A Provably-Secure ECC-Based Authentication Scheme for Wireless Sensor Networks
Abstract
: A smart-card-based user authentication scheme for wireless sensor networks (in short, a SUA-WSN scheme) is designed to restrict access to the sensor data only to users who are in possession of both a smart card and the corresponding password. While a significant number of SUA-WSN schemes have been suggested in recent years, their intended security properties lack formal definitions and proofs in a widely-accepted model. One consequence is that SUA-WSN schemes insecure against various attacks have proliferated. In this paper, we devise a security model for the analysis of SUA-WSN schemes by extending the widely-accepted model of Bellare, Pointcheval and Rogaway (2000). Our model provides formal definitions of authenticated key exchange and user anonymity while capturing side-channel attacks, as well as other common attacks. We also propose a new SUA-WSN scheme based on elliptic curve cryptography (ECC), and prove its security properties in our extended model. To the best of our knowledge, our proposed scheme is the first SUA-WSN scheme that provably achieves both authenticated key exchange and user anonymity. Our scheme is also computationally competitive with other ECC-based (non-provably secure) schemes.1. Introduction
As various sensors emerge and the related technologies advance, there has been a dramatic increase in the interest in wireless sensor networks (WSNs). Today, billions of physical, chemical and biological sensors are being deployed into various types of WSNs for numerous applications, including military surveillance, wildlife monitoring, vehicular tracking and healthcare diagnostics [1]. A major benefit of WSN systems is that they provide unprecedented abilities to explore and understand large-scale, real-world data and phenomena at a fine-grained level of temporal and spatial resolution. However, providing an application service in a WSN environment introduces significant security challenges to be addressed among the involved parties: users, sensors and gateways. One important challenge is to achieve authenticated key exchange between users and sensors (via the assistance of a gateway), thereby preventing illegal access to the sensor data and their transmissions. Authenticated key exchange in WSNs is more challenging to achieve than in traditional networks due to the sensor network characteristics, such as resource constraints, unreliable communication channel and unattended operation. Another important challenge is to provide user anonymity, which makes authenticated key exchange even harder. As privacy concern increases, user anonymity has become a major security property in WSN applications, as well as in many other applications, like mobile roaming services, anonymous web browsing, location-based services and e-voting. User authentication schemes for WSNs are designed to address these security challenges [2,3], and are a subject of active research in network security and cryptography.
Generally speaking, the design of cryptographic schemes (including user authentication schemes for WSNs) is error-prone, and their security analysis is time-consuming. The difficulty of getting a high level of assurance in the security of cryptographic schemes is well illustrated with examples of flaws discovered in many such schemes years after they were published; see, e.g., [4–6]. The many flaws identified in published schemes over the decades have promoted formal security analyses, which are broadly classified into two approaches [7,8]: the computer security approach and the computational complexity approach. The computer security approach places its emphasis on automated machine specification and analysis mostly in the Dolev–Yao adversarial model [9], where the underlying cryptographic primitives are often used in a black-box manner ignoring some of cryptographic details. The main problem with this automated approach is intractability and undecidability, as the adversary may exhibit a large set of possible behaviors, which leads to a state explosion. Cryptographic schemes proven secure in such a fashion could possibly be flawed, yielding a false positive result. In contrast, the computational complexity approach places its emphasis on deriving a polynomial-time reduction from the problem of breaking the scheme into another problem believed to be hard. A complete computational proof under a well-established cryptographic assumption provides a strong assurance that the security properties of the scheme are satisfied. Accordingly, it has been standard practice for the designers of cryptographic schemes to provide a proven reduction for the security of their schemes in a widely-accepted model [10,11]. Although these human-generated mathematical proofs are usually lengthy and complicated, they are certainly an invaluable tool for getting secure cryptographic schemes.
In 2009, Das [12] proposed a smart-card-based user authentication scheme for wireless sensor networks; throughout the paper, we call such a scheme a SUA-WSN scheme. Since then, the design of SUA-WSN schemes has received significant attention from researchers due to their potential to be widely deployed, and a number of solutions offering various levels of efficiency and security have been subsequently proposed [2,3,13–27]. Early schemes only aimed to achieve mutual authentication [13–15], while later schemes attempted to provide additional security properties, such as authenticated key exchange [2,3,16–27] and user anonymity [2,3,20,22–24,26]. Some schemes [16,21,27] employ elliptic curve cryptography to provide perfect forward secrecy, while others [2,3,12–14,17–20,22–26] only use symmetric cryptography and hash functions to focus on improving the efficiency.
One important security requirement for SUA-WSN schemes is to ensure that only a user who is in possession of both a smart card and the corresponding password can pass the authentication check of the gateway and gain access to the sensor network and data. A SUA-WSN scheme that meets this requirement is said to achieve two-factor security. To properly capture the notion of two-factor security, the adversary against SUA-WSN schemes is assumed to be able to either extract the sensitive information in the smart card of a user possibly via a side-channel attack [28,29] or learn the password of the user through shoulder-surfing or by exploiting a malicious card reader, but not both. Clearly, there is no means to prevent the adversary from impersonating a user if both the password of the user and the information in the smart card are disclosed.
Despite the research efforts over the recent years, it remains a significant challenge to design a robust SUA-WSN scheme that carries a formal proof of security in a widely-accepted model. As summarized in Table 1, most of the published schemes either provide no formal analysis of security [3,12–14,16,20–22,24–26] or fail to achieve important security properties, such as mutual authentication, session-key security, user anonymity, two-factor security and resistance against various attacks [3,13–16,19,21–27,30,31]. Some schemes [2,17–19,23,27] have been proven secure using a computer security approach, which, as mentioned above, suffers from intractability and undecidability and could possibly give a false positive result. To the best of our knowledge, Chen and Shih's scheme [15] is the only SUA-WSN scheme that was proven secure using a computational complexity approach. However, Chen and Shih's scheme does not provide key exchange functionality, but only focuses on mutual authentication (and thus, inherently, cannot carry a proof of authenticated key exchange). Moreover, the security model used for this scheme captures neither the user anonymity property nor the notion of two-factor security.
The contributions of this paper are two-fold:
- (1)
We present a security model for the analysis of sua-wsn schemes. Our security model is derived by extending the widely-accepted model of Bellare, Pointcheval and Rogaway [10] to incorporate into it the user anonymity property and the notion of two-factor security. Notice that the original Bellare–Pointcheval–Rogaway (BPR) model for authenticated key exchange (AKE) already captures insider attacks, offline dictionary attacks and other common attacks. We refer readers to [32] to understand how a key exchange scheme that is vulnerable to an offline dictionary attack can be rendered insecure in the BPR model. Our extension of the BPR model provides two security definitions, one for the AKE security and one for the user anonymity property, and both definitions capture the notion of two-factor security. Security properties like authentication, session-key security, perfect forward secrecy, known-key security and resistance against insider attacks and offline dictionary attacks are implied by the AKE security.
- (2)
We propose the first SUA-WSN scheme whose AKE security, as well as user anonymity are formally proven in a widely-accepted model. Our scheme employs elliptic curve cryptography (ECC) to provide perfect forward secrecy, but differs from other ECC-based schemes [16,21,27] in that it provides user anonymity. We prove the security properties of our scheme in the random oracle model under the elliptic curve computational Diffie–Hellman (ECCDH) assumption. We also show that our provably-secure scheme is computationally competitive compared with other ECC-based (non-provably secure) schemes.
Table 2 shows the basic notation that is used consistently throughout this paper.
The remainder of this paper is structured as follows. Section 2 describes our extended security model for the analysis of SUA-WSN schemes. Section 3 presents the proposed SUA-WSN scheme along with cryptographic primitives on which the security of the scheme relies and then compares our scheme with other ECC-based schemes, both in terms of efficiency and security. Section 4 provides proofs of the user anonymity property and the AKE security for our scheme. Section 5 concludes the paper, summarizing our result and presenting some interesting future work.
2. Our Extended Security Model for SUA-WSN Schemes
In this section, we present a security model extended from the BPR model [10] to capture the security properties of SUA-WSN schemes.
Participants and long-lived keys. Let GW be the gateway and
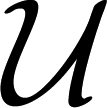
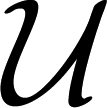

