Using RFID to Enhance Security in Off-Site Data Storage
Abstract
:1. Introduction
- An RFID-based identification mechanism for data custody units and employees [8], which increases the speed and reliability in the identification process compared to bar-codes, the most widely used existing technology.
- A set of security controls throughout the entire life cycle of the custody unit, including two-way confirmation scans, the segregation of duties, continuous inventory and theft protection measures. We also arrange these security controls in a set of security tiers, which allows us to leverage security requirements with usability and cost constraints when deploying the system in a given scenario.
- A Web-based management service, which allows all agents involved (customers, operators and managers) to monitor the data life cycle in real time.
2. The Off-Site Data Storage Process for Business Continuity Management
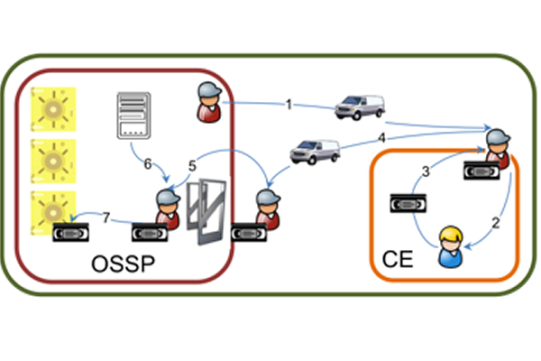
2.1. Off-site data storage service use cases
2.2. Key processes and security concerns
- Identification and authentication between the OSSP and CE employees because custody units must only be delivered to and retrieved from authorized personnel.
- Identification and validation of the delivered or retrieved custody units because only those custody units that have been authorized to be delivered or retrieved can be accepted. This is especially important when a single transport vehicle visits several customers because custody units must never be delivered to the wrong customers.
- Accountability of the entire process because it involves a responsibility transfer, which may include liabilities.
3. An RFID-Based, Off-Site Storage Management System
3.1. System architecture
3.2. Security mechanisms
3.2.1. Communication security controls
- TLS secure connections, using AES-128 ciphering to provide confidentiality [12].
- Server-side certificate at the MSS to provide server authentication. To generate the certificate, a public-key cryptography standard (PKCS) with a 2048-bit RSA key is used [13].
- User names and passwords to access the MSS from the PSS and CSS to provide client authentication.
- Subsystem client-side certificate at the GSS and ISS to provide authentication of these subsystems for their access to the MSS. Certificate generation is analogous to the server certificate.
- Browser client-side certificates of the PSS and CCSS subsystems, to provide an additional layer of authentication over username/password pairs for OSSP and CE employees when accessing the MSS. Again, certificate encryption strength is the same as that used for the server certificate.
3.2.2. RFID identification controls
- Plain RFID identification. Each custody unit or employee has an associated ISO15693 RFID tag [14] with an 8 bytes serial number (UID) that can be read by the GSS and PSS subsystems to identify them to the system.
- Password protected RFID identification. Each ISO15693 RFID tag has an internal memory where a protected identifier (PID) may be stored as data. Access to this data may be protected with a 64-bit password, which provides additional security against identifier theft or replication. This prevents accidental or intentional reading of the tag by unauthorized readers. It is still vulnerable, however, to communication eavesdropping between the reader and the tag.
- Encrypted RFID identification. Some manufacturers provide high-security RFID tags with encryption capabilities that can store a secret key and use it to provide confidentiality and authentication in the PID transfer from the tag to the reader.
3.2.3. Physical access controls
- Vault space division. The vault space may be divided to provide different security levels. For instance, a vault antechamber may be used to temporarily store the custody units intended to be put in transit (or that recently arrived from transit), while custody units that are not being moved are kept in a more secure environment in the inner vault. This would work as a custody unit ‘floodgate’.
- RFID-based vault access control. Any of the RFID identification mechanisms described in the previous section may be used to control access to the vault. A GSS using a RFID gate antenna connected to electronically operated doors may guarantee that only authorized personnel can access each section of the vault. Combined with the vault space division described above, this can effectively provide different physical access clearance levels.
- PIN-based vault access control. Employees may be required to enter a personal identification number (PIN) to access different sections of the vault. This has the advantage that the PIN cannot be lost or stolen (like an RFID card), but it makes identification a bit more time consuming (especially if access frequency is high) and can still be vulnerable to weak PINs (e.g., ‘1234’) or oversight (also known as ‘shoulder surfing’).
