1. Introduction
The phenomenon whereby data are acquired from several network-connected sensors for the purposes of sense-making and intelligent decision-making in smart systems is drastically accelerating. It is expected that there will be increasing numbers of large-scale deployments of devices that are instrumented with multi-modal sensors in the near future (e.g., in cities, transportation, museums, energy systems, etc.). These sensor devices generally have small form factors and possess limited processing and storage capabilities. In addition, they are typically powered by limited battery supplies and/or energy-harvesting sources.
An essential component for the realization of these wireless sensing devices is the data transport service,
i.e., the ‘routing protocol’, to carry data from the sensor devices to the back-end servers via one or more (Internet-enabled) gateways, for further processing and analysis. Due to the energy constraints of the nodes and the limited transmission range, the IEEE 802.15.4 standard [
1] for low-rate wireless personal area networks (LR-WPANs) is often used for inter-nodal communications. As the transmission range of such a radio is typically limited (often in the range of tens of meters), nodes that are deployed over large spatial regions are expected to communicate to the gateway(s) via multiple hops.
Due to these aspects and the few resources of the sensor nodes, providing efficient and reliable routing protocols is an important and challenging problem. For years now, several routing protocols for wireless sensor networks (WSN) have been standardized and developed [
2,
3,
4,
5,
6,
7,
8,
9,
10,
11]. While many efforts have been produced for their development, integration and performance evaluation, the conformance testing of their implementations has been somehow neglected.
The conformance testing of routing protocols is crucial, as a data transport service that does not behave in its expected manner can have detrimental impacts on data collection and severely impact the overall quality, as well as the usefulness of the system. Furthermore, in large-scale sensor systems, a single bug fix can be an extremely time-consuming and labor intensive process, especially if the nodes are placed in inaccessible locations across varying spatial locations.
However, though the conformance testing of these protocols is crucial to the reliability of the systems, there are paradoxically very few works. Indeed, the major ones are mostly dedicated to their performance analysis, application and security studied through simulation or emulation relying on non-formal models [
12,
13,
14,
15,
16,
17]. We propose in this paper a formal syntax and semantics to express the requirements of WSN routing protocols and to passively test them on real execution traces. These syntax and semantics do not need to be inevitably used on top of any protocol standard. We herein model and test common WSN requirements, as well as specific ones designed from a novel non-standardized routing protocol. We show that our approach is helpful from the very first stage of the system development life cycle and is complementary to the normalization phase, as well.
There are two main ways for testing the conformance of a protocol, either in an active or passive way. While the active ones require a simulation of the implementation under test (IUT) and an important testing architecture, the passive ones are based on the observation of input and output events of an IUT at run-time. Basically, passive testing techniques are applied whenever the state of an IUT cannot be controlled by means of test sequences, either because access to the interfaces of the system is unavailable or a reset of the IUT is undesired. This is specifically the case with the WSN where the topology is dynamic and the testing interfaces not always available. Moreover, in actively testing WSN protocols, we often deal with no direct access, wide fluctuations in the wireless channel and a high dependence on prevailing environmental characteristics.
In this context, some passive techniques have been proposed to test the conformance of protocols in wired systems. These passive testing approaches are based on the record of the observation during run-time and its comparison with the expected protocol behavior defined by either a formal model or as a set of formally-specified properties obtained from the requirements of the protocol [
18]. The observation is performed through a set of points of observation (PO) on monitored entities composing the system under test. The protocol messages observed in execution traces are generally modeled and analyzed through their control and data parts [
19]. These approaches are efficient, but are not suitable for wireless environments, like WSN and its own inherent constraints, as mentioned above. Although we already studied and tested wired networks with our formal testing approach [
20], we present in this paper an adaptation of this approach to passively test a routing protocol in wireless sensor-based smart systems. Common and specific WSN protocol properties are evaluated on collected execution traces to provide testing verdicts. We successfully assess our approach on an indoor testbed. As far as we know, this is the first work on formal passive testing of routing protocols in a WSN.
Our paper’s primary contributions are:
A logic-based approach for formally specifying some functional requirements of the WSN routing protocol. We provide an algorithm to evaluate these properties on protocol execution traces that are collected at run-time through PO set on the nodes.
With a real indoor testbed and the implementation of a new routing protocol and the implemented algorithm, we demonstrate the efficiency and suitability of our approach by providing relevant testing verdicts. The modeled requirements do not need to be compulsorily standardized, which helps the development life cycle processes.
The rest of this paper is organized as follows:
Section 2 discusses existing work in the literature. We describe the formal approach of our passive testing framework in
Section 3 and provide details of the sensor networking protocol to be tested in
Section 4.
Section 5 contains details of the experimental setup and evaluation results. We conclude our work in
Section 6.
2. Related Works
Although there exists many studies on protocol evaluation in WSNs, they mostly tackle their performance, application or security issues [
12,
13]. Very few works focus on the conformance testing of these protocols. In the following, we present the ones that inspired us and compare them.
In [
21], the authors study common functional testing approaches to tackle the security issues in wireless sensor networks. Since conformance testing techniques cannot assess the efficiency of the implementation of a security protocol (mainly because most of the security concepts are close to non-functional mechanisms), the authors propose to add randomness tests to conformance tests dedicated to the evaluation of security functions. One part of the SPINS protocols (security protocols for sensor networks) is chosen to illustrate their approach.
