1. Introduction
The IEEE 802.15.4 [
1] standard is popular for short-range and low-power wireless networks, which supports sixteen channels in 2.4-GHz and ten channels in 902-/928-MHz Industrial, Scientific and Medical (ISM) band. It specifies the physical and medium access control (MAC) layer and defines the format of the data handling. ZigBee is an enhancement to the IEEE 802.15.4 that supports the network to application layer. Integration of ZigBee with IEEE 802.15.4 is popular because of its low power consumption, low bandwidth, low cost and ease to implement. It is expected that these ZigBee sensors will play a major role in different applications of IoT. However, the critical requirements in the industrial/commercial IoT applications such as high reliability and low energy consumption in the industrial environment have not been addressed adequately in the IEEE 802.15.4 standard.
The IEEE 802.15.4 standard defines the slotted and unslotted channel access mechanism through carrier sense multiple access with collision avoidance (CSMA/CA) for communication. To start a transmission, each IEEE 802.15.4-enabled node first performs clear channel assessment (CCA) to ensure that the channel is idle. The IEEE 802.15.4e [
2] working group has redesigned the existing IEEE 802.15.4 MAC protocol to overcome the limitations such as low latency and robustness to meet the critical requirements of IoT applications. They define a low-power multi-hop MAC protocol, which is capable of addressing the emerging needs of different IoT applications. The final standard of the IEEE 802.15.4e MAC enhancement protocol adopts the ideas like slotted access, multi-channel communications and frequency hopping from WirelessHART [
3] and International Society of Automation (ISA) 100.11.a [
4].
IEEE 802.15.4e supports low latency deterministic network (LLDN) MAC, which can be applied to different applications like fall detection, factory automation, robots, automated dispensations, airport logistic and many emergent automated applications. The major requirements of such applications are to reduce the delay and energy consumption. It is to be noted that the sensing data of applications are typically of a few bytes, which make the time slot size very small. As a result, the sensing data from nodes can be accommodated in one superframe due to the small slot size. Allocating a dedicated time slot for each LLDN node in the superframe provides a deterministic system. Due to the strict requirements of such low-latency applications, LLDN uses a star topology with a minimal number of superframe structures. The star topology has a special node called the coordinator that manages communications among the nodes in a personal area network (PAN).
Various applications of wireless sensor networks (WSN) require low latency data transmissions. Therefore, if any sensor node fails to transmit its packet, a retransmission for the failed packet should be arranged within the current superframe to meet the low latency requirement. All retransmissions within an LLDN superframe are possible whenever the numbers of failed packet are less than or equal to the available retransmission slots. However, there is a problem that the numbers of failed packets are greater than the available retransmission slots. The PAN coordinator fixes the number of retransmission slots for a superframe and cannot be changed dynamically. Note that there is no provision of retransmissions in IEEE 802.15.4e LLDN in the case of the non-availability of retransmission slots, and as a result, the performance of the network in terms of delay, throughput and packet drop rate is degraded. Two types of slot allocations (dedicated or shared) are made for nodes attached to the coordinator in the LLDN superframe. In the case of shared slots, when a slot is not used by the slot owner, it can be used by other nodes associated with the slot through the CSMA/CA mechanism. As per the existing CSMA/CA mechanism of the IEEE 802.15.4e standard, a node has to go for the CCA twice in order to avoid the collision due to acknowledgment transmissions.
Normally, collisions occur in WSN either due to simultaneous channel assessment or a hidden terminal problem. When two nodes are not present in the communication range of each other and transmit to another node, which is present within both’s communication range, it is known as the hidden terminal problem. The hidden terminal problem can be avoided by allocating a common shared slot in the LLDN superframe to the nodes present within the same communication range and different shared slots to the hidden nodes. The random backoff and CCA in the CSMA/CA mechanism avoid the collisions and are only effective for the nodes that are not hidden. However, they cannot minimize the number of collisions due to simultaneous transmissions, and therefore, these problems need to be addressed for better channel utilization. To mitigate the problems, a new channel access mechanism is proposed in this paper.
The originalities in our work are that a new prediction model is designed to predict the optimal numbers of retransmission slots based on the historical data of the previous transmissions and performance analysis of different network parameters of the LLDN superframe such as reliability, throughput, energy consumption and delay, which have not been studied yet. The main contributions of our work can be summarized as follows.
In order to reduce the power consumption of sensors, a new CSMA/CA mechanism is designed for the shared slots of the LLDN superframes.
In order to avoid collision due to simultaneous transmission by nodes, a new channel access mechanism is designed.
Mathematical models are designed to predict the optimal numbers of retransmission slots based on the historical data of the previous transmissions.
The rest of the paper is organized as follows. The survey of related works of the existing IEEE 802.15.4 standard are given in
Section 2. The overview of LLDN superframe is given in
Section 3. The network model and proposed MAC mechanisms are presented in
Section 4. Various analytical models are designed in
Section 5. The performances of various network parameters are studied in
Section 6. Simulation results are given in
Section 7, and concluding remarks are made in
Section 8.
2. Related Works
A general approach to evaluate the IEEE 802.15.4 performance of slotted the CSMA/CA protocol for only the unsaturated traffic condition is designed in [
5]. By considering both saturated and unsaturated traffic to predict the energy consumption, as well as throughput, the authors in [
6] have presented an analytical model for the IEEE 802.15.4 MAC protocol. A Markov chain-based analytical model is introduced in [
7] to evaluate the impact of throughput and energy consumption on the probability of delivering a packet. However, these protocols did not talk about how to allocate the retransmission slots in case of packet failures. The authors in [
8] have designed one analytical model for the guaranteed time slot (GTS) allocation mechanism during the contention-free period (CFP). The authors in [
9] have proposed a methodology to analyze the GTS mechanism in the CFP. The performance of IEEE 802.15.4 MAC is analyzed in [
10] for both CFP and the contention access period (CAP). However, these works did not address transmission failures due to interference or collision, which is an important issue for the low latency applications. The authors in [
11] have designed one additional carrier sensing algorithm to get information from the busy channel due to data or acknowledgment (ACK) transmissions during the second CCA. However, the power consumption will be more if the second CCA is found busy due to data/ACK transmissions. A new MAC protocol is designed in [
12] to avoid the channel being busy due to acknowledgment packet transmission without any additional CCA. To increase the probability of data transmission by ignoring the first CCA channel busy condition due to ACK transmissions, the authors in [
13] propose one segmentized CCA mechanism. However, there is no improvement in the case that a node transmits a data packet instead of an ACK.
The effects of different
macSuperframeOrder (SO) values on the total network throughput, delay and energy consumption through simulation have been studied in [
14]. However, the work entirely focuses on the ideal channel condition, which is not realistic because the channel condition oscillates between good and poor in the wireless environment. The contention-based protocols are widely used in WSN applications to reduce delay and collisions. The authors [
15] have studied the stability and accuracy of the wireless technology by using the IEEE 802.15.4/ZigBee technology in monitoring human body temperature. However, the authors have not considered any retransmission opportunity for transmission failure. A mathematical model is designed in [
16] based on stochastic geometry, which is used for performance evaluations of success probability in transmitting packets from nodes to the coordinator. However, the authors have not done the performance analysis such as delay and energy, which are crucial factors for some WSN applications. The impact of fading statistics on the MAC performance in terms of reliability, delay and power consumption by varying traffic rates, inter-nodes distances, carrier sensing range and the signal-to-interference-plus-noise ratio (
) threshold have been studied in [
17]. However, all of these works are based on the IEEE 802.15.4 standard. The major requirements of industrial application are very low latency communication. Hence, the LLDN MAC mechanism of the IEEE 802.15.4e [
2] standard is most suitable for these requirements.
Comparisons of different technical parameters between Bluetooth, ZigBee and Wi-Fi are given in [
18], where the received signal strength indicator (RSSI) value, round trip delay (RTD) time and latency are analyzed. The performance of the network considering both high and low data rate is analyzed in [
19]. The impact of retry limit, backoff, network lifetime under all different data rates and traffic loads is also analyzed in the same work. However, they have not taken the priority into account for the transmission failure by the nodes. A comprehensive analysis of energy consumption of body area networks including the effect of packet inter-arrival time are given in [
20]. However, the work did not consider retransmissions within the current superframe. To enhance the reliability of the LLDN networks, the authors in [
21] propose one retransmission scheme for the time-varying channels by choosing the best relay node through the reinforcement-learning method. A new MAC protocol is proposed in [
22] to minimize the energy consumption in WSN, where the authors have not considered the transmission failure due to the channel error. To avoid external interference, different frequency adoption schemes are proposed in [
23]. A priority-based adaptive time slot allocation method is proposed in [
24] based on the IEEE 802.15.4 MAC protocol. However, they have not considered the transmission failure nodes.
