Secure Data Aggregation with Fully Homomorphic Encryption in Large-Scale Wireless Sensor Networks
Abstract
:1. Introduction
- To address the drawbacks of privacy homomorphic cryptography, we focus on the investigation of achievable FHE for end-to-end data confidentiality in LWSNs. The designed FESA can be implemented in sensor nodes, by which aggregators can do unlimited arithmetic aggregation functions on ciphertexts.
- In order to detect false data during both data forwarding and aggregation processes as early as possible, we propose MFN-group network structure which consists of monitoring node, forwarding node and neighboring node of aggregator. In this structure, the forwarding node and neighboring node verify the data computed by the monitoring node in the same group, and detect false data when it appears immediately. Thereby, this structure reduces the data transmission in the network with compromised nodes.
- We apply MACs to protect data integrity confidentially and conveniently. In our scheme, monitoring nodes compute MACs for the aggregated data, so that the group members can verify the integrity of data through computing and comparing the MACs directly. Therefore, we do not have to forward the plaintext for the verification. If the aggregator is captured, the attacker will not know the data.
2. Related Works
| Parameters | Data Confidentiality | Encryption Method | Data Integrity | Integrity Detection Method | Integrity Detection Position |
|---|---|---|---|---|---|
| Du et al. [23] | × | – | √ | MAC | Data aggregation |
| DAA [9] | √ | Hop-by-hop symmetric | √ | MAC | Data aggregation, forwarding and BS |
| CDA [12] | √ | End-to-end symmetric | × | – | – |
| Niu et al. [13] | √ | End-to-end symmetric | √ | Homomorphic hash | Data forwarding and BS |
| IPHCDA [14] | √ | End-to-end asymmetric | √ | MAC | BS |
| SDA-PH [15] | √ | End-to-end symmetric | √ | MAC | BS |
3. Model and Background
| Notation | Meaning |
|---|---|
| T | Network security factor |
| Ab | Backward data aggregator |
| Ac | Current data aggregator |
| An | Next data aggregator |
| Ni | Neighboring node i of aggregator |
| Fj | Forwarding node j of aggregator |
| Ml | Monitoring node l of aggregator |
| Kgroup | Group key of MFN-group |
| FH(X) | Fully homomorphic value of node X |
| subMAC(FH(X)) | subMAC of node X’s fully homomorphic value |
3.1. Network Assumptions
3.2. Attack Model
- Eavesdropping: It is the most common and easiest form of attack on data confidentiality. An attacker attempts to obtain private information by overhearing the transmissions over its neighboring wireless links. We assume the attacker can eavesdrop on the entire network.