Like in the previous proposal, [
22] recently proposed a remote testing method by stating the design and development of test routers in WSN. For that purpose, a remote testing platform is developed and assessed. The authors tackle the bad environment in which nodes are intensively placed. They study the energy consumption and the dynamic change of the network topology. These inherent constraints often prevent the testers from meeting the tested protocol requirements. Still, with the same objectives, a formal testing approach is proposed in [
23]. A nodes’ self-similarity approach for testing wireless mobile
ad hoc networks (MANET) is presented. Formal specifications and emulations are applied through the Dynamic Source Routing (DSR) [
24] protocol to provide relevant verdicts about the test of one of its implementations.
We also got inspiration by [
25] in which real wireless sensor nodes are deployed to test, through virtualized emulated nodes, TCP and some functions of their own faulty routing protocol RMRP (Rime mesh routing protocol). A state model is defined and test suites generated and executed through their architecture based on an interesting generated dynamic topology. In recent papers [
26,
27], the authors provided a suitable open conformance test system for standard-based WSNs, dedicated to the protocol evolution and the various hardware interfaces of the sensor nodes. However, these approaches do not provide a way of modeling non-standardized requirements as we tackle in this work. In our work, we propose an approach to test the functional behaviors without using any formal specifications. Further, we do not claim to interact with the designers through any testing process, but just by receiving the expected protocol requirements.
Though interesting results have been obtained by the works mentioned above, the tests are mostly applied through active testing architectures. The tests are intrusive and need to generate important test suites. One of our challenges is to the contrary to avoid any interaction with the implementation. By passively testing the implementation protocols, we also do not need any testing scripts and the related specification stages. Moreover, we here work on a real testbed, avoiding the simulation or emulation drawbacks often met in these kind of studies.
Recently, interesting works on passive diagnostics in WSN have been presented. First, we may cite [
28] in which the authors propose a probabilistic diagnosis approach for inferring the root causes model of abnormal phenomena in wireless sensor networks through the passive observation of eventual symptoms. A light-weight packet-marking scheme is defined to collect relevant hints and the probabilistic inference model located at the sinks targets the expected hints. Second, [
29] proposes a passive observation and mining of relevant collected information to diagnose WSN performance failures. The authors’ technique deduces the root causes of failures by focusing on the relationships between the sensing data, the failures in the networks and a failure knowledge library. Furthermore, [
30] proposes passive distributed assertions (PDA) as a novel tool for identifying failure causes. It allows a programmer to assert certain predicates over a distributed node state, while minimizing interference with the sensor network. Finally, a combination of active and passive testing approaches is presented in [
31] for fault localization in WSN. In this work, the scope is different from ours. The faulty components are searched by optimal end-to-end test suites, whereas we test the conformance of the protocols without trying to point at the faulty entity, since the implementation of the tested protocol is our objective. However, the proposed passive observation and the data aggregation procedure are of high interest in the definition of our formal approach.
We got inspired by these above-mentioned approaches, even if they are applied to the diagnosis or fault localization of WSN. Indeed, their symptoms or failure signatures can be compared to our formal properties, although in our framework, a logic-based approach is used. Moreover, some correlation processes are commonly applied in passive testing techniques. Nevertheless, we do not need any inferred models and do not impact the nodes reliability by any active processes. Additionally, different from passive distributed assertions, which concentrate on verifying the program states, we focus on a different issue: testing the behavior of the system, whether it conforms to the specific requirements.
3. Formal Passive Testing Approach
3.1. Preliminaries
We here define the syntax allowing us to describe some functional properties of network protocols.
Definition 1. A message of a protocol P is any element .
For each , we add a real number , which represents the time when the message m is received or sent by the monitored entity. The data domains are defined as atomic or compound. Once given a network protocol P, a compound domain can be defined by the set of labels and data domains derived from the message format defined in the protocol specification/requirements.
Definition 2. A term is defined in Backus–Naur form (BNF) as , where c is a constant in some domain, x is a variable, l represents a label and is called a selector variable.
Definition 3. An atom is defined as the relations between terms, .
Definition 4. A clause is an expression of the form , where are atoms. The relations between atoms are stated by the definition of clauses.
Definition 5. A formula is defined by the BNF: , where ∃ and ∀ represent “it exists” and “for all”, respectively.
According to these definition, we define the syntax based on the basic unit term. The ¬ quantifier is newly introduced to formalize some specific condition in the WSN. In the following subsection, we introduce the semantics and algorithm used for our testing approach.
3.2. Semantics and Algorithm
The semantics used in our work is related to the traditional Apt–Van Emden–Kowalsky semantics for logic programs [
32], from which an extended version has been provided in order to deal with messages and trace temporal quantifiers.
Definition 6. A substitution θ is a finite set of bindings , where each is a term and is a variable, such that and if .
Given a formula
ϕ defined by using a set of clauses
K as we mentioned above, a satisfaction result ‘⊤’ (‘pass’), ‘⊥’ (‘fail’) or ‘?’ (‘inconclusive’) will be given for a particular trace
ρ. Using substitution
θ, we recursively evaluate the formula
ϕ (
i.e., protocol property) on the real protocol execution trace
ρ, coupled with a modification of SLD (selective linear definite-clause) resolution algorithm [
33] for the evaluation of Horn clauses.