GW generates its master secret(s), issues a smart card to each UR ∈
and establishes a shared key with each SR ∈
; and
each UR ∈
chooses its private password pwUR from the set of all possible passwords.
Partnering. Informally, we say that two instances are partners (or partnered) if they participate together in a protocol session and establish a shared key. Formally, the partner relationship between instances is defined in terms of the notion of the session identifier. A session identifier (sid) is literally an identifier of a protocol session and is typically defined as a function of the messages exchanged in the session. Let denote the sid of instance . We say that two instances, and , are partners if: (1) both instances have accepted; and (2) .
Adversary capabilities. The adversary





Execute ( , , ): This query models passive eavesdropping on the protocol messages. It prompts a protocol execution among the instances , and and returns the transcript of the protocol execution to
.
, m): This query sends a message m to an instance , modeling active attacks against the protocol. Upon receiving m, the instance proceeds according to the protocol specification. Any message generated by is output and given to
. A query of the form Send( , start) prompts to initiate a protocol session.
Reveal( ): This query captures known key attacks. Upon receiving this query, the instance returns its session key back to
(if it has accepted).
CorruptLL(E): This query returns the long-lived secret(s) of entity E, capturing the notion of forward secrecy, as well as resistance to unknown key share attacks and insider attacks.
CorruptSC(UR): This query captures side-channel attacks (i.e., the notion of two-factor security) and returns the information stored in the smart card of UR.
TestAKE( ): This query is used for defining the indistinguishability-based security of session keys. The output of the query depends on a random bit b chosen by the oracle; in response to the query, either the real session key if b = 1 or a random key drawn from the session-key space if b = 0 is returned to
.
TestID(UR): This query is used for determining whether the protocol provides user anonymity or not. Depending on a random bit b chosen by the oracle,
is given either the identity actually used for UR in the protocol sessions (when b = 1) or a random identity drawn from the identity space (when b = 0).
SR and GW are said to be corrupted when they are asked a CorruptLL query, while UR is considered as corrupted if it has been asked both CorruptLL and CorruptSC queries.
Authenticated key exchange (AKE). We define the AKE security of the authentication and key exchange protocol P by using the notion of freshness of instances. Informally, a fresh instance refers to an instance whose session key should be kept indistinguishable from a random key to the adversary

Definition 1 (Freshness). An instance is fresh unless one of the following occurs:
queries Reveal( ) or Reveal( ), where , is the partner of ;
queries CorruptLL(SR) or CorruptLL(GW) before accepts.
queries both CorruptLL(UR) and CorruptSC(UR), for some UR ∈
, before accepts.
The AKE security of the protocol P is defined in the context of the following two-phase experiment: Experiment ExpAKE0:
Phase 1.

is not allowed to ask queries of the TestID oracle.
is not allowed to ask the TestAKE( ) query if the instance is not fresh.
is not allowed to ask the Reveal( ) query if it has already asked a TestAKE query of or its partner instance.
Phase 2. When Phase 1 is over,


