Dynamic Application Partitioning and Task-Scheduling Secure Schemes for Biosensor Healthcare Workload in Mobile Edge Cloud
Abstract
:1. Introduction
- Computation offloading plays a vital role in achieving optimal energy efficiency at the resource-constrained device, where computation-intensive workloads are offloaded to the server for execution. However, many parameters are considered during proposed application partitioning, such as bandwidth, execution time, and application deadline. Many existing offloading schemes during application partitioning consider pre-calculated parameters. However, many parameters can change during the runtime and require a dynamic and adaptive offloading scheme in the proposed architecture.
- Task scheduling is an NP-complete issue that involves scheduling tasks with heterogeneous resources based on a given constraint. It is never easy to schedule all jobs for complex resources so that the entire execution time stays within the constraints. Two types of failure could occur in a high-performance offloading system: intermittent network failure, and edge-cloud failure. Whenever a mobile user makes a dynamic decision to offload in a high-performance offloading system, the network connection or edge-cloud resource status becomes unstable during the offloading process. All rejected projects must be repaired within a set application deadline or completed locally if the available resources are sufficient. As mentioned earlier, a dynamic resubmission system, capable of correcting all rejected assignments while maintaining generosity, should be made available to address the problem.
- The task-scheduling problem in application partitioning has been widely solved based on HEFT (Heterogeneous Earliest Finish Time) approaches [5]. DAPWTS is the proposed algorithm scheme where many heuristics work together to achieve these goals. Initially, all applications are partitioned based on different metrics such as time, energy, and deadline based on the proposed min-cut algorithm. After partitioning, all tasks are prioritized based on their deadlines. All tasks are scheduled and maintain their failure status in the execution based on different schemes.
- The DAPWTS algorithm framework, in which data generated by sensors and profiling technologies develop real-time contents of the wireless network due to the real-time system, is explored. We offer a new task-scheduling mechanism that maps all mobile healthcare applications depending on their requirements. The proposed work scheduling approach relies heavily on the application deadline division and sequencing criteria.
- The study suggests an efficient failure-aware rescheduling approach that manages any failure with guaranteed performance in the proposed work.