The evaluation process is described as follows:
For every possible value
x in the trace, the following formula is used:
If the formula
is included in another formula, the result of evaluation is provided by:
The result “⊥” represents any violation that has been found. The evaluation of
is quite similar to the
, but it is looking for a “⊤” result.
The evaluation processes for
,
and
are the same as described before; we will not repeat them here. The interested readers can have a look at our previous work [
20,
34].
We also provide the evaluation algorithm in the following.
![Sensors 15 29250 i001]()
The algorithm starts by checking the existence of a trace
ρ and a requirement
ϕ. Then, if
ϕ contains subformulas, they will be sequentially tested by using recursive calls. For testing a formula
ϕ on a finite trace
ρ, the algorithm will firstly assign the values to substitution
θ from each message
m in the trace. Then, the obtained
will be used to compare with each atom in the formula
ϕ. If all of the atoms in
ϕ are satisfied, a truth value ‘⊤’ will be assigned, and the algorithm will stop to test the next message
m. Otherwise, any violation of the atoms will result in a truth value ‘⊥’, and the algorithm will immediately terminate the comparing process and stop to test the next message
m. The truth values ‘⊤’ and ‘⊥’ will be eventually transformed to the verdict ‘pass’, ‘fail’ or ‘inconclusive’ as the semantics defined in
Section 3. Finally, a final report will be provided when all of the sub-formulas of
ϕ are tested through the trace
ρ.
The complexity of the algorithm is decided by the number of quantifiers used in the formula being tested. In the worst case, the time complexity of our algorithm with k quantifiers is to analyze the trace, where n represents the number of messages in the trace. In the following section, we present a newly-designed routing protocol to be tested. It has been specified, developed and integrated in a real indoor testbed.
4. Protocol Description
We have designed our proprietary end-to-end networking stack for large-scale WSN deployments with modular components that are configurable, extensible, as well as plug-and-playable, depending on the sensing application requirements and the physical environment of the sensing region of interest. It is designed for scalability through the use of lightweight protocols that minimize both communication and storage overheads. Existing networking protocols are often designed in silo and, thus, unable to support our multi-faceted sensor network testbed requirements. In the following, we briefly describe its basics, the route establishment, the data transmission and the packet format.
The indoor testbed we use in this paper serves as an evaluation platform for our actual sensor-based smart system deployed in outdoor urban areas. As said before, our passive testing technique can be applied all along the development lifecycle, helping thus the normalization, as well as the deployment phase. Our outdoor sensor networks necessitate the use of multiple gateways in the network, so that timely and reliable data delivery can be achieved. Commercially available network protocols, such as ZigBee, are based on the
Ad hoc On-Demand Distance Vector (AODV) routing protocol [
35] and do not have inherent support for the use of multiple gateways in the network. The routing protocol in use is multi-hop and opportunistic in nature. It associates a metric called a gradient to each sensor towards the gateway of the network. According to prevailing link quality, a dynamic update of the routing gradients is performed.
4.1. Basics
A BEACON is periodically broadcast by each node (sensor and gateway) throughout its network lifetime and is used for:
During network initialization, each sensor node has a gradient value of infinity. The gateway then updates its gradient to be zero and sends this information together with its current sequence number, in its next BEACON. Upon receiving a non-infinite value of the gradient in a BEACON from a neighboring node , the sensor node updates its gradient (according to the selected metric) if the following conditions are satisfied: (i) the estimated link quality between and is above a pre-defined threshold T; and (ii) the gradient of is smaller than the gradient of .
When a sensor node has a DATA packet to forward to the gateway, the packet is broadcast into the wireless medium together with the gradient of . A neighboring node that receives the DATA packet from will send an acknowledgment(ACK) and help to forward the packet only if the gradient of is smaller than that of . The process is repeated along each hop until the gateway receives the DATA packet. It is thus possible for the gateway node to receive multiple copies of the DATA packet.
4.2. Route Establishment
At periodic intervals of 30 s, each node broadcasts a BEACON message to its one-hop neighbors for the purpose of neighbor discovery, topology maintenance, time synchronization and route discovery to the gateway. The BEACONs are used to compute running estimates of the link qualities between each node and its one-hop neighbors. This estimated link quality is subsequently used to determine the forwarding set from the node to the gateway.
Each sensor node is associated with a gradient (metric) towards the gateway node. The metric of an arbitrary node is denoted as . Generally, packets flow from nodes with higher gradients to nodes with lower gradients. In our testbed, the gateway is initialized with a metric value of ; all other nodes in the network are initialized with a default invalid metric value of . This metric information is piggybacked in the BEACONs that are transmitted by each node.
Upon receiving a BEACON with a valid metric value (i.e., 0) from an arbitrary neighbor , each node will update its metric value to the gateway as follows: the metric of node through the use of neighboring node is given by , where . If the estimated link quality between and is above a pre-determined threshold T and the metric through provides a better gradient to the gateway than the current metric (i.e., ), updates its metric, such that . In our indoor testbed, we use the values of and . Due to the transient nature of the wireless links in the network, the neighbor list and metric of a node can expire if the node does not receive BEACONs from its neighbors after a period of time.
