Secure Wireless Communication for Correlated Legitimate User and Eavesdropper Channels via Movable-Antenna Enhanced Frequency Diverse Array
Abstract
1. Introduction
- We propose the idea of employing MA and FDA to achieve PHY security. FDA can decouple the channels between the proximal LU and Eve through frequency domain capabilities. MA further enhances the decoupling performance by providing spatial degrees of freedom that compensate for the limitations of FDA. The proposed MA-FDA approach maximizes PHY security through multidimensional channel reconstruction, thereby achieving a higher secrecy rate.
- To address this idea, we formulate a secrecy rate maximization problem by jointly optimizing the positions of antennas, FDA frequency offsets, and beamforming vectors, subject to the predefined regions for antenna positions, frequency offsets range and energy constraints. The proposed formulation fully exploits the spatial and frequency degrees of freedom in the MA-FDA system, thereby significantly enhancing PHY security.
- The secrecy rate maximization problem is a non-convex problem involving coupled variables. To solve this difficult problem, the proposed problem is partitioned into several subproblems. An algorithm is then designed using the AO method [15] to iteratively update the parameters, specifically the antenna positions, FDA frequency offsets, and beamformers. However, as these subproblems remain difficult to solve, we employ the projected gradient ascent (PGA) method and block a successive upper-bound minimization (BSUM) method to handle them.
1.1. Related Works
1.2. Organization and Notations
2. System Model and Problem Statement
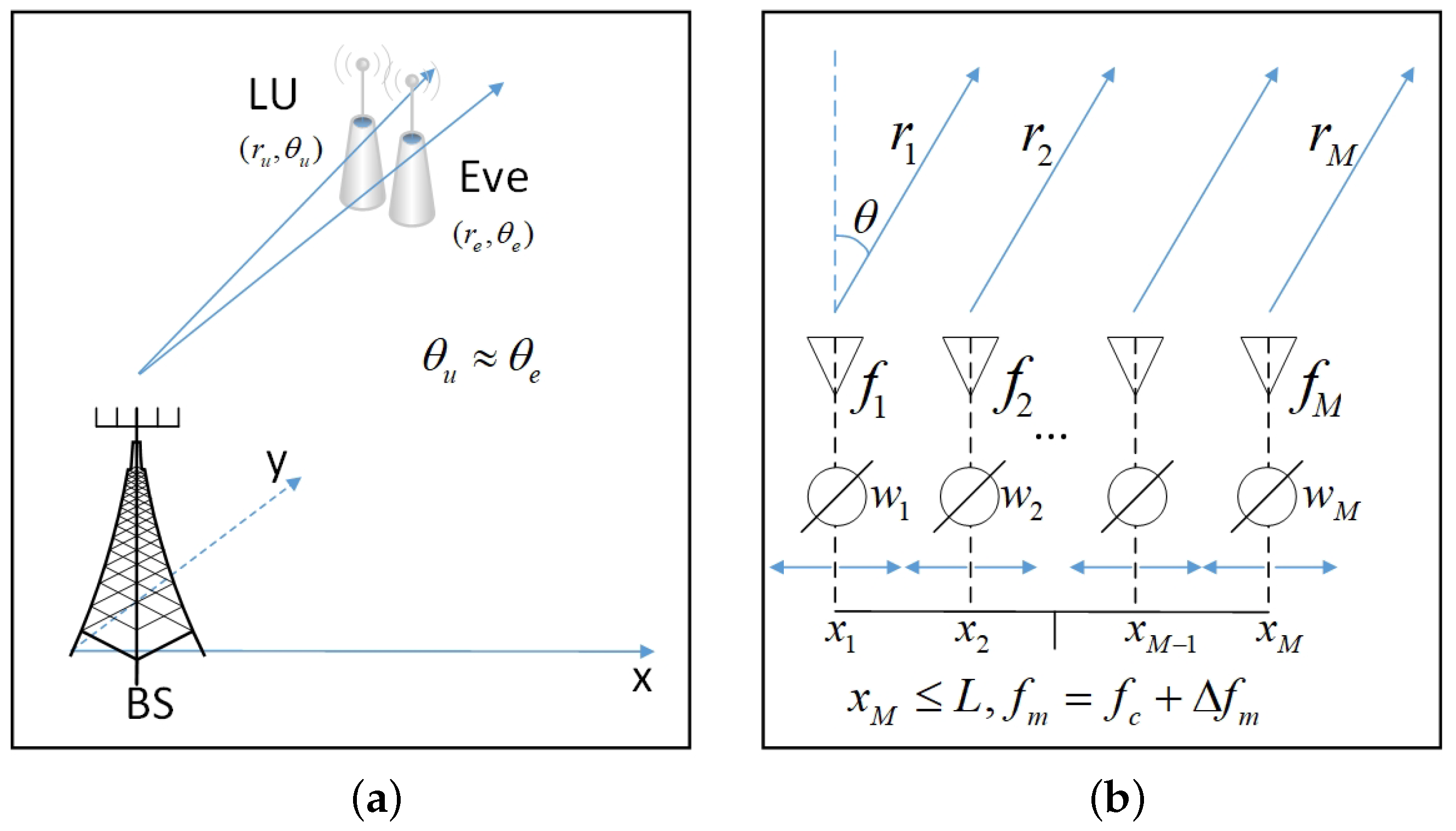
2.1. System Model
2.2. Problem Formulation
3. AO Algorithm for Problem (6a)–(6e)
3.1. -Subproblem
- Case 1: When and as shown in Figure 2a, is a straight line;
- Case 2: When and as shown in Figure 2b, is formed as a quadratic function, symmetrical along ;
- Case 3: When as shown in Figure 2c, is formed as a quadratic function, which is symmetric about the first-right valley point of beside the tangential point;
- Case 4: When as shown in Figure 2d, is formed as a quadratic function, which is symmetric about the first-left valley point of beside the tangential point.
