A Straight Skeleton Based Connectivity Restoration Strategy in the Presence of Obstacles for WSNs
Abstract
:1. Introduction
Our Contribution
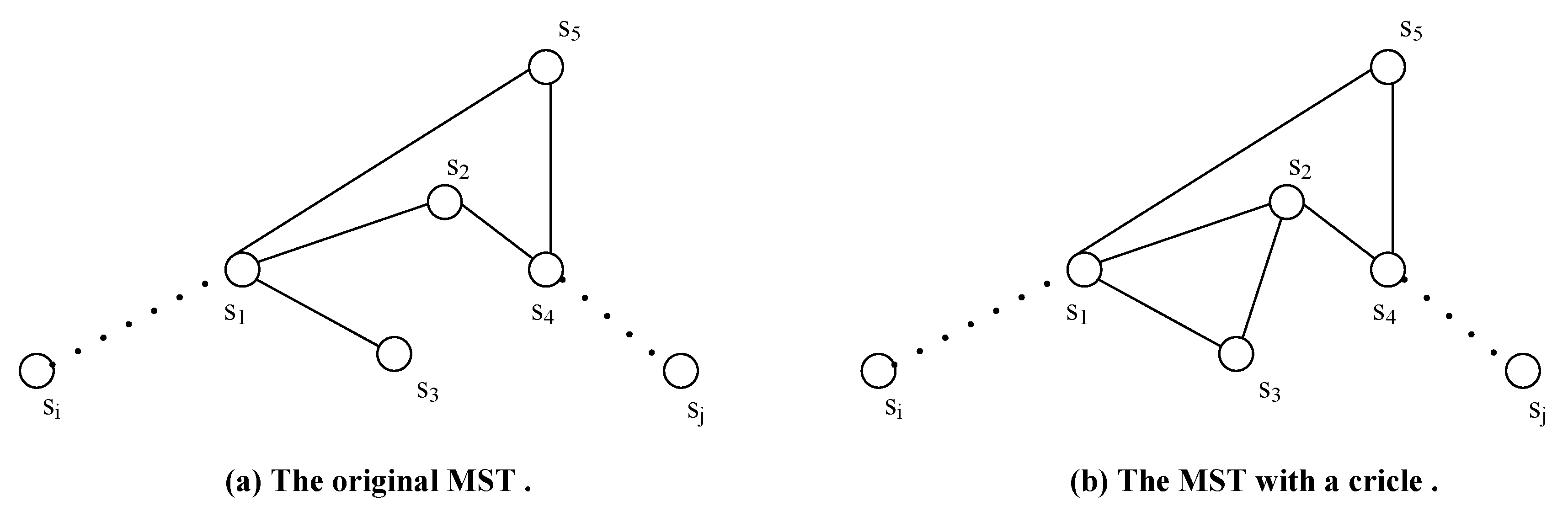
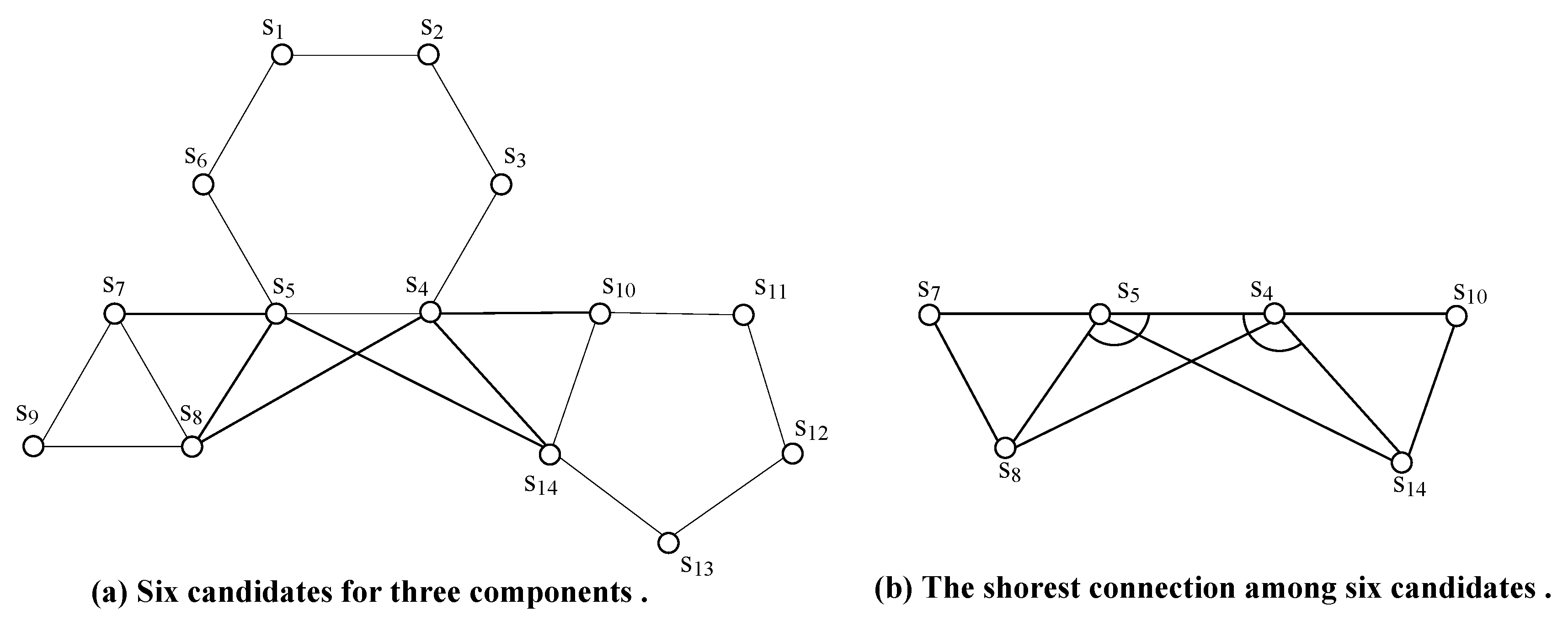
- We modify the well-known Minimum Spanning Tree (MST) construction algorithm to a circle-tolerant one, namely -, by choosing multiple nodes on the perimeter of each component as corresponding representatives such that the MST is constructed with the rule that circles formed by nodes on the same components should be neglected. Compared with other strategies that choose only one node for each component as its representative, the spanning tree established by - is much shorter.
- We develop an obstacle–avoid algorithm, OA, to deal with the case that there exist obstacles lying on the line-segment between each pair of nodes. Instead of choosing a detour going along the perimeter of an obstacle, the candidate point on the perimeter of the obstacle is carefully chosen such that a shortest path around the obstacle consists of at least two line-segments tangent at such point. In addition, compared with other strategies disregarding the presence of obstacles, OA can be applied to more realistic scenarios.
