1. Introduction
In recent years, continuous advancements in communications technology have led to significant increase in data transmission volumes. Digital images are often used as carriers of information due to their convenience and versatility, making them easy targets for attackers or eavesdroppers. As one of most effective image security techniques, encryption has been widely researched and used to address these vulnerabilities and protect the confidentiality of data.
However, non-chaotic encryption techniques still have disadvantages such as high computational overhead, insufficient key space, and deterministic behavior [
1]. Non-chaotic encryption techniques such as AES, DES, and RSA-based approaches face inherent challenges when applied to image data, while block ciphers such as AES (ECB/CBC modes) struggle with redundancy and bulk data in images, leading to inefficiency. Many non-chaotic systems exhibit linearity or periodic behavior, limiting their resistance to brute-force attacks. For instance, 128-bit AES keys may be vulnerable to quantum-assisted attacks, whereas chaotic systems offer exponentially larger key spaces via continuous parameters. Non-chaotic methods lack sensitivity to initial conditions, making them predictable under known/chosen-plaintext attacks. This contrasts sharply with chaotic systems, where microscopic parameter deviations yield entirely divergent ciphertexts.
Image encryption converts a plaintext image into a noise-like image by combining mathematical theories, cryptographical theories, and image processing techniques. The chaotic system features many excellent inherent characteristics, including ergodicity, aperiodicity, and high sensitivity to the initial conditions and control parameters used to generate pseudo-random sequences during encryption [
2,
3]. For example, Mansouri et al. proposed a novel one-dimensional chaotic map amplifier (1-DCMA) that enhances chaotic behavior, structure and control parameter sensitivity for 1D chaotic maps. This 1-DCMA was then used to generate pseudo-random sequences that could be further processed to disrupt the pixel positions [
2]. In [
3], the authors employed the random sequence engendered by a chaotic system to dynamically alter and reorganize the original image. Subsequently, synchronous permutation and diffusion procedures were performed on the permuted image to attain the cipher image.
Recently, many chaotic based image encryption algorithms were developed in combination with other techniques to pursue higher security. Compressed sensing techniques involving sparse signal representation, encoding measurements, and reconstruction algorithms have been extensively employed for image encryption, as they can reduce channel occupancy after compression [
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14]. In one case, a new structured measurement matrix was designed to simultaneously compress and encrypt multiple images [
4]. Moysis et al. proposed a novel pseudo-random bit generator and an image encryption technique based on shuffling the bit levels [
13]. The integration of shuffling and XOR operations produces a ciphertext image that is robust against a variety of attacks. In 2022, Ichraf et al. proposed two new piecewise compound one-dimensional chaotic maps to merge traditional and straightforward one-dimensional chaotic maps [
14]. Compared to classical chaotic maps, these 1D maps show better chaotic performances. In [
15], the authors employed an encryption algorithm founded upon chaos theory and matrix semi-tensor product theory. Analogous to neural networks, this approach possesses security advanatges for image encryption. Optical information security technology emphasizes the benefits of innate and expeditious parallel processing of large-volume data. This approach differs from the conventional math-centric computer cryptography and information security technology, and is being investigated for image encryption [
16,
17,
18]. In [
17], an optical discrete cosine transform-based double random phase encoding (DCT-DRPE) approach was employed for encrypting the initial image, effectuating an enlarged key space and fast encryption. Moreover, image encryption system based on DNA encoding combine the intricacy of biology and algorithms to improve encryption security [
19,
20,
21,
22,
23]. In [
19], the authors proposed a novel image encryption algorithm based on dynamic DNA encoding to enhance plaintext sensitivity and defend against chosen-plaintext attacks. Generation of the keystreams used in the permutation stage was influenced by the statistical properties of the plaintext. To cope with the ever-increasing amount of data transmission, many multi-image encryption (MIE) algorithms have been investigated to exploit the processing power and the parallel architecture of modern computers [
24,
25,
26] as well as to facilitate efficient storage and communication [
4,
27,
28]. The algorithm for parallel image encryption proposed by Song et al. harnesses parallel computing faculties by optimally utilizing extant threads and processor resources to accomplish elevated encryption velocities [
24].
Base64 encoding is widely recognized for its ability to convert raw data into printable ASCII characters, facilitating transmission across various communication protocols [
29]. Compared with other encoding rules, the transmission of data encoded in base64 provides excellent stability in network environments [
30,
31]. For example, binary data transmission may introduce the risk of certain binary values being mistaken for control characters, consequently leading to transmission failures. In ASCII encoding, the characters corresponding to ASCII values between 128 and 255 encompass invisible characters, which may produce different decoding results under different encoding rules. On the other hand, base64 encoding offers the ability to convert diverse file formats such as images, audio, and video files into printable texts. This versatility ensures that all computer files can be conveniently encoded as base64 characters, facilitating consistent treatment and transmission of data. In [
32], a file encryption system was developed in which the file is first encoded using a base64 algorithm, then encrypted using the well-known advanced encryption standard (AES). In 2021, Selimovic et al. [
33] developed a new image steganography algorithm, that included an innovative method for encoding the original image through base64 in order to expand the capacity of steganography information in the image.