- The secure min-cut algorithm is a weighted graph of mobile workflow applications that divides the graph into local and remote executions to minimize the makespan and energy of edges. Before delivering their data to the system cloud nodes, tasks are encrypted and decrypted locally. The secure min-cut algorithm’s primary purpose is to divide mobile workflow applications between local and remote-cloud execution depending on energy and time restrictions. The existing min-cut algorithms [7,9,11,12] focused solely on the security of jobs between their performance on various nodes, not on the safety of applications between local and cloud execution.
- The study devises the two phase-enabled security methods, ensuring data transaction security and storage security in the distributed mobile edge-cloud network.
2. Related Work
2.1. Task Partitioning Offloading Schemes
2.2. Task Allocation Schemes in Application Partitioning
2.3. Security Schemes in Application Partitioning
3. Problem Description
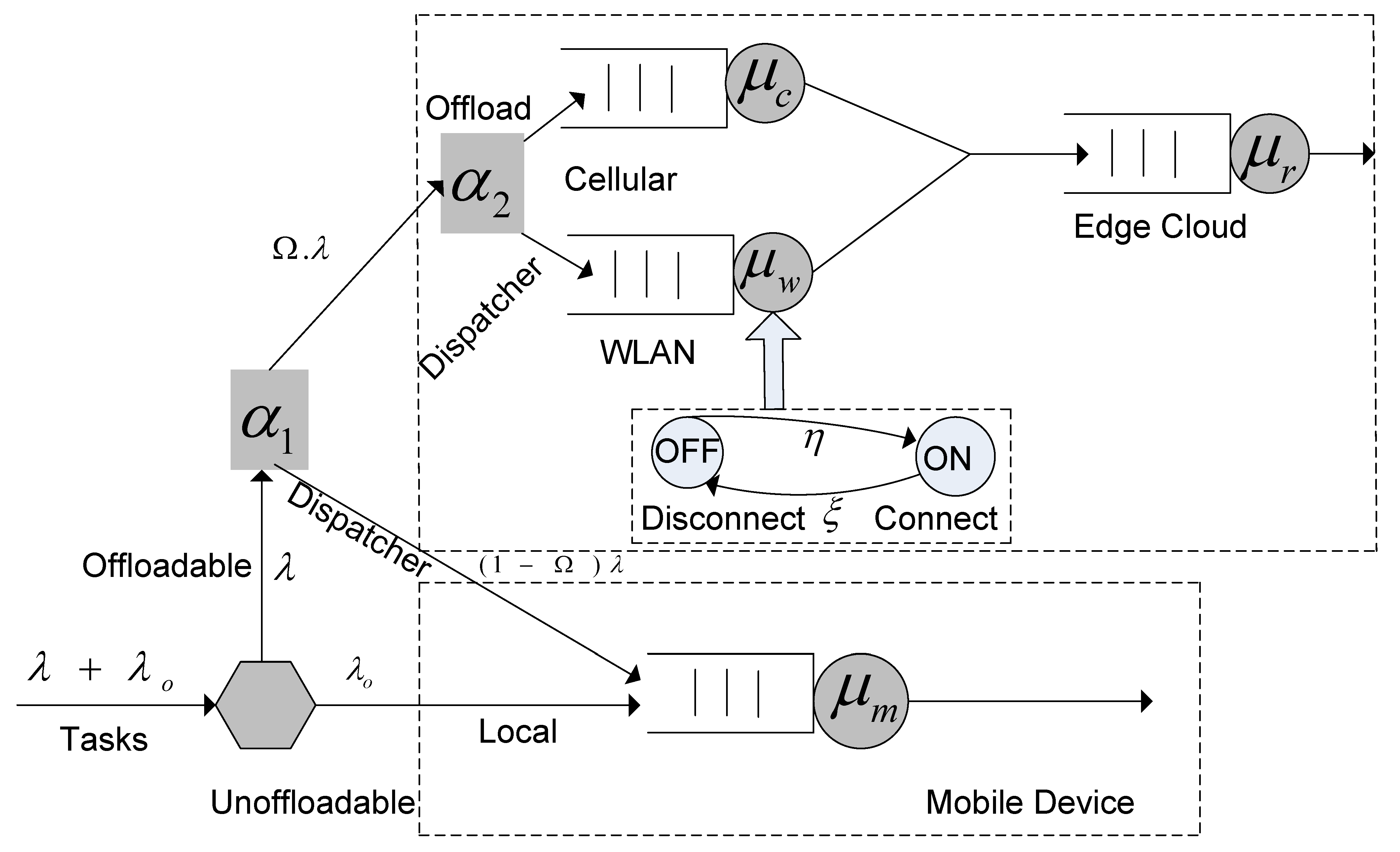
3.1. System Model and Problem Formulation
3.2. Application Energy Consumption
4. Proposed Algorithm DAPWTS Framework
| Algorithm 1: DAPWTS framework. |
| Input : ; |
| Output: ; |
 |
4.1. Secure Min-Cut Algorithm
| Algorithm 2: Min-Cut Algorithm. |
| Input : ; |
 |
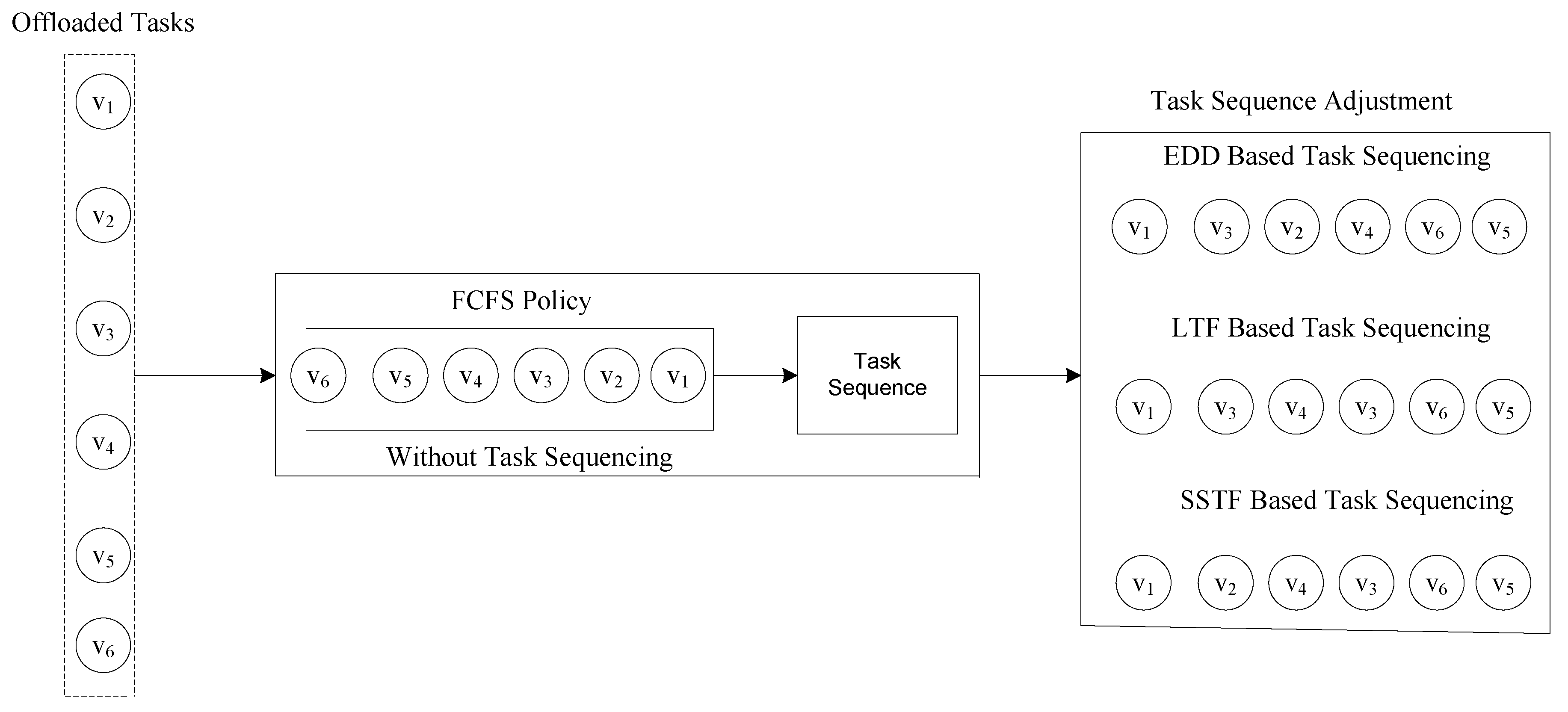
4.2. Task Sequencing
- Shortest deadline first (SDF): We sort the set of workflow applications based on their deadline. The smaller deadline application is sorted first and the bigger one later. If the deadlines are the same, then FCFS policy will be applied.
- Shortest slack time first (SSTF): The application tasks are sorted according to the task slack time (TST). The task which has the shortest slack time is scheduled first.
- Shortest weight first (SWF): The applications are sequenced based on the weight of all tasks, the shorter weight application arranged first and the bigger one later.
4.3. Optimal Power-Efficient Edge Node Searching
| Algorithm 3: Optimal edge-cloud node searching. |
| Input: () to Scheduling; |
 |
4.4. Energy-Efficient Task Scheduling
| Algorithm 4: Energy-efficient task scheduling. |
| Input : {,, , } ; |
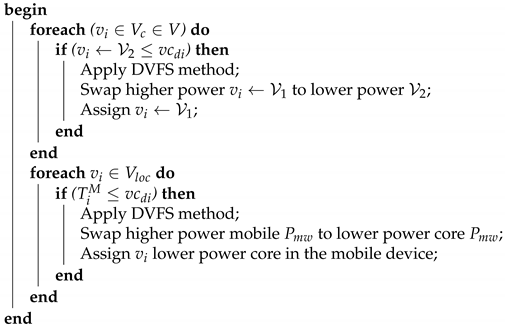 |
4.5. Failure-Aware Scenario
4.6. Failure task scheduling
| Algorithm 5: Failure-Aware Scheduling. |
| Input: (); |
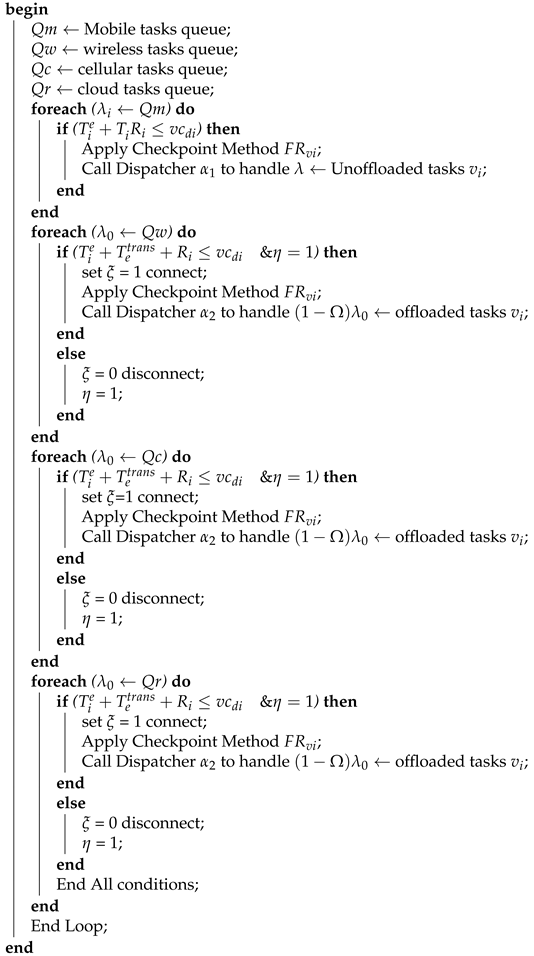 |
| End Main; |
- We manage the failure of tasks into the four queues, i.e., . denotes the mobile queue of failure tasks, illustrates the failure queue at the wireless network. and denote failure queues of cellular and cloud computing. denotes the failure of tasks at the mobile device, and shows the failure of offloaded tasks.