- We devise a straight skeleton based algorithm, SSIN, to build an SMT such that the shortest inter-component connection is achieved. Each straight skeleton will be placed within the potential convex hull of MST as the deployment route for RNs. Furthermore, if multiple line-segments between pairs of nodes have obstacles, then the SSIN is an option to avoid obstacles.
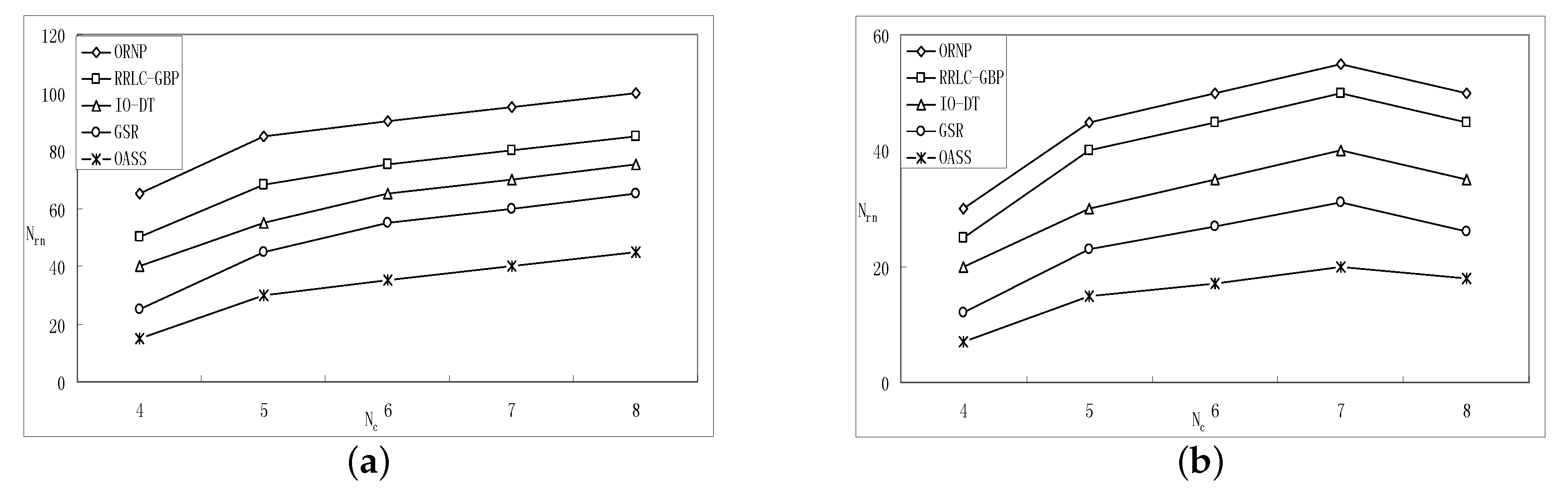
- We prove that OASS is a 3- approximation algorithm with the complexity of , and the approximation ratio can reduce to while the network topology can be decomposed into a series of convex hulls. The theoretical analysis and simulations show that the performance of OASS is better than other strategies, especially a series of which deploy RNs toward the center of the deployment area, not only in the number of RNs required but the quality of the established topology (i.e., distances between components, delivery latency and balanced traffic load) as well.