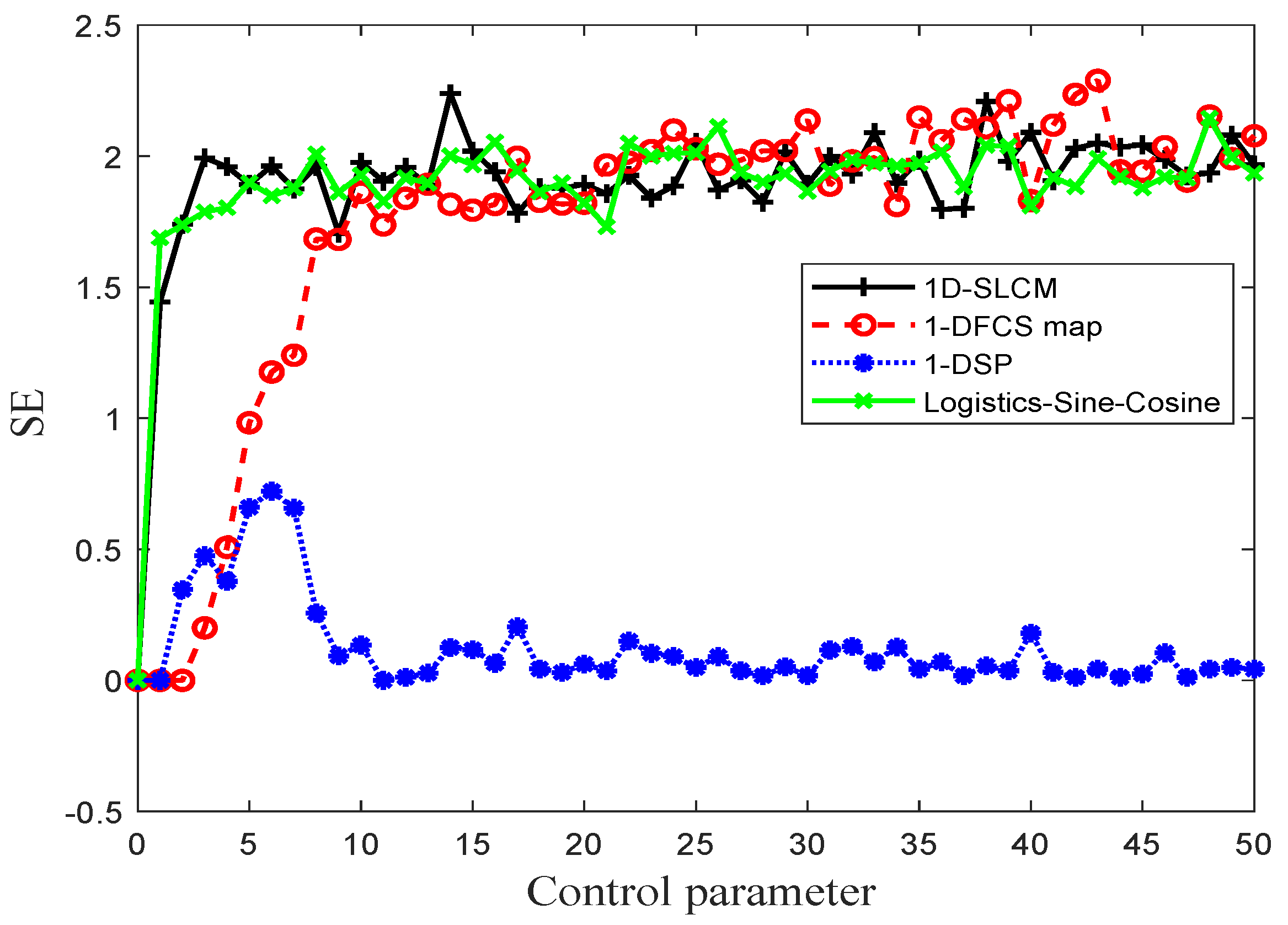
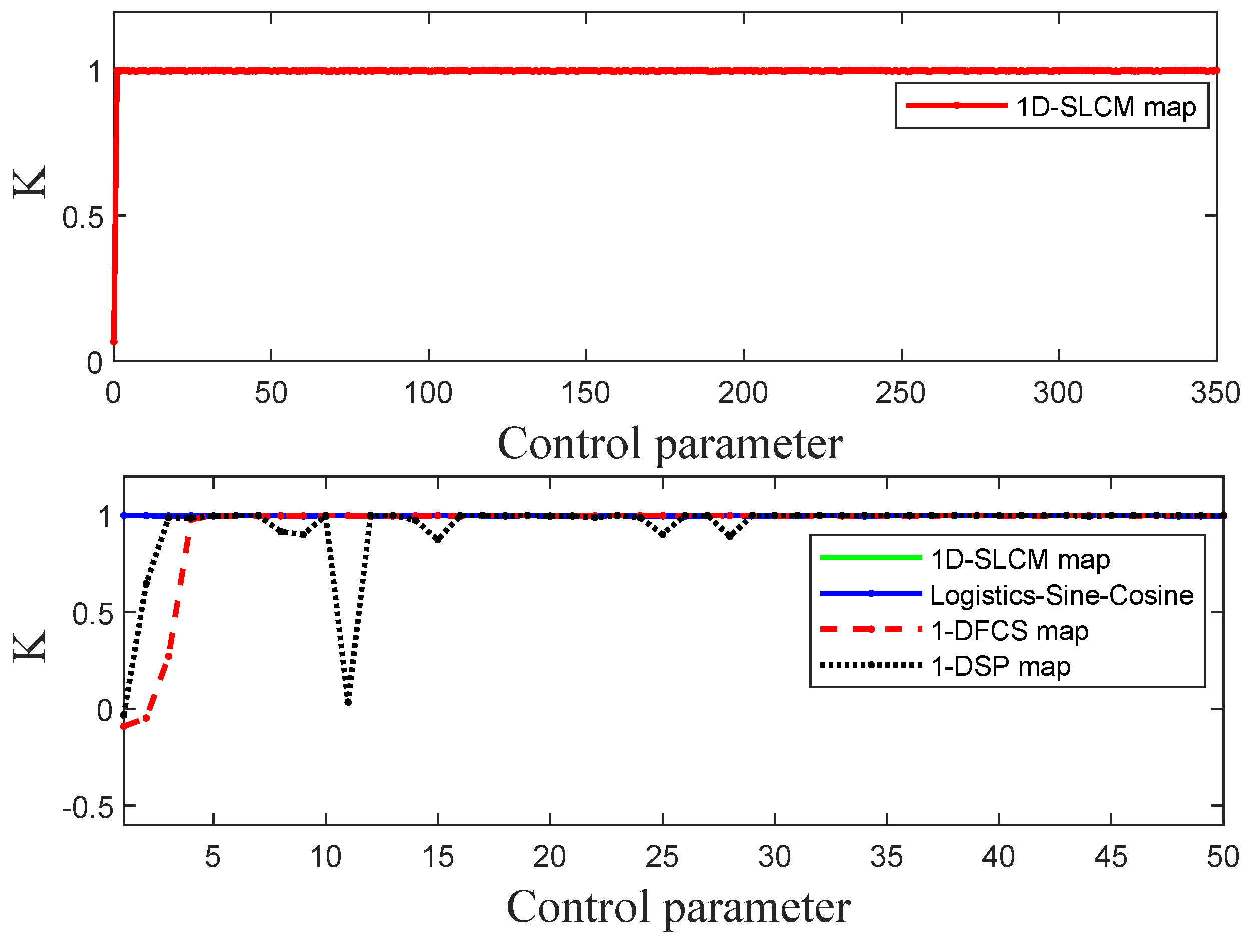
In this paper, we seek to overcome several disadvantages of existing one-dimensional chaotic systems, including low complex dynamic behavior, uneven output, and small chaotic range. Inspired by chaotic sine and logistic systems, we construct a new one-dimensional discrete chaotic system called 1D-SLCM. Furthermore, because base64 encoding has characteristics that make it suitable for information transmission, we introduce a multi-image encryption system that uses base64 encoding and our proposed 1D-SLCM system. The overall contributions of the work are summarized as follows:
- 1.
A new discrete chaotic system (1D-SLCM) is developed and its chaotic performance is extensively tested.
- 2.
Base64 encoding is used in image encryption to achieve high application value in network transmission contexts.
- 3.
By employing the proposed 1D-SLCM system and base64 encoding, we construct a multi-image encryption system. A novel plaintext association framework using the SHA-256 hash function is applied to encrypt the original image, helping to enhance plaintext sensitivity. Complete simulations prove the safety and reliability of our system.
