Social Milieu Oriented Routing: A New Dimension to Enhance Network Security in WSNs
Abstract
:1. Introduction
- For the first time, we map the aforementioned OSTP selection problem in large scale WSNs onto a transverse Ising spin glass (TISG) model. Then, we utilize configuration path-integral Monte Carlo (CPIMC) technology [13] with the aid of quantum-classical mapping and Jarzynski equality to perform the practical implementation of quantum annealing (QA) and solve the time-dependent Schrödinger equation in a very large and exponentially growing Hilbert space.
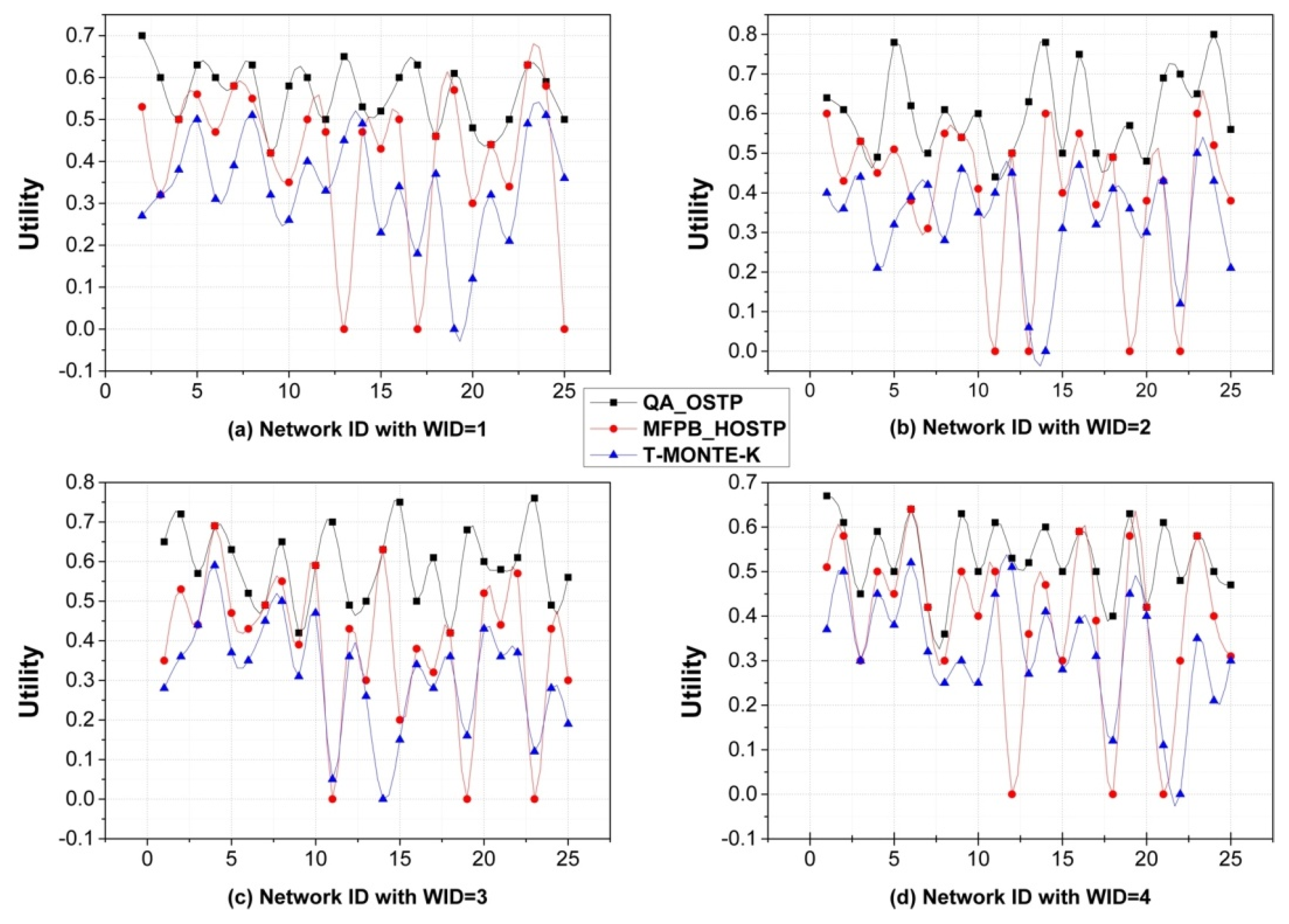
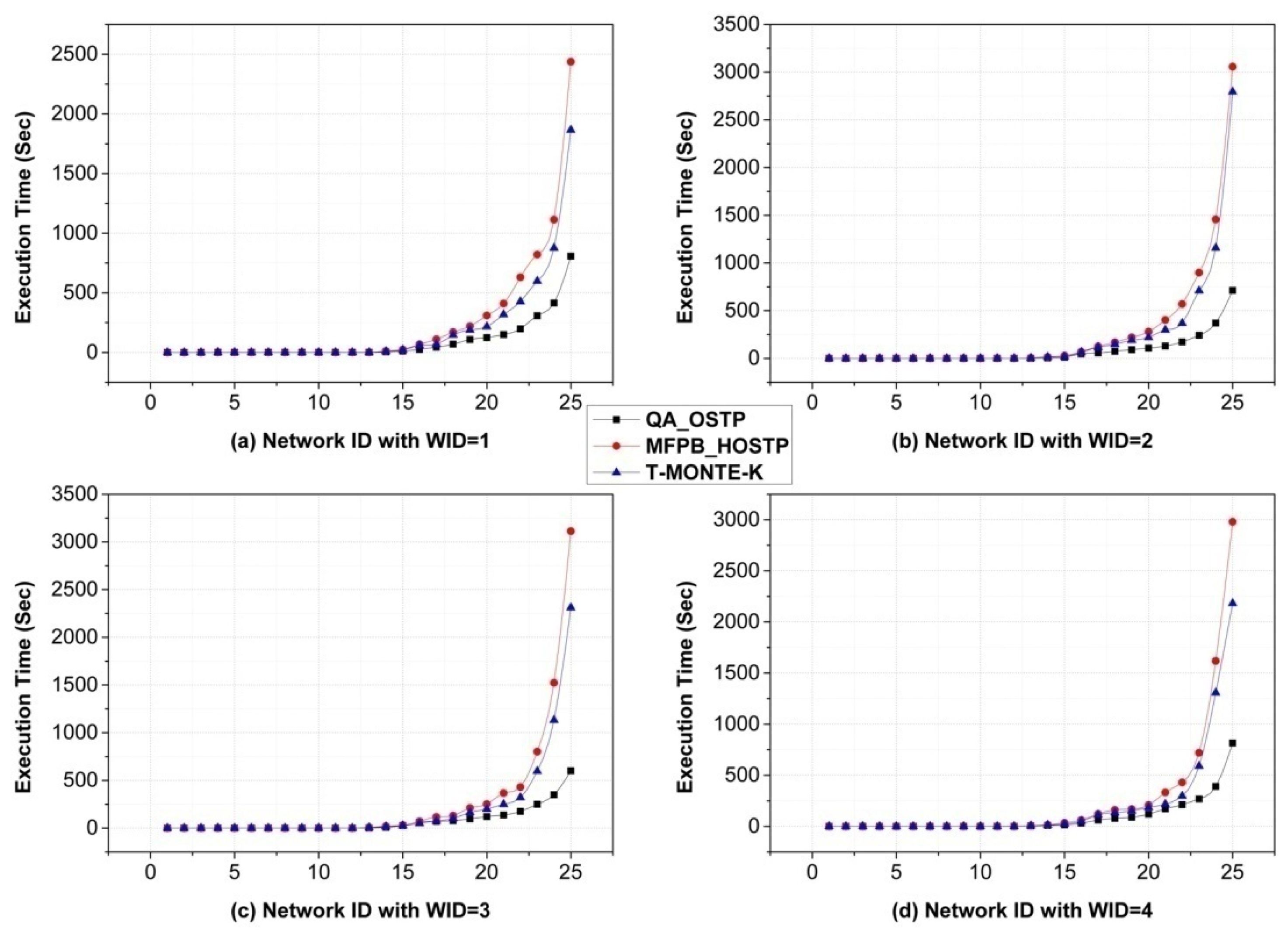
- We carry out the performance evaluation of the newly constructed QA_OSTP and compare it with the referenced method based on extensive experiments. The experimental results demonstrate the effectiveness of QA_OSTP and prove that QA_OSTP has better performance in terms of the utility of the selected social trust path and execution time than its counterpart does.
