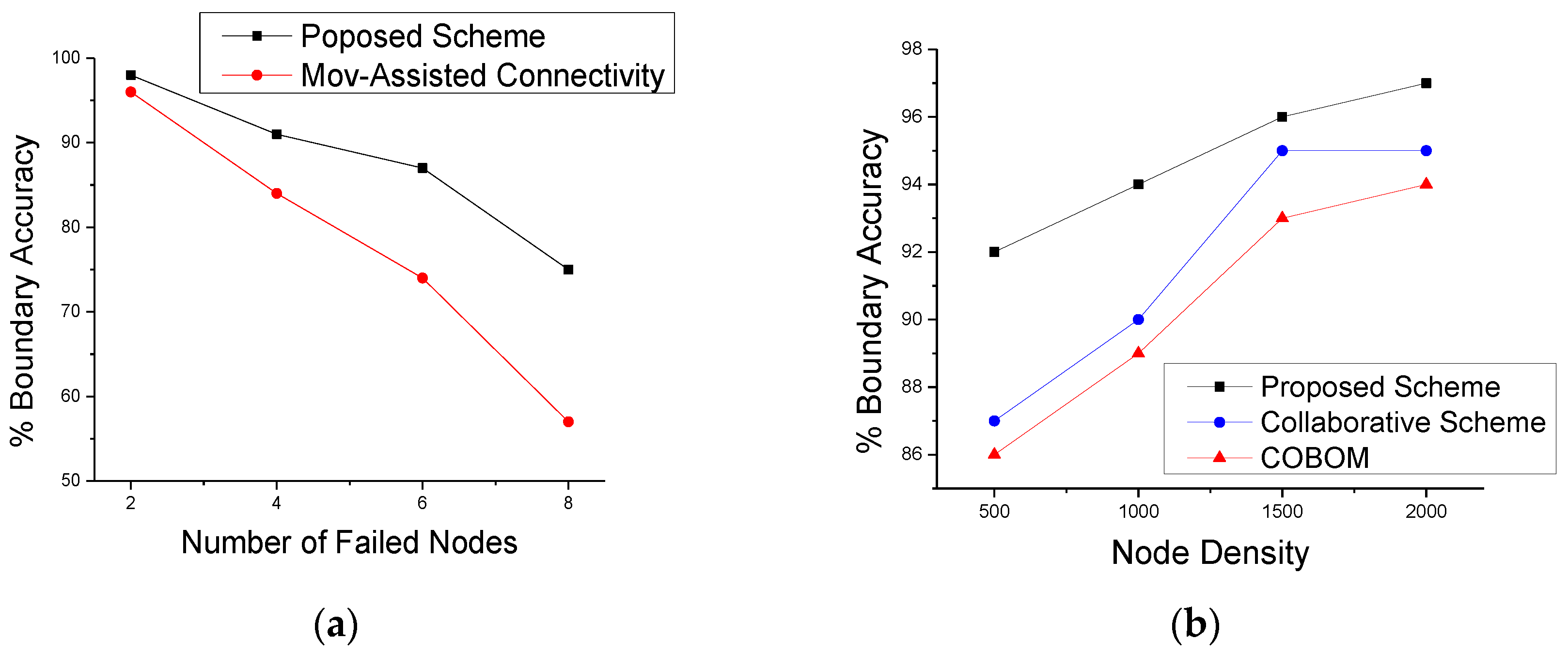
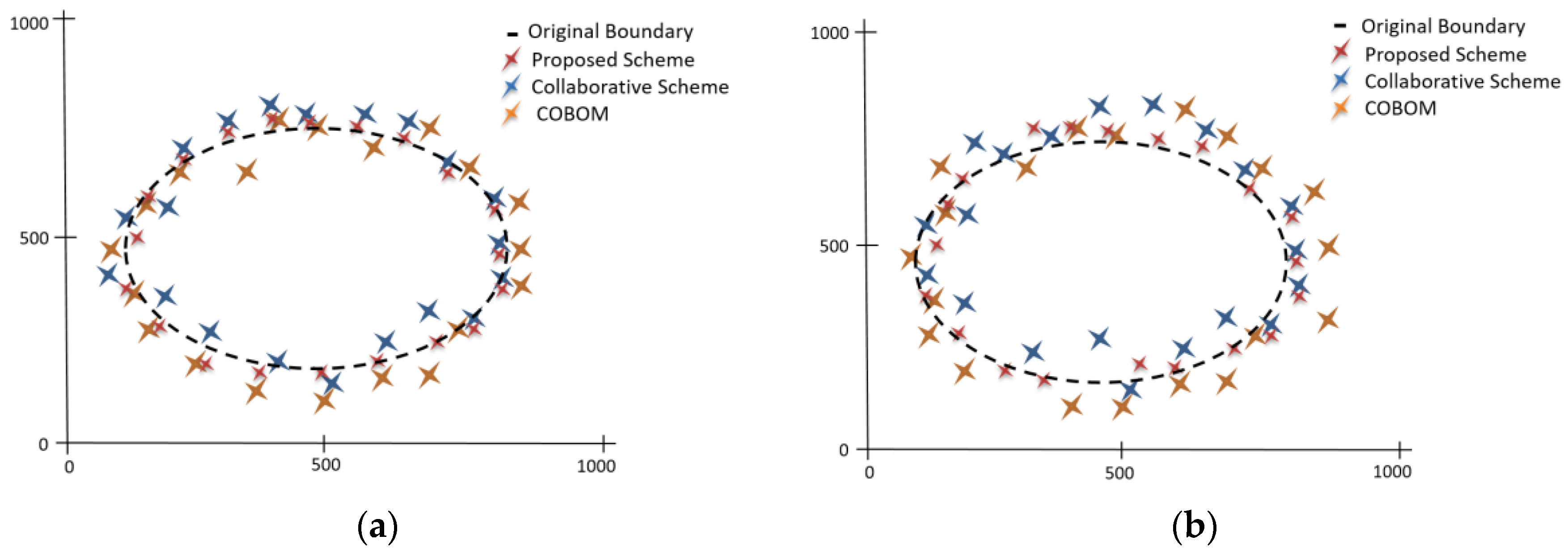
5. Performance Evaluation
5.1. Simulation Environment
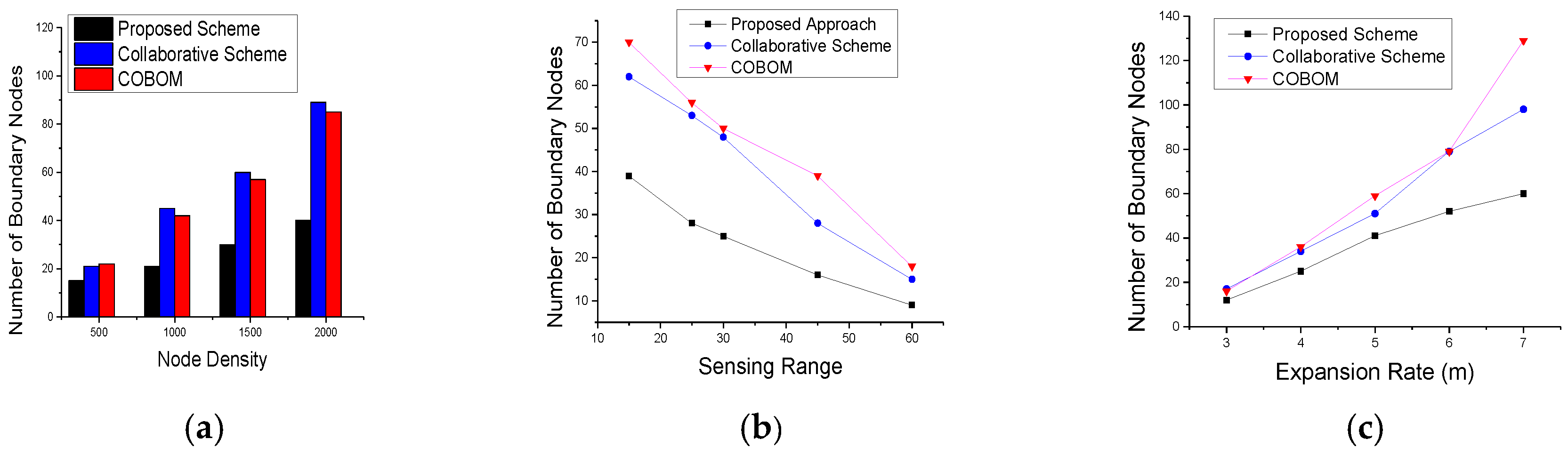
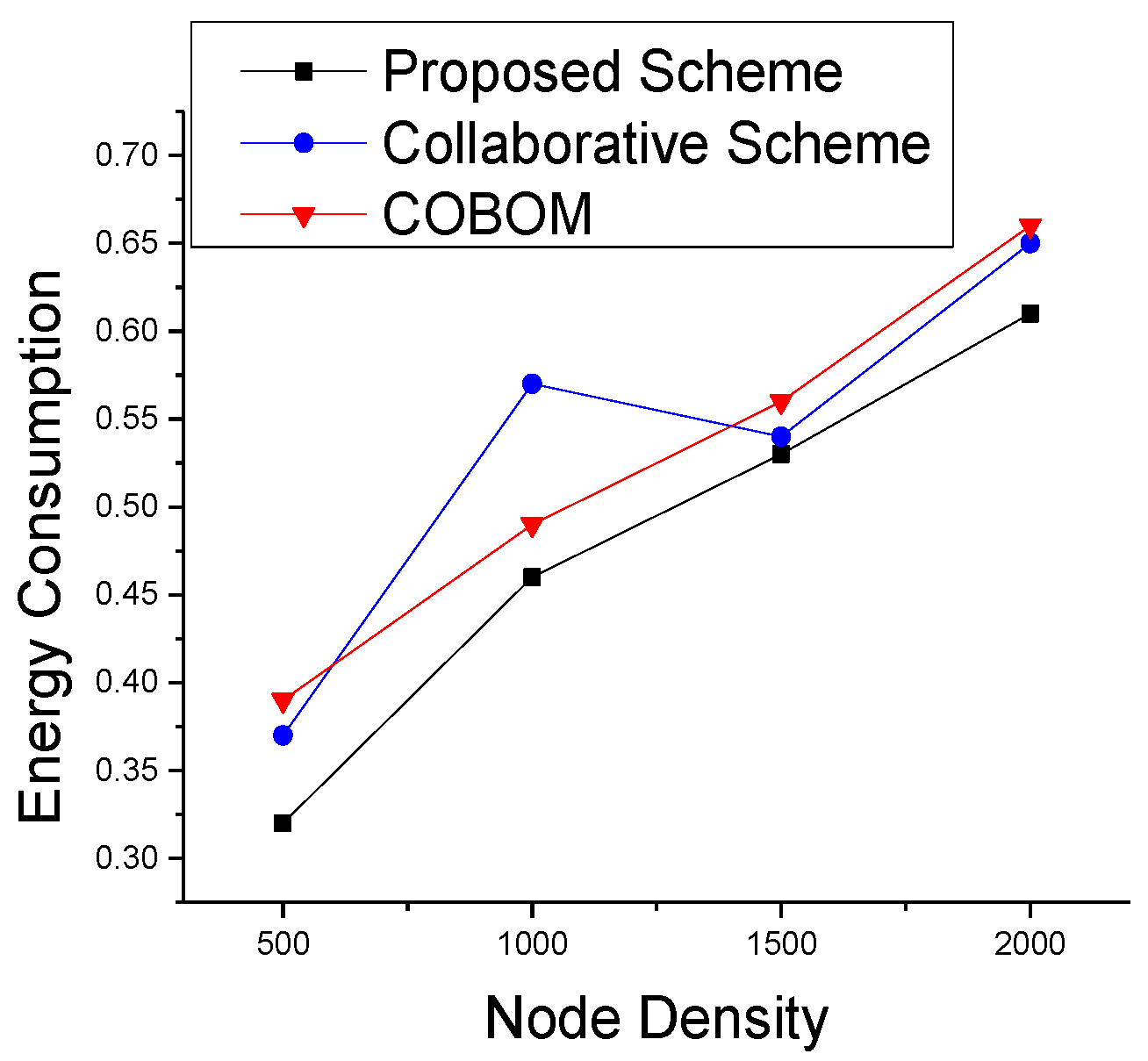