2. Related Works
3. Preliminary
3.1. System Model
- 1.
- Each terminal is a leave and each Steiner point connects to exactly three terminals.
- 2.
- The angle between each pair of adjacent edges at a Steiner point is exactly .
- 3.
- There are totally Steiner points for n terminals.
3.2. Problem Statement
4. The OASS Approach
4.1. Adapted Minimum Spanning Tree Construction Algorithm (-)
| Algorithm 1 Adapted Minimum Spanning Tree Construction Algorithm -. |
| Input: all nodes on the perimeter of all components and a set of shortest paths |
| Output: an MST |
| choose all nodes on as representatives of |
| employ to construct an MST among all representatives with one rule that each circle formed by nodes on the same component should be neglected |
| return an MST |
4.2. Obstacle–Avoid Algorithm (OA)
| Algorithm 2 Obstacle–Avoid Algorithm OA. |
| Input: the set of edges |
| Output: each a set of shortest paths around obstacles |
| for each pair of nodes and do |
| if there is an obstacle O on the line-segment then |
| find two points x and y on such that there exist two tangents and |
| using the least number of points on to construct |
| end if |
| end for |
| return a set of shortest paths around obstacles |
4.3. Straight Skeleton Based SMT Construction Algorithm (SSIC)
| Algorithm 3 Straight Skeleton based SMT Construction Algorithm (SSIC). |
| Input: an MST that consists of n representatives |
| Output: a straight skeleton based tree |
| randomly choose a leave node to draw an euler closed trail |
| for all do |
| if there exists an edge such that |
| then |
| end if |
| if there is a such that then and |
| else |
| end if |
| end for |
| for all s do |
| if there is no obstacles intersecting with the straight skeleton within the then |
| the straight skeleton of the is a relay node deployment route |
| else split the into parts such that |
| if there exists a , the straight skeleton of which is not intersecting with obstacles then |
| the straight skeleton will be the route for placing s |
| end if |
| for other s, , do each edge is a relay node deployment route |
| end for |
| end if |
| end for |
| return a straight skeleton based tree |
5. Performance Analysis
5.1. Theoretical Analysis
- 1.
- is the MST of G.
- 2.
- .
5.2. Validation Experiment
5.2.1. Comparison between the SMT and the Straight Skeleton
5.2.2. Experiment Setup, Performance Metrics and Baseline Approaches
5.2.3. Simulation Results and Comparison of the Generated Topology Quality
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Younis, M.; Senturk, I.F.; Akkaya, K.; Lee, S.; Senel, F. Topology management techniques for tolerating node failures in wireless sensor networks: A survey. Comput. Netw. 2014, 58, 254–283. [Google Scholar] [CrossRef]
- Chen, D.; Du, D.Z.; Hu, X.D.; Lin, G.H.; Wang, L.; Xue, G. Approximations for Steiner trees with minimum number of Steiner points. J. Glob. Optim. 2000, 18, 17–33. [Google Scholar] [CrossRef]
- Tang, J.; Hao, B.; Sen, A. Relay node placement in large scale wireless sensor networks. Comput. Commun. 2006, 29, 490–501. [Google Scholar] [CrossRef]
- Lloyd, E.L.; Xue, G. Relay Node Placement in Wireless Sensor Networks. IEEE Trans. Comput. 2007, 56, 134–138. [Google Scholar] [CrossRef]
- Cheng, X.; Du, D.Z.; Wang, L.; Xu, B. Relay sensor placement in wireless sensor networks. Wirel. Netw. 2008, 14, 347–355. [Google Scholar] [CrossRef]
