DEADS: Depth and Energy Aware Dominating Set Based Algorithm for Cooperative Routing along with Sink Mobility in Underwater WSNs
Abstract
: Performance enhancement of Underwater Wireless Sensor Networks (UWSNs) in terms of throughput maximization, energy conservation and Bit Error Rate (BER) minimization is a potential research area. However, limited available bandwidth, high propagation delay, highly dynamic network topology, and high error probability leads to performance degradation in these networks. In this regard, many cooperative communication protocols have been developed that either investigate the physical layer or the Medium Access Control (MAC) layer, however, the network layer is still unexplored. More specifically, cooperative routing has not yet been jointly considered with sink mobility. Therefore, this paper aims to enhance the network reliability and efficiency via dominating set based cooperative routing and sink mobility. The proposed work is validated via simulations which show relatively improved performance of our proposed work in terms the selected performance metrics.1. Introduction
Oceans cover about two-thirds of the surface of the earth. They have gained importance because of the hidden resources, military surveillance purposes and underwater environment monitoring. UWSNs have gained attention for these explorations. Typical framework of UWSN is composed of underwater sensor nodes, sink nodes, surface stations, etc. Acoustic signals are used for communication in UWSNs due to the relatively low absorption rate in underwater environment. However, continuously varying water temperature, salinity, pressure, density and noise make the underwater environment harsh for signal propagation. Furthermore, the unique characteristics of acoustic signals impose numerous challenges on devising efficient data routing protocols in UWSNs. Sensor nodes in UWSNs consume more energy due to severe environmental conditions where replacement or recharging of battery is not feasible. Bandwidth available for communication is limited (<100 kHz) because of high attenuation and absorption of acoustic signals. Link characteristics like transmission loss, propagation delay and Signal-to-Noise Ratio (SNR) are continuously varying with time and depth. Moreover, BER is also high due to multi-path fading and refraction phenomena. Therefore, improved network lifetime, energy efficiency and high throughput along with reliability of received data stand out as a critical consideration [1] .
Graph theory serves to model different network topologies. It is widely used to devise algorithms for efficient data routing in Wireless Sensor Networks (WSNs). UWSNs involving depth-based routing can be represented by a directed graph (or digraph), G = (V, A). A digraph is a graph, or set of nodes (V) connected by directed edges or arcs (A), where the arcs have a direction associated with them. We are considering a digraph for data routing in underwater environment because in depth-based routing data needs to be routed upwards, that is, towards low depth (surface station present on water surface).
Cooperative communication exploits the broadcast nature of wireless transmission and relies on cooperation of nodes in relaying each others' information. It involves the use of a source, relay and destination node. When source node broadcasts any signal it is received by destination node and also overheard by relay node in its sensing range. Relay node then forwards this overheard signal to destination node as a replica of the original signal [1]. Two types of relaying schemes usually implemented at relay nodes are: Amplify-and-Forward (AF) and Decode-and-Forward (DF) [2]. Relay node simply amplifies the signal and transmits it in the former scheme, whereas, received signal is decoded, corrected, recoded and then transmitted in later. Different number of relay nodes can be selected as per application requirement. Cooperative communication is incorporated in UWSNs to improve the network performance in terms of packet delivery ratio and data reliability.
General architecture [3–6] of UWSNs involves static sinks which are usually deployed on water surface. However, static sinks result in hotspot problem in which sensor nodes closer to the sinks tend to die early because of forwarding more packets (packets from nodes that lie far away from sinks), leaving certain area of network completely unmonitored. Hence, it is beneficial to use Mobile Sinks (MSs) to transfer sensed information [7].
In this paper, we present a mathematical model for cooperative routing along with sink mobility in UWSNs. This work is an extension of the work in [8] in which cooperative routing along with sink mobility is investigated at network layer. The proposed mathematical model involves an algorithm to compute the Dominating Set (DS) of a given network modeled as a digraph. DS formation helps in organizing nodes in a way that is optimal for cooperative routing. DS is a subset of vertices V such that each vertex in V – DS is adjacent to at least one vertex in DS. Vertices which belong to DS are able to perform tasks related to data routing and can serve vertices that are not in the set. DS formation reduces communication overhead, increases bandwidth efficiency and decreases energy consumption which ultimately increases network lifetime in UWSNs. Vertices in DS efficiently forward data towards MSs which are following pre-defined optimal trajectories.
The rest of the paper is organized as follows. In Section 2, related work along with motivation is presented. In Sections 3 and 4, the channel model and the mathematical model are discussed. Section 5 presents a detailed explanation of our proposed scheme. Section 6 deals with the discussion of simulation results and Section 7 concludes the paper.
2. Related Work and Motivation
Cooperative communication takes advantage of the broadcast nature of wireless transmissions in which transmitted signal can be overheard by many unintended sensor nodes. It has been proposed as an alternate mechanism over multi-hop communication for minimizing the effect of fading and other link impairments [1]. Some recent work involving cooperative communication is precisely reviewed here.
An innovative physical layer solution involving cooperative communication is given in [1], where outage probability and capacity expressions are derived for cooperative multicarrier Underwater Acoustic Communication (UAC) systems with AF and DF relaying. Effect of several channel parameters is demonstrated via the derived expressions. Furthermore, they propose a receiver design to mitigate the degrading Doppler effects. In [2], Cooperative UnderWater Acoustic Multiple Input Single Output (CUWA-MISO) using DF is proposed. Virtual antennas are used in this work and their effects on system performance are studied. Each node present in the network uses nearest adjacent node as a virtual antenna in a cooperative manner. This process improves the system performance with the help of spatial diversity. Luo et al. [9] explore cooperation at MAC layer and propose a distributed MAC protocol; Coordinated Transmission MAC (CT-MAC) for underwater Multiple Input Multiple Output (MIMO) based network uplink communication. Flooding is avoided by devising a coordination scheme among immediate neighbors for channel competition. CT-MAC also addresses long propagation delay and collision among control packets in UAC. Authors in [10] improved channel efficiency by applying asynchronous cooperative transmission for three dimensional UWSNs. Two typical forwarding schemes: AF and DF are implemented, analyzed and compared. Moreover, an adaptive and hybrid forwarding scheme is also proposed in which each node chooses appropriate forwarding scheme to achieve better BER performance. In COoperative Best Relay Assessment (COBRA) [11], a relay selection criterion for underwater cooperative acoustic networks is developed which requires channel statistical information instead of the instantaneous channel state. COBRA minimizes one-way packet transmission time. Best relay selection algorithm based on COBRA criterion is also proposed in this work. In [12], authors consider cooperative scheme focusing on physical, MAC and network layer. This scheme results in an efficient network operation and reduces the transceiver's complexity. Distance cost and local measurement of channel conditions are considered while selecting destination and potential relay nodes. This scheme enhances reliability by providing diversity gains through intermediate relay nodes.
Network lifetime may be improved by using sink mobility. Some of the protocols that involve sink mobility are briefly stated here.
An adaptive strategy for highly dynamic underwater environment is proposed in [7] that guarantees minimum energy consumption by enforcing sink redeployment. Sink redeployment decision is based on routing information. When there is high current mobility in the underwater environment, nodes use comparatively more power for communication. To overcome this high power usage, sink redeployment procedure starts to find an optimal new location for surface sink. A coordination scheme using sink mobility for data gathering in UWSNs is proposed by authors in [13] that achieve energy efficiency and communication reliability. The shortest wake up time and optimal period of sleep time for sensor nodes are investigated in this work. Furthermore, transmission power control by using received signal strength is introduced in order to decrease energy consumption. In [14], an underwater application model for collecting data with multiple MSs is presented. Three algorithms are presented to accomplish the entire network model. These algorithms achieve reduced energy consumption and lower end-to-end delay. In [15], sink mobility is used to improve network lifetime and energy efficiency in three dimensional UWSNs. An optimal mobile sink strategy is proposed to maximize network lifetime by converting each mobility pattern into a combination of circular motions via mapping. MobiRoute defined by authors in [16] supports sink mobility. Sink's controlled and predictable mobility and pause time are favorable features of MobiRoute. Autonomous Underwater Vehicle (AUV) aided Underwater Routing Protocol (AURP) in [17] minimizes total number of data transmissions by using multiple MSs or AUVs as relay nodes, which results in high packet delivery ratio and low energy consumption. In AUV aided Energy Efficient Routing Protocol (AEERP) for UWSNs [18], MS collects data from gateway nodes. Among all the nodes, gateway nodes communicate with MS. Gateway nodes are selected on the basis of their residual energy.
Localization-free, non-cooperative and cooperative, depth-based routing protocols for UWSNs are stated here.
In [3], a novel routing protocol known as Depth-Based Routing (DBR) is proposed that uses depth of sensor nodes as a routing metric and forwards data towards sink by applying greedy algorithm. In [4], an energy efficient routing protocol, named as Energy Efficient Depth Based Routing (EEDBR) is presented. EEDBR utilizes depth as well as residual energy of sensor nodes as routing metrics so that network lifetime can be improved. Authors in Improved Adaptive Mobility of Courier Nodes in Threshold-Optimized DBR (iAMCTD) [5] propose a forwarding function based routing scheme. It is a localization-free and flooding-based routing protocol for underwater applications. iAMCTD achieves energy conservation by incorporating threshold optimized data routing. CoDBR [6] is cooperative depth based routing protocol in which cooperation is employed at network layer. Cooperative routing increases reliability and throughput of the network. Potential relays are selected on the basis of depth information. Data from source node is cooperatively forwarded to the destination by relay nodes.
In UWSNs, high throughput along with reliability of the received information, reduced delay, low BER and energy conservation are of great concern. Novel routing solutions are therefore required for efficient data routing. Cooperative communication achieves high throughput along with reliable data transfer by reducing BER, however, it results in high propagation delay. Sink mobility reduces propagation delay and achieves energy conservation, however, it does not cater for reliability of received information. In this regard, many cooperative communication protocols [12] are proposed that either investigate the physical layer or the MAC layer, however, the network layer is still unexplored. More specifically, cooperative routing has not yet been jointly considered with sink mobility. Therefore, this work focuses on an efficient mathematical model for cooperative routing along with sink mobility in UWSNs because we are interested in taking advantage of positive aspects of both the techniques along with minimizing their drawbacks.
