Recent Technologies, Security Countermeasure and Ongoing Challenges of Industrial Internet of Things (IIoT): A Survey
Abstract
1. Introduction
- The difference between conventional systems and IIoT security concerns are summarized. Decentralized security approaches with high scalability, high interoperability, lightweight, and secure data processing have urged to address the high heterogeneity of “things,” high volume, and variety of collected sensor data, as opposed to conventional security systems focused on a centralized approach.
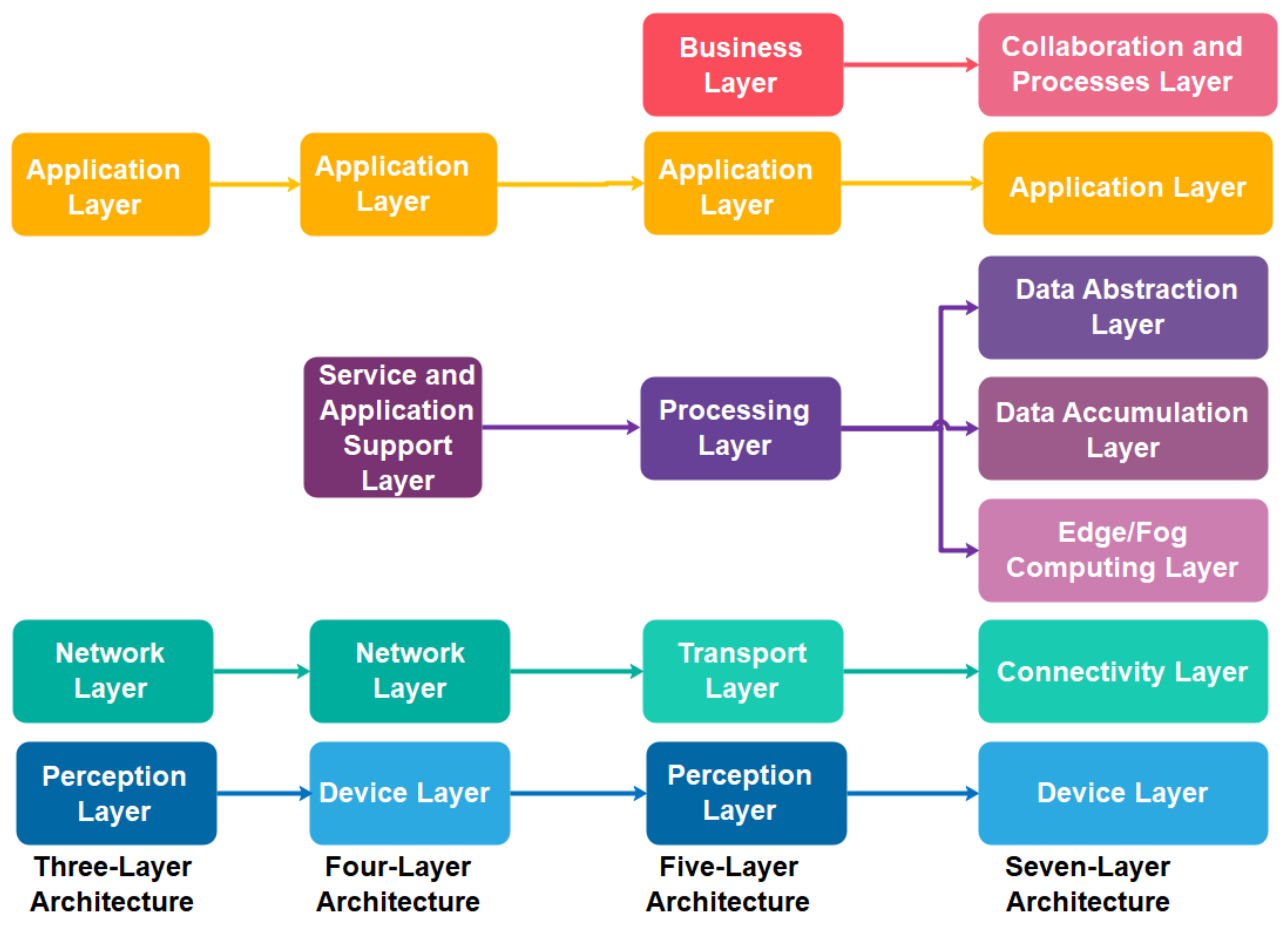
- Unlike recent IIoT architectures [24,25,26,27] that (i) focused on specific industries: aviation industry [25] and smart manufacturing [27], and (ii) targeted on particular technologies: M2M communication [24], green-aware multi-task scheduling [26] and 5G technology [27], we generalized the IIoT architecture into a four-layer architecture to cope with a wide of industry technologies and standards.
- Subsequently, we classify the recent IIoT technologies and standards into the proposed four-layer IIoT architecture
- The IIoT security requirements are further defined with the CIA+ model, includes confidentially(C), integrity(I), authentication(A), authorization and access control (A) and availability (A).
- A comprehensive end-to-end security analysis was conducted based on the defined IIoT CIA+ model. Subsequently, a fine-grained review on recent industry technologies and standards in each layer of the proposed IIoT architecture. The identified security risks and threats of these industry technologies, their deployed security countermeasures and future research works are summarized
- Lastly, we enumerate the open security challenges of IIoT and future research opportunities.
2. IIoT Security Challenges and Concerns
3. IIoT Architecture
3.1. Overview of IoT and IIoT Architecture
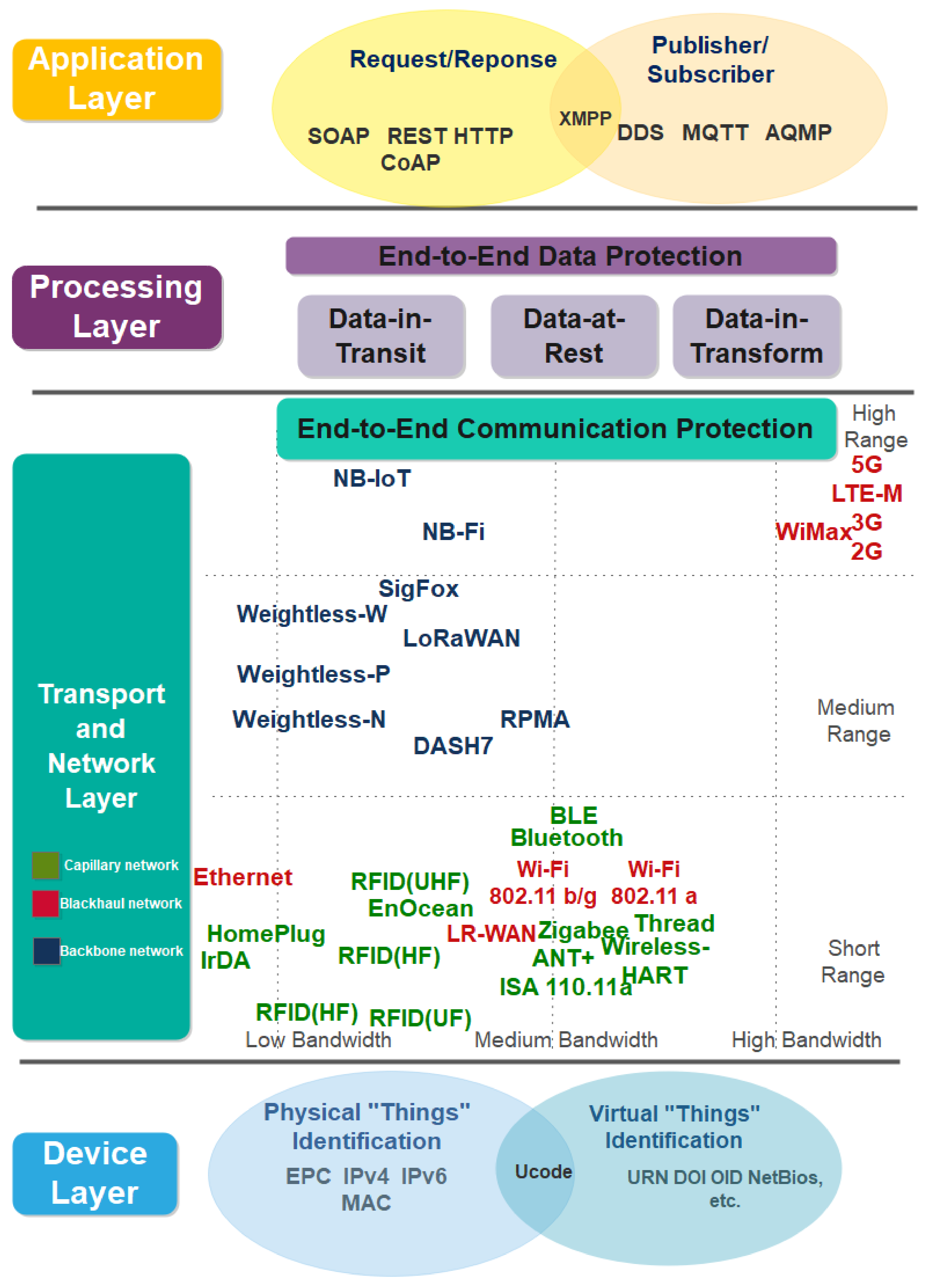
3.2. The Proposed IIoT Security Architecture
4. End to End Security Analysis on the Proposed IIoT Security Architecture
4.1. Device Layer
4.1.1. Electronic Product Code (EPC)
4.1.2. Ubiquitous Code (Ucode)
4.1.3. Media Access Control (MAC) and Internet Protocol (IP) Address
4.2. Transport Layer
4.2.1. Capillary Network and Communication Technologies
4.2.2. Backhaul Network and Communication Technologies
4.2.3. Backbone Networks
4.3. Data Processing Layer
- Data-in-TransitData-in-transit refers to data being transmitted from the network layer to the data processing layer and application layer, either forwardly or backwardly. Most of big data technologies relies on Kerberos authentication scheme, public key infrastructure (PKI) and network encryption algorithm such as Hadoop remote procedure call (RPC), secure socket layer (SSL), HDFS data transfer protocol, simple authentication and security layer (SASL) mechanism, to ensure data confidentiality and authentication. However, these security mechanisms provide limited access control and authorization capabilities. A more sophisticated access control scheme such as role-based, identity-based and attribute-based can be plug-in with additional security packages such as Cloudera Sentry, DataGuise, IBM Infosphere Optima Data Masking, Datastax Enterprise, Zettaset Secure and others [108,109]. While data-in-transit protection in IIoT is mainly constructed based on the conventional security mechanism such as PKI, it is recommended to employ the bottom-up approach for heterogeneous and distributed networks infrastructure. The more challenging issue here is the key management and distribution problem, includes distribute key across distributed network and communication technologies, maintaining a large scale of the certificate, key revocation, recovery, and updating process. The key management proposal should be able to solve the scalability and interoperability issues to solve these problems.
- Data-at-RestData-at-rest refers to the data being stored in persistent storage such as a disk file. Conventional data-at-rest protection approaches include installing tamper-resistant hardware in third-party service providers, full-disk encryption, database-level encryption, table level encryption, and application-level encryption. Data are encrypted in the application layer before being inserted into the database. For instance, TrustDB and CipherBase provide data-at-rest protection based on the co-design of hardware and software [110].
- Data-in-TransformData-in-transform indicates that data is subjected to various means and manipulation methods, including performing query, sorting, mathematical operations, statistical analysis, and other functions on data to produce meaningful output. Protection of data-in-transform in IIoT is critically vital as their necessities in supporting real-time data analytics. Most of the recent big data processing service providers are still inadequate to support confidentiality during data transformation.
4.4. Application Layer
5. Open Security Issues and Privacy of IIoT