- False data injection: This can possibly occur during data aggregation or data forwarding. A compromised node can distort data integrity by injecting false data and then drain the limited energy resources of the network. A joint data aggregation and false data detection technique has to ensure that data are changed by data aggregation only.
- Sybil attack: It is a type of attacks where the attacker is able to present more than one identity within the network. An adversary can launch a Sybil attack and generate n or more witness identities to make the base station accept the aggregation results.
3.3. Fully Homomorphic Encryption
3.4. Message Authentication Code
| Algorithm 1 The generation of subMAC |
Assumption: Ml is a member of a node group, and it shares the key Kgroup with other group mates. Each sensor node has the same pseudo-random sequence generator. begin node Ml uses Kgroup to compute MAC(Ml); Ml runs pseudo-random sequence generator Z/(T + 1) times to select Z/(T + 1) bits of MAC(Ml), and then forms the subMAC(Ml); return subMAC(Ml); end |
4. FESA: Secure Data Aggregation with Fully Homomorphic Encryption in Large-Scale Wireless Sensor Networks
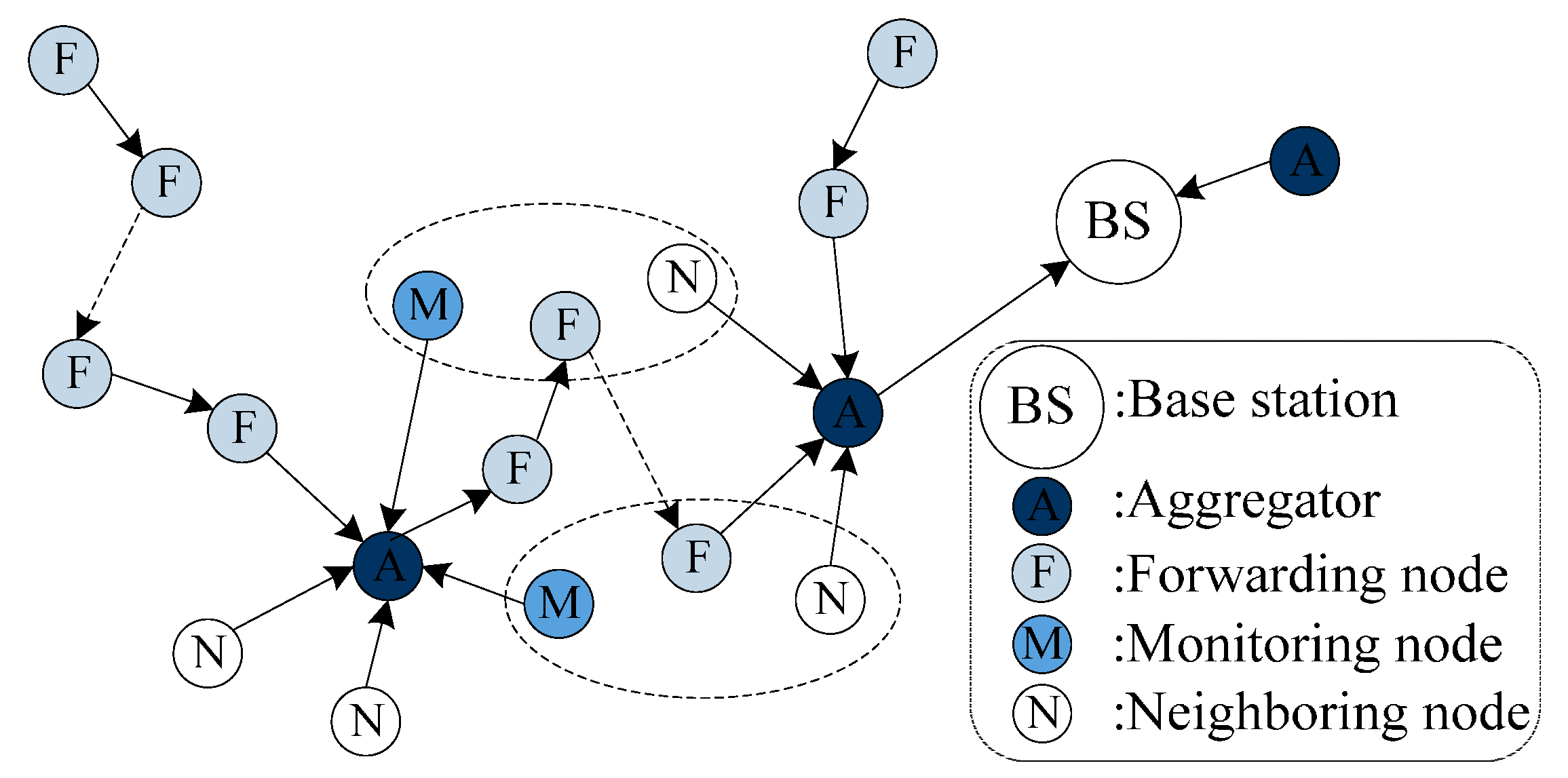
4.1. Network Structure
| Algorithm 2 The formation of network structure |
Assumption: Sensor nodes are densely distributed in the network. begin Step1. Use SANE protocol to select the aggregation nodes, make sure at least T nodes between two consecutive aggregation nodes, and each aggregation node has at least T neighboring nodes. Step2. Use MNS algorithm to select T monitoring nodes for each aggregation node. Step3. 1: An computes the MAC(Ni) of its neighboring nodes Ni and transmits the messages to Ac with the list message of Ni via Fj. 2: Fj adds its own ID into the message while transmitting. 3: Ac concatenates the IDs of Fj and Ni respectively in a random order and indexes them 1 to h and 1 to s. Then Ac computes the MAC of the concatenated IDs and broadcasts MAC, h and s to Ml. 4: Ml selects an index number between 1 to h and 1 to s, and knows the group mates Fj end |
4.1.1. Selection of Aggregators
- (1)
- There are at least T nodes, called forwarding nodes, on the path between any two consecutive aggregators.
- (2)
- Each aggregator has at least T neighboring nodes.
4.1.2. Selection of Monitoring Nodes
4.1.3. Formation of MFN-Groups
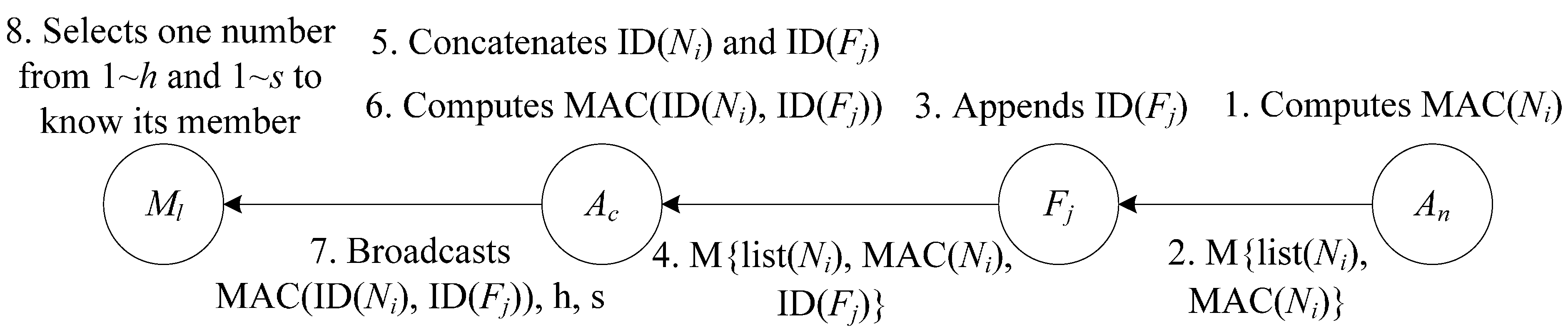
- (1)
- An computes the MAC of its neighboring node list, adds this MAC and its neighboring node list into a group discovery message M.
