1. Introduction
UAV swarm has the advantages of high mobility, strong robustness, and cost-effectiveness, and the deep cooperation of multiple UAVs can realize the nonlinear growth of individual performance, which has been widely used in many fields. At the same time, advances in radar systems have significantly improved their anti-jamming capabilities, especially with the popularity of networked radar systems; a single electronic jamming platform becomes less and less capable of jamming the target radar network. Therefore, more and more scholars have begun to study the use of UAV groups to interfere with network radar, and how to use UAV groups to make network radar generate realistic phantom tracks has become a current research hot spot.
In the field of jamming technology, the concept of range deception ghost track generation proposed in 2004 initiated systematic research [
1]. Scholars established the mathematical mapping relationship between flight paths and false tracks by constructing the ECAV collaborative trajectory model, laying the theoretical foundation for multi-platform cooperative deception [
2,
3,
4,
5]. As research focus shifted toward optimal control problems [
6,
7], Yunjun Xu proposed a method for designing real-time feasible and optimal trajectories inspired by motion camouflage, reducing problem dimensionality and improving computational efficiency [
8]. This work provided critical theoretical support for subsequent technological advancements. Zhiping Ouyang developed a multi-UAV cooperative track deception optimization model, analyzing UAV positions and motion states to derive motion parameters through simulation and determining the minimum number of UAVs and optimal spacing required for effective radar network jamming [
9]; N. Dhananjay addressed the generation of coherent virtual trajectories using ECAVs to deceive radar networks, providing sufficient conditions for feasible ECAV trajectories under proportional navigation missile-like scenarios. Line-of-sight guidance laws were employed to control ECAVs, and performance metrics were proposed to evaluate trajectory coherence [
10]. Zhe Fan investigated deception rules for UAV swarms attacking radar networks, establishing a geometric model to minimize the number of UAVs required for false trajectory generation and offering insights into enhancing swarm electronic countermeasures [
11]. In terms of application scenario expansion, Ratnoo constructed an adaptable deception formation controller for arbitrary initial positions based on the LOSG principle [
12]; Zhang, Y. innovatively proposed a closed-form solution method for dual moving-source jamming against monopulse radars [
13]; and Muhammad Abubakar Ali targeted the Linear Frequency Modulation (LFM) pulse Doppler radar. By intercepting the signal parameters and adding positive and negative delays, it was verified through simulation that highly similar false targets could be formed before and after the real echoes, confusing the radar discrimination [
14]; and Bin Rao proposed a cooperative deception method based on noncoherent dual-source jamming for distributed radar fusion systems. By statistically controlling the amplitude ratio and time delay of jamming signals, noncoherent angle scintillation effects are induced between decoy signals and target echoes. This causes radar angle tracking to deviate from the true target, undermining the ‘common origin’ feature of targets and degrading trajectory fusion discriminability. Simulation results validate the feasibility of this method [
15]. Yubing Wang analyzed the impact of radar positioning error and UAV jitter error on track spoofing in scenarios with missing prior information [
16]. Pan Yu reviewed the development process of interference signal design, proposed a general formula for unified interference waveform design, pointed out the existing problems of the current interference from the signal level, and proposed improvement directions such as compound interference and the introduction of machine learning algorithms [