Let SuccAKE0 be the event that



Definition 2 (AKE security). The authentication and key exchange protocol P is AKE-secure if is negligible for any PPT adversary 
User anonymity. The AKE security does not imply user anonymity. In other words, an authentication and key exchange protocol that does not provide user anonymity may still be rendered AKE secure.
Hence, a new, separate definition is necessary to capture the user anonymity property. Our definition of user anonymity is based on the notion of cleanness.
Definition 3 (Cleanness). A user U R ∈
queries CorruptLL(GW).
queries both CorruptLL(UR) and CorruptSC(UR).
Note that this definition of cleanness does not impose any restriction on asking a CorruptLL query to SR. This reflects our objective to achieve user anonymity even against the sensor SR.
Now, consider the following experiment to formalize the user anonymity property:
Experiment ExpID0:
- Phase 1.
A freely asks any oracle queries, except that:
is not allowed to ask queries of the TestAKE oracle.
is not allowed to ask the TestID(UR) query if the user UR is not clean.
is not allowed to ask CorruptLL and CorruptSC queries against GW and UR if it has already asked the TestID(UR) query.
- Phase 2.
When Phase 1 is over,
outputs a bit b′ as a guess on the random bit b selected by the TestID oracle.
succeeds if b = b′.
Let SuccID0 be the event that A succeeds in the experiment ExpID0. Then, we define the advantage of

Definition 4 (User anonymity). The authentication and key exchange protocol P provides user anonymity if is negligible for any PPT adversary 
3. The Proposed SUA-WSN Scheme
This section presents our ECC-based user authentication scheme for wireless sensor networks. Our scheme consists of three phases: the registration phase, the authentication, the key exchange phase and the password update phase. We begin by describing the cryptographic primitives on which the security of our scheme relies.
3.1. Preliminaries
Elliptic curve computational Diffie-Hellman (ECCDH) problem. Let













Symmetric encryption schemes. A symmetric encryption scheme Γ algorithms (Enc, Dec) where: (1) the encryption algorithm Enc takes as input an ℓ-bit key k and a plain text message m and outputs a ciphertext c; and (2) the decryption algorithm Dec takes as input a key k and a ciphertext c and outputs a message m. We require that Deck(Enck(m)) = m holds for all k ∈ {0,1}ℓ and all m ∈



| Experiment |
| for i = 1 to n |
| ki ∈R {0,1}ℓ |
(m0,i,m1,i) ←
 (Γ) (Γ) |
| ci ← Encki(mb,i) |
 (ci) (ci) |
b′ ←
 , where b′ ∈ {0,1} , where b′ ∈ {0,1} |
| return b′ |
Let
be the advantage of an eavesdropper

We say that Γ is secure if
is negligible in ℓ for any PPT adversary


Message authentication codes. A message authentication code (MAC) scheme Δ is a pair of efficient algorithms (Mac, Ver) where: (1) the MAC generation algorithm Mac takes as input an ℓ-bit key k and a message m and outputs a MAC δ and (2) the MAC verification algorithm Ver takes as input a key k, a message m and a MAC δ and outputs one if δ is valid for m under k or outputs zero if δ is invalid. Let
be the advantage of an adversary




