Social Image Security with Encryption and Watermarking in Hybrid Domains
Abstract
1. Introduction
- (1)
- DWT from block DCTs can encrypt and watermark images in hybrid domains.
- (2)
- The algorithm that protects social JPEG images is based on DWT from DCT blocks.
- (3)
- A lightweight security approach for social multimedia platforms is beneficial for resource-constrained equipment.
2. Background
2.1. Singular Value Decomposition
2.2. The Tree Structure Haar Transform
2.3. Cellular Automation
- Rule 1: Cells that are alive but have fewer than two live neighbors will die.
- Rule 2: Cells that are alive and have two or three live neighbors will survive.
- Rule 3: Cells that are alive but have more than three live neighbors will die.
- Rule 4: Cells that are dead but have exactly three live neighbors will revive.
- (1)
- A random sequence () is produced using a given chaotic map. A grid of cell is created based on this random sequence. The sum S of the sequence is calculated as , and the mean value is calculated as . For each cell in the grid, if the corresponding value , then the cell is set to 1, otherwise, it is set to 0. Using the initial grid and the rules of GoL, a sequence of matrices is generated.
- (2)
- According to the index, the elements of the original images are arranged in a zigzag formation and sequentially insert them into the encrypted images.
2.4. Secure Hash Algorithm (SHA-3)
2.5. Chaotic System
2.6. Joint Watermarking and Encryption
3. The Proposed Scheme
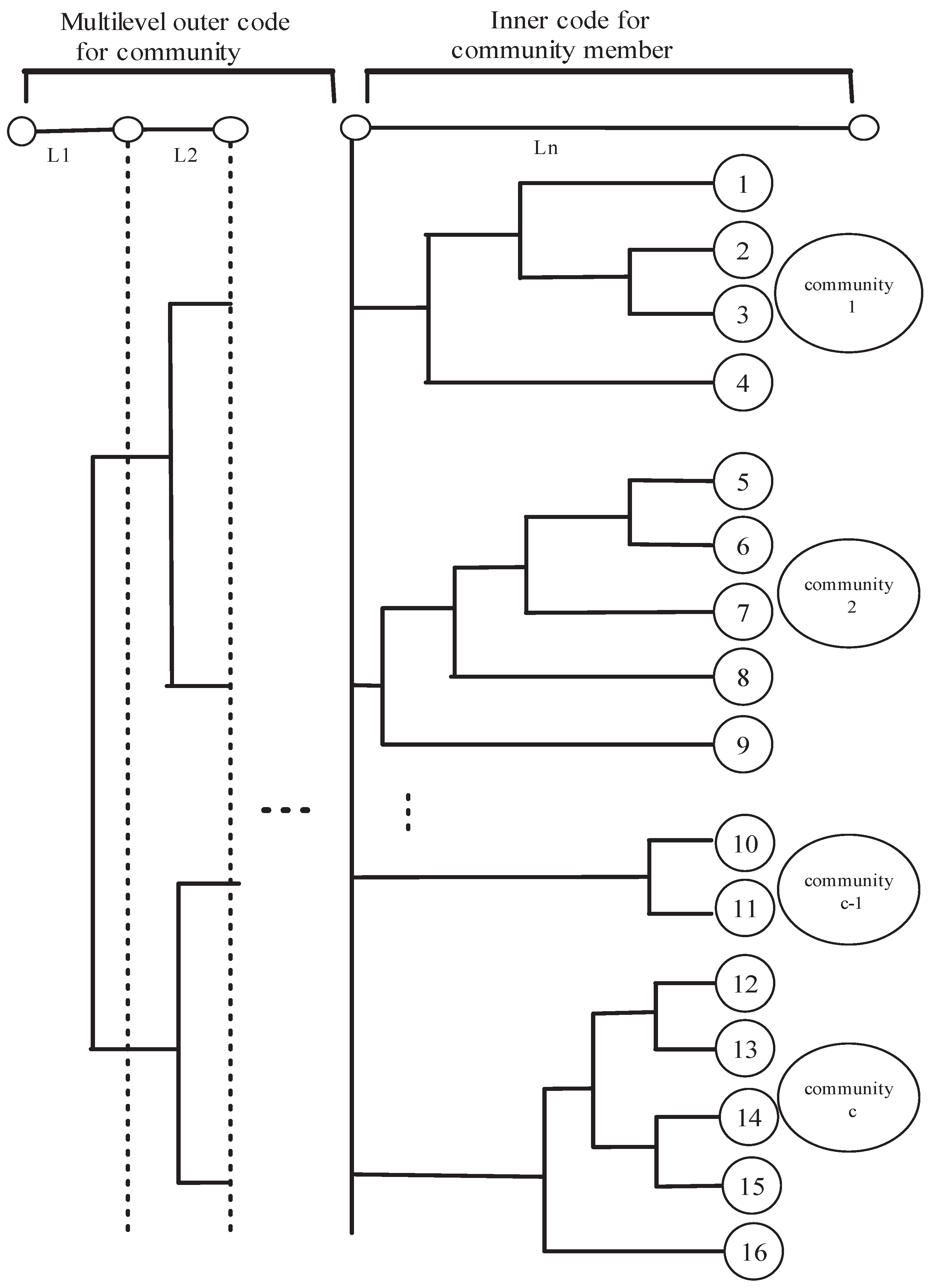
3.1. Coding Using Social Network Analysis
3.2. The Joint Watermarking and Encryption Scheme
3.2.1. Fingerprint Embedding and Traitor Tracing
3.2.2. Encryption and Decryption Algorithm