2. Related Work
3. Algorithm Description
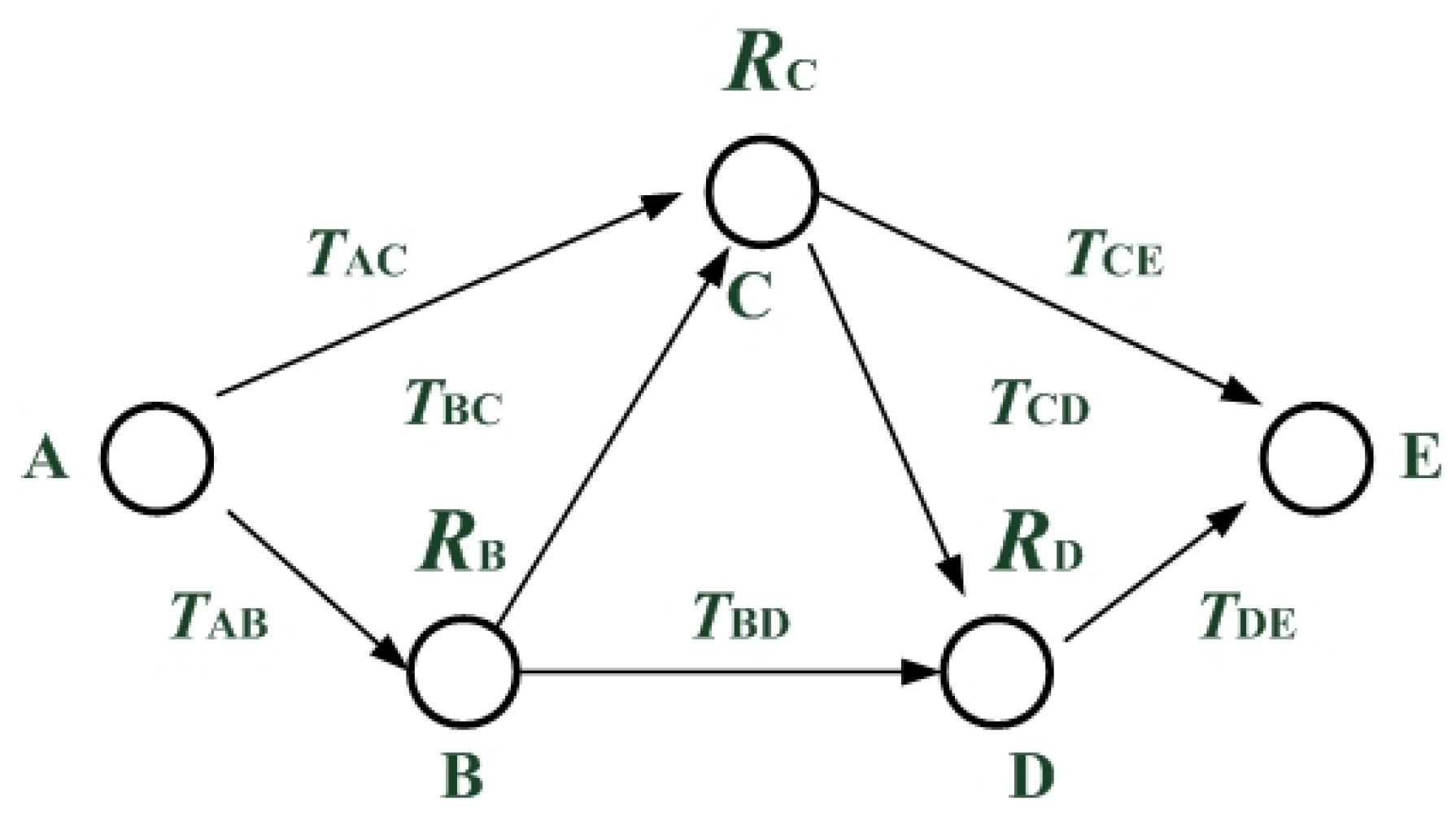
3.1. QoT Parameters Aggregation Rules and Related Definitions
3.2. Quantum Annealing (QA)
3.3. Problem Representation
- (i)
- Definition of Quantum Hamiltonian
- (ii)
- Hamiltonian Approximation Based on Suzuki-Trotter Transformation
3.4. Proposed QA_OSTP
| Algorithm 1. Pseudo-code of QA_OSTP for WSNs. |
| Data: G, N,Ss, Ds, P, T0, Γ0,,, Maxsteps Result: ostp(Ss,…,Ds), 1 begin 2 Set ,, 3 while do 4 Randomly disturb the order of replicas 5 for ,…,P, do 6 select the replica in position φ 7 for ,… do 8 Use “plus-minus” method to get and hence 9 10 if then 11 12 else 13 with probability 14 end for 15 end for 16 17 end |
4. Experimental Results
4.1. Experiment Setting
4.2. Performance Analysis
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: A survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Bangash, J.I.; Abdullah, A.H.; Anisi, M.H.; Khan, A.W. A survey of routing protocols in wireless body sensor networks. Sensors 2014, 14, 1322–1357. [Google Scholar] [CrossRef] [PubMed]
- Javaid, N.; Ilyas, N.; Ahmad, A.; Alrajeh, N.; Qasim, U.; Khan, Z.A.; Liaqat, T.; Khan, M.I. An Efficient Data-Gathering Routing Protocol for Underwater Wireless Sensor Networks. Sensors 2015, 15, 29149–29181. [Google Scholar] [CrossRef] [PubMed]
- Li, C.; Zhang, H.; Hao, B.; Li, J. A survey on routing protocols for large-scale wireless sensor networks. Sensors 2011, 11, 3498–3526. [Google Scholar] [CrossRef] [PubMed]
- Bhattacharyya, D.; Kim, T.-H.; Pal, S. A comparative study of wireless sensor networks and their routing protocols. Sensors 2010, 10, 10506–10523. [Google Scholar] [CrossRef] [PubMed]
- Liu, X. A survey on clustering routing protocols in wireless sensor networks. Sensors 2012, 12, 11113–11153. [Google Scholar] [CrossRef] [PubMed]
- Radi, M.; Dezfouli, B.; Bakar, K.A.; Lee, M. Multipath routing in wireless sensor networks: Survey and research challenges. Sensors 2012, 12, 650–685. [Google Scholar] [CrossRef] [PubMed]
- Liu, M.; Cao, J.; Chen, G.; Wang, X. An energy-aware routing protocol in wireless sensor networks. Sensors 2009, 9, 445–462. [Google Scholar] [CrossRef] [PubMed]
- García-Villalba, L.J.; Sandoval Orozco, A.L.; Triviño-Cabrera, A.; Barenco Abbas, C.J. Routing protocols in wireless sensor networks. Sensors 2009, 9, 8399–8421. [Google Scholar] [CrossRef] [PubMed]
