Image Privacy Protection Communication Scheme by Fibonacci Interleaved Diffusion and Non-Degenerate Discrete Chaos
Abstract
1. Introduction
- This encryption algorithm introduces a novel diffusion mechanism. By leveraging the principles of Fibonacci-related mathematics, a Fibonacci sequence interleaved diffusion method is devised, which effectively resists statistical analysis and enhances the security of encryption.
- The majority of existing encryption algorithms are susceptible to potential risks. This image privacy protection scheme employs plaintext correlation to generate dynamic chaotic keys, significantly enhancing the ability to resist cryptographic attacks.
- A significant number of the encryption algorithms currently in use are considered to be unreasonable. In the absence of relevant plaintext or ciphertext feedback, they become highly vulnerable to known-plaintext or chosen-plaintext attacks. In order to address this issue, the proposed secure image encryption scheme employs a dynamic feedback mechanism to continuously update encryption keys based on encrypted data. Building upon our current foundation of cryptanalysis research [52,53,54], it enhances security and strengthens the ability to withstand attacks like chosen-plaintext and chosen-ciphertext attacks.
2. Related Theory
2.1. Non-Degenerate Chaotic System
2.2. Fibonacci Q Matrix
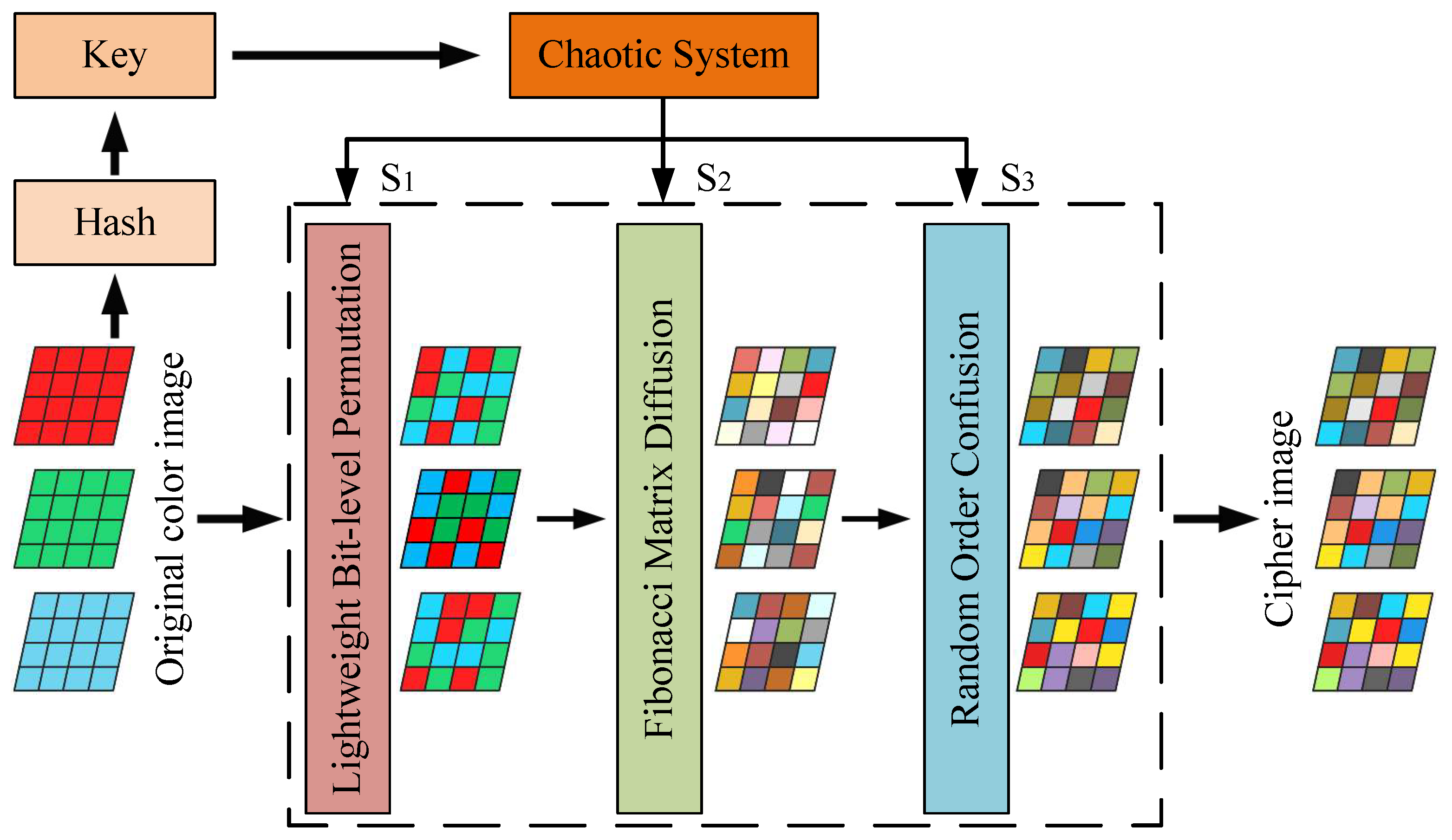
3. The Proposed Encryption Algorithm
3.1. Chaos Key Generation and Sequence Preprocessing
3.2. Lightweight Bit-Level Permutation
| Algorithm 1 Lightweight Bit-level Permutation |
| Require: Chaotic sequence ; plaintext image P of size Ensure: Intermediate ciphertext image
|
3.3. Fibonacci Matrix Diffusion
| Algorithm 2 Fibonacci Matrix Diffusion |
| Require: Chaotic matrix ; intermediate image of size Ensure: Diffused ciphertext image
|
3.4. Random Direction Confusion
| Algorithm 3 Random Direction Confusion |
| Require: Computing matrix S; index matrix I; intermediate ciphertext of size Ensure: Final ciphertext
|
4. Experimental Results and Analysis Discussion
4.1. Histogram Analysis
4.2. The Coefficient of Adjacent Pixels
4.3. Differential Attack Analysis
4.4. Image Quality Analysis
4.5. Information Entropy Analysis
4.6. Key Space Analysis
4.7. Analysis of Plaintext Sensitivity
4.8. Theoretical Security Analysis of Fibonacci Diffusion
4.8.1. Effective Nonlinearity Through Dynamic Matrix Diffusion
- Exponential Amplification: Elements of follow the Fibonacci recurrence , with growth rate , where . As n increases, even minor differences in are exponentially amplified.
- Path Confusion: The dynamic index , derived from a chaotic sequence , assigns a unique matrix to each block, disrupting any attempt at consistent linear modeling across the image.
4.8.2. Resistance to Differential Cryptanalysis
4.8.3. Key Sensitivity Analysis
4.8.4. Resistance to Algebraic Attacks
- Each block generates four linear equations but includes six unknowns: four matrix entries of and two plaintext variables.