- Security architecture and framework for IIoT.As the IIoT is still in its early stages of development, distinctive security models and designs were proposed as of late to address its security challenges and privacy concern issues. The point of these works are focused to make sure about a particular: (i) IIoT architecture, includes cyber-physical social based security model [109] focused on the U2IoT architecture [34] and Grid of security approach [38] targeted for securing SDN-based IIoT architecture; (ii) “things”, i.e., OSCAR [115] directed to protect constrained application protocol (CoAP) communication networks, Physically Unclonable Functions (PUFs) based authentication protocol [116] for ensuring RFID framework; (iii) systems, includes a lightweight security system focused for IPsec, DTLS, and IEEE 802.15.4 connection layer. As no single security architecture and framework can fix the entire IIoT ecosystem, a design of IIoT security architecture with a higher abstraction level by using the bottom-up approach is needed. The proposal’s emphasis should be on interoperability issues to integrate different security mechanisms supported by IIoT technologies and cross-layer security solutions. Below are some of the highlighted issues in this domain. How can encrypted data be passed through different network layers from the physical layer, transport layer to application layer securely supported by different communication technologies? How can the things identified with a different addressing scheme secured under different security mechanisms communicate universally? How to exchange data securely with a different set of data formats (e.g., XML, JSON, etc.)? How to implement a secure communication protocol across a diverse manufacturer? Besides that, scalability issues should be further addressed to support rapid growth in IIoT, such as the scalability of PKI to manage a large scale of X.509 certificates.
- Limitation of conventional point-to-point defenses system and security mechanisms.The connection and communication across IIoT networks are recently protected via conventional network security protocols such as TLS/SSL, IPSec, RADIUS, IKE, etc. Most of these security protocols work based on point-to-point defences. For instance, TLS/SSL offers protection over the transport layer, IPSec focuses on IPv6 and IPv4 MAC, data link, transport and network layer. As IIoT communication technologies diversify, these conventional security mechanisms that focus on point-to-point defences are less efficient against the new cyber advanced persistent threats (APT) attacks and malicious insider attacks. The malicious attacks can target any vulnerabilities or weak points of IIoT networks or application systems. For instance, multi-hop wireless broadcast communication is vulnerable to eavesdropping. These situations become worst with the bring your own device (BYOD) or bring your own technology (BYOT) environments. The hijacked or backdoor installed devices can penetrate IIoT networks easily.
- Lightweight and stronger cryptographic algorithmMost IIoT communication protocols and technologies still rely on conventional cryptographic algorithms such as RSA, MD5, RC4, and DES-56 to ensure data confidentiality and secure communication. However, some of these algorithms have been proven insecure and subjected to quantum attacks. Therefore, a more robust cryptographic algorithm needed to be adapted into these communication protocols, such as quantum-resistant NTRU and BLISS algorithms. Besides that, a lightweight but secure algorithm is highly sought after to protect the IIoT constrained resources (e.g., low energy, low storage and low bandwidth communication). For instance, RC5, SkipJack, high security and lightweight (HIGHT), corrected block TEA (XXTEA), SAFER++ have been proposed recently to secure wireless sensor networks [117,118].
- Limitation of IPSec and TLS/SSL mechanismMost IIoT technologies rely on IPSec and TLS/SSL mechanisms to secure their communication and data transmission. Both provide confidentiality, integrity and authentication of the message, with limited authorization and access control. However, without the assurance of availability and non-repudiation, they are still vulnerable to application-layer threats. Besides that, the scalability and interoperability issues of both IPSec and TLS/SSL need to be addressed further. These include scalability of key management and distribution to handle a large of “things” network keys, the implementation issues in a lightweight and constrained resource protocol such as CoAP.
- Password-based authentication schemeMost IIoT authentication schemes are still constructed based on single-factor authentication (SFA)—user’s ID and password. Some network keys are further derived from the user’s password. However, these short, weak, easily predictable and repeated passwords further paring security defences mechanism and subjected to a brute-force attack, dictionary attack, rainbow attack, etc. Recently, the two-step verification mechanism can be activated optionally, in which four- or six-digit verification code will be sent to a user via SMS or voice call, or alternative can be retrieved from the time-based one time password apps.