The stability of the WSNs in terms of throughput is analyzed in [
25] considering the exponential backoff scheme. However, the work is based on the IEEE 802.15.4 MAC mechanism. Collisions normally occur when the number of nodes increases in the network. To avoid the energy consumption due to collisions and to enhance the throughput of the network, the authors in [
26] have proposed one collision-free MAC mechanism. However, they have not considered the retransmission opportunity for the transmission failure nodes. The hidden node problem increases the number of retransmissions in the network such that the battery lifetime of nodes is affected. Imperfect channel sensing is also one of the causes to significantly affect the network performance. To avoid the hidden node collisions, a new protocol is proposed in [
27] by using carrier sense multiple access with collision notification (CSMA/CN) to approximate carrier sense multiple access with collision detection (CSMA/CD) for the wireless network. In this work, the authors use two antennas to emulate full duplex mode so that collision notifications can be allowed to broadcast, and the ongoing transmissions can be aborted. The use of transmission power control can help to address industrial issues concerning energy consumption, interference and fading. In [
28], an adaptive multi-channel transmission power control algorithm for industrial wireless networks such as WirelessHART, ISA 100.11a has been designed RSSI. However, when a transmitted packet is not acknowledged properly, it needs to be retransmitted at the cost of additional energy and delay. Besides, the authors did not consider the transmission failure due to channel error and the retransmission opportunity in the current superframe to avoid the delay.
A Markov model is designed in [
29] to analyze the throughput of the IEEE 802.15.4 network with the presence of hidden nodes. Almost all existing analytical models assume ideal channel conditions. However, in real-world scenarios, wireless channels exhibit burst errors. A three-dimensional Markov chain model is proposed in [
30], which is applied to analyze the network performance under burst channel errors. Comparative studies between IEEE 802.15.4e LLDN and IEEE 802.15.4 slotted CSMA/CA have been analyzed in [
31] under the ideal channel condition, which is not realistic. In [
32], the authors evaluate the impact of losing synchronization under the beacon-enabled star topology of the IEEE 802.15.4 network. To avoid collisions in a dense network, a new variable CCA MAC protocol for WSNs is designed and the performance analyzed in [
33]. However, this protocol needs a significant amount of energy, which is the major constraint for sensors.
From the current literature survey, we noticed that most works are based on the performance analysis of the IEEE 802.15.4 standard. To the best of our knowledge, the performance of LLDN has not been analyzed yet, which has many applications in home, healthcare and industry automation. In this paper, we not only propose a new channel access mechanism to avoid the collision due to simultaneous transmissions, but also design one CSMA/CA mechanism for the shared slots of LLDN superframes. In addition, one prediction model is proposed to predict the optimal number of required retransmission slots based on the historical data of the previous transmissions, and one analytical model is proposed to study the performance of different network parameters such as reliability, throughput, energy consumption and delay.
4. Proposed MAC for LLDN
In this section, for collisions due to simultaneous transmissions, a new MAC protocol is designed. Below, we first give the network model, as well as our assumptions and then present our detailed MAC protocol.
4.1. Network Model
Consider a WSN of star topology, where
N number of nodes,
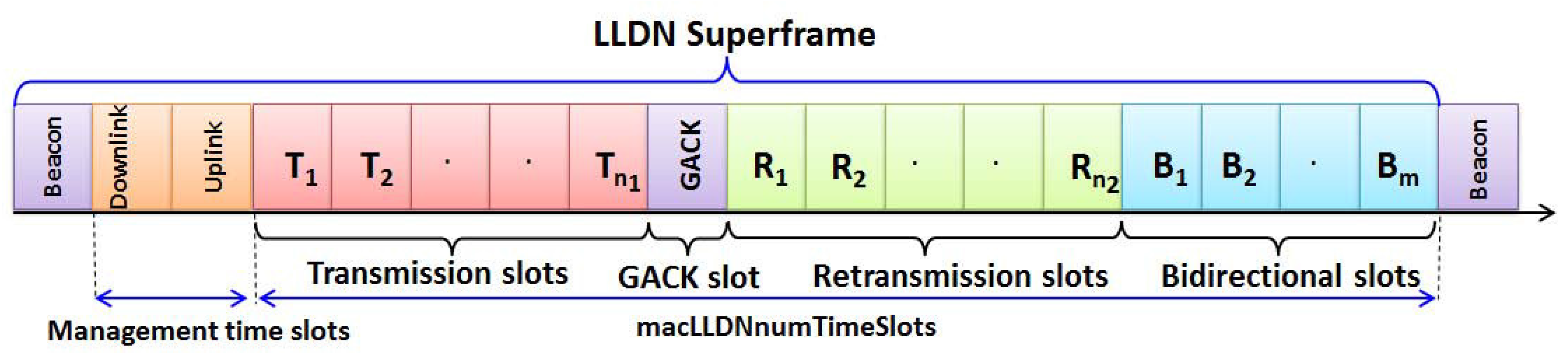
, are associated with the PAN coordinator. Each node uses the CSMA/CA channel access mechanism in the allotted shared slot for competing to transmit data frames to the coordinator. The coordinator follows the LLDN superframe structure as shown in
Figure 1. The owner nodes associated with dedicated slots have a better chance for successful transmissions. Assume that nodes always transmit the most recent generated data to the coordinator, and the sensing range of a node is twice of the transmission range. Every node goes for the power saving mode after the scheduled transmission/receiving slots. A node defers the transmission during accessing the channel in a shared slot if the remaining time is not enough to transmit the data in the shared slot.
4.2. Proposed CSMA/CA Mechanism for LLDN
Consider a node that tries to transmit a generated packet at a certain time. According to the procedure of the IEEE 802.15.4e MAC protocol, the node needs to wait for a random number of back-off periods and then goes for CCAs twice. The node is allowed to transmit data, if the channel is idle during both CCAs. Unfortunately, this procedure can cause collision due to simultaneous transmissions, if any two nodes generate the same random back-off period. Since a node remains unaware of the collision until the acknowledgment is received, it goes for the data transmission, which increases the energy consumption of the node. Our proposed approach wants to eliminate the simultaneous transmissions to avoid the collision, which can reduce energy consumption. According to the standard, one backoff slot is 20 symbol periods, and the CCA detection time requires eight symbol periods. One symbol is considered as s, and the data rate is 250 kbps. Therefore, using the rest 12 symbols of a mini slot, we can send a signal of bytes. We use these remaining 12 symbols and design a uniquely computed known signal (KS) set of the six-byte uniquely-computed signal (, and each element has the length of six bytes) for our proposed method to avoid the simultaneous collision. These known signals are the random patterns designed by the coordinator that distract from the information. In our proposed method, these six-byte signals acts like a preamble to sense the medium in order to know whether any other node is performing CCA at the same slot within the communication range of the node.
It is proposed that a node utilizes two antennas in which one is used for normal transmissions and the other one is dedicated to listening to the intended signal. The presence of a dual antenna in the sensor may increase the hardware cost. However, it reduces the power consumption significantly [
27]. The concept of using two antennas in our protocol is similar to the idea given in [
27], but the power consumption of our protocol is less than [
27], as both antennas in our design are active during the CCA period only instead of being fully active throughout the communication duration in [
27].
When a node has a packet to transmit, it goes for the random backoff and CCA. During the first 128
s of the mini slot, a node can find the channel busy if any other node is transmitting at the same time. The node can enable its transmitter after 128
s of the CCA, and sends one random six-byte signal from
(say
). All nodes performing CCA at the same time also transmit one random signal. The node of the received signal in the same slot will calculate the signal correlation with the rest of the signals in
. This signal correlation is the optimal technique [
27] for detecting a known waveform in the environment with random noise.
Let
be the complex number representing the
n-th transmitted symbol and
be the complex number representing the
n-th received symbol. Then:
where
H is a complex number representing the channel coefficient between the transmitter and the receiver and
is the random noise. The cross-correlation known symbol pattern of length
L in the received signal
Y at a shifted length
l is:
where
is the complex conjugate of
. The cross-correlation value
is low, when
is not present in
Y. Taking a threshold for the correlation coefficient, we can detect the presence of
. The cross-correlation value is greater than the known signal threshold
, when
is aligned to the same features in the received signal. The node makes the channel free for others in the vicinity, if the correlation value is above
. A node goes for the transmission if it finds the cross-correlation value to be below
, i.e., if it does not receive any signal during the CCA from other nodes present within the carrier sense range of the node.