- The chaotic index n differs per block, preventing consistent coefficient reuse and eliminating possibilities of system-wide equation alignment.
- The modular reduction operation () introduces nonlinear discontinuities (wrap-around effects), further complicating algebraic inference.
4.9. Cryptanalysis of the Proposed Encryption Algorithm
- 170 (10101010): Probes alternating bit patterns.
- 255 (11111111): Evaluates all-one input handling.
4.10. Run Time Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Lai, Q.; Liu, Y.; Yang, L. Image encryption using memristive hyperchaos. Appl. Intell. 2023, 53, 22863–22881. [Google Scholar] [CrossRef]
- Lu, X.; Xie, E.Y.; Li, C. Periodicity Analysis of Logistic Map over Ring Z3n. Int. J. Bifurc. Chaos 2023, 33, 2350063. [Google Scholar] [CrossRef]
- Ma, Y.; Li, C.; Ou, B. Cryptanalysis of an image block encryption algorithm based on chaotic maps. J. Inf. Secur. Appl. 2020, 54, 102566. [Google Scholar] [CrossRef]
- Zeng, W.; Zhang, C.; Xia, J.; Liang, X.; Lin, Y.; Li, Y.; Wang, S.; Yang, G. Chaotic 4D Modulation with Intrusion Detection for Secure Data Centers. J. Light. Technol. 2025, 1–10. [Google Scholar] [CrossRef]
- Chai, X.; Wang, Y.; Gan, Z.; Chen, X.; Zhang, Y. Preserving privacy while revealing thumbnail for content-based encrypted image retrieval in the cloud. Inf. Sci. 2022, 604, 115–141. [Google Scholar] [CrossRef]
- Yu, F.; Gong, X.; Li, H.; Wang, S. Differential cryptanalysis of image cipher using block-based scrambling and image filtering. Inf. Sci. 2021, 554, 145–156. [Google Scholar] [CrossRef]
- Chai, X.; Fu, J.; Gan, Z.; Lu, Y.; Zhang, Y. An image encryption scheme based on multi-objective optimization and block compressed sensing. Nonlinear Dyn. 2022, 108, 2671–2704. [Google Scholar] [CrossRef]
- Kocak, O.; Erkan, U.; Toktas, A.; Gao, S. PSO-based image encryption scheme using modular integrated logistic exponential map. Expert Syst. Appl. 2023, 237, 121452. [Google Scholar] [CrossRef]
- Toktas, A.; Erkan, U.; Gao, S.; Pak, C. A robust bit-level image encryption based on Bessel map. Appl. Math. Comput. 2024, 462, 128340. [Google Scholar] [CrossRef]
- Gao, S.; Liu, S.; Wang, X.; Wu, R.; Wang, J.; Li, Q.; Tang, X. New image encryption algorithm based on hyperchaotic 3D-IHAL and a hybrid cryptosystem. Appl. Intell. 2023, 53, 27826–27843. [Google Scholar] [CrossRef]
- Li, Q.; Wang, X.; Wang, H.; Ye, X.; Zhou, S.; Gao, S.; Shi, Y. A secure image protection algorithm by steganography and encryption using the 2D-TSCC. Chin. Phys. B 2021, 30, 110501. [Google Scholar] [CrossRef]
- Li, Q.; Ma, B.; Wang, X.; Wang, C.; Gao, S. Image Steganography in Color Conversion. IEEE Trans. Circuits Syst. II Express Briefs 2024, 71, 106–110. [Google Scholar] [CrossRef]
- Wen, W.; Huang, H.; Qi, S.; Zhang, Y.; Fang, Y. Joint Coverless Steganography and Image Transformation for Covert Communication of Secret Messages. IEEE Trans. Netw. Sci. Eng. 2024, 11, 2951–2962. [Google Scholar] [CrossRef]
- Liu, H.; Teng, L.; Zhang, Y.; Si, R.; Liu, P. Mutil-medical image encryption by a new spatiotemporal chaos model and DNA new computing for information security. Expert Syst. Appl. 2023, 235, 121090. [Google Scholar] [CrossRef]