The remainder of this paper is organized as follows:
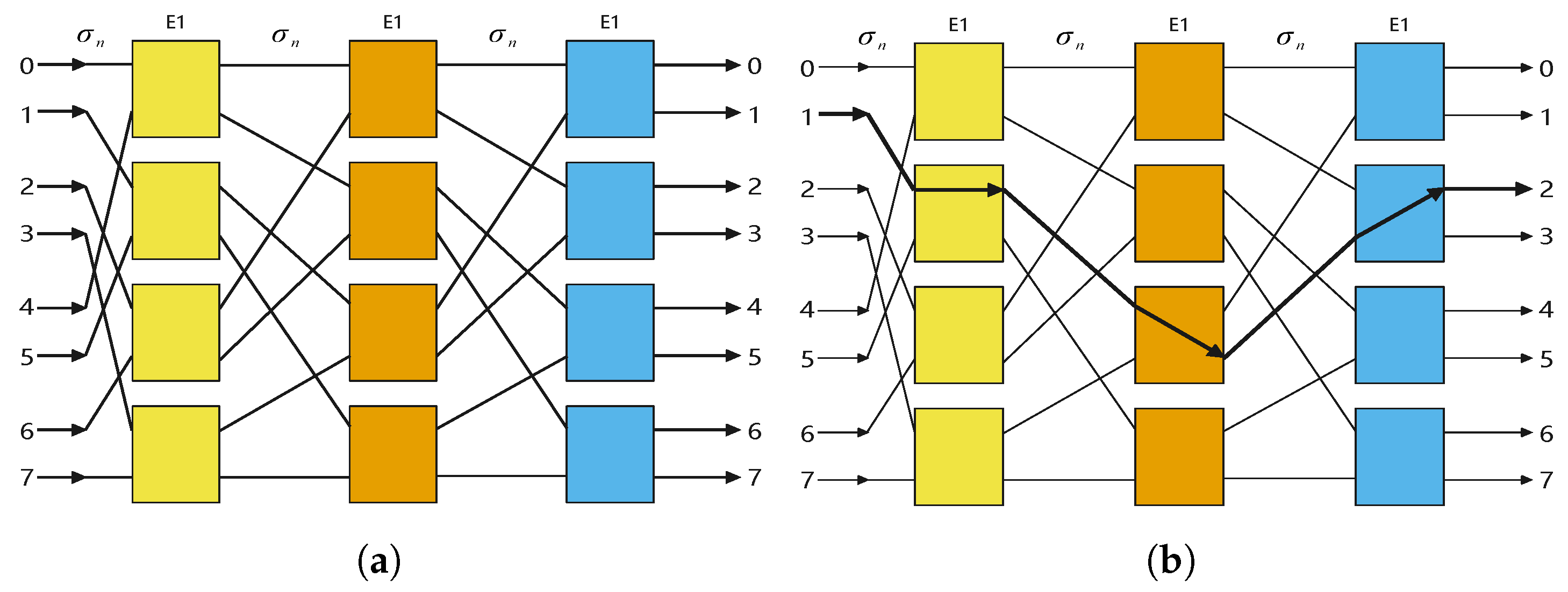
Section 2 provides an introduction to base64 encoding and omega networks;
Section 3 constructs an XOR mapping for base64 encoding using an N = 64 omega network;
Section 4 presents the proposed one-dimensional discrete chaotic system (1D-SLCM);
Section 5 details our novel system for encrypting images through base64 encoding;
Section 6 provides the simulation and security analysis results of the proposed algorithm; finally,
Section 7 summarizes the paper.