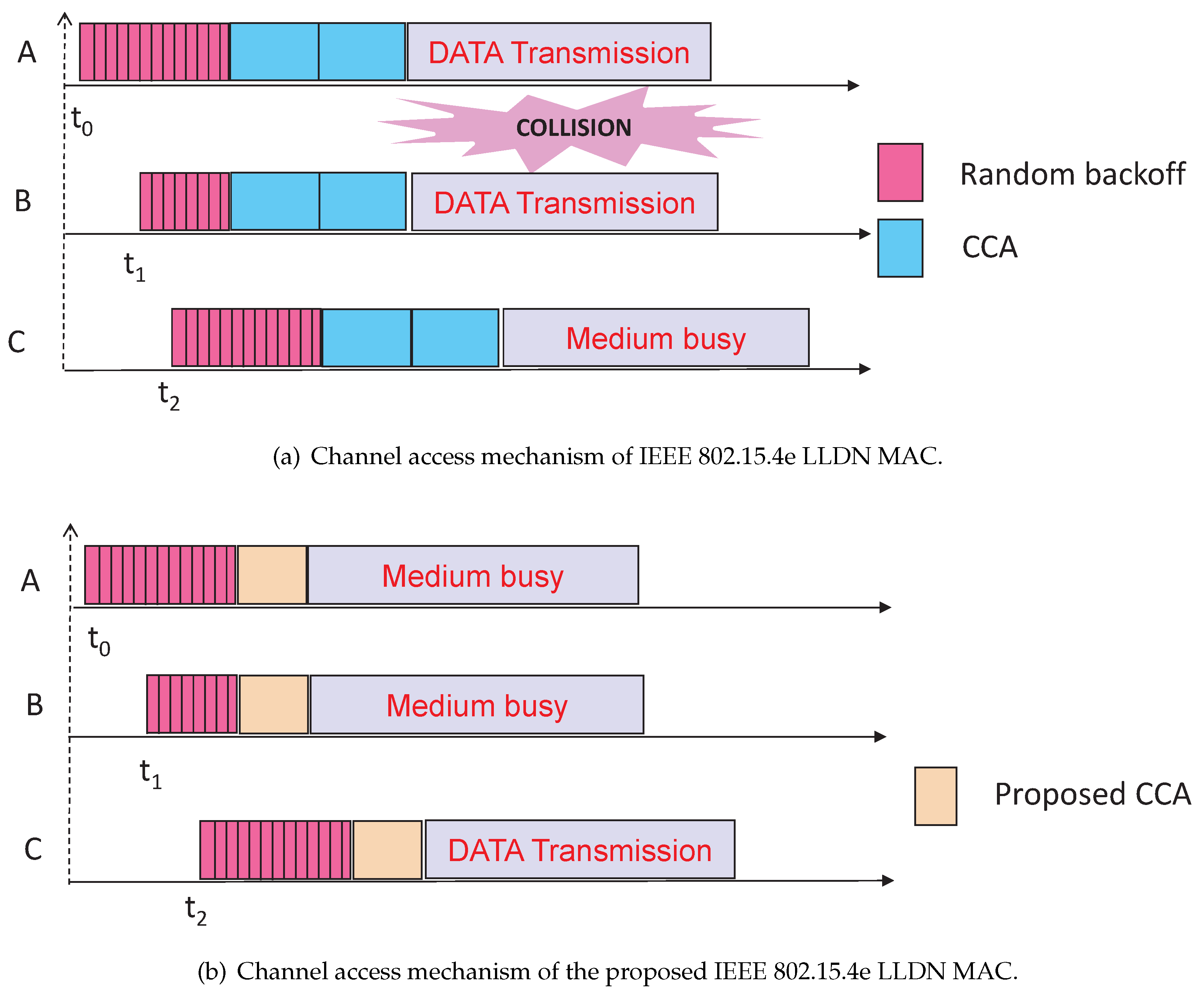
As shown in
Figure 2a, let data packets be arrived at nodes
A,
B and
C at time
,
and
, respectively, where nodes
A and
B perform the channel access at the same slot after their random backoff. Both nodes find the channel busy due to performing CCA simultaneously. Hence, both of them should go for the random backoff. On the contrary, in IEEE 802.15.4e LLDN MAC, both nodes find the channel idle and transmit there data, which leads to a collision. Again, as shown in
Figure 2b, node
C finds the channel idle and transmits its data successfully. However, node
C finds the channel busy in IEEE 802.15.4e LLDN MAC. Therefore, by avoiding simultaneous transmissions, our proposed channel access mechanism saves energy for nodes
A and
B and enhances throughput for node
C. The detailed procedure of our proposed carrier sensing mechanism is given in Algorithm 1.
| Algorithm 1 New carrier sensing mechanism |
- Require:
Known signal and received signal Y. - Ensure:
Channel access success/failure. - 1:
Locate backoff period boundary, and perform CCA for 128 s; - 2:
if channel is found idle then - 3:
; - 4:
Enable transmitter and transmit one random signal from ; - 5:
Receive the signal Y; - 6:
while do - 7:
if then - 8:
Calculate ; - 9:
if then - 10:
Channel access failure and stop; - 11:
end if - 12:
else - 13:
j = j + 1; - 14:
end if - 15:
end while - 16:
Channel access success; - 17:
end if
|
4.3. Proposed CSMA/CA Mechanism for Shared Slots
The nodes in the network following the IEEE 802.15.4e CSMA/CA mechanism get equal chances to access the channel. For data transmission during dedicated slots in the LLDN superframe, the slot owner transmits data directly, whereas in the case of shared slots , nodes compete to send data by following CSMA/CA mechanism. Let the time duration of one slot, performing CCA and data transmission be , and , respectively. The nodes during the shared slots have to adopt the CSMA/CA procedure according to the recent standard. All nodes have to perform CCA two times to avoid collisions due to the transmission of acknowledgment. However, the acknowledgment for all nodes in the LLDN superframe is aggregated through one common GACK, and the use of two CCAs is not required. Hence, we suggest to modify the current channel access mechanism in order to reduce the energy consumption and latency by restricting the number of CCAs to one.
As per the current IEEE 802.15.4e standard, the node with to-be-transmitted data initializes the variables CW, NB and BE: CW represents the contention window, which depends on the random backoff value; NB represents the number of times the node has been delayed before the current transmission and is initialized to zero for each new transmission; BE represents the backoff exponent whose value increases on each channel access failure. Before transmission, the node chooses a random number in the range of as backoff time periods. When this backoff period reaches zero, the node in the shared slot performs CCAs twice and starts transmission if the channel is found idle during these CCAs.
Due to the smaller slot size of the LLDN superframe, we propose here only one time random backoff before the channel access. As described in Algorithm 2, consider a node that tries to transmit data in a shared slot of the LLDN superframe. If the slot owner of the shared slot has no data to transmit, associated nodes can assess the slot through the CSMA/CA procedure. In our proposed mechanism, associated nodes have to delay for the duration of the random backoff period in the range of units, where is the size of the contention window for the shared slots. Let be the number of nodes having data arrival rate associated with the shared slot. Hence, the expected number of active nodes could be . To avoid choosing the same random backoff value by the nodes, we consider . After the random backoff period is over, the tagged node accesses the channel in the case that the transmission is possible with the current remaining time of the shared slot. Otherwise, nodes have to store their remaining backoff time at the end of the shared slot and resume the same procedure in the next shared slot.
If a channel is found idle during the CCA, a node can transmit data and waits for the ACK. The received corresponding ACK is considered as a successful transmission. However, if the node fails to receive the ACK due to collision or channel error and a retransmission slot (SLOTR) is available, it can retransmit the data. Otherwise, the packet will be discarded due to the retry failure. The retransmission slots are not assigned exclusively by the coordinator. The total numbers of retransmission slots available in the current superframe are broadcast in the beacon and the number of failed nodes through GACK by the coordinator. The node that fails first during the transmission can use the first retransmission slot. Our proposed model can reduce the number of CCAs to minimize the amount of control packet overhead.
| Algorithm 2 New channel access mechanism |
- Require:
Number of sensor attached to the shared slot. - Ensure:
Transmission success/failure. - 1:
if and not then - 2:
locate backoff period boundary, and wait for periods; - 3:
if ( then - 4:
resume backoff at the next ; - 5:
else - 6:
perform channel sensing as described in Algorithm 1; - 7:
if channel access success then - 8:
go to Step 14; - 9:
else - 10:
wait for next ; - 11:
end if - 12:
end if - 13:
else - 14:
start transmission - 15:
if transmission success then - 16:
stop; - 17:
else - 18:
if available then - 19:
start retransmission at the allotted ; - 20:
else - 21:
wait for next ; - 22:
end if - 23:
end if - 24:
end if
|
4.4. Prediction Model for the Optimal Number of LLDN Retransmission Slots
The LLDN superframe of the current IEEE 802.15.4e provides retransmission opportunities to the failed nodes. However, to use these retransmission opportunities, the number of failed nodes should be less than or equal to the number of available retransmission slots in the superframe. The random allocation of the slots for retransmission by the PAN coordinator depends on the number of nodes attached to the coordinator. Due to this random allocation, it is possible that the allocated retransmission slots may be less than the number of failed nodes. If so, there is no provision in the current standard for retransmissions, and those nodes that cannot get retransmission slots in the same superframe have to reject data transmissions. Once the superframe has started, the number of retransmission slots cannot be changed. It is necessary to choose prior the number of optimal retransmission slots as correctly as possible so that we can increase the reliability. In this section, based on the number of past failed data transmissions and the allocated number of retransmission slots, we would like to find the optimal number of retransmission slots by using regression analysis. It is noted that sensors/nodes are limited in processing capacity and memory and for which we want to develop one statistical model that is used to forecast the optimal values of retransmission slots.
Let
and
be the average
and average waiting packets during the
j-th LLDN superframe, respectively. The
value of the current superframe can be estimated by taking the mean of the lowest and highest value of the
that was received in the previous superframe. Let
be the number of required retransmission slots during the
j-th LLDN superframe. Considering the value
from the past
n number of LLDN superframes for the prediction. We can design the regression model as:
where
represents the predicted value of
X for the
j-th observation,
for
and the error term
is added to reduce the number of packet rejections. It is to be noted that we want to minimize the error, which is the difference between the original and predicted value. In other words, we need to minimize the sum of the squared differences, i.e.,
, where
is the predicted value of
X for the
j-th observation. Thus,
needs to be minimized with three unknowns
for
. Again, using the partial derivatives with respect to
and equating to zero for each
i, the following equation is obtained.