- (2)
- Then An sends M to Ac via forwarding nodes on the path between Ac and An.
- (3)
- Each forwarding node appends its ID to the message it forwards.
- (4)
- Assuming that An has s neighboring nodes and there are h forwarding nodes between Ac and An (s, h ≥ T), then the message Ac received contains the IDs of its forwarding nodes and neighboring nodes of An.
- (5)
- After receiving this message, Ac concatenates the IDs of the forwarding nodes in a random order and indexes them 1 to h, and also concatenates the IDs of the neighboring nodes in a random order and indexes them 1 to s.
- (6)
- Then, Ac computes the MAC of the concatenated IDs list using Kgroup.
- (7)
- Ac broadcasts the MAC, h and s to its T monitoring nodes.
- (8)
- Each monitoring node of Ac selects an index number between 1 to h and 1 to s, so that Ml of Ac knows its group members from the concatenated IDs list it received.
4.2. Key Generation
4.3. Data Encryption
4.4. Data Aggregation and Integrity Detection
- (1)
- The current aggregator Ac first collects data from its neighboring nodes. In order to detect whether any false data exists in the backward aggregator Abq, Ac broadcasts the data it received to its neighboring nodes, such that the neighboring node of Ac who is in the same MFN-group with the monitoring node of Abq verifies the data integrity by computing the subMAC. If there is at least one verification fail, Ac discards this data and informs Abq.
- (2)
- Aggregator Ac and its T monitoring nodes aggregate the received data, respectively. Ac computes the subMAC of aggregated data using Kpair, monitoring node Ml computes the subMAC of aggregated data using Kgroup, then finally T + 1 subMACs are obtained.
| Algorithm 3 Data aggregation and integrity detection algorithm |
Assumption: Ac has p leaf aggregation nodes {Ab1, …, Abp}, s neighboring nodes {N1, …, Ns}, T monitoring nodes {M1, …, MT} and h forwarding nodes {F1, …, Fh}. begin Step 1. Acand Ni verify the data integrity of Abq during data aggregation. for (q =1 to p) do 1: The last forwarding node Ni of Abqreceives the data sent by Abq, then transmits it to Ac 2: Acreceives the data and computes subMAC(FH(Abq)) to verify the data integrity 3: if the subMAC(FH(Abq)) computed by Ac and Abq are not equal then Ac drops the data immediately and informs Abq 4: else Ac broadcasts the data packet to Ni 5: All neighboring nodes of Ac, which are the member of MFN-groups, verify the data integrity. 6: if the subMAC computed by Ni is not equals to which computed by the same MFN-group member monitoring nodes of Abq then Acdrops the data immediately and informs Abq end for Step 2. Aggregate the data. 1: Ac and each monitoring node Ml aggregate all the verified data it received (l = 1 to T). 2: Ac uses the key it shared with An to compute subMAC(FH(Ac)). Ml uses the group key to compute subMAC(FH(Ml)). Each Ml sends its subMAC(FH(Ml)) to Ac. 3: Ac forms a packet containing FH(Ac), subMAC(FH(Ac)) and subMAC(FH(Ml)) and sends it to its first forwarding node. Step 3. The forwarding nodes of Ac verify the integrity of the data during data transmission. for (j = 1 to h) do 1: if Fj is not the member of MFN-groups then Fj just transmits the packet it received to the next forwarding node or An 2: else Fj verifies the subMAC(FH(Ml)) 3: if the verification is successful then Fj transmits the packet to the next forwarding node or An 4: else Fj drops the packet and informs Ac about it end for Step 4. Repeat the steps above, until the packet arrives at the base station. Relabel Ac and An as Aband Ac, respectively. Go to Step 1 to repeat the steps, until the packet is transmitted to the base station. end |
- (3)
- Ac collects these T + 1 subMACs to transmit to the next aggregator An along with aggregated data via forwarding nodes. When the forwarding nodes of Ac receive the packet, the node which is the group member of MFN-group, expressed as Fj, computes the subMAC of the aggregated data which is aggregated by its corresponding monitoring node, and then matches this subMAC. If the verification fails, Fj discards this packet immediately and informs Ac. Otherwise, if verification is successful, Fj forwards this packet.
- (4)
- When the packet arrives at the next aggregator An, An verifies the subMAC which is calculated by Ac. If this verification is successful, Ac and An are relabeled as Abq and Ac, respectively, then repeat step 1 to verify the data integrity during data aggregation.
4.5. Data Decryption
5. Security Analysis
5.1. Data Confidentiality
5.1.1. Security Analysis of FHE
5.1.2. Security Analysis of SubMAC
5.2. Data Integrity
- Lemma 1. Assume that Ac is compromised and there are additional at most T − 1 collaborating compromised nodes among the neighboring nodes of Ac and An. Then, any false data injected by Ac are detected by the An’s neighboring nodes only.