4. Performance Test and Comparative Analysis
4.1. Fingerprint Imperceptibility
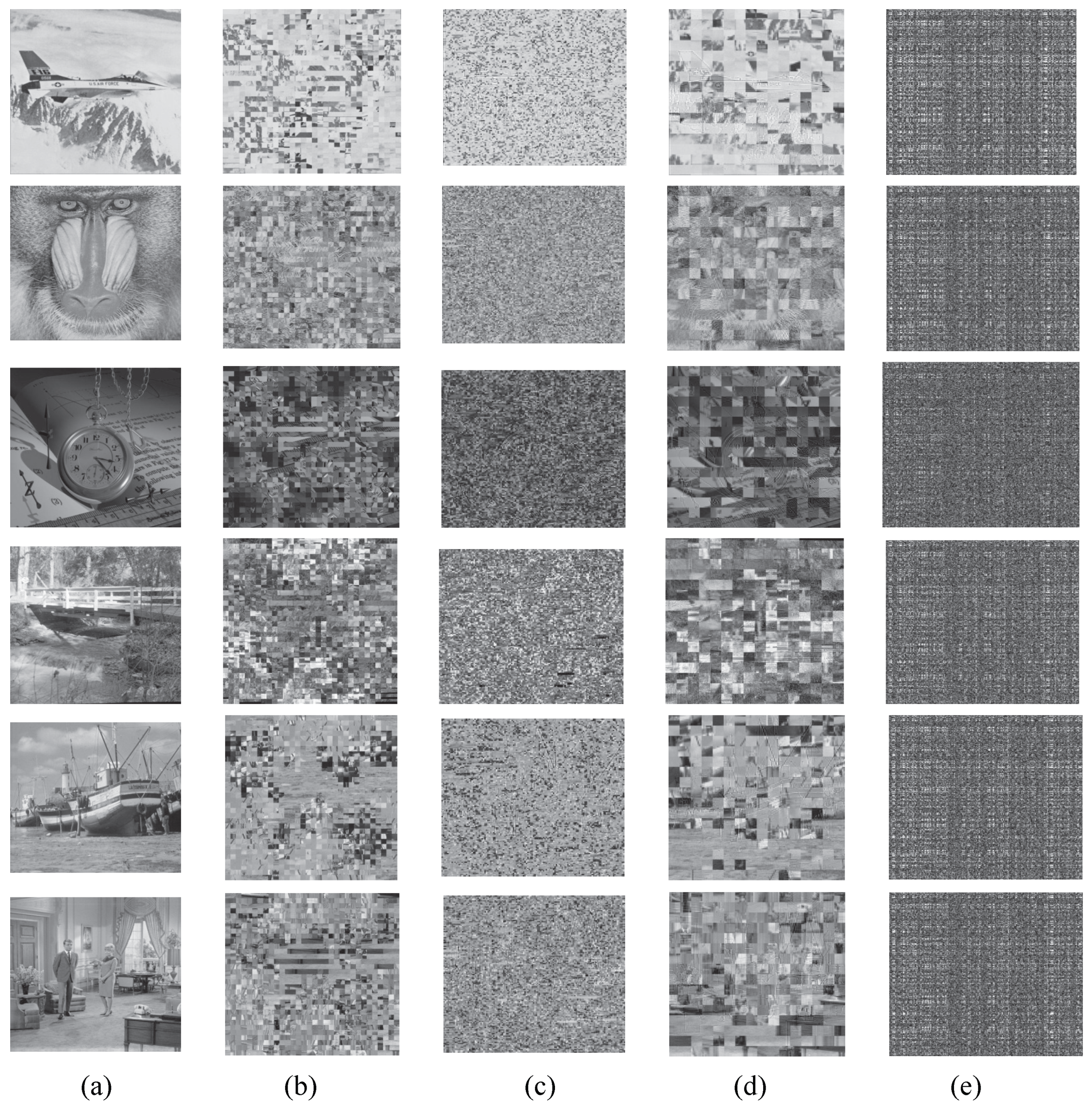
4.2. Perceptual Effect of Encrypted Images
4.3. Exhaustive Attack Discussion
4.4. Statistical Attack Discussion
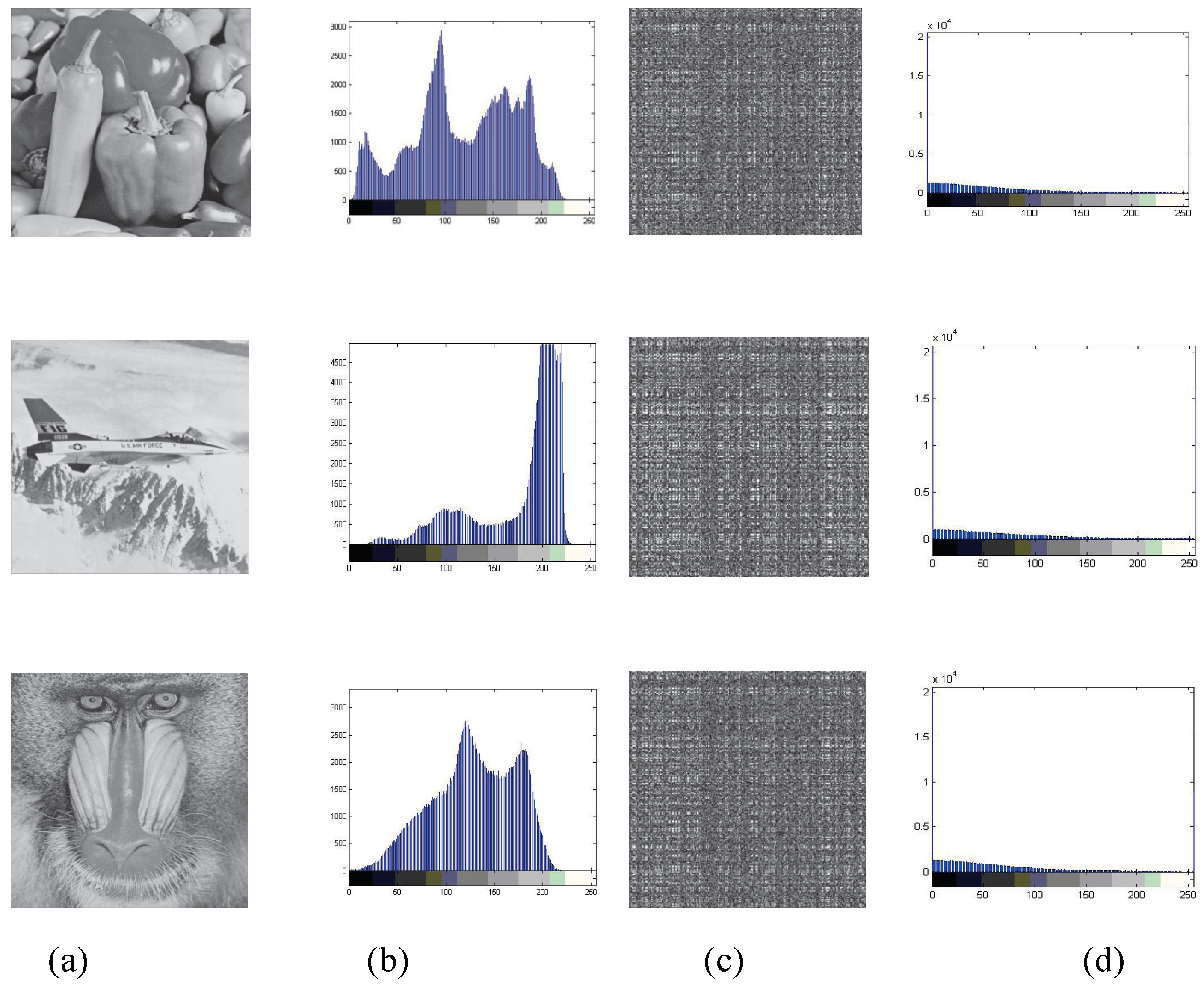
4.4.1. Histogram Attack Discussion
4.4.2. Correlation Analysis
4.5. Encryption Process Discussion
4.6. Encryption and Watermarking Performance Discussion
4.6.1. Comparative Analysis
4.6.2. Algorithm Comparison
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| GoL | Game of Life |
| SVD | Singular value decomposition |
| DWT | Discrete wavelet transform |
| JWE | Joint watermarking and encryption |
| SHA | Secure hash algorithm |
| DPV | Discrete point vector |
| HNN | Hopfield neural network |
| QIM | Quantization index modulation |
| FRFT | Fractional Fourier transform |
| TSH | Tree structure Haar |
| SNA | Social network analysis |
| NC | Normalized correlation |
References
- Chai, X.; Cao, G.; Gan, Z.; Zhang, Y.; Ma, Y.; He, X. TPE-AP: Thumbnail-Preserving Encryption Based on Adjustable Precision for JPEG Images. IEEE Internet Things J. 2024, 11, 37021–37031. [Google Scholar] [CrossRef]
- Zhang, Y.; Tong, Y.; Li, C.; Peng, Y.; Tan, F. Hybrid diffusion-based visual image encryption for secure cloud storage. Nonlinear Dyn. 2024. early access. [Google Scholar] [CrossRef]
- Yang, J.; Liu, X. Enhancing secure storage and sharing of multi-image in cloud environments using a novel chaotic map. Expert Syst. Appl. 2025, 264, 125897. [Google Scholar] [CrossRef]
- Ping, P.; Wei, P.; Fu, D.; Guo, B.; Bloh, O.T.; Xu, F. IMIH: Imperceptible Medical Image Hiding for Secure Healthcare. IEEE Trans. Dependable Secur. Comput. 2024, 21, 4652–4667. [Google Scholar] [CrossRef]