17].
Radar anti-jamming technologies have undergone iterative upgrades, with multidimensional innovations enhancing system stability. Zhao et al. [
18] exploited spatial scattering differences and multi-channel correlation tests to detect false targets under arbitrary deception. Li [
19] employed Hermitian distance for true/false discrimination in distributed radars. Qiang Li [
20] effectively identifies false targets in the scenario of combined distance-speed deception by utilizing the difference in the statistical distribution of velocities between real targets and false targets. Zhe Ji [
21] proposes a radar networking anti-multi-range false target interference technology based on azimuth measurement correlation and nearest neighbor correlation. Hengli Yu [
22] utilizes the spatial coherence difference between the target echo and the interference signal in multi-station radar and improves the target detection performance by combining noise subspace projection with generalized likelihood ratio detection (GLRT). Yang [
23] addressed false data injection attacks with a confidence covariance intersection algorithm that adaptively down-weights suspect data. Zhou [
24] fused bispectral features via Bayesian decision theory and kernel density estimation to distinguish true echoes, deception jamming, and noise. Zhang [
25] proposed a non-coherent integration detection algorithm for joint jamming suppression and target detection. Han [
26] introduced an active/passive networked radar method leveraging radar position error during initialization and sequential track correlation for false target elimination. Yang [
27] fused nearest-neighbor algorithms with passive radar to improve tracking accuracy, and Zhang [
28] used multi-perspective fully polarimetric observations in a multiple hypothesis testing model. Cheng Feng [
29] proposed an optimization method for radar anti-jamming strategies based on key time nodes. The behavior of the interfering party was modeled through the Markov decision process to enhance the concealment of the strategy.
In recent years, the intelligent evolution of electronic warfare has accelerated. Li introduced a multi-agent deep-reinforcement-learning motion-allocation algorithm that adaptively re-positions UAV swarms, markedly enhancing cooperative jamming [
30]; Yang refined MADDPG with clipped double Q-networks and delayed policy updates, curbing over-estimation and boosting pursuit efficiency [
31]; Guo broke the SAR deception–template bottleneck via OTSCycGAN [
32]; Haowei Zhang et al. addressed the resource allocation problem in UAV-aided joint radar and communication (JRC) networks. They proposed the JCAPASA and JPBSA strategies, taking the Cramér-Rao Lower Bound (CRLB) as the optimization metric to jointly optimize resource allocation, including power and subchannels [
33,
34]; Sun enhanced distributed-radar tracking with the ADJ-JRAPS joint strategy [
35]; Zhang realized simultaneous gains in transmission efficiency and detection through fusion-based techniques [
36]; Yongkang Wang utilized the integration of multiple networks to extract the spatiotemporal characteristics of trajectories and effectively identify active deception interference [
37]; XiYu combined with SVM proposed a multi-domain feature fusion method based on time-domain envelope fluctuations and frequency-domain similarity for interference identification [
38]; and Tan’s PASS-Net excelled in few-shot modulation classification [
39]. Collectively, these studies herald a shift toward intelligent, collaborative, cross-domain jamming. The main contributions of this paper are:
Most cooperative-deception studies presuppose error-free conditions. We separately model radar prior-position, UAV-position. and time-delay errors, then integrate them into a spatially coupled comprehensive model. Using the principle of homologous testing, we derive conditions under which false targets satisfy spatial-consistency checks throughout track formation.