- Towards a data-centric approach for end-to-end data protectionAs no single security mechanism and framework can fix the entire IIoT ecosystem due to its inherent, the data-centric approach can serve as another alternative towards end-to-end security for IIoT. Instead of targeting to protect different networks, communication technologies and protocols, the data-centric approach aims to protect the data itself—whenever and wherever it goes. These data-centric approaches include homomorphic encryption, attribute-based encryption scheme, private information retrieve scheme, searchable encryption scheme and multi-party computation scheme [119,120,121,122]. Most of these schemes can assure data-in-transit, data-in-transform and data-at-rest security, thus significantly resolving the interoperability and scalability issues of integrating different security mechanisms across IIoT networks and technologies. These schemes also significantly reduce the risk of privacy (e.g., collection and abuse use of personal data, habits and geolocation). Homomorphic encryption, for example, permits a third-party data processing centre to undertake real-time analytical work without having to decrypt data collected from any industry.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Weber, R.H. Internet of Things–New security and privacy challenges. Comput. Law Secur. Rev. 2010, 26, 23–30. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad Hoc Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef]
- Zhao, K.; Ge, L. A Survey on the Internet of Things Security. In Proceedings of the 9th International Conference Computational Intelligence Security-CIS, Emeishan, China, 14–15 December 2013; pp. 663–667. [Google Scholar] [CrossRef]
- Ziegeldorf, J.H.; Morchon, O.G.; Wehrle, K. Privacy in the Internet of Things: Threats and challenges. Secur. Commun. Netw. 2014, 7, 2728–2742. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and Challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Fremantle, P.; Scott, P. A Security Survey of Middleware for the Internet of Things. PeerJ PrePrints 2015, 3, e1521. Available online: https://peerj.com/preprints/1241.pdf (accessed on 4 October 2021).
- Granjal, J.; Monteiro, E.J.; Silva, S. Security for the Internet of Things: A Survey of Existing Protocols and Open Research Issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Nguyen, K.T.; Laurent, M.; Oualha, N. Survey on Secure Communication Protocols for the Internet of Things. Ad Hoc Netw. 2015, 32, 17–31. [Google Scholar] [CrossRef]
- Airehrour, D.; Gutierrez, J.; Ray, S.K. Secure Routing for Internet of Things: A Survey. J. Netw. Comput. Appl. 2016, 66, 198–213. [Google Scholar] [CrossRef]
- Qin, Y.; Sheng, Q.Z.; Falkner, N.J.G.; Dustdar, S.; Wang, H.; Vasilakos, A.V. When Things Matter: A Survey on Data-Centric Internet of Things. J. Netw. Comput. Appl. 2016, 64, 137–153. [Google Scholar] [CrossRef]
- Loi, F.; Sivanathan, A.; Hassan, H.G.; Radford, A.; Sivaraman, V. Systematically Evaluating Security and Privacy for Consumer IoT Devices. In Proceedings of the 2017 Workshop on Internet of Things Security and Privacy, New York, NY, USA, 3 November 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on the use of Blockchain for the Internet of Things. IEEE Access 2018, 6, 32979–33001. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Berkay, C.; Fernandes, E.; Pauley, E.; Tan, G.; McDaniel, P. Program Analysis of Commodity IoT Applications for Security and Privacy: Challenges and Opportunities. ACM Comput. Surv. 2019, 52, 1–30. [Google Scholar] [CrossRef]
- Tabrizi, F.M.; Pattabiraman, K. Design-Level and Code-Level Security Analysis of IoT Devices. ACM Trans. Embed. Comput. Syst. 2019, 18, 1–25. [Google Scholar] [CrossRef]
- Amanullah, M.A.; Habeeb, R.A.A.; Nasaruddin, F.H.; Gani, A.; Ahmed, E.; Nainar, A.S.M.; Akim, N.M.; Imran, M. Deep Learning and Big Data Technologies for IoT security. Comput. Commun. 2020, 141, 495–517. [Google Scholar] [CrossRef]
- Lao, L.; Li, Z.; Hou, S.; Xiao, B. A Survey of IoT Applications in Blockchain Systems: Architecture, Consensus, and Traffic Modeling. ACM Comput. Surv. 2020, 53, 1–32. [Google Scholar] [CrossRef]
- João, B.; Sequeiros, F.; Francisco, T.; Chimuco, M.; Samaila, G.; Freire, M.M.; Pedro Inácio, R.M. Attack and System Modeling Applied to IoT, Cloud, and Mobile Ecosystems: Embedding Security by Design. ACM Comput. Surv. 2020, 53, 1–32. [Google Scholar] [CrossRef]
- Polychronou, N.-P.; Thevenon, P.-H.; Puys, M.; Beroulle, V. A Comprehensive Survey of Attacks without Physical Access Targeting Hardware Vulnerabilities in IoT/IIoT Devices, and Their Detection Mechanisms. ACM Trans. Des. Autom. Electron. Systems 2021, 27, 1–35. [Google Scholar] [CrossRef]
- Gaspar, P.D.; Fernandez, C.M.; Soares, V.N.G.J.; Caldeira, J.M.L.P.; Silva, H. Development of Technological Capabilities through the Internet of Things (IoT): Survey of Opportunities and Barriers for IoT Implementation in Portugal’s Agro-Industry. Appl. Sci. 2021, 11, 3454. [Google Scholar] [CrossRef]
- Wu, Y.; Wang, Z.; Ma, Y.; Leung, V.C. Deep reinforcement learning for blockchain in industrial IoT: A survey. Comput. Netw. 2021, 191, 108004. [Google Scholar] [CrossRef]
- Latif, S.; Idrees, Z.; e Huma, Z.; Ahmad, J. Blockchain technology for the Industrial Internet of Things: A comprehensive survey on security challenges, architectures, applications, and future research directions. Trans. Emerg. Telecommun. Technol. 2021, 191, e4337. [Google Scholar] [CrossRef]
- Gilchrist, A. IIoT Reference Architecture. In Industry 4.0; Apress: Berkeley, CA, USA, 2016. [Google Scholar] [CrossRef]
- Ghosh, A.; Mukherjee, A.; Misra, S. SEGA: Secured Edge Gateway Microservices Architecture for IIoT-based Machine Monitoring. IEEE Trans. Ind. Inform. 2021. [Google Scholar] [CrossRef]
- Lamis, R.D.; Mohamed, T.E.-W.; Mahmoud, M.F. Towards sustainable industry 4.0: A green real-time IIoT multitask scheduling architecture for distributed 3D printing services. J. Manuf. Syst. 2021, 61, 196–209. [Google Scholar] [CrossRef]
- Chandra, S.R.V.; Kumarswamy, P.; Phridviraj, M.S.B.; Venkatramulu, S.; Subba, R.V. 5G Enabled Industrial Internet of Things (IIoT) Architecture for Smart Manufacturing. Lect. Notes Data Eng. Commun. Technol. 2021, 63, 193–201. [Google Scholar] [CrossRef]
- International Telecommunication Union. Overview of the Internet of Things. Available online: https://www.itu.int/rec/dologin_pub.asp?lang=e&id=T-REC-Y.2060-201206-I!!PDF-E&type=items (accessed on 4 October 2021).
- Ashton, K. That ‘Internet of Things’ Thing. RFiD J. 2009, 22, 97–114. Available online: http://www.itrco.jp/libraries/RFIDjournal-That%20Internet%20of%20Things%20Thing.pdf (accessed on 4 October 2021).
- Minerva, R.; Biru, A.; Rotondi, D. Towards a definition of the Internet of Things (IoT). IEEE Internet Things 2015, 1–86. Available online: https://iot.ieee.org/images/files/pdf/IEEE_IoT_Towards_Definition_Internet_of_Things_Revision1_27MAY15.pdf (accessed on 4 October 2021).
- W3C. Web of Things at W3C. Available online: https://www.w3.org/WoT/ (accessed on 4 October 2021).
- Noura, M.; Atiquzzaman, M.; Gaedke, M. Interoperability in Internet of Things: Taxonomies and Open Challenges. Mob. Netw. Appl. 2019, 24, 796–809. [Google Scholar] [CrossRef]
- Internet Architecture Board (IAB). Architectural Considerations in Smart Object Networking, RFC 7452. Available online: https://tools.ietf.org/html/rfc7452 (accessed on 4 October 2021).
- Ning, H.; Wang, Z. Future Internet of Things Architecture: Like Mankind Neural System or Social Organization Framework? IEEE Commun. Lett. 2011, 15, 461–463. [Google Scholar] [CrossRef]
- Guinard, D. A Web of Things Application Architecture-Integrating the Real-World into the Web. Ph.D. Thesis, University of Fribourg, Fribourg, Switzerland, 2011. Available online: https://webofthings.org/dom/thesis.pdf (accessed on 4 October 2021).