- Wen, H.; Xie, Z.; Wu, Z.; Lin, Y.; Feng, W. Exploring the future application of UAVs: Face image privacy protection scheme based on chaos and DNA cryptography. J. King Saud Univ.—Comput. Inf. Sci. 2023, 36, 101871. [Google Scholar] [CrossRef]
- Wang, X.; Gao, S. Image encryption algorithm based on the matrix semi-tensor product with a compound secret key produced by a Boolean network. Inf. Sci. 2020, 539, 195–214. [Google Scholar] [CrossRef]
- Gao, S.; Wu, R.; Wang, X.; Liu, J.; Li, Q.; Tang, X. EFR-CSTP: Encryption for face recognition based on the chaos and semi-tensor product theory. Inf. Sci. 2022, 621, 766–781. [Google Scholar] [CrossRef]
- Wang, X.; Gao, S. A chaotic image encryption algorithm based on a counting system and the semi-tensor product. Multimed. Tools Appl. 2020, 80, 10301–10322. [Google Scholar] [CrossRef]
- Zhou, S.; Wei, Y.; Zhang, Y.; Iu, H.; Zhang, H. Image encryption algorithm based on the dynamic RNA computing and a new chaotic map. Integration 2024, 101, 102336. [Google Scholar] [CrossRef]
- Vikas; Parhi, D.R. Chaos-based optimal path planning of humanoid robot using hybridized regression-gravity search algorithm in static and dynamic terrains. Appl. Soft Comput. 2023, 140, 110236. [Google Scholar] [CrossRef]
- Gao, S.; Iu, H.H.C.; Mou, J.; Erkan, U.; Liu, J.; Wu, R.; Tang, X. Temporal action segmentation for video encryption. Chaos Solitons Fractals 2024, 183, 114958. [Google Scholar] [CrossRef]
- Xiang, Y.; Xiao, D.; Zhang, R.; Liang, J.; Liu, R. Cryptanalysis and improvement of a reversible data-hiding scheme in encrypted images by redundant space transfer. Inf. Sci. 2021, 545, 188–206. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, J.; Chen, Y.; Qin, Z.; Zhang, Y.; Ahmad, M.; Woźniak, M. Exploiting robust quadratic polynomial hyperchaotic map and pixel fusion strategy for efficient image encryption. Expert Syst. Appl. 2024, 246, 123190. [Google Scholar] [CrossRef]
- Gao, S.; Iu, H.H.C.; Wang, M.; Jiang, D.; El-latif, A.; Wu, R.; Tang, X. Design, Hardware Implementation, and Application in Video Encryption of the 2D Memristive Cubic Map. IEEE Internet Things J. 2024, 11, 21807–21815. [Google Scholar] [CrossRef]
- Gao, S.; Wu, R.; Wang, X.; Liu, J.; Li, Q.; Wang, C.; Tang, X. Asynchronous Updating Boolean Network Encryption Algorithm. IEEE Trans. Circuits Syst. Video Technol. 2023, 33, 4388–4400. [Google Scholar] [CrossRef]
- Li, Q.; Li, Q.; Ling, B.; Pun, C.M.; Huang, G.; Yuan, X.; Zhong, G.; Ayouni, S.; Chen, J. DPPAD-IE: Dynamic Polyhedra Permutating and Arnold Diffusing Medical Image Encryption Using 2D Cross Gaussian Hyperchaotic Map. IEEE Trans. Consum. Electron. 2025; early access. [Google Scholar] [CrossRef]
- Xing, Z.; Lam, C.T.; Yuan, X.; Im, S.K.; Machado, P. MMQW: Multi-Modal Quantum Watermarking Scheme. IEEE Trans. Inf. Forensics Secur. 2024, 19, 5181–5195. [Google Scholar] [CrossRef]