- Liang, J.; Liu, Y.; Gao, L.; Zhang, Z.; Liu, X. ISWP: Novel high-fidelity adversarial examples generated by incorporating invisible and secure watermark perturbations. Appl. Intell. 2025, 55, 40. [Google Scholar] [CrossRef]
- Wei, C.; Wang, Y.; Gao, K.; Shao, S.; Li, Y.; Wang, Z.; Qin, Z. PointNCBW: Toward Dataset Ownership Verification for Point Clouds via Negative Clean-Label Backdoor Watermark. IEEE Trans. Inf. Forensics Secur. 2025, 20, 191–206. [Google Scholar] [CrossRef]
- Deng, Q.; Wang, C.; Sun, Y.; Deng, Z.; Yang, G. Memristive Tabu Learning Neuron Generated Multi-Wing Attractor with FPGA Implementation and Application in Encryption. IEEE Trans. Circuits Syst. I Regul. Pap. 2024, 72, 300–311. [Google Scholar] [CrossRef]
- Li, J.; Wang, C.; Deng, Q. Symmetric multi-double-scroll attractors in Hopfield neural network under pulse controlled memristor. Nonlinear Dyn. 2024, 112, 14463–14477. [Google Scholar] [CrossRef]
- Wu, W.; Zhou, J. Constructing new high-order polynomial chaotic maps and application in pseudorandom number generator. Phys. Scr. 2024, 99, 035238. [Google Scholar] [CrossRef]
- Hua, Z.; Yao, J.; Zhang, Y.; Bao, H.; Yi, S. Two-Dimensional Coupled Complex Chaotic Map. IEEE Trans. Ind. Inform. 2024, 21, 85–95. [Google Scholar] [CrossRef]
- Liu, X.; Yang, J. A novel multi-layer image encryption algorithm based on 2D drop-wave function. Nonlinear Dyn. 2025, 113, 1775–1797. [Google Scholar] [CrossRef]
- Meng, B.; Yuan, X.; Zhang, Q.; Lam, C.T.; Huang, G. Encryption-then-embedding-based hybrid data hiding scheme for medical images. J. King Saud Univ.-Comput. Inf. Sci. 2024, 36, 101932. [Google Scholar] [CrossRef]