Cryptographic hash functions. Our scheme uses three cryptographic hash functions L : {0,1}* → {0,1}ℓ, H : {0,1}* → {0,1}κ and F : {0,1}* → {0,1}ɛ, where ℓ is as defined for Δ and Γ, κis the bit-length of session keys and ε is the bit-length of SIDUR (see Section 3.2.1 for the definition of SIDUR). These hash functions are modeled as random oracles in our security proofs.
3.2. Description of the Scheme
The public system parameters for our scheme include:
an elliptic curve group
with a generator P of prime order q,
a symmetric encryption scheme Γ = (Enc, Dec),
a MAC scheme Δ = (Mac, Ver), and
three hash functions L, H and F.
We assume that these public system parameters are fixed during an initialization phase and are known to all parties in the network. As part of the initialization, the gateway GW chooses two master keys , computes its public key X = xP and establishes a shared secret key kGS = L(IDSR‖y) with each sensor SR.
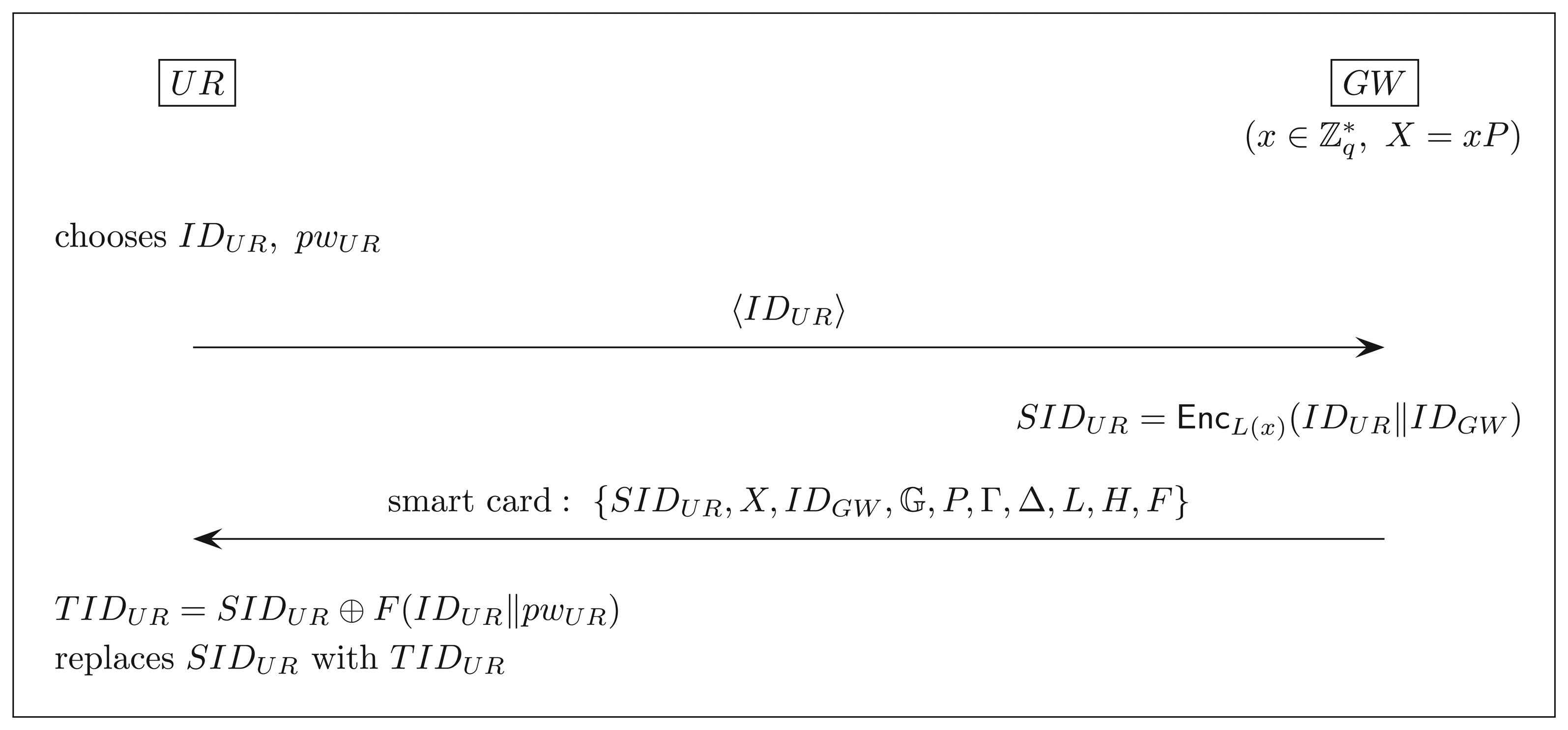
3.2.1. Registration Phase
A user UR registers itself with the gateway GW as follows:
UR chooses its identity I DUR and password pwUR freely and submits the identity I DUR to GW via a secure channel.
GW computes SIDUR = EncL(x)(IDUR‖IDGW) and issues UR a smart card loaded with {SIDUR, X, IDGW,
, P, Γ, Δ, L, H, F}. (We assume that q is implicit in
.)
UR replaces SIDUR with TIDUR = SIDUR ⊕ F(IDUR‖pwUR).
This phase of user registration is depicted in Figure 1.
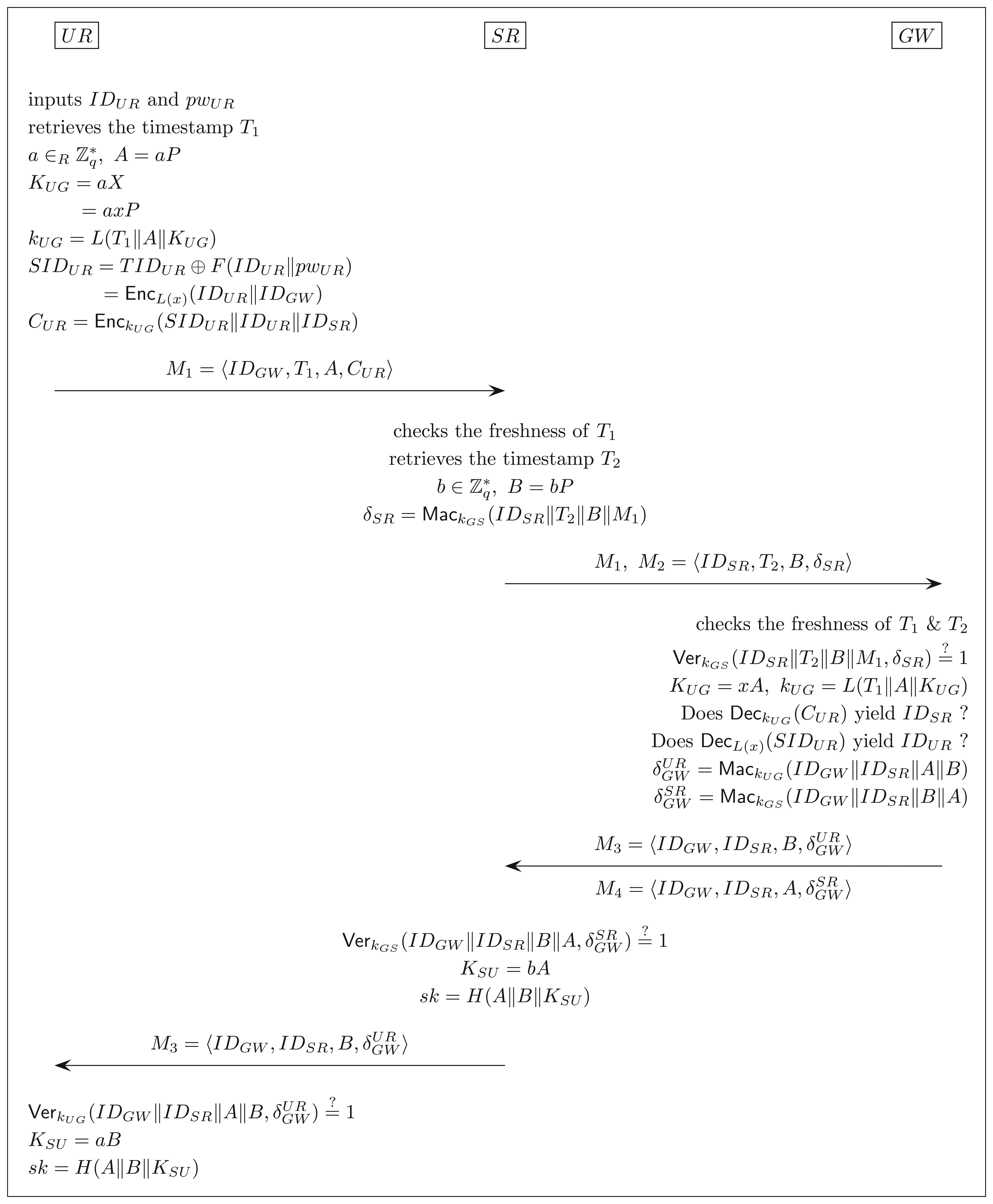
3.2.2. Authentication and Key Exchange Phase
UR needs to perform this phase with SR and GW whenever it wishes to gain access to the sensor network and data. The steps of the phase are depicted in Figure 2 and are described as follows:
- Step 1.
UR inserts its smart card into a card reader and inputs its identity IDUR and password pwUR. Given IDUR and pwUR, the smart card retrieves the current timestamp T1, selects a random and computes:
After the computations, the smart card sends the message M1 = 〈IDGW, T1, A, CUR〉 to the sensor SR.
- Step 2.
Upon receiving M1, SR first checks the freshness of T1. If T1 is not fresh, SR aborts the protocol. Otherwise, SR retrieves the current timestamp T2, chooses a random and computes B and δsr as follows:
Then, SR sends the message M2 = 〈IDSR, T2, B, δSR〉 along with M1 to GW.
- Step 3
After having received M1 and M2, GW verifies that: (1) T1 and T2 are fresh; and (2) VerkGS(IDSR‖T2‖B‖M1, δSR) = 1. If any of the verifications fails, GW aborts the protocol. Otherwise, GW computes KUG = xA and kUG = L(T1‖A‖KUG), decrypts CUR with key kUG and checks if the decryption produces the same IDSR as contained in M2. GW aborts if the check fails. Otherwise, GW decrypts SIDUR with key L(x) and checks if this decryption yields the same IDUR as produced through the decryption of CUR. If only the two IDs match, GW computes:
and sends two messages M3 = 〈IDGW, IDSR, B, 〉 and M4 = 〈IDGW,IDsr,A, 〉 to SR.- Step 4.
When receiving M3 and M4, SR verifies that VerkGS(IDGW‖IDSR‖B‖A, ) = 1. If the verification fails, SR aborts the protocol. Otherwise, SR forwards the message M3 to UR and computes the shared secret KSU = bA and the session key sk = H(A‖B‖KSU).
- Step 5.
Upon receiving M3, UR checks if VerkUG(IDGW‖IDSR‖A‖B, ) = 1. U R aborts the protocol if the check fails. Otherwise, U R computes KSU = aB and sk = H(A‖B‖KSU).