To offset real-world errors and raise deception success, we propose two compensation schemes: (1) Zonal Track Compensation, which algebraically quantifies offsets under coupled errors; and (2) UAV Formation Compensation, which geometrically suppresses horizontal UAV position errors.
Numerical simulations show that while individual errors displace false targets, the proposed schemes shrink the required range gate and, when combined, deliver the best performance—confirming their practicality and effectiveness.
3. System Model
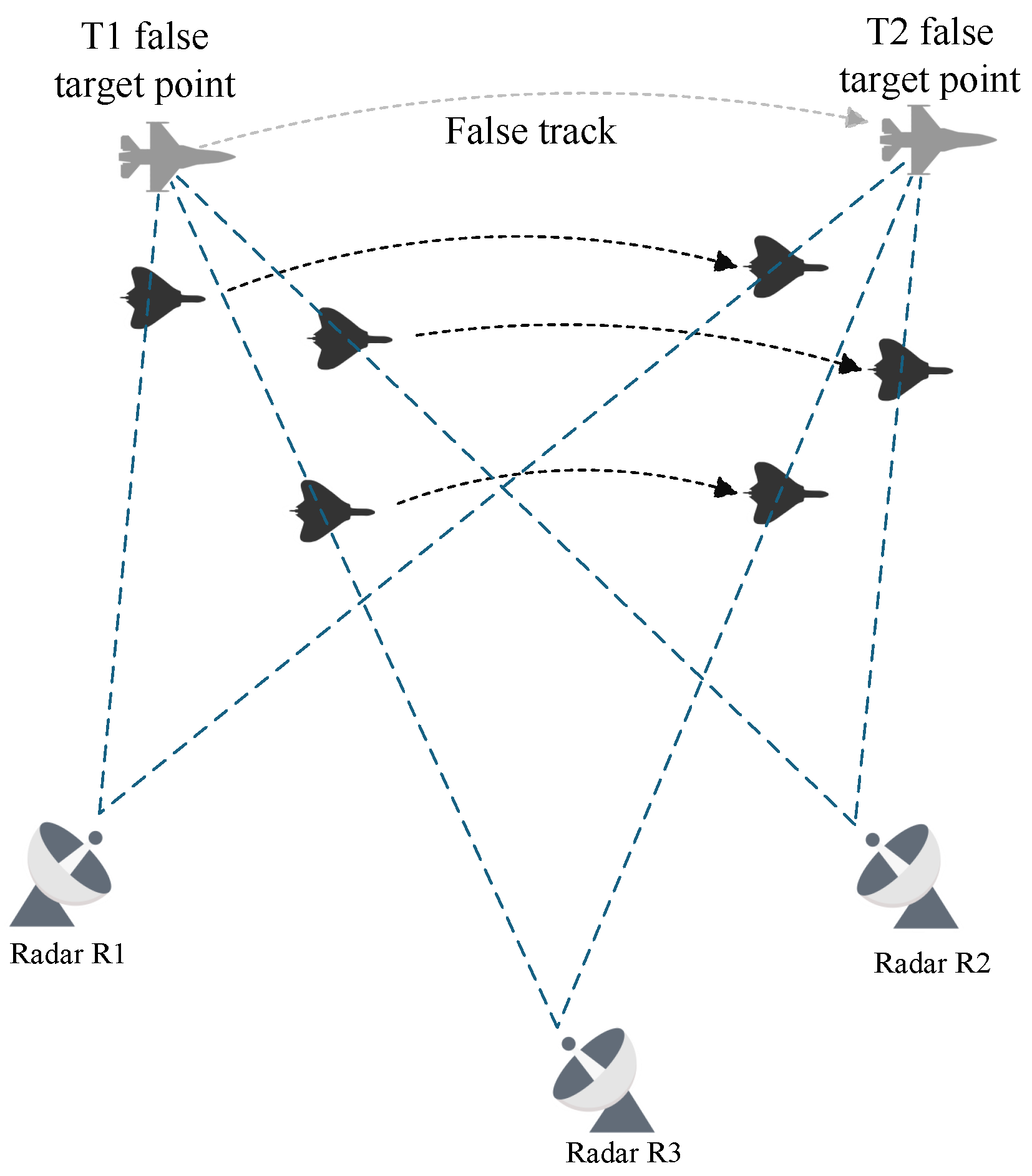
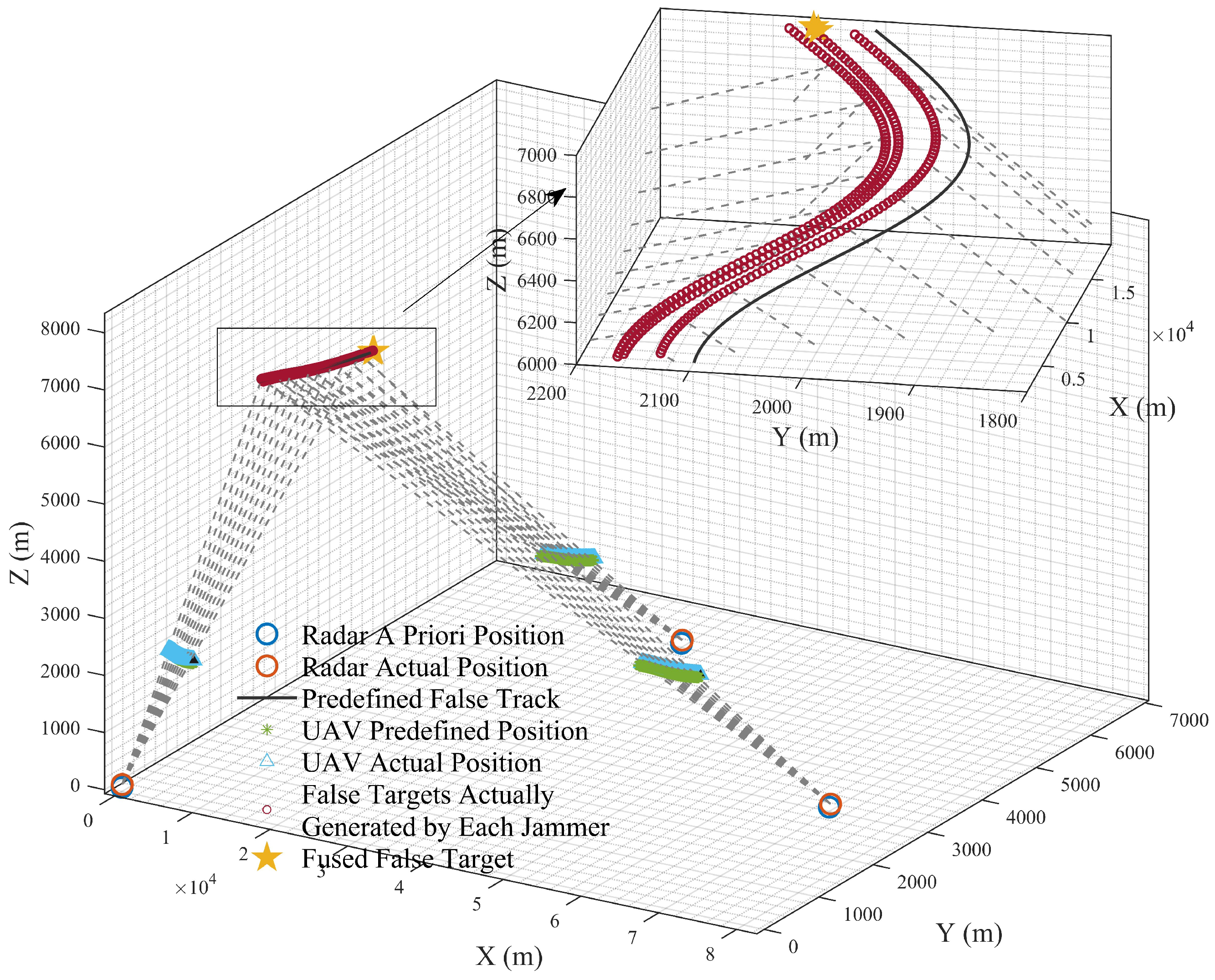
Since the scenario in this paper is premised on main lobe deception jamming, radars, UAVs, and false targets all lie along the same line. For false targets located on the line of sight between radars and UAVs, their spatial positions are jointly determined by UAV positions, radar positions, and time delay parameters. Consequently, false targets generated by different UAVs jamming different radars within the networked radar system must coincide in position; otherwise, they will be identified as false targets and eliminated by the system.
Current solutions for track deception primarily adopt a “reverse approach,” where UAV positions at each time are derived backward based on pre-defined false tracks and target radar positions [
42]. Under ideal conditions, parameters of false targets detected by individual radars are coupled across domains. However, in real-world environments, various uncertainties cause false targets to be eliminated during fusion processing. Therefore, it is essential to analyze and account for these errors and their impacts.
3.1. Error Analysis of Radar A Priori Position
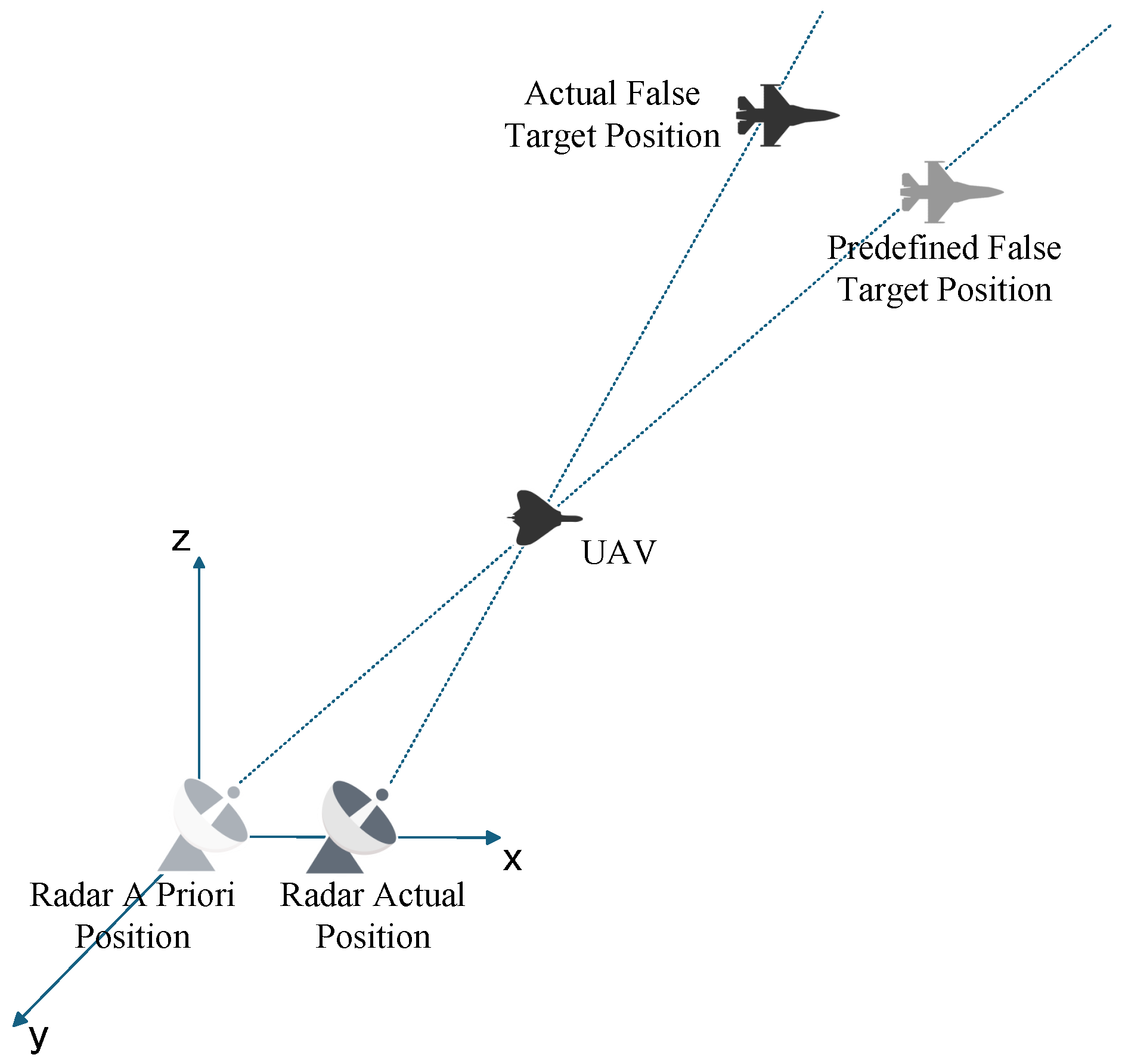
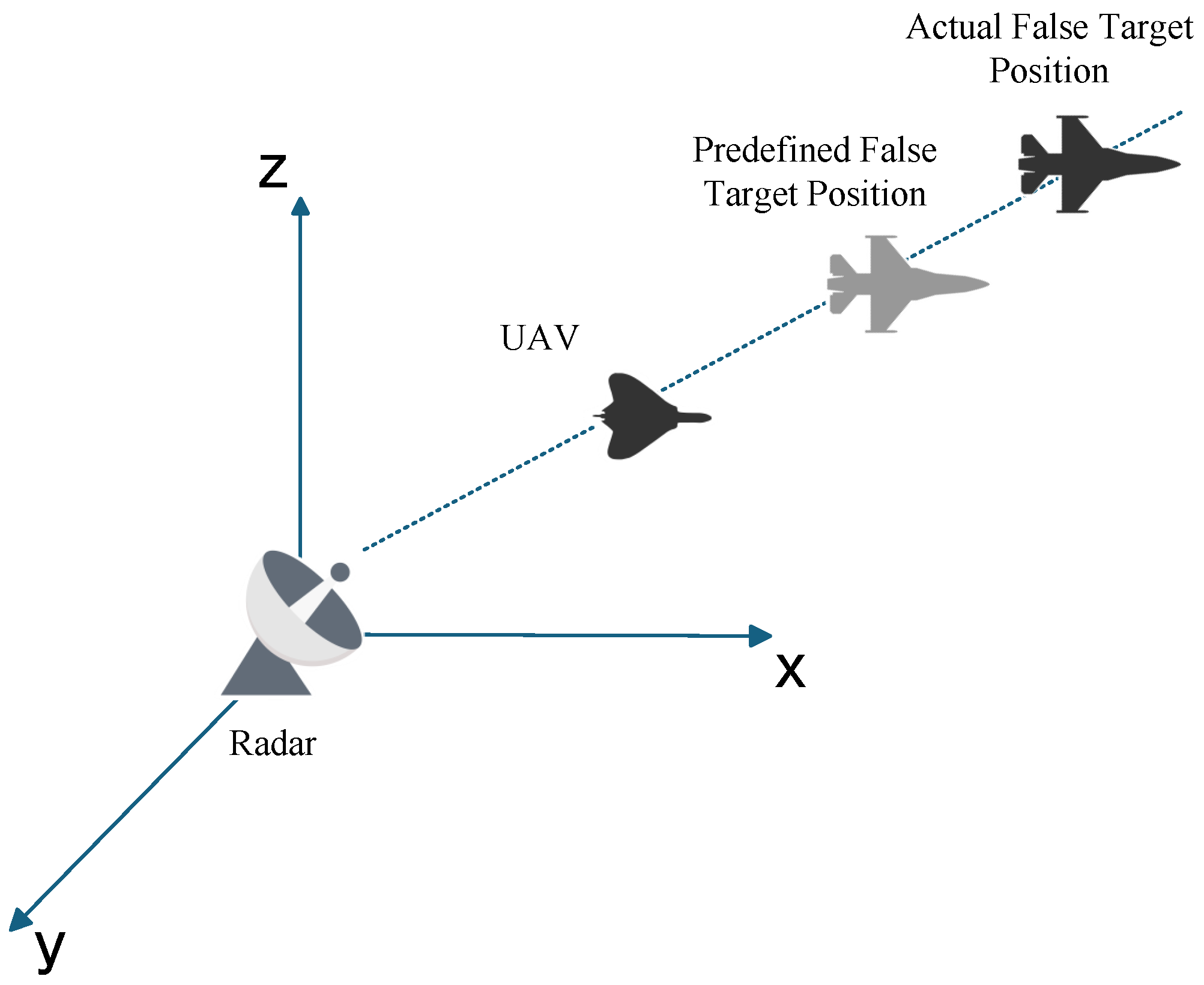
The radar prior position error is mainly caused by the positioning system. In the actual positioning process, complex terrains such as mountainous areas will affect the propagation of radar signals. The signal will be occluded, reflected, or refracted by the mountain, resulting in the distortion of the positioning system signal. However, in a complex electromagnetic environment, interference signals may mislead the positioning system to make misjudgments and eventually lead to positioning deviation. In addition, the technical limitations of the positioning system itself may also make the obtained radar prior position deviate from the actual position. The implementation of main lobe track deception jamming relies on the line of sight (LOS) criterion. When false tracks and UAV positions are predetermined without offsets, discrepancies between detected and actual radar positions will cause the predefined false targets to shift, leading to the splitting of false target points detected by individual radars within the networked radar system.
Figure 4 illustrates that errors between Radar A Priori Position and Radar Actual Position result in False Target offset.
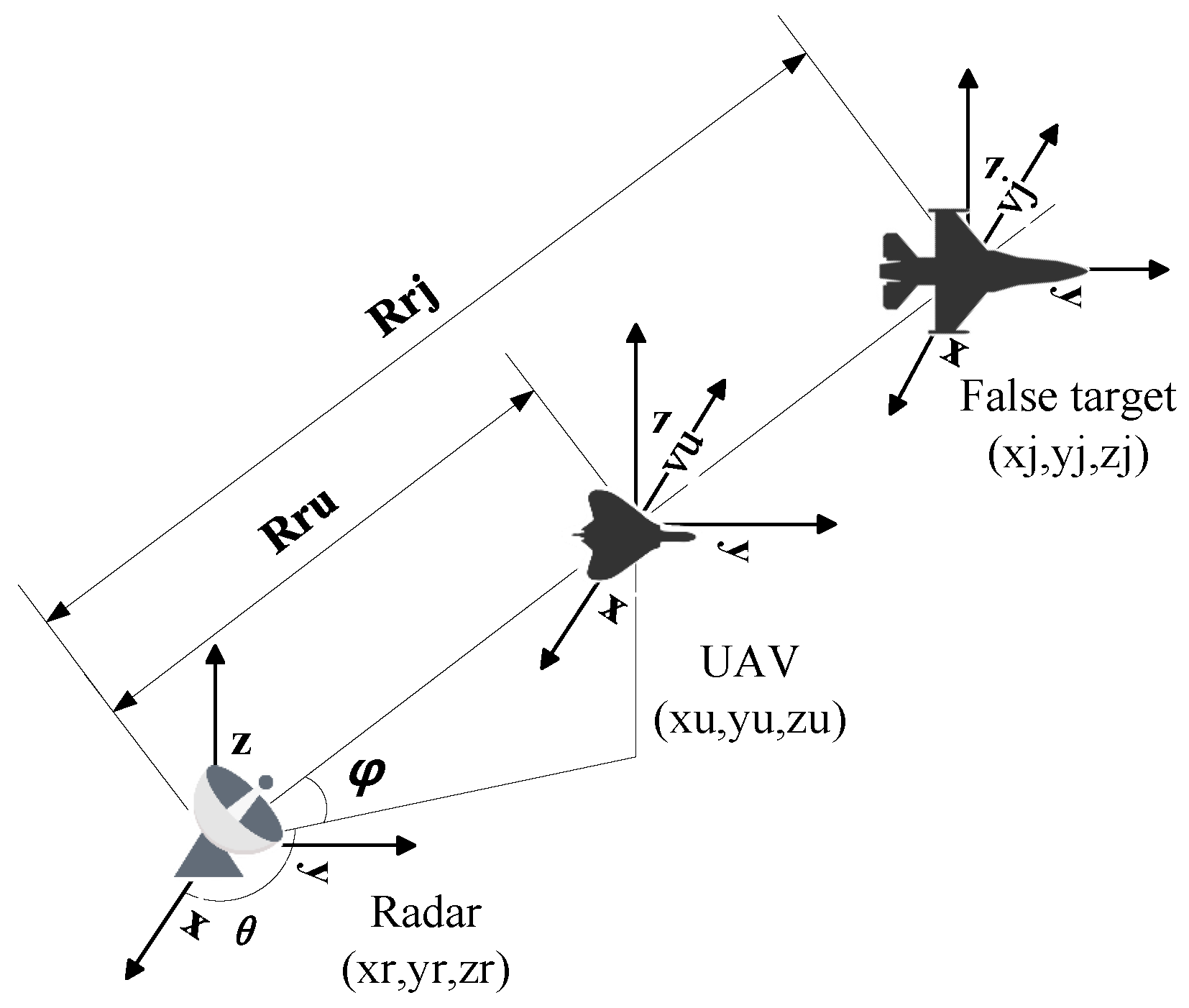
Assume that the radar a priori position error magnitude is
, the resulting false target offset is
, the distance from the radar a priori position to the UAV is
, and the distance from the UAV to the predefined false target is
, where the ratio of
to
is
p. Through geometric approximation, the relationship between the offset and the error can be approximated as follows.
From
Figure 3 and the triangle inequality theorem, the following system of inequalities can be derived.
Therefore, to satisfy measurement association, it follows from Equations (
8) and (
11) that the following conditions must be met.
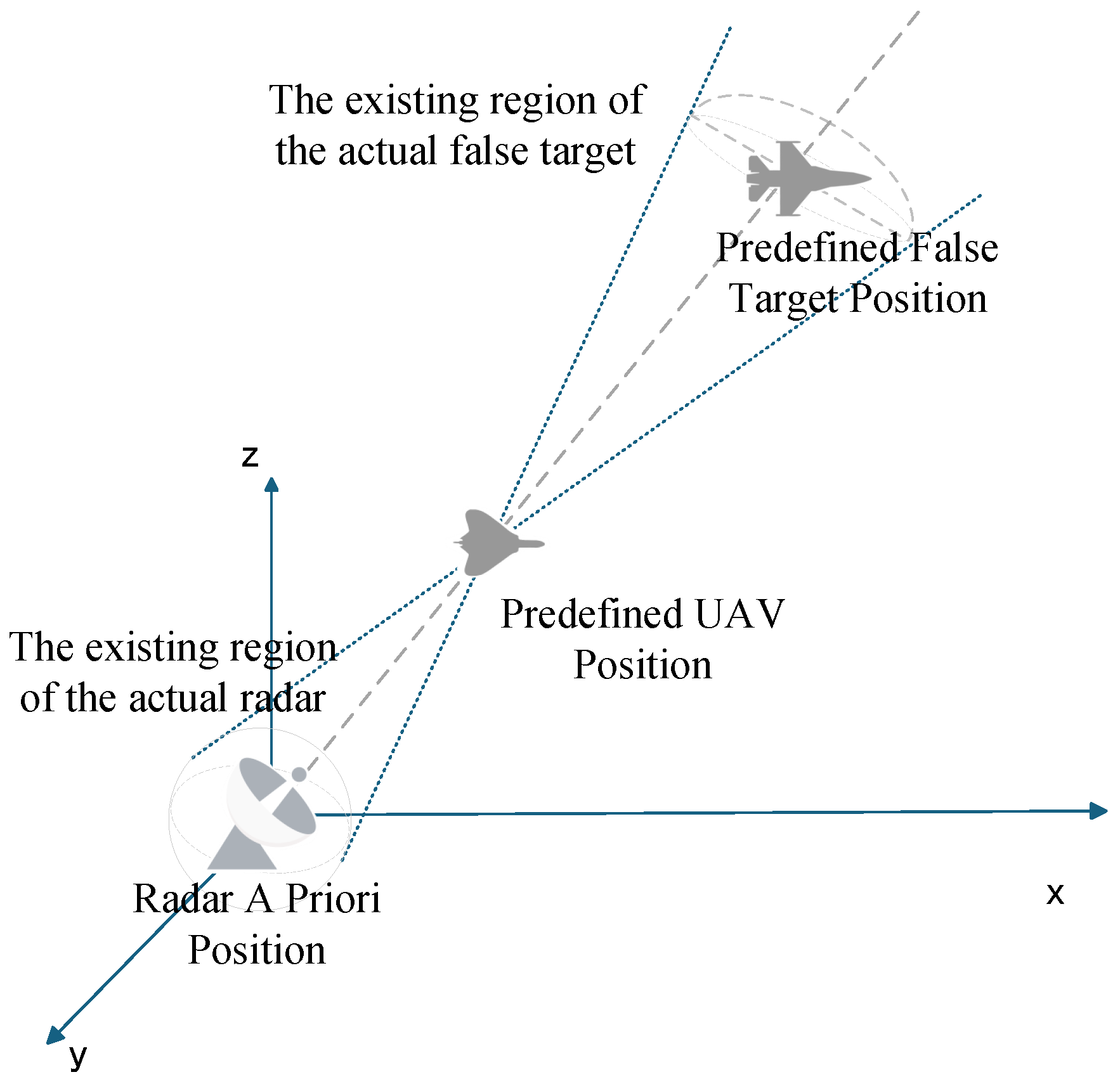
Assume that the magnitude of radar a priori position error is known (if only the error range is determined, the maximum value is selected). However, since the direction of the error vector is unknown, to derive conditions that ensure measurement association, it is necessary to calculate the false target distribution to determine the maximum false target deviation.