- Xu, X.; Zhang, T.; Zhao, Y.; Dai, W.; Wu, S.; Li, G. Application of two general Memristor models in chaotic systems. In Memristors—The Fourth Fundamental Circuit Element—Theory, Device, and Applications; IntechOpen: Rijeka, Croatia, 2023. [Google Scholar]
- Gu, Y.; Li, G.; Xu, X.; Song, X.; Wu, S. Multistable dynamics and attractors self-reproducing in a new hyperchaotic complex Lü system. Chaos Interdiscip. J. Nonlinear Sci. 2023, 33, 093112. [Google Scholar] [CrossRef] [PubMed]
- He, P.; Liu, H.; Li, G.; Xu, X.; Gu, Y. A general method for generating multi-scroll and multi-wing chaotic systems and its implementation of attractor reproduction. Phys. Scr. 2023, 98, 085232. [Google Scholar] [CrossRef]
- Zheng, H.; Li, G.; Xu, W.; Zhong, H.; Xu, X. A compressive sensing encryption scheme for dual color images based on discrete memristor map and Rubik’s cube scramble. Optik 2023, 286, 170991. [Google Scholar] [CrossRef]
- Wu, S.; Li, G.; Xu, W.; Xu, X.; Zhong, H. Modelling and dynamic analysis of a novel seven-dimensional Hamilton conservative hyperchaotic systems with wide range of parameter. Phys. Scr. 2023, 98, 055218. [Google Scholar] [CrossRef]
- Xie, Z.; Lin, Y.; Liu, T.; Wen, H. Face privacy protection scheme by security-enhanced encryption structure and nonlinear dynamics. iScience 2024, 27, 110768. [Google Scholar] [CrossRef]
- Zhou, S.; Zhang, Q.; He, S.; Zhang, Y. What is the lowest cost to calculate the Lyapunov exponents from fractional differential equations? Nonlinear Dyn. 2025, 113, 14825–14871. [Google Scholar] [CrossRef]
- Zeng, W.; Zhang, C.; Liang, X.; Xia, J.; Lin, Y.; Lin, Y. Intrusion Detection-Embedded Chaotic Encryption via Hybrid Modulation for Data Center Interconnects. Opt. Lett. 2025, 50, 4450–4453. [Google Scholar] [CrossRef] [PubMed]
- Gao, S.; Iu, H.H.; Erkan, U.; Şimşek, C.; Toktas, A.; Cao, Y.; Wu, R.; Mou, J.; Li, Q.; Wang, C. A 3D Memristive Cubic Map with Dual Discrete Memristors: Design, Implementation, and Application in Image Encryption. IEEE Trans. Circuits Syst. Video Technol. 2025; early access. [Google Scholar]
- Zeng, W.; Zhang, C.; Liang, X.; Lin, Y.; Xia, J.; Li, Y. A Novel Secure Key Stream Generator Based on Chaotic Multi-State Cellular Automata. IEEE Internet Things J. 2025, 1. [Google Scholar] [CrossRef]
- Lin, Y.; Xie, Z.; Chen, T.; Cheng, X.; Wen, H. Image privacy protection scheme based on high-quality reconstruction DCT compression and nonlinear dynamics. Expert Syst. Appl. 2024, 257, 124891. [Google Scholar] [CrossRef]
- Kumar, S. Image data security using Quasigroup combined with Fibonacci Q-transformation. J. Inf. Secur. Appl. 2021, 61, 102941. [Google Scholar] [CrossRef]
- Maiti, C.; Dhara, B.C.; Umer, S.; Asari, V. An Efficient and Secure Method of Plaintext-Based Image Encryption Using Fibonacci and Tribonacci Transformations. IEEE Access 2023, 11, 48421–48440. [Google Scholar] [CrossRef]
- Bouarroudj, R.; Souami, F.; Zohra Bellala, F.; Zerrouki, N. A reversible fragile watermarking technique using fourier transform and Fibonacci Q-matrix for medical image authentication. Biomed. Signal Process. Control 2024, 92, 105967. [Google Scholar] [CrossRef]