3. Channel Model
Channel model is discussed in this section. Each source node modulates its data using Binary Phase Shift Keying (BPSK) modulation scheme. In water (as a communication medium), the transmitted signal suffers fading and noise. Fading is due to multiple paths traversed by the transmitted signal and noise is due to shipping, turbulence, wind, thermal activities, etc. In under water environment, typical considerations involve absence of the dominant component. Thus, we assume Rayleigh fading and subject to noise we assume the AWGN model. Equations (1), (2) and (3) [19] describe relationship between the signals that are transmitted and received by source, relay and destination nodes. Xs is the original signal, Ysd and Ysr are signals received at destination and relay nodes via source node. Yrd is signal received at destination node via relay node. nsd and nsr are channel noises existing over source to destination and source to relay links. nrd represents channel noise existing over relay to destination link. gsd and gsr are channel gains existing over source to destination and source to relay links. grd represents channel gain existing over relay to destination link. Signals received at relay and destination nodes via source node are represented as:
Signal received at destination node via relay node is represented as:
Two independently faded copies (Ysd and Yrd) of source's data are combined at destination node by using Maximal Ratio Combining (MRC) as a diversity combining technique [19].
4. Mathematical Model
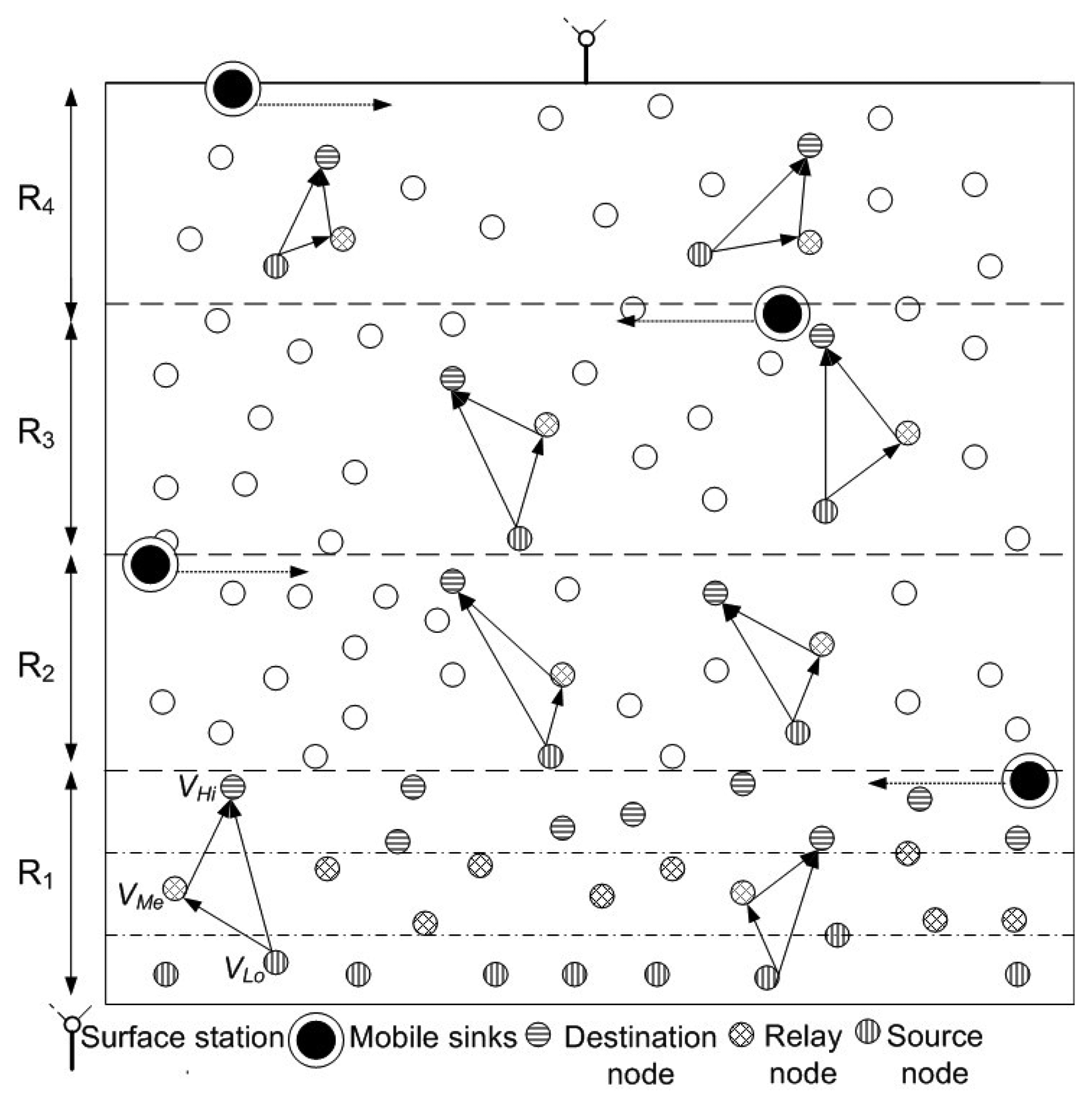
In the proposed model, we consider that nodes are randomly deployed in an underwater environment, as shown in Figure 1. All nodes have a predefined transmission range associated with them. Initially, nodes do not possess depth and residual energy information of one-hop neighbors. This information is attained in the broadcasting phase. In this phase, all nodes share depth and residual energy information with one-hop neighbors. Along with this, nodes keep on sharing their residual energy information (at regular time intervals) during the network lifetime. Different rules and concepts that are followed in our algorithm are detailed:
Rule 1: Network is divided into 4 distinct regions or sub-graphs (Rk | k = 1 − 4) on the basis of depth (D), such that, in any subgraph all nodes are one-hop apart and lie within each other's transmission range. Figure 1 signifies rule 1 by showing one-hop apart nodes within each sub-graph.
D(R1) > D(R2) > D(R3) > D(R4)
Rule 2: In each Rk, vertices are divided among three distinct sets, VHi, VMe and VLo as shown in Figure 1, where
VHi are high depth vertices in a sub-graph
VMe are medium depth vertices in a sub-graph
VLo are low depth vertices in a sub-graph