Since KSU = bA = aB = abP, UR and SR will compute the same session key sk = H(A‖B‖abP; in the presence of a passive adversary.
3.2.3. Password Update Phase
One of the general guidelines to get better password security is to ensure that passwords are changed at regular intervals. Our scheme allows users to update their passwords at will.
UR inserts his smart card into a card reader and enters the identity IDUR, the current password pwUR and the new password .
The smart card computes and replaces TIDUR with .
3.3. Performance and Security Comparison
Table 3 compares our scheme with other ECC-based SUA-WSN schemes in terms of the computational requirements, the AKE security and user anonymity. For fairness of comparison, SUA-WSN schemes that use only lightweight symmetric cryptographic primitives are not considered in the table since they cannot achieve forward secrecy, but have a clear efficiency advantage over the ECC-based schemes.
The scalar-point multiplication and map-to-point operation are much more expensive than the other operations considered in the table, such as symmetric encryption/decryption, MAC generation/verification and hash function evaluation. The total number of modular exponentiations and map-to-point operations required in Yeh et al.'s scheme [16] is 10, while the number is reduced to six in the other schemes. Therefore, the overall performance of Yeh et al.'s scheme is not as good as those of the other schemes.
From the viewpoint of the computational burden on the sensor SR, our scheme is competitive with Choi et al.'s scheme [27] and Shi and Gong's scheme [21], since a MAC generation/verification is almost as fast as a hash function evaluation. According to Crypto++ benchmarks, HMACwith SHA-1 takes 11.9 cycles per byte, while SHA-1 takes 11.4 cycles per byte (see Table 4).
Another point we wish to make is that a hash function evaluation with a long input string may not be faster than a symmetric encryption with a relatively short plain text input, though the opposite is generally true for the same length of inputs. For example, the computation of the ciphertext CUR in our scheme is unlikely to be more expensive than the computations of the hash values β, γ and δ, which are defined in both Choi et al.'s scheme and Shi and Gong's scheme. In this sense, it is fair to say that our scheme is competitive also in terms of the overall computational cost.
As is obvious from the table, our scheme is the only one that provides user anonymity (regardless of whether it is proven or not). This explains how the other schemes could have been designed without using any form of encryption algorithm. Choi et al. [27] prove that their scheme achieves the AKE security, but only using a computer security approach. In contrast, we use a computational complexity approach in proving both the AKE security and the user anonymity property
4. Security Results
Let P denote the authentication and key exchange protocol of our scheme depicted in Figure 2. This section proves that the protocol P is AKE-secure and provides user anonymity (against any party other than the gateway GW); see Section 2 for the formal definitions of the AKE security and the user anonymity property
4.1. Proof of AKE Security
Theorem 1. Our authentication and key exchange protocol P is AKE-secure in the random oracle model under the ECCDH assumption in