- Biometric access control. Biometric identification mechanisms (e.g., fingerprint scans) may be used to provide access control to the vault in a more secure manner when needed.
- RFID-based CU check-in and check-out control. Regarding personnel access control, any of the RFID mechanisms described in the previous section may be used. This controls which custody units enter or exit the vault, allowing only authorized custody units (e.g., those that are intended to be delivered) to leave the vault with authorized personnel (e.g., the driver entitled to the delivery). In addition, similar controls can be put in transport vans to prevent mistakes when extracting custody units for delivery to a customer.
- Continuous RFID inventory. This involves deploying an ISS at the inner vault, which performs periodic scans on all custody units stored in the vault. In this way, positive control of custody units (i.e., custody unit X has been detected in the vault) may be performed instead of negative control (i.e., custody unit X has not been detected leaving the vault).
3.2.4. Process controls
- Custody unit scan at critical operations. Custody units are the most critical assets in the off-site storage service; therefore, custody unit management mistakes must be avoided. In addition to ‘due care and diligence’ measures (such as transportation in padded cases and with adequate temperature conditions), special attention must be paid to the logical management of mistakes, such as preparing the wrong custody units for exit or delivering custody units to the wrong customer. To avoid such mistakes, any operation with custody units may be forced to involve a custody unit scan with the PSS, thus allowing the MSS to check that the operation is being performed with the right set of custody units.
- Employee authentication at every operation. Because the custody unit scan involves using the PSS, an additional control mechanism would be to require the employee to log in to the PSS before performing any operation. This permits the MSS to check that the operation is being performed by an authorized employee. Furthermore, to avoid session-hijacking, we can take advantage of the scan capabilities of the PSS and have the employee scan his/her RFID card, thus providing a two-factor authentication.
- Segregation of duties. In the security audit literature, the segregation of duties is seen as a paramount process control [15]. Basically, the segregation of duties implies that no single person has control over every stage of a critical process to prevent accidental or intentional propagation of mistakes or other irregularities in the processes. In the use cases under consideration, the segregation of duties may be implemented at different stages. For example, there may be a warehouse employee who prepares the custody units to be transported and leaves them in the vault antechamber, where they are retrieved by a driver who leaves the vault, puts the custody units in the transport and carries them to the customer facilities. Once there, a co-driver may be the only person entitled to take these custody units from the transport van and deliver them to the customer. An analogous segregation of duties may be implemented for the retrieval use case. If, at every step, the involved employee performs the aforementioned custody unit check, we effectively increase the security against the propagation of irregularities.
- Retrieval/delivery receipts. As stated in Section II, the custody unit exchange between OSSP and CE employees is one of the most critical processes in both use cases because it is the transaction where responsibility for the custody units is transferred between the OSSP and CE. For accountability and liability reasons, a receipt should be generated at each exchange that details the date and time of the exchange, the custody units exchanged and the names and signatures of the OSSP and CE employees involved in the transaction.
- PSS-generated receipts. Even though the use of receipts provides accountability, it may not be completely useful if it is not backed up by authentication and custody unit check mechanisms. The use of the PSS to generate the receipts may provide such mechanisms. The PSS scan capabilities may be used to authenticate the OSSP and CE employees (also to put their names in the receipt) and check that the custody units exchanged are the proper ones (and log the custody unit identifiers in the receipt). They may also provide real-time logging of the transaction via the MSS. In addition, the authentication of the CE employees through their RFID cards may be used to provide different authorization levels for special services (e.g., emergency deliveries).
- Real-time custody unit tracking. The PSS-based controls discussed in this section, along with the physical access controls described in the previous section, allow for every MSS operation to be logged in. This allows OSSP and CE managers to track custody units in real time, which may provide them with supervision capabilities, greatly enhancing the security of the process.
3.3. Security tiers
- Security Tier 0. No specific security controls. The processes would follow the use cases described in section II.1 without additional security mechanisms. This tier is included only as a reference and we strongly discourage its use.
- Security Tier 1. Includes PIN-based vault access control and retrieval/delivery receipts. It adds vault space division and segregation of duties. Custody unit identification and classification for delivery and retrieval are performed using bar codes. This is the standard security level provided by most off-site storage providers.
- Security Tier 2. Substitutes retrieval/delivery receipts by PSS-generated receipts using plain RFID scans. Custody unit and employee scans are only performed during the exchange between OSSP and CE employees. It adds TLS secure connections, username/password authentication, server-side certificates and subsystem client-side certificates to secure access to the MSS. It also adds real-time custody unit tracking for OSSP managers.
