Ransomware Detection Using the Dynamic Analysis and Machine Learning: A Survey and Research Directions
Abstract
:1. Introduction
1.1. Paper Contribution
- i.
- This survey presented a brief taxonomy while outlining the ransomware attack detection studies from 2019 to 2021 with the focus on dynamic analysis for different platforms.
- ii.
- Presented a collection of datasets, their sources and analysis tools been utilized to carry out the dynamic analysis, to train and test the ransomware detection systems developed using machine and deep learning techniques.
- iii.
- Extensive overview of ransomware detection studies utilizing machine and deep learning and categorized the studies with respect to encryption process timelines.
- iv.
- Extraction of the list of research directions that need to be addressed by future researcher.
1.2. Paper Ogranization
2. Competing Surveys
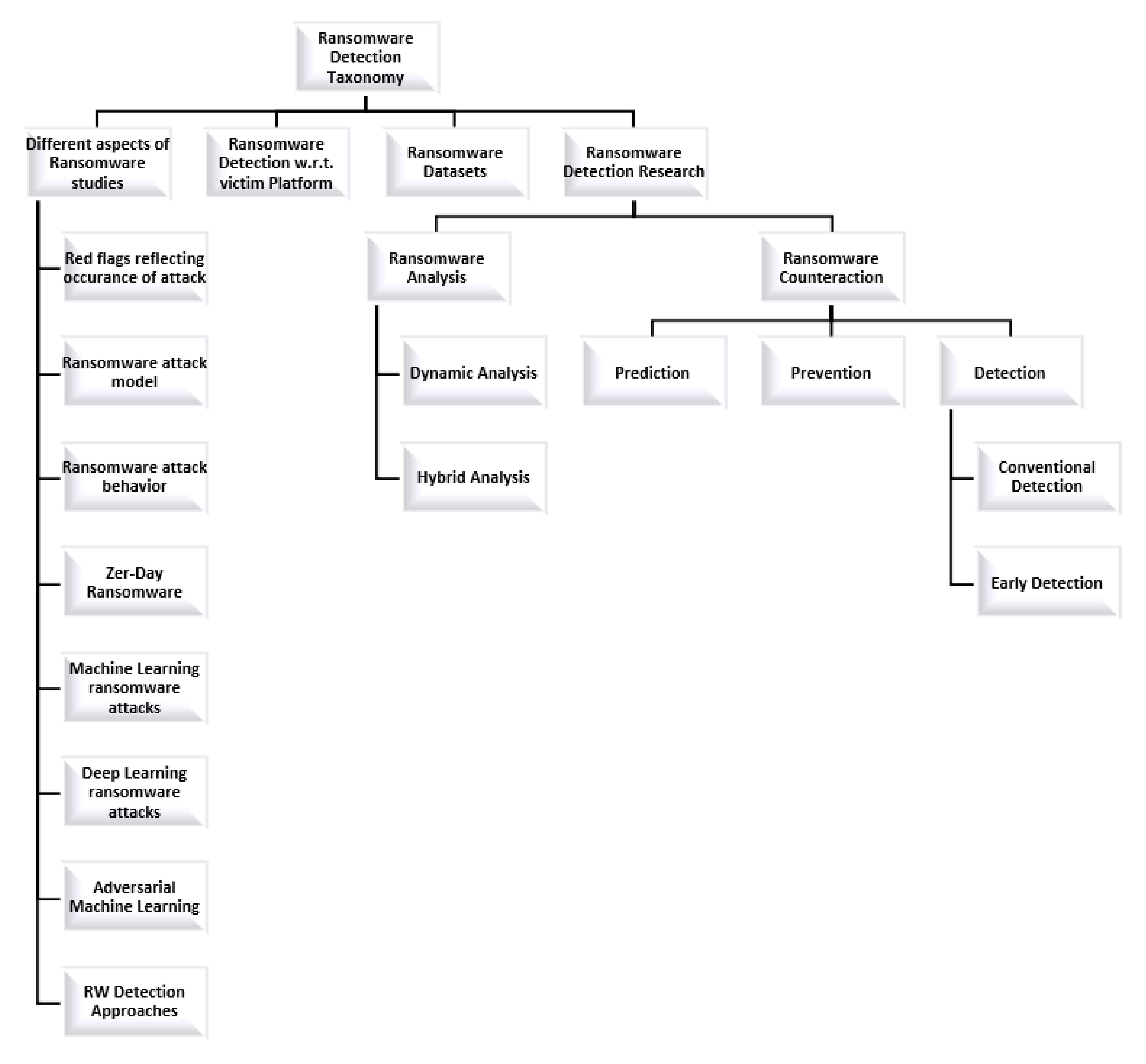
3. Different Aspects of Ransomware Studies
3.1. Red Flags Reflecting Occurrence of Ransomware Attack
- (1)
- Opening of many files [47].
- (2)
- Structure of input and output streams to a process is different [47].
- (3)
- Many write/overwrite operations [48].
- (4)
- A process calling encryption APIs [49].
- (5)
- Frequent reading and rewriting/deleting requests in a short period of time [50].
- (6)
- Communication with command-and-control server [48].
- (7)
- Change in the user registry keys [51].
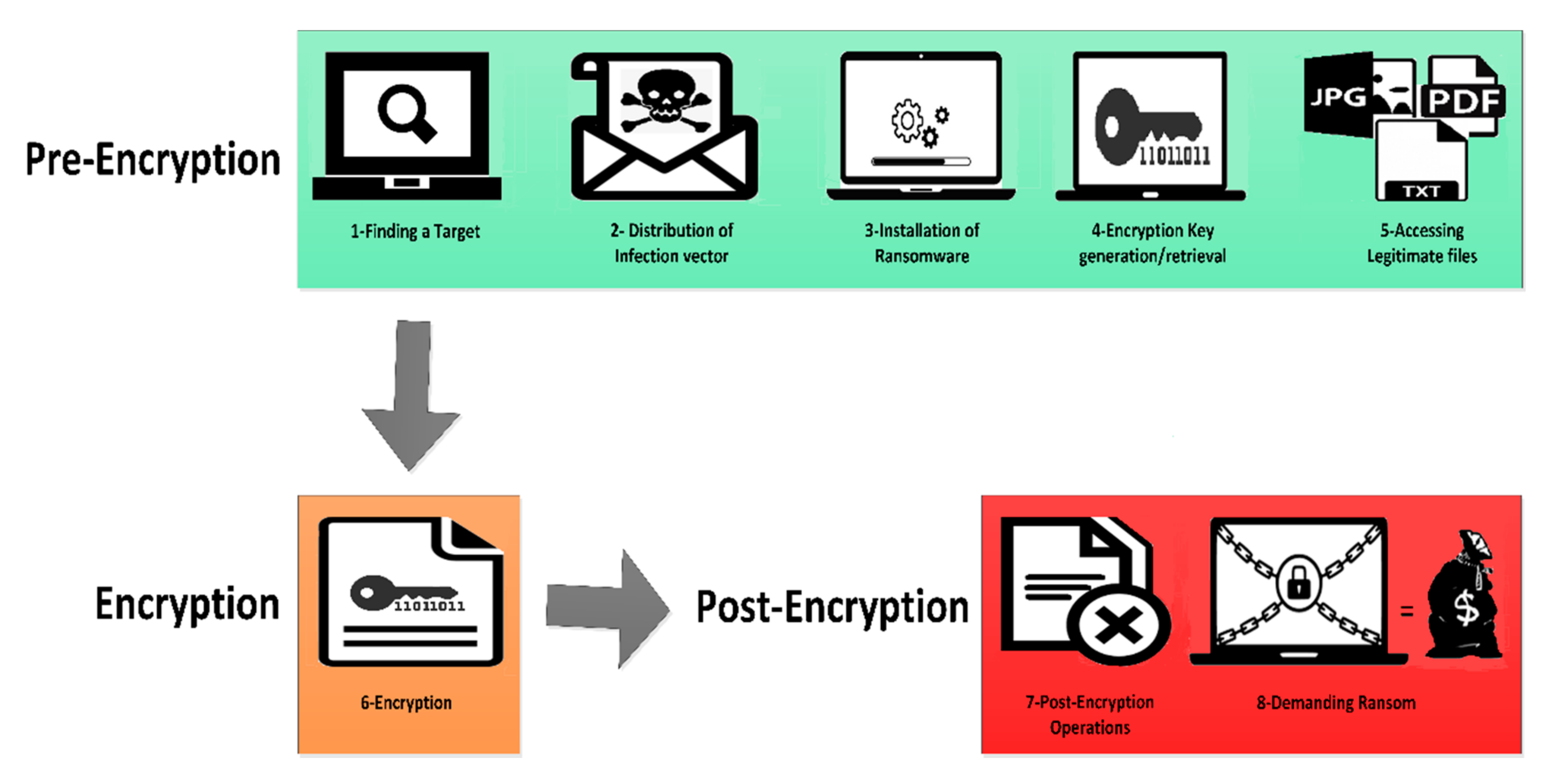
3.2. Ransomware Attack Model
- (1)
- Finding a target;
- (2)
- Distribution of the infection vector;
- (3)
- Installation of ransomware;
- (4)
- Encryption key generation and retrieval;
- (5)
- Accessing legitimate files;
- (6)
- Encryption;
- (7)
- Post Encryption operations;
- (8)
- Demanding Ransom.
3.3. Ransomware Attack Behaviour
3.4. Zero-Day Ransomware
3.5. Machine Learning Ransomware Attacks
3.6. Deep Learning Ransomware Attacks
3.7. Adversarial Machine Learning
3.8. Ransomware Detection Approaches
3.8.1. Misuse based Ransomware Detection Approaches
- I.
- Signature based Detection Approaches
- II.
- Behavioral based Detection Approaches
- III.
- Hybrid Detection Approaches
3.8.2. Anomaly based Ransomware Detection Approaches
4. Ransomware Detection Studies w.r.t Compromised Platforms
- (1)
- Ransomware attacks on PC and smartphones;
- (2)
- Ransomware attacks on IoT ecosystem (Cloud, Fog, IoT, and Ransomwear);
- (3)
- Ransomware attacks on network.