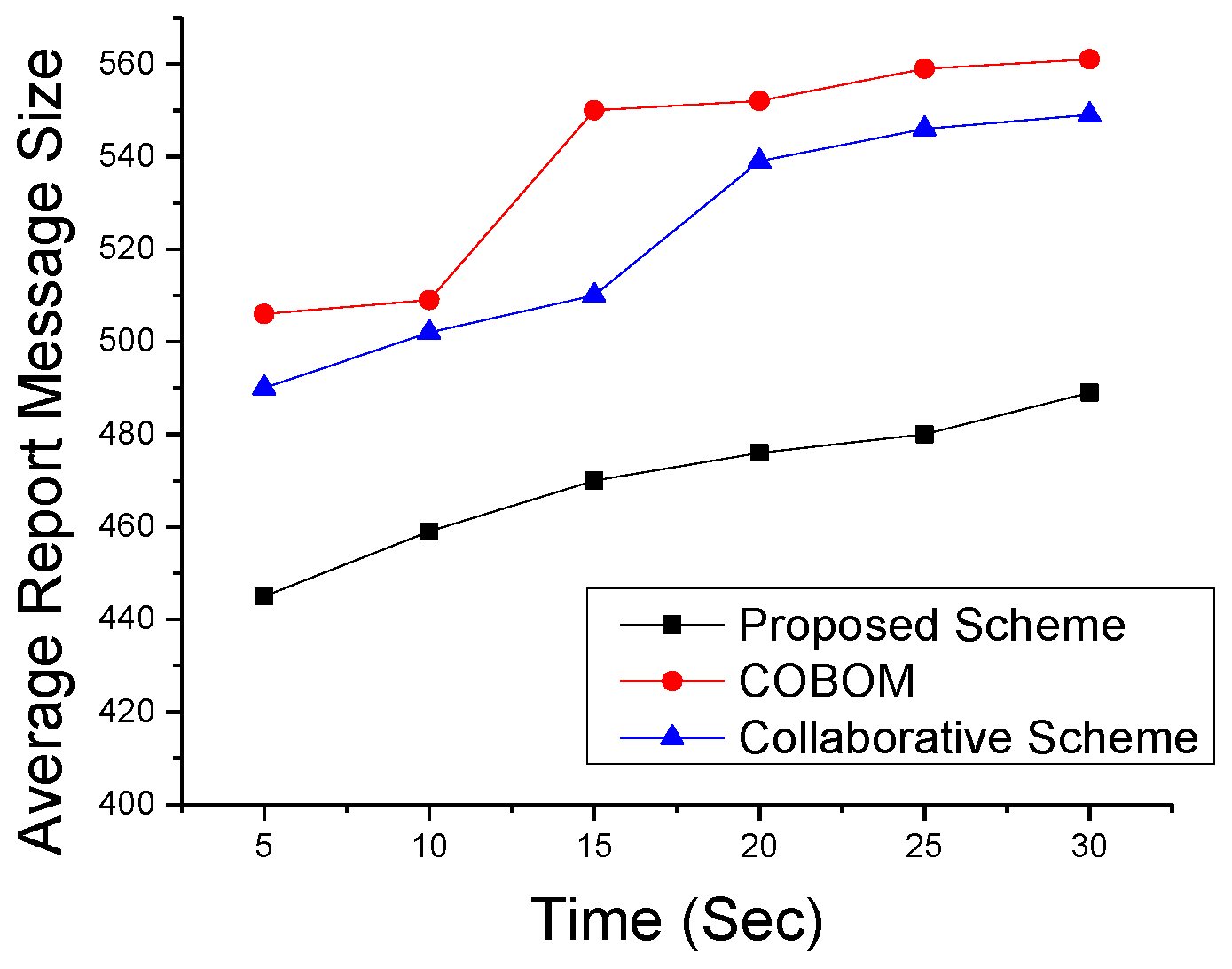
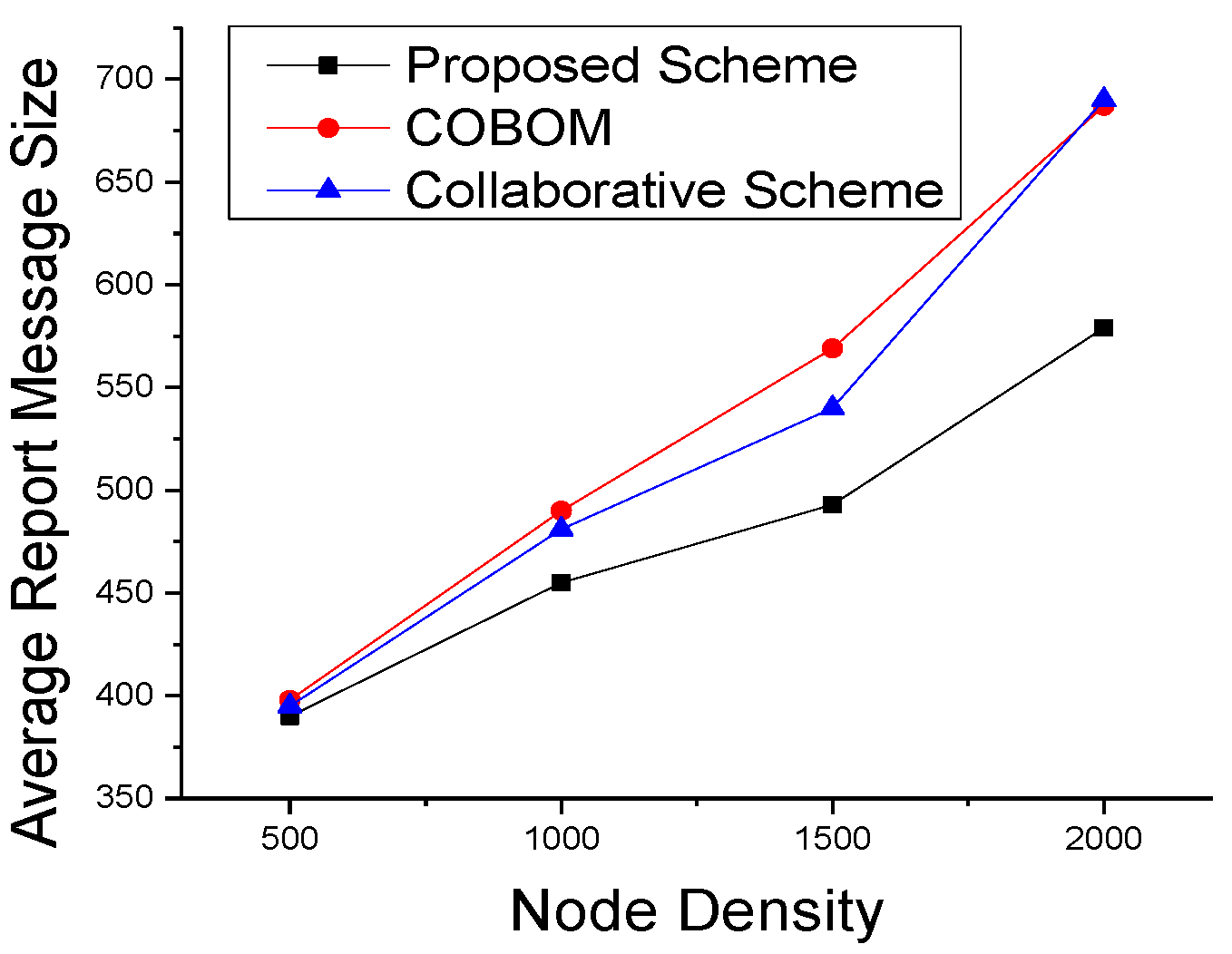
5.2. Simulation Results
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Safia, A.A.; al Aghbari, Z.; Kamel, I. Phenomena Detection in Mobile Wireless Sensor Networks. J. Netw. Syst. Manag. 2015, 24, 92–115. [Google Scholar] [CrossRef]
- Sheltami, T.R.; Khan, S.; Shakshuki, E.M.; Menshawi, M.K. Continuous objects detection and tracking in wireless sensor networks. J. Ambient Intell. Humaniz. Comput. 2016, 7, 489–508. [Google Scholar] [CrossRef]
- Chen, J.; Matsumoto, M. EUCOW: Energy-efficient boundary monitoring for unsmoothed continuous objects in wireless sensor network. In Proceedings of the 2009 IEEE 6th International Conference on Mobile Adhoc and Sensor Systems, Macau, China, 12–15 October 2009; pp. 906–911.