- Lines 6–19 show unoffloaded tasks that failed at the mobile device, and we apply the checkpointing technique to recover the task from the point of failure. If the recovery time and current execution are still less than the deadline, the dispatcher reads from the queue and tries to recover it. This process will continue until failed tasks recover successfully.
- Lines 10–14 show offloaded tasks that failed at the cellular network, and we apply the checkpointing technique to recover the task from the point of failure. If the recovery time, current execution, and communication time are still less than the deadline, the dispatcher reads from the queue and tries to recover it. This process will continue until failed tasks recover successfully. Lines 15–17 show the user changes its connections between cellular and wireless during mobility, and network status varies between on and off.
- Lines 18–22 show offloaded tasks that failed at the wireless network, and we apply the checkpointing technique to recover the task from the point of failure. If the recovery time, current execution, and communication time are still less than the deadline, the dispatcher reads from the queue and tries to recover it. This process will continue until failed tasks recover successfully. Lines 23–25 show that the user changes its cellular and wireless connections during mobility, and network status varies between on and off.
- Lines 26–30 show offloaded tasks that failed at the cloud resource, and we apply the checkpointing technique to recover the task from the point of failure. If the recovery time, current execution, and communication time are still less than the deadline, the dispatcher reads from the queue and tries to recover it. This process will continue until failed tasks recover successfully. Lines 31–36 show that the user changes its cellular and wireless connections during mobility, and network status varies between on and off. When all tasks are retrieved from the failed queue, the condition, loop, and main loop will be terminated.
4.7. Time Complexity
5. Performance Evaluation Simulation Setup
5.1. Baseline Approaches
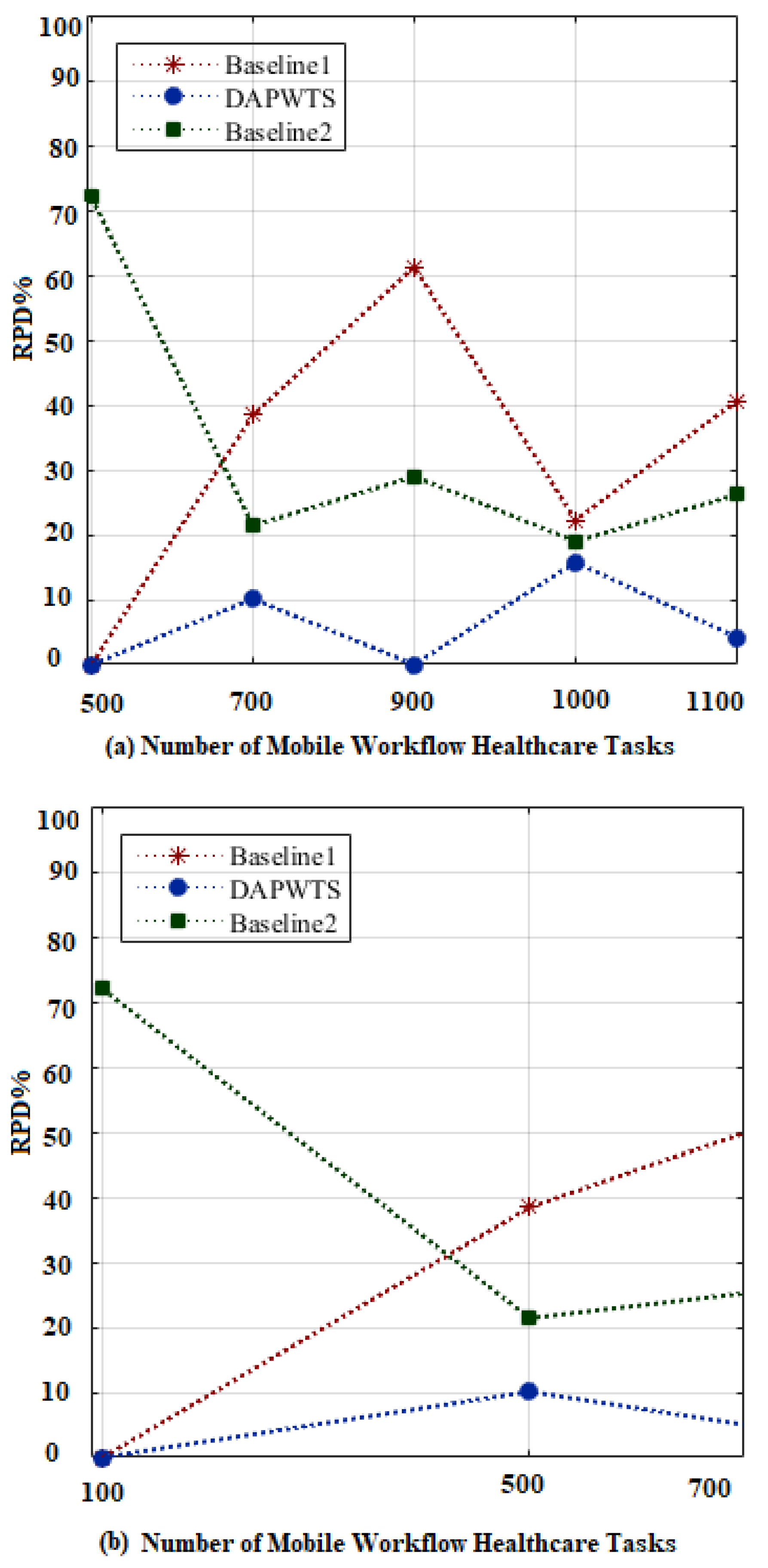
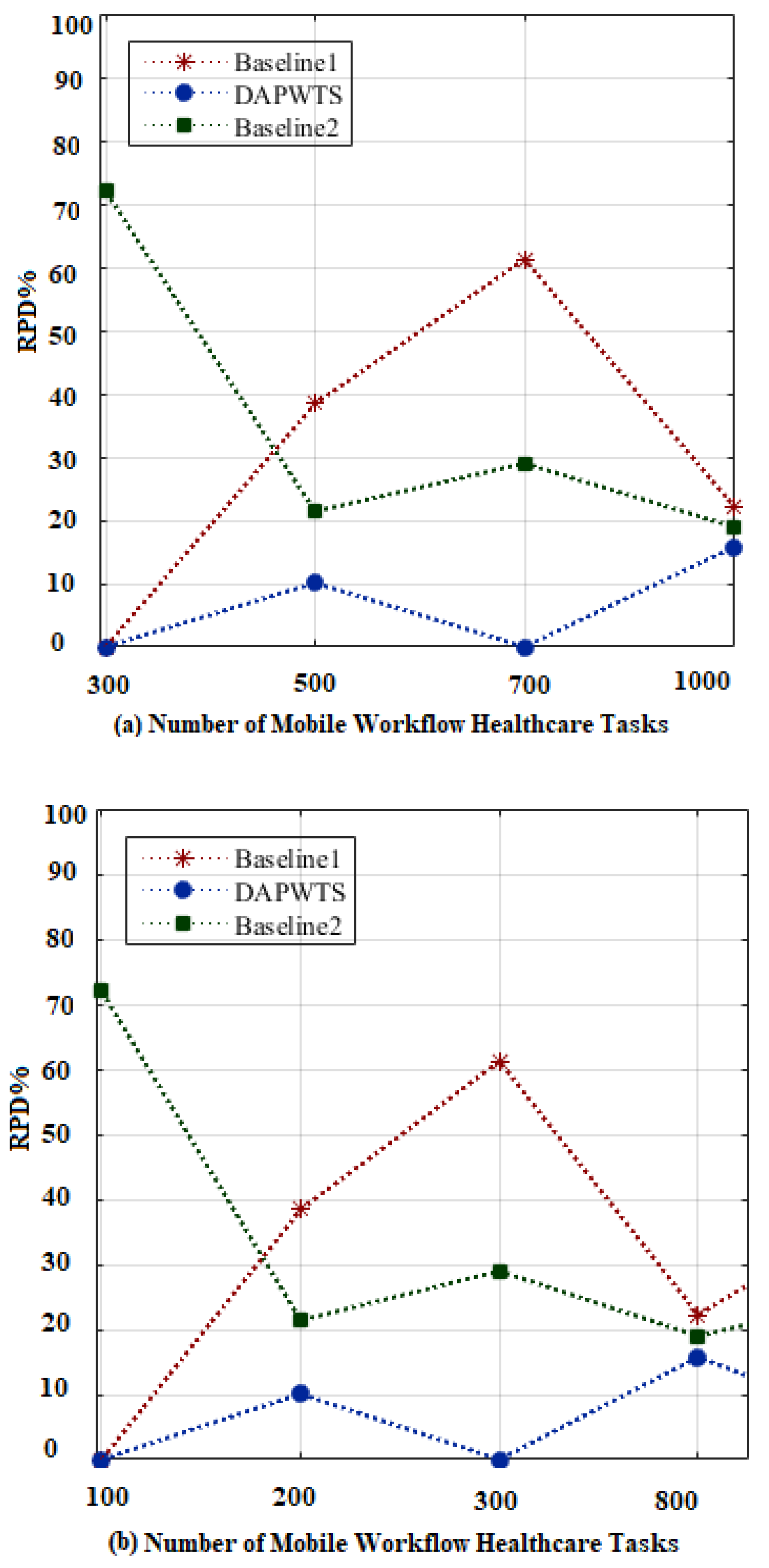
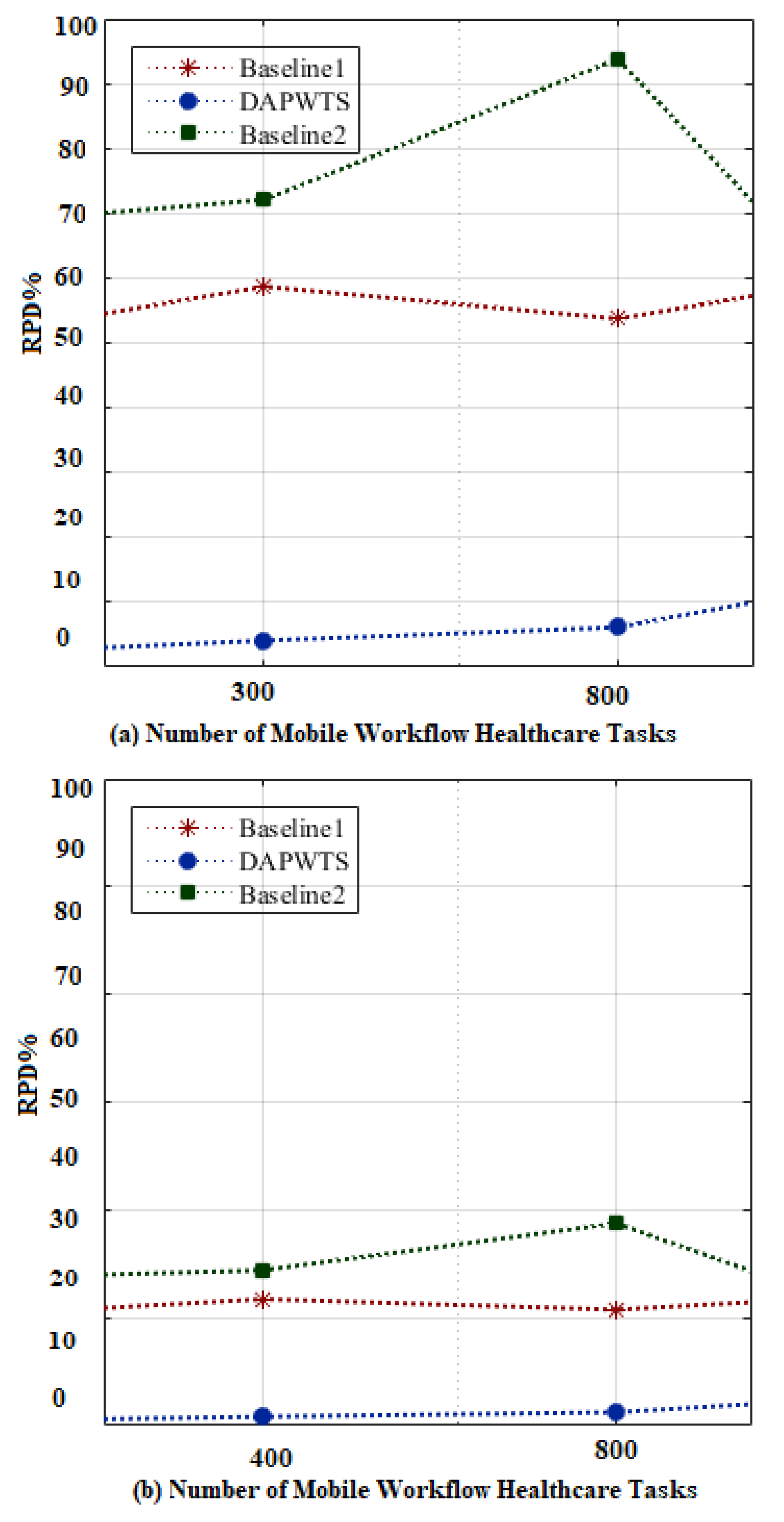
- Baseline1: This is a default min-cut scheme-enabled application partitioning and computational offloading method that allows running the entire workload locally or fully offloaded to the edge cloud. These kinds of schemes exploit many existing studies [7,8,9]. To evaluate the effectiveness and efficiency of DAPWTS, we implemented these environments for testing purposes and with our proposed system.