4.1. Ransomware Attacks on PC and Smartphones
4.2. Ransomware Attacks on IoT Ecosystem
4.3. Networks Based Ransomware
5. Ransomware Datasets
6. Research in Ransomware Detection
6.1. Ransomware Analysis
6.1.1. Static Analysis
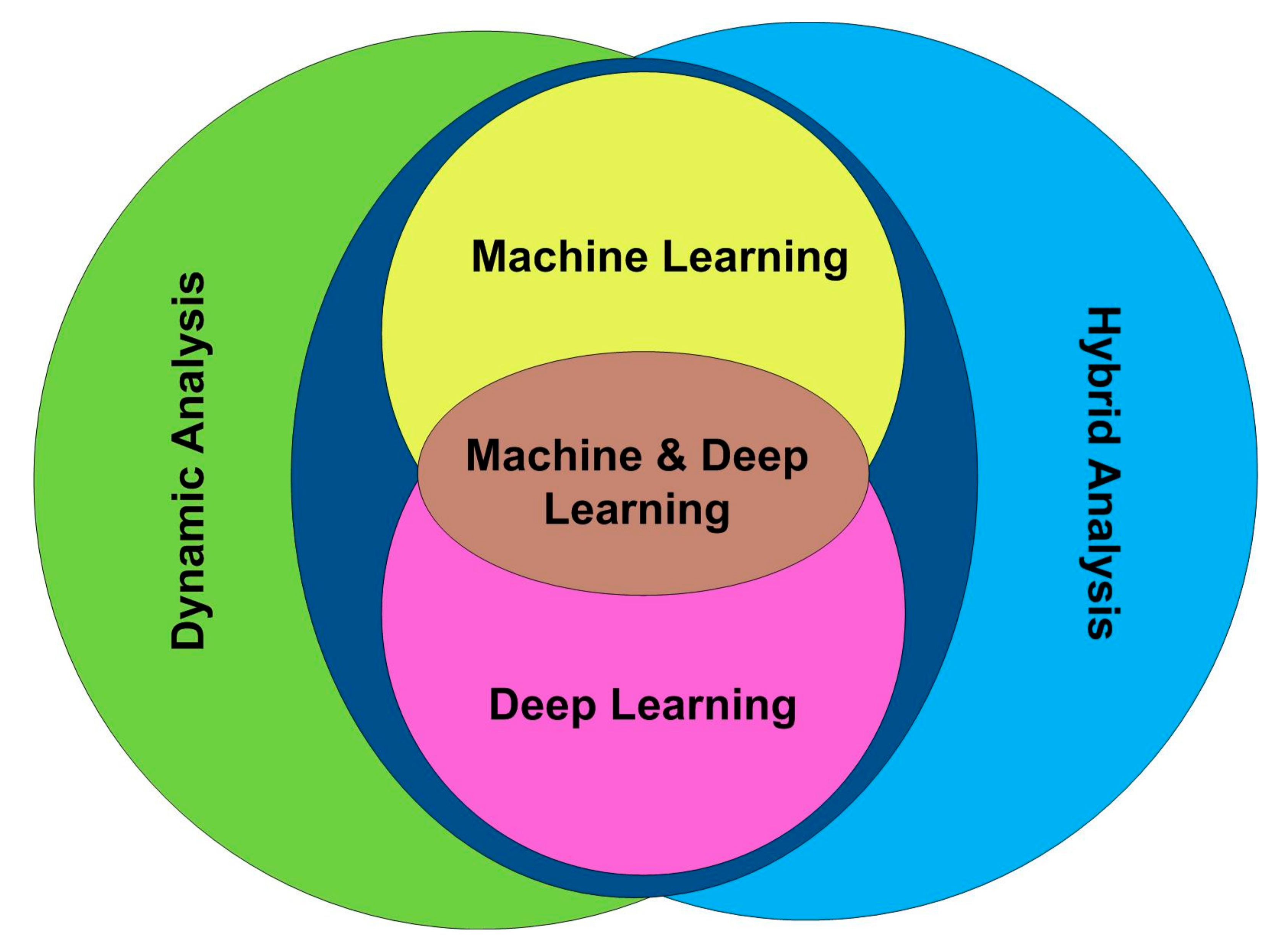
6.1.2. Dynamic Analysis
- I.
- Ransomware Dynamic Analysis Studies Utilizing Machine Learning
- II.
- Ransomware Dynamic Analysis Studies Utilizing Deep Learning
- III.
- Ransomware Dynamic Analysis Studies Utilizing both Machine Learning and Deep Learning
6.1.3. Hybrid Analysis
- I.
- Ransomware Hybrid Analysis Studies Utilizing Machine Learning
- II.
- Ransomware Hybrid Analysis Studies Utilizing Deep Learning
- III.
- Ransomware Hybrid Analysis Studies Utilizing Both Machine Learning and Deep Learning
6.1.4. Limitation of Analysis Performed in Ransomware Detection Studies
- Ransomware that are developed using its own encryption mechanism may evade analysis.
- Static analysis has limited scope because of higher false alarms and limited accuracy.
- Ransomware that fingerprints the environment, can bypass the analysis.
- Few studies did not mention details about the dataset and analysis.
- Analysis carried out for the fixed time could helped the evasion techniques.
- Availability of limited amount of data in the initial stage of encryption process.
- The ransomware using obfuscation and evasion techniques are difficult to discover.
- Ransomware samples run for the short time could evade the detection.
- Some of the studies lack in defining the source of dataset and number of samples used.
- Some of the detection studies cannot detect the system API calls or encrypted operations that run during execution.
- Runtime detection programs could be infected to malicious programs. The hardware data can be corrupted due to malicious program.
6.2. Ransomware Counteraction
6.2.1. Prediction
6.2.2. Prevention
- I.
- Proactive Prevention
- II.
- Reactive Prevention
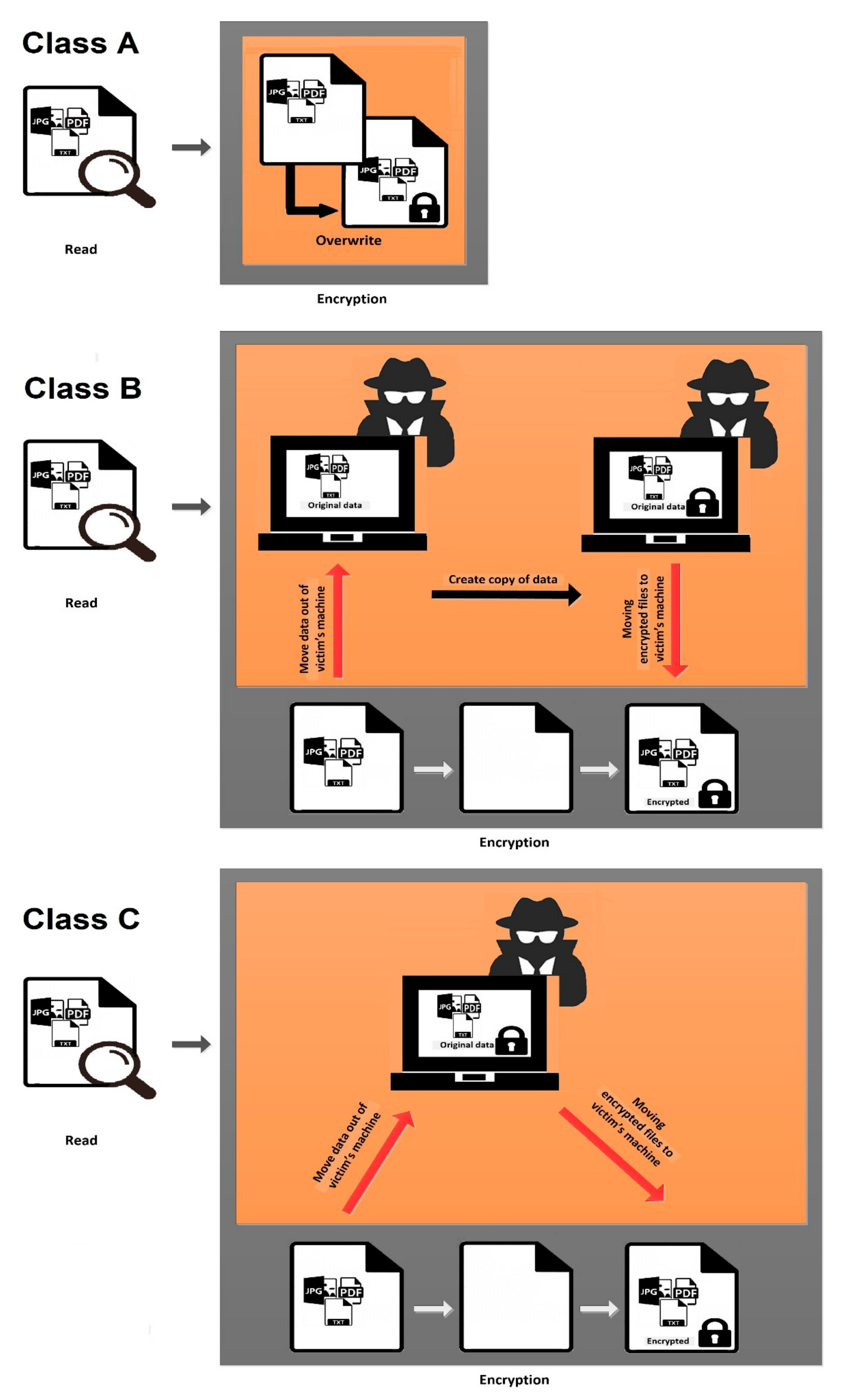
6.2.3. Detection
- A.
- Ransomware Detection Studies w.r.t. Pre and Post Encryption
- I.
- Conventional Detection Studies
- i.
- Conventional Detection Studies Utilizing Machine Learning
- ii.