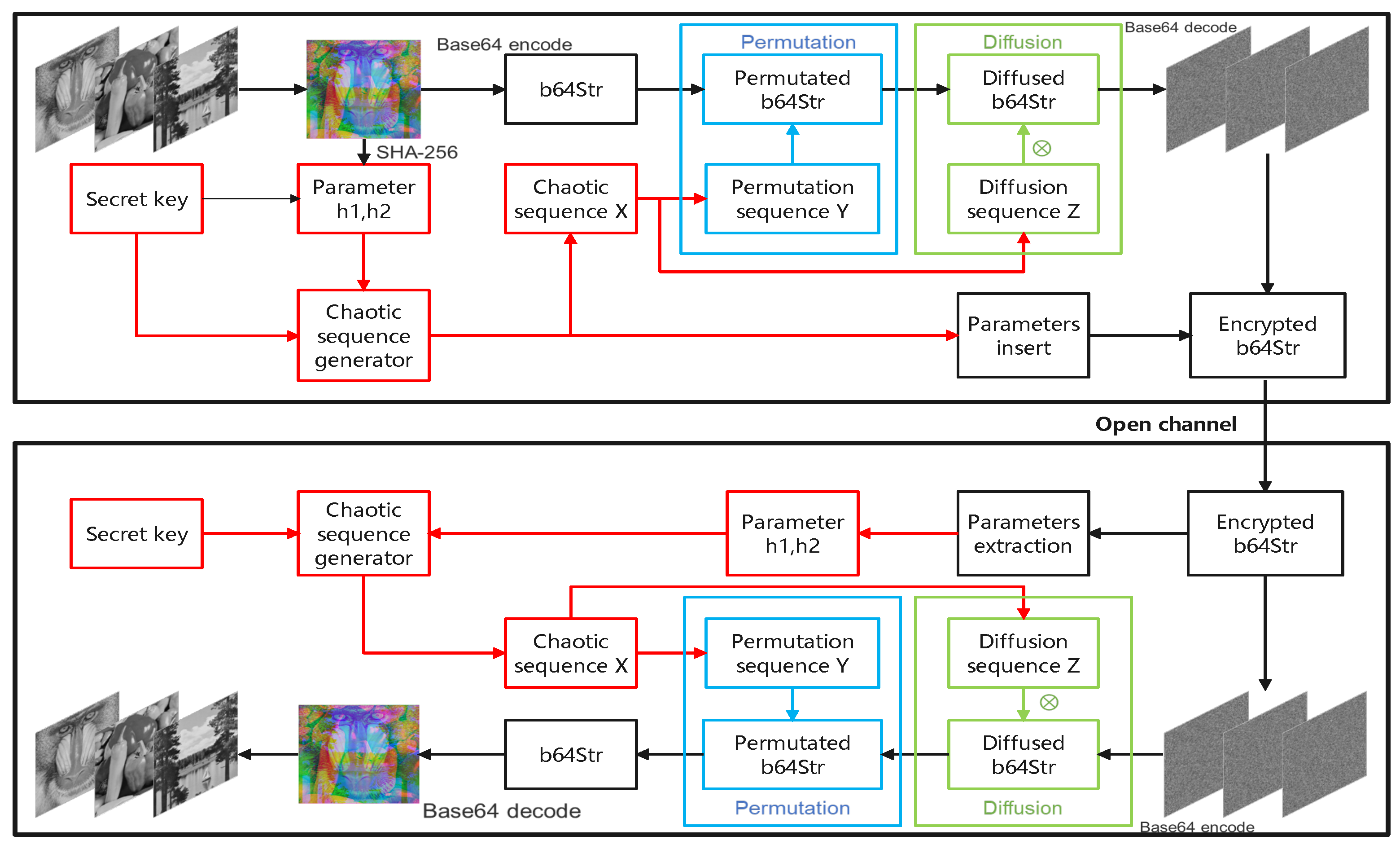
5. The Proposed Encryption Framework
This paper proposes a novel image encryption system that leverages the versatility of base64 encoding to convert various forms of files such as text, images, audio, and video into ASCII characters. The flow chart of the proposed encryption framework is shown in
Figure 7.
Step 1: Combine three gray images with size into an RGB color image () where each image corresponds to one channel (red, green or blue).
Step 2: To bolster the sensitivity of the encryption algorithm to plaintext variations, the SHA-256 hash function is employed to derive a 256-bit hash value
h. We partition
h into eight distinct groups, as delineated in Equation (
13):
By executing pairwise XOR operations on each group, a pair of parameters
and
is produced using Equation (
14):
Step 3: Following Step 1, the RGB color image is subjected to encoding utilizing the base64 technique, yielding a string with size .
Step 4: In order to expand the key space of the algorithm, eight initial values
of the chaotic system are chosen from the key space, then used to iterate the chaotic system
times. The first
iterations are discarded to obtain eight sequences, as described by Equation (
15):
To improve the key sensitivity of the algorithm, the
element is then modified by Equation (
16) before performing subsequent iterations:
Using the eight modified value
, the chaotic system is continually iterated
times to obtain eight sequences, as delineated by Equation (
17):
Finally, the eight sequences are linked together to obtain the final sequence
X with size
, which is processed using Equation (
18) to derive sequence
Y for permutation and sequence
Z for diffusion:
Step 5: Perform the permutation operation. The base64-encoded string is scrambled using sequence Y, as detailed in Algorithm 1.
Step 6: Perform the diffusion operation. Each character in is mapped to a new character using Z as the control signal, obtaining the encrypted character string .
Step 7: Because the two parameters and are needed in the decryption process, and are both embedded in the ciphertext and transmitted to the receiver.