- Choudhary, V. Energy Efficient Object Tracking Technique using Mobile Data Collectors in Wireless Sensor Networks. Int. J. Comput. Appl. 2012, 2, 82–115. [Google Scholar]
- Park, S.; Hong, S.W.; Lee, E.; Kim, S.H.; Crespi, N. Large-scale mobile phenomena monitoring with energy-efficiency in wireless sensor networks. Comput. Netw. 2015, 81, 116–135. [Google Scholar] [CrossRef]
- Hussain, C.S.; Park, M.S.; Bashir, A.K.; Shah, S.C.; Lee, J. A Collaborative Scheme for Boundary Detection and Tracking of Continuous Objects in Wsns. Intell. Autom. Soft Comput. 2013, 19, 439–456. [Google Scholar] [CrossRef]
- Zhong, C.; Worboys, M. Energy-Efficient Continuous Boundary Monitoring in Sensor Networks; Technical Report; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Boudries, A.; Aliouat, M.; Siarry, P. Detection and replacement of a failing node in the wireless sensors networks. Comput. Electr. Eng. 2014, 40, 421–432. [Google Scholar] [CrossRef]
- Sumalatha, G.; Zareena, N.; Raju, C.G. A Review on Failure Node Recovery Algorithms. Int. J. Comput. Trends Technol. 2014, 12, 94–98. [Google Scholar] [CrossRef]
- Demigha, O.; Hidouci, W.-K.K.; Ahmed, T. On Energy Efficiency in Collaborative Target Tracking in Wireless Sensor Network: A Review. IEEE Commun. Surv. Tutor. 2013, 15, 1210–1222. [Google Scholar] [CrossRef]
- Chang, W.-R.; Lin, H.-T.; Cheng, Z.-Z. CODA: A Continuous Object Detection and Tracking Algorithm for Wireless Ad Hoc Sensor Networks. In Proceedings of the 2008 5th IEEE Consumer Communications and Networking Conference, Las Vegas, NV, USA, 10–12 January 2008; pp. 168–174.
- Chen, J.; Kher, S.; Somani, A. Distributed Fault Detection of Wireless Sensor Networks. In Proceedings of the 2006 Workshop on Dependability Issues in Wireless Ad Hoc Networks and Sensor Networks, Los Angeles, CA, USA, 26 September 2006; pp. 65–72.
- Ding, M.; Chen, D.; Xing, K.; Cheng, X. Localized Fault-Tolerant Event Boundary Detection in Sensor Networks. In Proceedings of the 24th Annual Joint Conference of the IEEE Computer and Communications Societies, New York, NY, USA, 13–17 March 2005; pp. 902–913.