- Shaikh, R.A.; Jameel, H.; d’Auriol, B.J.; Heejo, L.; Sungyoung, L.; Young-Jae, S. Group-Based Trust Management Scheme for Clustered Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2009, 20, 1698–1712. [Google Scholar] [CrossRef]
- Liu, G.; Wang, Y.; Orgun, M.; Lim, E. Finding the Optimal Social Trust Path for the Selection of Trustworthy Service Providers in Complex Social Networks. IEEE Trans. Serv. Comput. 2011, 6, 1–15. [Google Scholar]
- Kozen, D.C. The Design and Analysis of Algorithms; Springer: Berlin, Germany, 2012. [Google Scholar]
- Schoof, T.; Bonitz, M.; Filinov, A.; Hochstuhl, D.; Dufty, J. Configuration path integral Monte Carlo. Contrib. Plasma Phys. 2011, 51, 687–697. [Google Scholar] [CrossRef]
- Korkmaz, T.; Krunz, M. Multi-constrained optimal path selection. In Proceedings of the INFOCOM 2001 Twentieth Annual Joint Conference of the IEEE Computer and Communications Societies, Anchorage, AK, USA, 22–26 April 2001.
- Yu, T.; Zhang, Y.; Lin, K.-J. Efficient algorithms for Web services selection with end-to-end QoS constraints. ACM Trans. Web 2007, 1, 98–111. [Google Scholar] [CrossRef]
- Alhadad, N.; Serrano-Alvarado, P.; Busnel, Y.; Lamarre, P. System Modeling and Trust Evaluation of Distributed Systems. Trans. Large-Scale Data Knowl. Cent. Syst. 2015, 9430, 33–74. [Google Scholar]
- Li, M.; Xiang, Y.; Zhang, B.; Huang, Z.; Zhang, J. A trust evaluation scheme for complex links in a social network: Alink strength perspective. Appl. Intell. 2016. [Google Scholar] [CrossRef]
- Liu, G.; Zhao, L.; Zheng, K.; Liu, A.; Xu, J.; Li, Z. An Efficient Method to Find the Optimal Social Trust Path in Contextual Social Graphs. In Database Systems for Advanced Applications; Springer International Publishing: Cham, Switzerland, 2015. [Google Scholar]
- Burt, R.S. Network-Related Personality and the Agency Question: Multirole Evidence from a VirtualWorld1. Am. J. Sociol. 2012, 118, 543–591. [Google Scholar] [CrossRef]
- Pham, D.; Karaboga, D. Intelligent Optimisation Techniques: Genetic Algorithms, Tabu Search, Simulated Annealing and Neural Networks; Springer: New York, NY, USA, 2000. [Google Scholar]
- Ioannidis, Y.E. Review—Optimization by Simmulated Annealing. Available online: http://dblp.uni-trier.de/db/journals/dr/Ioannidis99 (accessed on 1 January 2016).