3.2. -Subproblem
3.3. -Subproblem
3.4. Algorithm Summary
- -subproblem: .
- -subproblem: the complexity of gradient computation and projection are and , respectively.
- -subproblem: .
| Algorithm 1 AO approach for solving problem (6a)–(6e) |
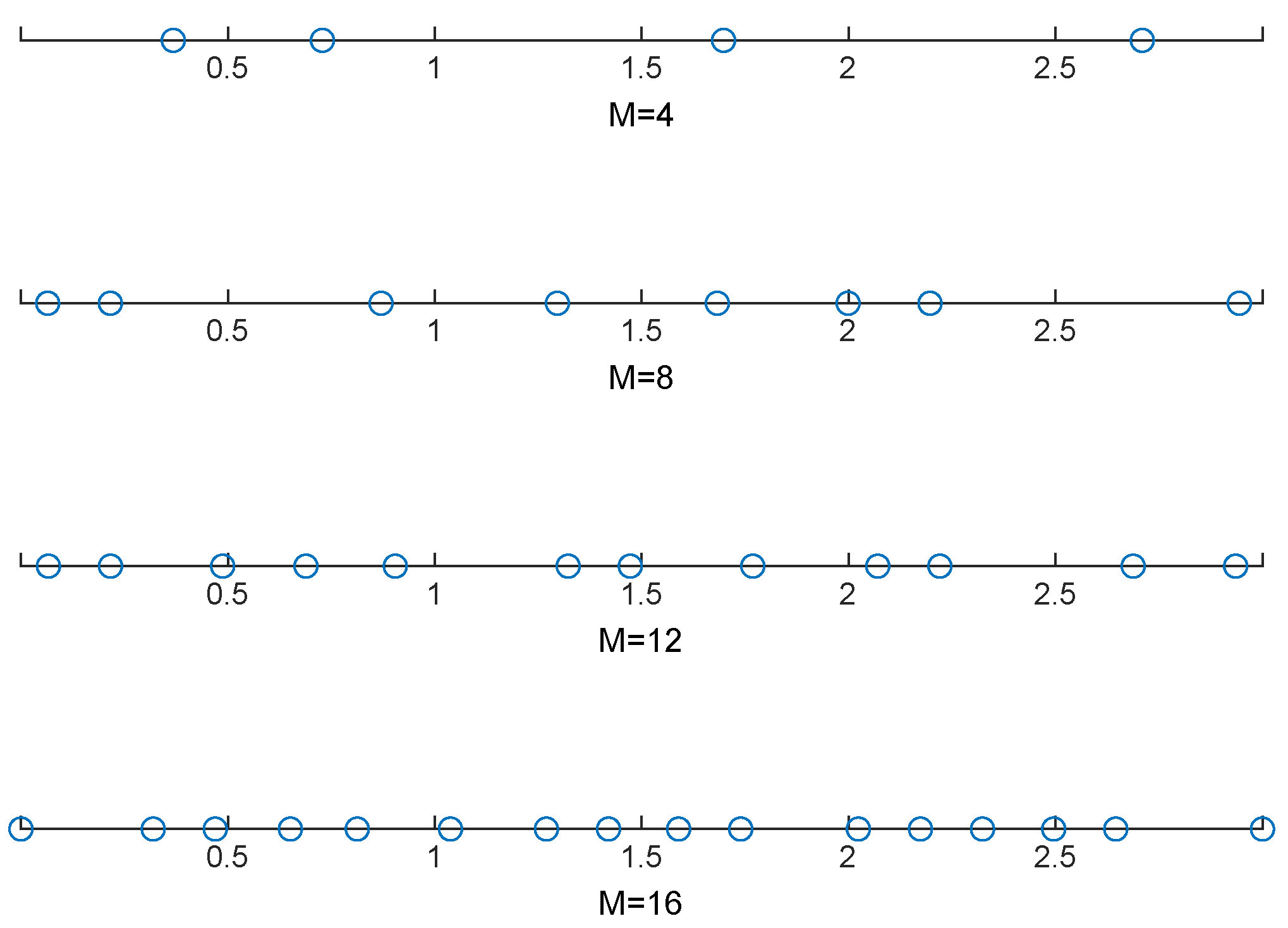
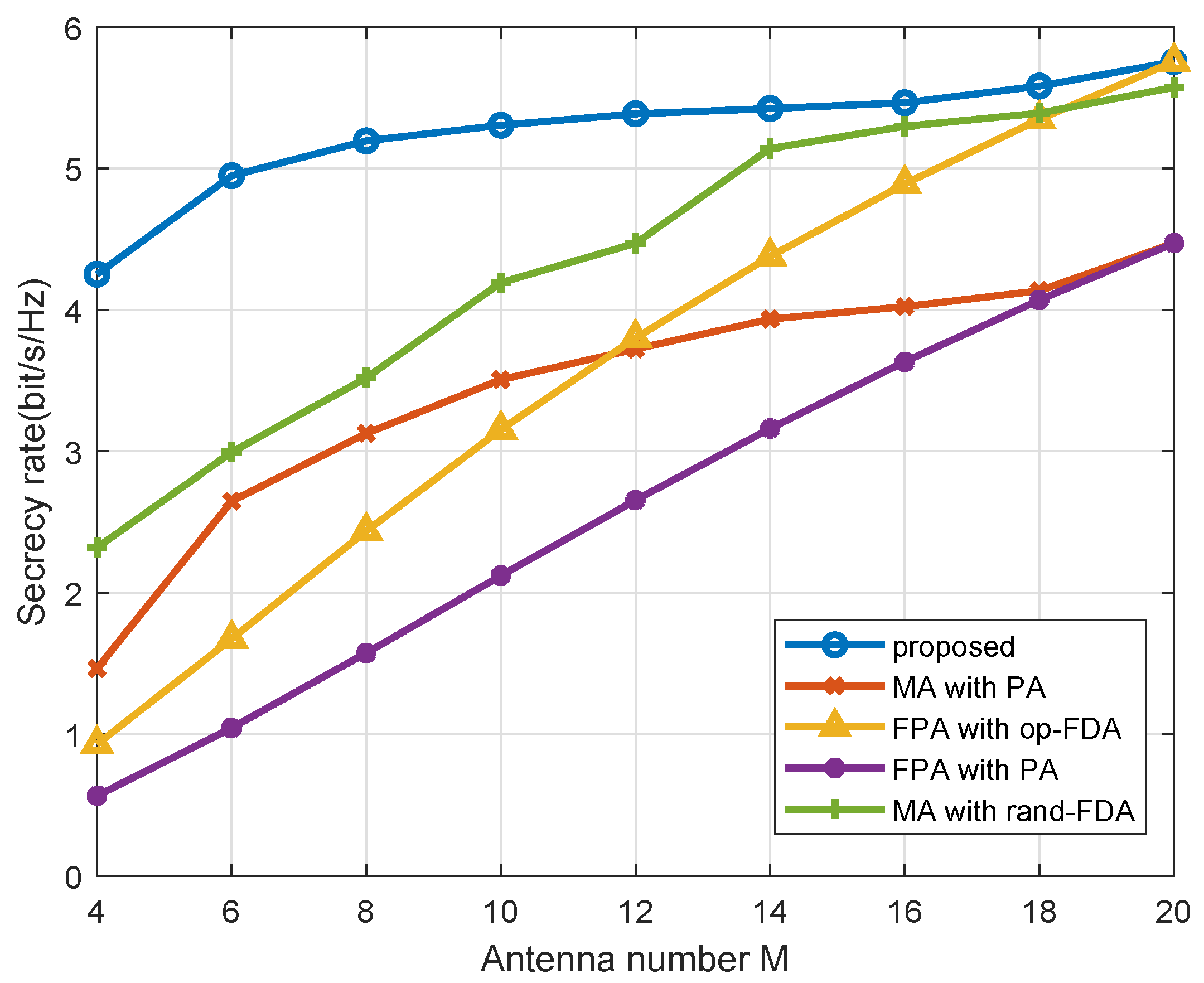
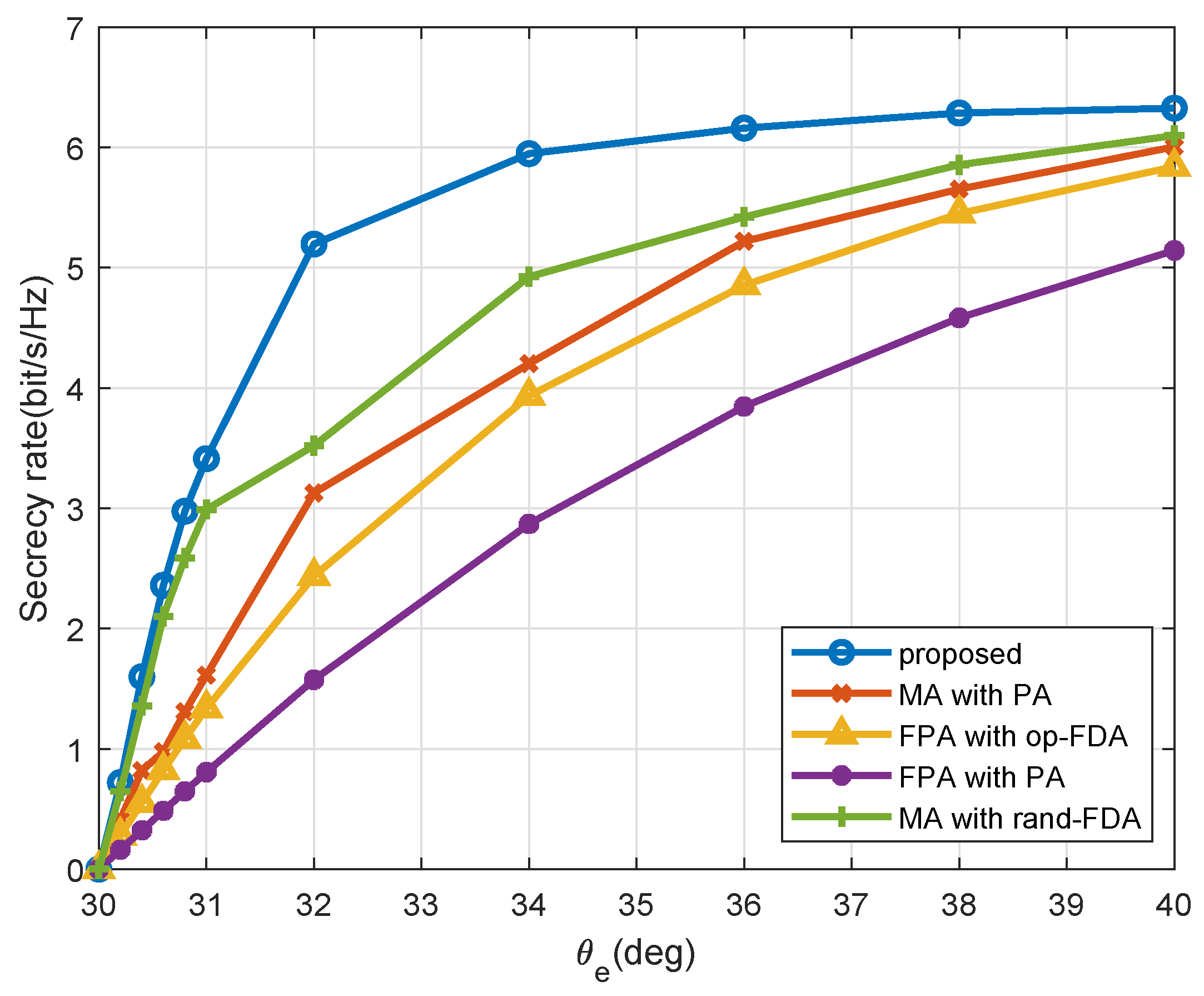
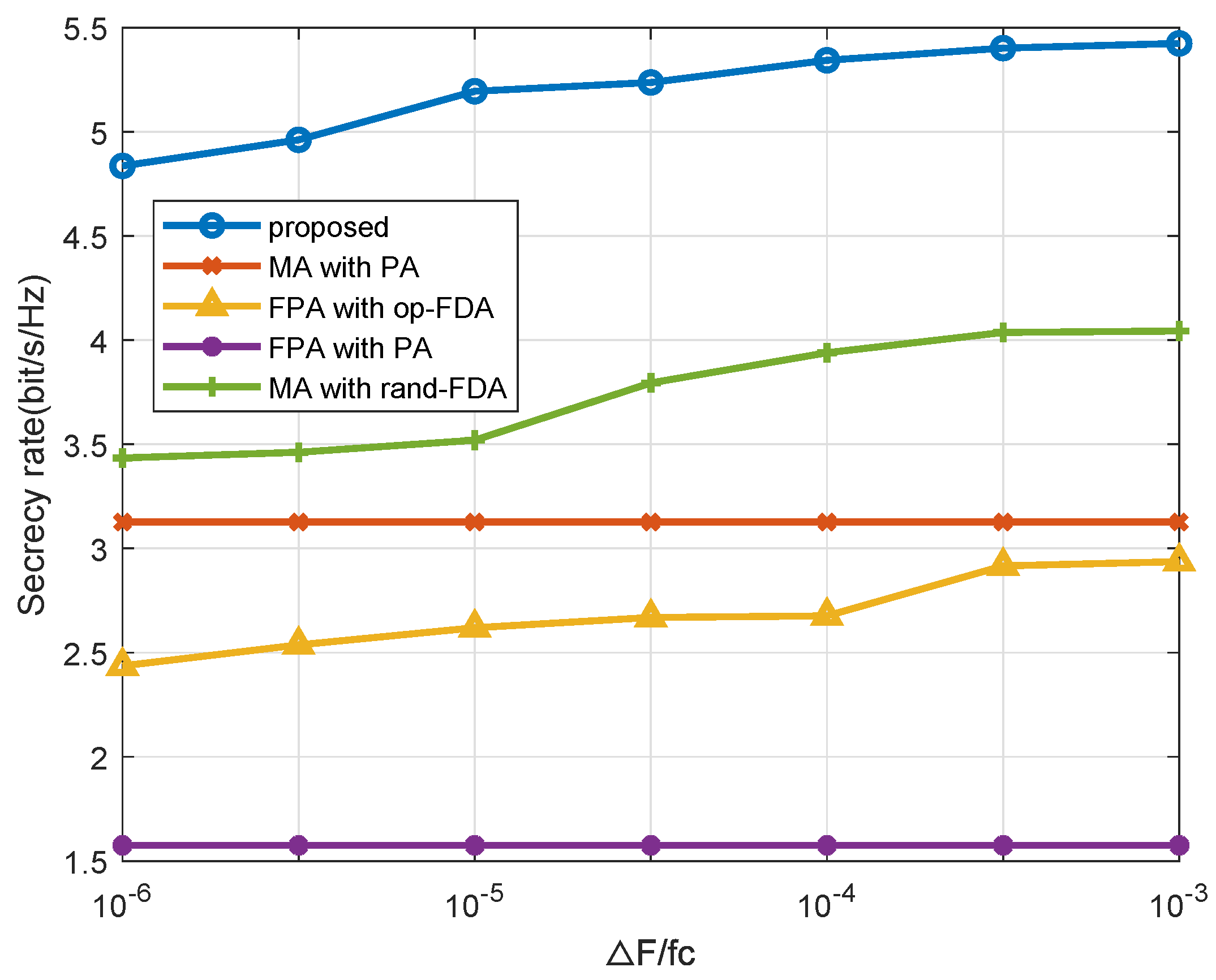
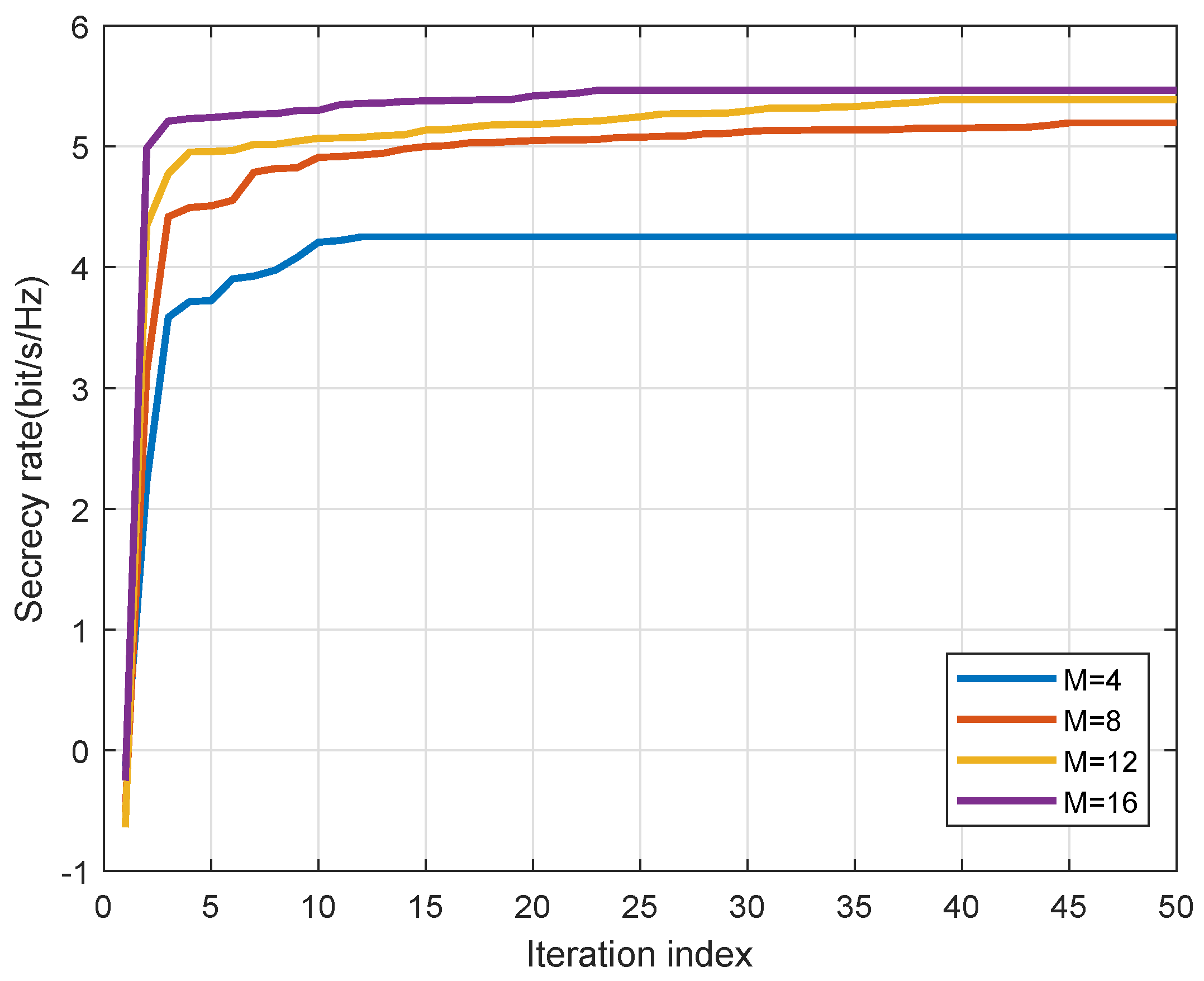
4. Numerical Simulations
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| PHY | Physical-Layer |
| LU | Legitimate User |
| Eve | Eavesdropper |
| BS | Base Station |
| AO | Alternating Optimization |
| PGA | Projected Gradient Ascent |
| BSUM | Block Successive Upper-Bound Minimization |
| FDA | Frequency Diverse Arrays |
| MA | Movable Antenna |
| PA | Phased Array |
| SINR | Signal-to-Interference-Plus-Noise Ratio |
| FPA | Fixed Position Antenna |
Appendix A. Proof of Proposition 1
Appendix B. Proof of Proposition 2
References
- Liu, Y.; Chen, H.H.; Wang, L. Physical Layer Security for Next Generation Wireless Networks: Theories, Technologies, and Challenges. IEEE Commun. Surv. Tutor. 2017, 19, 347–376. [Google Scholar]
- Khan, W.U.; Lagunas, E.; Ali, Z.; Javed, M.; Ahmed, M.; Chatzinotas, S.; Ottersten, B.; Popovski, P. Opportunities for Physical Layer Security in UAV Communication Enhanced with Intelligent Reflective Surfaces. IEEE Wirel. Commun. 2022, 29, 22–28. [Google Scholar]