- Proof of Lemma 1. The neighboring nodes of Ac verify all the data broadcasted by Ac, each monitoring node of Ac also aggregates the entire data by itself and then computes a subMAC for the aggregated data. If Ac injects false data, it can be detected by An’s neighboring nodes that are the MFN-group members of the monitoring nodes of Ac. Since the subMACs of the plain aggregated data are verified by T neighboring nodes of An, Ac needs at least T compromised monitoring nodes to inject false data.
- Lemma 2. Assume that Ac and An are not compromised, even if all forwarding nodes of Ac are compromised, false data that they inject are detected by An.
- Proof of Lemma 2. Those forwarding nodes that are the MFN-group members of Ac’s monitoring nodes verify the transferred data, but they do not compute new subMACs for the verified data. Thus, an attacked forwarding node that injects false data cannot add a new subMAC for its false data. Because all the forwarding nodes of Ac are assumed to be compromised, the false data injected by these compromised nodes are not detected during data forwarding. This implies that An receives the false data. In Algorithm 3, aggregators verify the received data using the subMACs computed by the backward aggregators. Therefore, when An receives the false data from compromised forwarding nodes, An fails to verify the subMAC computed by Ac, which is assumed to be not compromised.
6. Simulation Results
| Parameters | Value |
|---|---|
| Number of nodes | 250 |
| Terrain dimensions | 400 × 400 m2 |
| Transmission range | 50 m |
| Data rate | 0.1 Mbps |
| Propagation pathloss model | Two-ray |
| MAC protocol | IEEE 802.11 |
| Routing protocol | DSDV |
| Simulation time | 200 s |
6.1. Computational Overhead
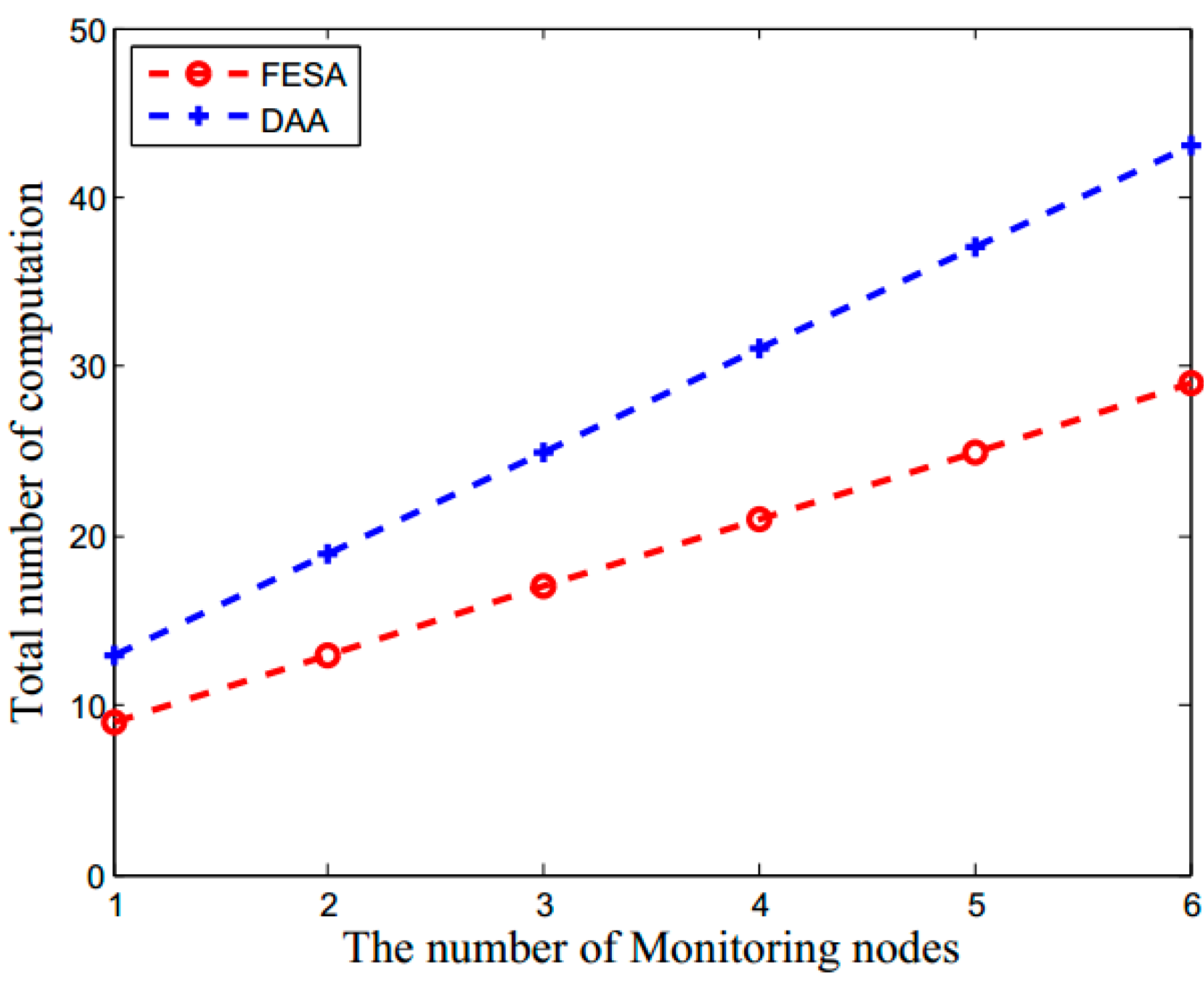
6.1.1. Computational Overhead of Encryption and Decryption
6.1.2. Computational Overhead of MACs
| Position | Aggregators | Monitoring Nodes | Forwarding Nodes | Neighboring Nodes |
|---|---|---|---|---|
| DAA | 4 | 2T | T | T |
| FESA | 2 | T | T | T |
6.2. Communication Overhead
6.2.1. Communication Overhead in Aggregator
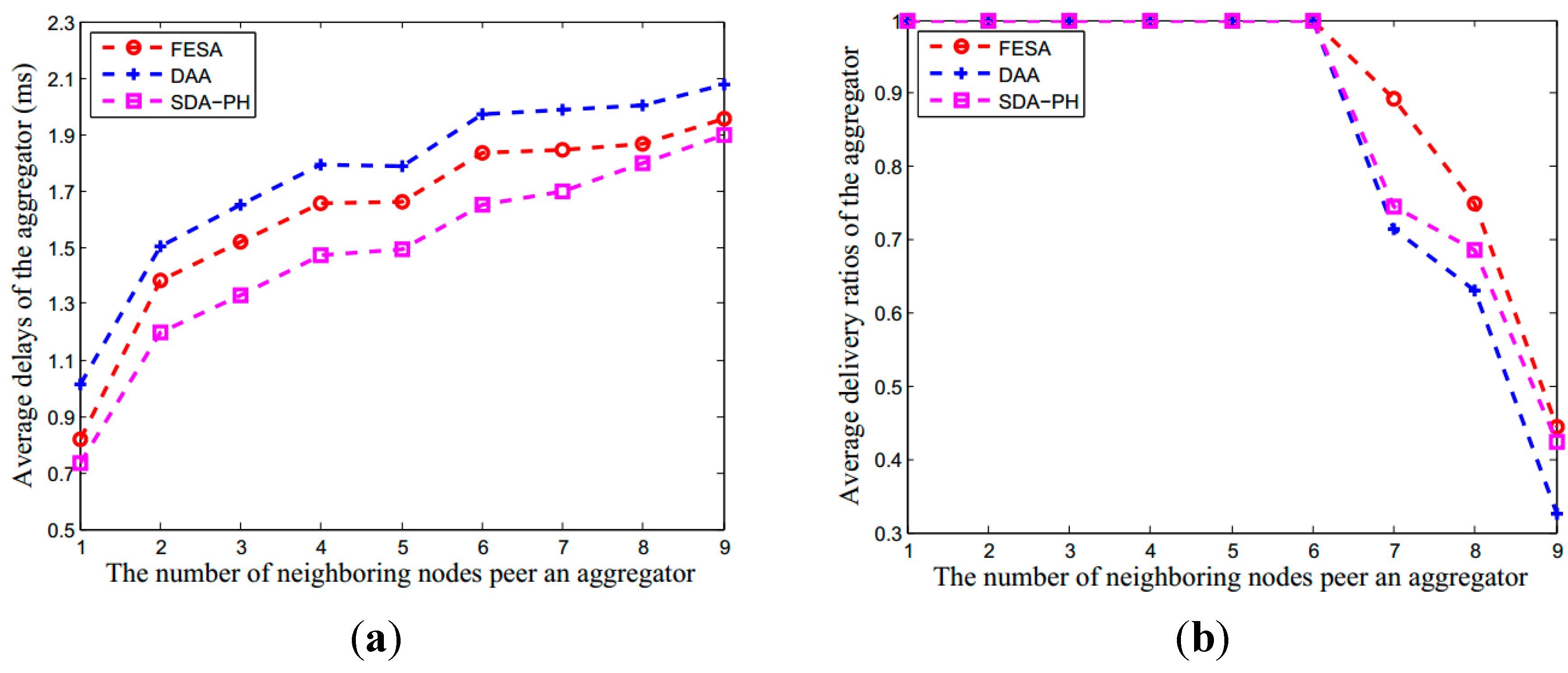
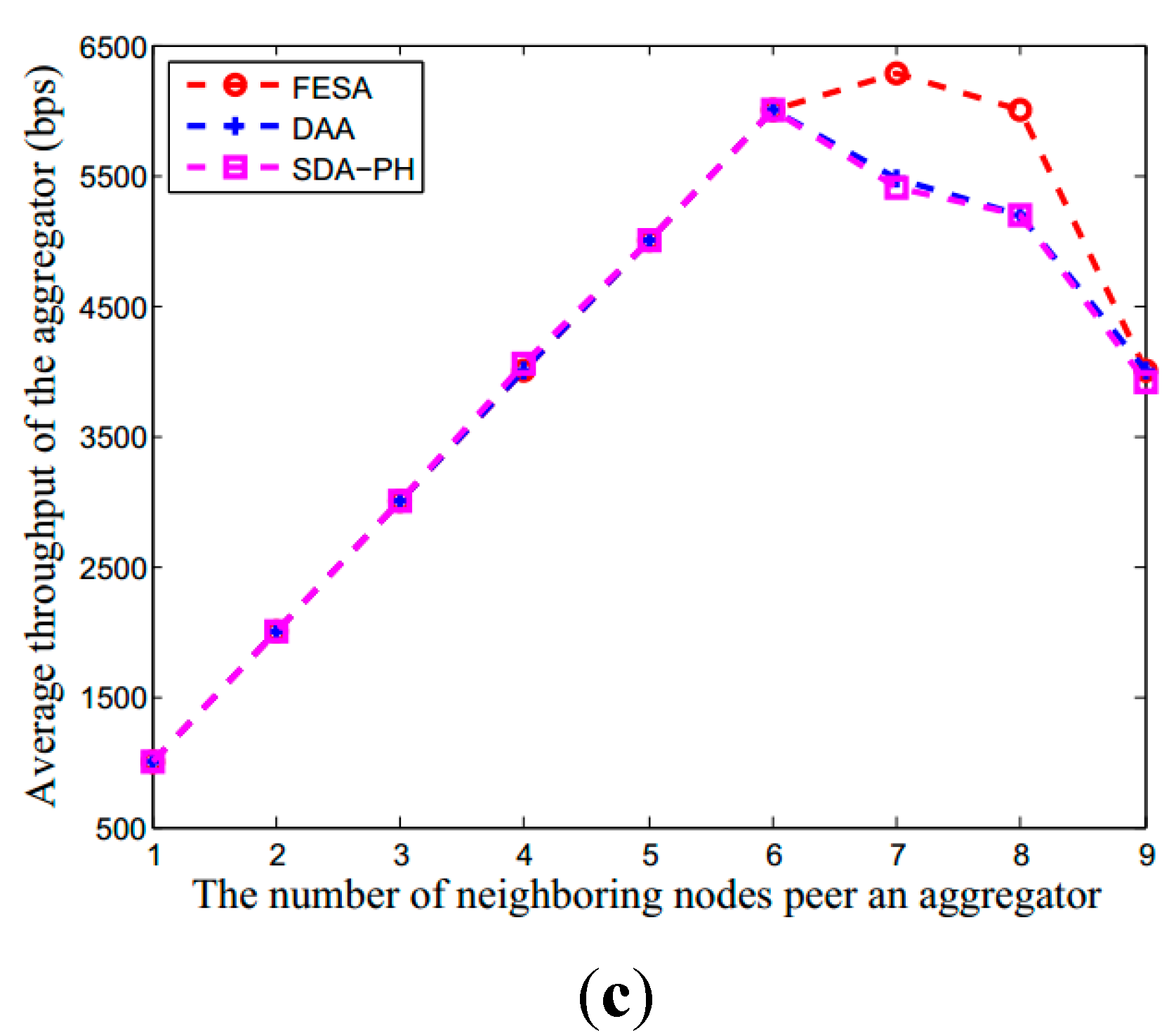
6.2.2. Communication Overhead of Network