- Conventional Detection Studies Utilizing Deep Learning
- iii.
- Conventional Detection Studies Utilizing Both Machine Learning and Deep Learning
- II.
- Early Detection or Pre-Encryption Studies
- i.
- Early Detection Studies Utilizing Machine Learning
- ii.
- Early Detection Studies Utilizing Deep Learning
- iii.
- Early Detection Studies Utilizing Both Machine Learning and Deep Learning
- B.
- Limitations of Ransomware Detection Studies
- Most of the conducted studies for the ransomware detection fall under conventional class where ransomware is detected after the encryption starts.
- In the literature there is not a single study that deals with population drift concept while considering the pre-encryption early detection.
- High number of irrelevant and redundant system calls used to bypass the detection.
- Developed ransomware studies used different number of logs from different ransomware families.
- The ransomware detection systems are platform dependent. A system developed for windows API cannot be implemented for cloud and mobile devices.
- Ransomware detection study cannot detect the ransomware which encrypt data using its own native code.
- Not all the detection studies available in the literature are practical to implement. Some of the presented studies are empirical or supplement detection systems.
- Honeypot methods are not fully reliable as there is no guarantee the honeypot folders will always be accessed by the attack.
- Analyzing the samples for limited or ample time made the detection studies inadequate to implement.
- Dealing with little amount of data or massive data with high redundant values.
- Some of the studies did not explain well about the analysis performed for the detection.
- There are few studies that detected ransomware for the backup systems. More studies are needed in this domain.
- Datasets used to train data are synthetic and are extracted from specific sources, i.e., pseudo real world events.
7. Research Direction
- Dealing with computational and time complexities: The detection systems should be developed considering the computational overhead. A system should detect the ransomware attack in no time to make it valid. There should be detection systems with less time complexities. Specially for the devices with resources constrains, i.e., IoT and embedded systems.
- Dealing with hardware complexities: Most of the developed systems are hard disk supported having high RAM. System with limited hardware should also considered while developing a detection system. The more complex detection systems will incur the high cost. Some of the available solutions are also hardware dependent requiring advance hardware.
- Evasion and obfuscation: Ransomware development and detection is a non-stationary field which keep on evolving with time. Developing ransomware detection solutions should cope with ransomware evasion and obfuscation techniques. System which can deal with evasion and obfuscation will be more reliable with high accuracy and low false alarms.
- Real-time system: Most of the available studies in the ransomware detection are empirical and proposed. A real-time detection system with minimal time to response to the attack is required. Failing to provide the real-time detection will lead to irreversible encryption of some or all the data.
- Distributed environment: Most of the available ransomware detection solutions are developed for the desktops and mobile devices. There should more research on the spread of ransomware attack in a distributed environment. In a distributed network environment, most damage can be caused just by attacking a single device.
- Scalable and adaptive: The developed solutions for the ransomware should be scalable so that they can deal with detection on multiple machines, i.e., improving the detection capabilities. The new ransomware detection model should be scalable to the advance ransomware and newly updated datasets. With the passage of time new and more sophisticated ransomware samples are being developed. These advanced ransomwares can be dealt well with the adaptive and scalable ransomware detection model.
- Forensic by design concept: The integration of forensics by design and ransomware detection system would reduce the loss. Use of forensic by design will help to detect, mitigate, and roll back the ransomware attacks. This will also help in forensic investigation.
- Use of fuzzy modelling: With the evolution of ransomware attacks there should be an automatic computation system for the ransomware. This will assess the damage to a zero-day ransomware attack. This fuzzy system will also help to detect the ransomware attacks based on the feature obtained after automatic analysis.
- Use of stream data mining: Stream data mining can be used to reduce the ransomware detection time as this method works well with high dimensional and rapidly changing data. The integration of stream data mining will also bring the optimal solution for ransomware detection.
- Feature reduction for deep learning models: The deep learning models requires plenty of data to get train and make decision. While in the ransomware detection only little data is available before encryption happens. So, there should be feature reduction methods for the deep learning networks.
- Development of Pre-Encryption detection systems: There are few studies available that are providing solution to early detection of ransomware attacks but still limited in the scope. Early detection is vital to restrain the ransomware attacks. Available solutions are limited and do not fit well to the advanced variants of ransomware.
- Rich Dataset: There should be a dataset that contains all the ransomware attack patterns which could be used to train the machine and deep learning models. This model should be updated periodically. There is not a single dataset available that can be used as a benchmark to the developing ransomware detection systems.
- Population drift: Ransomware is being populated day by day. Its variants are becoming more sophisticated with time. There should be detection studies which deal with population drift concept of ransomware.
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
Nomenclature
| Acronym | Description |
| TP | True Positive |
| NB | Naive Bayes |
| BN | Bayes Network |
| LR | Logistic Regression |
| RF | Random Forest |
| RT | Random Tree |
| DT | Decision Tree |
| ML | Machine Learning |
| DL | Deep Learning |
| IoT | Internet of Things |
| KNN | K-Nearest Neighbor |
| SVM | Support Vector Machine |
| SVC | Support Vector Classifier |
| SDN | Software Defined Networking |
| SGD | Stochastic Gradient Descent |
| SSD | Solid State Drive |
| DLL | Dynamic Link Library |
| CPU | Central Processing Unit |
| RNN | Recurrent Neural Network |
| DNN | Deep Neural Network |
| CNN | Convolutional Neural Network |
| LMT | Logistic Model Tree |
| MLP | Multilayer Perceptron |
| NLP | Natural Language Processing |
| PSO | Particle Swarm Optimization |
| BCS | Binary Cuckoo Search |
| GIGO | Garbage In, Garbage Out |
| LSTM | Long Short-Term Memory |
| MOGWO | Multi-Objective Grey Wolf Optimization |
| LIBSVM | Library for Support Vector Machine |
References
- Khalaf, B.A.; Mostafa, S.A.; Mustapha, A.; Mohammed, M.A.; Mahmoud, M.A.; Al-Rimy, B.A.S.; Abd Razak, S.; Elhoseny, M.; Marks, A. An Adaptive Protection of Flooding Attacks Model for Complex Network Environments. Secur. Commun. Netw. 2021, 2021, 5542919. [Google Scholar] [CrossRef]
- Maseer, Z.K.; Yusof, R.; Mostafa, S.A.; Bahaman, N.; Musa, O.; Al-rimy, B.A.S. DeepIoT. IDS: Hybrid Deep Learning for Enhancing IoT Network Intrusion Detection. CMC Comput. Mater. Contin. 2021, 69, 3945–3966. [Google Scholar]
- Young, A.; Yung, M. Cryptovirology: Extortion-Based security threats and countermeasures. In Proceedings of the 1996 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 6–8 May 1996; pp. 129–140. [Google Scholar]
- Aboaoja, F.A.; Zainal, A.; Ghaleb, F.A.; Al-rimy, B.A.S. Toward an Ensemble Behavioral-Based Early Evasive Malware Detection Framework. In Proceedings of the 2021 International Conference on Data Science and Its Applications (ICoDSA), Bandung, Indonesia, 6–7 October 2021; pp. 181–186. [Google Scholar]