- Gómez-Goiri, A.; López-de-Ipiña, D. On the Complementarity of Triple Spaces and the Web of Things. In Proceedings of the Second International Workshop on Web of Things-WoT 11, San Francisco, CA, USA, 12–15 June 2011; pp. 1–6. [Google Scholar] [CrossRef]
- Vernet, D.; Zaballos, A.; Martin De Pozuelo, R.; Caballero, V. High Performance Web of Things Architecture for the Smart Grid Domain. Int. J. Distrib. Sens. Netw. 2015, 11, 347413. [Google Scholar] [CrossRef]
- Olivier, F.; Carlos, G.; Florent, N. New Security Architecture for IoT Network. Procedia Comput. Sci. 2015, 52, 1028–1033. [Google Scholar] [CrossRef]
- Qin, Z.; Denker, G.; Giannelli, C.; Bellavista, P.; Venkatasubramanian, N. A Software Defined Networking Architecture for the Internet-of-Things. In Proceedings of the IEEE Network Operator Management Symposium (NOMS), Krakow, Poland, 5–9 May 2014; pp. 1–9. [Google Scholar] [CrossRef]
- Bauer, M.; Boussard, M.; Bui, N.; Carrez, F. Project Deliverable D1.5–Final Architectural Reference Model for IoT, IoT-A. Available online: https://cordis.europa.eu/project/id/257521 (accessed on 4 October 2021).
- iCore? D2.5 Final Architecture Reference Model, iCore. Available online: https://cordis.europa.eu/docs/projects/cnect/8/287708/080/deliverables/001-20141031finalarchitectureAres20143821100.pdf (accessed on 4 October 2021).
- SENSEI. Available online: http://www.sensei-project.eu/ (accessed on 4 October 2021).
- D1.2.2 Final COMPOSE Architecture Document, FP7-317862-COMPOSE. 2018. Available online: https://cordis.europa.eu/project/id/317862 (accessed on 4 October 2021).
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A Vision, Architectural Elements, and Future Directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Farris, I.; Militano, L.; Nitti, M.; Atzori, L.; Iera, A. MIFaaS: A Mobile-IoT-Federation-as-a-Service model for dynamic cooperation of IoT Cloud Providers. Future Gener. Comput. Syst. 2016, 70, 126–137. [Google Scholar] [CrossRef]
- Conti, M.; Kaliyar, P.; Lal, C. CENSOR: Cloud-enabled secure IoT architecture over SDN paradigm. Concurr. Comput. Pract. Exp. 2018, 31, e4978. [Google Scholar] [CrossRef]
- Park, S.; Park, S. A Cloud-based Middleware for Self-Adaptive IoT-Collaboration Services. Sensors 2019, 19, 4559. [Google Scholar] [CrossRef]
- Devadas, T.J.; Subramanian, R.R. Paradigms for Intelligent IOT Architecture. In Principles of Internet of Things (IoT) Ecosystem: Insight Paradigm; Springer: Berlin/Heidelberg, Germany, 2020; Volume 174, pp. 67–100. [Google Scholar] [CrossRef]
- Memon, R.A.; Li, J.P.; Nazeer, M.I.; Khan, A.N.; Ahmed, J. DualFog-IoT: Additional Fog Layer for Solving Blockchain Integration Problem in Internet of Things. IEEE Access 2019, 7, 169073–169093. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Zhang, Q.; Choo, K.-K.R. An Energy-efficient SDN Controller Architecture for IoT Networks with Blockchain-based Security. IEEE Trans. Serv. Comput. 2020, 13, 625–638. [Google Scholar] [CrossRef]
- Medhane, D.V.; Sangaiah, A.K.; Hossain, M.S.; Muhammad, G.; Wang, J. Blockchain-enabled Distributed Security Framework for Next Generation IoT: An Edge-Cloud and Software Defined Network Integrated Approach. IEEE Internet Things J. 2020, 7, 6143–6149. [Google Scholar] [CrossRef]
- Telecommunication Standardization Sector ITU-T Y.2002 Overview of Ubiquitous Networking and of Its Support in NGN. Int. Telecommun. Union 2009. Available online: https://www.itu.int/rec/T-REC-Y.2002-200910-I/en (accessed on 4 October 2021).
- Wu, M.; Lu, T.J.; Ling, F.Y.; Sun, J.; Du, H.Y. Research on the Architecture of Internet of Things. In Proceedings of the 3rd International Conference Advanced Computer Theory Engineering 2010, Chengdu, China, 20–22 August 2010; pp. 484–487. [Google Scholar] [CrossRef]
- Candanedoa, I.-S.; Alonso, R.S.; Corchado, J.M.; González, S.R.; Vara, R.C. A review of edge computing reference architectures and a new global edge proposal. Future Gener. Comput. Syst. 2019, 99, 278–294. [Google Scholar] [CrossRef]
- ITU-T X.800. Security Architecture for Structure and Applications. Int. Telecommun. Union 1991. Available online: https://www.itu.int/rec/dologin_pub.asp?lang=e&id=T-REC-X.800-199103-I!!PDF-E&type=items (accessed on 4 October 2021).
- ITU-T X.805. Security Architecture for Systems Providing End-to-End Communications. Int. Telecommun. Union 2003. Available online: https://www.itu.int/rec/dologin_pub.asp?lang=e&id=T-REC-X.805-200310-I!!PDF-E&type=items (accessed on 4 October 2021).
- Houyou, A.M.; Huth, H.-P.; Mechs, S.; Völksen, G.; Hof, H.-J.; Kloukinas, C.; Siveroni, I.; Trsek, H. IoT@Work WP 2 – COMMUNICATION NETWORKS D2.1 – IOT ADDRESSING SCHEMES APPLIED TO MANUFACTURING. Available online: https://www.researchgate.net/publication/321587894_IoTWork_WP_2-COMMUNICATION_NETWORKS_D21-IOT_ADDRESSING_SCHEMES_APPLIED_TO_MANUFACTURING?enrichId=rgreq-49ee97e346acdaa334e3ab19db2fbe52-XXX&enrichSource=Y292ZXJQYWdlOzMyMTU4Nzg5NDtBUzo1Njg1OTkzNTU2OTUxMDRAMTUxMjU3NjA1ODQxNA%3D%3D&el=1_x_2&_esc=publicationCoverPdf (accessed on 4 October 2021).
- Internet of Things: The New Government to Business Platform: A Review of Opportunities, Practices, and Challenges. In The World Bank Group 2017, 1–112. Available online: http://documents.worldbank.org/curated/en/610081509689089303/pdf/120876-REVISED-WP-PUBLIC-Internet-of-Things-Report.pdf (accessed on 4 October 2021).
- Armene, F.; Barthel, H.; Dietrich, P.; Duker, J.; Floerkemeier, C.; Garrett, J.; Harrison, M.; Hogan, B.; Mitsugi, J.; Preishuber-Pfluegl, J.; et al. The EPCglobal Architecture Framework. Available online: https://www.gs1.org/sites/default/files/docs/architecture/architecture_1_3-framework-20090319.pdf (accessed on 4 October 2021).
- EPC Tag Data Standard. Released 1.11, GS1 2017. Available online: https://www.gs1.org/sites/default/files/docs/epc/GS1_EPC_TDS_i1_11.pdf (accessed on 4 October 2021).
- NXP Semiconductors. MIFARE DESFire EV1. Available online: https://www.nxp.com/products/rfid-nfc/mifare-hf/mifare-desfire/mifare-desfire-ev1:MIFARE_DESFIRE_EV1_2K_8K (accessed on 4 October 2021).
- ORIDAO, Secured EPC Gen2 RFID ASIC. Available online: http://html.transferts-lr.org/ORIDAO.pdf (accessed on 4 October 2021).
- Shugo, M.; Dai, W.; Yang, L.; Kazuo, S. Fully Integrated Passive UHF RFID Tag for Hash-Based Mutual Authentication Protocol. Sci. World J. 2015, 498610, 11. [Google Scholar] [CrossRef]
- Rolando, T.R. Priacy in RFID and Mobile Objects. Ph.D. Thesis, Universitat Rovira i Virgili, Tarragona, Spain, 2012. Available online: https://www.tdx.cat/bitstream/handle/10803/86942/Thesis?sequence=1 (accessed on 4 October 2021).