A DS is formed for each Rk on the basis of a certain criterion. We define DS with respect to this work as;
DS: DS is a subset of vertices V of any Rk such that every vertex not in the DS is adjacent to at least one vertex in DS.
DS for cooperative routing is computed on the bases of depth and residual energy information of sensor nodes. Nodes having lowest depth and highest residual energy in each Rk form a DS such that all the other nodes in that Rk are connected to at least one node in DS.
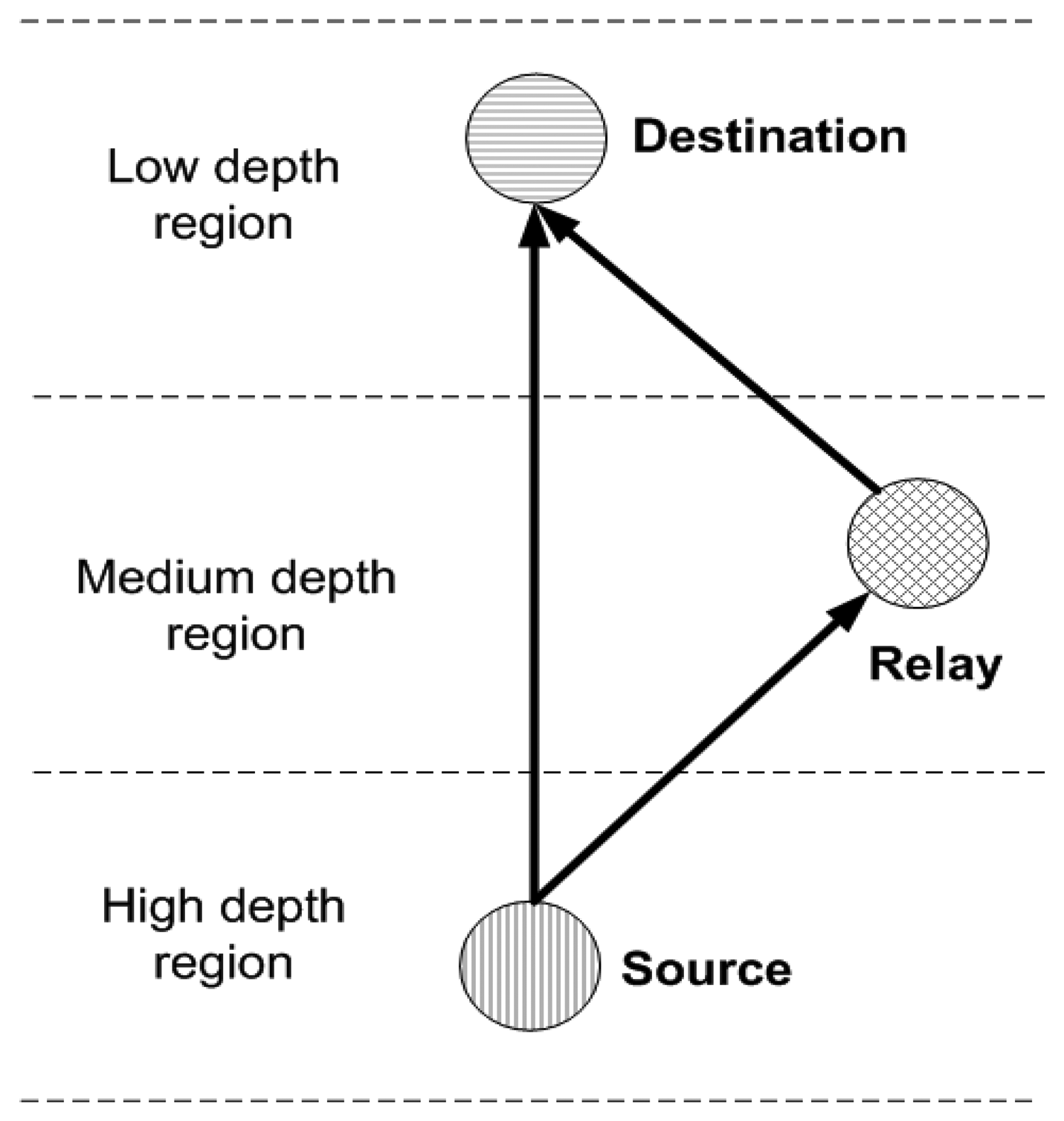
Rule 3: Source, relay and destination nodes in any Rk belong to VLo, VMe and VHi such that;
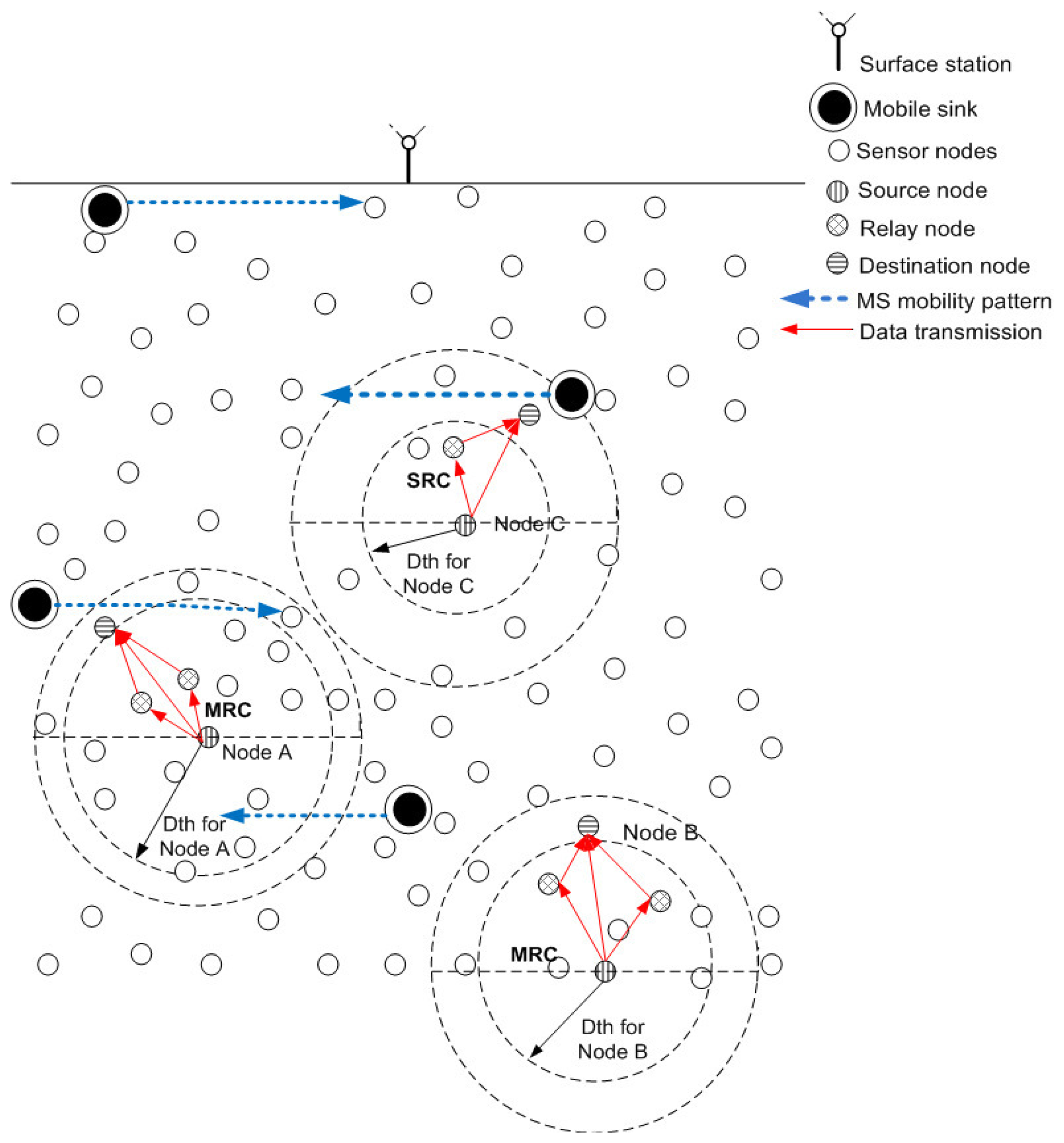
DD < DR < DS where DD, DR and DS represent depth of destination, relay and source nodes respectively. This relation shows that source, relay and destination nodes are present at highest, medium and lowest depth regions in any Rk, respectively. Rule 3 is shown in Figure 2. We assume that MSs are periodically transmitting beacon signals because of which nodes are aware of their mobility pattern and are forwarding data accordingly.
In wireless transmission, flooding is a routing process in which each incoming data packet is sent via every outgoing link except the one from which it was received. Flooding results in duplication of data and thus wastes resources of the network. In depth-based routing, depth threshold (dth) is used to avoid flooding by limiting the number of outgoing links for each incoming data packet.
DBR [3], EEDBR [4], iAMCTD [5] and CoDBR [6] are existing depth-based routing protocols in UWSNs. In DBR, EEDBR and CoDBR, dth is pre-defined and remains fixed throughout the network lifetime. In iAMCTD, dth is selected and varied according to the network density information which requires exchange of control packets at regular time intervals. This exchange acts as an overhead and wastes network resources. We present a way for varying dth that minimizes this huge control packet exchange. In our work, nodes just require the residual energy information of one-hop neighbors.
Rule 4: Value of dth is selected and varied according to the number of alive neighbors of a node, i.e.,
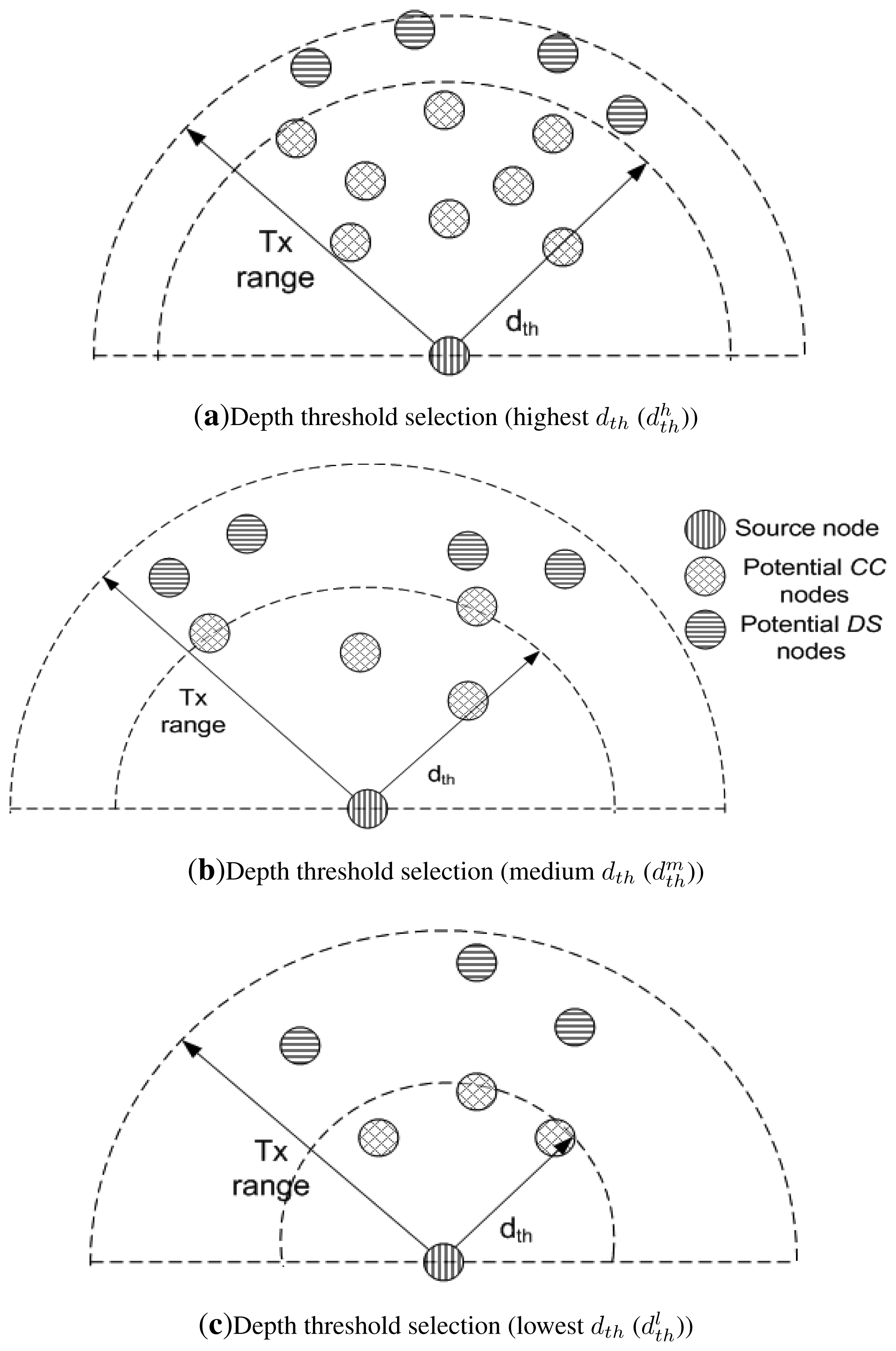
Increase in N leads to increased dth and decrease in N leads to decreased dth. This relation signifies that the greater the number of alive neighbors, higher is the value of dth and vice versa. In this way, nodes just require one-hop neighbor information instead of complete network information. dth plays an important role in selection of destination and relay nodes. Neighbors of a node are distinguished as potential DS and Cooperative Connector (CC) nodes on the basis of dth as shown in Figure 3. Destination and relay nodes belong to DS and CC node sets.