- Alghofaili, Y.; Albattah, A.; Alrajeh, N.; Rassam, M.A.; Al-rimy, B.A.S. Secure Cloud Infrastructure: A Survey on Issues, Current Solutions, and Open Challenges. Appl. Sci. 2021, 11, 9005. [Google Scholar] [CrossRef]
- Zavarsky, P.; Lindskog, D. Experimental analysis of ransomware on windows and android platforms: Evolution and characterization. Procedia Comput. Sci. 2016, 94, 465–472. [Google Scholar]
- Fernandez Maimo, L.; Huertas Celdran, A.; Perales Gomez, A.L.; Garcia Clemente, F.J.; Weimer, J.; Lee, I. Intelligent and dynamic ransomware spread detection and mitigation in integrated clinical environments. Sensors 2019, 19, 1114. [Google Scholar] [CrossRef] [Green Version]
- Mercaldo, F.; Nardone, V.; Santone, A.; Visaggio, C.A. Ransomware steals your phone. Formal methods rescue it. In Proceedings of the International Conference on Formal Techniques for Distributed Objects, Components, and Systems, Heraklion, Crete, 6–9 June 2016; Springer: Cham, Switzerland, 2016; pp. 212–221. [Google Scholar]
- Scaife, N.; Carter, H.; Traynor, P.; Butler, K.R. Cryptolock (and drop it): Stopping ransomware attacks on user data. In Proceedings of the 2016 IEEE 36th International Conference on Distributed Computing Systems (ICDCS), Nara, Japan, 27–30 June 2016; pp. 303–312. [Google Scholar]
- Forestiero, A.; Mastroianni, C.; Spezzano, G. A Multi-Agent Approach for the. Self-Organ. Auton. Inform. 2005, 135, 220. [Google Scholar]
- Comito, C.; Forestiero, A.; Pizzuti, C. Word embedding based clustering to detect topics in social media. In Proceedings of the 2019 IEEE/WIC/ACM International Conference on Web Intelligence (WI), Thessaloniki, Greece, 14–17 October 2019; pp. 192–199. [Google Scholar]
- Forestiero, A.; Mastroianni, C.; Meo, M.; Papuzzo, G.; Sheikhalishahi, M. Hierarchical approach for green workload management in distributed data centers. In European Conference on Parallel Processing; Springer: Cham, Switzerland, 2014; pp. 323–334. [Google Scholar]
- Kharraz, A.; Robertson, W.; Balzarotti, D.; Bilge, L.; Kirda, E. Cutting the gordian knot: A look under the hood of ransomware attacks. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Milan, Italy, 9–10 July 2015; Springer: Cham, Switzerland, 2015; pp. 3–24. [Google Scholar]
- Kharaz, A.; Arshad, S.; Mulliner, C.; Robertson, W.; Kirda, E. {UNVEIL}: A large-scale, automated approach to detecting ransomware. In Proceedings of the 25th {USENIX} Security Symposium ({USENIX} Security 16), Austin, TX, USA, 10–12 August 2016; pp. 757–772. [Google Scholar]
- Popli, N.K.; Girdhar, A. Behavioural analysis of recent ransomwares and prediction of future attacks by polymorphic and metamorphic ransomware. In Computational Intelligence: Theories, Applications and Future Directions—Volume II; Springer: Singapore, 2019; pp. 65–80. [Google Scholar]
- Sharmeen, S.; Ahmed, Y.A.; Huda, S.; Koçer, B.Ş.; Hassan, M.M. Avoiding future digital extortion through robust protection against ransomware threats using deep learning based adaptive approaches. IEEE Access 2020, 8, 24522–24534. [Google Scholar] [CrossRef]
- Al-Rimy, B.A.S.; Maarof, M.A.; Alazab, M.; Alsolami, F.; Shaid, S.Z.M.; Ghaleb, F.A.; Al-Hadhrami, T.; Ali, A.M. A pseudo feedback-based annotated TF-IDF technique for dynamic crypto-ransomware pre-encryption boundary delineation and features extraction. IEEE Access 2020, 8, 140586–140598. [Google Scholar] [CrossRef]
- A Ghaleb, F.; Saeed, F.; Al-Sarem, M.; Ali Saleh Al-rimy, B.; Boulila, W.; Eljialy, A.; Aloufi, K.; Alazab, M. Misbehavior-Aware on-demand collaborative intrusion detection system using distributed ensemble learning for VANET. Electronics 2020, 9, 1411. [Google Scholar] [CrossRef]
- Geluvaraj, B.; Satwik, P.; Kumar, T.A. The future of cybersecurity: Major role of artificial intelligence, machine learning, and deep learning in cyberspace. In Proceedings of the International Conference on Computer Networks and Communication Technologies, Coimbatore, India, 23–24 May 2019; Springer: Singapore, 2019; pp. 739–747. [Google Scholar]
- Bae, S.I.; Lee, G.B.; Im, E.G. Ransomware detection using machine learning algorithms. Concurr. Comput. Pract. Exp. 2020, 32, e5422. [Google Scholar] [CrossRef]
- Krishnan, K.S.; Thampi, S.M. Deep Learning Approaches for IoT Security in the Big Data Era. In Combating Security Challenges in the Age of Big Data; Springer: Cham, Switzerland, 2020; pp. 105–135. [Google Scholar]
- Faris, H.; Habib, M.; Almomani, I.; Eshtay, M.; Aljarah, I. Optimizing extreme learning machines using chains of salps for efficient Android ransomware detection. Appl. Sci. 2020, 10, 3706. [Google Scholar] [CrossRef]
- Al-rimy, B.A.S.; Maarof, M.A.; Prasetyo, Y.A.; Shaid, S.Z.M.; Ariffin, A.F.M. Zero-day aware decision fusion-based model for crypto-ransomware early detection. Int. J. Integr. Eng. 2018, 10, 82–88. [Google Scholar] [CrossRef]
- Al-rimy, B.A.S.; Maarof, M.A.; Shaid, S.Z.M. Ransomware threat success factors, taxonomy, and countermeasures: A survey and research directions. Comput. Secur. 2018, 74, 144–166. [Google Scholar] [CrossRef]
- Herrera Silva, J.A.; Barona López, L.I.; Valdivieso Caraguay, Á.L.; Hernández-Álvarez, M. A Survey on Situational Awareness of Ransomware Attacks—Detection and Prevention Parameters. Remote Sens. 2019, 11, 1168. [Google Scholar] [CrossRef] [Green Version]
- Aurangzeb, S.; Aleem, M.; Iqbal, M.A.; Islam, M.A. Ransomware: A Survey and Trends. J. Inf. Assur. Secur. 2017, 6, 48–58. [Google Scholar]
- Kok, S.; Abdullah, A.; Jhanjhi, N.; Supramaniam, M. Ransomware, threat and detection techniques: A review. Int. J. Comput. Sci. Netw. Secur. 2019, 19, 136. [Google Scholar]
- Alzahrani, N.; Alghazzawi, D. A Review on Android Ransomware Detection Using Deep Learning Techniques. In Proceedings of the 11th International Conference on Management of Digital EcoSystems, Limassol, Cyprus, 12–14 November 2019; pp. 330–335. [Google Scholar]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.; Du, X.; Ali, I.; Guizani, M. A survey of machine and deep learning methods for internet of things (IoT) security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef] [Green Version]
- Tariq, M.I.; Memon, N.A.; Ahmed, S.; Tayyaba, S.; Mushtaq, M.T.; Mian, N.A.; Imran, M.; Ashraf, M.W. A Review of Deep Learning Security and Privacy Defensive Techniques. Mob. Inf. Syst. 2020, 2020, 6535834. [Google Scholar] [CrossRef]
- Berman, D.S.; Buczak, A.L.; Chavis, J.S.; Corbett, C.L. A survey of deep learning methods for cyber security. Information 2019, 10, 122. [Google Scholar] [CrossRef] [Green Version]
- Noorbehbahani, F.; Rasouli, F.; Saberi, M. Analysis of machine learning techniques for ransomware detection. In Proceedings of the 2019 16th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology (ISCISC), Mashhad, Iran, 28–29 August 2019; pp. 128–133. [Google Scholar]
- Fernando, D.W.; Komninos, N.; Chen, T. A Study on the Evolution of Ransomware Detection Using Machine Learning and Deep Learning Techniques. IOT 2020, 1, 30. [Google Scholar] [CrossRef]
- Oz, H.; Aris, A.; Levi, A.; Uluagac, A.S. A Survey on Ransomware: Evolution, Taxonomy, and Defense Solutions. arXiv 2021, arXiv:2102.06249. [Google Scholar]
- Sharma, S.; Kumar, R.; Rama Krishna, C. A survey on analysis and detection of Android ransomware. Concurr. Comput. Pract. Exp. 2021, 33, e6272. [Google Scholar] [CrossRef]
- Kumari, M. Application of Machine Learning and Deep Learning in Cybercrime Prevention—A Study. Int. J. Trend Res. Dev. 2019, 1–4. [Google Scholar]
- KP, S. A short review on Applications of Deep learning for Cyber security. arXiv 2018, arXiv:1812.06292. [Google Scholar]
- Humayun, M.; Jhanjhi, N.; Alsayat, A.; Ponnusamy, V. Internet of things and ransomware: Evolution, mitigation and prevention. Egypt. Inform. J. 2020, 22, 105–117. [Google Scholar] [CrossRef]
- Reshmi, T. Information security breaches due to ransomware attacks-a systematic literature review. Int. J. Inf. Manag. Data Insights 2021, 1, 100013. [Google Scholar] [CrossRef]
- Olaimat, M.N.; Maarof, M.A.; Al-rimy, B.A.S. Ransomware Anti-Analysis and Evasion Techniques: A Survey and Research Directions. In Proceedings of the 2021 3rd International Cyber Resilience Conference (CRC), Langkawi Island, Malaysia, 29–31 January 2021; pp. 1–6. [Google Scholar]