Solving Equation (
4), all three can be obtained. It is to be noted that the network coordinator can get the estimated number of retransmission slots required in the next superframe by using the value of
in (
3). Then, the coordinator modifies the superframe structure with the newly estimated retransmission slots and broadcasts the information through beacon in the next superframe. This proposed estimation can help the coordinator to allocate the optimal number of retransmission slots, which ultimately reduces the retransmission delay and increases the network reliability.
5. Analytical Model for Shared Slots in the LLDN Superframe
In this section, we design one Markov model to analyze the network performance on the shared slots. We consider that the network traffic is unsaturated. Based on such unsaturated traffic and the notations given in
Table 1, the analytical model can be designed as follows.
Recall that
is the number of nodes associated with a shared slot, and each node has data arrival rate
. As shown in
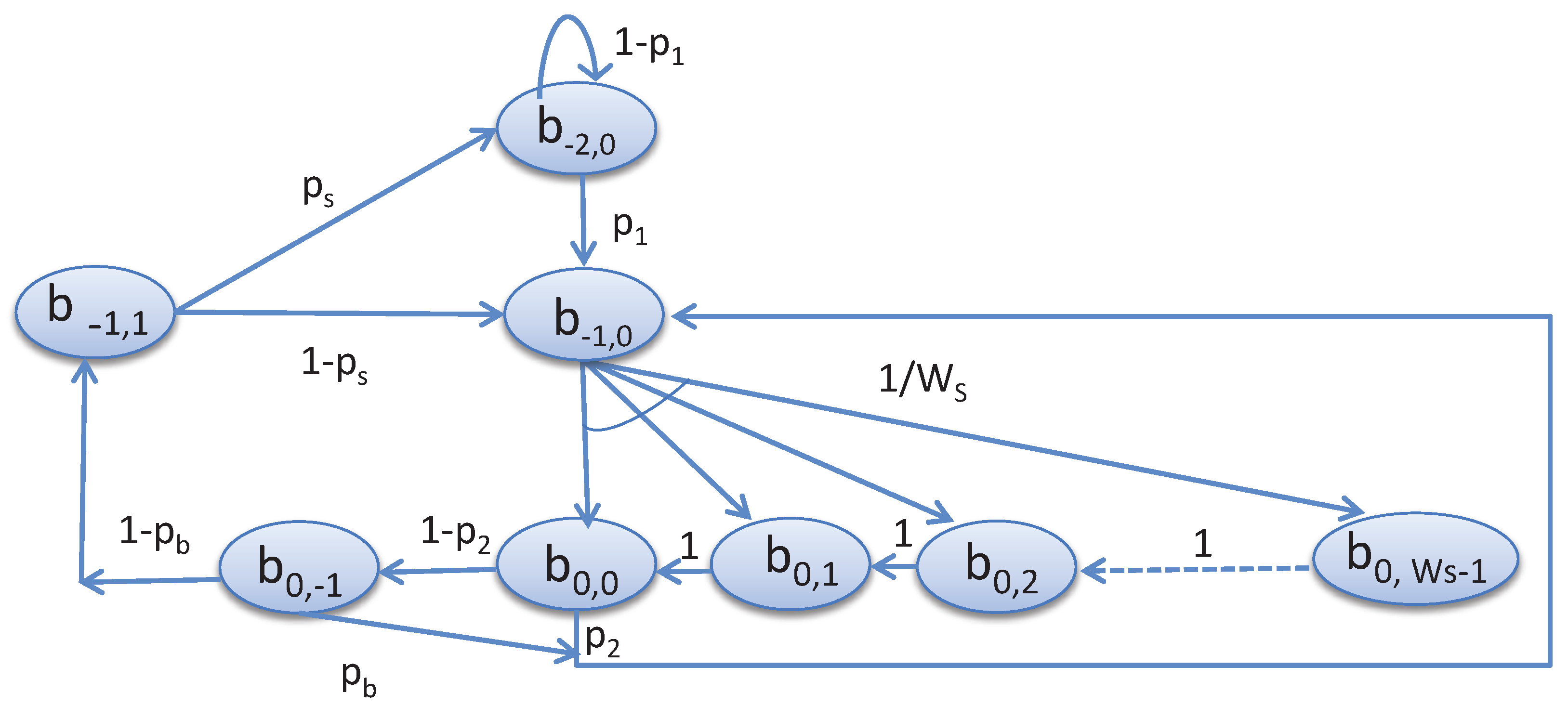
Figure 3, the stochastic processes
and
represent the backoff states for a given node, which is fixed to zero, and the backoff counter for the contention window for the shared slot, i.e.,
, respectively. Let,
, where
. The time
t corresponds to the system time.
,
and
represent the states corresponding to the start of the channel access, transmission and idle state, respectively. Let us consider
as the probability that a node generates one packet for transmission. The node first goes to the
state, chooses a random backoff
state, for
. Let,
be the probability of accessing the channel busy during the CCA and
be the probability that the remaining time in the shared slot is sufficient to complete the data transmission. Once the channel is found idle, the node goes to the transmission state. We have considered
as the probability of successful transmission. Based on the proposed Markov chain model given in
Figure 3, the transition probabilities for deducing the steady state probabilities can be derived as follows.
Equation (
5) represents the decrement of the backoff counter, which occurs with a probability of one. Equation (
6) represents the probability of finding the channel busy during the CCA, and thereafter, a node selects a state in the next backoff state. Based on these transition probabilities, we can derive the steady state probabilities as follows. A node normally goes for the CCA after the random backoff period whenever the remaining time in the shared slot is enough to transmit the data. The corresponding steady state probability can be deduced as follows.
If the remaining time in the shared slot is sufficient for the data transmission, the node goes for the CCA, and upon finding the channel idle, it starts the data transmission. The corresponding state probability is:
When a transmission failure occurs without exceeding the retransmission limits, the tagged node enters into the active state. The corresponding steady state probability can be deduced as follows.
The node enters into the idle state after successful data transmission or no packet to transmit. The corresponding steady state probability is:
By the theory of total probability of the Markov model, we have the equation:
Let
be the probability that a node attempts to do carrier sensing. Then, this probability can be as follows.
Normally, there are two cases if the channel is found busy by the node. The channel may be busy when another node present within its sensing range is transmitting or any other node also accessing the channel in the same slot and is transmitting the known signal. During one beacon interval, the probability of a node having data arrival is
. Therefore, the expected number of nodes
with data arrival associated with a shared slot will be:
Hence, the value of the probability of the channel being busy
due to simultaneous CCAs and the probability of the channel being busy
due to data transmission by any other node can be calculated as follows.
Hence, the probability of a busy channel during CCA for the node is:
7. Simulation Results
In this section, we describe our simulation results and validate the models using the OMNeT++ [
34] simulator. We conduct the simulation to compare the performance of our protocol with IEEE 802.15.4e. We have analyzed the performance of our proposed protocol under the assumption that nodes are active in their allotted slots and go for power saving mode in the rest of the beacon interval. In our simulation environment, the star topology is considered, and the nodes are deployed randomly, keeping the coordinator in the center of the circle. We set the simulation parameters according to the IEEE 802.15.4e standard, which are given in
Table 2.