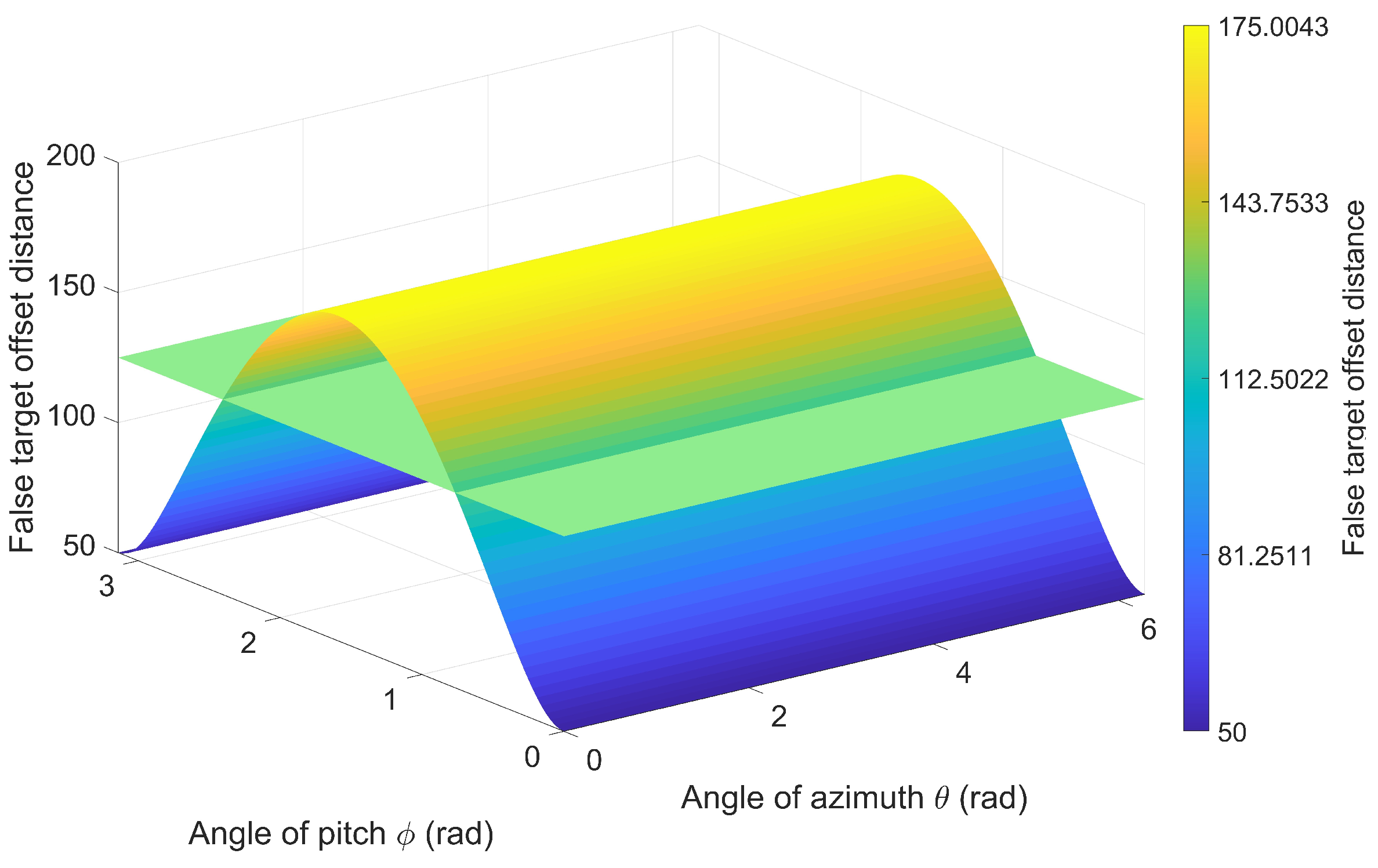
Figure 5 illustrates the false target distribution influenced solely by radar prior position error. Assume that the UAV position is
, the actual false target position is
, and the deception distance is d. The distribution of actual false targets can be derived as follows:
Based on the calculation of entropy in Equation (
9), we need to obtain the probability that the deviation distance is less than a certain threshold. Therefore, through derivation, the distribution function of the threshold
under this condition can be obtained as follows:
Furthermore, we can derive the maximum False Target Deviation when only radar a priori position errors exist, as follows.
In Equation (
15), at time
k, the maximum distance of the false target offset caused by Radar
i a priori position error is
, where the deception distance is
, the distance from the radar a priori position to the predefined UAV position is
, and the radar a priori position error is
.
3.2. Error Analysis of UAV Position
The position error of a UAV is mainly caused by its own characteristics and external environmental factors. Due to the small size and light weight of the UAV, it is extremely vulnerable to airflow disturbance when flying at high altitude. In addition, the positioning system on board has real-time calculation error, and the signal is also susceptible to external interference, which will cause positioning deviation. From the perspective of the external environment, the communication delay has a particularly significant impact on the position control of UAV. There is a time lag between the command issued by the ground control station and the command received and executed by the UAV. This lag will lead to the deviation between the actual position of the UAV and the expected position in the high-speed flight state and then cause the position deviation of the false target.
Figure 6 illustrates that position errors between the actual and predefined UAV positions directly result in false target misalignment.
Assume that the radar a priori position error magnitude is
, and the resulting false target offset is
. Through geometric approximation, the relationship between the offset and the error can be approximated as follows.
Following the same methodology as the radar a priori position error analysis, we first derive the distribution of actual false target positions, then determine the maximum false target deviation, and finally derive the measurement association conditions.
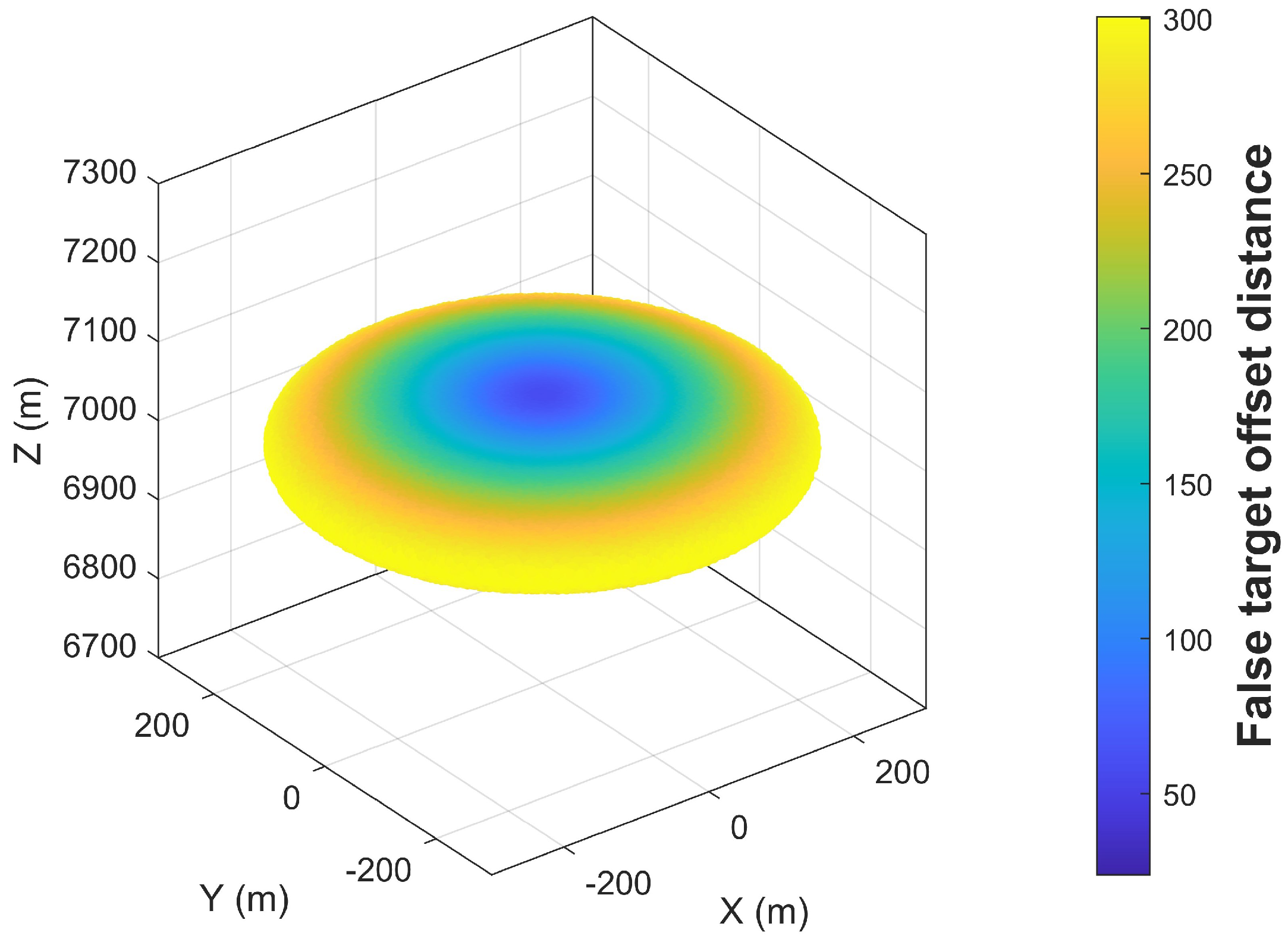
Figure 7 illustrates the false target distribution influenced solely by UAV position error.