- Hu, J.W.; Zhang, Y.; Cui, Y.P. Research on Android ransomware protection technology. In Journal of Physics: Conference Series; IOP Publishing: Bristol, UK, 2020; p. 012004. [Google Scholar]
- Maigida, A.M.; Olalere, M.; Alhassan, J.K.; Chiroma, H.; Dada, E.G. Systematic literature review and metadata analysis of ransomware attacks and detection mechanisms. J. Reliab. Intell. Environ. 2019, 5, 67–89. [Google Scholar] [CrossRef]
- Sharma, B.; Mangrulkar, R. Deep learning applications in cyber security: A comprehensive review, challenges and prospects. Int. J. Eng. Appl. Sci. Technol. 2019, 4, 148–159. [Google Scholar] [CrossRef]
- Bello, I.; Chiroma, H.; Abdullahi, U.A.; Gital, A.Y.u.; Jauro, F.; Khan, A.; Okesola, J.O.; Shafi’i, M.A. Detecting ransomware attacks using intelligent algorithms: Recent development and next direction from deep learning and big data perspectives. J. Ambient. Intell. Humaniz. Comput. 2020, 12, 8699–8717. [Google Scholar] [CrossRef]
- Sneha, M.; Arya, A.; Agarwal, P. Ransomware Detection techniques in the Dawn of Artificial Intelligence: A Survey. In Proceedings of the 2020 the 9th International Conference on Networks, Communication and Computing, Tokyo, Japan, 18–20 December 2020; pp. 26–33. [Google Scholar]
- Urooj, U.; Maarof, M.A.B.; Al-rimy, B.A.S. A proposed Adaptive Pre-Encryption Crypto-Ransomware Early Detection Model. In Proceedings of the 2021 3rd International Cyber Resilience Conference (CRC), Langkawi Island, Malaysia, 29–31 January 2021; pp. 1–6. [Google Scholar]
- Mbol, F.; Robert, J.-M.; Sadighian, A. An efficient approach to detect torrentlocker ransomware in computer systems. In Proceedings of the International Conference on Cryptology and Network Security, Milan, Italy, 14–16 November 2016; Springer: Cham, Switzerland, 2016; pp. 532–541. [Google Scholar]
- Alrawashdeh, K.; Purdy, C. Ransomware detection using limited precision deep learning structure in fpga. In Proceedings of the NAECON 2018-IEEE National Aerospace and Electronics Conference, Dayton, OH, USA, 23–26 July 2018; pp. 152–157. [Google Scholar]
- Feng, Y.; Liu, C.; Liu, B. Poster: A new approach to detecting ransomware with deception. In Proceedings of the 38th IEEE Symposium on Security and Privacy Workshops, San Jose, CA, USA, 22–24 May 2017. [Google Scholar]
- Paik, J.-Y.; Shin, K.; Cho, E.-S. Poster: Self-defensible storage devices based on flash memory against ransomware. In Proceedings of the IEEE Symposium on Security and Privacy, San Jose, CA, USA, 23–25 May 2016. [Google Scholar]
- Bhardwaj, A.; Avasthi, V.; Sastry, H.; Subrahmanyam, G. Ransomware digital extortion: A rising new age threat. Indian J. Sci. Technol. 2016, 9, 1–5. [Google Scholar] [CrossRef]
- Al-Rimy, B.A.S.; Maarof, M.A.; Alazab, M.; Shaid, S.Z.M.; Ghaleb, F.A.; Almalawi, A.; Ali, A.M.; Al-Hadhrami, T. Redundancy coefficient gradual up-weighting-based mutual information feature selection technique for crypto-ransomware early detection. Future Gener. Comput. Syst. 2021, 115, 641–658. [Google Scholar] [CrossRef]
- Gazet, A. Comparative analysis of various ransomware virii. J. Comput. Virol. 2010, 6, 77–90. [Google Scholar] [CrossRef]
- Baek, S.; Jung, Y.; Mohaisen, A.; Lee, S.; Nyang, D. SSD-Assisted Ransomware Detection and Data Recovery Techniques. IEEE Trans. Comput. 2020, 70, 1762–1776. [Google Scholar] [CrossRef]
- Song, S.; Kim, B.; Lee, S. The effective ransomware prevention technique using process monitoring on android platform. Mob. Inf. Syst. 2016, 2016, 2946735. [Google Scholar] [CrossRef] [Green Version]
- Gómez-Hernández, J.A.; Álvarez-González, L.; García-Teodoro, P. R-Locker: Thwarting ransomware action through a honeyfile-based approach. Comput. Secur. 2018, 73, 389–398. [Google Scholar] [CrossRef] [Green Version]
- Maiorca, D.; Mercaldo, F.; Giacinto, G.; Visaggio, C.A.; Martinelli, F. R-PackDroid: API package-based characterization and detection of mobile ransomware. In Proceedings of the Symposium on Applied Computing, Marrakech, Morocco, 3–7 April 2017; pp. 1718–1723. [Google Scholar]
- Sgandurra, D.; Muñoz-González, L.; Mohsen, R.; Lupu, E.C. Automated dynamic analysis of ransomware: Benefits, limitations and use for detection. arXiv 2016, arXiv:1609.03020. [Google Scholar]
- Alhawi, O.M.; Baldwin, J.; Dehghantanha, A. Leveraging machine learning techniques for windows ransomware network traffic detection. In Cyber Threat Intelligence; Springer: Cham, Switzerland, 2018; pp. 93–106. [Google Scholar]
- Homayoun, S.; Dehghantanha, A.; Ahmadzadeh, M.; Hashemi, S.; Khayami, R. Know abnormal, find evil: Frequent pattern mining for ransomware threat hunting and intelligence. IEEE Trans. Emerg. Top. Comput. 2017, 8, 341–351. [Google Scholar] [CrossRef]
- Almomani, I.; Qaddoura, R.; Habib, M.; Alsoghyer, S.; Al Khayer, A.; Aljarah, I.; Faris, H. Android Ransomware Detection Based on a Hybrid Evolutionary Approach in the Context of Highly Imbalanced Data. IEEE Access 2021, 9, 57674–57691. [Google Scholar] [CrossRef]
- Homayoun, S.; Dehghantanha, A.; Ahmadzadeh, M.; Hashemi, S.; Khayami, R.; Choo, K.-K.R.; Newton, D.E. DRTHIS: Deep ransomware threat hunting and intelligence system at the fog layer. Future Gener. Comput. Syst. 2019, 90, 94–104. [Google Scholar] [CrossRef]
- Maniath, S.; Ashok, A.; Poornachandran, P.; Sujadevi, V.; Sankar, A.P.; Jan, S. Deep learning LSTM based ransomware detection. In Proceedings of the 2017 Recent Developments in Control, Automation & Power Engineering (RDCAPE), Noida, India, 26–27 October 2017; pp. 442–446. [Google Scholar]
- Vinayakumar, R.; Soman, K.; Velan, K.S.; Ganorkar, S. Evaluating shallow and deep networks for ransomware detection and classification. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Udupi, India, 13–16 September 2017; pp. 259–265. [Google Scholar]
- Gharib, A.; Ghorbani, A. Dna-droid: A real-time android ransomware detection framework. In International Conference on Network and System Security; Springer: Cham, Switzerland, 2017; pp. 184–198. [Google Scholar]
- Tseng, A.; Chen, Y.; Kao, Y.; Lin, T. Deep learning for ransomware detection. IEICE Tech. Rep. 2016, 116, 87–92. [Google Scholar]
- Kianpour, M.; Wen, S.-F. Timing attacks on machine learning: State of the art. In Proceedings of the SAI Intelligent Systems Conference, London, UK, 5–6 September 2019; pp. 111–125. [Google Scholar]
- Kurakin, A.; Goodfellow, I.; Bengio, S. Adversarial machine learning at scale. arXiv 2016, arXiv:1611.01236. [Google Scholar]
- Goodfellow, I.; McDaniel, P.; Papernot, N. Making machine learning robust against adversarial inputs. Commun. ACM 2018, 61, 56–66. [Google Scholar] [CrossRef]
- Ameer, M. Android Ransomware Detection Using Machine Learning Techniques to Mitigate Adversarial Evasion Attacks. Ph.D. Thesis, Capital University of Science and Technology, Islamabad, Pakistan, 2019. [Google Scholar]
- Cara, F.; Scalas, M.; Giacinto, G.; Maiorca, D. On the Feasibility of Adversarial Sample Creation Using the Android System API. Information 2020, 11, 433. [Google Scholar] [CrossRef]
- Andronio, N.; Zanero, S.; Maggi, F. Heldroid: Dissecting and detecting mobile ransomware. In Proceedings of the International Symposium on Recent Advances in Intrusion Detection, Kyoto, Japan, 2–4 November 2015; pp. 382–404. [Google Scholar]
- Zhang, H.; Xiao, X.; Mercaldo, F.; Ni, S.; Martinelli, F.; Sangaiah, A.K. Classification of ransomware families with machine learning based on N-Gram of opcodes. Future Gener. Comput. Syst. 2019, 90, 211–221. [Google Scholar] [CrossRef]
- Zhang, B.; Xiao, W.; Xiao, X.; Sangaiah, A.K.; Zhang, W.; Zhang, J. Ransomware classification using patch-based CNN and self-attention network on embedded N-grams of opcodes. Future Gener. Comput. Syst. 2020, 110, 708–720. [Google Scholar] [CrossRef]
- Moore, C. Detecting ransomware with honeypot techniques. In Proceedings of the 2016 Cybersecurity and Cyberforensics Conference (CCC), Amman, Jordan, 2–4 August 2016; pp. 77–81. [Google Scholar]
- Cabaj, K.; Gawkowski, P.; Grochowski, K.; Osojca, D. Network activity analysis of CryptoWall ransomware. Prz. Elektrotech. 2015, 91, 201–204. [Google Scholar] [CrossRef] [Green Version]
- Damodaran, A.; Di Troia, F.; Visaggio, C.A.; Austin, T.H.; Stamp, M. A comparison of static, dynamic, and hybrid analysis for malware detection. J. Comput. Virol. Hacking Tech. 2017, 13, 1–12. [Google Scholar] [CrossRef]