4.3. Opportunistic Data Transmission
Data transmission takes place in an opportunistic fashion within the network. A node with data to send to the gateway will include its current metric in the DATA packet, which is broadcast to the local one-hop neighborhood. An arbitrary neighbor that receives the data packet will send an acknowledgment packet ACK to , if it has a better metric to the gateway, i.e., . As wireless links may fluctuate, the transmitting node can retransmit DATA packets up to a maximum of five times before the packet is discarded from its transmit buffer. The process is repeated along each hop until the gateway receives the DATA packet. Due to the opportunistic nature of the routing protocol, it is possible for duplicate copies of the same packet to arrive at the gateway by using sequence numbers. The duplication of packets is resolved at the back-end through the use of sequence numbers.
4.4. Protocol Format
There are three possible types of packets that are used in the protocol:
BEACON packets that are broadcast to neighboring nodes at periodic intervals of 30 s.
DATA packets that are generated by the sensor nodes at periodic intervals of 120 s.
ACK packets that are generated by the gateway or intermediate forwarding node (i.e., the node that receives the data from another node with a higher metric).
The corresponding format of each packet is as follows:
BEACON: [sequenceNum], [UNIXTime], [gatewayAddress], [gatewaySequenceNum], [metricToGateway]
DATA: [portNumber], [dataLength], [metricToGateway], [dataSequenceNumber], [routeIncluded]
ACK: [dataSource], [dataSequenceNumber]
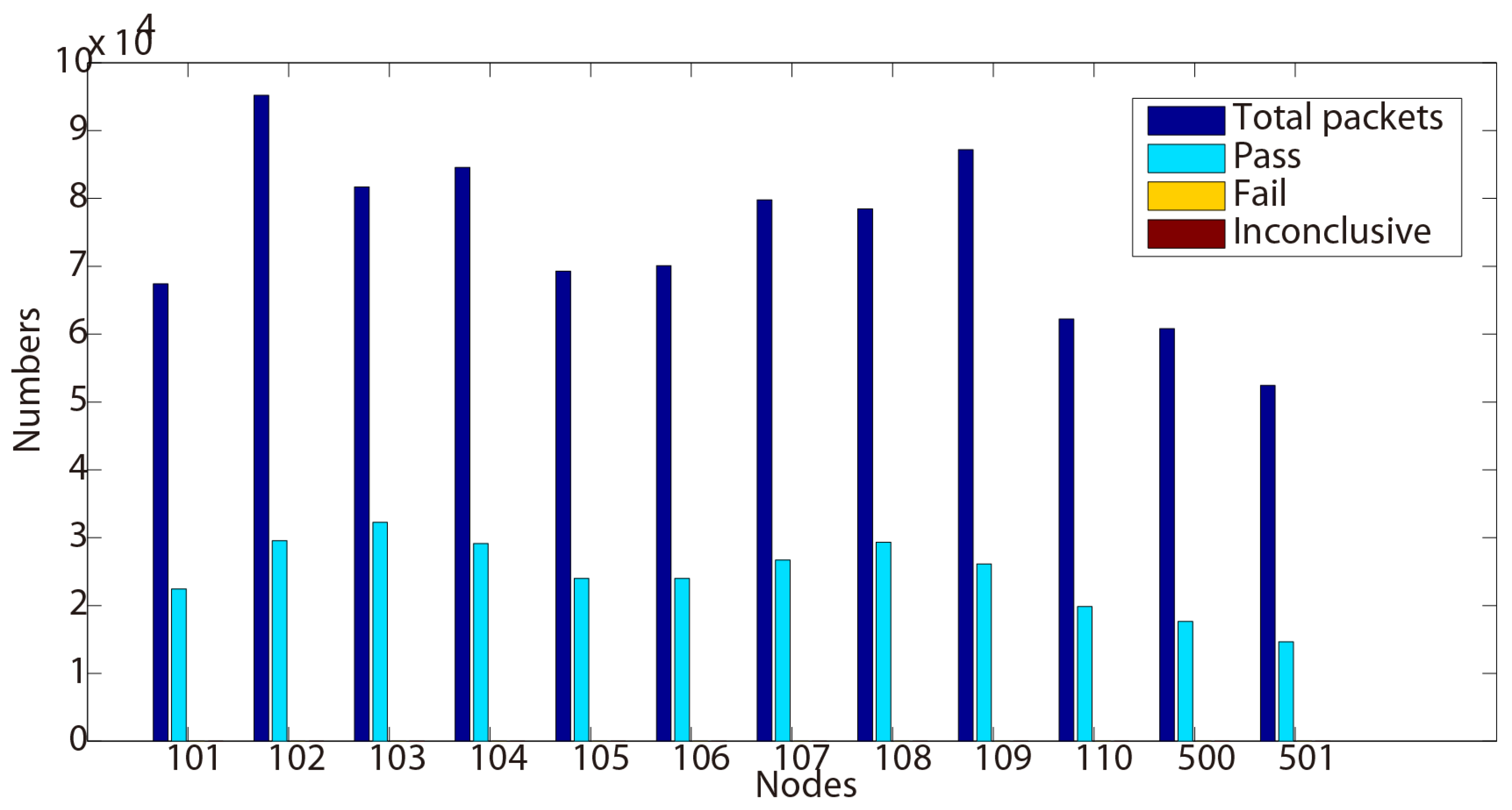