- Baseline2 [19,20]: This is the computational offloading scheme that allows the entire clone of the application to be submitted to the cloud system for execution. Numerous studies [11,13,16] have exploited this scheme to run different mobile workflow applications in their frameworks. It is a widely exploited offloading scheme that is adopted by many studies in the mobile cloud system. It enables the mobile workflow application to run onto distributed computing resources to obtain energy-consumption objectives efficiently. We implemented similar offloading in our DAPWTS framework to simultaneously maintain the trade-off between mobile energy and cloud energy.
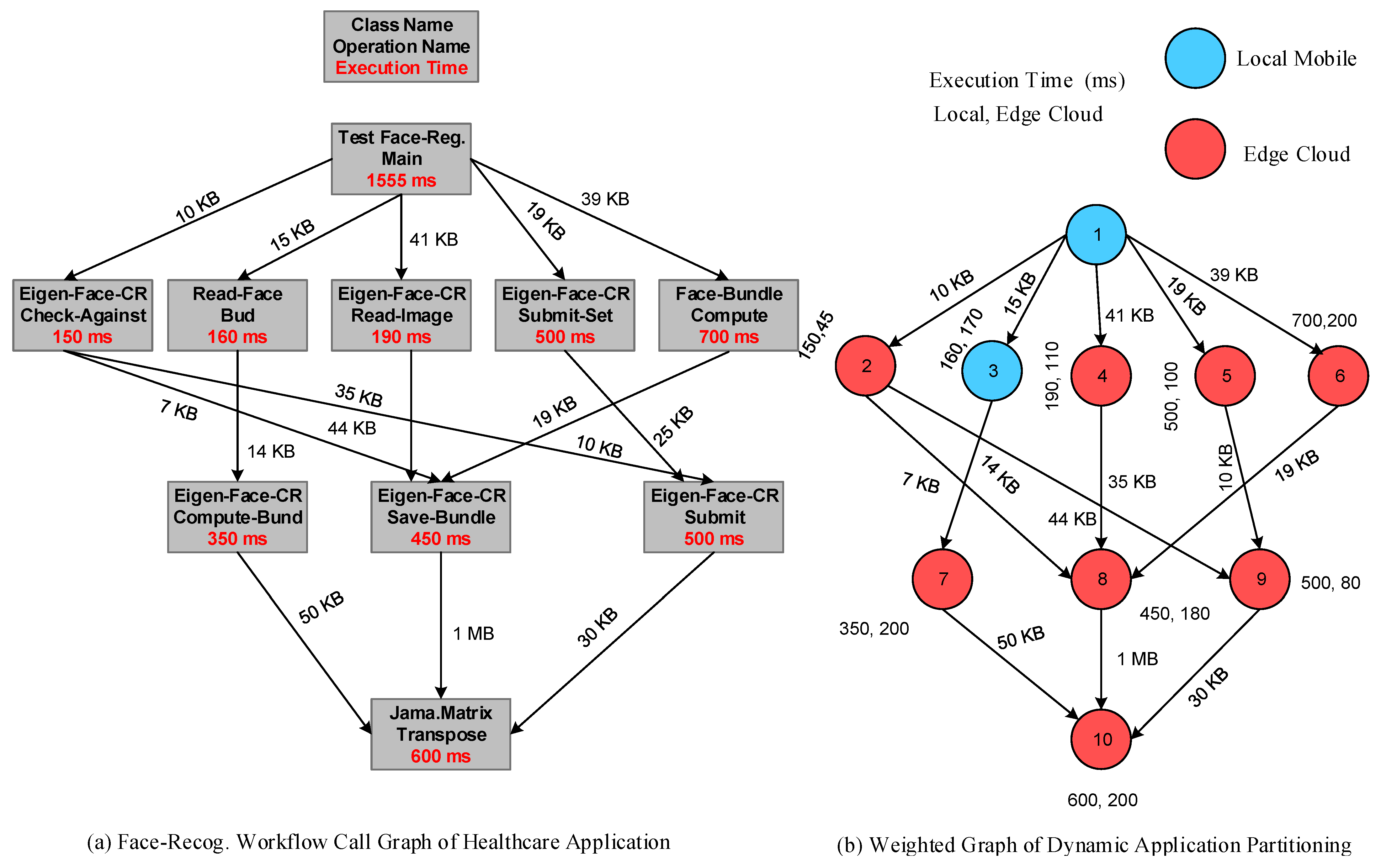
5.2. Mobile Workflow Application-Partitioning System
5.3. Profiling Technologies
Dynamic Application-Partitioning Setup
5.4. Components Calibration of DAPWTS Framework
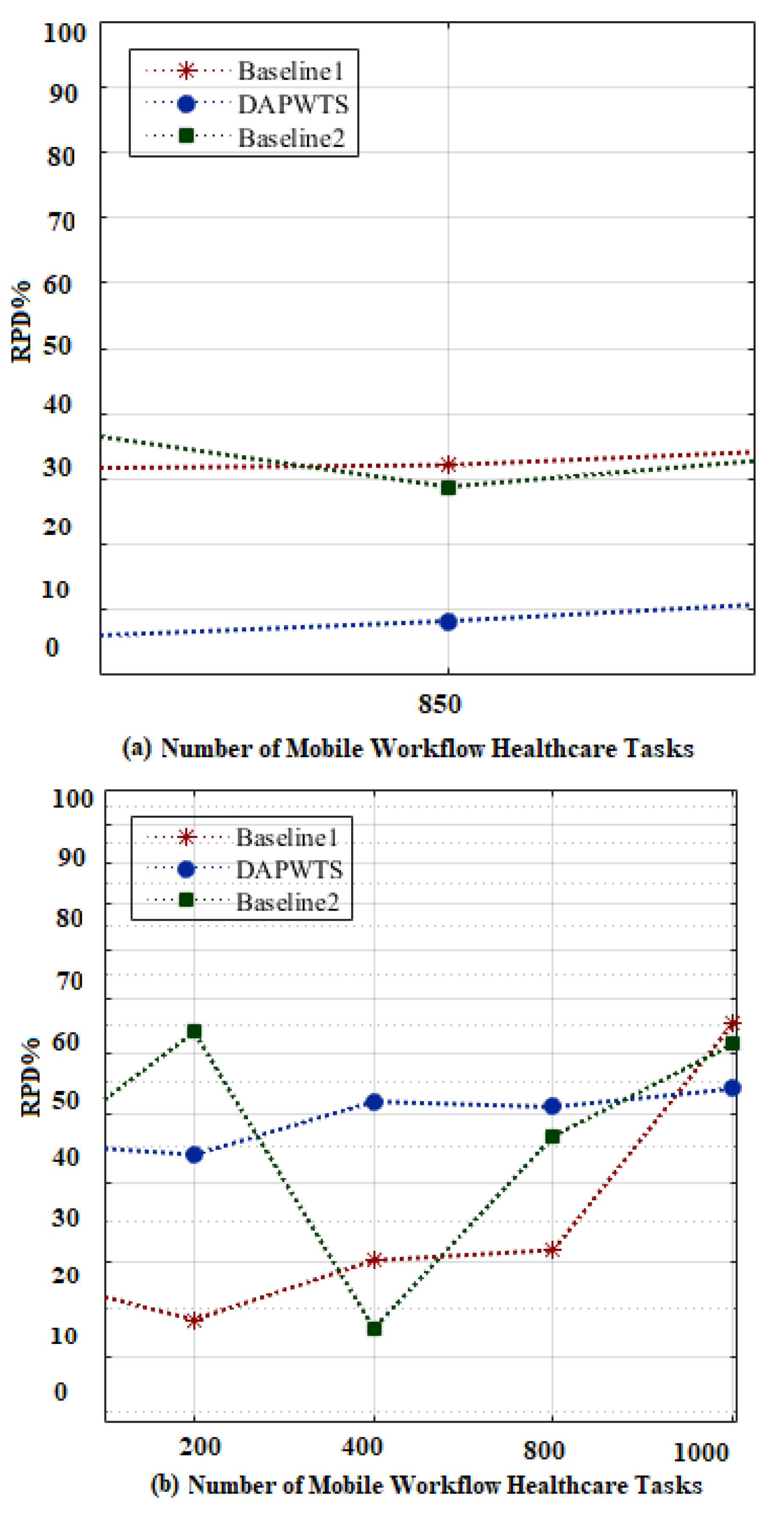
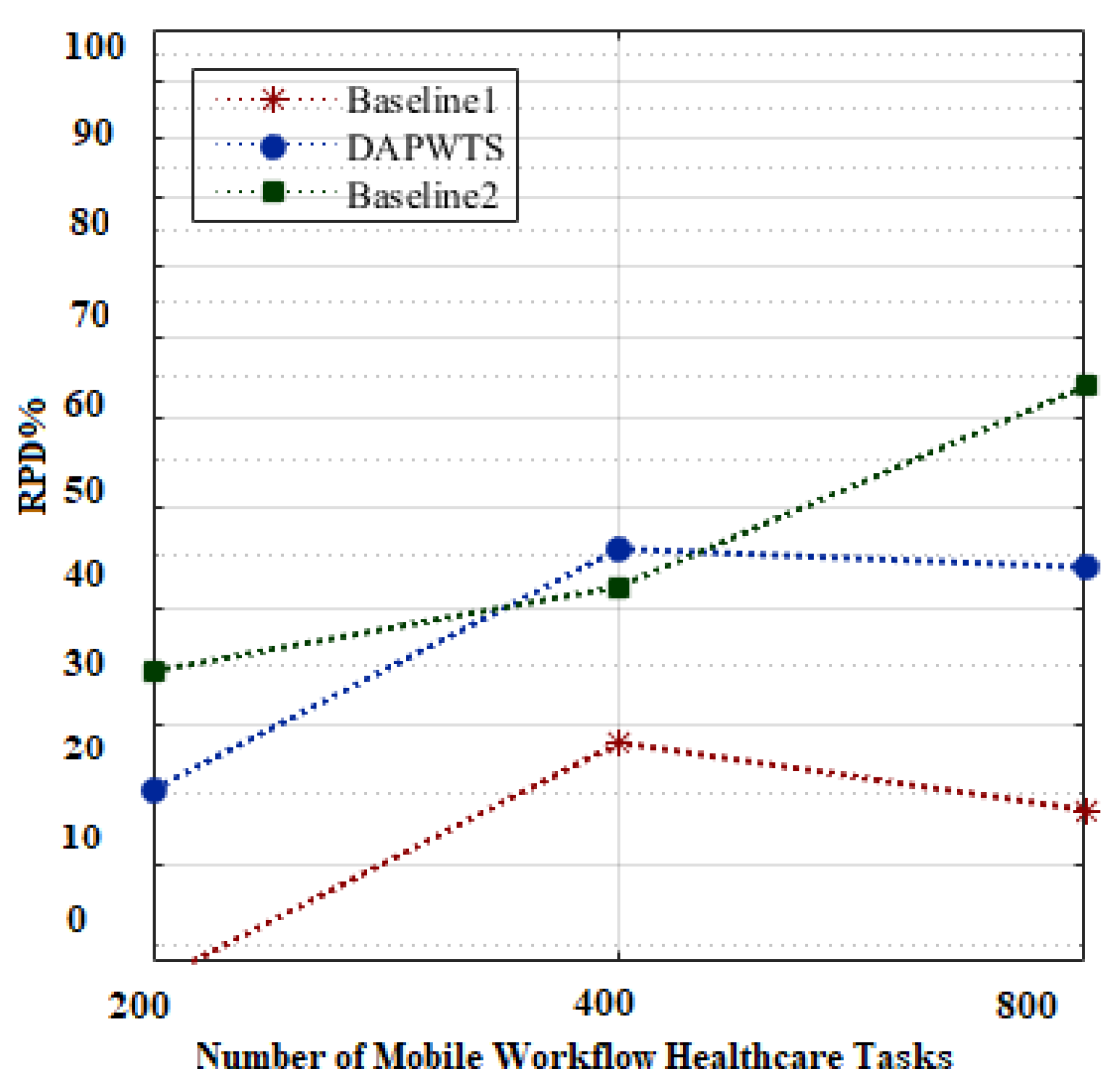
5.4.1. Task-Sequencing Rules
5.4.2. Secure Min-Cut Algorithm
5.4.3. Task-Scheduling Phase
5.4.4. Energy-Efficient Task Scheduling
5.4.5. Failure-Aware Task Scheduling
5.5. Research Findings and Limitations
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kwon, D.; Yu, S.; Lee, J.; Son, S.; Park, Y. WSN-SLAP: Secure and lightweight mutual authentication protocol for wireless sensor networks. Sensors 2021, 21, 936. [Google Scholar] [CrossRef]
- Lee, C.C. Security and privacy in wireless sensor networks: Advances and challenges. Sensors 2020, 20, 744. [Google Scholar] [CrossRef] [Green Version]
- Woźniak, M. Advanced Computational Intelligence for Object Detection, Feature Extraction and Recognition in Smart Sensor Environments. Sensors 2020, 21, 45. [Google Scholar] [CrossRef]
- Waseem, M.; Lakhan, A.; Jamali, I.A. Data security of mobile cloud computing, on cloud server. Open Access Libr. J. 2016, 1, 11. [Google Scholar] [CrossRef]
- Shahbazi, Z.; Byun, Y.C. Integration of Blockchain, IoT and Machine Learning for Multistage Quality Control and Enhancing Security in Smart Manufacturing. Sensors 2021, 21, 1467. [Google Scholar] [CrossRef]
- Lin, Y. An analytic computation-driven algorithm for Decentralized Multicore Systems. Future Gener. Comput. Syst. 2019, 96, 101–110. [Google Scholar] [CrossRef]
- Liu, G.; Peng, B.; Zhong, X. A Novel Epidemic Model for Wireless Rechargeable Sensor Network Security. Sensors 2021, 21, 123. [Google Scholar] [CrossRef]
- Khoso, F.H.; Arain, A.A.; Lakhan, A.; Kehar, A.; Nizamani, S.Z. Proposing a Novel IoT Framework by Identifying Security and Privacy Issues in Fog Cloud Services Network. Int. J. 2021, 9, 592–596. [Google Scholar]