Assume that the coordinates of the predefined UAV position are
, the spherical coordinates of the actual UAV position are
, the angle between the predefined UAV position and the actual UAV position in the
z-axis direction is
, the spherical coordinates of the actual false target position are
, and the deception distance is
d. Define:
The distribution of actual false targets can be derived as follows:
Similarly, we can derive the distribution function under this condition as follows:
We can derive the maximum False Target offset when only UAV position errors exist, as follows.
In Equation (
19), at time
k, the maximum distance of the false target offset caused by the position error of UAV
j to radar
i implementing jamming is
, where the deception distance is
, the distance from the radar a priori position to the predefined UAV position is
, and the position error of UAV
j at time
k is
.
3.3. Error Analysis of Time Delay
The time delay parameter error in radar systems is mainly caused by the combined effect of the inherent characteristics of the system and external environmental factors. The stability of clock sources such as crystal oscillators in the signal generation circuit is insufficient, which will lead to the deviation of the time reference of the interference signal. In addition, the limitation of conversion accuracy and speed in the process of digital-to-analog conversion (DAC) will also cause systematic time delay errors. In terms of the external environment, increased operating temperature or changes in the physical state of the hardware will change the circuit characteristics and then introduce time delay offsets, which may lengthen or shorten the distance of the false target. As shown in
Figure 8, time delay errors can also cause false target offset.
Based on radar detection principles, it can be derived that the following relationship exists between time delay error and false target offset:
In Equation (
20), at time
k, the maximum distance of false target offset caused by the delay error of UAV
j jamming radar
i is
, the maximum delay of UAV
j is
.
Therefore, under the condition that only time-delay errors exist, the measurement association conditions for two radars are as follows:
3.4. Error Analysis of Spatial Coupling Synthesis
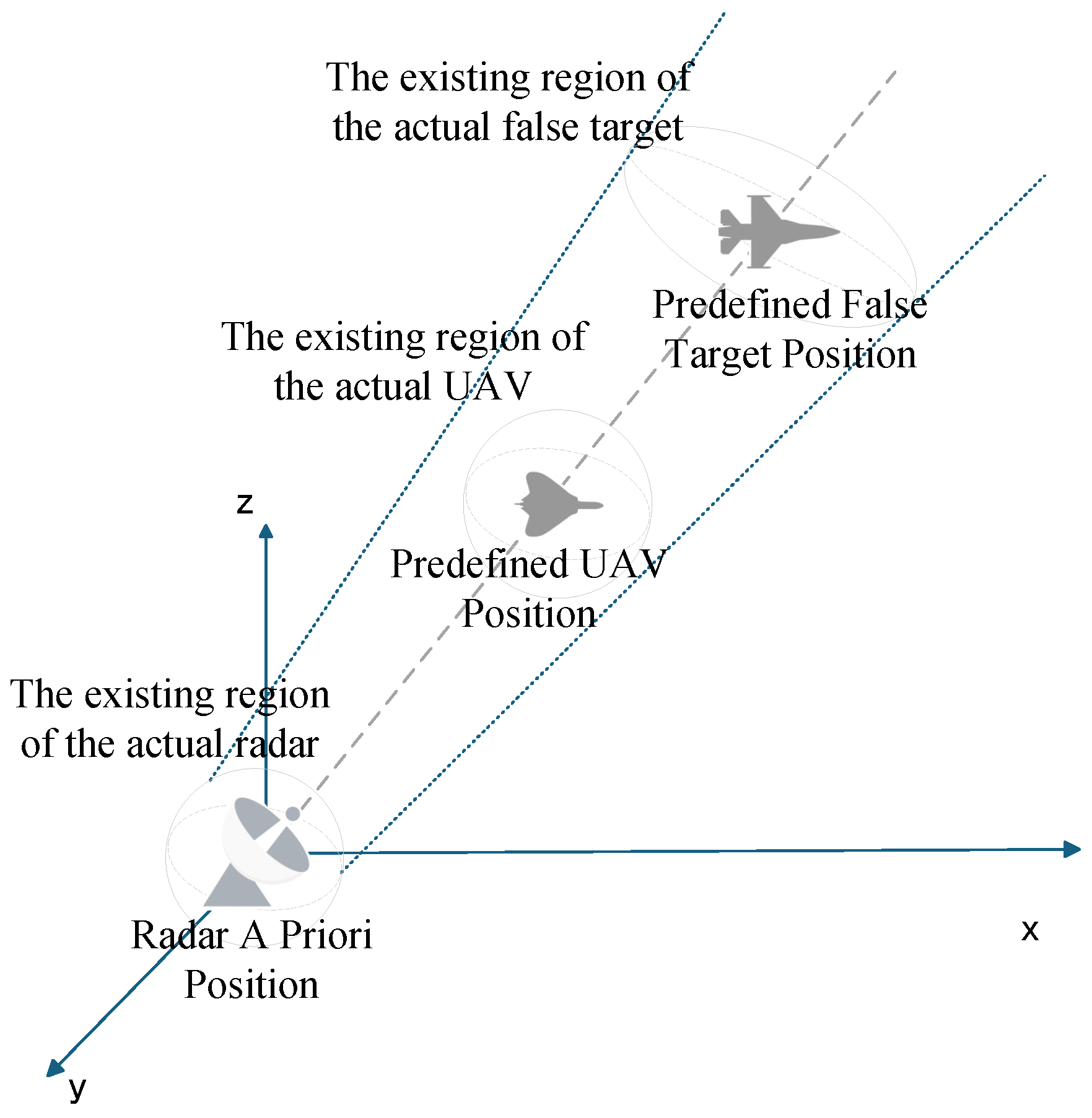
During the implementation of radar jamming, false targets are subject to the combined effects of multiple error sources. As previously discussed, radar a priori position errors, UAV position errors, and time delay parameter errors each contribute to spatial misalignment of false targets. However, in real-world scenarios (as shown in
Figure 9), these errors often act synergistically, necessitating an investigation into whether their impacts are merely additive or involve complex interactions and accumulations that ultimately amplify false target offset.
Assume that the coordinates of the actual radar position are
, and the coordinates of the predefined UAV position are
, the coordinates of the actual UAV position are
, the coordinates of the actual false target position are
, and the deception distance is d.
Assuming the radar priori position error vector is
= (
) and the UAV position error vector is
= (
),
, the probability density functions (PDFs) of the parameters can be obtained as follows:
We can derive the distribution function under the condition of comprehensive error as follows:
Given the complexity of the complete probability density function, an appropriate simplification allows us to derive the maximum false target offset under the influence of spatial coupling comprehensive errors as follows.
In Equation (
24), at time
k, the maximum distance of false target offset caused by the spatial coupling comprehensive errors of UAV
j jamming radar
i is
, the deception distance is
, the distance from the radar a priori position to the predefined UAV position is
, the radar a priori position error is
, the position error of UAV
j is
, and the maximum delay of UAV
j is
.
The measurement association conditions for two radars under spatial coupling comprehensive errors can be analogously derived from Equation (
11), the specific measurement association conditions are as follows.
Focusing on the scenario with
N radars, we first analyze the conditions for successfully deceiving Radar
. At time
k, the measurement association requirements are as follows.
Summing all inequalities in Equation (
26) yields the following inequality:
Simplifying yields the following result:
Furthermore, for measurement association among
N radars, the following conditions must be satisfied:
Alternatively, suppose that at time
k, the maximum false target splitting distances are reordered from smallest to largest as
.
For measurement association among
N radars, the following conditions must be satisfied:
In summary, the sufficient but not necessary conditions and necessary but not sufficient conditions for measurement association among
N radars are as follows:
However, in most cases, the specific magnitude of errors cannot be accurately obtained, and they often follow certain distributions. This paper conducts further research based on the normal distribution. Assuming that the radar priori position error
, the UAV position error
, and the time delay error
follow normal distributions, their probability distributions can be expressed as follows:
Through analysis, the probability density functions (PDFs) of the parameters can be obtained as follows:
The distribution function of the false target’s deviation distance can then be derived as follows:
Combining with Equation (
9), the information entropy of false targets can be obtained as follows:
Therefore, with a 95% significance detection threshold, the jamming effectiveness must satisfy the following condition:
4. Solution Techniques
Through geometric analysis and algebraic manipulation, the previous section derived sufficient but not necessary conditions for measurement association among N radars under spatial coupling errors. When these conditions are not met in practical scenarios, it is imperative to develop practical and effective error compensation schemes to ensure successful jamming implementation. For track deception, the primary research focuses on the target radar, UAV, and jamming payload. Given that the target radar is a noncooperative entity, this paper proposes two compensation schemes targeting UAVs and jamming payloads.