As shown in Figure 3a, number of nodes are present within the transmission range of source node. Due to this high node density its dth is high ( ). As node density within the transmission range decreases, dth also decreases. and show the decreased dth in Figure 3b,c.
Rule 5: Neighbor set of an ith node is represented as
Noutdth(i) represents neighbors of an ith node that lie outside the boundary specified by dth as shown in Figure 3 as potential DS nodes.
Nindth (i) represents neighbors of an ith node that lie inside the boundary specified by dth as shown in Figure 3 as potential CC nodes.
Equation (7) signifies that Noutdth(i) and Nindth(i) are low and medium depth vertices in any Rk, respectively.
Rule 6: For each Rk, the potential DS nodes are
Initially, for any particular Rk, lowest depth one-hop neighbors (Noutdth) of vertices represented by VHi are considered eligible for inclusion in the DS. Smaller the size of DS, lesser is the message overhead and network routing efficiency is also improved. In order to reduce the size of DS, nodes are further pruned, using their residual energy as a pruning parameter. After pruning in each Rk, lowest depth nodes possessing highest energy are present in DS.
Rule 7: The lowest depth and highest energy DS nodes are the destination nodes for cooperative routing. Whereas, Probability of selection (Ps) of any node i belonging to VLo as DS node is
Hence, Selection Parameter for DS nodes, (SPDS), is a function of nodes' depth and residual energy:
SP for DS nodes at time t, SPDS(t) is given as:
Re(t): Residual energy of any DS node at time t in joules
D(t): Depth of any DS node at time t in meters
The higher the value of SPDS(t) for any particular node, the greater the chance of its inclusion in DS and vice versa. DS node set recalculation is performed at regular time interval, t = 120 s, so that the nodes having minimum depth and high energy are selected as DS nodes. In this way, chances of data reception at MS are increased and a balanced energy consumption is involved in the network throughout the network operation.
Rule 8: The highest energy one hop neighbors (belonging to Nindth) of vertices represented by VHi are considered eligible to be used as CCs. CCs are the relay nodes used in cooperative routing. They connect source nodes with the DS nodes via an alternate path.
For each Rk, CC nodes are:
Rule 9: The highest energy nodes are the CCs for cooperative routing. Where, Ps of any node i belonging to VMe as CC node is:
Hence, Selection Parameter for CC nodes, (SPCC), is a function of nodes' residual energy:
SP for the CC at time t is
The larger the value of SPCC(t) for any particular node belonging to VMe, the greater the chances of its inclusion in CC node set and vice versa. CC node set recalculation is performed at regular time interval, t = 120 s, so that high energy nodes are selected as CC nodes and a balanced energy consumption is involved in the network throughout the network operation.
Rule 10: All CC and non-CC medium depth vertices in each Rk forward their data towards non-DS low depth vertices directly or in a cooperative manner (depending on node availability).
Similarly, all non-DS low depth vertices in any sub-graph k forward their data towards MSs directly or in a cooperative manner (depending on node availability). For any particular Rk;
DS recalculation is performed at regular time interval, t = 120 s, in order to achieve balanced energy consumption throughout the network operation. The nodes require residual energy information in DS re-calculation. However, in contrast to the existing iAMCTD, the information exchange in our proposed work is limited to one-hop neighbors only. In this way, the overhead is reduced.
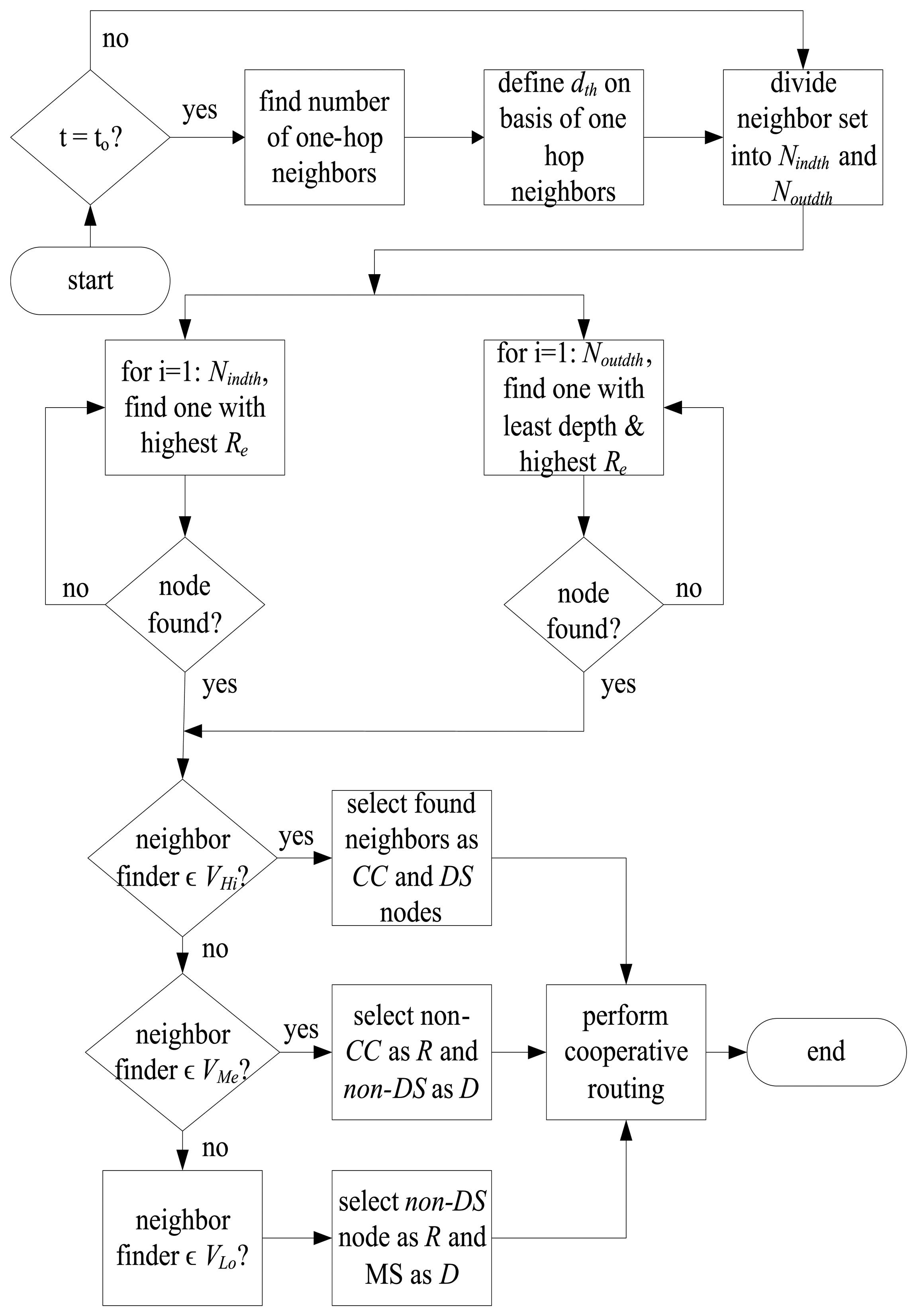
The flow chart in Figure 4 shows the selection of relay and destination nodes which is then followed by cooperative routing. All nodes find their one-hop neighbors at regular time intervals, to and define their dth by following rule 4. If a node does not possess any neighboring node it goes in the sleep mode in which it does not perform transmission/reception. After selection of dth, neighboring nodes are differentiated among Nindth and Noutdth according to rule 5. Nodes belonging to VHi use rules 6–9 for the selection of CC and DS nodes. CC node belongs to Nindth and possesses the highest Re, whereas, destination node is one that belongs to Noutdth and possesses the highest Re and least depth. Nodes belonging to VMe and VLo follow rule 10 for selection of relay and destination nodes. This is because all the nodes that belong to VMe and VLo might not act as CC or DS nodes, however, all of them have to forward their data to mobile sink and they forward it by following rule 10. If the neighbor finder node belongs to VMe of any particular sub-graph, then it selects any non-CC node as a relay and non-DS node as a destination node. On the other hand, if the neighbor finder node belongs to VLo of any particular sub-graph, then it selects any non-DS node as a relay, MS as a destination node and forwards data cooperatively.
Now, let us consider a special case of a node which does not find its neighbors. How will it communicate? Well, the chances of the occurrence of this special case are very rare due to two reasons: (i) nodes are densely deployed; and (ii) all the nodes uniformly consume energy. However, near the end of network lifetime, if this situation arises then we handle it via two approaches; (i) if the node is within the communication range of the mobile sink then it directly communicates with it; and (ii) if the node is not within the communication range of the mobile sink, then it remains disconnected from the network and is considered as dead.
5. DEADS: The Proposed Scheme
Detailed discussion of the proposed protocol (DEADS) is given in the following subsection. Data sensing and routing example explains the selection of relay and destination nodes in a sub-graph.
5.1. Data Sensing and Routing
Let us consider a particular sub-graph as shown in Figure 5 to describe the construction of DS. In this example, depth and energy aware DS construction for a particular sub-graph is shown. For any vertex a, we represent its neighbor set as; N(a) = b ∊ V | a, b ∊ A where b ∊ n (n represents total number of nodes in a network).
Initially, each source node finds the number of its one-hop neighbors and selects dth on its basis. dth selection process in shown in Algorithm 1. Network lifetime is represented in terms of seconds. dth recalculation is performed at regular intervals (120 s).
Once a node becomes aware of its dth, it divides its neighbor set into two distinct sets (Noutdth and Nindth) as shown by the given expressions. In this sub-graph, eligible DS nodes are Noutdth and the eligible CC nodes are Nindth. For example, node a has nodes h, i, j, q, r and s within its transmission range. After finding its dth node a divides its neighbor set into two sets, finds CC and DS nodes by following rules 6 to 9 and perform cooperative routing. Node b, c, d, e, f and g follow the same procedure as followed by node a. Whereas, all the non-CC and non-DS nodes forward data by following rule 10.