- Chai, X.; Tang, Z.; Gan, Z.; Lu, Y.; Wang, B.; Zhang, Y. SE-NDEND: A novel symmetric watermarking framework with neural network-based chaotic encryption for Internet of Medical Things. Biomed. Signal Process. Control 2024, 90, 105877. [Google Scholar] [CrossRef]
- Nawaz, S.A.; Li, J.; Bhatti, U.A.; Shoukat, M.U.; Li, D.; Raza, M.A. Hybrid watermarking algorithm for medical images based on digital transformation and MobileNetV2. Inf. Sci. 2024, 653, 119810. [Google Scholar] [CrossRef]
- Wang, M.; Teng, L.; Zhou, W.; Yan, X.; Xia, Z.; Zhou, S. A new 2D cross hyperchaotic Sine-modulation-Logistic map and its application in bit-level image encryption. Expert Syst. Appl. 2025, 261, 125328. [Google Scholar] [CrossRef]
- Toktas, F.; Erkan, U.; Yetgin, Z. Cross-channel color image encryption through 2D hyperchaotic hybrid map of optimization test functions. Expert Syst. Appl. 2024, 249, 123583. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, J.; Chen, Y.; Qin, Z.; Zhang, Y.; Ahmad, M.; Wozniakd, M. Exploiting robust quadratic polynomial hyperchaotic map and pixel fusion strategy for efficient image encryption. Expert Syst. Appl. 2024, 246, 123190. [Google Scholar] [CrossRef]
- Feng, W.; Wang, Q.; Liu, H.; Ren, Y.; Zhang, J.; Zhang, S.; Qian, K.; Wen, H. Exploiting Newly Designed Fractional-Order 3D Lorenz Chaotic System and 2D Discrete Polynomial Hyper-Chaotic Map for High-Performance Multi-Image Encryption. Fractal Fract. 2023, 7, 887. [Google Scholar] [CrossRef]
- Feng, W.; Yang, J.; Zhao, X.; Qin, Z.; Zhang, J.; Zhu, Z.; Wen, H.; Qian, K. A Novel Multi-Channel Image Encryption Algorithm Leveraging Pixel Reorganization and Hyperchaotic Maps. Mathematics 2024, 12, 3917. [Google Scholar] [CrossRef]