- Liu, Z.; Liu, D.; Li, L.; Lin, H.; Yong, Z. Implementation of a New RFID Authentication Protocol for EPC Gen2 Standard. IEEE Sens. J. 2015, 15, 1003–1011. [Google Scholar] [CrossRef]
- Khalid, M.; Mujahid, U.; Najam-ul-Islam, M. Ultralightweight resilient mutual authentication protocol for IoT based edge networks. J. Ambient. Intell. Humaniz. Comput. 2021, 183. [Google Scholar] [CrossRef]
- Din, N.; Waheed, A.; Zareei, M.; Alanazi, F. An Improved Identity-Based Generalized Signcryption Scheme for Secure Multi-Access Edge Computing Empowered Flying Ad Hoc Networks. IEEE Access 2021, 9, 120704–120714. [Google Scholar] [CrossRef]
- Ren, Y.; Xie, R.; Yu, F.R.; Huang, T.; Liu, Y. Potential Identity Resolution Systems for the Industrial Internet of Things: A Survey. IEEE Commun. Surv. Tutor. 2021, 23, 391–430. [Google Scholar] [CrossRef]
- Han, T.Y.; Zhu, S.Y.; Xie, B.; Tian, J. Advanced EPC network architecture based on hardware information service. ZTE Commun. 2020, 18, 18–23. [Google Scholar] [CrossRef]
- Sakamura, K. Ubiquitous ID Technologies 2011. uID Center. 2011. Available online: https://www.tron.org/ja/wp-content/themes/dp-magjam/pdf/en_US/UID910-W001-110324.pdf (accessed on 4 October 2021).
- Ishikawa, C. A URN Namespace for ucode. RFC 6588. 2012. Available online: https://ietf.org/rfc/rfc6588.html (accessed on 4 October 2021).
- Tian, Y.; Shen, J.; Tao, Y.; Liu, J. Development and Prospect of Identification Service Technology for Advanced Manufacturing. In China’s e-Science Blue Book 2018; Chinese Academy of Sciences, Ed.; Springer: Singapore, 2019; pp. 291–305. [Google Scholar] [CrossRef]
- Khan, M.F.F.; Sakamura, K. A Distributed Approach to Delegation of Access Rights for Electronic Health Records. In Proceedings of the International Conference on Electronics, Information, and Communication (ICEIC), Barcelona, Spain, 19–22 January 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Lohachab, A.; Lohachab, A.; Jangra, A. A Comprehensive Survey of Prominent Cryptographic Aspects for Securing Communication in Post-Quantum IoT Networks. Internet Things 2020, 9, 100174. [Google Scholar] [CrossRef]
- Salem, M.A.; El-Kader, S.M.A.; Youssef, M.I.; Tarrad, I.F. M2M in 5G Communication Networks: Characteristics, Applications, Taxonomy, Technologies, and Future Challenges. In Fundamental and Supportive Technologies for 5G Mobile Networks; IGI Global: Pennsylvania, PA, USA, 2020; pp. 309–321. [Google Scholar] [CrossRef]
- Kent, S. IP Encapsulating Security Payload (ESP). RFC 4303. 2005. Available online: https://www.rfc-editor.org/info/rfc4303 (accessed on 4 October 2021). [CrossRef]
- Thakor, V.A.; Razzaque, M.A.; Khandaker, M.R.A. Lightweight Cryptography Algorithms for Resource-Constrained IoT Devices: A Review, Comparison and Research Opportunities. IEEE Access 2021, 9, 28177–28193. [Google Scholar] [CrossRef]
- Yu, Y.; Liew, S.C.; Wang, T. Multi-Agent Deep Reinforcement Learning Multiple Access for Heterogeneous Wireless Networks with Imperfect Channels. IEEE Trans. Mob. Comput. 2021, 1. [Google Scholar] [CrossRef]
- Capillary Networks–A Smart Way to Get Things Connected. Ericsson Review 2014, 8. Available online: https://www.ericsson.com/4ae11c/assets/local/reports-papers/ericsson-technology-review/docs/2014/er-capillary-networks.pdf (accessed on 4 October 2021).
- GSM Association Official Document CLP.14-IoT Security Guidelines for Network Operators Version 2.2. 29 February 2020. Available online: https://www.gsma.com/iot/wp-content/uploads/2020/03/CLP.14-v2.2-GSMA-IoT-Security-Guidelines-for-Network-Operators.pdf (accessed on 4 October 2021).
- Rubio, J.E.; Roman, R.; Lopez, J. Integration of a Threat Traceability Solution in the Industrial Internet of Things. IEEE Trans. Ind. Inform. 2020, 16, 6575–6583. [Google Scholar] [CrossRef]
- Koutras, D.; Stergiopoulos, G.; Dasaklis, T.; Kotzanikolaou, P.; Glynos, D.; Douligeris, C. Security in IoMT Communications: A Survey. Sensors 2020, 20, 4828. [Google Scholar] [CrossRef] [PubMed]
- Aghili, S.F.; Mala, H.; Kaliyar, P.; Conti, M. SecLAP: Secure and lightweight RFID authentication protocol for Medical IoT. Future Gener. Comput. Syst. 2019, 101, 621–634. [Google Scholar] [CrossRef]
- Boucouvalas, A.; Chatzimisios, P.; Ghassemlooy, Z.; Uysal, M.; Yiannopoulos, K. Standards for indoor Optical Wireless Communications. IEEE Commun. Mag. 2015, 53, 24–31. [Google Scholar] [CrossRef]
- Hassan, S.S.; Bibon, S.D.; Hossain, M.S.; Atiquzzaman, M. Security threats in Bluetooth technology. Comput. Secur. 2018, 74, 308–322. [Google Scholar] [CrossRef]
- Zeadally, S.; Siddiqui, F.; Baig, Z. 25 Years of Bluetooth Technology. Future Internet 2019, 11, 194. [Google Scholar] [CrossRef]
- Figueroa Lorenzo, S.; Añorga Benito, J.; García Cardarelli, P.; Alberdi Garaia, J.; Arrizabalaga Juaristi, S. A Comprehensive Review of RFID and Bluetooth Security: Practical Analysis. Technologies 2019, 7, 15. [Google Scholar] [CrossRef]
- Jonas, K.; Vogl, B.; Rademacher, M. Security Mechanisms of wireless Building Automation Systems; Technical Report; Hochschule Bonn-Rhein-Sieg: Sankt Augustin, Germany, 2017. [Google Scholar] [CrossRef]
- Katharina, H.-S. A Formal Analysis of EnOcean’s Teach-in and Authentication. In Proceedings of the 16th International Conference on Availability, Reliability and Security, ACM International Conference Proceeding Series (ICPS), Vienna, Austria, 17–20 August 2021. [Google Scholar] [CrossRef]
- Pestourie, B. UWB Secure Ranging and Localization. Ph.D. Thesis, Université Grenoble Alpes, Grenoble, France, 4 December 2020. Available online: https://hal.archives-ouvertes.fr/tel-03136561/document (accessed on 4 October 2021).
- Rensburg, R.V. System Control Applications of Low-Power Radio Frequency Devices. J. Phys. Conf. Ser. 2017, 889. Available online: https://iopscience.iop.org/article/10.1088/1742-6596/889/1/012016/ (accessed on 4 October 2021). [CrossRef]
- Scholz, R.; Wressnegger, C. Security Analysis of Devolo HomePlug Devices. In Proceedings of the12th European Workshop on Systems Security, Dresden, Germany, 25 March 2019. [Google Scholar] [CrossRef]
- Dudek, S. HomePlugAV PLC: Practical attacks and backdooring. Additional information after the presentation made at NoSuchCon. 2014. Available online: https://penthertz.com/resources/NSC2014-HomePlugAV_attacks-Sebastien_Dudek.pdf (accessed on 4 October 2021).
- Nardo, M.D.; Yu, H. Intelligent Ventilation Systems in Mining Engineering: Is ZigBee WSN Technology the Best Choice? Appl. Syst. Innov. 2021, 4, 42. [Google Scholar] [CrossRef]
- Boom, B.V.D. State machine inference of Thread networking protocol. Bachelor’s Thesis, Radboud University, Nijmegen, The Netherlands, 29 June 2018. Available online: https://www.cs.ru.nl/bachelors-theses/2018/Bart_van_den_Boom___4382218___State_machine_inference_of_thread_networking_protocol.pdf (accessed on 4 October 2021).
- Coldrey, M.; Engström, U.; Helmersson, K.W.; Hashemi, M. Wireless backhaul in future heterogeneous networks. Ericsson Review. 2014. Available online: https://www.hit.bme.hu/~jakab/edu/litr/Mobile_backhaul/er-wireless-backhaul-hn.pdf (accessed on 4 October 2021).