- Nguyen, V.D.; Duong, T.; Dobre, O.; Shin, O.S. Joint Information and Jamming Beamforming for Secrecy Rate Maximization in Cognitive Radio Networks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2609–2623. [Google Scholar]
- Li, X.; Wang, W.; Zhang, M.; Zhou, F.; Al-Dhahir, N. Robust Secure Beamforming for SWIPT-Aided Relay Systems with Full-Duplex Receiver and Imperfect CSI. IEEE Trans. Veh. Technol. 2020, 69, 1867–1878. [Google Scholar]
- Zhao, S.; Liu, J.; Shen, Y.; Jiang, X.; Shiratori, N. Secure Beamforming for Full-Duplex MIMO Two-Way Untrusted Relay Systems. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3775–3790. [Google Scholar] [CrossRef]
- Fu, H.; Feng, S.; Tang, W.; Ng, D.W.K. Robust Secure Beamforming Design for Two-User Downlink MISO Rate-Splitting Systems. IEEE Trans. Wirel. Commun. 2020, 19, 8351–8365. [Google Scholar]
- Lin, J.; Li, Q.; Yang, J.; Shao, H.; Wang, W.-Q. Physical-Layer Security for Proximal Legitimate User and Eavesdropper: A Frequency Diverse Array Beamforming Approach. IEEE Trans. Inf. Forensics Secur. 2018, 13, 671–684. [Google Scholar]
- Bang, H.; Yan, Y.S.; Basit, A.; Wang, W.-Q.; Cheng, J. Radar Cross Section Characterization of Frequency Diverse Array Radar. IEEE Trans. Aerosp. Electron. Syst. 2023, 59, 460–471. [Google Scholar]
- Cheng, J.; Juhlin, M.; Jakobsson, A.; Wang, W.-Q. Designing Optimal Frequency Offsets for Frequency Diverse Array MIMO Radar. IEEE Trans. Aerosp. Electron. Syst. 2023, 59, 8104–8118. [Google Scholar]