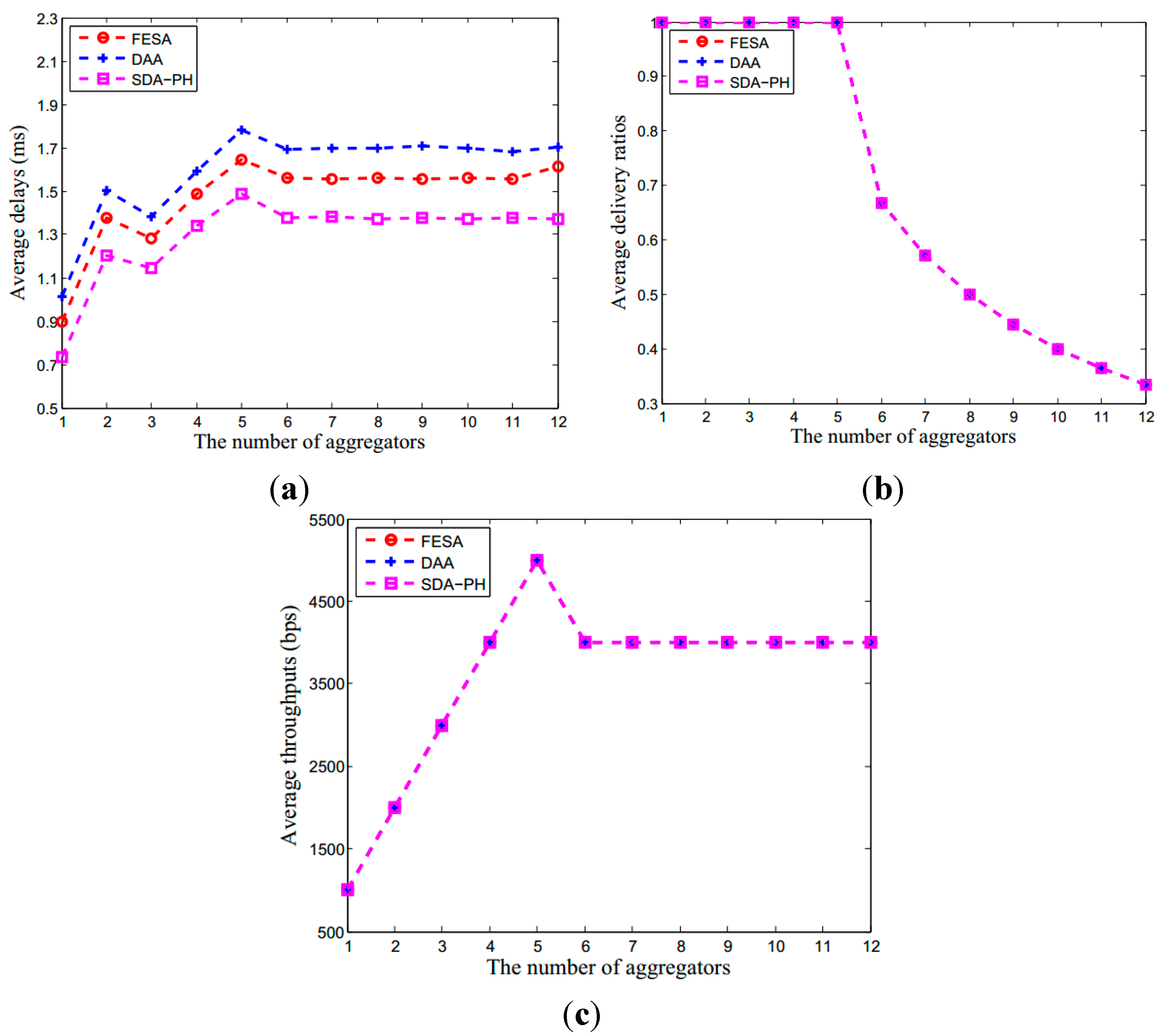

7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Leuchter, S.; Muhlenberg, D.; Schonbein, R. Agent-based web for information fusion in military intelligence, surveillance, and reconnaissance. In Proceedings of the IEEE International Conference on Systems, Man and Cybernetics (SMC’08), Suntec, Singapore, 12–15 October 2008; pp. 3732–3737.
- Bhatti, S.; Memon, S.; Jokhio, I.A.; Memon, M.A. Modelling and symmetry reduction of a target-tracking protocol using wireless sensor networks. IET Commun. 2012, 6, 1205–1211. [Google Scholar] [CrossRef]
- Dyo, V.; Ellwood, S.A.; Macdonald, D.W.; Markham, A.; Trigoni, N.; Wohlers, R.; Mascolo, C.; Pásztor, B.; Scellato, S.; Yousef, K. WILDSENSING: Design and deployment of a sustainable sensor network for wildlife monitoring. ACM Trans. Sensor Netw. 2012, 8. [Google Scholar] [CrossRef]
- Darwish, A.; Hassanien, A.E. Wearable and implantable wireless sensor network solutions for healthcare monitoring. Sensors 2011, 11, 5561–5595. [Google Scholar] [CrossRef] [PubMed]