- Liyanage, M.; Gurtov, A. Secured VPN Models for LTE Backhaul Networks. In Proceedings of the 2012 IEEE Vehicular Technology Conference (VTC Fall), Quebec City, QC, Canada, 3–6 September 2012; pp. 1–5. [Google Scholar] [CrossRef]
- Sharma, T.; Chehri, A.; Fortier, P. Review of optical and wireless backhaul networks and emerging trends of next generation 5G and 6G technologies. Trans. Emerg. Telecommun. Technol. 2021, 32, e4155. [Google Scholar] [CrossRef]
- Raza, H. A brief survey of radio access network backhaul evolution: Part II. IEEE Commun. Mag. 2013, 51, 170–177. [Google Scholar] [CrossRef]
- Chen, F.; Wang, N.; German, R.; Dressler, F. Simulation study of IEEE 802.15.4 LR-WPAN for industrial applications. Wirel. Commun. Mob. Comput. 2009, 10, 609–621. [Google Scholar] [CrossRef]
- Bembe, M.; Abu-Mahfouz, A.; Masonta, M.; Ngqondi, T. A survey on low-power wide area networks for IoT applications. Telecommun. Syst. 2019, 71, 249–274. [Google Scholar] [CrossRef]
- Rashmi, S.S.; Wei, Y.; Hwang, S.-H. A survey on LPWA technology: LoRa and NB-IoT. ICT Express 2016, 3, 1. [Google Scholar] [CrossRef]
- Joseph, F.; Stephen, B. A Comparative Survey of LPWA Networking. arXiv 2018, arXiv:1802.04222. Available online: https://arxiv.org/pdf/1802.04222.pdf (accessed on 4 October 2021).
- Pham, T.L.; Nguyen, H.; Nguyen, H.; Bui, V.; Nguyen, V.H.; Jang, Y.M. Low Power Wide Area Network Technologies for Smart Cities Applications. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju, South Korea, 16–18 October 2019. [Google Scholar] [CrossRef]
- Dhillon, H.S.; Huang, H.; Viswanathan, H. Wide-area Wireless Communication Challenges for the Internet of Things. IEEE Commun. Mag. 2017, 55, 168–174. [Google Scholar] [CrossRef]
- Martinez, B.; Adelantado, F.; Bartoli, A.; Vilajosana, X. Exploring the Performance Boundaries of NB-IoT. IEEE Internet Things J. 2019, 6, 5702–5712. [Google Scholar] [CrossRef]
- Hayouni, H.; Hamdi, M. A novel energy-efficient encryption algorithm for secure data in WSNs. J. Supercomput. 2021, 77, 4754–4777. [Google Scholar] [CrossRef]
- Tan, S.F.; Samsudin, A. A Survey of Homomorphic Encryption for Outsourced Big Data Computation. KSII Trans. Internet Inf. Syst. 2016, 1, 1–28. [Google Scholar] [CrossRef][Green Version]
- Tan, S.F.; Samsudin, A.; Suraya, A. Securing Big Data Processing with Homomorphic Encryption. TEST Eng. Manag. 2020, 82, 11980–11991. Available online: https://www.testmagzine.biz/index.php/testmagzine/article/view/2770/2442 (accessed on 4 October 2021).
- Ning, H.; Liu, H. Cyber-Physical-Social Based Security Architecture for Future Internet of Things. Adv. Internet Things 2012, 2, 1–7. [Google Scholar] [CrossRef]
- Gazis, V.; Gortz, M.; Huber, M.; Leonardi, A.; Mathioudakis, K.; Wiesmaier, A.; Vasilomanolakis, E. A survey of technologies for the internet of things. In Proceedings of the International Wireless Communications and Mobile Computing Conference (IWCMC), Dubrovnik, Croatia, 24–28 August 2015. [Google Scholar] [CrossRef]
- Tightiz, L.; Yang, H. A Comprehensive Review on IoT Protocols’ Features in Smart Grid Communication. Energies 2020, 13, 2762. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17(4), 2347–2376. [Google Scholar] [CrossRef]
- Babovic, Z.B.; Protic, J.; Milutinovic, V. Web Performance Evaluation for Internet of Things Applications. IEEE Access 2016, 4, 6974–6992. [Google Scholar] [CrossRef]
- Malisa, V.; Tourancheau, B.; Rousseau, F.; Duda, A.; Damon, L.; Guizzetti, R. OSCAR? Object Security Architecture for the Internet of Things. Ad Hoc Netw. 2015, 32, 3–16. [Google Scholar] [CrossRef]
- Akgün, M.; Çaglayan, M.U. Providing Destructive Privacy and Scalability in RFID Systems using PUFs. Ad Hoc Netw. 2015, 32, 32–42. [Google Scholar] [CrossRef]
- Biswas, K.; Muthukkumarasamy, V.; Wu, X.; Singh, K. Performance Evaluation of Block Ciphers for Wireless Sensor Networks. Adv. Comput. Commun. Technol. 2016, 452, 443–452. [Google Scholar] [CrossRef]
- Guo, X.; Hua, J.; Zhang, Y.; Wang, D. A Complexity-Reduced Block Encryption Algorithm Suitable for Internet of Things. IEEE Access 2019, 7, 54760–54769. [Google Scholar] [CrossRef]
- Malik, M.; Dutta, M.; Granjal, J.A. Survey of Key Bootstrapping Protocols Based on Public Key Cryptography in the Internet of Things. IEEE Access 2019, 27, 443–27464. [Google Scholar] [CrossRef]
- Tan, S.F.; Samsudin, A. Attribute Based Encryption—A Data Centric Approach for Securing Internet of Things (IoT). Adv. Sci. Lett. 2017, 23, 4219–4223. [Google Scholar] [CrossRef]
- Aintzane, M.-S.; Marc, B.; Jasone, A.; Aitor, U. Securing IIoT using Defence-in-Depth: Towards an End-to-End secure Industry 4.0. J. Manuf. Syst. 2020, 57, 367–378. [Google Scholar] [CrossRef]
- Jawhara, B.; Anna, L.M. Searchable Encryption with Access Control in Industrial Internet of Things (IIoT). Wirel. Commun. Mob. Comput. 2021, 2021, 5555362. [Google Scholar] [CrossRef]
| Year | Reference | S | I | G | O | Focuses |
|---|---|---|---|---|---|---|
| 2010 | Atzori et al. [1] | √ | √ | √ | Data integrity and privacy issues specifically on wireless technologies: RFID and WSN | |
| Weber [2] | √ | Limited to address data and privacy legislation of the IoT and RFID | ||||
| 2012 | Miorandi et al. [3] | √ | √ | √ | A general overview of data confidentiality, privacy and trust specifically on distributed intelligence, communication and identification technologies | |
| 2013 | Zhao and Ge [4] | √ | √ | A brief discussion of security attacks and measurements based on three-layer IoT architecture (perception layer, transport layer and application layer) | ||
| 2014 | Ziegeldorf et al. [5] | √ | A general overview of IoT privacy threats and challenges | |||
| Jing et al. [6] | √ | √ | √ | Analyze the cross-layer heterogenous and security issues of three-layer IoT architecture (Perception layer, transport layer and application layer) and focuses specifically on WSN and RFID | ||
| 2015 | Fremantle and Scott [7] | √ | √ | √ | Middleware systems and their security properties, as well as a very brief discussion on future works | |
| Granjal et al. [8] | √ | √ | IoT communication protocols and technologies specifically on MAC and Physical layers | |||
| Nguyen et al. [9] | √ | √ | IoT security protocols and key distribution specifically on WSN | |||
| 2016 | Airehrour et al. [10] | √ | √ | √ | Secure routing protocols and trust models | |
| Qin et al. [11] | √ | √ | Review IoT from a data-centric perspective, specifically on RFID | |||
| 2017 | Loi et al. [12] | √ | √ | √ | Comprehensive security analysis on consumer IoT Devices | |
| 2018 | Fernández-Caramés et al. [13] | √ | √ | Blockchain-based IoT application | ||
| 2019 | Hassija et al. [14] | √ | √ | Studies on the relationship between IoT application and related technologies: blockchain, machine learning, fog and cloud computing | ||
| Berkay et al. [15] | √ | √ | Security analysis of IoT programming platforms | |||
| Tabrizi and Pattabiraman [16] | √ | √ | Design-level and code-level security analysis on IoT devices | |||
| 2020 | Amanullah et al. [17] | √ | √ | √ | Comparative analysis on the relationship of IoT security, deep learning and big data technologies | |
| Lao et al. [18] | √ | √ | √ | A review on blockchain-based IoT architecture | ||
| Joao et al. [19] | √ | √ | A general review on threat models and attack path of IoT | |||
| 2021 | Polychronou et al. [20] | √ | √ | Software attacks targeting hardware vulnerabilities and deep learning detection mechanisms in IIoT | ||
| Gaspar et al. [21] | √ | √ | A general IoT technologies review on Portugal’s Agro-Industry | |||
| Wu et al. [22] | √ | √ | Relations between machine learning and blockchain in IIoT | |||
| Latif et al. [23] | √ | √ | A general review on blockchain-based decentralized IIoT security |
| Concerns | Conventional System | IIoT |
|---|---|---|
| Connected Nodes/Devices | Small to medium volume within the local networks | Billions of sensor nodes, actuators and automation devices connected |
| Communication Networks | Homogenous | Heterogeneous |
| System Scalability | Optional | High scalability The design of IIoT security systems should consider the identification and authentication of an enormous scale of “things”, scalability of communication networks and security key distribution and revocation issues in future |
| System Interoperability | Optional | High interoperability Diverse security mechanisms and defence systems over the distributed networks must be standardized and compatible with each other to communicate, exchange and process data securely |