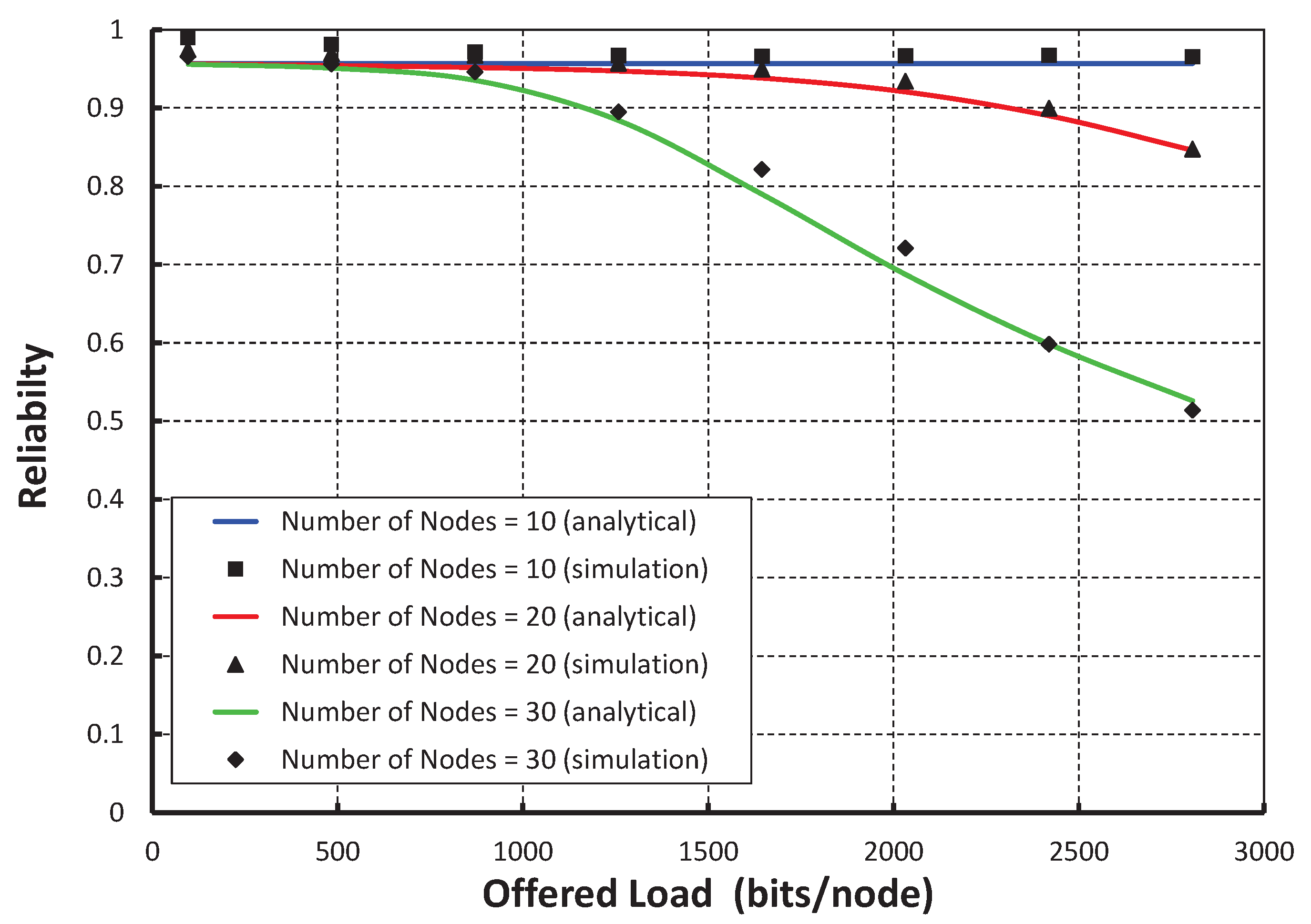
In
Figure 4, let the
X axis be the different offered loads for each node and the
Y axis be the corresponding packet success probabilities. It is observed that the packet success probabilities decrease with respect to the loads per node increase irrespective of the number of nodes in the network attached to a shared slot. When 10 nodes per shared slot are considered and the offered load is of 500 bits, we find that the success probability is 0.77. However, we got the success probabilities for 20 and 30 nodes per shared slots as 0.71 and 0.68, respectively. It is also seen from
Figure 4 that the simulation result matches with the analytical one. From
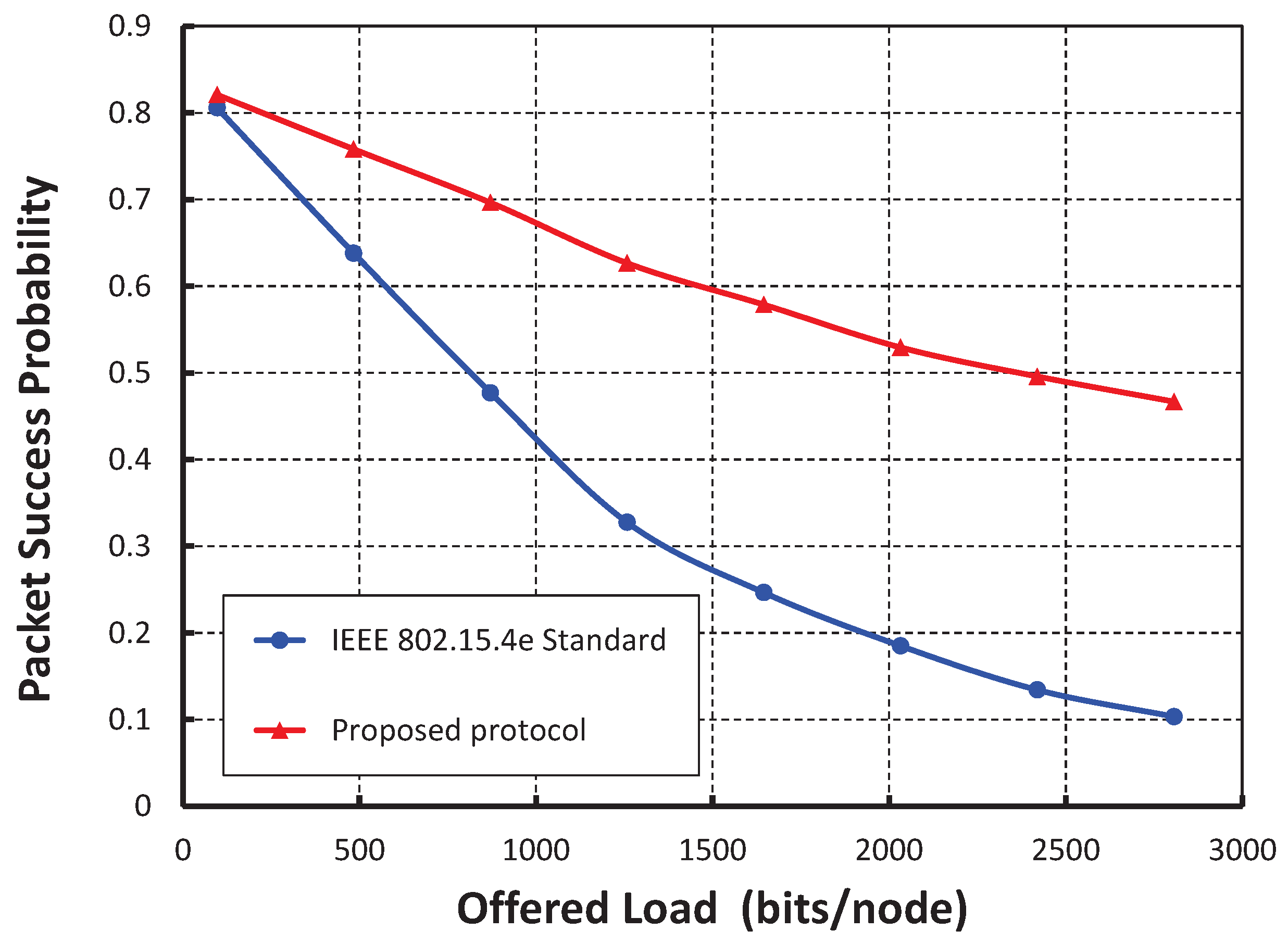
Figure 5, it is observed that the packet success probabilities decrease with respect to the number of nodes attached to the shared slot with or without hidden terminal problem under the offered load 200 bits/node. The comparison of our proposed protocol with IEEE 802.15.4e for the packet success probability under ideal channel condition with 20 nodes per shared slots is shown in
Figure 6. It is observed that the packet success probabilities decrease, if the offered loads to a shared slot increase. According to the IEEE 802.15.4e standard, the initial contention window for the stations is
. Hence, the expected number of nodes choosing the same slot will be
. Accordingly, the chance of transmission by two stations at the same time is higher. Fortunately, in our proposed protocol, the contention window is based on the active number of nodes per shared slot such that the expected number of nodes choosing the same slot is always less than or equal to one. Hence, the packet success probability of our MAC protocol outperforms, as noticed in
Figure 6. Even if, two nodes choose the same random backoff value and access the channel in the same slot, our carrier sensing mechanism lets the nodes go to the backoff state. For example, as shown in
Figure 2b,
A and
B find the channel busy due to simultaneous CCAs and stop the packet transmissions, and
C can transmit its packet successfully. As a result, the packet success probability is enhanced.