- Das, A.; Chakrabarti, B.K. Colloquium: Quantum annealing and analog quantum computation. Rev. Mod. Phys. 2008, 80, 1061. [Google Scholar] [CrossRef]
- Rønnow, H.; Parthasarathy, R.; Jensen, J.; Aeppli, G.; Rosenbaum, T.; McMorrow, D. Quantum phase transition of a magnet in a spin bath. Science 2005, 308, 389–392. [Google Scholar] [CrossRef] [PubMed]
- Boixo, S. Experimental signatures of quantum annealing. Bull. Am. Phys. Soc. 2013, 58, 21–28. [Google Scholar]
- Battaglia, D.A.; Santoro, G.E.; Tosatti, E. Optimization by quantum annealing: Lessons from hard satisfiability problems. Phys. Rev. E 2005, 71, 066707. [Google Scholar] [CrossRef] [PubMed]
- Santoro, G.E.; Martoňák, R.; Tosatti, E.; Car, R. Theory of quantum annealing of an Ising spin glass. Science 2002, 295, 2427–2430. [Google Scholar] [CrossRef] [PubMed]
- Khribi, M.K.; Jemni, M.; Nasraoui, O. Automatic Recommendations for E-Learning Personalization Based on Web Usage Mining Techniques and Information Retrieval. In Proceedings of the Eighth IEEE International Conference on Advanced Learning Technologies (ICALT’08), Santander, Spain, 1–5 July 2008; pp. 241–245.
- Suzuki, S.; Inoue, J.-I.; Chakrabarti, B.K. Quantum Ising Phases and Transitions in Transverse Ising Models; Springer: Berlin, Germany, 2013. [Google Scholar]
- Liu, L.; Feng, G. Simulated annealing based multi-constrained qos routing in mobile ad hoc networks. Wirel. Pers. Commun. 2007, 41, 393–405. [Google Scholar] [CrossRef]
- Paiva, T.; Khatami, E.; Yang, S.; Rousseau, V.; Jarrell, M.; Moreno, J.; Hulet, R.G.; Scalettar, R.T. Cooling Atomic Gases with Disorder. Phys. Rev. Lett. 2015, 115, 240402. [Google Scholar] [CrossRef] [PubMed]
- Mukherjee, S.; Chakrabarti, B.K. Multivariable optimization: Quantum annealing and computation. Eur. Phys. J. Special Top. 2015, 224, 17–24. [Google Scholar] [CrossRef]