- Misra, S.; Hong, S.D.; Xue, G.; Tang, J. Constrained relay node placement in wireless sensor networks: Formulation and approximations. IEEE/ACM Trans. Netw. 2010, 18, 434–447. [Google Scholar] [CrossRef]
- Yang, D.; Misra, S.; Fang, X.; Xue, G.; Zhang, J. Two-tiered constrained relay node placement in wireless sensor networks: Computational complexity and efficient approximations. IEEE Trans. Mob. Comput. 2012, 11, 1399–1411. [Google Scholar] [CrossRef]
- Misra, S.; Majd, N.E.; Huang, H. Approximation algorithms for constrained relay node placement in energy harvesting wireless sensor networks. IEEE Trans. Comput. 2014, 63, 2933–2947. [Google Scholar] [CrossRef]
- Wang, X.; Xu, L.; Zhou, S. Restoration Strategy Based on Optimal Relay Node Placement in Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2015, 11, 409085. [Google Scholar] [CrossRef]
- Efrat, A.; Fekete, S.P.; Mitchell, J.S.B.; Polishchuk, V.; Suomela, J. Improved approximation algorithms for relay placement. ACM Trans. Algorithms 2016, 12, 20. [Google Scholar]
- Senel, F.; Younis, M. Novel relay node placement algorithms for establishing connected topologies. J. Netw. Comput. Appl. 2016, 70, 114–130. [Google Scholar] [CrossRef]
- Joshi, Y.K.; Younis, M. Exploiting skeletonization to restore connectivity in a wireless sensor network. Comput. Commun. 2016, 75, 97–107. [Google Scholar] [CrossRef]
- Lee, S.; Younis, M. Optimized relay node placement for connecting disjoint wireless sensor networks. Comput. Netw. 2012, 56, 2788–2804. [Google Scholar] [CrossRef]
- Ranga, V.; Dave, M.; Verma, A.K. Relay node placement to heal partitioned wireless sensor networks. Comput. Electr. Eng. 2015, 48, 371–388. [Google Scholar] [CrossRef]
- Lee, S.; Younis, M.; Lee, M. Connectivity restoration in a partitioned wireless sensor network with assured fault tolerance. Ad Hoc Netw. 2015, 24, 1–19. [Google Scholar] [CrossRef]
- Uwitonze, A.; Huang, J.; Ye, Y.; Cheng, W. Connectivity Restoration in Wireless Sensor Networks via Space Network Coding. Sensors 2017, 17, 902. [Google Scholar] [CrossRef] [PubMed]
- Abbas, A.; Younis, M. Establishing connectivity among disjoint terminals using a mix of stationary and mobile relays. Comput. Commun. 2013, 36, 1411–1421. [Google Scholar]
- Joshi, Y.K.; Younis, M. Restoring connectivity in a resource constrained WSN. J. Netw. Comput. Appl. 2016, 66, 151–165. [Google Scholar] [CrossRef]
- Zhou, S.; Wu, M.; Shu, W. Terrain-constrained mobile sensor networks. In Proceedings of the GGLOBECOM ’05, IEEE Global Telecommunications Conference, St. Louis, MO, USA, 28 November–2 December 2005; p. 5. [Google Scholar]
- Senturk, I.F.; Akkaya, K.; Janansefat, S. Towards realistic connectivity restoration in partitioned mobile sensor networks. Int. J. Commun. Syst. 2014, 29, 230–250. [Google Scholar] [CrossRef]
- Truong, T.T.; Brown, K.N.; Sreenan, C.J. Multi-objective hierarchical algorithms for restoring wireless sensor network connectivity in known environments. Ad Hoc Netw. 2015, 33, 190–208. [Google Scholar] [CrossRef]
- Mi, Z.; Yang, Y.; Yang, J. Restoring connectivity of mobile robotic sensor networks while avoiding obstacles. Sens. J. IEEE 2015, 15, 4640–4650. [Google Scholar] [CrossRef]
- Wang, X.; Xu, L.; Zhou, S.; Wu, W. Hybrid Recovery Strategy Based on Random Terrain in Wireless Sensor Networks. Sci. Program. 2017, 2017, 1–19. [Google Scholar] [CrossRef]
- Robins, G.; Zelikovsky, A. Tighter bounds for graph Steiner tree approximation. SIAM J. Discret. Math. 2005, 19, 122–134. [Google Scholar] [CrossRef]