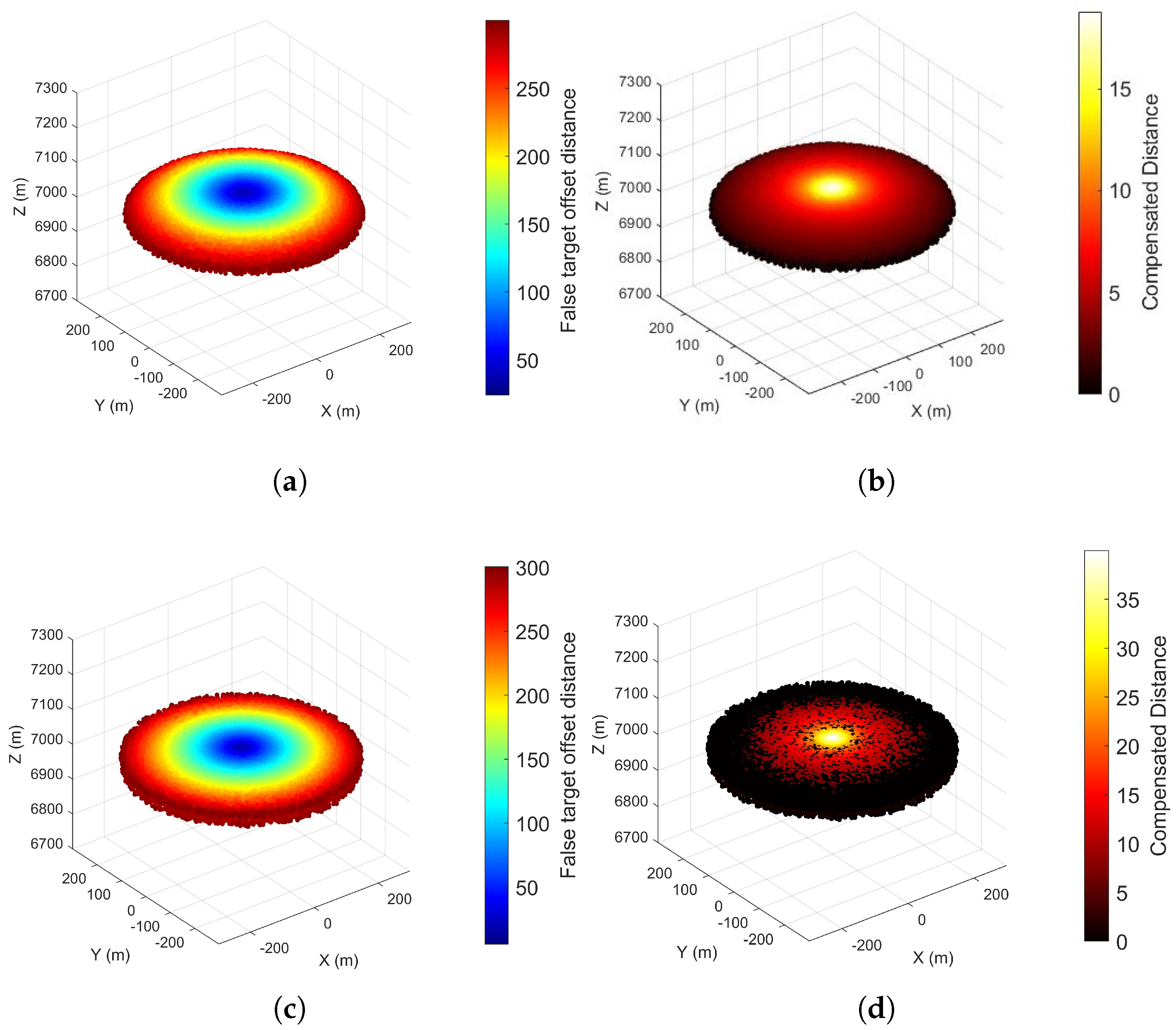
4.1. Zonal Track Compensation Method
The zonal track compensation method, as the name implies, this method ultimately forms a target false track by creating a zonal track. The underlying principle involves generating multiple additional false targets around the originally induced false target, thereby increasing the probability of measurement association at each time step and ensuring the production of point traces suitable for track formation. As shown in
Figure 10,
M and
A represent the false target points generated by Radar
and Radar
, respectively.
Taking radar
as an example, where
is a constant greater than zero, the measurement association conditions fail to hold under the following circumstances:
At this time, two additional false targets
B and
C are generated at a distance
from the original false target
M, where
. The value of
is defined as follows:
In Equation (
38),
. Consequently, the following scenarios can be derived:
From a geometric perspective, when
is an obtuse triangle with
as the median to side
, if
is obtuse, then
. This result can be derived as follows:
Comparison with Equation (
11) reveals that compensation reduces the Euclidean distance between false target splitting points, thereby reducing the required size of the association gate and increasing the measurement association probability.
Generalizing to the case of
N radars, from an algebraic perspective, the zonal track compensation Method can be interpreted as systematically modifying time delay errors. By taking the derivative of
in Equation (
24), the increasing and decreasing intervals are derived as Equation (
41) and Equation (
42), respectively:
From Equations (
41) and (
42), it can be derived that
attains a minimum value, which is given by:
When a minimum is achieved, errors in arbitrary directions can be mitigated; however, the compensation effectiveness varies with error orientation. Therefore, given prior information about the deception distance , the distance from the radar’s prior position to the pre-positioned UAV , the radar’s prior position error , the time delay error , and the UAV position error , an appropriate value can be determined to minimize , thereby reducing the impact of comprehensive errors. Additionally, empirical formulas derived from engineering practice can be developed for convenient computation.
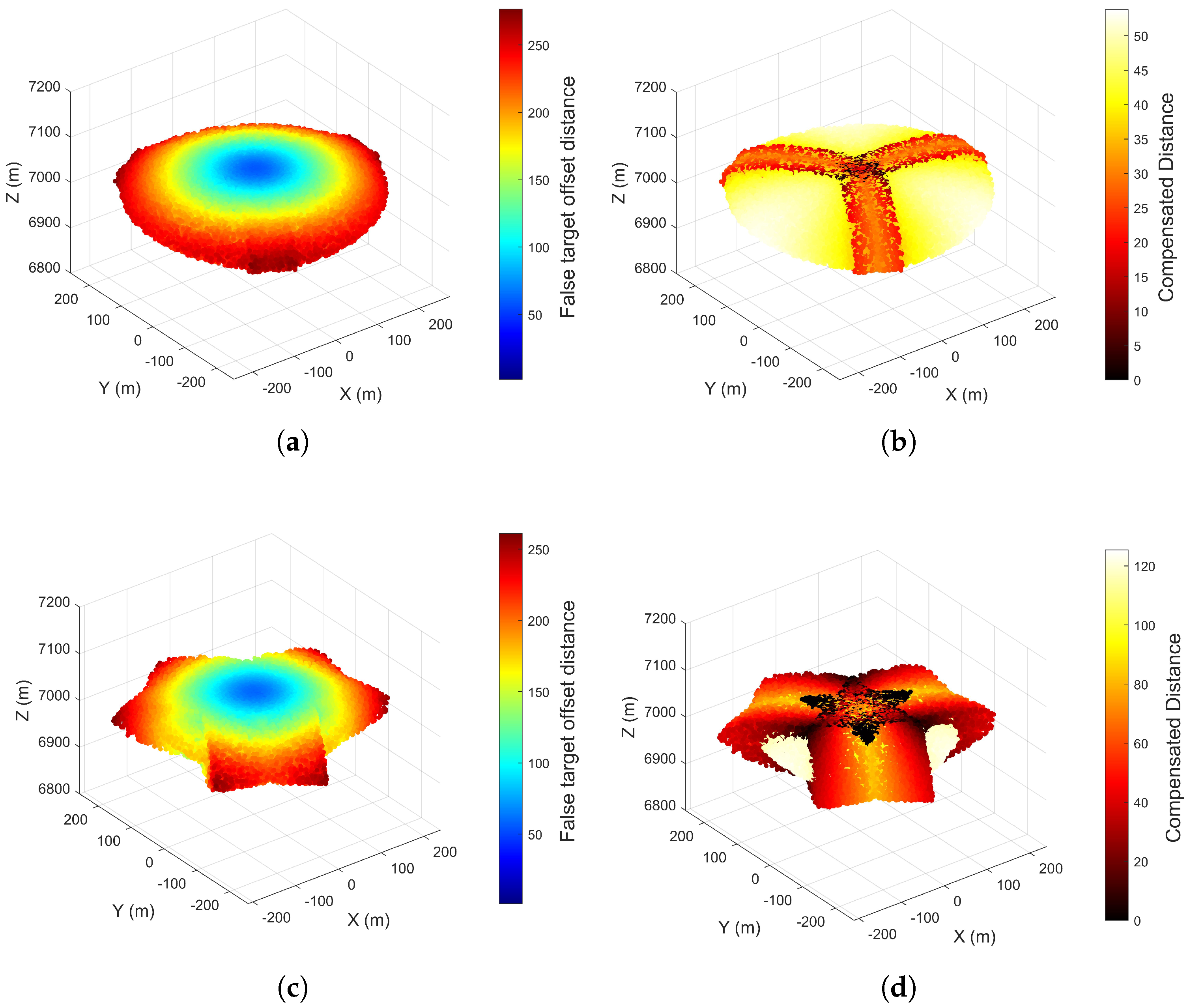
4.2. Formation Jamming Compensation Method
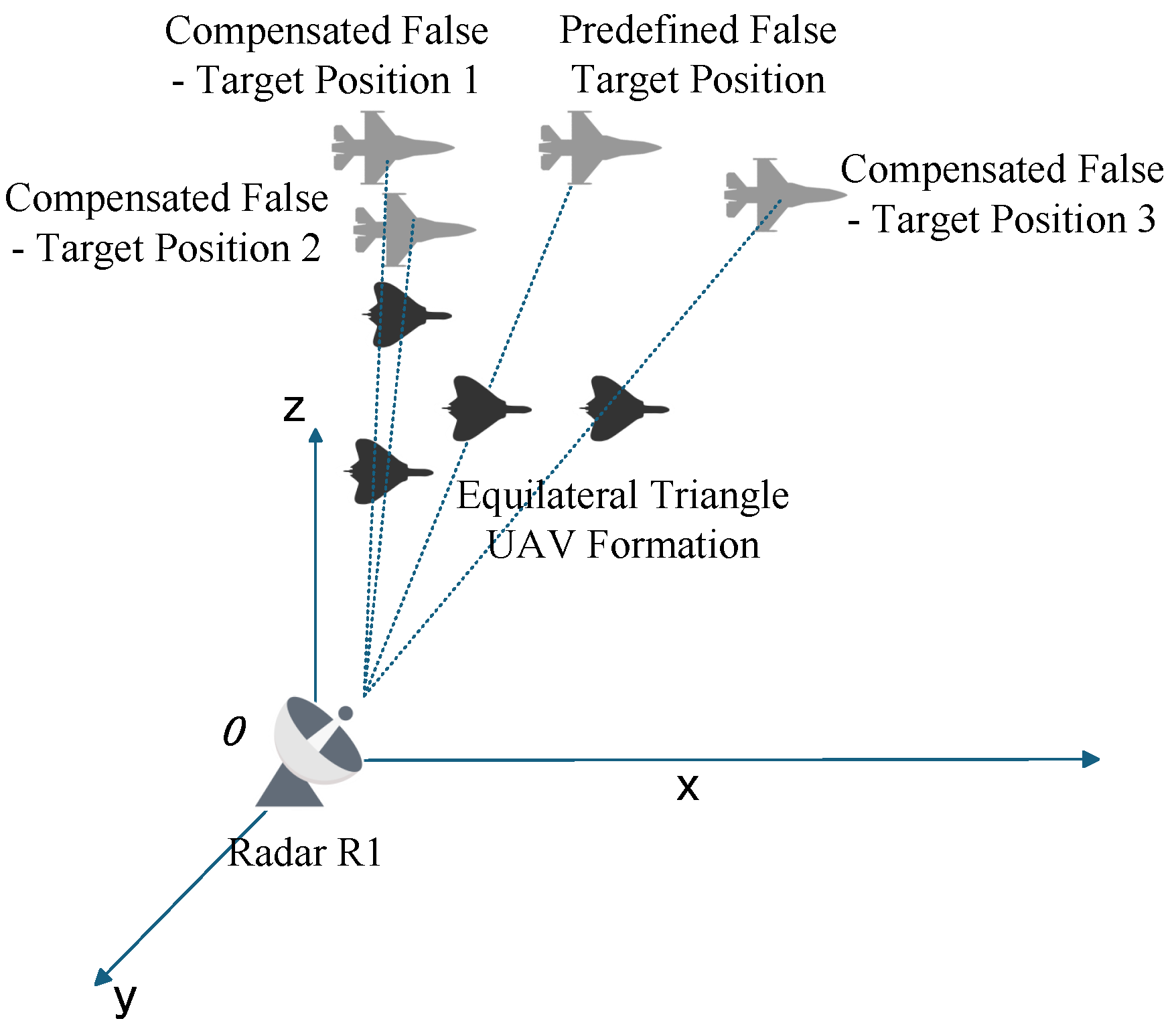
The formation jamming compensation method evolves from single—UAV jamming against a single radar at an initial time step to UAV formation jamming against the same radar. As shown in
Figure 11, a four—UAV formation is typically employed in an equilateral triangle configuration, where the geometric center coincides with the original single—UAV jamming position. The distance from each of the three vertex UAVs to the center is
.