- Liao, Y.; Zeng, G.; Luo, Z.; Liu, Q. Time-Variance Analysis for Frequency-Diverse Array Beampatterns. IEEE Trans. Antennas Propag. 2023, 71, 6558–6567. [Google Scholar]
- Zheng, J.; Zhang, J.; Du, H.; Niyato, D.; Sun, S.; Ai, B.; Letaief, K. Flexible-Position MIMO for Wireless Communications: Fundamentals, Challenges, and Future Directions. IEEE Wirel. Commun. 2023, 31, 18–26. [Google Scholar] [CrossRef]
- Zhu, L.; Ma, W.; Ning, B.; Zhang, R. Movable-Antenna Enhanced Multiuser Communication via Antenna Position Optimization. IEEE Trans. Wirel. Commun. 2024, 23, 7214–7229. [Google Scholar] [CrossRef]
- Zhu, L.; Ma, W.; Zhang, R. Movable-Antenna Array Enhanced Beamforming: Achieving Full Array Gain with Null Steering. IEEE Commun. Lett. 2023, 27, 3340–3344. [Google Scholar] [CrossRef]
- Ma, W.; Zhu, L.; Zhang, R. Multi-Beam Forming with Movable-Antenna Array. IEEE Commun. Lett. 2023, 28, 697–701. [Google Scholar] [CrossRef]
- Li, R.; Sun, S.; Tao, M. Ergodic Achievable Rate Maximization of RIS-Assisted Millimeter-Wave MIMO-OFDM Communication Systems. IEEE Trans. Wirel. Commun. 2023, 22, 2171–2184. [Google Scholar] [CrossRef]
- Zhu, L.; Ma, W.; Zhang, R. Movable Antennas for Wireless Communication: Opportunities and Challenges. IEEE Commun. Mag. 2023, 62, 114–120. [Google Scholar] [CrossRef]
- Ma, W.; Zhu, L.; Zhang, R. Movable Antenna Enhanced Wireless Sensing via Antenna Position Optimization. IEEE Trans. Wirel. Commun. 2024, 23, 16575–16589. [Google Scholar] [CrossRef]
