Transmit Power Allocation for Physical Layer Security in Cooperative Multi-Hop Full-Duplex Relay Networks
Abstract
:1. Introduction
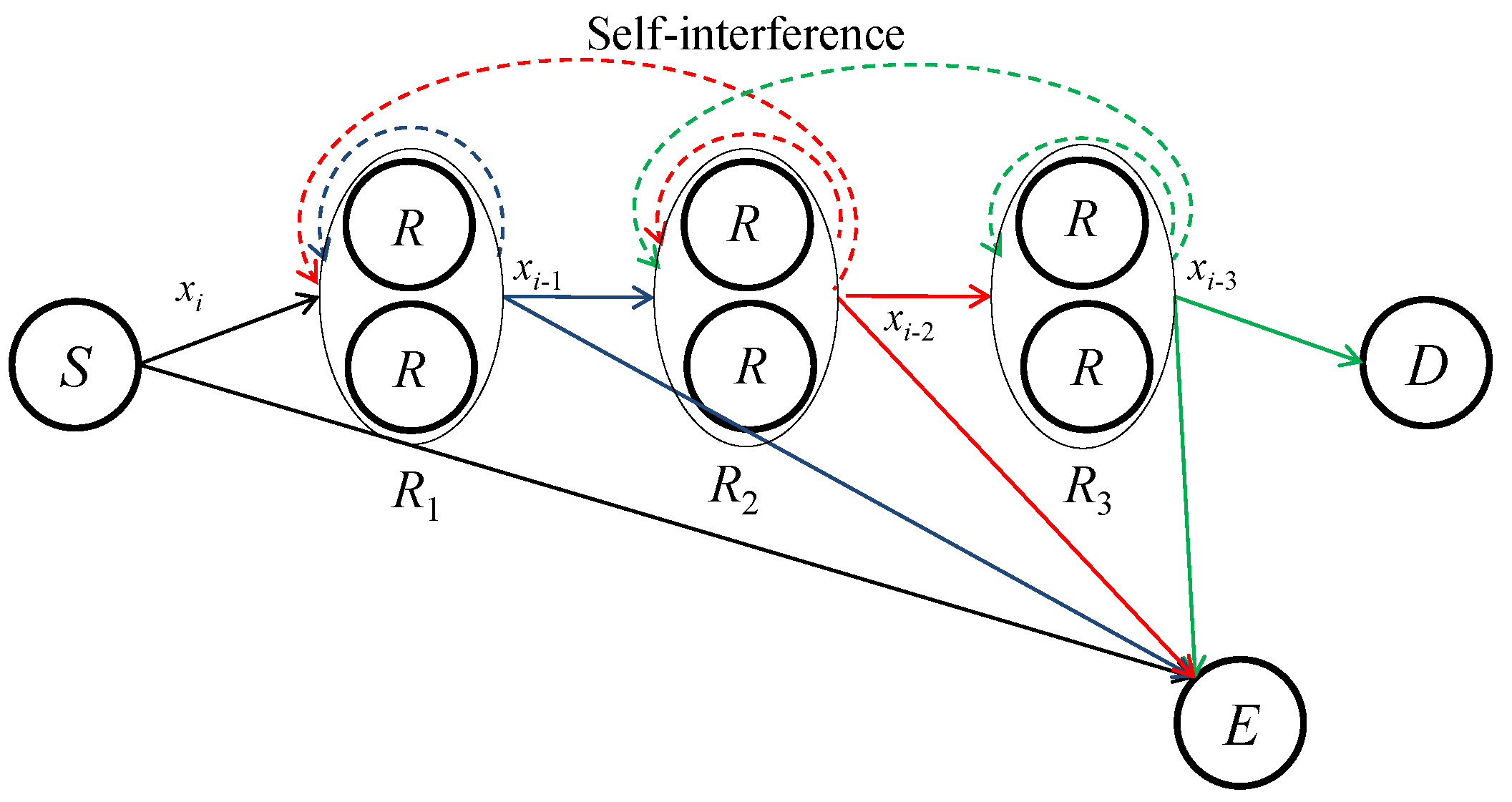
2. System Description
2.1. Signal Model
2.2. Cooperative Beamformer Design
3. Transmit Power Allocation
3.1. Optimal Power Allocation for PSIC
- We can achieve positive secrecy rates only when , and the OPA is given bywhere and
- We have no choice but to obtain zero secrecy rates when .