- Wen, H.; Lin, Y.; Xie, Z.; Liu, T. Chaos-based block permutation and dynamic sequence multiplexing for video encryption. Sci. Rep. 2023, 13, 14721. [Google Scholar] [CrossRef]
- Zhou, Y.; Bao, L.; Chen, C.P. A new 1D chaotic system for image encryption. Signal Process. 2014, 97, 172–182. [Google Scholar] [CrossRef]
- Chai, X.; Tang, Z.; Gan, Z.; Lu, Y.; Wang, B.; Zhang, Y. SE-NDEND: A novel symmetric watermarking framework with neural network-based chaotic encryption for Internet of Medical Things. Biomed. Signal Process. Control 2024, 90, 105877. [Google Scholar] [CrossRef]
- Zeng, W.; Zhang, C.; Liang, X.; Luo, Y.; Wang, X.; Qiu, K. Chaotic phase noise-like encryption based on geometric shaping for coherent data center interconnections. Opt. Express 2023, 32, 1595–1608. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Feng, B.; Lü, J.; Hao, F. Cryptanalysis of a Chaotic Image Encryption Algorithm Based on Information Entropy. IEEE Access 2018, 6, 75834–75842. [Google Scholar] [CrossRef]
- Xie, E.Y.; Li, C.; Yu, S.; Lu, J. On the cryptanalysis of Fridrich’s chaotic image encryption scheme. Signal Process. 2016, 132, 150–154. [Google Scholar] [CrossRef]
- Liao, Y.; Lin, Y.; Li, Q.; Xing, Z.; Yuan, X. Lightweight Image Encryption Algorithm Using 4D-NDS: Compound Dynamic Diffusion and Single-Round Efficiency. IEEE Access 2025, 13, 74652–74662. [Google Scholar] [CrossRef]
- Zhou, S.; Yin, Y.; Erkan, U.; Toktas, A.; Zhang, Y. Novel hyperchaotic system: Implementation to audio encryption. Chaos Solitons Fractals 2025, 193, 116088. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, T.; Zhao, R.; Wen, W.; Zhu, Y. RAPP: Reversible Privacy Preservation for Various Face Attributes. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3074–3087. [Google Scholar] [CrossRef]
- Liao, Y.; Lin, Y.; Zheng, X.; Yuan, X. Privacy Image Secrecy Scheme Based on Chaos-Driven Fractal Sorting Matrix and Fibonacci Q-Matrix. Vis. Comput. 2025, 41, 6931–6941. [Google Scholar]
- Wen, H.; Lin, Y. Cryptanalysis of an image encryption algorithm using quantum chaotic map and DNA coding. Expert Syst. Appl. 2023, 237, 121514. [Google Scholar] [CrossRef]
- Wen, H.; Lin, Y.; Feng, Z. Cryptanalyzing a bit-level image encryption algorithm based on chaotic maps. Eng. Sci. Technol. Int. J. 2024, 51, 101634. [Google Scholar] [CrossRef]
- Wen, H.; Lin, Y. Cryptanalyzing an image cipher using multiple chaos and DNA operations. J. King Saud Univ.—Comput. Inf. Sci. 2023, 35, 101612. [Google Scholar] [CrossRef]
- Wen, H.; Liu, Z.; Lai, H.; Zhang, C.; Liu, L.; Yang, J.; Lin, Y.; Li, Y.; Liao, Y.; Ma, L.; et al. Secure DNA-Coding Image Optical Communication Using Non-Degenerate Hyperchaos and Dynamic Secret-Key. Mathematics 2022, 10, 3180. [Google Scholar] [CrossRef]
- Zhang, H.; Hu, H.; Ding, W. VSDHS-CIEA: Color image encryption algorithm based on novel variable-structure discrete hyperchaotic system and cross-plane confusion strategy. Inf. Sci. 2024, 665, 120332. [Google Scholar] [CrossRef]