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. A survey on sensor networks. IEEE Commun. Mag. 2002, 40, 102–114. [Google Scholar] [CrossRef]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Wang, L.M.; Shi, Y. Patrol detection for replica attacks on wireless sensor networks. Sensors 2011, 11, 2496–2504. [Google Scholar] [CrossRef] [PubMed]
- Zhu, S.; Setia, S.; Jajodia, S.; Ning, P. Interleaved hop-by-hop authentication against false data injection attacks in sensor networks. ACM Trans. Sensor Netw. 2007, 3. [Google Scholar] [CrossRef]
- Ozdemir, S.; Cam, H. Integration of false data detection with data aggregation and confidential transmission in wireless sensor networks. IEEE/ACM Trans. Netw. 2010, 18, 736–749. [Google Scholar] [CrossRef]
- Ozdemir, S.; Yang, X. Secure data aggregation in wireless sensor networks: A comprehensive overview. Comput. Netw. 2009, 53, 2022–2037. [Google Scholar] [CrossRef]
- Sang, Y.P.; Shen, H.; Inoguchi, Y.; Tan, Y.; Xiong, N. Secure data aggregation in wireless sensor networks: A survey. In Proceedings of the 7th International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT’06), Taipei, China, 4–7 December 2006; pp. 315–320.