| Collected Data Types | Unified encoding scheme and data format, structured data | Confluent with the terms of “big data” characteristic:
|
| Data Processing Model | Moving data to process, moderate speed | Moving processing to data. In most industrial cases, high velocity necessitates real-time analytical processing |
| Security and Privacy Concerns | Data-at-rest Data-in-memory Data-in-transit | Data-at-rest Data-in-memory Data-in-transit Data-in-transform |
| Authentication and Access Control Mechanisms | Centralized Approach | Distributed, decentralized approach Lightweight scheme |
| Security Requirements | Description | IIoT Security Properties |
|---|---|---|
| Confidentially(C) | The protection of IIoT from unauthorized disclosure and access. | The security defences and mechanisms should be able to:
|
| Integrity(I) | The assurance of IIoT consistency, accuracy, and trustworthiness of data or services over its entire life cycle. | The security mechanisms should be able to detect any data modification and manipulation such as insertion, deletion or replay attacks on the “things” or data of IIoT. |
| Authentication(A) | The assurance that the communicating entity is the one that it claims to be. | The security mechanisms should be able to ensure:
|
| Authorization and Access Control (A) | The prevention of unauthorized use of IIoT resources. | The security mechanisms should be able to ensure:
|
| Availability (A) | The assurance that the IIoT resources are always available. | The security defences and mechanisms should prevent or detect denial of service attacks on IIoT resources. |
| Security Dimensions | Security Risks and Threats | Deployed Security Countermeasures | Ongoing Challenges and Future Research Works |
|---|---|---|---|
| Confidentiality and Privacy |
|
|
|
| Integrity |
|
|
|
| Authentication |
|
|
|
| Authorization and Access Control |
|
|
|
| Availability |
|
|
|
| Security Dimensions | Security Risks and Threats | Deployed Security Countermeasures | Ongoing Challenges and Future Research Works |
|---|---|---|---|
| Confidentiality and Privacy |
|
| |
| Integrity |
|
|
|
| Authentication |
|
|
|
| Authorization and Access Control |
|
|
|
| Availability |
|
|
|
| Security Dimensions | Security Risks, Threats and Ongoing Challenges | Deployed Security Countermeasures | Ongoing Challenges and Future Woks |
|---|---|---|---|
| Confidentiality and Privacy |
|
|
|
| Integrity and Authentication |
|
|
|
| Authorization and Access Control |
|
|
|
| Availability |
|
|
|
| Technology /Standard | Features/ Functionalities | Analysis of Security Requirement | Deployed Security Countermeasures | Ongoing Challenges and Future Woks | |||
|---|---|---|---|---|---|---|---|
| C | I | A | V | ||||
| IrDA | Use infrared light in a range of <1 m; Application: remote control, data transfer | × | × | × | × |
|
|
| RFID | Radio waves with 125 kHz, 13.56 MHz or 902 to 928 MHz within the range of 1 m; Application: tracking, inventory access | √ | √ | √ | √ |
|
|
| NFC | Radio waves with 13.56 MHz, range less than 30 m; Application: payment system, access control, tracking, assisted living | √ | √ | √ | × | ECMA International established several NFC security standards to ensure secure channel and shared service (ECMA-385), data confidentiality and integrity with AES and ECDH (ECMA-386), data authenticated encryption with 256-bit ECDH key agreement and AES in GCM mode (ECMA-409), mutual authentication mechanisms, either with asymmetric cryptography (ECMA-410) or symmetric cryptographic (ECMA-411) |
|
| INSTEON | Radio waves with 902 to 924 MHz, range less than 50 m; Application: home automation, domestics | √ | √ | √ | × | INSTEON provides limited security protection as follows:
| Current security mechanisms are less efficient against recent network penetration attacks (e.g., eavesdropping attack by guessing device address). Therefore, more robust access control and authorization mechanisms and lightweight data encryption are needed instead relies on extended message payloads |
| Bluetooth | Radio waves with 2.4 GHz Medium within range of 10 m and up to 100 m with a higher power; Application: wireless headsets, audio apps, health, animal tagging, intelligent transport systems, Smart home, automotive | √ | √ | √ | × |
| Short password-based security is vulnerable to password guessing attacks, randomness PIN, scalability of PIN management [84,85,86] |
| Bluetooth Smart/BLE | Radio waves with 2.4 GHz Medium, Range: >100 m, Application: wearables, gaming, healthcare, sport and fitness | √ | √ | √ | × | Enjoys similar security protection as Bluetooth technologies; however, it enforces stronger security features as follows:
| Do not implement end-to-end security and still vulnerable to pairing eavesdropping, man-in-the-middle attacks, DoS attack, fuzzing attack, SSP attack, bluesnarfing, bluebugging, bluejacking [85,86,87] |
| EnOcean Energy harvesting wireless | Radio Waves with 902.875, 928.35 MHz, 868 MHz, 315 MH within a range up to 30 m (inside buildings) and 300 m (open-air); Application: building automation, transportation, smart home, domestics | √ | √ | √ | × |
| Security mechanisms for ensuring availability of service and preventing DoS attack, lightweight encryption algorithm and authentication mechanisms [88,89] |
| Ultra-wideband (UWB) low power and high speed data | Radio waves with 3.1 MHz to 10.6 GHz, Range: <10 m, Application: target detection and tracking, precision navigation, search and rescue, geographic routing, security surveillance, automotive | √ | √ | √ | √ |
| Secure positioning algorithms such as pseudo-random turnaround delay protocol, secure localization and authentication algorithm such as SLS, secure device pairing algorithm [90] |
| ANT+ | Radio waves with 2.4 GHz, Range: <10 m; Application: Health and Sport & Fitness Monitoring, Intelligent Transport System, Assisted Live | √ | √ | × | × |
| AES encryption cannot be used in multichannel mode, forcing the usage of single-channel communications. |
| HomePlug | Power link communication; Application: smart home, home automation and control and electric vehicle communication applications | √ | √ | √ | × |
| Detected network security vulnerabilities, subjected to remote attacks under default security and authentication settings, lightweight and stronger security mechanisms [92,93] |
| ZigBee | Radio Waves with 2.4 GHz, Range: <10 m; Application: home monitoring and control, security, smart applications, intelligent transport system, animal tagging, positioning and tracking | √ | √ | √ | × |
| Still vulnerable to RF-based attacks such as frequency jamming attacks, stronger and lightweight security mechanisms [88,94] |
| ISA110.11a | Radio waves with 2.4 GHz, Range: <10 m; Application: industrial monitoring and control | √ | √ | √ | × |
| Password-based schemes such as lightweight hash function enforce availability into security mechanisms, lightweight and stronger encryption algorithm |
| Wireless-HART | Radio waves with 2.4 GHz, Range: <10 m; Application: industrial monitoring and control | √ | √ | √ | × |
| Security mechanisms for ensuring availability of service and preventing DoS attack, lightweight encryption algorithm and authentication mechanisms |
| Thread | Radio waves with 2.4 GHz, Range: <10 m; Application: smart home, building, domestics | √ | √ | √ | × | End-to-end communication and data protection mechanisms | |
| Technology/Standard | Features/ Functionalities | Analysis of Security Requirement | Deployed Industry Countermeasure | Ongoing Challenges and Future Woks | |||
|---|---|---|---|---|---|---|---|
| C | I | A | V | ||||
| 802.3 Ethernet | Range: up to 100 m, Mobility: Portable Bandwidth: 10 Mbps to 10 Gbps shared | √ | √ | √ | × | Enforce confidentiality, integrity, authentication and access control with the following standards:
| Address the reliability, scalability of bandwidth and network size, redundancy and fast network recovery, interoperability with existing commercial standards, employ stronger and lightweight security mechanisms, access control mechanisms such as identity-based or attribute-based access control. |
| 802.11 WLAN/WiFi | Range: 30 m, Mobility: Portable Frequency: 2.4 GHz (802.11b/g), 5.2 GHz (802.11a) Bandwidth: 11–54 Mbps shared | √ | √ | √ | × | Enforce several security modes to ensure confidentiality, authentication, integrity and access control as follows:
|
|
| 802.15.4 LR-WPAN | Range: <10 m Mobility: portable frequency: 868 MHz, 915 MHz, 2450 MHz Bandwidth: up to 250 Kbit/s. | √ | √ | √ | × | Security Specification offers several options of security suites that fulfil different security requirements as follows.