- Wang, S.; Pan, J.; Cui, Y.; Chen, Z.; Zhan, W. Fast Color Image Encryption Algorithm Based on DNA Coding and Multi-Chaotic Systems. Mathematics 2024, 12, 3297. [Google Scholar] [CrossRef]
- Teng, L.; Du, L.; Leng, Z.; Wang, X. Chaotic image encryption based on partial face recognition and DNA diffusion. Appl. Intell. 2024, 54, 10360–10373. [Google Scholar] [CrossRef]
- Jiang, D.; Ahmad, J.; Suo, Z.; Alsulami, M.M.; Ghadi, Y.Y.; Boulila, W. ML-FAS: Multi-Level Face Anonymization Scheme and Its Application to E-Commerce Systems. IEEE Trans. Consum. Electron. 2024, 70, 5090–5100. [Google Scholar] [CrossRef]
- Yan, X.; Hu, Q.; Teng, L.; Su, Y. Unmanned ship image encryption method based on a new four-wing three-dimensional chaotic system and compressed sensing. Chaos Solitons Fractals 2024, 185, 115146. [Google Scholar] [CrossRef]
- Rostami, M.J.; Shahba, A.; Saryazdi, S.; Nezamabadi-pour, H. A novel parallel image encryption with chaotic windows based on logistic map. Comput. Electr. Eng. 2017, 62, 384–400. [Google Scholar] [CrossRef]
- Diaconu, A.V. Circular inter-intra pixels bit-level permutation and chaos-based image encryption. Inf. Sci. 2016, 355, 314–327. [Google Scholar] [CrossRef]
- Wei, D.; Deng, Y. Redistributed invariant redundant fractional wavelet transform and its application in watermarking algorithm. Expert Syst. Appl. 2025, 262, 125707. [Google Scholar] [CrossRef]
- Thanki, R.; Kothari, A. Multi-level security of medical images based on encryption and watermarking for telemedicine applications. Multimed. Tools Appl. 2020, 80, 4307–4325. [Google Scholar] [CrossRef]
- Wang, L.; Zhou, N.; Sun, B.; Cao, Y.; Mou, J. Novel self-embedding holographic watermarking image encryption protection scheme. Chin. Phys. B 2024, 33, 050501. [Google Scholar] [CrossRef]