- Security Tier 3. Adds custody unit scan and employee authentication at every operation.
- Security Tier 4. Adds real-time custody unit tracking for CE managers and browser client-side certificates for access to the MSS from the CCSS.
- Security Tier 5. Substitutes PIN-based access control at the vault by RFID-based access control using plain RFID scans. It adds RFID-based check-in and check-out at the vault and involves implementing a GSS at the vault.
- Security Tier 6. Adds biometric access control to the vault.
- Security Tier 7. Substitutes plain RFID scans by password-protected RFID scans.
- Security Tier 8. Substitutes password-protected RFID scans with encrypted RFID scans.
- Security Tier 9. Adds RFID-based CU check-in and check-out at the transport vans. Involves implementing a GSS at each transport van.
- Security Tier 10. Adds continuous RFID inventory at the vault. Involves implementing an ISS at the vault.
4. Performance Evaluation
4.1. Experimental settings
4.2. Experimental results
5. Conclusions
List of Acronyms
| CCSS | Customer Client Subsystem |
| CE | Customer Enterprise |
| CEE | CE Employee |
| CU | Custody Unit |
| GSS | Gate Subsystem |
| ISS | Inventory Subsystem |
| MSS | Management Subsystem |
| OSSP | Off-site Data Storage Service Provider |
| OSSPE | OSSP Employee |
| PIN | Personal Identification Number |
| PKCS | Public-key Cryptography Standards |
| PSS | Portable Subsystem |
References
- DoD, CSC-STD-001-83. Trusted Computer System Evaluation Criteria; US Department of Defense: Fort Meade, MD, USA, 1983. [Google Scholar]
- Khalfan, AM. Information security considerations in IS/IT outsourcing projects: A descriptive case study of two sectors. Int. J. Info. Manage 2004, 24, 29–42. [Google Scholar]
- Grocholski, GT; Noble, A. Top Business/Technology Issues Survey Results; ISACA: Rolling Meadows, IL, USA, 2008; p. 16. [Google Scholar]
- Kermarkar, U; Manga, V. Business continuity and technology in the retail sector. In The Business and Information Technologies (BIT) Project: A Global Study of Business Practice; World Scientific Publishing: Singapore, 2006; pp. 289–299. [Google Scholar]
- Lam, W. Ensuring business continuity. IT Prof 2002, 4, 19–25. [Google Scholar]
- Ward, T. Security of backup data. Info. Secur. J. A Glob. Perspective 2006, 15, 31–34. [Google Scholar]
- Bajgoric, N. Continuous Computing Technologies for Enhancing Business Continuity; IGI Global: Hershey, PA, USA, 2009; pp. 234–251. [Google Scholar]
- Finkenzeller, K. RFID Handbook Fundamentals and Applications in Contactless Smart Cards and Identification; John Wiley & Sons: Hoboken, NJ, USA, 2003; pp. 11–28. [Google Scholar]
- Hodge, GM. Best practices for digital archiving: An information life cycle approach. J Electron Publ 2000. [Google Scholar] [CrossRef]
- Foley, SN. The specification and implementation of commercial security requirements including dynamic segregation of duties. Proceedings of the 4th ACM Conference on Computer and Communications Security CCS '97, Zurich, Switzerland; April 1997; pp. 125–134. [Google Scholar]
- Rodrigo, A; Marsa-Maestre, I. Servicio de Custodia Basado en RFID (in Spanish); M. Sc. Thesis; Universidad de Alcalá: Alcala de Henares, Spain, 2008. [Google Scholar]
- Chown, P. RFC 3268––Advanced Encryption Standard (AES) Ciphersuites for Transport Layer Security (TLS). June 2002. Available online: http://tools.ietf.org/html/rfc3268 (accessed on 26 August 2010).
- Jonsson, J; Kaliski, B. RFC 3447––Public-Key Cryptography Standards (PKCS) #1: RSA Cryptography Specifications Version 21. February 2003. Available online: http://tools.ietf.org/html/rfc3447 (accessed on 26 August 2010).
- ISO, ISO/IEC 15693-1to3. Identification cards––Contactless integrated circuit(s) cards––Vicinity cards. Available online: http://www.iso.org (accessed on 26 August 2010).
- Eloff, JH; Eloff, M. Information security architecture. Comput. Fraud Secur 2005, 11, 10–16. [Google Scholar]
- Business continuity management (BSCM) Ltd. corporate web site (in Spanish). Available online: http://www.bscm.es (accessed on 26 August 2010).