- Liao, J.; Zhu, F.; Hu, G. Jamming-Assisted Wireless Information Surveillance with Movable Antenna. IEEE Commun. Lett. 2024, 28, 2739–2743. [Google Scholar] [CrossRef]
- Zhang, B.; Xu, K.; Xia, X.; Hu, G.; Wei, C.; Li, C.; Cheng, K. Sum-Rate Enhancement for RIS-Assisted Movable Antenna Systems: Joint Transmit Beamforming, Reflecting Design, and Antenna Positioning. IEEE Trans. Veh. Technol. 2025, 74, 4376–4392. [Google Scholar] [CrossRef]
- Wu, Y.; Xu, D.; Ng, D.W.K.; Gerstacker, W.; Schober, R. Movable Antenna-Enhanced Multiuser Communication: Jointly Optimal Discrete Antenna Positioning and Beamforming. In Proceedings of the GLOBECOM 2023—2023 IEEE Global Communications Conference, Kuala Lumpur, Malaysia, 4–8 December 2023; pp. 7508–7513. [Google Scholar]
- Chen, X.; Feng, B.; Wu, Y.; Ng, D.W.K.; Schober, R. Joint Beamforming and Antenna Movement Design for Moveable Antenna Systems Based on Statistical CSI. In Proceedings of the GLOBECOM 2023—2023 IEEE Global Communications Conference, Kuala Lumpur, Malaysia, 4–8 December 2023; pp. 4387–4392. [Google Scholar]
- Hu, G.; Wu, Q.; Xu, K.; Si, J.; Al-Dhahir, N. Secure Wireless Communication via Movable-Antenna Array. IEEE Signal Process. Lett. 2023, 31, 516–520. [Google Scholar] [CrossRef]