Proof. Assume a ppt adversary






Experiment ExpAKE1. In this first modified experiment, the simulator answers the queries to the L oracle as follows:
Simulation of the L oracle
For each query of L on a string m, the simulator first checks if an entry of the form (m, l) is in a list called LList, which is maintained to store input-output pairs of L. If it is, the simulator outputs l as the answer to the hash query. Otherwise, the simulator chooses a random ℓ-bit string str, answers the query with str and adds the entry (m, str) to LList.
This is the only difference between ExpAKE1 and ExpAKE0; the simulator answers all other oracle queries of

Claim 1. PrP,


Experiment ExpAKE2. In this experiment, we modify the computations of X and A as follows:
The ExpAKE2 modification
The simulator chooses two random elements Y,Y′ ∈
and sets X = Y′.
For every fresh instance, the simulator chooses a random and sets A = rY. For other instances, the simulator computes A as in experiment ExpAKE1.
Due to the modification, the simulator does not know the master secret x. The simulator aborts the experiment if



Claim 2., where qL is the number of queries made of the L oracle.
Proof. We prove the claim via a reduction from the ECCDH problem, which is believed to be hard, to the problem of distinguishing two experiments ExpAKE1 and ExpAKE2. Assume that the success probability of














Before proceeding further, we define the event Forge as follows:
Forge: The event that the adversary

Experiment ExpAKE3. This experiment is different from ExpAKE2 in that it is aborted and the adversary

Claim 3., where qsend is the number of queries made for the oracle Send.
Proof. Assume that the event Forge occurs with a non-negligible probability. Then, we construct an algorithm



Let nk be the total number of MAC keys used in the sessions initiated via a Send query. Clearly, nk ≤ qsend.







If the guess i is correct, then the simulation is perfect and


Experiment ExpAKE4. We next modify the way of answering queries of the H oracle as follows:
Simulation of the H oracle
For each H query on a string m, the simulator first checks if an entry of the form (m, h) is in a list called HList, which is maintained to store input-output pairs of H. If it is, h is the answer to the hash query. Otherwise, the simulator chooses a random κ-bit string str, answers the query with str and adds the entry (m, str) to HList.
Other oracle queries of

Claim 4. PrP,


Experiment ExpAKE5. We finally modify the experiment so that, for each fresh instance of SR, the computation of B is done as follows:
The ExpAKE5 modification
The simulator selects a random and computes B = r′X.
The simulator sets the session key sk to a random κ-bit string for each pair of fresh instances, as it cannot compute KSU. Accordingly, the success probability of

Claim 5., where qH is the number of queries made of the H oracle.
Proof. Suppose that the difference in the advantage of















In experiment ExpAKE5, the adversary



4.2. Proof of User Anonymity
Theorem 2. The authentication and key exchange protocol P provides user anonymity in the random oracle model under the ECCDH assumption in

Proof. Assume a PPT adversary





Experiment ExpID1. This experiment is different from ExpID0 in that the random oracle L is simulated as follows:
Simulation of the L oracle
For each query to L on a string m, the simulator first checks if an entry of the form (m, l) is in a list called LList, which is maintained to store input-output pairs of L. If it is, the simulator outputs l as the answer to the hash query. Otherwise, the simulator chooses a random ℓ-bit string str, answers the query with str and adds the entry (m, str) to LList.
Other oracle queries of

Claim 6. PrP,


Experiment ExpID2. Here, we modify the experiment so that A is computed as follows:
The ExpID2 modification
The simulator chooses a random exponent and computes Y = y P.
For each instance of users, the simulator chooses a random and sets A = rY.
As a result of the modification, each KUg is set to xyrP for some random
. Since the view of

Claim 7. PrP,


Experiment ExpID3. In this experiment, we modify the computations of X and A as follows:
The ExpID3 modification
The simulator chooses two random elements Y,Y′∈
and sets X = Y′.
For instances of every clean user, the simulator chooses a random and sets A = rY. For other instances, the simulator computes A as in experiment ExpID2.
As a result, the simulator does not know the master secret x. The simulator aborts the experiment if



Claim 8. where qL is the number of queries made to the L oracle.
Proof. We prove the claim via a reduction from the ECCDH problem, which is believed to be hard, to the problem of distinguishing two experiments ExpID2 and ExpID3. Assume that the success probability of












Experiment ExpID4. We finally modify the experiment so that, for each clean user UR ∈
Claim 9..
Proof. We prove the claim by constructing an eavesdropper







eav outputs (SIDUR‖IDUR‖IDSR, SIDUR‖ID′UR‖IDSR) as its plain text pair in the indistinguishability experiment . Let c be the ciphertext received in return for the plain text pair.
eav sets Cur equal to the ciphertext c.
That is,



The probability that
eav outputs one when the first plain texts are encrypted in the experiment is equal to the probability that
succeeds in the experiment ExpID3.
The probability that
eav outputs one when the second plain texts are encrypted in the experiment is equal to the probability that
succeeds in the experiment ExpID4.
That is,
. Note that in the simulation,