3.2. GP-Based Power Allocation for ISIC
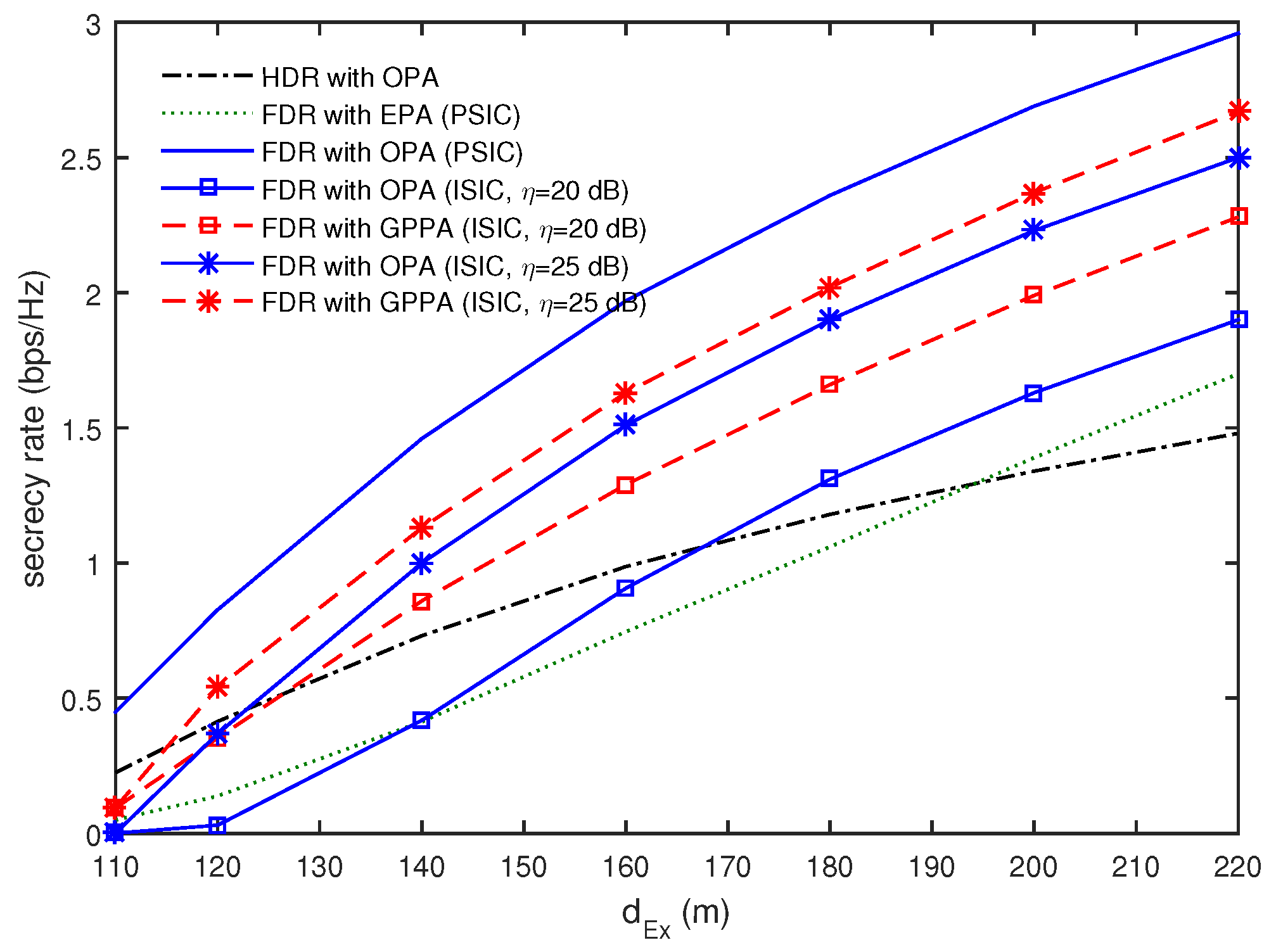
4. Numerical Results
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix A
Appendix B
References
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J.; Swindlehurst, A.L. Principles of physical layer security in multiuser wireless networks: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Dong, L.; Han, Z.; Petropulu, A.P.; Poor, H.V. Improving wireless physical layer security via cooperating relays. IEEE Trans. Signal Process. 2010, 58, 1875–1888. [Google Scholar] [CrossRef]
- Zhang, J.; Gursoy, M.C. Relay beamforming strategies for physical-layer security. In Proceedings of the 44th Annual Conference on Information Sciences and Systems (CISS), Princeton, NJ, USA, 17–19 March 2010; pp. 1–6.