First, and are each converted into binary sequences, which are integrated to generate a new sequence with a size of 64, denoted as . Second, two binary numbers and are generated by and appended to the end of . Third, the new sequence is divided into eleven groups, each of which is converted to a decimal number ranging from 0 to 63. Fourth, each decimal number is mapped to a corresponding base64 character.
Finally, the eleven base64 characters are inserted into
to obtain the final
according to the insertion position
, which is calculated using Equations (
19) and (
20):
| Algorithm 1 Encryption algorithm |
Input: The base64 encoded string and two random sequences Y, Z.
Output: Encrypted Base64 encoding string .
- 1:
for do - 2:
- 3:
- 4:
- 5:
end for - 6:
for do - 7:
Perform Base64 encoding diffusion process to obtain . - 8:
end for - 9:
Calculate the sequence with Equation ( 19) and ( 20). - 10:
Insert and to and get .
|
Decryption follows the reverse process to encryption. First, the same random sequence
X is generated. Second,
and
are extracted from the encrypted string
to obtain
. Third, sequences
Y and
Z are generated by
X with
and
using Equations (
15)–(
18). Finally, the decryption process is performed as detailed in Algorithm 2.
| Algorithm 2 Decryption algorithm |
Input: The encrypted Base64 encoding string , sequences Y, Z.
- 1:
for do - 2:
Perform Base64 encoding inverse diffusion process to obtain . - 3:
end for - 4:
for do - 5:
- 6:
- 7:
- 8:
end for - 9:
An image ← Base64 decode .
|
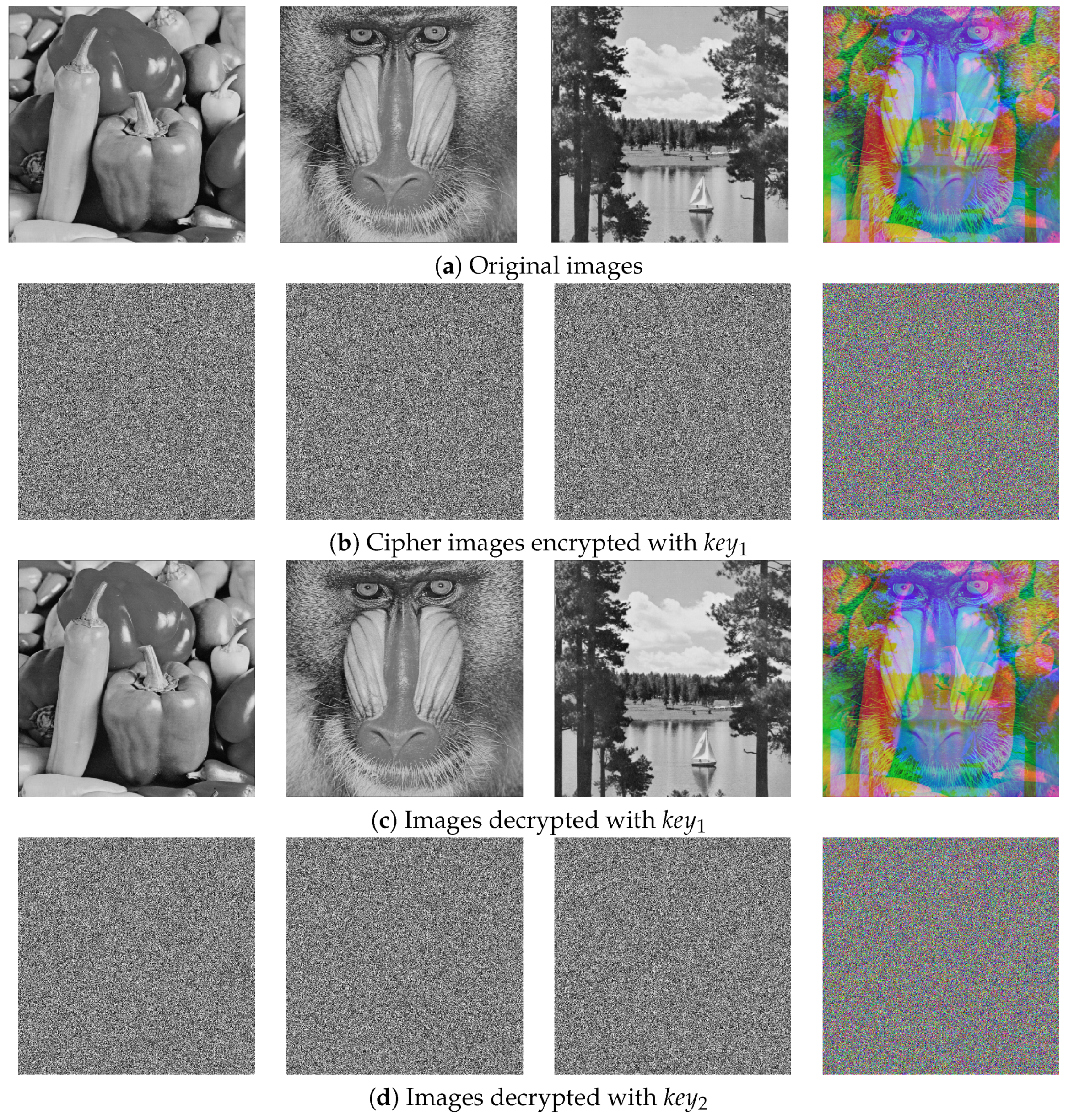
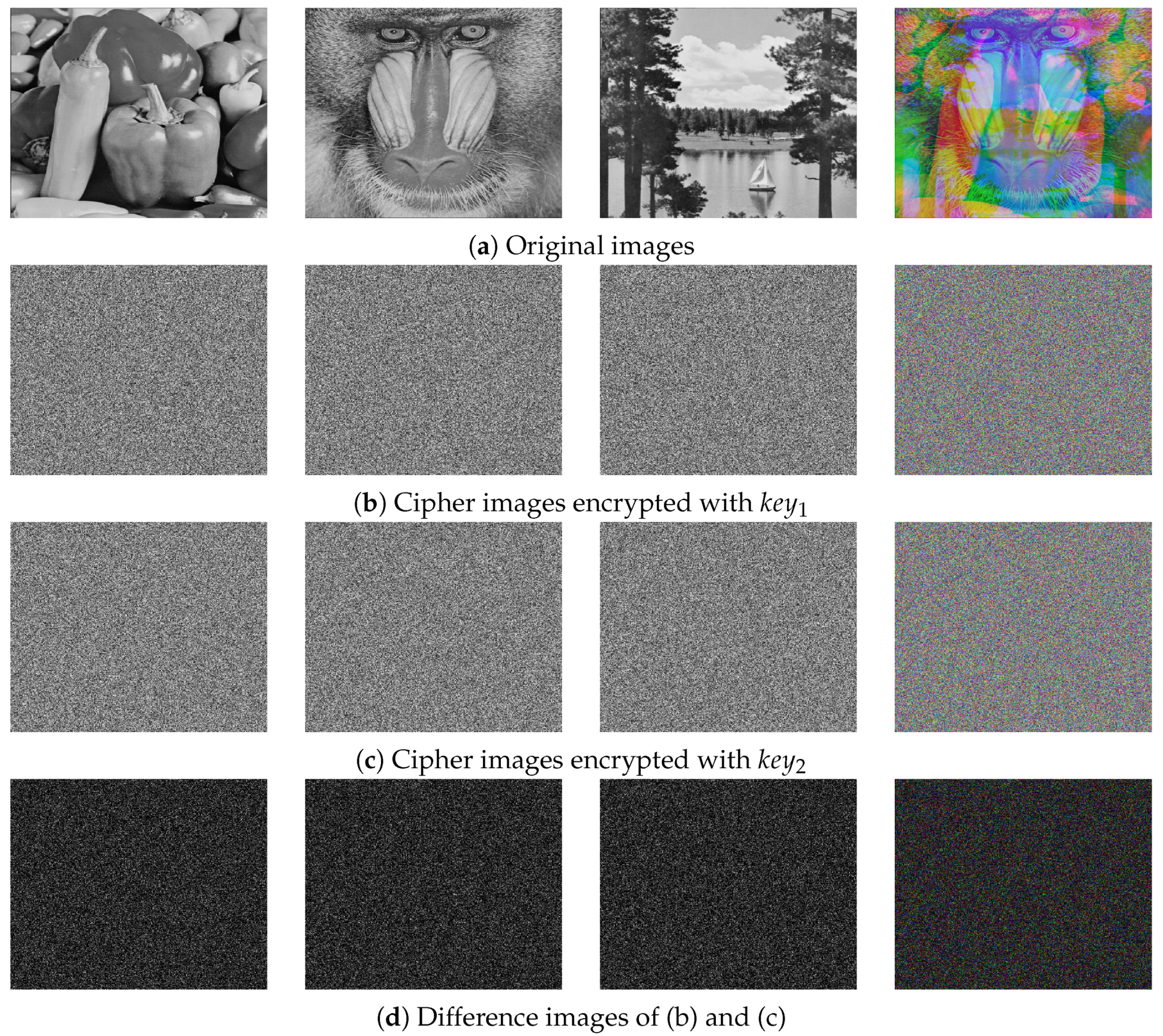
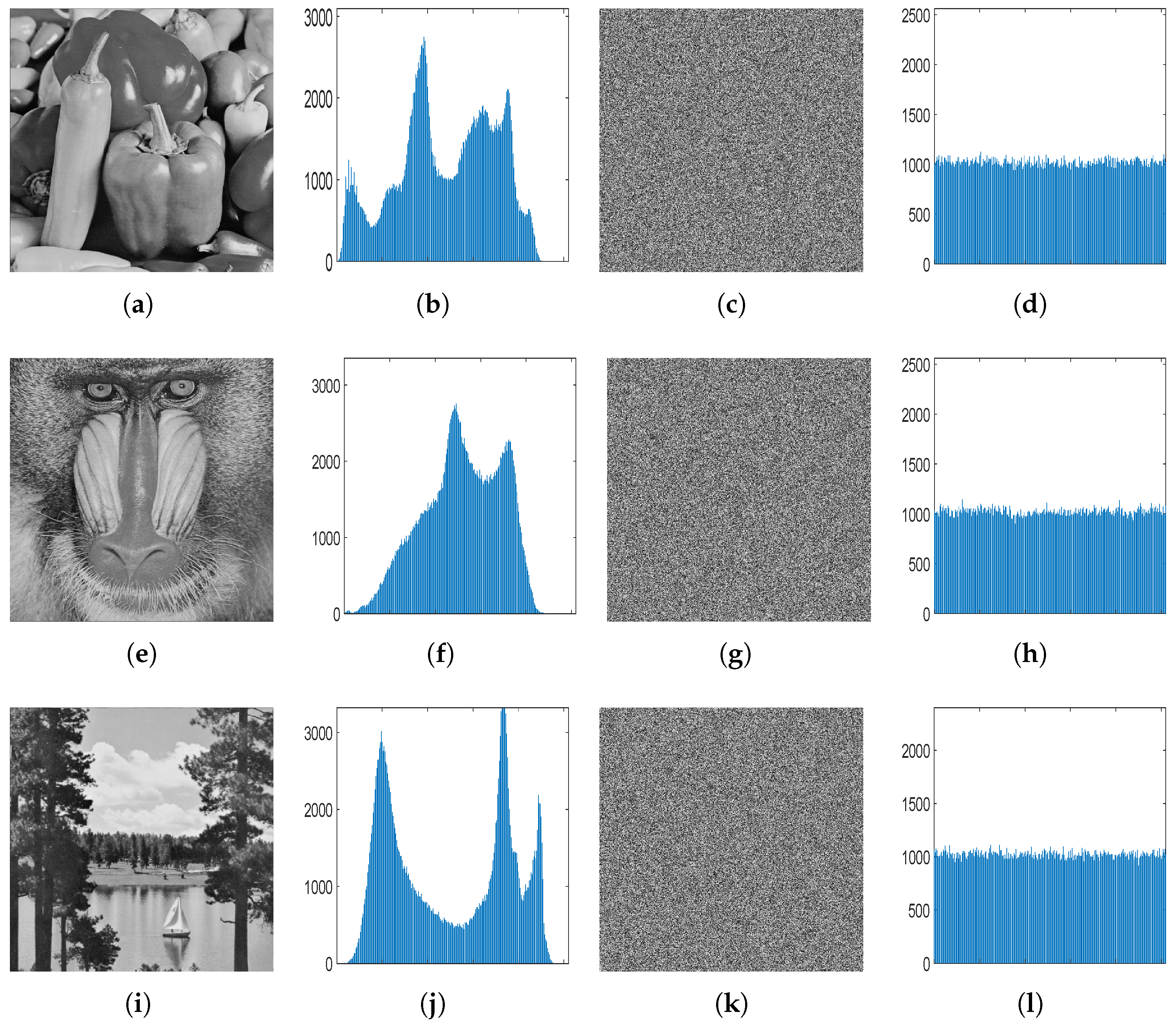
7. Conclusions
This paper introduces a new chaotic system called 1D-LSCM along with a novel multi-image encryption algorithm. Simulation results indicate that the proposed algorithm can efficiently encrypt three grayscale images simultaneously. However, due to the characteristics of base64 encoding, this encryption algorithm cannot resist Gaussian attacks, and can only be used for encrypting digital images.
Because all types of computer files, including text, audio, and video, can be converted into base64 encoding, the encryption algorithm proposed in this paper holds significant potential for widespread future adoption in the communications field. The proposed algorithm’s efficiency, safety, and compatibility with various data formats make it a promising solution for secure communication applications. In addiion, its ability to handle different types of data while maintaining high levels of security and efficiency positions it as a reliable choice for ensuring confidentiality in contemporary communication systems.