In the experiment ExpID4, the adversary


5. Concluding Remarks
We have extended the widely-accepted security model of Bellare, Pointcheval and Rogaway [10] to formally capture the security requirements for SUA-WSN schemes—smart-card-based user authentication schemes for wireless sensor networks. Our extended model provides formal definitions of the AKE security and the user anonymity property, while capturing the notion of two-factor security. We have also proposed a new SUA-WSN scheme and proved that it achieves user anonymity, as well as the AKE security in the extended model. To the best of our knowledge, our scheme is the first SUA-WSN scheme that is proven secure in a widely-accepted model.
We believe that our result lays a solid foundation for designing provably-secure two-factor authentication schemes for mobile roaming services, where user anonymity, as well as authenticated key exchange are also of critical security importance; see, e.g., the recent work of He et al. [33,34]. A concrete design of such a provably-secure roaming authentication scheme would be interesting future work. We also leave it as future work to present a formal treatment of security properties for three-factor authentication schemes [35].
Acknowledgments
This work was supported by Konkuk University.
Author contributions
M.K. and Y.L. conceived and designed the experiments; M.K. and Y.L. performed the experiments; J.P. and D.W. analyzed the data; J.N. and D.W. proved the security of the protocol; J.N. and J.P. wrote the paper.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Rawat, P.; Singh, K.; Chaouchi, H.; Bonnin, J. Wireless sensor networks: A survey on recent developments and potential synergies. J. Supercomput 2014, 68, 1–48. [Google Scholar]
- Kumar, P.; Choudhury, A.; Sain, M.; Lee, S.; Lee, H. RUASN: A robust user authentication framework for wireless sensor networks. Sensors 2011, 11, 5020–5046. [Google Scholar]
- Khan, M.; Kumari, S. An improved user authentication protocol for healthcare services via wireless medical sensor networks. Int. J. Distrib. Sens. Netw 2014, 2014(347169). [Google Scholar]
- Choo, K.K.R.; Boyd, C.; Hitchcock, Y. Errors in computational complexity proofs for protocols. Proceedings of ASIACRYPT 2005, Chennai, India, 4–8 December 2005; pp. 624–643.
- Nam, J.; Paik, J.; Won, D. A security weakness in Abdalla et al.'s generic construction of a group key exchange protocol. Inf. Sci 2011, 181, 234–238. [Google Scholar]
- Nam, J.; Choo, K.K.R.; Kim, M.; Paik, J.; Won, D. Dictionary attacks against password-based authenticated three-party key exchange protocols. KSII Trans. Internet Inf. Syst 2013, 7, 3244–3260. [Google Scholar]
- Choo, K.K.R. Refuting security proofs for tripartite key exchange with model checker in planning problem setting. Proceedings of 19th IEEE Computer Security Foundations Workshop, Venice, Italy, 5–7 July 2006; pp. 297–308.
- Choo, K.K.R. Secure Key Establishment; Springer: Berlin, Germany, 2008. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar]
- Bellare, M.; Pointcheval, D.; Rogaway, P. Authenticated key exchange secure against dictionary attacks. Proceedings of EUROCRYPT 2000, Bruges, Belgium, 14–18 May 2000; pp. 139–155.
- Canetti, R.; Krawczyk, H. Analysis of key-exchange protocols and their use for building secure channels. Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques: Advances in Cryptology, Innsbruck, Austria, 6–10 May 2001; pp. 453–474.
- Das, M. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun 2009, 8, 1086–1090. [Google Scholar]
- He, D.; Gao, Y.; Chan, S.; Chen, C.; Bu, J. An enhanced two-factor user authentication scheme in wireless sensor networks. Adhoc Sens. Wirel. Netw 2010, 10, 361–371. [Google Scholar]
- Khan, M.; Alghathbar, K. Cryptanalysis and security improvements of “two-factor user authentication in wireless sensor networks”. Sensors 2010, 10, 2450–2459. [Google Scholar]
- Chen, T.; Shih, W. A robust mutual authentication protocol for wireless sensor networks. ETRI J 2010, 32, 704–712. [Google Scholar]
- Yeh, H.; Chen, T.; Liu, P.; Kim, T.; Wei, H. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar]
- Kumar, P.; Lee, S.; Lee, H. E-SAP: Efficient-strong authentication protocol for healthcare applications using wireless medical sensor networks. Sensors 2012, 12, 1625–1647. [Google Scholar]
- Yoo, S.; Park, K.; Kim, J. A security-performance-balanced user authentication scheme for wireless sensor networks. Int. J. Distrib. Sens. Netw 2012, 2012(382810). [Google Scholar]
- Vaidya, B.; Makrakis, D.; Mouftah, H. Two-factor mutual authentication with key agreement in wireless sensor networks. Secur. Commun. Netw 2012. [Google Scholar] [CrossRef]
- Xue, K.; Ma, C.; Hong, P.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl 2013, 36, 316–323. [Google Scholar]
- Shi, W.; Gong, P. A new user authentication protocol for wireless sensor networks using elliptic curves cryptography. Int. J. Distrib. Sens. Netw 2013, 2013(730831). [Google Scholar]
- Kumar, P.; Gurtov, A.; Ylianttila, M.; Lee, S.; Lee, H. A strong authentication scheme with user privacy for wireless sensor networks. ETRI J 2013, 35, 889–899. [Google Scholar]
- He, D.; Kumar, N.; Chen, J.; Lee, C.; Chilamkurti, N.; Yeo, S. Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimed. Syst 2013. [Google Scholar] [CrossRef]
- Chi, L.; Hu, L.; Li, H.; Chu, J. Analysis and improvement of a robust user authentication framework for ubiquitous sensor networks. Int. J. Distrib. Sens. Netw 2014, 2014(637684). [Google Scholar]