- Lokuketagoda, B.; Weerakoon, M.P.; Kuruppu, U.M.; Senarathne, A.N.; Abeywardena, K.Y. R-Killer: An email based ransomware protection tool. In Proceedings of the 2018 13th International Conference on Computer Science & Education (ICCSE), Colombo, Sri Lanka, 8–11 August 2018; pp. 1–7. [Google Scholar]
- Kok, S.; Abdullah, A.; Jhanjhi, N. Early detection of crypto-ransomware using pre-encryption detection algorithm. J. King Saud Univ.-Comput. Inf. Sci. 2020, in press. [Google Scholar] [CrossRef]
- Ashraf, A.; Aziz, A.; Zahoora, U.; Rajarajan, M.; Khan, A. Ransomware Analysis using Feature Engineering and Deep Neural Networks. arXiv 2019, arXiv:1910.00286. [Google Scholar]
- Alam, M.; Sinha, S.; Bhattacharya, S.; Dutta, S.; Mukhopadhyay, D.; Chattopadhyay, A. RAPPER: Ransomware prevention via performance counters. arXiv 2020, arXiv:2004.01712. [Google Scholar]
- Shukla, M.; Mondal, S.; Lodha, S. Poster: Locally virtualized environment for mitigating ransomware threat. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, New York, NY, USA, 24–28 October 2016; pp. 1784–1786. [Google Scholar]
- Silva, J.A.H.; Hernández-Alvarez, M. Large scale ransomware detection by cognitive security. In Proceedings of the 2017 IEEE Second Ecuador Technical Chapters Meeting (ETCM), Salinas, Ecuador, 16–20 October 2017; pp. 1–4. [Google Scholar]
- Al-rimy, B.A.S.; Maarof, M.A.; Shaid, S.Z.M. A 0-day aware crypto-ransomware early behavioral detection framework. In Proceedings of the International Conference of Reliable Information and Communication Technology, Johor Bahru, Malaysia, 23–24 April 2017; pp. 758–766. [Google Scholar]
- Roy, K.C.; Chen, Q. DeepRan: Attention-based BiLSTM and CRF for Ransomware Early Detection and Classifcation. Inf. Syst. Front. 2020, 23, 299–315. [Google Scholar] [CrossRef]
- Chandrasekar, K.; Cleary, G.; Cox, O.; Lau, H.; Nahorney, B.; Gorman, B.; O’Brien, D.; Wallace, S.; Wood, P.; Wueest, C. ISTR April 2017. Internet Secur. Threat. Rep.-Symantec 2017, 22, 77. [Google Scholar]
- Hwang, J.; Kim, J.; Lee, S.; Kim, K. Two-stage ransomware detection using dynamic analysis and machine learning techniques. Wirel. Pers. Commun. 2020, 112, 2597–2609. [Google Scholar] [CrossRef]
- Al-Hawawreh, M.; Sitnikova, E. Leveraging deep learning models for ransomware detection in the industrial internet of things environment. In Proceedings of the 2019 Military Communications and Information Systems Conference (MilCIS), Canberra, Australia, 12–14 November 2019; pp. 1–6. [Google Scholar]
- Al-Hawawreh, M.; Sitnikova, E. Industrial Internet of Things based ransomware detection using stacked variational neural network. In Proceedings of the 3rd International Conference on Big Data and Internet of Things, Melbourn, Australia, 22–24 August 2019; pp. 126–130. [Google Scholar]
- Lee, K.; Lee, S.-Y.; Yim, K. Machine learning based file entropy analysis for ransomware detection in backup systems. IEEE Access 2019, 7, 110205–110215. [Google Scholar] [CrossRef]
- Ahmadian, M.M.; Shahriari, H.R.; Ghaffarian, S.M. Connection-monitor & connection-breaker: A novel approach for prevention and detection of high survivable ransomwares. In Proceedings of the 2015 12th International Iranian Society of Cryptology Conference on Information Security and Cryptology (ISCISC), Rasht, Iran, 8–10 September 2015; pp. 79–84. [Google Scholar]
- Da-Yu, K.; HSIAO, S.-C.; Raylin, T. Analyzing WannaCry ransomware considering the weapons and exploits. In Proceedings of the 2019 21st International Conference on Advanced Communication Technology (ICACT), PyeongChang, Korea, 17–20 February 2019; pp. 1098–1107. [Google Scholar]
- Cusack, G.; Michel, O.; Keller, E. Machine learning-based detection of ransomware using SDN. In Proceedings of the 2018 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, Tempe, AZ, USA, 21 March 2018; pp. 1–6. [Google Scholar]
- Ahmed, Y.A.; Koçer, B.; Huda, S.; Al-rimy, B.A.S.; Hassan, M.M. A system call refinement-based enhanced Minimum Redundancy Maximum Relevance method for ransomware early detection. J. Netw. Comput. Appl. 2020, 167, 102753. [Google Scholar] [CrossRef]
- Al-rimy, B.A.S.; Maarof, M.A.; Shaid, S.Z.M. Crypto-ransomware early detection model using novel incremental bagging with enhanced semi-random subspace selection. Future Gener. Comput. Syst. 2019, 101, 476–491. [Google Scholar] [CrossRef]
- Zuhair, H.; Selamat, A. RANDS: A Machine Learning-Based Anti-Ransomware Tool for Windows Platforms. In Advancing Technology Industrialization Through Intelligent Software Methodologies, Tools and Techniques; IOS Press: Amsterdam, The Netherlands, 2019; pp. 573–587. [Google Scholar]
- Kok, S.; Azween, A.; Jhanjhi, N. Evaluation metric for crypto-ransomware detection using machine learning. J. Inf. Secur. Appl. 2020, 55, 102646. [Google Scholar] [CrossRef]
- Adamu, U.; Awan, I. Ransomware prediction using supervised learning algorithms. In Proceedings of the 2019 7th International Conference on Future Internet of Things and Cloud (FiCloud), Istanbul, Turkey, 26–28 August 2019; pp. 57–63. [Google Scholar]
- Chen, Q.; Islam, S.R.; Haswell, H.; Bridges, R.A. Automated ransomware behavior analysis: Pattern extraction and early detection. In Proceedings of the International Conference on Science of Cyber Security, Nanjing, China, 9–11 August 2019; pp. 199–214. [Google Scholar]
- Pundir, N.; Tehranipoor, M.; Rahman, F. RanStop: A Hardware-assisted Runtime Crypto-Ransomware Detection Technique. arXiv 2020, arXiv:2011.12248. [Google Scholar]
- Almashhadani, A.O.; Kaiiali, M.; Sezer, S.; O’Kane, P. A multi-classifier network-based crypto ransomware detection system: A case study of locky ransomware. IEEE Access 2019, 7, 47053–47067. [Google Scholar] [CrossRef]
- Bahrani, A.; Bidgly, A.J. Ransomware detection using process mining and classification algorithms. In Proceedings of the 2019 16th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology (ISCISC), Mashhad, Iran, 28–29 August 2019; pp. 73–77. [Google Scholar]
- Poudyal, S.; Dasgupta, D. AI-Powered Ransomware Detection Framework. In Proceedings of the 2020 IEEE Symposium Series on Computational Intelligence (SSCI), Canberra, Australia, 1–4 December 2020; pp. 1154–1161. [Google Scholar]
- Ahmed, Y.A.; Kocer, B.; Al-rimy, B.A.S. Automated Analysis Approach for the Detection of High Survivable Ransomware. KSII Trans. Internet Inf. Syst. 2020, 14, 2236–2257. [Google Scholar]
- Zuhair, H.; Selamat, A.; Krejcar, O. A Multi-Tier Streaming Analytics Model of 0-Day Ransomware Detection Using Machine Learning. Appl. Sci. 2020, 10, 3210. [Google Scholar] [CrossRef]
- Kok, S.; Abdullah, A.; Jhanjhi, N.; Supramaniam, M. Prevention of crypto-ransomware using a pre-encryption detection algorithm. Computers 2019, 8, 79. [Google Scholar] [CrossRef] [Green Version]
- Yang, C.-Y.; Sahita, R. Towards a Resilient Machine Learning Classifier-a Case Study of Ransomware Detection. arXiv 2020, arXiv:2003.06428. [Google Scholar]
- AbdulsalamYa’u, G.; Job, G.K.; Waziri, S.M.; Jaafar, B.; SabonGari, N.A.; Yakubu, I.Z. Deep Learning for Detecting Ransomware in Edge Computing Devices Based On Autoencoder Classifier. In Proceedings of the 2019 4th International Conference on Electrical, Electronics, Communication, Computer Technologies and Optimization Techniques (ICEECCOT), Mysuru, India, 13–14 December 2019; pp. 240–243. [Google Scholar]
- Basnet, M.; Poudyal, S.; Ali, M.; Dasgupta, D. Ransomware Detection Using Deep Learning in the SCADA System of Electric Vehicle Charging Station. arXiv 2021, arXiv:2104.07409. [Google Scholar]
- Ganfure, G.O.; Wu, C.-F.; Chang, Y.-H.; Shih, W.-K. DeepGuard: Deep Generative User-behavior Analytics for Ransomware Detection. In Proceedings of the 2020 IEEE International Conference on Intelligence and Security Informatics (ISI), Arlington, VA, USA, 9–10 November 2020; pp. 1–6. [Google Scholar]
- Nurnoby, M.F.; El-Alfy, E.-S.M. Overview and Case Study for Ransomware Classification Using Deep Neural Network. In Proceedings of the 2019 2nd IEEE Middle East and North Africa COMMunications Conference (MENACOMM), Manama, Bahrain, 19–21 November 2019; pp. 1–6. [Google Scholar]
- Ullah, F.; Javaid, Q.; Salam, A.; Ahmad, M.; Sarwar, N.; Shah, D.; Abrar, M. Modified Decision Tree Technique for Ransomware Detection at Runtime through API Calls. Sci. Program. 2020, 2020, 8845833. [Google Scholar] [CrossRef]