- Cheng, Z.; Li, N.; Zhu, J.; She, X.; Ouyang, C.; Chen, P. Enabling Secure Wireless Communications via Movable Antennas. In Proceedings of the IEEE International Conference on Acoustics, Speech, and Signal Processing, Seoul, Republic of Korea, 14–19 April 2023. [Google Scholar]
- Liu, P.; Si, J.; Cheng, Z.; Li, Z.; Hu, H. Movable-Antenna Enabled Covert Communication. IEEE Wirel. Commun. Lett. 2025, 14, 280–284. [Google Scholar] [CrossRef]
- Gui, R.; Huang, B.; Wang, W.; Sun, Y. Generalized Ambiguity Function for FDA Radar Joint Range, Angle and Doppler Resolution Evaluation. IEEE Geosci. Remote Sens. Lett. 2020, 19, 1–5. [Google Scholar] [CrossRef]
- Hasheminasab, M.; Cheldavi, A.; Kishk, A. Investigating Discular Frequency Diverse Arrays for Scanning Applications. In Proceedings of the 2023 3rd International Conference on Electrical, Computer, Communications and Mechatronics Engineering (ICECCME), Tenerife, Canary Islands, Spain, 19–21 July 2023; pp. 1–4. [Google Scholar]
- qin Wang, W. Frequency Diverse Array Auto-Scanning Beam Characteristics and Potential Radar Applications. IEEE Access 2022, 10, 85278–85288. [Google Scholar] [CrossRef]
- Gao, J.; Yuan, Z.; Zhou, J.; Qiu, B. Artificial-Noise-Aided Energy-Efficient Secure Multibeam Wireless Communication Schemes Based on Frequency Diverse Array. Wirel. Commun. Mob. Comput. 2020, 2020, 4715929. [Google Scholar] [CrossRef]
- Hu, J.; Yan, S.; Shu, F.; Wang, J.; Li, J.Y.; Zhang, Y. Artificial-Noise-Aided Secure Transmission with Directional Modulation Based on Random Frequency Diverse Arrays. IEEE Access 2016, 5, 1658–1667. [Google Scholar] [CrossRef]