- Zheng, G.; Choo, L.; Wong, K. Optimal cooperative jamming to enhance physical layer security using relays. IEEE Trans. Signal Process. 2011, 59, 1317–1322. [Google Scholar] [CrossRef]
- Li, J.; Petropulu, A.P.; Weber, S. On cooperative relaying schemes for wireless physical layer security. IEEE Trans. Signal Process. 2011, 59, 4985–4997. [Google Scholar] [CrossRef]
- Wang, H.-M.; Luo, M.; Yin, Q.; Xia, X.-G. Hybrid cooperative beamforming and jamming for physical-layer security of two-way relay networks. IEEE Trans. Inf. Forensics Secur. 2013, 8, 2007–2020. [Google Scholar] [CrossRef]
- Wang, H.-M.; Liu, F.; Yang, M. Joint cooperative beamforming, jamming and power allocation to secure AF relay systems. IEEE Trans. Veh. Technol. 2015, 64, 4893–4898. [Google Scholar] [CrossRef]
- Wang, H.-M.; Xia, X.-G. Enhancing wireless secrecy via cooperation: Signal design and optimization. IEEE Commun. Mag. 2015, 53, 47–53. [Google Scholar] [CrossRef]
- Lee, J.-H. Optimal power allocation for physical layer security in multi-hop DF relay networks. IEEE Trans. Wirel. Commun. 2016, 15, 28–38. [Google Scholar] [CrossRef]
- Zheng, G.; Krikidis, I.; Li, J.; Petropulu, A.P.; Ottersten, B. Improving physical layer security using full-duplex jamming receivers. IEEE Trans. Signal Process. 2013, 61, 4962–4974. [Google Scholar] [CrossRef]
- Chen, G.; Gong, Y.; Xiao, P.; Liu, Y.; Chambers, J.A. Physical layer network security in the full-duplex relay system. IEEE Trans. Inf. Forensics Secur. 2015, 10, 574–583. [Google Scholar] [CrossRef]
- Lee, J.-H. Full-duplex relay for enhancing physical layer security in multi-hop relaying systems. IEEE Commun. Lett. 2015, 19, 525–528. [Google Scholar] [CrossRef]
- Duarte, M.; Dick, C.; Sabharwal, A. Experiment-driven characterization of full-duplex wireless systems. IEEE Trans. Wirel. Commun. 2012, 11, 4296–4307. [Google Scholar] [CrossRef]
- Bharadia, D.; McMilin, E.; Katti, S. Full duplex radios. In Proceedings of the Annual Conference of the Special Interest Group on Data Communication (SIGCOMM), Hong Kong, China, 12–16 August 2013; pp. 375–386.
- Lee, J.-H. Self-interference cancelation using phase rotation in full-duplex wireless. IEEE Trans. Veh. Technol. 2013, 62, 4421–4429. [Google Scholar]
- Bharadia, D.; Katti, S. Full duplex MIMO radios. In Proceedings of the 11th USENIX Symposium on Networked Systems Design and Implementation, Seattle, WA, USA, 2–4 April 2014; pp. 359–372.
- Lee, J.-H.; Choi, J.; Jung, J.-H.; Kim, S.-C.; Kim, Y.-H. Analog cancellation for full-duplex wireless in multipath self-interference channels. IEICE Trans. Commun. 2015, E98-B, 646–652. [Google Scholar] [CrossRef]
- Jeong, C.; Kim, I.-M. Optimal power allocation for secure multicarrier relay systems. IEEE Trans. Signal Process. 2011, 59, 5428–5442. [Google Scholar] [CrossRef]
- Zhao, J.; Lu, Z.; Wen, X.; Zhang, H.; He, S.; Jing, W. Resource management based on security satisfaction ratio with fairness-aware in two-way relay networks. Int. J. Distrib. Sens. Netw. 2015, 2015, 819195. [Google Scholar] [CrossRef]
- Zhang, H.; Xing, H.; Cheng, J.; Nallanathan, A.; Leung, V.C.M. Secure resource allocation for OFDMA two-way relay wireless sensor networks without and with cooperative jamming. IEEE Trans. Ind. Inform. 2015, PP, 1. [Google Scholar] [CrossRef]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Huang, J.; Swindlehurst, A.L. Cooperative jamming for secure communications in MIMO relay networks. IEEE Trans. Signal Process. 2011, 59, 4871–4884. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J.O.; Rodrigues, M.R.D.; McLaughlin, S.W. Wireless information-theoretic security. IEEE Trans. Inf. Theory. 2008, 54, 2515–2534. [Google Scholar] [CrossRef]