- Peng, Y.; Lan, Z.; Sun, K.; Xu, W. A simple color image encryption algorithm based on a discrete memristive hyperchaotic map and time-controllable operation. Opt. Laser Technol. 2023, 165, 109543. [Google Scholar] [CrossRef]
- Zhang, H.; Hu, H. An image encryption algorithm based on a compound-coupled chaotic system. Digit. Signal Process. 2023, 146, 104367. [Google Scholar] [CrossRef]
- Song, W.; Fu, C.; Zheng, Y.; Zhang, Y.; Chen, J.; Wang, P. Batch image encryption using cross image permutation and diffusion. J. Inf. Secur. Appl. 2024, 80, 103686. [Google Scholar] [CrossRef]
- Tang, S.; Xu, X.; Jiang, Z.H.; Meng, D.; Sun, K. An image encryption scheme without additional key transmission based on an N-dimensional closed-loop coupled triangular wave model. Chaos Solitons Fractals 2024, 185, 115039. [Google Scholar] [CrossRef]
- Wang, M.; Teng, L.; Zhou, W.; Yan, X.; Xia, Z.; Zhou, S. A new 2D cross hyperchaotic Sine-modulation-Logistic map and its application in bit-level image encryption. Expert Syst. Appl. 2024, 261, 125328. [Google Scholar] [CrossRef]
- Zhou, S.; Tao, Z.; Erkan, U.; Toktas, A.; Iu, H.H.C.; Zhang, Y.; Zhang, H. Multidimensional chaotic signals generation using deep learning and its application in image encryption. Eng. Appl. Artif. Intell. 2025, 156, 111017. [Google Scholar] [CrossRef]











| Component | Direction | Original Image | Proposed |
|---|---|---|---|
| Horizontal | 0.9882 | 0.0010 | |
| R channel | Vertical | 0.9821 | 0.0036 |
| Diagonal | 0.9651 | −0.0201 | |
| Anti-diagonal | 0.9741 | 0.0071 | |
| Horizontal | 0.9820 | −0.0031 | |
| G channel | Vertical | 0.9668 | 0.0059 |
| Diagonal | 0.9556 | −0.0471 | |
| Anti-diagonal | 0.9683 | −0.0002 | |
| Horizontal | 0.9589 | −0.0505 | |
| B channel | Vertical | 0.9321 | 0.0175 |
| Diagonal | 0.9158 | −0.0121 | |
| Anti-diagonal | 0.9295 | −0.0443 |
| Filename | Proposed | Ref. [56] | Ref. [57] | Ref. [58] | Ref. [59] |
|---|---|---|---|---|---|
| Airplane | 99.6075 | 99.6283 | 99.6330 | 99.6092 | / |
| Couple | 99.6140 | 99.5845 | / | / | 99.6130 |
| House | 99.6017 | 99.6296 | 99.6399 | 99.6128 | 99.6110 |
| Mandrill | 99.6143 | 99.6296 | / | 99.6131 | 99.6110 |
| Peppers | 99.6178 | 99.6236 | 99.6174 | 99.6071 | / |
| San Diego | 99.6052 | 99.6291 | 99.6172 | / | / |
| Tree | 99.5926 | 99.6074 | / | / | / |
| Female | 99.6109 | / | 99.5880 | / | / |
| Oakland | 99.6088 | / | 99.6147 | / | / |
| Stockton | 99.6093 | / | 99.6066 | / | / |
| Filename | Proposed | Ref. [56] | Ref. [57] | Ref. [58] | Ref. [59] |
|---|---|---|---|---|---|
| Airplane | 7.9998 | 7.9983 | 7.9994 | 7.9992 | / |
| Couple | 7.9989 | 7.9987 | / | / | 7.9973 |
| House | 7.9989 | 7.9988 | 7.9978 | 7.9994 | 7.9968 |
| Mandrill | 7.9998 | 7.9986 | / | 7.9992 | 7.9992 |
| Peppers | 7.9998 | 7.9992 | 7.9994 | 7.9989 | 7.9971 |
| San Diego | 7.9998 | 7.9995 | 7.9998 | / | / |
| Tree | 7.9990 | 7.9994 | / | / | / |
| Female | 7.9990 | / | 7.9974 | / | 7.9971 |
| Oakland | 7.9999 | / | 7.9998 | / | / |
| Stockton | 7.9999 | / | 7.9998 | / | / |
| Filename | Description | Size | Channel | NPCR | UACI | BACI | MSE | PSNR | SSIM | HI | HC |