- Qin, B.; Wang, Y.; Ma, C. API Call Based Ransomware Dynamic Detection Approach Using TextCNN. In Proceedings of the 2020 International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE), Fuzhou, China, 12–14 June 2020; pp. 162–166. [Google Scholar]
- Aurangzeb, S.; Rais, R.N.B.; Aleem, M.; Islam, M.A.; Iqbal, M.A. On the classification of Microsoft-Windows ransomware using hardware profile. PeerJ. Comput. Sci. 2021, 7, e361. [Google Scholar] [CrossRef] [PubMed]
- Abdullah, Z.; Muhadi, F.W.; Saudi, M.M.; Hamid, I.R.A.; Foozy, C.F.M. Android ransomware detection based on dynamic obtained features. In Proceedings of the International Conference on Soft Computing and Data Mining, Langkawi, Malaysia, 22–23 January 2020; pp. 121–129. [Google Scholar]
- Ahmed, M.E.; Kim, H.; Camtepe, S.; Nepal, S. Peeler: Profiling Kernel-Level Events to Detect Ransomware. arXiv 2021, arXiv:2101.12434. [Google Scholar]
- Ayub, M.A.; Continella, A.; Siraj, A. An I/O Request Packet (IRP) Driven Effective Ransomware Detection Scheme using Artificial Neural Network. In Proceedings of the 2020 IEEE 21st International Conference on Information Reuse and Integration for Data Science (IRI), Las Vegas, NV, USA, 11–13 August 2020; pp. 319–324. [Google Scholar]
- Jethva, B.; Traoré, I.; Ghaleb, A.; Ganame, K.; Ahmed, S. Multilayer ransomware detection using grouped registry key operations, file entropy and file signature monitoring. J. Comput. Secur. 2020, 28, 337–373. [Google Scholar] [CrossRef]
- Alsoghyer, S.; Almomani, I. On the effectiveness of application permissions for Android ransomware detection. In Proceedings of the 2020 6th Conference on Data Science and Machine Learning Applications (CDMA), Riyadh, Saudi Arabia, 4–5 March 2020; pp. 94–99. [Google Scholar]
- Kim, D.; Kim, S. Design of quantification model for ransom ware prevent. World J. Eng. Technol. 2015, 3, 203. [Google Scholar] [CrossRef] [Green Version]
- Bajpai, P.; Enbody, R. Attacking key management in ransomware. IT Prof. 2020, 22, 21–27. [Google Scholar] [CrossRef]
- Kumari, A.; Bhuiyan, M.Z.A.; Namdeo, J.; Kanaujia, S.; Amin, R.; Vollala, S. Ransomware attack protection: A cryptographic approach. In Proceedings of the International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, Atlanta, GA, USA, 14–17 July 2019; pp. 15–25. [Google Scholar]
- Lei, I.-S.; Tang, S.-K.; Chao, I.-K.; Tse, R. Self-Recovery Service Securing Edge Server in IoT Network against Ransomware Attack. In Proceedings of the IoTBDS 2020, 5th International Conference on Internet of Things, Big Data and Security, Online Streaming, 7–9 May 2020; pp. 399–404. [Google Scholar]
- Monge, M.A.S.; Vidal, J.M.; Villalba, L.J.G. A novel self-organizing network solution towards crypto-ransomware mitigation. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg Germany, 27–28 August 2018; pp. 1–10. [Google Scholar]
- Mehnaz, S.; Mudgerikar, A.; Bertino, E. Rwguard: A real-time detection system against cryptographic ransomware. In International Symposium on Research in Attacks, Intrusions, and Defenses; Springer: Cham, Switzerland, 2018; pp. 114–136. [Google Scholar]
- Victoriano, O.B. Exposing android ransomware using machine learning. In Proceedings of the 2019 International Conference on Information System and System Management, Rabat, Morocco, 14–16 October 2019; pp. 32–37. [Google Scholar]
- Khan, F.; Ncube, C.; Ramasamy, L.K.; Kadry, S.; Nam, Y. A digital DNA sequencing engine for ransomware detection using machine learning. IEEE Access 2020, 8, 119710–119719. [Google Scholar] [CrossRef]
- Morato, D.; Berrueta, E.; Magaña, E.; Izal, M. Ransomware early detection by the analysis of file sharing traffic. J. Netw. Comput. Appl. 2018, 124, 14–32. [Google Scholar] [CrossRef]

| Ransomware Detection Approaches | |||||
|---|---|---|---|---|---|
| Sr# | Study | Misuse Based | Anomaly Based | ||
| Signature | Behavioral | Hybrid | |||
| 1 | [72] | ✓ | |||
| 2 | [9] | ✓ | |||
| 3 | [8] | ✓ | |||
| 4 | [75] | ✓ | |||
| 5 | [82] | ✓ | |||
| 6 | [78] | ✓ | |||
| 7 | [49] | ✓ | |||
| 8 | [83] | ✓ | |||
| 9 | [50] | ✓ | |||
| 10 | [57] | ✓ | |||
| 11 | [79] | ✓ | |||
| 12 | [76] | ✓ | |||
| 13 | [84] | ✓ | |||
| 14 | [73] | ✓ | |||
| 15 | [80] | ✓ | |||
| 16 | [85] | ✓ | |||
| 17 | [74] | ✓ | |||
| Ransomware Detection Studies w.r.t. Victim Platform | |||||||
|---|---|---|---|---|---|---|---|
| Sr# | Study | Desktop and Smartphone | IoT Ecosystem | Networks | |||
| PC | Smartphone | Cloud | Fog | IoT | |||
| 1 | [8] | ✓ | |||||
| 2 | [14] | ✓ | |||||
| 3 | [48] | ✓ | |||||
| 4 | [50] | ✓ | |||||
| 5 | [55] | ✓ | |||||
| 6 | [57] | ✓ | |||||
| 7 | [62] | ✓ | |||||
| 8 | [66] | ✓ | |||||
| 9 | [72] | ✓ | |||||
| 10 | [75] | ✓ | |||||
| 11 | [76] | ✓ | |||||
| 12 | [82] | ✓ | |||||
| 13 | [83] | ✓ | |||||
| 14 | [87] | ✓ | |||||
| 15 | [88] | ✓ | |||||
| 16 | [89] | ✓ | |||||
| 17 | [90] | ✓ | |||||
| 18 | [91] | ✓ | |||||
| Ransomware Datasets | |||||||
|---|---|---|---|---|---|---|---|
| Sr# | Study | Tool | Platform | Dataset Type | Family Name | Dataset Source | # of Samples |
| 1 | [94] | Cuckoo | Desktop Windows | Ransomware | VirusShare VirusTotal | 1354 | |
| Benign | Software-informer System 32 | 1358 | |||||
| 2 | [20] | Intel Pin 3.2 | Desktop Windows | Ransomware | VirusTotal | 1000 | |
| Malware | VirusTotal | 900 | |||||
| Benign | Windows 7 system directory | 300 | |||||
| 3 | [89] | Did not mention | Industrial IoT | Ransomware | NA | 582 | |
| Benign | Windows application | 942 | |||||
| 4 | DRTHIS [62] | Did not mention Event recorder | Fog Layer | Ransomware | VirusTotal | 660 | |
| Benign | NA | 219 | |||||
| 5 | RanSD [80] | Cuckoo | Windows | Static Dataset 3646 | Ransomware | VirusTotal VirusShare | 1700 |
| Goodware | Window 7 | 1946 | |||||
| Dynamic Dataset 3444 | Ransomware | VirusTotal VirusShare | 1455 | ||||
| Goodware | Window 7 | 1989 | |||||
| 6 | DeepRan [85] | Log Parser | Networks Bare metal server | Ransomware event logs | PC host logs | 17 | |
| Benign event logs | PC host logs | 103,330 | |||||
| 7 | [90] | Did not mentioned tool | Industrial IoT | Ransomware | Sgundara | NA | 582 |
| Benign | Sgundara | NA | 942 | ||||
| 8 | [95] | Cuckoo Sandbox | Ransomware | VirusShare | 8152 | ||
| Benign | Informer.com | 1000 | |||||
| 9 | RAPPER [81] | Cuckoo sandbox | Windows | Ransomware | Wannacry | NA | NA |
| Vipasana | |||||||
| Locky | |||||||
| Petya | |||||||
| Benign | NA | ||||||
| 10 | RANDS [96] | Virtual testbed | Windows | Ransomware | AiDS | VirusTotal Malware Blacklist | 400 |
| RaaS | 310 | ||||||
| GpCode | 800 | ||||||
| CryptoLocker | 720 | ||||||
| Archiveus | 1500 | ||||||
| CryptoWall | 3250 | ||||||
| WinLock | 2620 | ||||||
| Reveton | 400 | ||||||
| Benign | Website | 500 | |||||
| 11 | [97] | Cuckoo | Windows | Ransomware | VirusTotal Sgandurra theZoo | 357 | |
| 491 | |||||||
| 56 | |||||||
| Benign | Sgandurra | 942 | |||||
| 12 | [7] | Flow exporter Flow controller | IoT | Ransomware | Wannacry | 50,537 | |
| Petya | |||||||
| BadRabbit | |||||||
| PowerGhost | |||||||
| Benign | Network Traffic generated by Integrated Clinical Environment (ICE) | 100,000 | |||||
| 13 | [98] | Did not mention | Windows | Ransomware | RISS of ICL machine learning online repository | 582 | |
| Goodware | 942 | ||||||
| 14 | PEDA [79] | Cuckoo | Windows | Ransomware | Sgandurra | VirusShare VS malware repository theZoo | 995 |
| Goodware | NA | 942 | |||||
| 15 | [99] | Cuckoo | Host in Security Operation Centre | Ransomware attacked logs | WannaCry | Infected System logs | NA |
| DBGer | |||||||
| Defray | |||||||
| Locky | |||||||
| Cerber | |||||||
| GandCrab | |||||||
| nRansom | |||||||
| Non attacked logs | Uninfected logs | NA | |||||
| 16 | RanStop [100] | Monitoring of micro-architectural events using hardware performance counter | Windows | Ransomware | VirusShare | 80 | |
| Goodware | OpenSSL C programs | 76 | |||||
| 17 | [101] | Python script and MATLAB | Networks | Dataset created by the network traffic of Malware Capture Facility Project (MCFP) | |||
| 18 | [91] | User clint software | Backup Systems | Encrypted files | System files Documents Images Source code Executables Compressed | NA | 600 |
| Normal files | System files Documents Images Source code Executables Compressed | NA | 600 | ||||