N(a) = h, i, j, q, r, s, Nindth(a) = h, i, j, Noutdth(a) = q, r, s,
N(b) = i, j, k, r, s, t, Nindth(b) = r, e, h, i, Noutdth(b) = r, s, t,
N(c) = j, k, i, l, s, t, u, v, Nindth(c) = j, k, i, l, Noutdth(c) = s, t, u, v,
N(d) = k, l, m, t, u, v, Nindth(d) = k, l, m, Noutdth(d) = t, u, v,
N(e) = l, m, n, w, x, y, Nindth(e) = l, m, n, Noutdth(e) = w, x, y,
N(f) = m, n, o, w, x, y, z, Nindth(f) = m, n, o, Noutdth(f) = w, x, y, z,
N(g) = n, p, o, x, y, z, Nindth(g) = p, n, o, Noutdth(g) = x, y, z,
| Algorithm 1 Depth Threshold Selection |
| to ← predefined time interval in seconds |
| Tmax ← Network lifetime in seconds |
| N ← Number of a node's neighbors (N1 > N2) |
| Dth ← Depth threshold |
| Dth1, Dth2, Dth3 ← Optimal values of depth threshold (Dth1 > Dth2 > Dth3) |
| for T = 1 : to : Tmax do |
| if N ≥ N1 then |
| Dth = Dth1 |
| else if N1 > N ≥ N2 then |
| Dth =Dth2 |
| else if N < N2 then |
| Dth = Dth3 |
| end if |
| end for |
Traditional routing schemes [3,4,6] consume surplus energy due to transmission of redundant data and retransmission of critical data. We exploit threshold based data sensing in which data is transmitted only when certain predefined thresholds are met. Threshold values depend on the required application. Algorithm 2 describes data sensing and routing procedure. After nodes become aware of their neighbors, they start sensing the specified environmental attribute and forward the sensed data by using cooperative routing.
| Algorithm 2 Data Sensing and Transmission |
| S ← Sensed attribute |
| Hth ← Hard threshold |
| Sth ← Soft threshold |
| P ← Data packet |
| Re ← Residual energy |
| F ← Flag |
| if S ≥ Hth AND Re > 0 then |
| send P |
| set F = 1 |
| else if Sth ≤ S < Hth AND Re > 0 then |
| send P |
| set F = 0 |
| else |
| no transmission |
| end if |
According to rule 6 (Equation (8)), DS is formed and by utilizing SPDS given in rule 7 (Equations (9), (10) and (11)) each node selects an appropriate destination node that belongs to the DS nodes. Similarly, according to rule 8 (Equation (12)), CC set is formed and by utilizing rule 9 (Equations (13), (14) and (15)) each node selects an appropriate relay node that belongs to the CC nodes. CC, non-CC, DS and non-DS nodes also forward their data by utilizing rule 10 (Equations (16), (17), (18) and (19)). In this way, the most optimal destination and relay nodes are selected cooperative routing as shown in Figure 5. DS nodes and non-DS destination nodes implement MRC on received copies of the data and forward it to MS in its vicinity.
In order to indicate the severity of sensed attribute, flag is introduced. At the on-shore data center, the range of the sensed value can be interpreted just by viewing the flag field. For example, if the sensed attribute is temperature, then “1” indicates that the temperature is very high and appropriate measures must be readily adopted whereas “0” indicates that temperature is high but within an acceptable limit. We have implemented threshold based routing (reactive routing) to conserve network energy. In this type of routing, data is transmitted if the thresholds are met. On the other hand, if data transmission is based on energy then all the nodes will be transmitting all the time (till they are alive) whether it is critical data or not. In this way, relatively more energy will be consumed as compared to the threshold based data transmissions.
5.2. Sink Mobility
Conventional UWSN models assume static sink(s), usually present at the surface of water. The sensor nodes forward their data to the sink(s) via multi-hopping. Due to multi-hop communication, the chances of data being corrupted due to link impairments were high. In order to fix this drawback, we use mobile sink in UWSNs. These mobile sinks (also called mobile nodes) move on pre-defined paths and collect data from sensor nodes which are static. In this way, multi-hop communication is significantly reduced. On the other hand, rules are related to the sensor nodes to select their respective relay and destination nodes for cooperative routing. Mobile sinks move on the predefined path, and stop at sojourn locations at every predefined lap of time and collect data from DS nodes in their vicinity. Thus, the idea is to provide alternate paths via relay nodes for assuring transmission to the sink. The mobility patterns are discussed in detail in the following subsections.
5.2.1. Linear Mobility Pattern
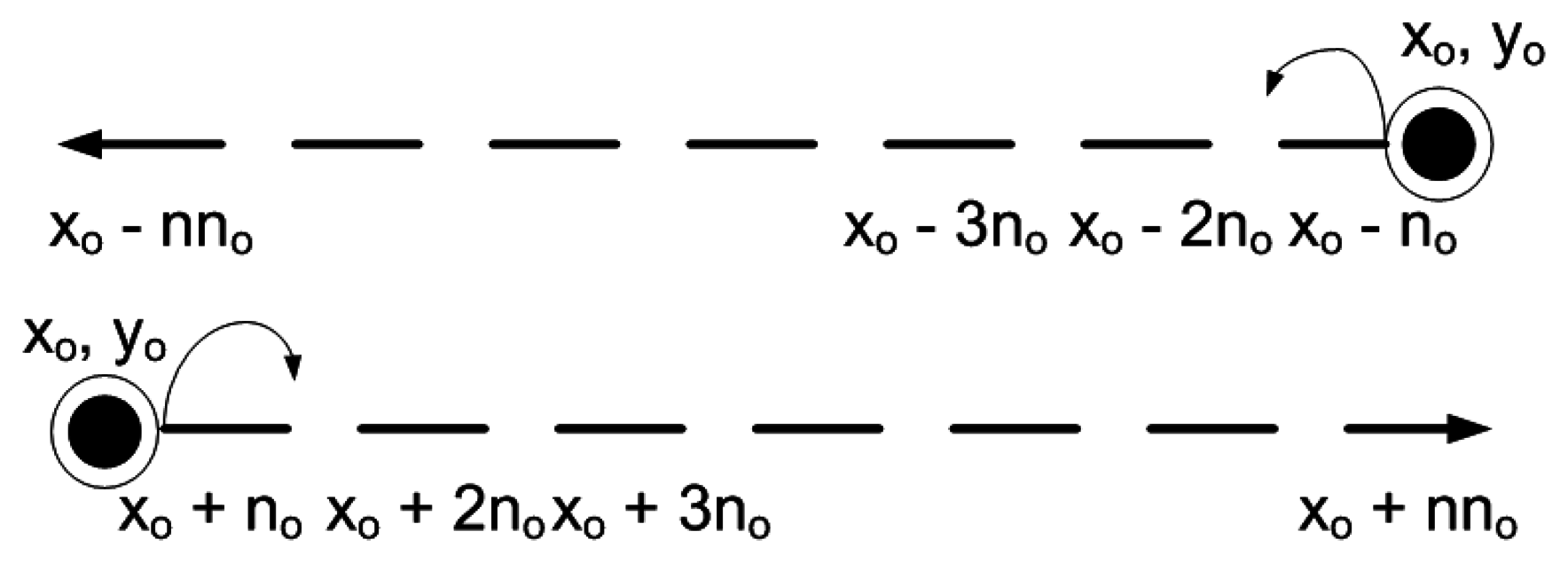
MSs follow a horizontally varying linear mobility pattern. MSs are present at different depths (yo) that remain same throughout the network lifetime. They move either leftwards or rightwards to cover the entire network. MSs change their position after predefined time interval. New position of MSs after a predefined time interval is represented as:
5.2.2. Elliptical Mobility Pattern
Each MS follow an elliptical mobility pattern (with vertical major-axis) represented by equation:
MSs move either Clock-Wise (CW) or Counter Clock-Wise (CCW) to cover the entire network. MSs change their position after regular time interval. New position of MSs represented by their x and y dimensions is given by:
Figure 8 shows the elliptical mobility path followed by each MS. xo and yo represent the center coordinates of each elliptical path which are the same for each ellipse. a and b represent semi-major and semi-minor axis of each elliptical pattern, where; a = 2b. Values of a and b are different for each elliptical path. θ represents the angle which is varied for clock-wise or counter clock-wise movement. After each predefined time interval, θ is incremented or decremented by a certain value for counter clock-wise or clock-wise movement of MSs. Value of θ can be adjusted according to the network requirements. Figure 9 shows data routing in the network in which MSs follow an elliptical mobility pattern. Data is routed from high depth to low depth region according to the rules defined in Section 4. All the nodes find dth, find appropriate CC or R, DS or D nodes and then forward data by using cooperative manner. Nodes forward data by using either DEADS-SRC or DEADS-MRC. As shown in Figure 9, node D and F are forwarding data towards the preselected next-hop (DS or D) node via MRC, whereas, node E forwards data directly towards MS via SRC.