|---|---|---|---|---|---|---|---|---|---|---|---|
| 4.1.01 | Female (NTSC test image) | 256 | Red | 99.5789 | 32.0279 | 24.5693 | 36,350 | 2.5258 | 0.0094 | 6.8981 | 7.9992 |
| 4.1.01 | Female (NTSC test image) | 256 | Green | 99.6155 | 36.2976 | 27.4752 | |||||
| 4.1.01 | Female (NTSC test image) | 256 | Blue | 99.6384 | 37.4646 | 28.2366 | |||||
| 4.1.02 | Couple (NTSC test image) | 256 | Red | 99.6338 | 38.3150 | 28.5548 | 46,240 | 1.4806 | 0.0062 | 6.2945 | 7.9989 |
| 4.1.02 | Couple (NTSC test image) | 256 | Green | 99.6140 | 41.1581 | 30.5070 | |||||
| 4.1.02 | Couple (NTSC test image) | 256 | Blue | 99.6140 | 41.5659 | 30.7450 | |||||
| 4.1.03 | Female (from Bell Labs?) | 256 | Red | 99.6216 | 27.0281 | 19.0294 | 19,733 | 5.1789 | 0.0118 | 5.9709 | 7.9991 |
| 4.1.03 | Female (from Bell Labs?) | 256 | Green | 99.5850 | 26.6231 | 18.6229 | |||||
| 4.1.03 | Female (from Bell Labs?) | 256 | Blue | 99.5941 | 26.7814 | 18.8846 | |||||
| 4.1.04 | Female | 256 | Red | 99.6109 | 31.0961 | 23.4600 | 25,462 | 4.0718 | 0.0107 | 7.4270 | 7.9990 |
| 4.1.04 | Female | 256 | Green | 99.5911 | 30.6080 | 22.7991 | |||||
| 4.1.04 | Female | 256 | Blue | 99.6246 | 27.4894 | 19.8438 | |||||
| 4.1.05 | House | 256 | Red | 99.6323 | 27.3262 | 19.8229 | 25,063 | 4.1405 | 0.0098 | 7.0686 | 7.9989 |
| 4.1.05 | House | 256 | Green | 99.6338 | 29.9497 | 22.7503 | |||||
| 4.1.05 | House | 256 | Blue | 99.6017 | 31.3619 | 23.9620 | |||||
| 4.1.06 | Tree | 256 | Red | 99.6323 | 30.1875 | 22.9725 | 29,906 | 3.3732 | 0.0100 | 7.5371 | 7.9990 |
| 4.1.06 | Tree | 256 | Green | 99.6368 | 34.2251 | 26.7309 | |||||
| 4.1.06 | Tree | 256 | Blue | 99.5926 | 31.6424 | 24.5670 | |||||
| 4.1.07 | Jelly beans | 256 | Red | 99.6078 | 30.8726 | 24.4918 | 27,006 | 3.8162 | 0.0102 | 6.5835 | 7.9990 |
| 4.1.07 | Jelly beans | 256 | Green | 99.6246 | 32.5520 | 26.0160 | |||||
| 4.1.07 | Jelly beans | 256 | Blue | 99.5636 | 28.1269 | 21.1757 | |||||
| 4.1.08 | Jelly beans | 256 | Red | 99.6292 | 30.7943 | 24.3415 | 26,610 | 3.8803 | 0.0099 | 6.8527 | 7.9991 |
| 4.1.08 | Jelly beans | 256 | Green | 99.6490 | 31.8561 | 25.1864 | |||||
| 4.1.08 | Jelly beans | 256 | Blue | 99.6384 | 28.3174 | 21.0733 | |||||
| 4.2.01 | Splash | 512 | Red | 99.6136 | 34.2512 | 26.5957 | 33,716 | 2.8524 | 0.0100 | 7.2428 | 7.9998 |
| 4.2.01 | Splash | 512 | Green | 99.5983 | 35.6868 | 27.4607 | |||||
| 4.2.01 | Splash | 512 | Blue | 99.6109 | 31.9245 | 25.2354 | |||||
| 4.2.03 | Mandrill (a.k.a. Baboon) | 512 | Red | 99.6208 | 29.9609 | 22.3660 | 25,848 | 4.0065 | 0.0097 | 7.7624 | 7.9998 |
| 4.2.03 | Mandrill (a.k.a. Baboon) | 512 | Green | 99.6231 | 28.6218 | 21.6130 | |||||
| 4.2.03 | Mandrill (a.k.a. Baboon) | 512 | Blue | 99.6143 | 31.2127 | 23.9263 | |||||
| 4.2.05 | Airplane (F-16) | 512 | Red | 99.6143 | 31.9916 | 25.0842 | 31,045 | 3.2109 | 0.0099 | 6.6639 | 7.9998 |
| 4.2.05 | Airplane (F-16) | 512 | Green | 99.6075 | 33.0359 | 26.0583 | |||||
| 4.2.05 | Airplane (F-16) | 512 | Blue | 99.5869 | 32.7045 | 25.8280 | |||||