- Westhoff, D.; Girao, J.; Acharya, M. Concealed data aggregation for reverse multicast traffic in sensor networks: Encryption keydistribution and routing adaptation. IEEE Trans. Mobile Comput. 2006, 5, 1417–1431. [Google Scholar] [CrossRef]
- Niu, S.F.; Wang, C.F.; Yu, Z.X.; Cao, S. Lossy data aggregation integrity scheme in wireless sensor networks. Comput. Electr. Eng. 2013, 39, 1726–1735. [Google Scholar] [CrossRef]
- Ozdemir, S.; Yang, X. Integrity protecting hierarchical concealed data aggregation for wireless sensor networks. Comput. Netw. 2011, 55, 1735–1746. [Google Scholar] [CrossRef]
- Zhou, Q.; Yang, G.; He, L.W. An efficient secure data aggregation based on homomorphic primitives in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2014, 2014, 962925. [Google Scholar] [CrossRef]
- Rivest, R.L.; Adleman, L.; Dertouzos, M.L. On data banks and privacy homomorphisms. Found. Secure Comput. 1978, 4, 169–180. [Google Scholar]
- Gentry, C. Fully homomorphic encryption using ideal lattices. In Proceedings of the 41th ACM Symposium on Theory of Computing (STOC’09), Bethesda, MD, USA, 31 May–2 June 2009; pp. 169–178.
- Dijk, M.V.; Gentry, C.; Halevi, S.; Vaikuntanathan, V. Fully homomorphic encryption over the integers. In Proceedings of the 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT’10), Riviera, France, 30 May–3 June 2010; pp. 24–43.
- Perrig, A.; Szewczyk, R.; Tygar, D.; Wen, V.; Culler, D. SPINS: Security protocols for sensor networks. Wirel. Netw. J. 2002, 8, 521–534. [Google Scholar] [CrossRef]
- Du, W.L.; Deng, H.; Han, Y.S.; Varshney, P.K.; Katz, J.; Khalili, A. A pairwise key predistribution scheme for wireless sensor networks. ACM Trans. Inf. Syst. Secur. 2005, 8, 228–258. [Google Scholar] [CrossRef]
- Harn, L.; Lin, C.L. Authenticated group key transfer protocol based on secret sharing. IEEE Trans. Comput. 2010, 59, 842–846. [Google Scholar] [CrossRef]
- Katz, J.; Yung, M. Scalable protocols for authenticated group key exchange. J. Cryptol. 2007, 20, 85–113. [Google Scholar] [CrossRef]
- Du, W.L.; Deng, H.; Han, Y.S.; Varshney, P.K. A witness-based approach for data fusion assurance in wireless sensor networks. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM’03), San Francisco, CA, USA, 1–5 December 2003; pp. 1435–1439.
- Rivest, R.L.; Adleman, L.; Dertouzos, M.L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Zhao, F.; Li, C.; Liu, C.F. A cloud computing security solution based on fully homomorphic encryption. In Proceedings of the 16th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Korea, 16–19 February 2014; pp. 485–488.
- Castelluccia, C.; Mykletun, E.; Tsudik, G. Efficient aggregation of encrypted data in wireless sensor networks. In Proceedings of the 2nd Annual International Conference on Mobile and Ubiquitous Systems: Networking and Services (MobiQuitous’05), San Francisco, CA, USA, 17–21 July 2005; pp. 109–117.
- Karlof, C.; Sastry, N.; Wagner, D. TinySec: A link layer security architecture for wireless sensor networks. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems (SenSys’04), Baltimore, MD, USA, 3–5 November 2004; ACM Press: New York, NY, USA; pp. 162–175.
- Seetharam, D.; Rhee, S. An efficient pseudo random number generator for low-power sensor networks. In Proceedings of the 29th Annual IEEE International Conference on Local Computer Networks (LCN’04), Washington, DC, USA, 16–18 November 2004; pp. 560–562.
- Sirivianos, M.; Westhoff, D.; Armknecht, F.; Girao, J. Nonmanipulable aggregator node election protocols for wireless sensor networks. In Proceedings of the International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks (WiOpt’07), Limassol, Cyprus, 16–20 April 2007; pp. 1–10.
- The Network Simulator– ns-2. Available online: http://www.isi.edu/nsnam/ns (accessed on 30 May 2015).
- Zhu, X.Y.; Jiang, S.R.; Wang, L.M.; Li, H.; Zhang, W.D.; Li, Z. Privacy-preserving authentication based on group signature for VANETs. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013; pp. 4609–4614.
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, X.; Chen, D.; Li, C.; Wang, L. Secure Data Aggregation with Fully Homomorphic Encryption in Large-Scale Wireless Sensor Networks. Sensors 2015, 15, 15952-15973. https://doi.org/10.3390/s150715952
Li X, Chen D, Li C, Wang L. Secure Data Aggregation with Fully Homomorphic Encryption in Large-Scale Wireless Sensor Networks. Sensors. 2015; 15(7):15952-15973. https://doi.org/10.3390/s150715952
Chicago/Turabian StyleLi, Xing, Dexin Chen, Chunyan Li, and Liangmin Wang. 2015. "Secure Data Aggregation with Fully Homomorphic Encryption in Large-Scale Wireless Sensor Networks" Sensors 15, no. 7: 15952-15973. https://doi.org/10.3390/s150715952
APA StyleLi, X., Chen, D., Li, C., & Wang, L. (2015). Secure Data Aggregation with Fully Homomorphic Encryption in Large-Scale Wireless Sensor Networks. Sensors, 15(7), 15952-15973. https://doi.org/10.3390/s150715952