- Lakhan, A.; Li, X. Transient fault aware application partitioning computational offloading algorithm in microservices based mobile cloudlet networks. Computing 2020, 102, 105–139. [Google Scholar] [CrossRef]
- Lakhan, A.; Xiaoping, L. Energy aware dynamic workflow application partitioning and task scheduling in heterogeneous mobile cloud network. In Proceedings of the 2018 International Conference on Cloud Computing, Big Data and Blockchain (ICCBB), Fuzhou, China, 15–17 November 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–8. [Google Scholar]
- Lakhan, A.; Li, X. Content Aware Task Scheduling Framework for Mobile Workflow Applications in Heterogeneous Mobile-Edge-Cloud Paradigms: CATSA Framework. In Proceedings of the 2019 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), Xiamen, China, 16–18 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 242–249. [Google Scholar]
- Sharma, P.K.; Park, J.H.; Cho, K. Blockchain and federated learning-based distributed computing defence framework for sustainable society. Sustain. Cities Soc. 2020, 59, 102220. [Google Scholar] [CrossRef]
- Mastoi, Q.-u.-a.; Ying Wah, T.; Gopal Raj, R.; Lakhan, A. A Novel Cost-Efficient Framework for Critical Heartbeat Task Scheduling Using the Internet of Medical Things in a Fog Cloud System. Sensors 2020, 20, 441. [Google Scholar] [CrossRef] [Green Version]
- Lakhan, A.; Ahmad, M.; Bilal, M.; Jolfaei, A.; Mehmood, R.M. Mobility Aware Blockchain Enabled Offloading and Scheduling in Vehicular Fog Cloud Computing. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4212–4223. [Google Scholar] [CrossRef]
- Pinto, M.F.; Marcato, A.L.; Melo, A.G.; Honório, L.M.; Urdiales, C. A framework for analyzing fog-cloud computing cooperation applied to information processing of UAVs. Wirel. Commun. Mob. Comput. 2019, 2019, 7497924. [Google Scholar] [CrossRef] [Green Version]
- Garg, S.; Aujla, G.S.; Erbad, A.; Rodrigues, J.J.; Chen, M.; Wang, X. Guest Editorial: Blockchain Envisioned Drones: Realizing 5G-Enabled Flying Automation. IEEE Netw. 2021, 35, 16–19. [Google Scholar] [CrossRef]
- Gill, S.S.; Tuli, S.; Xu, M.; Singh, I.; Singh, K.V.; Lindsay, D.; Tuli, S.; Smirnova, D.; Singh, M.; Jain, U.; et al. Transformative effects of IoT, Blockchain and Artificial Intelligence on cloud computing: Evolution, vision, trends and open challenges. Internet Things 2019, 8, 100118. [Google Scholar] [CrossRef] [Green Version]
- Ferrag, M.A.; Shu, L.; Yang, X.; Derhab, A.; Maglaras, L. Security and privacy for green IoT-based agriculture: Review, blockchain solutions, and challenges. IEEE Access 2020, 8, 32031–32053. [Google Scholar] [CrossRef]