- Truong, T.T.; Brown, K.N.; Sreenan, C.J. An online approach for wireless network repair in partially-known environments. Ad Hoc Netw. 2015, 15, 47–64. [Google Scholar] [CrossRef]
- Younis, M.; Senturk, I.F.; Akkaya, K.; Lee, S.; Senel, F. Topology management techniques for tolerating node failures in wireless sensor networks: A survey. Comput. Netw. 2014, 58, 254–283. [Google Scholar] [CrossRef]
- Wang, S.; Mao, X.; Tang, S.J.; Li, X.Y.; Zhao, J.; Dai, G. Moovement-assisted connectivity restoration in wireless sensor and actor networks. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 687–694. [Google Scholar] [CrossRef]
- Schieferdecker, D. Location-Free Detection of Network Boundaries. ACM Trans. Sens. Netw. 2015, 11. [Google Scholar] [CrossRef]
- Oh, S. A scalable multi-target tracking algorithm for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2012, 2012, 938521. [Google Scholar] [CrossRef]
- Susca, S.; Bullo, F.; Martinez, S. Monitoring environmental boundaries with a robotic sensor network. IEEE Trans. Control Syst. Technol. 2008, 16, 288–296. [Google Scholar] [CrossRef]
- Rafiei, A.; Maali, Y.; Abolhasan, M.; Franklin, D. A geometrical sink-based cooperative coverage hole recovery strategy for WSNs. In Proceedings of the 2015 9th International Conference on Signal Processing and Communication Systems (ICSPCS), Cairns, Australia, 14–16 December 2015; pp. 1–8.
- Liu, H.; Cao, X.; He, J.; Cheng, P.; Li, C.; Chen, J.; Sun, Y. Distributed Identification of the Most Critical Node for Average Consensus. IEEE Trans. Signal Process. 2015, 63, 4315–4328. [Google Scholar] [CrossRef]
- Stanley-Marbell, P.; Basten, T.; Rousselot, J.; Oliver, R.S.; Karl, H.; Geilen, M.; Hoes, R.; Fohler, G.; Decotignie, J. System Models in Wireless Sensor Networks; Eindhoven University of Technology: Eindhoven, The Netherlands, 2008. [Google Scholar]
- Hossain, A. Sensing and Link Model for Wireless Sensor Network: Coverage and Connectivity Analysis. arXiv 2014. [Google Scholar]
- Beutel, J.; Römer, K.; Ringwald, M.; Woehrle, M. Deployment Techniques for Sensor Networks. Sens. Netw. 2009, 67322, 219–248. [Google Scholar]
- Devi, S.R. Classification of WSN Deployment Schemes. Int. J. Comput. Eng. Res. 2015, 4, 78–82. [Google Scholar]
- Younis, M.; Akkaya, K. Strategies and techniques for node placement in wireless sensor networks: A survey. Ad Hoc Netw. 2008, 6, 621–655. [Google Scholar] [CrossRef]




| Notation | Explanation |
|---|---|
| Boundary node (BN) | A node that receives at least one changed and one unchanged detection status of its one-hop neighbors. |
| Strong boundary node (SBN) | A BN that receives a detection status from its two-hop neighbors. |
| Leader node (LN) | A node that is selected among its one-hop neighbor BNs and sends its collected data from these nodes to the sink. |
| Node u | A node with a changed detection status. |
| Node v | A one-hop neighbor of node u. |
| Node w | A two-hop neighbor of node u. |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Imran, S.; Ko, Y.-B. A Continuous Object Boundary Detection and Tracking Scheme for Failure-Prone Sensor Networks. Sensors 2017, 17, 361. https://doi.org/10.3390/s17020361
Imran S, Ko Y-B. A Continuous Object Boundary Detection and Tracking Scheme for Failure-Prone Sensor Networks. Sensors. 2017; 17(2):361. https://doi.org/10.3390/s17020361
Chicago/Turabian StyleImran, Sajida, and Young-Bae Ko. 2017. "A Continuous Object Boundary Detection and Tracking Scheme for Failure-Prone Sensor Networks" Sensors 17, no. 2: 361. https://doi.org/10.3390/s17020361
APA StyleImran, S., & Ko, Y.-B. (2017). A Continuous Object Boundary Detection and Tracking Scheme for Failure-Prone Sensor Networks. Sensors, 17(2), 361. https://doi.org/10.3390/s17020361