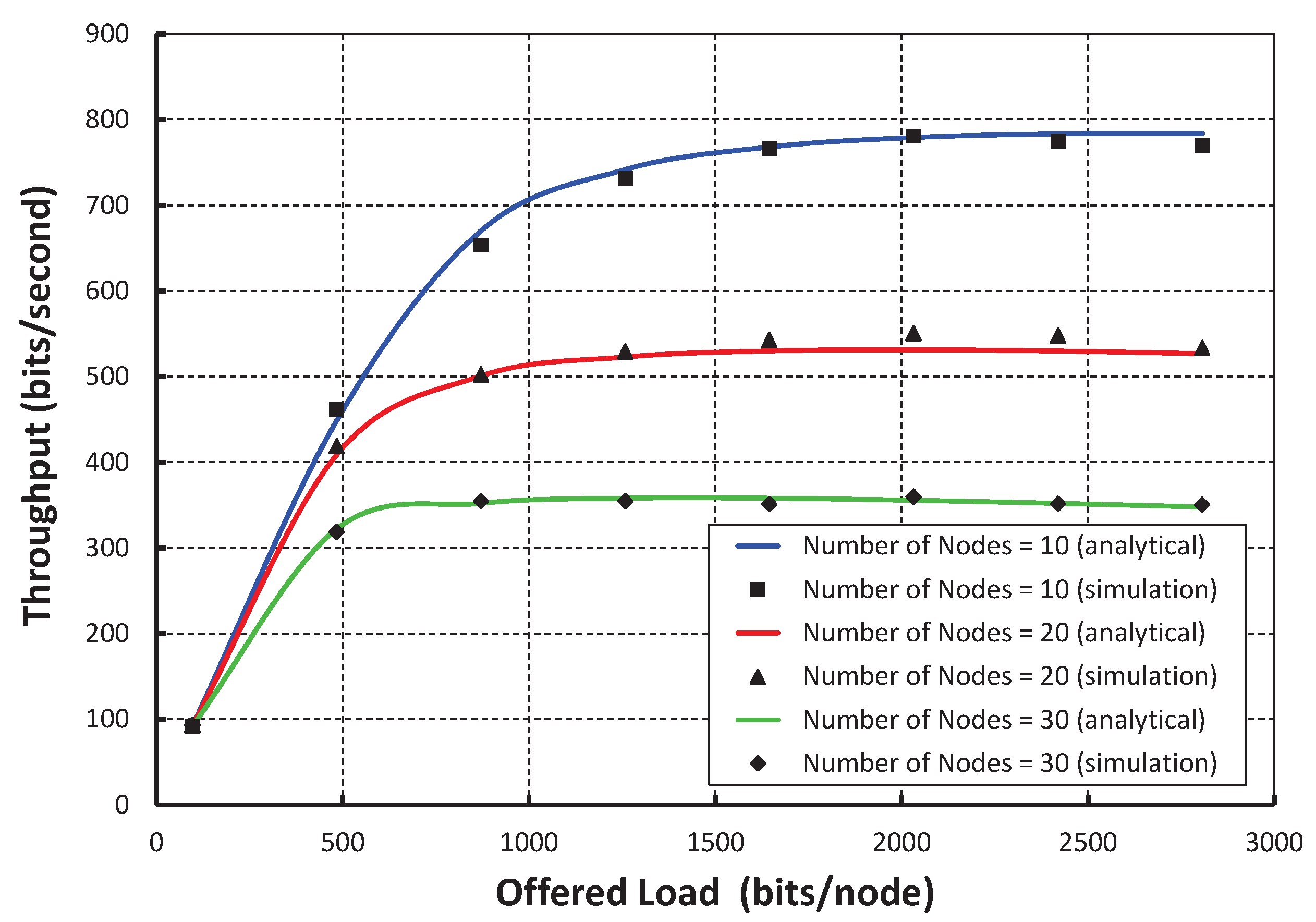
In
Figure 7, we consider the offered loads along the
X axis and the corresponding throughput along the
Y axis. The data payload size is a maximum of 127 bytes including the physical and MAC layer overhead and address. We consider the physical, MAC layer and address to be 6 bytes, 3 bytes, and 8 bits, respectively. The throughput initially increases with respect to the offered load. However, it remains constant after certain offered loads. The significant changes in the graph are due to the presence of different numbers of nodes per shared slot. We observe that the maximum throughput is achieved as 780 bits per second, when only 10 nodes per shared slots are considered and the payload is 100 bytes. However, the throughput remains constant after the offered load is 800 bytes irrespective of the number of nodes. The close agreement between the simulation and analytical results shows the accuracy of the proposed analytical model though there is little difference due to the assumptions. From
Figure 8, it is shown that throughput decreases with respect to the number of nodes attached to the shared slot with or without the hidden terminal problem considering the offered load as 200 bits/node. As shown in
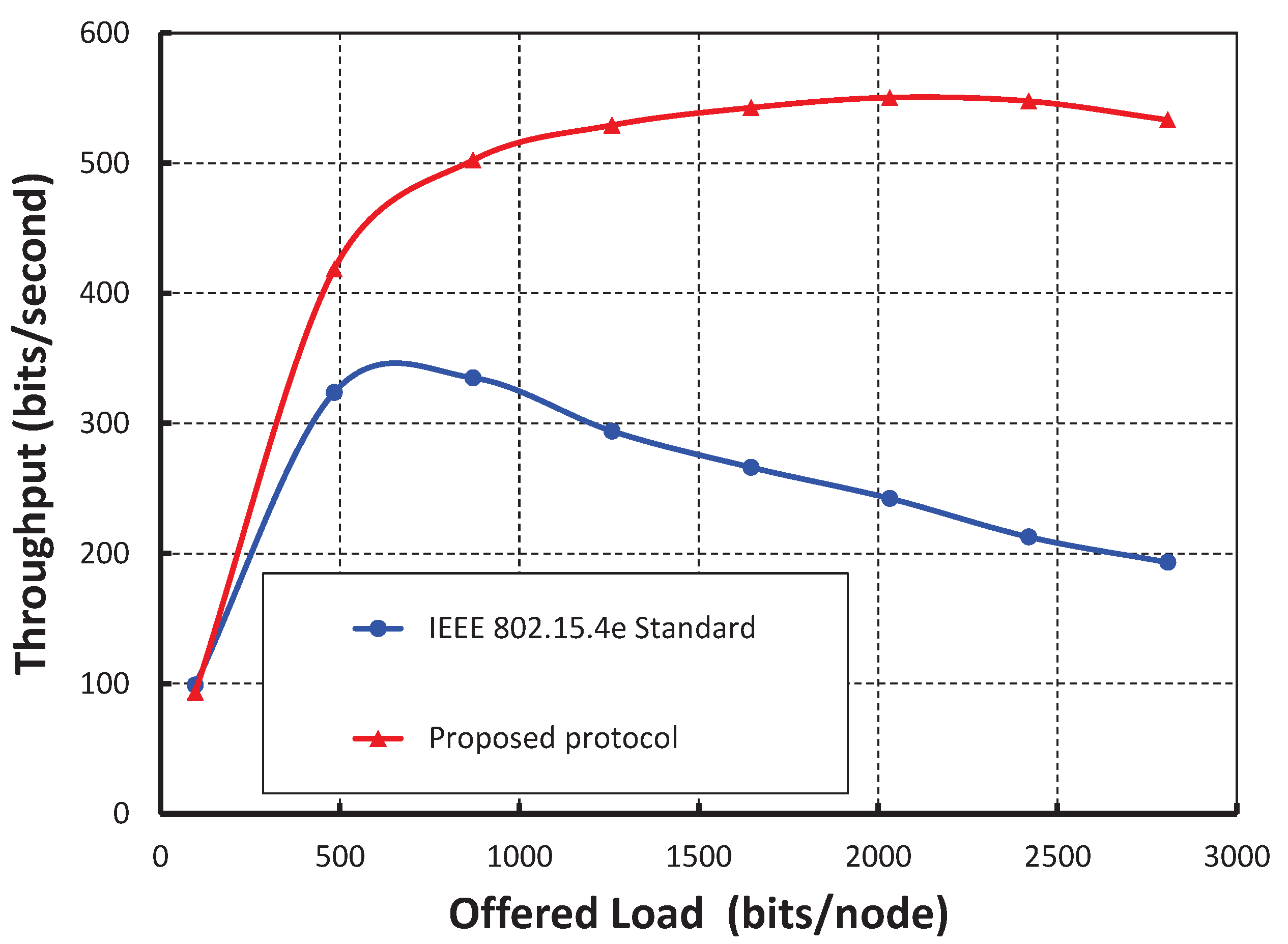
Figure 9, we compare the IEEE 802.15.4e protocol with ours. It is observed that the throughput of our protocol is significantly higher than the standard when we consider only 20 nodes per shared slot. This happens since our carrier sensing mechanism sends the nodes to backoff when they access the channel in the same time slot. Hence, any other node can access the channel successfully.
As shown in
Figure 10, we take the offered loads along the
X axis and get the average energy consumption along the
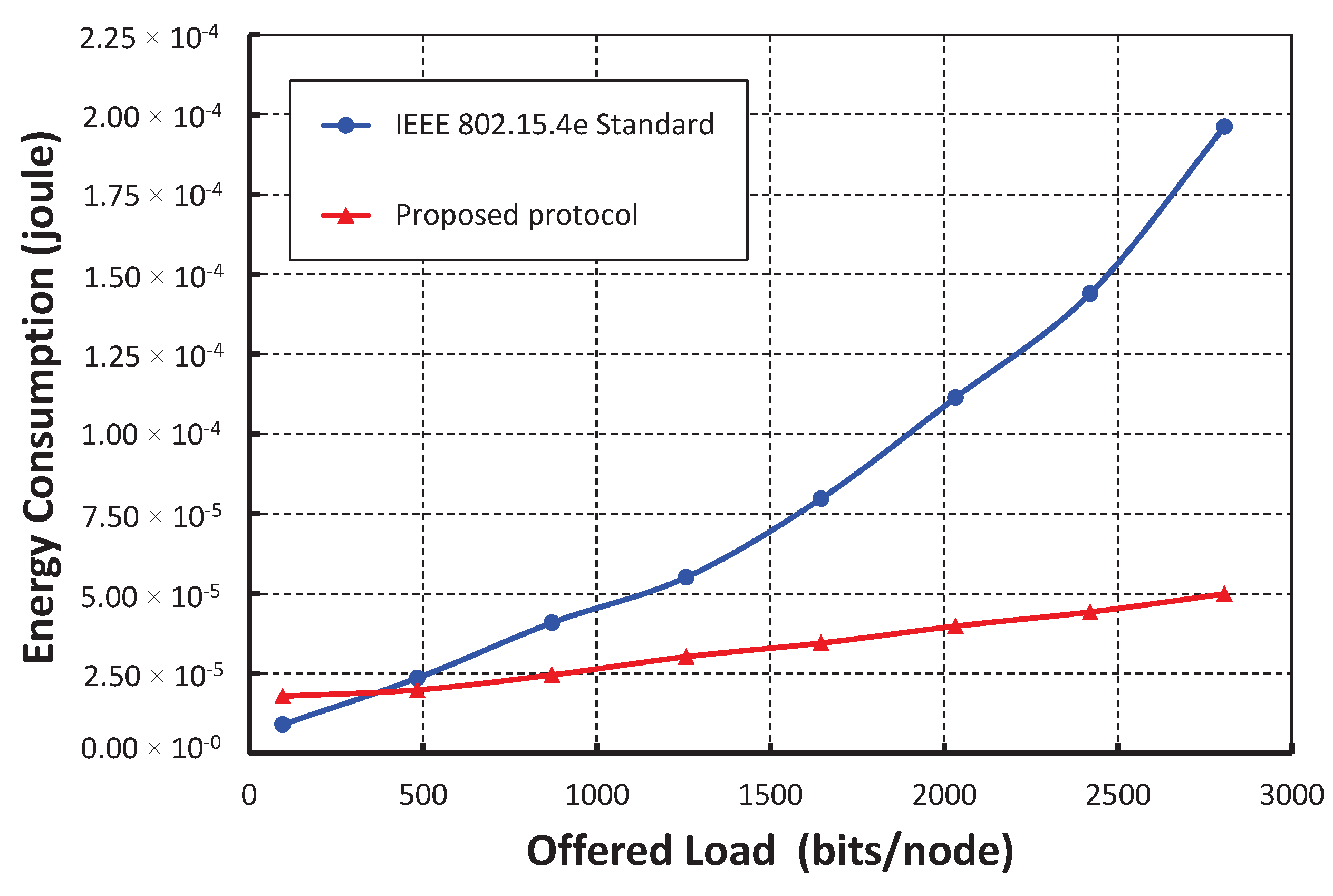
Y axis. The energy consumptions for data transmissions in a shared slot increase with respect to the loads per node increase, which is due to the active number of nodes presented in a shared slot. As shown in
Figure 11, we compare our proposed protocol with the IEEE 802.15.4e standard. It is observed that the energy consumption in our protocol is significantly less than the standard when only 20 nodes per shared slot are considered. This result happens as our carrier sensing mechanism sends one additional known signal that lets the nodes accessing the channel in the same slot to go for backoff. For example, as shown in
Figure 2b,
A and
B find the channel busy as they perform simultaneous CCAs and stop the packet transmissions. Hence, both nodes
A and
B can save energy in our protocol.