- Kiwelekar, A.W.; Patil, P.; Netak, L.D.; Waikar, S.U. Blockchain-Based Security Services for Fog Computing. In Fog/Edge Computing For Security, Privacy, and Applications; Springer: Berlin, Germany, 2021; pp. 271–290. [Google Scholar]
- Blasch, E.; Xu, R.; Chen, Y.; Chen, G.; Shen, D. Blockchain methods for trusted avionics systems. In Proceedings of the 2019 IEEE National Aerospace and Electronics Conference (NAECON), Dayton, OH, USA, 15–19 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 192–199. [Google Scholar]
- Li, T.; Wang, Z.; Chen, Y.; Li, C.; Jia, Y.; Yang, Y. Is semi-selfish mining available without being detected? Int. J. Intell. Syst. 2021, 2, 1–21. [Google Scholar] [CrossRef]
- Li, T.; Wang, Z.; Yang, G.; Cui, Y.; Chen, Y.; Yu, X. Semi-Selfish Mining based on Hidden Markov Decision Process. Int. J. Intell. Syst. 2021, 36, 3596–3612. [Google Scholar] [CrossRef]
- Yu, X.; Wang, Z.; Wang, Y.; Li, F.; Li, T.; Chen, Y.; Tian, Y.; Yu, X. ImpSuic: A Quality Updating Rule in Mixing Coins with Maximum Utilities. Int. J. Intell. Syst. 2020, 36, 1182–1198. [Google Scholar] [CrossRef]
- Li, T.; Chen, Y.; Wang, Y.; Wang, Y.; Zhao, M.; Zhu, H.; Tian, Y.; Yu, X.; Yang, Y. Rational Protocols and Attacks in Blockchain System. Secur. Commun. Netw. 2020, 2020, 8839047. [Google Scholar] [CrossRef]
- Yang, G.; Wang, Y.; Wang, Z.; Tian, Y.; Yu, X.; Li, S. IPBSM: An optimal bribery selfish mining in the presence of intelligent and pure attackers. Int. J. Intell. Syst. 2020, 35, 1735–1748. [Google Scholar] [CrossRef]
- Wang, Y.; Yang, G.; Li, T.; Zhang, L.; Wang, Y.; Ke, L.; Dou, Y.; Li, S.; Yu, X. Optimal mixed block withholding attacks based on reinforcement learning. Int. J. Intell. Syst. 2020, 35, 2032–2048. [Google Scholar] [CrossRef]
- Liu, X.; Yu, X.; Zhu, H.; Yang, G.; Wang, Y.; Yu, X. A game-theoretic approach of mixing different qualities of coins. Int. J. Intell. Syst. 2020, 35, 1899–1911. [Google Scholar] [CrossRef]
- Khan, G.; Jabeen, S.; Khan, M.Z.; Khan, M.U.G.; Iqbal, R. Blockchain-enabled deep semantic video-to-video summarization for IoT devices. Comput. Electr. Eng. 2020, 81, 106524. [Google Scholar] [CrossRef]
- Rodrigues, T.A.; Patrikar, J.; Choudhry, A.; Feldgoise, J.; Arcot, V.; Gahlaut, A.; Lau, S.; Moon, B.; Wagner, B.; Scott Matthews, H.; et al. Data Collected with Package Delivery Quadcopter Drone. Carnegie Mellon University. Dataset. 2020. Available online: https://kilthub.cmu.edu/articles/dataset/Data_Collected_with_Package_Delivery_Quadcopter_Drone/12683453 (accessed on 10 February 2021).