- Ganong, R. The emergence of e-vaulting. Info. Manage. J 2003, 37, 1–9. [Google Scholar]
- Mosharaf, NM. A survey of network virtualization. Comput. Netw 2010, 54, 862–876. [Google Scholar]





| Security Mechanism | Security Tier | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | |
| TLS secure connections, username/password, server-side certs., subsystem certs. | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| Real-time custody unit tracking, browser client-side certificates | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||
| Plain RFID identification | ✓ | ✓ | |||||||||
| Password protected RFID identification | ✓ | ||||||||||
| Encrypted RFID identification | ✓ | ✓ | ✓ | ||||||||
| Vault space division, segregation of duties | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| PIN-based vault access control | ✓ | ✓ | ✓ | ✓ | |||||||
| RFID-based vault access control, RFID-based CU check-in and check-out at vault | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||
| RFID-based CU check-in and check-out at the transport vans | ✓ | ✓ | |||||||||
| Biometric vault access control | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| Continuous RFID inventory | ✓ | ||||||||||
| CU and employee authentication at every operation | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||
| Retrieval/delivery receipts | ✓ | ||||||||||
| PSS-generated receipts | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||
| Security Risk | Security Tier | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | |
| Impersonation of OSSP and CE employees | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| OSSP and CE employee credential forgery | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||
| Custody unit ID tag forgeries | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||
| Delivery or retrieval repudiation | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| Delivery or retrieval to wrong customers | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| CU exposure to unauthorized customers | ✓ | ✓ | |||||||||
| Unauthorized CUs leaving the vault | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||
| Unauthorized access to the vault | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| Theft / oversight of credentials for vault access | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| Custody unit operations by unauthorized personnel | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||
| Mistaken/malicious CU operations by authorized pers. | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||
| Undue CU manipulations within the vault | ✓ | ||||||||||
| # of CU | Tier-1 | Tier-5 | ||
|---|---|---|---|---|
| error rate | failure rate | error rate | failure rate | |
| 1 | 0 | 0 | 0 | 0 |
| 5 | 0 | 0 | 0 | 0 |
| 10 | 0 | 0 | 0 | 0 |
| 20 | 0.01 | 0.002 | 0 | 0 |
| 30 | 0.02 | 0.005 | 0.005 | 0 |
| 50 | 0.05 | 0.01 | 0.01 | 0.0001 |
| Intermediary experiment attack success rate (wrong CU leave vault) | Conscious attack experiment | |||||
|---|---|---|---|---|---|---|
| attack success rate (wrong CU leave vault) | attack success rate (CU mis-delivered) | |||||
| # of CU | Tier-1 | Tier-5 | Tier-1 | Tier-5 | Tier-1 | Tier-5 |
| 1 | 0 | 0 | 1 | 0 | 0 | 0 |
| 5 | 0 | 0 | 1 | 0 | 0 | 0 |
| 10 | 0 | 0 | 1 | 0 | 0.12 | 0 |
| 20 | 0.004 | 0 | 1 | 0 | 0.26 | 0 |
| 30 | 0.007 | 0 | 1 | 0 | 1 | 0 |
| 50 | 0.02 | 0.0002 | 1 | 0.0002 | 1 | 0.0003 |
© 2010 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Lopez-Carmona, M.A.; Marsa-Maestre, I.; De la Hoz, E.; Velasco, J.R. Using RFID to Enhance Security in Off-Site Data Storage. Sensors 2010, 10, 8010-8027. https://doi.org/10.3390/s100908010
Lopez-Carmona MA, Marsa-Maestre I, De la Hoz E, Velasco JR. Using RFID to Enhance Security in Off-Site Data Storage. Sensors. 2010; 10(9):8010-8027. https://doi.org/10.3390/s100908010
Chicago/Turabian StyleLopez-Carmona, Miguel A., Ivan Marsa-Maestre, Enrique De la Hoz, and Juan R. Velasco. 2010. "Using RFID to Enhance Security in Off-Site Data Storage" Sensors 10, no. 9: 8010-8027. https://doi.org/10.3390/s100908010
APA StyleLopez-Carmona, M. A., Marsa-Maestre, I., De la Hoz, E., & Velasco, J. R. (2010). Using RFID to Enhance Security in Off-Site Data Storage. Sensors, 10(9), 8010-8027. https://doi.org/10.3390/s100908010