| 19 | [102] | Virtual machine, Disco, and process monitoring | Windows | Ransomware | VirusShare | NA | |
| Benign | NA | NA | |||||
| 20 | AIRaD [103] | Sandbox | Windows | Ransomware | VirusTotal | 550 | |
| Benign | Windows 10 Open Source Software | 540 | |||||
| 21 | [104] | Cuckoo | Windows | Ransomware 1254 | TeslaCrypt | VirusShare VirusTotal | 96 |
| Petya | 89 | ||||||
| Pgpcoder | 46 | ||||||
| Reveton | 50 | ||||||
| CryptoWall | 151 | ||||||
| Kollah | 73 | ||||||
| Kovter | 23 | ||||||
| Citroni | 67 | ||||||
| Trojan | 82 | ||||||
| CryptLocker | 173 | ||||||
| Torrent Locker | 108 | ||||||
| Cerber | 171 | ||||||
| WannaCry | 74 | ||||||
| Dirty Decrypt | 51 | ||||||
| Benign 1308 | Software.informer System32 of Win7 Pro | NA | |||||
| 22 | [105] | Weka and Python code | NA | Ransomware 35015 | Archiveus | VirusTotal VirusShare | 1500 |
| CryptoLocker | 1720 | ||||||
| AiDS | 4000 | ||||||
| RaaS | 1300 | ||||||
| Zeus | 1500 | ||||||
| Locky | 2000 | ||||||
| GpCode | 8000 | ||||||
| CryptoWall | 3250 | ||||||
| Crysis | 1320 | ||||||
| WinLock | 3620 | ||||||
| WannaCry | 1300 | ||||||
| Sopra | 1570 | ||||||
| Reveton | 2400 | ||||||
| Cerber | 1535 | ||||||
| Malware | 500 | ||||||
| Goodware | Developed with Software | 500 | |||||
| 23 | [106] | Cuckoo | Windows | Ransomware 582 | CryptoLocker | Resilient Information System Security (RISS) dataset | 107 |
| Reveton | 90 | ||||||
| Kovter | 64 | ||||||
| Critroni | 50 | ||||||
| TeslaCrypt | 6 | ||||||
| Locker | 97 | ||||||
| CryptoWall | 46 | ||||||
| MATSNU | 59 | ||||||
| KOLLAH | 25 | ||||||
| GPCODER | 4 | ||||||
| Trojan-Ransom | 34 | ||||||
| Goodware | 942 | ||||||
| 24 | [88] | Cuckoo | Windows | Ransomware | VirusShare | 1909 | |
| Benign | Softonic | 1139 | |||||
| 25 | [107] | Cuckoo Sandbox | Windows | Ransomware | VirusTotal | 22,000 | |
| Benign | Windows | 100 | |||||
| 26 | [108] | Cuckoo | Edge Computing | Ransomware | Resilient Information Security System (RISS) | 582 | |
| Benign | 942 | ||||||
| 27 | [16] | Cuckoo Sandbox | Windows | Ransomware 1232 | CryptoWall | VirusShare VirusTotal Malwarebytes Offensive-Computing | 151 |
| Trojan Ransom | 82 | ||||||
| TeslaCrypt | 74 | ||||||
| Kollah | 73 | ||||||
| Reveton | 50 | ||||||
| Citroni | 67 | ||||||
| TorrentLocker | 108 | ||||||
| Pgpcoder | 46 | ||||||
| Dirty Decrypt | 51 | ||||||
| Kovter | 23 | ||||||
| CryptoLocker | 173 | ||||||
| Petya | 89 | ||||||
| Cerber | 171 | ||||||
| WannaCry | 74 | ||||||
| Benign | Software-informer System 32 of Windows 7 Pro | 1308 | |||||
| 28 | [109] | PIN tool and Custom Python program | Supervisory control and data acquisition systems (SCADA) | Ransomware | VirusTotal | 561 | |
| Benign | Windows | 447 | |||||
| 29 | DeepGuard [110] | Cuckoo | Windows | Ransomware | VirusShare | 2000 | |
| Goodware | System logs | 2000 | |||||
| 30 | [111] | Cuckoo Sandbox | Windows/Mac/Mobile | Ransomware | Sgandurra | 582 | |
| Benign | 360 | ||||||
| 31 | [112] | Did not mention | Desktop | Ransomware | VirusTotal | 35,369 | |
| Benign | 43,191 | ||||||
| 32 | DRDT [113] | Cuckoo | Windows | Ransomware | Sangfor Technologies Incorporation | 1000 | |
| Benign | 1000 | ||||||
| 33 | [114] | Cuckoo Sandbox | Windows | Ransomware | NA | 80 | |
| Non-Ransomware | NA | 80 | |||||
| 34 | [115] | Genymotion | Mobile Android | Ransomware | VirusTotal | 400 | |
| Benign apps | GooglePlay Store | 400 | |||||
| 35 | Peeler [116] | I/O patterns observation from Process execution patterns | Windows | Ransomware | Cerber | VirusTotal MalwareBazaar theZoo Malware samples from github | 33 |
| Sodinokibi | 14 | ||||||
| GoldenEye | 12 | ||||||
| Sage | 5 | ||||||
| Locky | 5 | ||||||
| Dharma | 3 | ||||||
| dotExe | 3 | ||||||
| WannaCry | 3 | ||||||
| Xorist | 2 | ||||||
| Virlock.Gen.5 | 83 | ||||||
| LockScree.AGU | 12 | ||||||
| Alphabet | 2 | ||||||
| Other | 29 | ||||||
| Benign | |||||||
| 36 | [117] | Did not mention | Windows | Ransomware | CryptoWall | VirusTotal | 17 |
| Deshacop | 2 | ||||||
| CryptoDefense | 6 | ||||||
| Upatre | 56 | ||||||
| Zbot | 6 | ||||||
| Critroni | 2 | ||||||
| Yakes | 150 | ||||||
| Crowti | 23 | ||||||
| Others | 10 | ||||||
| Benign | Windows 7, 8.1, 10 logs | NA | |||||
| 37 | [118] | Cuckoo Sandbox | Windows | Ransomware 666 | TeslaCrypt | VirusTotal | 348 |
| CryptoShield | 4 | ||||||
| Cerber | 122 | ||||||
| Crysis | 8 | ||||||
| Sage | 5 | ||||||
| Unlock26 | 3 | ||||||
| Locky | 129 | ||||||
| CryptoMix | 2 | ||||||
| Petya | 2 | ||||||
| WannaCry | 1 | ||||||
| Flawed | 1 | ||||||
| Benign | Software repository website | 103 | |||||
| Ransomware Analysis | |||||||
|---|---|---|---|---|---|---|---|
| Sr# | Study | Dynamic | Hybrid | ||||
| ML | DL | ML and DL | ML | DL | ML and DL | ||
| 1 | [94] | ✓ | |||||
| 2 | [20] | ✓ | |||||
| 3 | [89] | ✓ | |||||
| 4 | [62] | ✓ | |||||
| 5 | [80] | ✓ | |||||
| 6 | [85] | ✓ | |||||
| 7 | [90] | ✓ | |||||
| 8 | [81] | ✓ | |||||
| 9 | [119] | ✓ | |||||
| 10 | RANDS [96] | ✓ | |||||
| 11 | [97] | ✓ | |||||
| 12 | [7] | ✓ | |||||
| 13 | [98] | ✓ | |||||
| 14 | PEDA [79] | ✓ | |||||
| 15 | [99] | ✓ | |||||
| 16 | RanStop [100] | ✓ | |||||
| 17 | [101] | ✓ | |||||
| 18 | [91] | ✓ | |||||
| 19 | [95] | ✓ | |||||
| 20 | [102] | ✓ | |||||
| 21 | [118] | ✓ | |||||
| 22 | AIRaD [103] | ✓ | |||||
| 23 | [104] | ✓ | |||||
| 24 | [105] | ✓ | |||||
| 25 | [106] | ✓ | |||||
| 26 | [88] | ✓ | |||||
| 27 | [107] | ✓ | |||||
| 28 | [108] | ✓ | |||||
| 29 | [16] | ✓ | |||||
| 30 | [109] | ✓ | |||||
| 31 | DeepGuard [110] | ✓ | |||||
| 32 | [112] | ✓ | |||||
| 33 | DRDT [113] | ✓ | |||||
| Counteraction Studies | |||||
|---|---|---|---|---|---|
| Sr# | Study | Detection | Prediction | Prevention | |
| Proactive | Reactive | ||||
| 1 | [120] | ✓ | |||
| 2 | [93] | ✓ | ✓ | ||
| 3 | [66] | ✓ | |||
| 4 | [119] | ✓ | |||
| 5 | [76] | ✓ | |||
| 6 | [8] | ✓ | |||
| 7 | [55] | ✓ | |||
| 8 | [14] | ✓ | |||
| 9 | [98] | ✓ | |||
| 10 | [50] | ✓ | |||
| 11 | [82] | ✓ | |||
| 12 | [57] | ✓ | |||
| 13 | [83] | ✓ | ✓ | ||
| 14 | [48] | ✓ | |||
| 15 | [61] | ✓ | |||
| 16 | [81] | ✓ | |||
| 17 | [109] | ✓ | |||
| 18 | [91] | ✓ | |||
| Detection Studies w.r.t. Pre and Post Encryption | |||||||
|---|---|---|---|---|---|---|---|
| Sr# | Study | Conventional | Early/Pre-Encryption | ||||
| ML | DL | ML and DL | ML | DL | ML and DL | ||
| 1 | [94] | ✓ | |||||
| 2 | [20] | ✓ | |||||
| 3 | [89] | ✓ | |||||
| 4 | DRTHIS [62] | ✓ | |||||
| 5 | RanSD [80] | ✓ | |||||
| 6 | DeepRan [85] | ✓ | |||||
| 7 | [90] | ✓ | |||||
| 8 | RAPPER [81] | ✓ | |||||
| 9 | [119] | ✓ | |||||
| 10 | RANDS [96] | ✓ | |||||
| 11 | [97] | ✓ | |||||
| 12 | [7] | ✓ | |||||
| 13 | [126] | ✓ | |||||
| 14 | [98] | ✓ | |||||
| 15 | PEDA [79] | ✓ | |||||
| 16 | [99] | ✓ | |||||
| 17 | RanStop [100] | ✓ | |||||
| 18 | [101] | ✓ | |||||
| 19 | [91] | ✓ | |||||
| 20 | [32] | ✓ | |||||
| 21 | [102] | ✓ | |||||
| 22 | [127] | ✓ | |||||
| 23 | [103] | ✓ | |||||
| 24 | [104] | ✓ | |||||
| 25 | [105] | ✓ | |||||
| 26 | [106] | ✓ | |||||
| 27 | [88] | ✓ | |||||
| 28 | [107] | ✓ | |||||
| 29 | [108] | ✓ | |||||
| 30 | [16] | ✓ | |||||
| 31 | [109] | ✓ | |||||
| 32 | DeepGuard [110] | ✓ | |||||
| 33 | DRDT [113] | ✓ | |||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Urooj, U.; Al-rimy, B.A.S.; Zainal, A.; Ghaleb, F.A.; Rassam, M.A. Ransomware Detection Using the Dynamic Analysis and Machine Learning: A Survey and Research Directions. Appl. Sci. 2022, 12, 172. https://doi.org/10.3390/app12010172
Urooj U, Al-rimy BAS, Zainal A, Ghaleb FA, Rassam MA. Ransomware Detection Using the Dynamic Analysis and Machine Learning: A Survey and Research Directions. Applied Sciences. 2022; 12(1):172. https://doi.org/10.3390/app12010172
Chicago/Turabian StyleUrooj, Umara, Bander Ali Saleh Al-rimy, Anazida Zainal, Fuad A. Ghaleb, and Murad A. Rassam. 2022. "Ransomware Detection Using the Dynamic Analysis and Machine Learning: A Survey and Research Directions" Applied Sciences 12, no. 1: 172. https://doi.org/10.3390/app12010172
APA StyleUrooj, U., Al-rimy, B. A. S., Zainal, A., Ghaleb, F. A., & Rassam, M. A. (2022). Ransomware Detection Using the Dynamic Analysis and Machine Learning: A Survey and Research Directions. Applied Sciences, 12(1), 172. https://doi.org/10.3390/app12010172