- Ji, S.; Wang, W. Physical-Layer Security for Frequency Diverse Array Communication System over Nakagami-m Fading Channels. IEEE Syst. J. 2020, 14, 2370–2381. [Google Scholar] [CrossRef]
- Ding, Y.; Zhang, J.; Fusco, V. Frequency diverse array OFDM transmitter for secure wireless communication. Electron. Lett. 2015, 51, 1374–1376. [Google Scholar] [CrossRef]
- Nusenu, S.Y.; Wang, W.Q.; Ji, S. Secure directional modulation using frequency diverse array antenna. In Proceedings of the 2017 IEEE Radar Conference (RadarConf), Seattle, WA, USA, 8–12 May 2017; pp. 0378–0382. [Google Scholar] [CrossRef]
- Li, L.; Chen, Z.; Chen, R.; Yang, L.; Yan, S. Covert Wireless Communication with Random Frequency Diverse Array. IEEE Trans. Veh. Technol. 2024, 73, 1473–1478. [Google Scholar] [CrossRef]
- You, B.; Lee, I.H.; Jung, H.; Duong, T.Q.; Shin, H. Secure 3D Directional Modulation Using Subarrays Based on Planar Frequency Diverse Array with Nonuniform Frequency Offsets. IEEE Trans. Commun. 2024; early access. [Google Scholar] [CrossRef]
- Chen, K.; Yang, S.; Chen, Y.; Qu, S. Accurate Models of Time-Invariant Beampatterns for Frequency Diverse Arrays. IEEE Trans. Antennas Propag. 2019, 67, 3022–3029. [Google Scholar] [CrossRef]
- Khisti, A.; Wornell, G. Secure Transmission with Multiple Antennas I: The MISOME Wiretap Channel. IEEE Trans. Inf. Theory 2007, 56, 3088–3104. [Google Scholar]