When the main lobe of the target radar illuminates the UAV at the geometric center, multiple UAVs simultaneously generate false targets along the line connecting each radar to its corresponding UAV. To rigorously analyze this from an algebraic perspective, we take the derivative of
in Equation (
24) and derive the increasing interval as follows.
Since the right-hand side of the inequality is always negative,
is a monotonically increasing function of
over
. Therefore, the basic compensation strategy is to reduce UAV position errors. Let the pitch and azimuth angles of the UAV position error
be
and
, respectively, which can be represented in vector form as
. From another perspective, the three newly added UAVs introduce errors with magnitude
, pitch angle
, and azimuth angles
,
, and
relative to the original
. Due to the equilateral triangle formation,
Figure 12 illustrates the simplified model leveraging geometric symmetry.
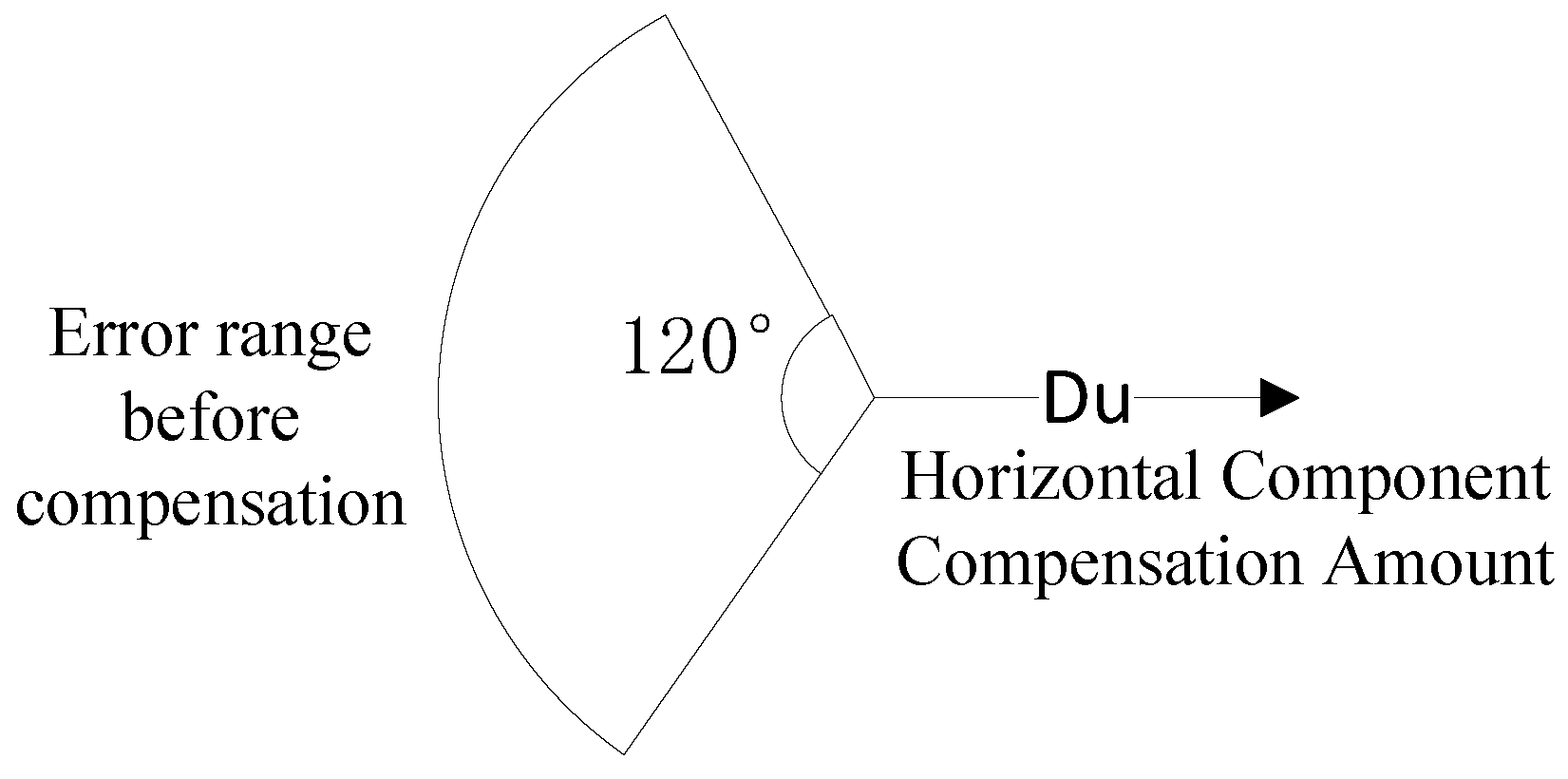
Consequently, the compensated error is derived as follows:
From the above equation, it can be obtained that this compensation method mainly compensates for the horizontal component of the UAV position error. To make the UAV position error effectively compensated, the magnitude of the compensated UAV position error
should be smaller than the original
. After simplification, the magnitude of
can be obtained to be smaller than the original
, as follows:
Since the horizontal component compensation effectiveness degrades when
approaches the boundary (where the value approaches zero), to ensure the compensation scheme remains effective under most conditions, we assume
and rederive the valid range of
using Equation (
47) as follows.
From Equation (
47), it can be derived that
q satisfies the following condition:
Therefore, the range of
is as follows.
To ensure the compensation probability exceeds 70%, the following formula is derived:
And then, we derive that . Specifically, when the UAV position error is known, using an equilateral triangle formation with vertex UAVs positioned at from the center achieves compensation effectiveness in over 70% of scenarios.
The previously analyzed compensation implementation using a triangular formation represents a trade-off between compensation effectiveness and jamming resource utilization. However, when prioritizing compensation performance under sufficient jamming resources, the formation jamming strategy can be generalized to a regular n-gon configuration. For a given UAV position error
R and a required compensation probability exceeding
, the following condition is derived:
Similarly, it can be derived that
q must satisfy the following condition under this constraint:
In summary, when using the equilateral
n-sided formation jamming for compensation, a sufficient but not necessary condition for the compensation probability to reach
is
. Moreover, as can be seen from Equation (
53), the larger the value of
n, the larger the range of values for
q; conversely, the larger the value of
m, the smaller the range of values for
q. Although this paper has established a model and derived the setting conditions for the jamming formation, in engineering practice, due to the minimum distance constraint between drones, the compensation probability can be appropriately reduced. Alternatively, the formation jamming can be scaled down to the arraying of jammer antennas to compensate for the position errors of drones.