- Kim, J.; Lee, D.; Jeon, W.; Lee, Y.; Won, D. Security analysis and improvements of two-factor mutual authentication with key agreement in wireless sensor networks. Sensors 2014 14, 6443–6462.
- Jiang, Q.; Ma, J.; Lu, X.; Tian, Y. An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-Peer Netw. Appl 2014. [Google Scholar] [CrossRef]
- Choi, Y.; Lee, D.; Kim, J.; Jung, J.; Nam, J.; Won, D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. Proceedings of CRYPTO 1999, Santa Barbara, CA, USA, 15–19 August 1999; pp. 388–397.
- Messerges, T.; Dabbish, E.; Sloan, R. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput 2002, 51, 541–552. [Google Scholar]
- Han, W. Weakness of a secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Available online: http://eprint.iacr.org/2011/293 (accessed on 15 August 2014).
- Kumar, P.; Lee, H. Cryptanalysis on two user authentication protocols using smart card or wireless sensor networks. Proceedings of the IEEE Wireless Advanced (WiAd), London, UK, 20-22 June 2011; pp. 241–245.
- Nam, J.; Choo, K.K.R.; Paik, J.; Won, D. Password-only authenticated three-party key exchange proven secure against insider dictionary attacks. Sci World J 2014, 2014. No. 802359. [Google Scholar]
- He, D.; Kumar, N.; Khan, M.; Lee, J. Anonymous two-factor authentication for consumer roaming service in global mobility networks. IEEE Trans. Consum. Electron 2013, 59, 811–817. [Google Scholar]
- He, D.; Zhang, Y.; Chen, J. Cryptanalysis and improvement of an anonymous authentication protocol for wireless access networks. Wirel. Pers. Commun 2014, 74, 229–243. [Google Scholar]
- He, D.; Kumar, N.; Lee, J.; Sherratt, R. Enhanced three-factor security protocol for USB mass storage devices. IEEE Trans. Consum. Electron 2014, 60, 30–37. [Google Scholar]
| Scheme | Security Justification | Major Weaknesses |
|---|---|---|
| Das [12] | Heuristic arguments | No key-exchange functionality |
| He et al. (2010) [13] | Heuristic arguments | No key-exchange functionality |
| Khan and Alghathbar [14] | Heuristic arguments | No key-exchange functionality |
| Chen and Shih [15] | Computational complexity approach (only for entity authentication) | No key-exchange functionality |
| Yeh et al. [16] | Heuristic arguments | Failures of mutual authentication and forward secrecy [30] |
| Kumar et al. (2011) [2] | Computer security approach | Vulnerability to a node capture attack [24] |
| Kumar et al. (2012) [17] | Computer security approach | Failures of authenticated key exchange, user anonymity and two-factor security [3,23] |
| Yoo et al. [18] | Computer security approach | Vulnerability to a man-in-the-middle attack [22] |
| Vaidya et al. [19] | Computer security approach | Failure of user authentication [25] |
| Xue et al. [20] | Heuristic arguments | Vulnerability to a privileged insider attack [26] |
| Shi and Gong [21] | Heuristic arguments | Failures of authenticated key exchange and two-factor security [27] |
| Kumar et al. (2013) [22] | Heuristic arguments | |
| He et al. (2013) [23] | Computer security approach | |
| Chi et al. [24] | Heuristic arguments | |
| Kim et al. [25] | Heuristic arguments | |
| Khan and Kumari [3] | Heuristic arguments | |
| Jiang et al. [26] | Heuristic arguments | |
| Choi et al. [27] | Computer security approach | No provision of user anonymity |
| Symbol | Description |
|---|---|
| UR | User |
| SR | Sensor |
| GW | Gateway |
| IDUR,IDSR,IDGW | Identities of UR, SR and GW |
| pwUR | Password of U |
| sk | Session key |
 | Probabilistic polynomial-time adversary |
| L(·),H(·),F(·) | Cryptographic hash functions |
| Enck(·)/Deck(·) | Symmetric encryption/decryption under key k |
| MAC | Message authentication code |
| Mack(·)/Verk(·) | MAC generation/verification under key k |
| ⊕ | Bitwise exclusive-or (XOR) operation |
| ‖ | String concatenation operation |
| {0,1}n | Bit strings of length n |
| Scheme | Computation | Security | ||
|---|---|---|---|---|
| SR | UR+SR+GW | AKE | Anonymity | |
| Our scheme | 2M +2A+1H | 6M +3E +6A+6H | Proven | Proven |
| Choi et al. [27] | 2M +5H | 6M +18H | Proven using a computer security approach | No |
| Shi and Gong [21] | 2M +4H | 6M +15H | Broken [27] | No |
| Yeh et al. [16] | 2M +1P + 2H | 8M +2P +9H | Broken [30] | No |
M: scalar-point multiplication; P: map-to-point operation; E: symmetric encryption/decryption; A: MAC generation/verification; H: hash function evaluation.
| Algorithm | HMAC (SHA-1) | SHA-1 | AES/CTR | AES/CBC | AES/OFB | AES/ECB |
|---|---|---|---|---|---|---|
| Cycles Per Byte | 11.9 | 11.4 | 12.6 | 16.0 | 16.9 | 16.0 |
© 2014 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nam, J.; Kim, M.; Paik, J.; Lee, Y.; Won, D. A Provably-Secure ECC-Based Authentication Scheme for Wireless Sensor Networks. Sensors 2014, 14, 21023-21044. https://doi.org/10.3390/s141121023
Nam J, Kim M, Paik J, Lee Y, Won D. A Provably-Secure ECC-Based Authentication Scheme for Wireless Sensor Networks. Sensors. 2014; 14(11):21023-21044. https://doi.org/10.3390/s141121023
Chicago/Turabian StyleNam, Junghyun, Moonseong Kim, Juryon Paik, Youngsook Lee, and Dongho Won. 2014. "A Provably-Secure ECC-Based Authentication Scheme for Wireless Sensor Networks" Sensors 14, no. 11: 21023-21044. https://doi.org/10.3390/s141121023
APA StyleNam, J., Kim, M., Paik, J., Lee, Y., & Won, D. (2014). A Provably-Secure ECC-Based Authentication Scheme for Wireless Sensor Networks. Sensors, 14(11), 21023-21044. https://doi.org/10.3390/s141121023