6. Simulation Results and Discussions
We validate and evaluate our proposed scheme via simulations. We compare DEADS-SRC and DEADS-MRC with existing depth-based routing protocols; DBR, EEDBR, CoDBR and iAMCTD. The selected existing routing protocols have assumed 225 nodes. Thus, for the sake of fair comparison, we have also assumed the same number of nodes. Thus, the 225 sensor nodes are randomly deployed in underwater area of 500 m × 500 m × 500 m. Four MSs are deployed under water at different depths and they are following linear and elliptical mobility patterns. Each sensor node is equipped with an initial energy of 5 Joules and is having a fixed transmission range of 100 m. Size of data packet and control packet is 200 byte and 8 byte respectively. LinkQuest UWM1000 [20] acoustic modem is used having 10 kbps bit rate. Power consumption of a node in transmitting, receiving and in idle modes is 2 W, 0.1 W and 10 mW, respectively. In iAMCTD, there are 4 static sinks and 4 courier nodes for data reception, however, in the proposed protocol only 4 MSs are present. We excluded 4 static sinks present in iAMCTD in order to make it comparable with our proposed protocol. Due to water currents, the sensor nodes exhibit slight horizontal drift but their depth remains unchanged. Moreover, the routing protocol only takes depth of nodes into consideration that is why we assume static nodes. On the other hand, mobile sinks follow predefined elliptical and horizontal trajectories. We also assume the same underlying MAC protocol as in DBR [3], which uses the MAC protocol used in [21]. This, MAC protocol is based on CSMA. Whenever, a node has packets to send, it senses the channel, and then broadcasts the packet(s) if free channel is found. In case of busy channel, it uses a back-off algorithm (with 4 maximum back offs) to contend the channel. The data rate is set to 500 kbps, and the propagation speed of acoustic signals is set 1500 m/s.
DBR, EEDBR and CoDBR are proactive routing (continuous data routing) protocols, whereas, iAMCTD and DEADS are reactive routing (data routing occurs only when certain thresholds are met) protocols. An analysis of the proposed and existing protocols with respect to different parameters is given in Table 1. DBR and CoDBR consider depth, EEDBR considers depth and residual energy and iAMCTD considers link's state in terms of SNR, depth and residual energy of the forwarding nodes as an ultimate forwarding node determining factor. Whereas, in DEADS, depth and residual energy of the forwarding nodes are considered as forwarding node determining factor. To evaluate the performance of DEADS following evaluation metrics are considered:
Network lifetime: Network lifetime is the duration up till which all nodes in the network run out of energy. At any time instant, alive nodes represent the number of nodes which have sufficient residual energy for data transmission.
Residual energy: It is the total unexpended energy possessed by the network per time instant.
Throughput: It is the total number of data packets received at sink per unit time.
Packet drop: It shows the number of dropped packets out of total number of packets generated by nodes.
Packet Acceptance Ratio (PAR): It is defined as the ratio of total number of packets received at sink to the total number of packets sent to the sink at regular time interval.
As shown in Figure 10, in DBR, EEDBR and CoDBR, node density decreases sharply with time. The instability period is better in DBR as compared to EEDBR as there is a gradual increase in energy consumption. When network becomes sparse, number of neighbors decreases quickly which causes network instability. In DBR and CoDBR, low-depth nodes die at an earlier stage due to huge data forwarding and constant dth. DBR and CoDBR neglects both residual energy of nodes as well as link state in terms of SNR, whereas, EEDBR neglects link state which badly affects network throughput of these protocols. Number of dead nodes sharply increases with time in EEDBR as there is high load on high energy nodes because of considering residual energy as a routing metric. In CoDBR, network density decreases at the fastest rate because of cooperative routing being performed. Cooperative routing involves high energy consumption because of multiple transmissions and receptions of same data packet. Stability period (time up till which all nodes in the network are alive) of iAMCTD is highest because of optimal dth selection. Also, in iAMCTD, only source node transmits data to its next hop neighbor which conserves energy and results in improved stability period. Although due to implementation of rule 4, dth selection is more optimized in DEADS-SRC and DEADS-MRC as it requires only one-hop neighbor information instead of complete network density information, however, data is transmitted from source node as well as relay node(s) to the next hop. So, it is consuming 2 (SRC) to 3 (MRC) times more transmission and reception energy than iAMCTD due to which stability period is compromised. This shows the tradeoff between network stability period and reliability.
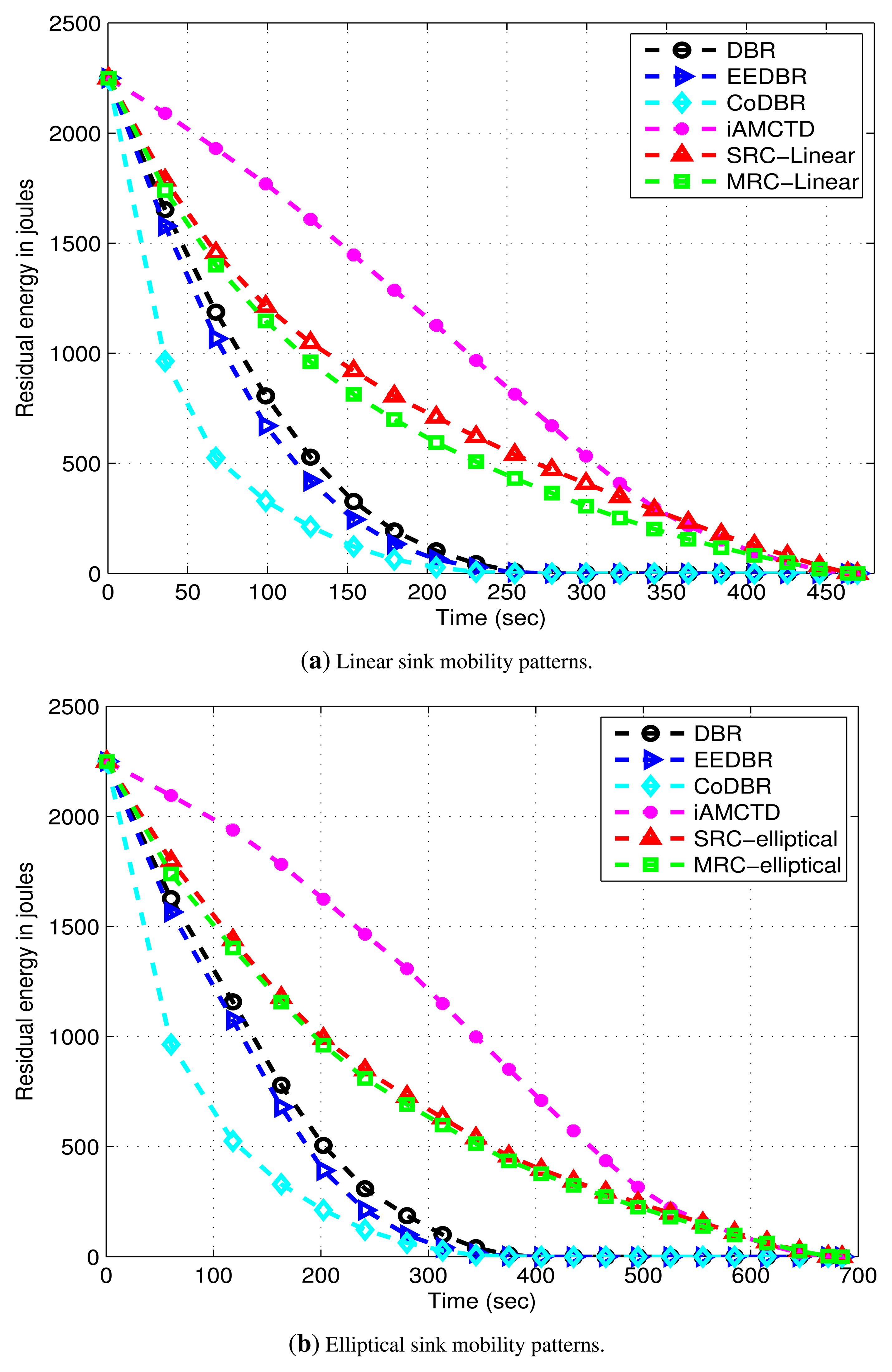
DBR shows better energy management than EEDBR as shown in Figure 11. In DBR, network residual energy steadily decreases as total number of eligible neighbors drops off with network density. Energy consumption of EEDBR is the highest among all other protocols due to frequent selection of high energy nodes. Moreover, higher energy consumption in DBR, EEDBR and CoDBR is because of reactive routing being performed in these protocols. Although CoDBR attains data reliability and high throughput, however, energy consumption is highest because of cooperative routing in the network as well as flooding resulting from fixed dth. iAMCTD attains a balanced residual energy throughout the network lifetime due to proper forwarder selection, optimal mobility patterns of courier nodes and maintenance of uniform network density. In DEADS-SRC and DEADS-MRC, high energy consumption is involved as compared to iAMCTD. This high energy consumption is because of cooperative routing. In the proposed protocol, as the network starts, nodes become active and start the sensing and transmission process. Initially all nodes are alive, each node finds appropriate relay and destination nodes and performs transmission and reception process due to which energy consumption is increased. After certain time, rate at which nodes become dead increases and energy consumption decreases. The reason behind this decreased energy consumption with increasing time is that nodes fail to find optimal relay nodes because of reduction in network density. As a result, chances of cooperative routing being performed by any source node are reduced which reduces energy consumption and most of the data is directly transmitted to the MSs or next hop node only. The proposed scheme achieves a much better energy management in spite of performing cooperative routing which involves high energy consumption.