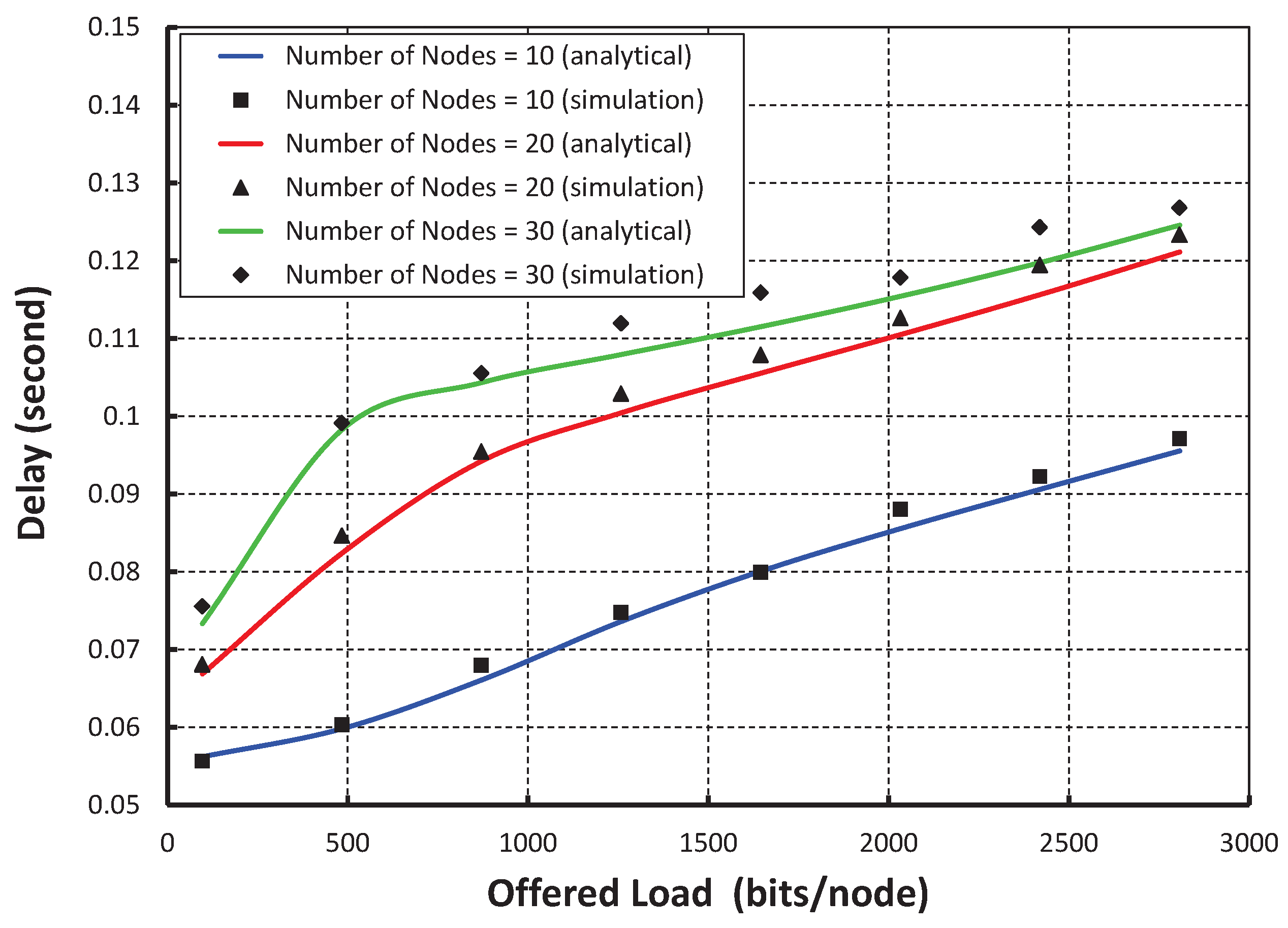
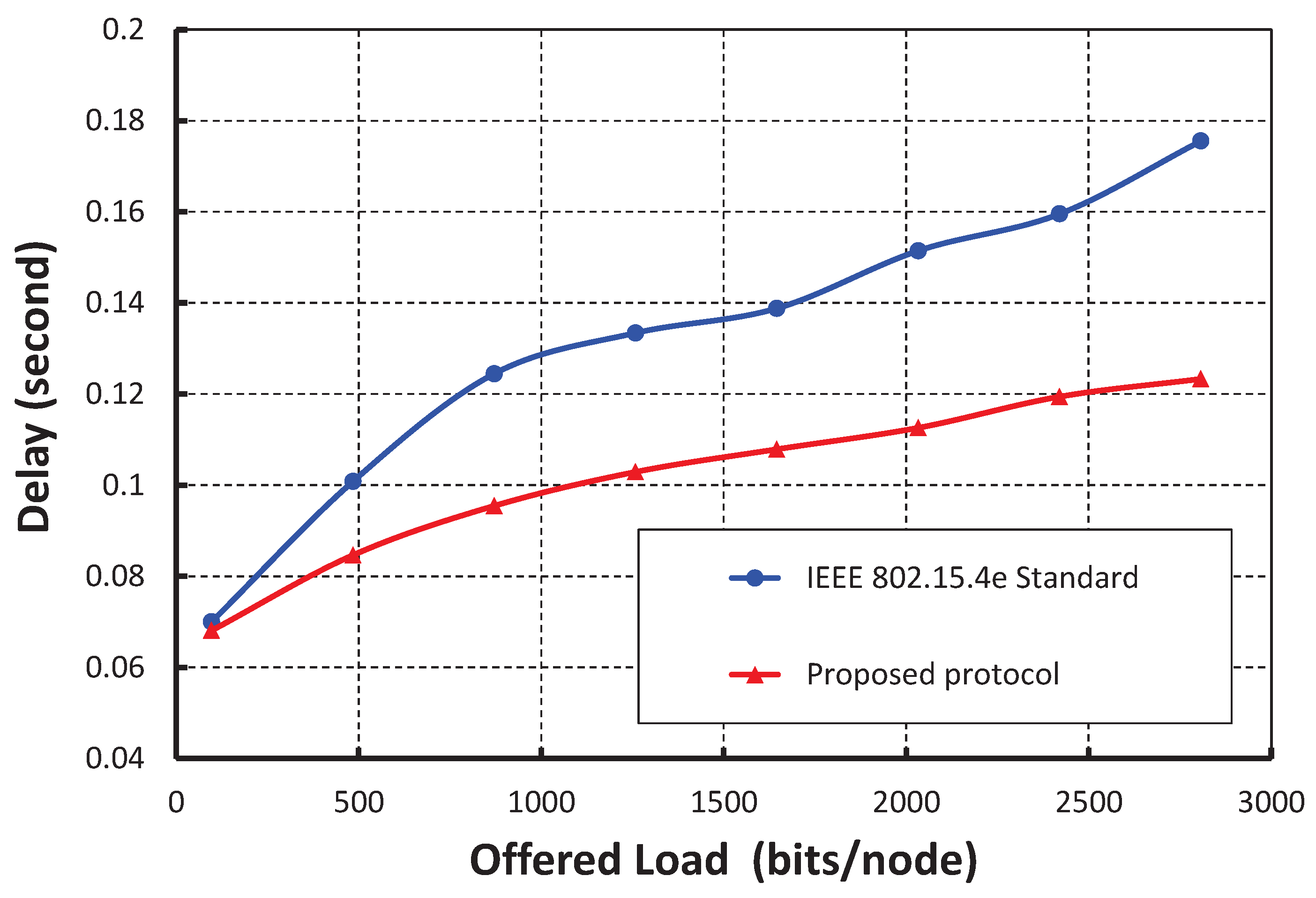
Figure 12 shows the result of transmission delay for a data payload of 100 bytes. It is observed that the transmission delay increases with the increase in the offered loads irrespective of the number of nodes accessing in a shared slot. As shown in
Figure 13, the transmission delay in our protocol is compared with the IEEE 802.15.4e standard under the ideal channel condition. It is observed that the transmission delay of our protocol is significantly less as compared to the IEEE 802.15.4e standard.