- Ranjan, R.; Bhattacharya, A.; Mukhopadhyay, S.; Mishra, H.B. A Gradient Ascent Based Low Complexity Rate Maximization Algorithm for Intelligent Reflecting Surface-Aided OFDM Systems. IEEE Commun. Lett. 2023, 27, 2083–2087. [Google Scholar]
- Tseng, P. Convergence of a Block Coordinate Descent Method for Nondifferentiable Minimization. J. Optim. Theory Appl. 2001, 109, 475–494. [Google Scholar]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, X.; Shao, H.; Lin, J.; Pan, Y.; Xiong, W. Secure Wireless Communication for Correlated Legitimate User and Eavesdropper Channels via Movable-Antenna Enhanced Frequency Diverse Array. Entropy 2025, 27, 401. https://doi.org/10.3390/e27040401
Wu X, Shao H, Lin J, Pan Y, Xiong W. Secure Wireless Communication for Correlated Legitimate User and Eavesdropper Channels via Movable-Antenna Enhanced Frequency Diverse Array. Entropy. 2025; 27(4):401. https://doi.org/10.3390/e27040401
Chicago/Turabian StyleWu, Xuehan, Huaizong Shao, Jingran Lin, Ye Pan, and Weijie Xiong. 2025. "Secure Wireless Communication for Correlated Legitimate User and Eavesdropper Channels via Movable-Antenna Enhanced Frequency Diverse Array" Entropy 27, no. 4: 401. https://doi.org/10.3390/e27040401
APA StyleWu, X., Shao, H., Lin, J., Pan, Y., & Xiong, W. (2025). Secure Wireless Communication for Correlated Legitimate User and Eavesdropper Channels via Movable-Antenna Enhanced Frequency Diverse Array. Entropy, 27(4), 401. https://doi.org/10.3390/e27040401