- Wang, X.; Wang, K.; Zhang, X. Secure relay beamforming with imperfect channel side information. IEEE Trans. Veh. Technol. 2013, 62, 2140–2155. [Google Scholar] [CrossRef]
- Liao, W.-C.; Chang, T.-H.; Ma, W.-K.; Chi, C.-Y. QoS-based transmit beamforming in the presence of eavesdroppers: An optimized artificialnoise-added approach. IEEE Trans. Signal Process. 2011, 59, 4871–4884. [Google Scholar] [CrossRef]
- Liao, P.-H.; Lai, S.-H.; Lin, S.-C.; Su, H.-J. On secrecy rate of the generalized artificial-noise assisted secure beamforming for wiretap channels. IEEE J. Sel. Areas Commun. 2013, 31, 1728–1740. [Google Scholar]
- Sidiropoulos, N.D.; Davidson, T.N.; Lou, Z. Transmit beamforming for physical-layer multicasting. IEEE Trans. Signal Process. 2006, 54, 2239–2251. [Google Scholar] [CrossRef]
- Lee, J.-H. Confidential multicasting assisted by multi-hop multi-antenna DF relays in the presence of multiple eavesdroppers. IEEE Trans. Commun. 2016, 10, 4295–4304. [Google Scholar] [CrossRef]
- Koh, K.; Kim, S.J.; Mutapcic, A.; Boyd, S. GPPOSY: A Matlab Solver for Geometric Programs in Posynomial Form. 2006. Available online: http://web.stanford.edu/~boyd/ggplab/gpposy.pdf (accessed on 15 October 2016).
- Nasir, A.A.; Ngo, D.T.; Zhou, X.; Kennedy, R.A.; Durrani, S. Joint resource optimization for multicell networks with wireless energy harvesting relays. IEEE Trans. Veh. Technol. 2016, 65, 6168–6183. [Google Scholar] [CrossRef]
- Chiang, M. Geometric programming for communication systems. Found. Trends Commun. Inf. Theory. 2005, 2, 1–156. [Google Scholar] [CrossRef]
- Boyd, S.; Kim, S.-J.; Vandenberghe, L.; Hassibi, A. A tutorial on geometric programming. Optim. Eng. 2007, 8, 67–127. [Google Scholar] [CrossRef]
- Havary-Nassab, V.; Shahbazpanahi, S.; Grami, A.; Luo, Z. Distributed beamforming for relay networks based on second-order statistics of the channel state information. IEEE Trans. Signal Process. 2008, 56, 4306–4316. [Google Scholar] [CrossRef]
- Luo, Z.; Ma, W.; So, A.; Ye, Y.; Zhang, S. Semidefinite relaxation of quadratic optimization problems. IEEE Signal Process. Mag. 2010, 27, 20–34. [Google Scholar] [CrossRef]
- Sturm, J.F. Using SeDuMi 1.02, a Matlab toolbox for optimization over symmetric cones. Optim. Methods Softw. 1999, 11, 625–653. [Google Scholar] [CrossRef]
- Lofberg, J. YALMIP: A toolbox for modeling and optimization in MATLAB. In Proceedings of the IEEE International Symposium on Computer Aided Control Systems Design, Taipei, Taiwan, 2–4 September 2004; pp. 284–289.



© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, J.-H.; Sohn, I.; Kim, Y.-H. Transmit Power Allocation for Physical Layer Security in Cooperative Multi-Hop Full-Duplex Relay Networks. Sensors 2016, 16, 1726. https://doi.org/10.3390/s16101726
Lee J-H, Sohn I, Kim Y-H. Transmit Power Allocation for Physical Layer Security in Cooperative Multi-Hop Full-Duplex Relay Networks. Sensors. 2016; 16(10):1726. https://doi.org/10.3390/s16101726
Chicago/Turabian StyleLee, Jong-Ho, Illsoo Sohn, and Yong-Hwa Kim. 2016. "Transmit Power Allocation for Physical Layer Security in Cooperative Multi-Hop Full-Duplex Relay Networks" Sensors 16, no. 10: 1726. https://doi.org/10.3390/s16101726
APA StyleLee, J.-H., Sohn, I., & Kim, Y.-H. (2016). Transmit Power Allocation for Physical Layer Security in Cooperative Multi-Hop Full-Duplex Relay Networks. Sensors, 16(10), 1726. https://doi.org/10.3390/s16101726