In
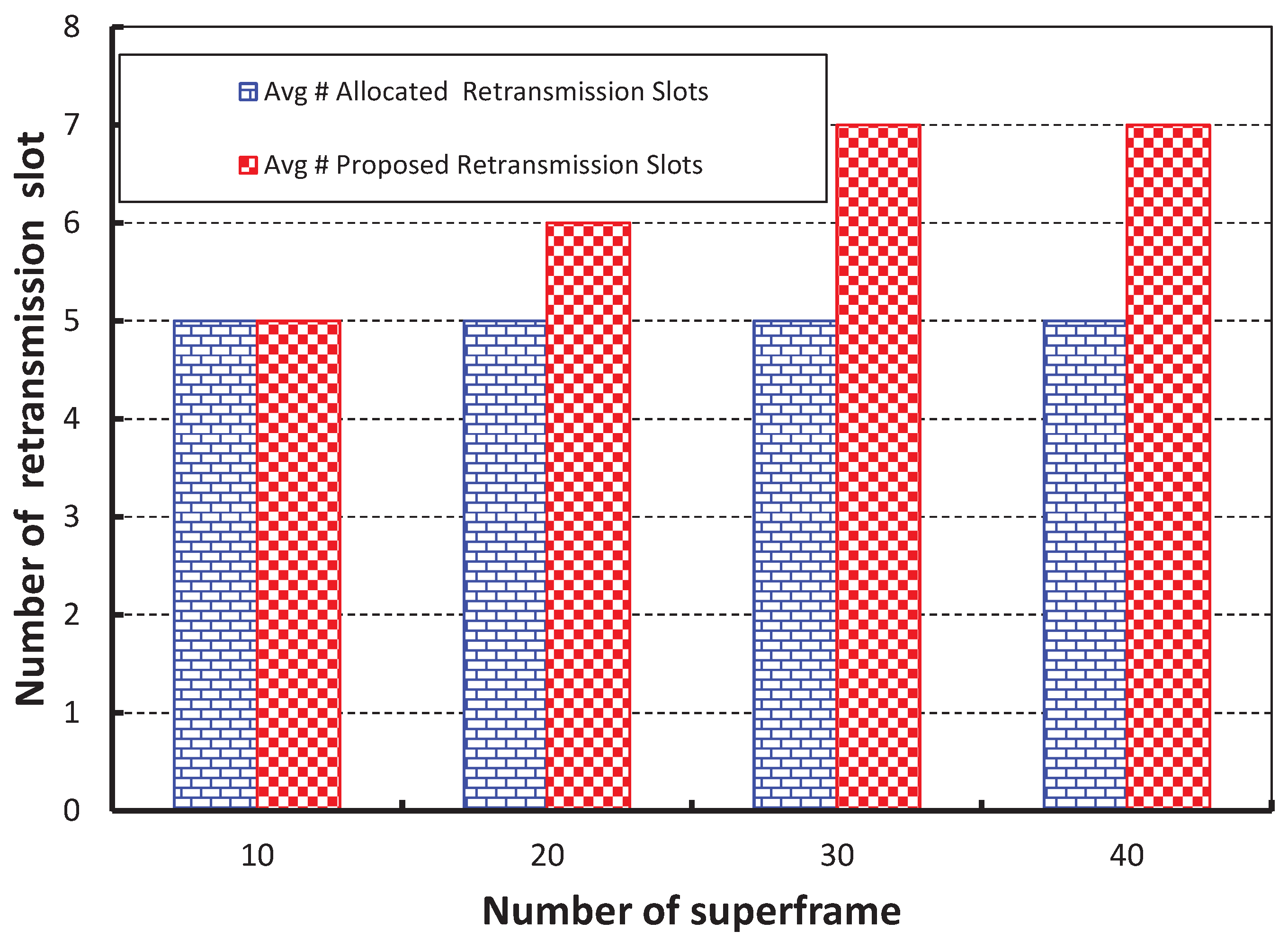
Figure 14, we take the number of superframes along the
X axis and get the expected number of retransmission slots along the
Y axis. It is observed that the required average number of retransmission slots is nearly equal to our predicted value when 10 superframes and 20 nodes per shared slot are considered. However, the predicted number of retransmission slots is higher than the average number of retransmission slots when more superframes are considered.
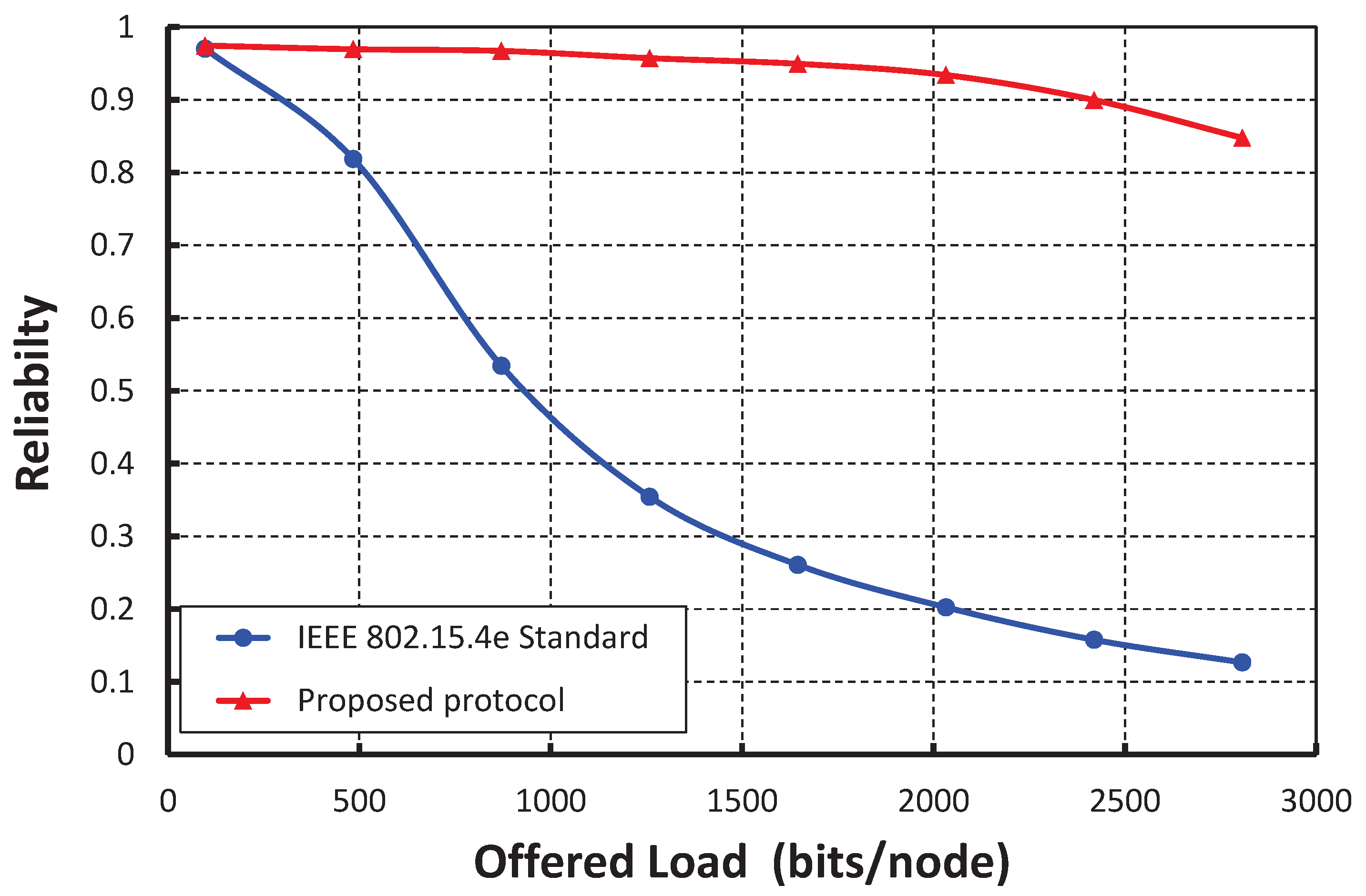
Figure 15 shows the result of reliability for different offered loads. We find that the radiabilities decrease with respect to the offered loads and irrespective of the number of nodes accessing in a shared slot. In
Figure 16, we compare the reliability of the IEEE 802.15.4e standard with ours under the ideal channel condition. It is observed that the reliability of our protocol is significantly higher than the IEEE 802.15.4e standard.
Table 3 shows the summarization of the statistical results for transmission success probability, throughput, delay, energy consumption and reliability.