|
|
| 802.16 WiMax | Range: 30 km–50 km, Mobility: Fixed (Mobile -802.16e-2005), Frequency: 2–11 GHz and 23.5–43.5 GHz (802.16a), Bandwidth: up to 70 Mbps shared | √ | √ | √ | × | Enforce confidentiality, integrity, authentication and access control with the IEEE 802.16-2004, IEEE 802.16e-2005, IEEE 802.16-2009, IEEE 802.16j-2009 that provides: -
|
|
| UMTS 3G | Range: UMTS coverage Mobility: full mobility, Frequency: UMTS frequency bands varies on countries (e.g., 2100 MHz for China and Asia, 1900 MHz for US) Bandwidth: 384 Kbps–2 Mbps | √ | √ | √ | × | Provides a better security solution to GSM solutions as follows.
|
|
| Technology/Standard | Features/ Functionalities | Analysis of Security Requirement | Deployed Security Countermeasures | Ongoing Challenges and Future Research Woks | |||
|---|---|---|---|---|---|---|---|
| C | I | A | V | ||||
| NB-IoT | Radio Waves: 1.4 MHz, 20 MHz,180 kHz Range: Application: smart home, smart city, automotive, energy and logistic | √ | √ | √ | × | Inherits some of the existing LTE security features and uses a partial ciphering mechanism to ensure user data security.
| Lightweight EEA and EIA mechanisms [106] |
| Link Labs LoRaWAN | Radio waves: 868 MHz and 915 MHz Range: 7.2 km Network topology: star on star Application: smart cities, smart home | √ | √ | √ | × |
|
|
| WAVIoT NB-Fi (cloud-based) | Radio Waves: 915 MHz, 868 MHz, 500 MHz and 433 MHz Range: Up to 16 km in the city and 50 km in the countryside Application: Water Metering, Smart Grid control, parking, smart home, security surveillance | √ | - | - | - | Employ symmetric cipher eXtended Tiny Encryption Algorithm (XTEA) to ensure data confidentiality with the length of 256 key.
| XTEA algorithm is subjected to several differential attacks [107] |
| NWAVE Weightless-P (Weightless-N, Weightless-W) | Radio Waves: 169 MHz, 433 MHz, 470 MHz, 780 MHz, 868 MHz, 915 MHz, 923 MHz Range: 2 km–5 km Network Topology: Star Application: automotive, sensors, asset tracking, healthcare | √ | × | √ | × | Password-based authentication and access control mechanisms, data encryption algorithm with AES-128 or AES-256, nonce for preventing replay attack, use temporary device identifiers for privacy protection | Short-password based security mechanism |
| SigFox UNB Cloud-based | Radio Wave:868 MHz (Europe, Middle East), 902 MHz (North America), 920 MHz (South America, Australia, New Zealand), Range: 9.5 km, Application: Smart Cities, Asset Management, Water Metering, Healthcare, pet tracking, climate monitoring | √ | √ | √ | × | Unique device ID for ensuring identification and authentication via AES encrypted signature, use the sequence number to prevent spoofing attack on transmitted message, data encryption with AES-128 |
|
| Ingenu RPMA | Radio Waves:2.4 GHz Range: 4.6 km Network topology: star application: smart parking, transportation, tracking, smart building | √ | √ | √ | × | Provides message confidentiality with a 256-bit encryption algorithm, uses a 16-byte hash function for message integrity, subsequently meets the FIPS 140-2 Level 2 encryption standards (e.g., tamper-evidence against unauthorized physical access, role-based authentication, etc.) | Availability and assurance mechanism |
| DASH7 | Radio Waves: 915 MHz, 868 MHz, 500 MHz and 433 MHz Range: 2 km Network topology: star, tree, node-to-node, Application: water metering, smart grid control, parking, smart home, security surveillance | √ | √ | √ | × | Employs AES-128-bit shared encryption, subsequently enforce security properties with data link layer security (AES-128 in EAX mode for authentication and confidentiality, 32-bit integrity check, 56-bit Nonce, 32-bit authentication tag), network layer security and application layer security (secure exchange protocol that possibly constructed part of IPSec. | End-to-end protection |
| Technology/ Standard | Features/ Functionalities | Analysis of Security Requirement | Deployed Security Countermeasures | Ongoing Challenges and Future Woks | |||
|---|---|---|---|---|---|---|---|
| C | I | A | V | ||||
| SOAP | Transport Protocol: HTTP (common use), SMTP, TCP, UDP, JMS; Implement QoS; Architecture: Request/response | √ | √ | √ | × | Use web service security (WS-Security) or SSL to ensure confidentiality, integrity, authentication and access control via:
|
|
| CoAP | Transport Protocol: UDP; Implement QoS; Architecture: request/response | √ | √ | √ | √ | Use Datagram Transport Layer Security (DTLS) that inherits some security feature from TLS/SSL, either:
|
|
| REST HTTP | Transport Protocol: HTTP; no implement QoS; Architecture: request/response | √ | √ | √ | × | Use Hypertext Transfer Protocol Secure (HTTPS) that leverages the Transport Layer Security/Secure Socket Layer (TLS/SSL) to provide session-oriented security as follows:
|
|
| MQTT | Transport Protocol: TCP; Implement QoS; Architecture: Publish/Subscribe | √ | √ | √ | × |
| |
| XMPP | Transport Protocol: TCP; No Implement QoS; Architecture: Publish/subscribe and request/response | √ | √ | √ | × | ||
| AMQP | Transport Protocol: TCP; Implement QoS; Architecture: publish/subscribe | √ | √ | √ | × | ||
| DDS | Transport Protocol: TCP; Implement QoS; Architecture: publish/subscribe | √ | √ | √ | × | Based on DDS Security Version 1.0 -Beta 2: Confidentiality with symmetric cryptography AES-128/AES-256
|
|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tan, S.F.; Samsudin, A. Recent Technologies, Security Countermeasure and Ongoing Challenges of Industrial Internet of Things (IIoT): A Survey. Sensors 2021, 21, 6647. https://doi.org/10.3390/s21196647
Tan SF, Samsudin A. Recent Technologies, Security Countermeasure and Ongoing Challenges of Industrial Internet of Things (IIoT): A Survey. Sensors. 2021; 21(19):6647. https://doi.org/10.3390/s21196647
Chicago/Turabian StyleTan, Soo Fun, and Azman Samsudin. 2021. "Recent Technologies, Security Countermeasure and Ongoing Challenges of Industrial Internet of Things (IIoT): A Survey" Sensors 21, no. 19: 6647. https://doi.org/10.3390/s21196647
APA StyleTan, S. F., & Samsudin, A. (2021). Recent Technologies, Security Countermeasure and Ongoing Challenges of Industrial Internet of Things (IIoT): A Survey. Sensors, 21(19), 6647. https://doi.org/10.3390/s21196647