Algorithm 1 summarizes the error-aware compensation workflow applied at each radar scan step: it evaluates the upper-bound offset induced by coupled uncertainties and conditionally applies zonal or formation compensation to maintain measurement consistency and coherent false-target tracks.
| Algorithm 1: Error-Aware Compensation Workflow |
| Input: estimated error bounds , association threshold |
| Output: adjusted compensation parameters |
| 1 for each radar scan step k do |
| 2 compute upper-bound offset using Equation (24) |
| 3 if then |
| 4 adjust heuristically per Equations (41)–(43) |
| 5 recompute |
| 6 end if |
| 7 if then |
| 8 adjust UAV geometry: set with q satisfying Equation (53) |
| 9 end if |
| 10 record compensation parameters for step k |
| 11 end for |
6. Conclusions and Future Work
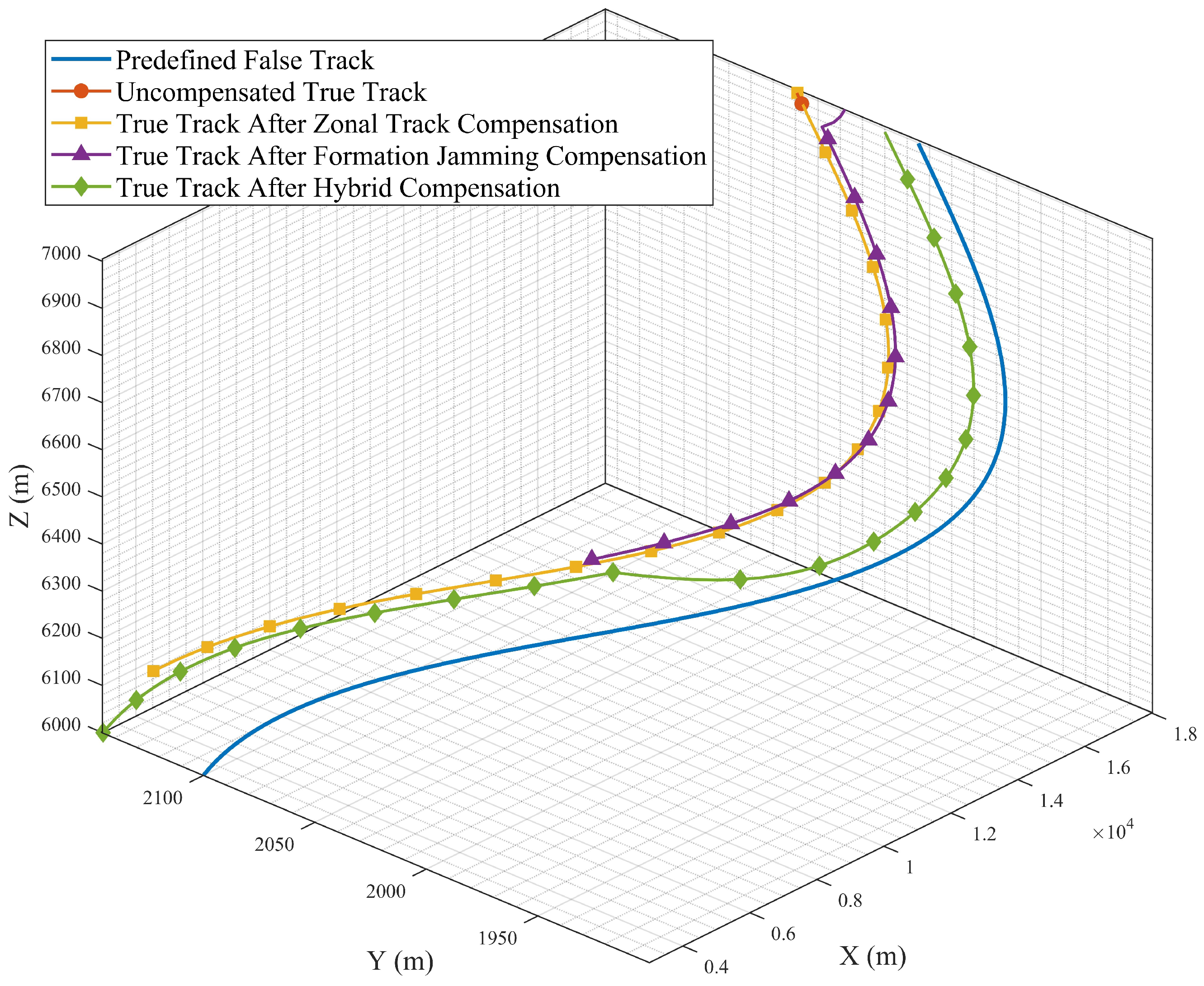
This study proposed an error-aware deception framework that explicitly models radar- position, UAV-navigation, and time-delay uncertainties—and, crucially, captures their spatial coupling. By analyzing how each error source inflates false-target splitting, we derived closed-form conditions under which deceptive measurements remain mutually consistent across radars. These theoretical results were then translated into two practical compensation schemes:zonal trajectory compensation, which inserts auxiliary false targets to form a dense deception belt, and formation-based compensation, which reshapes the swarm geometry to suppress horizontal error components.
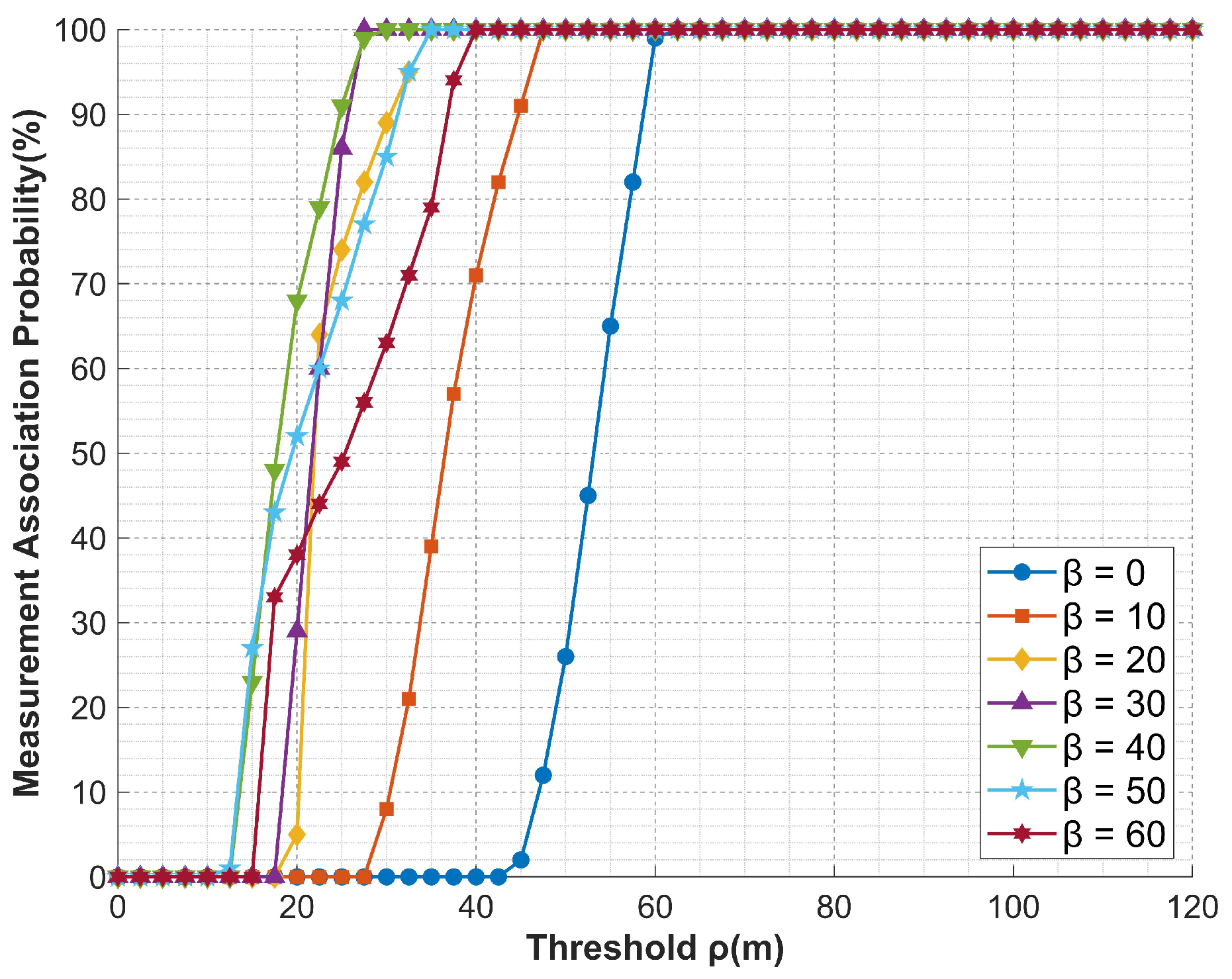
Without compensation, the correlation-gate radius had to be about 60 m to maintain even modest track coherence. This large gate was required because coupled position and timing errors substantially displaced the false targets. The proposed zonal-trajectory compensation reduced the required gate to 27.5 m and markedly improved false-target alignment across multiple radars. Likewise, the formation-based compensation lowered the gate threshold to approximately 30 m and produced stable track structures across diverse error orientations. Simulations further showed that combining both strategies provided the best trade-off between compensation effectiveness and robustness. Under representative simulation settings involving radar-position errors of 50 m and time-delay offsets of 10 m, the combined compensation method maintained measurement association across all evaluated time steps. These findings indicate that the joint compensation scheme markedly enhances the reliability and spatial coherence of multi-UAV deception under realistic uncertainties, thereby reducing the gap between theory and practice.
Despite these gains, several limitations remain. The present model omits dynamic radar-cross-section variations, Doppler-velocity coupling, and channel-specific electromagnetic distortions. Furthermore, the compensation logic is purely geometric; questions of power allocation, waveform design, and cognitive electronic-warfare adaptation are left unaddressed. Finally, all evaluations were performed in simulation, so real-time feedback constraints on UAV manoeuvring were not fully captured.
Future research will therefore move in four directions. First, we will extend the homology test to incorporate RCS variability and Doppler misregistration, enabling deception that is robust against velocity-gated fusion filters. Second, an adaptive compensation controller will be developed by embedding an online Kalman estimator that updates error bounds and tunes compensation gains during flight, thus enhancing resilience to wind-induced perturbations and clock drifts. Third, hardware-in-the-loop trials—with a software-defined-radio swarm platform—will be conducted to validate latency, power consumption, and spectral-mask compliance under dense electronic-warfare conditions. Finally, we aim to generalize the framework to cross-domain scenarios in which RF decoys are synchronized with infrared flares, allowing a coordinated attack on multi-sensor fusion radars. Collectively, these efforts will advance the proposed methodology from high-fidelity simulation toward field-deployable multi-UAV deception technology.