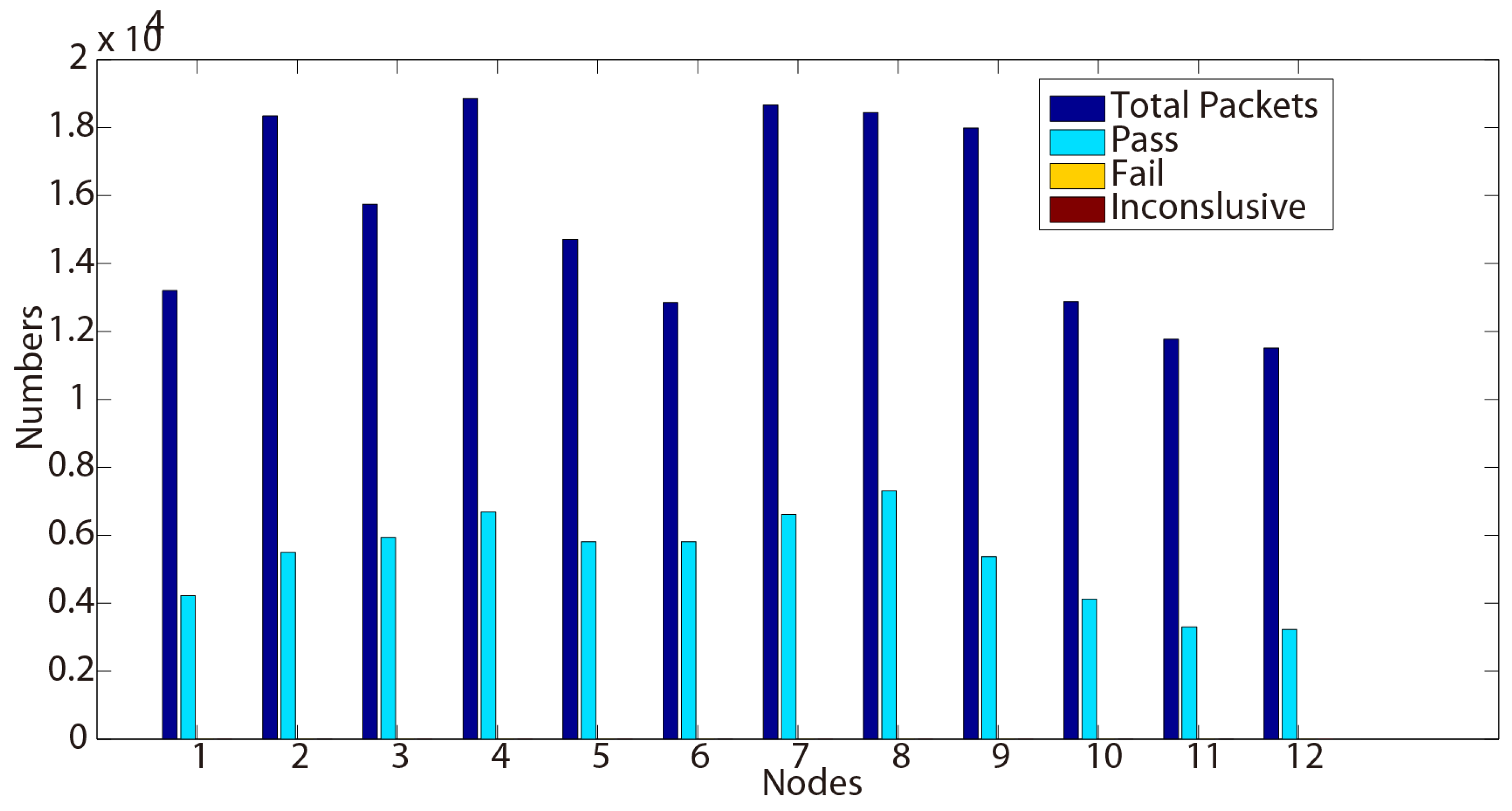
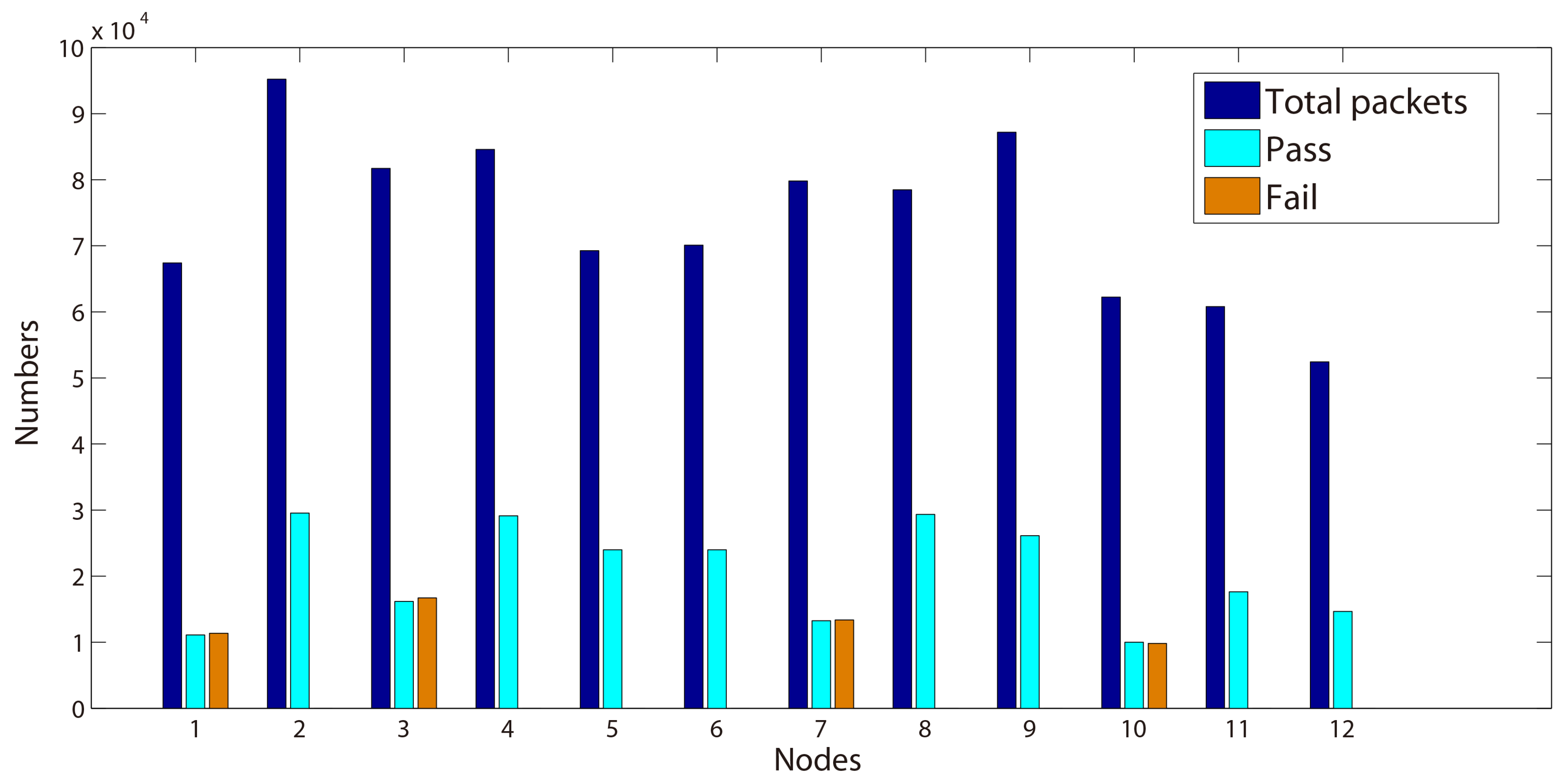
Example 1. Transmitted message (BEACON): 105, 65535, 0, 3, 9, 1404388288, 101, 1404388247, 30.
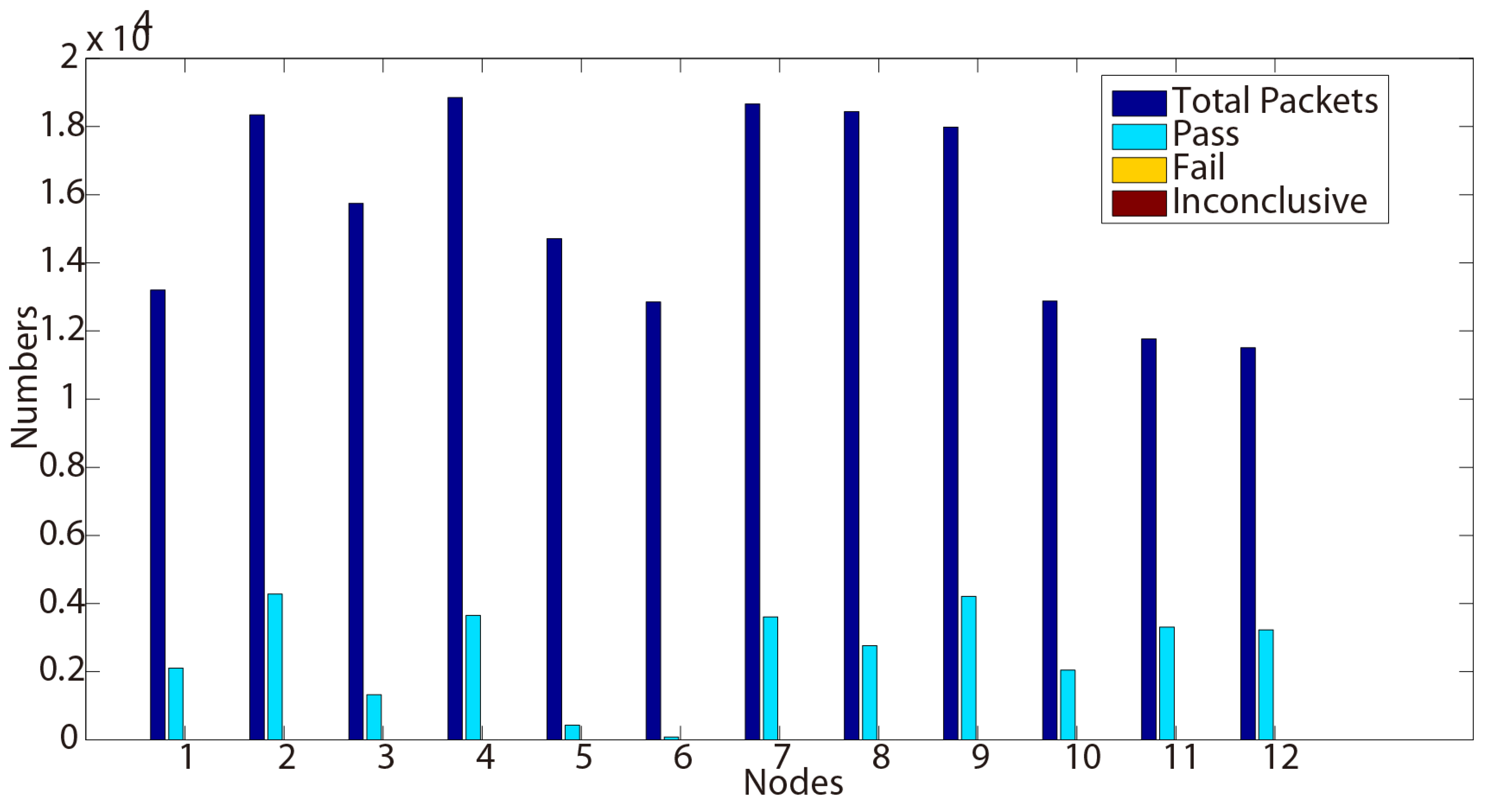
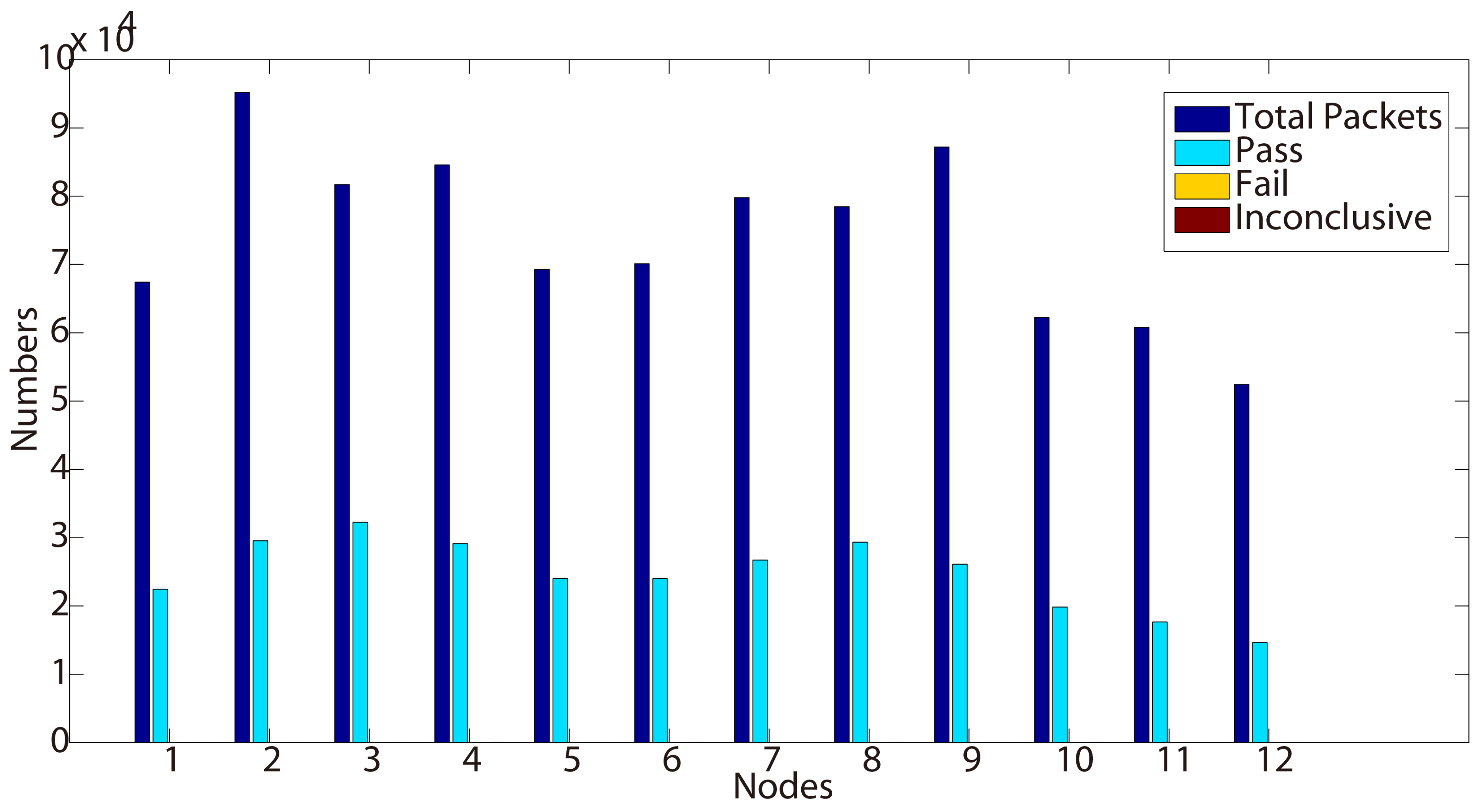
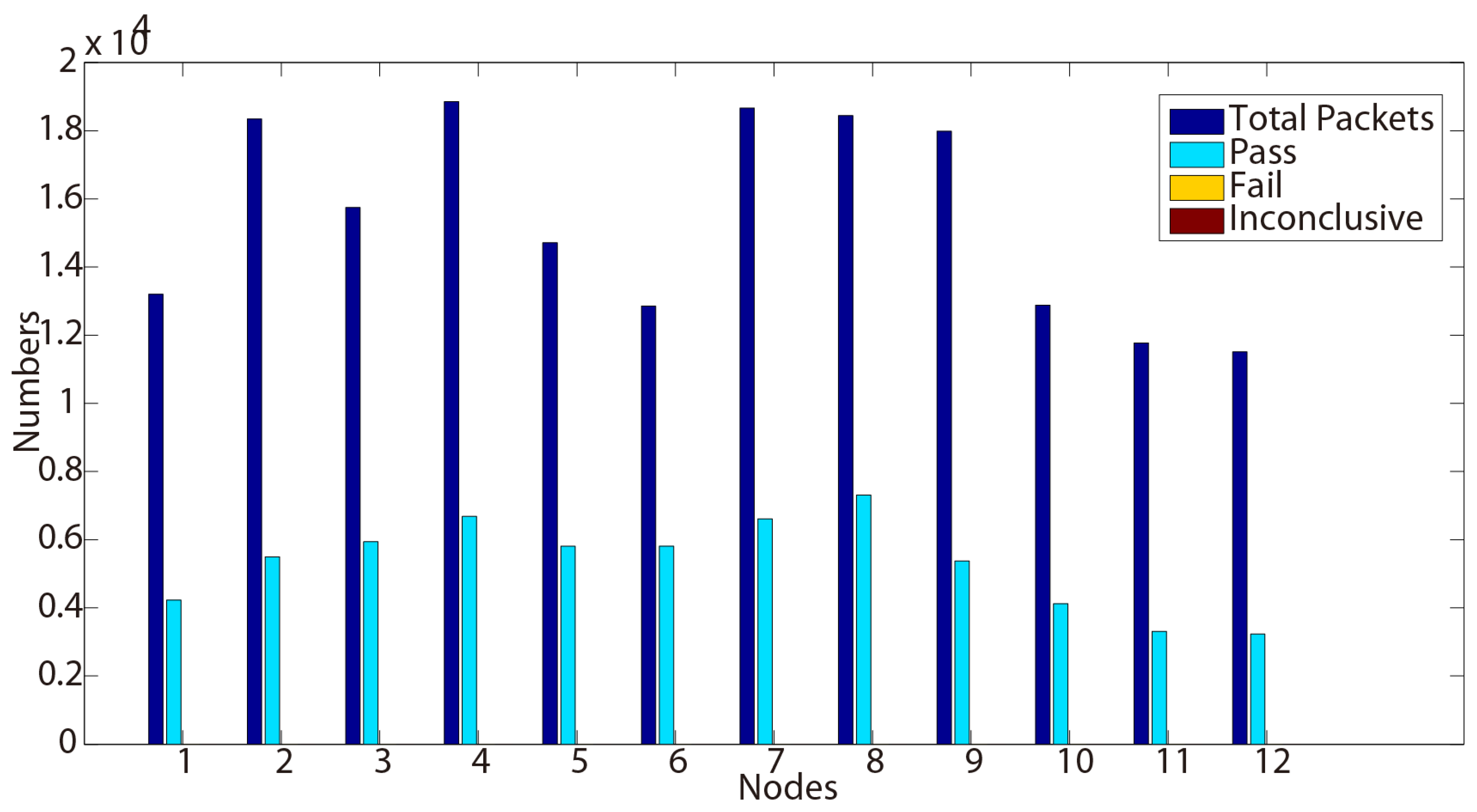
In Example 1, we illustrate a BEACON packet of sequence number nine, that is broadcast by node 105 to its neighboring nodes at time 1404388288. The BEACON contains the information that the metric from node 105 to the gateway 101 is 30 and that the last known gateway sequence number from 101 is 1404388247. The gateway sequence number is used to expire stale routes and prevent routing loops in the network. We present in the following the testing results we obtained while testing this new protocol from four properties.
6. Conclusions
This paper presents a formal approach for testing the functional requirements of a novel routing protocol used in wireless sensor networks. The routing protocol is designed by considering the inherent constraints of our smart system requirements and to cope with the drawbacks and lack of current available commercial protocols for our outdoor urban large-scale network. The main objective was therefore to test this new developed WSN routing protocol before its deployment, in a formal way, through a real testbed and without being intrusive. For that purpose, we defined a logic-based syntax and semantics to model the functional properties of the protocol. We also designed an efficient algorithm to evaluate these properties on real extracted execution traces.
Our approach has been successfully evaluated by experiments on the WSN testbed. We have shown that our formal approach has several advantages, among others: (i) the syntax and semantics are simple enough to allow any engineers (not only testers) to design their own functional properties to be tested; (ii) we may test several nodes at the same moment in a very short time; and (iii) we do not need either standardized properties or complete formal models to test a protocol; this is highly convenient while testing a new protocol during its development and deployment periods.
For future work, we will study the rewriting of some specific functional properties and the impacts on the testing process. We will apply and assess our approach on our large-scale outdoor deployed WSN focusing on the reliability of our algorithm, our protocol and specific behaviors between gateways.