- Aarts, E.; Lenstra, J.K. Local Search in Combinatorial Optimization; Princeton University Press: Princeton, NJ, USA, 2003. [Google Scholar]
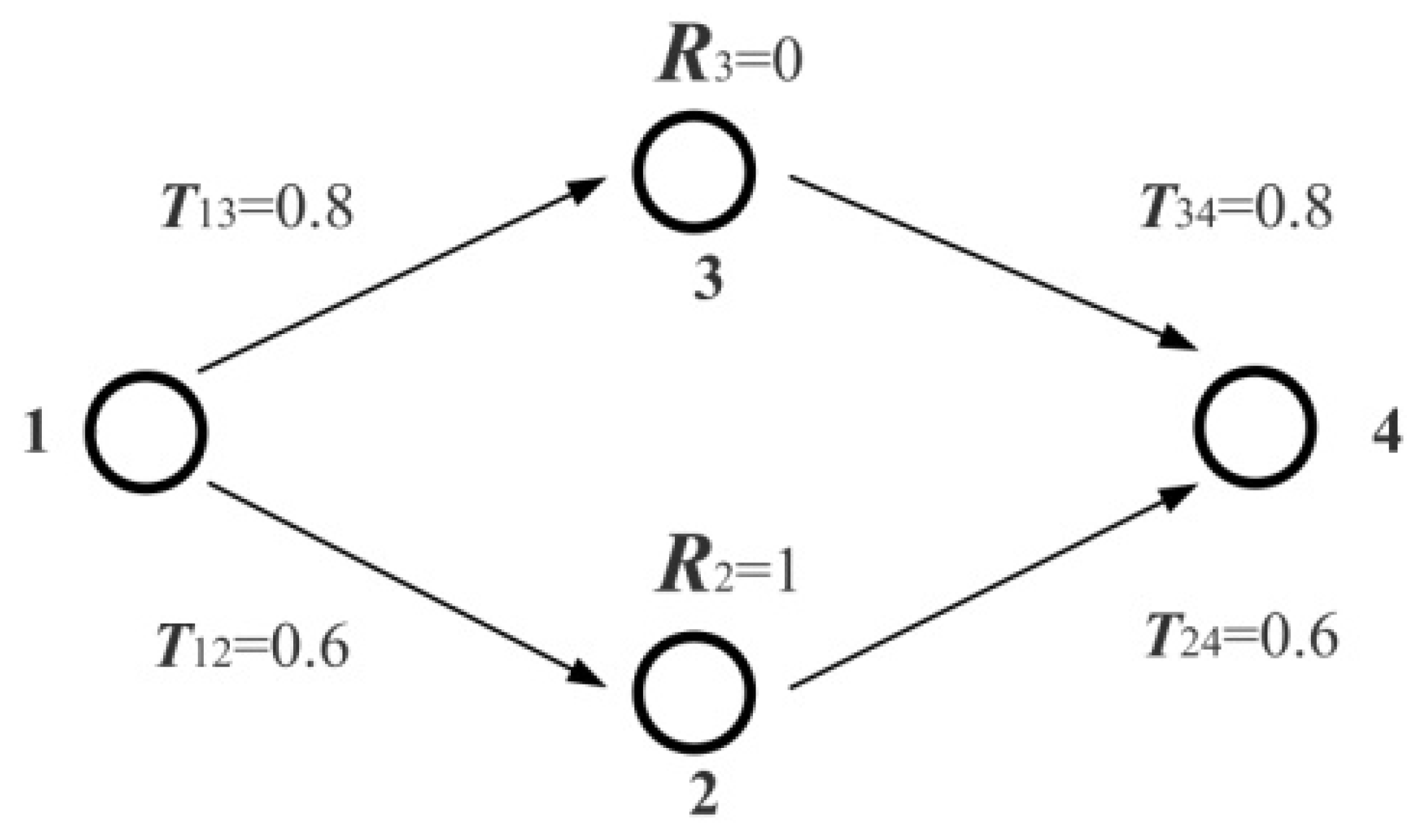
| Social Trust Path | State Vector | Utility | |
|---|---|---|---|
| 1—2—4 | 0.616 | ||
| 1—3—4 | 0.384 | ||
| Invalid path | Invalid | ||
| Invalid path | Invalid |
| G | Social graph of WSNs with two QoT parameters |
| Ss | Trustor node |
| Ds | Target trustee node |
| Utility of a social trust path configuration | |
| P | The number of replicas |
| T | Temperature parameter |
| T0 | Optimal initial temperature |
| Γ | Transverse field |
| Γ0 | An initial value of the transverse field |
| M | Fixed number of nearest neighbors of participant |
| Sequence number of a certain replica | |
| N | Number of nodes in WSNs |
| φ | The series number of replica |
| Total CPIMC time | |
| Maxsteps | Maximum number of CPIMC steps |
| Ni | Number of iterations |
| A social trust path configuration | |
| A series of , also known as | |
| Neighbor of configuration | |
| Trust constraint of social trust path | |
| Recommendation degree constraint of social trust path |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, L.; Chen, L.; Jia, H. Social Milieu Oriented Routing: A New Dimension to Enhance Network Security in WSNs. Sensors 2016, 16, 247. https://doi.org/10.3390/s16020247
Liu L, Chen L, Jia H. Social Milieu Oriented Routing: A New Dimension to Enhance Network Security in WSNs. Sensors. 2016; 16(2):247. https://doi.org/10.3390/s16020247
Chicago/Turabian StyleLiu, Lianggui, Li Chen, and Huiling Jia. 2016. "Social Milieu Oriented Routing: A New Dimension to Enhance Network Security in WSNs" Sensors 16, no. 2: 247. https://doi.org/10.3390/s16020247
APA StyleLiu, L., Chen, L., & Jia, H. (2016). Social Milieu Oriented Routing: A New Dimension to Enhance Network Security in WSNs. Sensors, 16(2), 247. https://doi.org/10.3390/s16020247