- Dovgal, V.A. Decision-Making for Placing Unmanned Aerial Vehicles to Implementation of Analyzing Cloud Computing Cooperation Applied to Information Processing. In Proceedings of the 2020 International Conference on Industrial Engineering, Applications and Manufacturing (ICIEAM), Sochi, Russia, 18–22 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–5. [Google Scholar]
- Yaqoob, S.; Ullah, A.; Awais, M.; Katib, I.; Albeshri, A.; Mehmood, R.; Raza, M.; Ul Islam, S.; Rodrigues, J.J. Novel congestion avoidance scheme for Internet of Drones. Comput. Commun. 2021, 169, 202–210. [Google Scholar] [CrossRef]





| Notation | Description |
|---|---|
| N | Number of tasks v |
| DAG | Directed Acyclic Graph of Application |
| Reschedule the rejected tasks on mobile | |
| Reschedule the rejected tasks on edge cloud | |
| Number of virtual machines | |
| virtual machine in edge server | |
| Workflow application task | |
| Local set of tasks | |
| c | Edge-Cloud tasks |
| Weight of the each task | |
| = | All tasks arrival rate |
| Arrival rate at cloudlet virtual machine | |
| Arrival rate at mobile device | |
| Current Cloudlet speedup factor rate | |
| The mobile service rate | |
| Cellular and WLAN bandwidth rate | |
| Application partitioning factor during offloading | |
| Speed rate of virtual machine | |
| Speed rate of mobile processor | |
| Execution cost of task on edge cloud k | |
| Execution cost of task on mobile | |
| Power consumption rate at edge-cloud virtual machine | |
| Power consumption rate at mobile device | |
| Assignment of task on virtual machine j | |
| Upload bandwidth | |
| Download bandwidth | |
| Begin time of the task | |
| Finish time of the task | |
| Call graph of application G | |
| Deadline of the application G | |
| Most Tightly Connected Vertices | |
| a | Arbitrary of vertex G |
| weight of each task on graph | |
| source and sink in call graph | |
| Recover time of a task during failure | |
| Failed ratio of a task |
| Simulation Parameters | Values | Symbol |
|---|---|---|
| Languages | JAVA | JVM |
| Applications | Healthcare | G |
| Arrival of tasks | 5 s | |
| Simulation Time | 6 h | - |
| Experiment Repetition | 14 | - |
| No. of Mobile devices | 2000 | - |
| WAN-WLAN Network Bandwidth | 20 to 300 mbps | |
| WAN-Propagation Delay | 50 to 150 mbps | |
| Upload/download data size of a task | 2000/150 KB | |
| Possibility offload to edge cloud | 80% | |
| Possibility offload to loc | 12% | |
| VM processing speed cloudlet | 1200/22,000 MIPS | |
| No. VMS per cloudlet | 3/∞ | |
| Mobile-Device Capability. | 64 GB | |
| VMs speed | 500–2500 MIPS | |
| Mobile Devices | 10–4 GB RAM, 64 ROOM | - |
| Edge-Cloud-1 | Core i3 | - |
| Edge-Cloud-2 | Core i5 | - |
| Edge-Cloud-3 | Core i7 | - |
| Edge-Cloud-4 | Core i9 | - |
| Edge-Cloud-5 | Core GPU | - |
| Heartbeat Sensor | Arduino | |
| SPO2 Sensor | Arduino | |
| airflow Sensor | Arduino | |
| body temperature Sensor | Arduino | |
| ECG Sensor | Arduino | |
| Glucometer Sensor | Aurdino | |
| galvanic skin Sensor | Aurdino | |
| EMG Sensor | Aurdino | |
| EEG Sensor | Aurdino | |
| MQ2 Sensor | Aurdino | |
| Lead-1 Sensor | Aurdino | |
| Lead-2 Sensor | Aurdino |
| Workload | Data Size (GB) | C.Ins. (MI) | No. of Tasks |
|---|---|---|---|
| G1 | 5 | 5.8 | 1000 |
| G2 | 3 | 6.8 | 900 |
| G3 | 4 | 7.8 | 800 |
| Mobile Device | Edge-Cloud-1 | Edge-Cloud-2 | Edge-Cloud-3 | Edge-Cloud-4 | Edge-Cloud-5 |
|---|---|---|---|---|---|
| Core | 1 | 1 | 1 | 1 | 1 |
| MIPS/Core | 200 | 400 | 600 | 800 | 1000 |
| Power/Core | 50 W | 100 W | 150 W | 200 W | 250 W |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lakhan, A.; Li, J.; Groenli, T.M.; Sodhro, A.H.; Zardari, N.A.; Imran, A.S.; Thinnukool, O.; Khuwuthyakorn, P. Dynamic Application Partitioning and Task-Scheduling Secure Schemes for Biosensor Healthcare Workload in Mobile Edge Cloud. Electronics 2021, 10, 2797. https://doi.org/10.3390/electronics10222797
Lakhan A, Li J, Groenli TM, Sodhro AH, Zardari NA, Imran AS, Thinnukool O, Khuwuthyakorn P. Dynamic Application Partitioning and Task-Scheduling Secure Schemes for Biosensor Healthcare Workload in Mobile Edge Cloud. Electronics. 2021; 10(22):2797. https://doi.org/10.3390/electronics10222797
Chicago/Turabian StyleLakhan, Abdullah, Jin Li, Tor Morten Groenli, Ali Hassan Sodhro, Nawaz Ali Zardari, Ali Shariq Imran, Orawit Thinnukool, and Pattaraporn Khuwuthyakorn. 2021. "Dynamic Application Partitioning and Task-Scheduling Secure Schemes for Biosensor Healthcare Workload in Mobile Edge Cloud" Electronics 10, no. 22: 2797. https://doi.org/10.3390/electronics10222797
APA StyleLakhan, A., Li, J., Groenli, T. M., Sodhro, A. H., Zardari, N. A., Imran, A. S., Thinnukool, O., & Khuwuthyakorn, P. (2021). Dynamic Application Partitioning and Task-Scheduling Secure Schemes for Biosensor Healthcare Workload in Mobile Edge Cloud. Electronics, 10(22), 2797. https://doi.org/10.3390/electronics10222797