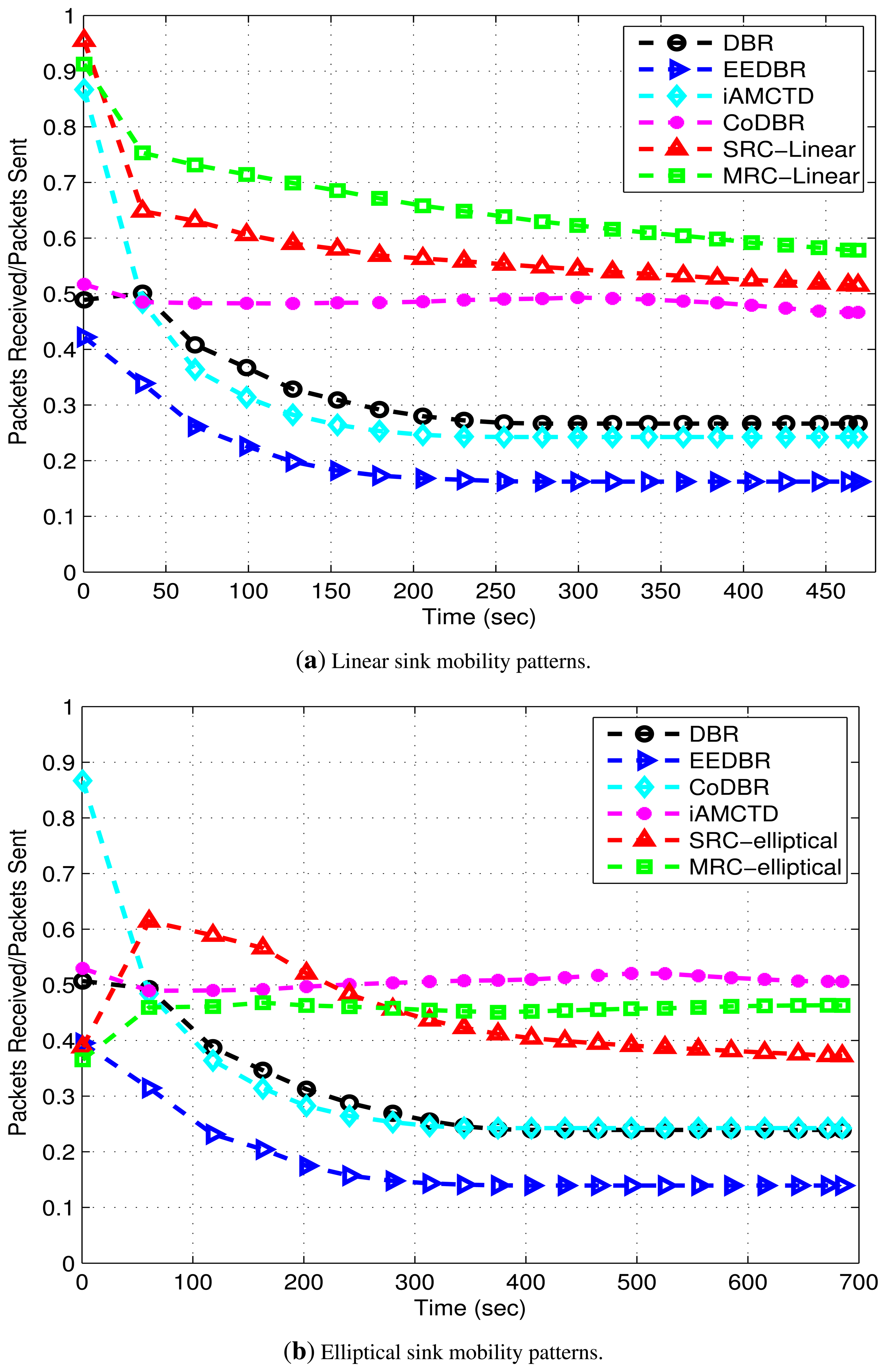
Figure 12 shows throughput of proposed and compared protocols. Throughput of DBR and EEDBR is almost constant after 100 s. This constant value is due to quick fall in network density. As network density decreases, nodes fail to find optimal forwarders for data forwarding due to which throughput attains a constant value. This behavior is unsuitable for both delay-tolerant and delay-sensitive applications. CoDBR attains high throughput due to cooperatively forwarding the data packets. Throughput of iAMCTD, DEADS-SRC and DEADS-MRC demonstrate the amount of threshold-optimized data obtained from reactive networks. In these protocols, unnecessary data transmission is avoided. In iAMCTD, throughput is high because of the selection of most optimal forwarder. This optimal forwarder is the one that possesses highest residual energy, least depth and depth difference (between source and next-hop node) and best link state at any particular time instant. Hence probability of data packet being corrupted by link impairments are reduced and high throughput is achieved. The proposed model for data routing attains optimal results with linear sink mobility as compared to elliptical sink mobility. Although, in DEADS-SRC and DEADS-MRC, only forwarder node's depth and residual energy are considered as selection parameters represented by Equations (11) and (15); however, improved results are achieved as compared to iAMCTD due to implementation of cooperative routing. If data received via direct route (source to DS node) is corrupted, it can be received successfully via an alternate route (source to CC to DS node). Along with this, implementation of MRC (diversity combining technique) at DS nodes further improves SNR of received data which results in high throughput. The highest throughput is achieved DEADS-SRC and DEADS-MRC with linear mobility pattern of MSs. Hence, this particular mathematical model performs the best with linear mobility pattern of MSs.
Figure 13 show packet drop. High packet drop of DBR, EEDBR and iAMCTD is due to the availability of single link with poor link state most of the time. In CoDBR, packet drop is lesser because of cooperative routing. Although, iAMCTD considers link state of potential forwarder node before their selection, even then, the presence of redundant links as well as implementation of MRC (diversity combining technique) gives improved results and makes DEADS-SRC and DEADS-MRC more reliable. In CoDBR, DEADS-SRC and DEADS-MRC, packets are dropped only when no link (direct link to the DS node or via CC to DS node) is available for data forwarding or SNR of combined signal received at DS node (source to DS node, source to CC to DS node) is below an acceptable limit. In CoDBR, multiple transmissions of same data packet are performed before it is received by static sink. Effect of link impairments is high because of these multiple transmissions and as a result packet drop is high. Packet drop is higher in DEADS-SRC and DEADS-MRC with elliptical mobility pattern as compared to linear mobility pattern of MSs. This is because the proposed model is not optimized for elliptical mobility pattern. Whenever the condition(s) specified by Hth and Sth is met, packets are generated by nodes. Sink only accepts those packets that possess an acceptable SNR value and drops the remaining packets. In DEADS-SRC and DEADS-MRC with elliptical mobility pattern of MSs, data packets have to traverse multiple hops in order to get received at sink because of which their probability of being erroneous is high which results in packet drop. On the other hand, MSs are available for data reception mostly at one hop distance in linear sink mobility scenario because of which packet drop is reduced. Table 2 shows that packet drop rate of DEADS-SRC and DEADS-MRC is lowest with linear mobility pattern of MSs.
PAR is shown in Figure 14. DBR and EEDBR have the lowest PAR as the number of packets received at sink are less due to single link having poor link state most of the time. iAMCTD shows higher PAR than DBR and EEDBR as it selects forwarder nodes on the basis of their respective link's SNR. This results in high throughput and increased PAR. Initially CoDBR attains higher PAR as compared to DBR, EEDBR and iAMCTD which later at decreases as throughput decreases. PAR is higher in DEADS-SRC and DEADS-MRC with linear mobility pattern of MSs as the number of packets received at sink in this scenario is high and packet drop is low.
Table 2 shows the improvement attained by our proposed protocol with respect to network lifetime, throughput and packet drop. Zero indicates that both protocols have same value for that specific evaluation metric. Negative value indicates reduced value of a particular metric with respect to compared protocol. Network lifetime of the proposed scheme is same as iAMCTD but outperforms DBR and EEDBR. Highest throughput and lowest packet drop is achieved by DEADS-SRC and DEADS-MRC with linear mobility pattern of MSs.
6.1. Performance Tradeoffs Made by DEADS
DEADS is a reactive routing protocol in which data is transmitted only when certain predefined thresholds are met. Hence it is not suitable for applications where continuous data monitoring and reception are required.
DEADS achieves improved network lifetime by introducing sink mobility in the network. In DEADS, cooperative routing is performed and high throughput is achieved at the cost of increased energy consumption and control overhead. Two to three times more energy consumption is involved when cooperative routing is performed in a network as shown in Figure 11. Along with this, control packet exchange for selection of cooperative partner nodes increases control overhead.
An optimized value of dth in accordance with Equation (4) is attained at the cost of control packet exchange. Nodes require their one-hop neighbor information in order to select their dth.
There is a tradeoff between the network's stability period and data reliability. The stability period is compromised in order to attain reliable data transfer as shown in Figure 10. Data reliability refers to the authenticity of received data and it is affected by the damage caused by link impairments. The greater the effect of link impairments on the received data, the less reliable it is and increased are the chances of it being dropped by receiving node and vice versa. Whereas, the link state varies from node to node. Higher energy consumption causes nodes to die at the start of the network compromising stability period, however, because of transmission via alternate paths data reliability is achieved.
Reliable data transmission results in high throughput, as shown in Figure 12 because chances of successful data reception at sink are increased. Hence, there is a tradeoff between throughput and energy consumption.
Reliable data transfer is attained at the cost of increased processing overhead (in terms of MRC and AF) and increased delay. Data is transmitted from source to relay and destination node. Relay node after performing AF at the received data forwards it to destination node. Destination node performs MRC at the received copies, selects appropriate relay and destination node and then forwards the data. In all this processing, a certain overhead is involved. Delay is also introduced because of which the proposed protocol is not suitable for delay sensitive applications.
DEADS achieves reduced packet drop as shown in Figure 13 at the cost of multiple transmissions. Greater number of transmissions increase reliability at the cost of extra energy consumption. Tradeoffs are shown in Table 3.
7. Conclusions
In this paper, we proposed a DS based cooperative routing algorithm along with sink mobility for UWSNs. The proposed algorithm operates in three phases: the neighbor selection phase, DS and CC set formation phase, and threshold based data sensing and routing phase. During the neighbor selection phase, nodes select dth, find neighbors, and attain their depth and residual energy information. During the DS and CC set formation phase, source nodes utilize information attained in previous phase and select their respective DS and CC nodes for cooperative routing. In the threshold based data sensing and routing phase, source nodes sense data on the basis of pre-defined threshold value and forward it to their cooperative partner nodes. We evaluated the performance of our proposed protocol by comparing it with DBR, EEDBR, and iAMCTD in terms of network lifetime, throughput, PAR and energy consumption. Results show better performance of our proposed work as compared to the existing works in terms of the selected performance metrics.
Acknowledgements
The authors would like to extend their sincere appreciation to the Deanship of Scientific Research at King Saud University for funding this Research group No. 037-1435-RG.
Author Contributions
All authors have equal contributions for the manuscript.
Conflicts of Interest
The author declares no conflict of interest.