- Bondy, J.A.; Murty, U.S.R. Graph Theory with Applications; Macmillan: London, UK, 1976; pp. 237–238. [Google Scholar]
- Soukup, J.; Chow, W.F. Set of test problems for the minimum length connection networks. ACM SIGMAP Bull. 1973, 15, 48–51. [Google Scholar] [CrossRef]
- Du, D.Z.; Hwang, F.K. The state of art on Steiner ratio problems. Comput. Euclidean Geom. 1992, 1, 163–191. [Google Scholar]
- Therese, B.; Martin, H.; Stefan, H.; Dominik, K.; Peter, P. A simple algorithm for computing positively weighted straight skeletons of monotone polygons. Inf. Process. Lett. 2015, 115, 243–247. [Google Scholar]
- Barber, C.B.; Dobkin, D.P.; Huhdanpaa, H. The quickhull algorithm for convex hulls. ACM Trans. Math. Softw. 1996, 22, 469–483. [Google Scholar] [CrossRef]





| Authors | Approximation Ratio | Complexity |
|---|---|---|
| Misra et al. [8] | 12.4 | |
| Lloyd et al. [4] | 7 | |
| Yang et al. [7] | 6.43 | |
| Misra et al. [6] | 6.2 | |
| Tang et al. [3] | 4.5 | Not available |
| Efrat et al. [10] | 3.11 | |
| Cheng et al. [5] | 3 | |
| Chen et al. [2] | 3 | |
| Wang et al. [9] | 3 | |
| OASS (this paper) | 3 | |
| OASS satisfying a certain condition (this paper) | ||
| Cheng et al. [5] | 2.5 |
| Symbols | Descriptions |
|---|---|
| the polygon consists of nodes on the perimeter of | |
| the convex hull of an obstacle O | |
| a path from to | |
| a shortest path from to around the obstacle O | |
| the Euclidean distance of an edge | |
| the length of the graph G in Euclidean space, that is | |
| s consumption function of the approach A |
| Number of Soukup Example | Number of Nodes | SMT | Straight Skeleton |
|---|---|---|---|
| EX.1 | 5 | 165.43 | 166.57 |
| EX.2 | 6 | 155.06 | 156.04 |
| EX.3 | 6 | 158.60 | 159.05 |
| EX.4 | 6 | 130.15 | 131.03 |
| EX.5 | 9 | 163.20 | 163.85 |
| EX.6 | 9 | 128.50 | 129.10 |
| EX.7 | 12 | 221.20 | 222.06 |
| EX.8 | 14 | 122.02 | 122.64 |
| EX.9 | 3 | 115.54 | 116.32 |
| EX.10 | 10 | 164.26 | 165.20 |
| EX.11 | 62 | 382.56 | 383.62 |
| EX.12 | 14 | 172.30 | 173.23 |
| EX.13 | 3 | 104.15 | 105.10 |
| EX.14 | 5 | 182.92 | 183.05 |
| EX.15 | 4 | 50.30 | 51.22 |
| Hops | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| A | B | A | B | A | B | A | B | A | B | |
| 0 | 0 | 7 | 9 | 8 | 9 | 8 | 8 | 7 | 8 | |
| 7 | 9 | 0 | 0 | 5 | 10 | 9 | 9 | 8 | 9 | |
| 8 | 9 | 5 | 10 | 0 | 0 | 10 | 9 | 9 | 9 | |
| 8 | 8 | 9 | 9 | 10 | 9 | 0 | 0 | 5 | 7 | |
| 7 | 8 | 8 | 9 | 9 | 9 | 5 | 7 | 0 | 0 | |
| Sum | 30 | 34 | 29 | 37 | 32 | 37 | 32 | 33 | 29 | 33 |
| Ave. | 6 | 6.8 | 5.8 | 7.4 | 6.4 | 7.4 | 6.4 | 6.6 | 5.8 | 6.6 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, X.; Xu, L.; Zhou, S. A Straight Skeleton Based Connectivity Restoration Strategy in the Presence of Obstacles for WSNs. Sensors 2017, 17, 2299. https://doi.org/10.3390/s17102299
Wang X, Xu L, Zhou S. A Straight Skeleton Based Connectivity Restoration Strategy in the Presence of Obstacles for WSNs. Sensors. 2017; 17(10):2299. https://doi.org/10.3390/s17102299
Chicago/Turabian StyleWang, Xiaoding, Li Xu, and Shuming Zhou. 2017. "A Straight Skeleton Based Connectivity Restoration Strategy in the Presence of Obstacles for WSNs" Sensors 17, no. 10: 2299. https://doi.org/10.3390/s17102299
APA StyleWang, X., Xu, L., & Zhou, S. (2017). A Straight Skeleton Based Connectivity Restoration Strategy in the Presence of Obstacles for WSNs. Sensors, 17(10), 2299. https://doi.org/10.3390/s17102299