| 4.2.06 | Sailboat on lake | 512 | Red | 99.6140 | 27.9360 | 20.6481 | 30,347 | 3.3097 | 0.0105 | 7.7622 | 7.9998 |
| 4.2.06 | Sailboat on lake | 512 | Green | 99.5796 | 34.3896 | 26.7540 | |||||
| 4.2.06 | Sailboat on lake | 512 | Blue | 99.6254 | 34.3947 | 27.1026 | |||||
| 4.2.07 | Peppers | 512 | Red | 99.6223 | 28.9599 | 21.7661 | 30,327 | 3.3125 | 0.0104 | 7.6698 | 7.9998 |
| 4.2.07 | Peppers | 512 | Green | 99.6178 | 33.8983 | 25.9169 | |||||
| 4.2.07 | Peppers | 512 | Blue | 99.5857 | 33.7585 | 25.7967 | |||||
| house | House | 512 | Red | 99.6193 | 30.1928 | 23.1123 | 27,746 | 3.6989 | 0.0091 | 7.4858 | 7.9998 |
| house | House | 512 | Green | 99.6113 | 31.3346 | 24.0914 | |||||
| house | House | 512 | Blue | 99.6414 | 31.1798 | 23.9693 |
| Channel | (H/4, W/4) | (H × 3/4, W/4) | (H/4, W × 3/4) | (H×3/4, W × 3/4) | |
|---|---|---|---|---|---|
| 4.1.01 | Red | 99.5895 | 99.5941 | 99.6124 | 99.6338 |
| 4.1.01 | Green | 99.6353 | 99.6307 | 99.5956 | 99.5712 |
| 4.1.01 | Blue | 99.5972 | 99.6384 | 99.6124 | 99.5895 |
| 4.1.02 | Red | 99.5773 | 99.5926 | 99.6323 | 99.6246 |
| 4.1.02 | Green | 99.6307 | 99.6017 | 99.6185 | 99.6155 |
| 4.1.02 | Blue | 99.5804 | 99.5667 | 99.6414 | 99.6094 |
| 4.1.03 | Red | 99.6140 | 99.6414 | 99.6002 | 99.6246 |
| 4.1.03 | Green | 99.5667 | 99.5834 | 99.6094 | 99.6872 |
| 4.1.03 | Blue | 99.5682 | 99.5850 | 99.6155 | 99.5697 |
| 2.1.01 | Red | 99.6159 | 99.6067 | 99.6071 | 99.6017 |
| 2.1.01 | Green | 99.6307 | 99.6429 | 99.6101 | 99.5945 |
| 2.1.01 | Blue | 99.6216 | 99.6254 | 99.6082 | 99.6178 |
| 2.1.02 | Red | 99.6014 | 99.6193 | 99.6357 | 99.5781 |
| 2.1.02 | Green | 99.6166 | 99.6025 | 99.6170 | 99.6201 |
| 2.2.02 | Red | 99.6089 | 99.6164 | 99.6058 | 99.6119 |
| 2.2.02 | Green | 99.6180 | 99.6065 | 99.6064 | 99.6090 |
| 2.2.02 | Blue | 99.6103 | 99.6139 | 99.6077 | 99.6006 |
| 2.2.03 | Red | 99.6074 | 99.6130 | 99.6183 | 99.5976 |
| 2.2.03 | Green | 99.6119 | 99.6126 | 99.6103 | 99.6076 |
| 2.2.03 | Blue | 99.6099 | 99.6031 | 99.6061 | 99.6064 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xie, Z.; Xie, W.; Cheng, X.; Yuan, Z.; Cheng, W.; Lin, Y. Image Privacy Protection Communication Scheme by Fibonacci Interleaved Diffusion and Non-Degenerate Discrete Chaos. Entropy 2025, 27, 790. https://doi.org/10.3390/e27080790
Xie Z, Xie W, Cheng X, Yuan Z, Cheng W, Lin Y. Image Privacy Protection Communication Scheme by Fibonacci Interleaved Diffusion and Non-Degenerate Discrete Chaos. Entropy. 2025; 27(8):790. https://doi.org/10.3390/e27080790
Chicago/Turabian StyleXie, Zhiyu, Weihong Xie, Xiyuan Cheng, Zhengqin Yuan, Wenbin Cheng, and Yiting Lin. 2025. "Image Privacy Protection Communication Scheme by Fibonacci Interleaved Diffusion and Non-Degenerate Discrete Chaos" Entropy 27, no. 8: 790. https://doi.org/10.3390/e27080790
APA StyleXie, Z., Xie, W., Cheng, X., Yuan, Z., Cheng, W., & Lin, Y. (2025). Image Privacy Protection Communication Scheme by Fibonacci Interleaved Diffusion and Non-Degenerate Discrete Chaos. Entropy, 27(8), 790. https://doi.org/10.3390/e27080790