References
- Al-Dharrab, S.; Ibrahim, S. Cooperative Communication over Underwater Acoustic Channels. Ph.D. Thesis, University of Waterloo, Waterloo, ON, 2013. [Google Scholar]
- Jannati, M.J.; Aref, A.D.; Vakily, V.T. Implementation of cooperative virtual MISO communication in underwater acoustic wireless sensor networks. IJCSI 2011, 8, 124–130. [Google Scholar]
- Yan, H.; Shi, Z.J.; Cui, J.H. DBR: Depth-Based routing for underwater sensor networks. Proceedings of the 7th International IFIP-TC6 Networking Conference on Ad Hoc and Sensor Networks, Wireless Networks, Next Generation Internet (NETWORKING '08), Singapore, 5–9 May 2008; pp. 72–86.
- Wahid, A.; Lee, S.; Jeong, H.; Kim, D. EEDBR: Energy-Efficient Depth-Based Routing protocol for underwater wireless sensor networks. Adv. Comput. Sci. Inf. Technol. 2011, 195, 223–234. [Google Scholar]
- Javaid, N.; Jafri, M. R.; Khan, Z. A.; Qasim, U.; Alghamdi, T. A.; Ali, M. iAMCTD: Improved Adaptive Mobility of Courier Nodes in Threshold-Optimized DBR Protocol for Underwater Wireless Sensor Networks. IJDSN 2014. [Google Scholar] [CrossRef]
- Nasir, H.; Javaid, N.; Ashraf, H.; Manzoor, S.; Khan, Z.A.; Qasim, U.; Sher, M. CoDBR: Cooperative Depth Based Routing for Underwater Wireless Sensor Networks. Proceedings of the Ninth International Conference on Broadband and Wireless Computing, Communication and Applications (BWCCA), Guangdong, China, 8–10 November 2014; pp. 52–57.
- Al-Bzoor, M.; Zhu, Y.; Liu, J.; Ammar, R.; Cui, J.-H.; Rajasekaran, S. An adaptive surface sink redeployment strategy for Underwater Sensor Networks. Proceedings of the IEEE ISCC, Split, Croatia, 7–10 July 2013. [CrossRef]
- Umar, A.; Akbar, M.; Ahmed, S.; Javaid, N.; Khan, Z.A.; Qasim, U. Underwater Wireless Sensor Network's Performance Enhancement with Cooperative Routing and Sink Mobility. Proceedings of the Ninth International Conference on Broadband and Wireless Computing, Communication and Applications (BWCCA), Guangdong, China, 8–10 November 2014; pp. 26–33.
- Luo, Y.; Pu, L.; Peng, Z.; Zhou, Z.; Cui, J.H. CT-MAC: A MAC protocol for underwater MIMO based network uplink communications. Proceedings of the Seventh ACM International Conference on Underwater Networks and Systems (WUWNet '12), Los Angeles, CA, USA, 5–6 November 2012.
- Wang, P.; Zhang, L.; Li, V.O.K. Asynchronous cooperative transmission for three-dimensional underwater acoustic networks. IET Commun. 2013, 7, 286–294. [Google Scholar]
- Luo, Y.; Pu, L.; Peng, Z.; Zhou, Z.; Cui, J.; Zhang, Z. Effective Relay Selection for Underwater Cooperative Acoustic Networks. Proceedings of the IEEE 10th International Conference on Mobile Ad-Hoc and Sensor Systems (MASS), Hangzhou, China, 14–16 October 2013; pp. 104–112.
- Tan, D.D.; Le, T.T.; Kim, D.S. Distributed cooperative transmission for underwater acoustic sensor networks. Proceedings of the 2003 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Shanghai, China, 7–10 April 2013; pp. 205–210.
- Ruoyu, S.; Venkatesan, R.; Cheng, L. A new node coordination scheme for data gathering in underwater acoustic sensor networks using autonomous underwater vehicle. Proceedings of the 2003 IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013; pp. 4370–4374.
- Wang, J.; Li, D.; Zhou, M.; Ghosal, D. Data Collection with Multiple Mobile Actors in Underwater Sensor Networks. Proceedings of the 28th International Conference on Distributed Computing Systems Workshops, ICDCS '08, Beijing, China, 17–20 June 2008; pp. 216–221.
- Shen, S.; Zhan, A.; Yang, P.; Chen, G. Exploiting Sink Mobility to Maximize Lifetime in 3D Underwater Sensor Networks. Proceedings of the 2010 IEEE International Conference on Communications (ICC), Cape Town, South Afica, 23–27 May 2010; pp. 1–5.
- Luo, J.; Panchard, J.; Piorkowski, M. Mobiroute: Routing towards a mobile sink for improving lifetime in sensor networks. Proceedings of the Second IEEE International ConferenceDistributed Computing in Sensor Systems, San Francisco, CA, USA, 8–20 June 2006; pp. 480–497.
- Yoon, S.; Azad, A.K.; Oh, H.; Kim, S. AURP: An AUV-aided underwater routing protocol for underwater acoustic sensor networks. Sensors 2012, 12, 1827–1845. [Google Scholar]
- Ahmad, A.; Wahid, A.; Kim, D. AEERP: AUV aided energy efficient routing protocol for underwater acoustic sensor network. Proceedings of the 8th ACM Workshop on Performance Monitoring and Measurement of Heterogeneous Wireless and Wired Networks (PM2HW2N '13), Barcelona, Spain, 03–08 November 2013; pp. 53–60.
- El-Darymli, K. Amplify-and-Forward cooperative relaying for a linear Wireless Sensor Network. Proceedings of the IEEE International Conference on Systems Man and Cybernetics (SMC), Istanbul, Turkey, 10–13 October 2010; pp. 106–112.
- Wills, J.; Ye, W.; Heidemann, J. Low-Power acoustic modem for dense underwater sensor networks. Proceedings of the 1st ACM International Workshop on Underwater Networks, Los Angeles, CA, USA, 29 September 2006; pp. 79–85.
- Xie, P.; Cui, J.-H.; Lao, L. Vbf: Vector-Based Forwarding Protocol for Underwater Sensor Networks. Proceedings of the IFIP Networking, Coimbra, Portugal, 15–19 May 2006.






| Protocol | Depth Threshold (dth) | Sink Mobility | Routing | Parameter for Forwarder Node Selection |
|---|---|---|---|---|
| DBR | Fixed | Static sinks (on water surface) | Multi-hop routing | Depth |
| EEDBR | Fixed | Static sinks (on water surface) | Multi-hop routing | Depth and residual energy |
| CoDBR | Fixed | Static sinks (on water surface) | Cooperative routing | Depth |
| iAMCTD | Variable (on basis of network density information) | Mobile courier nodes | Multi-hop routing | Depth, residual energy and link's SNR |
| DEADS (proposed) | Variable (on basis of one-hop neighbor information) | Mobile sinks | Cooperative routing | Depth and residual energy |
| Evaluation Metric | Protocol | DEADS-SRC | DEADS-MRC | ||
|---|---|---|---|---|---|
| Linear | Elliptical | Linear | Elliptical | ||
| Network lifetime | DBR | 40% | 45% | 40% | 45% |
| EEDBR | 40% | 45% | 40% | 45% | |
| CoDBR | 40% | 45% | 40% | 45% | |
| iAMCTD | 0 | 0 | 0 | 0 | |
| Throughput | DBR | 76% | 69% | 75% | 71% |
| EEDBR | 76% | 69% | 75% | 71% | |
| CoDBR | 63% | 51% | 60% | 55% | |
| iAMCTD | 6.4% | −23% | −1% | −13% | |
| Packet drop | DBR | −41% | −29% | −51% | −31% |
| EEDBR | −37.5% | −25% | −48% | −27% | |
| CoDBR | −15% | 1.5% | −30% | −1.5% | |
| iAMCTD | −35% | −22% | −46% | −24% | |
| DEADS | Modification over Existing Protocols | Advances Achieved | Price to Pay |
|---|---|---|---|
| DEADS-SRC | Single relay cooperative routing along with sink mobility | High throughput (Figure 12), reduced packet drop (Figure 13), optimized dth (rule 4) | High energy consumption (Figure 11), stability period compromised (Figure 10), control and processing overhead |
| DEADS-MRC | Multiple relay cooperative routing along with sink mobility | High throughput (Figure 12), reduced packet drop (Figure 13), optimized dth (rule 4) | High energy consumption (Figure 11), stability period compromised (Figure 10), control and processing overhead |
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Umar, A.; Javaid, N.; Ahmad, A.; Khan, Z.A.; Qasim, U.; Alrajeh, N.; Hayat, A. DEADS: Depth and Energy Aware Dominating Set Based Algorithm for Cooperative Routing along with Sink Mobility in Underwater WSNs. Sensors 2015, 15, 14458-14486. https://doi.org/10.3390/s150614458
Umar A, Javaid N, Ahmad A, Khan ZA, Qasim U, Alrajeh N, Hayat A. DEADS: Depth and Energy Aware Dominating Set Based Algorithm for Cooperative Routing along with Sink Mobility in Underwater WSNs. Sensors. 2015; 15(6):14458-14486. https://doi.org/10.3390/s150614458
Chicago/Turabian StyleUmar, Amara, Nadeem Javaid, Ashfaq Ahmad, Zahoor Ali Khan, Umar Qasim, Nabil Alrajeh, and Amir Hayat. 2015. "DEADS: Depth and Energy Aware Dominating Set Based Algorithm for Cooperative Routing along with Sink Mobility in Underwater WSNs" Sensors 15, no. 6: 14458-14486. https://doi.org/10.3390/s150614458
APA StyleUmar, A., Javaid, N., Ahmad, A., Khan, Z. A., Qasim, U., Alrajeh, N., & Hayat, A. (2015). DEADS: Depth and Energy Aware Dominating Set Based Algorithm for Cooperative Routing along with Sink Mobility in Underwater WSNs. Sensors, 15(6), 14458-14486. https://doi.org/10.3390/s150614458