- Wang, L.; Banerjee, S.; Cao, Y.; Mou, J.; Sun, B. A new self-embedding digital watermarking encryption scheme. Nonlinear Dyn. 2024, 112, 8637–8652. [Google Scholar] [CrossRef]
- Yan, F.; Wang, Z.; Hirota, K. Dual medical image watermarking using SRU-enhanced network and EICC chaotic map. Complex Intell. Syst. 2025, 11, 101. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. An improved DWT-SVD domain watermarking for medical information security. Comput. Commun. 2020, 152, 72–80. [Google Scholar] [CrossRef]
- Ye, C.; Chen, C. Secure medical image sharing for smart healthcare system based on cellular neural network. Complex Intell. Syst. 2023, 9, 1653–1670. [Google Scholar] [CrossRef]
- Lin, Y.; Xie, Z.; Chen, T.; Cheng, X.; Wen, H. Image privacy protection scheme based on high-quality reconstruction DCT compression and nonlinear dynamics. Expert Syst. Appl. 2024, 257, 124891. [Google Scholar] [CrossRef]
- Liu, R.; Tan, T. An SVD-based watermarking scheme for protecting rightful ownership. IEEE Trans. Multimed. 2002, 4, 121–128. [Google Scholar] [CrossRef]
- Egiazarian, K.; Astola, J. Tree-structured Haar transforms. J. Math. Imaging Vis. 2002, 16, 269–279. [Google Scholar] [CrossRef]
- Wolfram, S. A New Kind of Science; Wolfram Media: Champaign, IL, USA, 2002. [Google Scholar]
- Jungk, B.; Stoettinger, M. Serialized lightweight SHA-3 FPGA implementations. Micorprocess. Microsyst. 2019, 71, 102857. [Google Scholar] [CrossRef]
- Wang, M.; Song, X.; Liu, S.; Zhao, X.; Zhou, N. A novel 2D Log-Logistic-Sine chaotic map for image encryption. Nonlinear Dyn. 2025, 113, 2867–2896. [Google Scholar] [CrossRef]
- Hopfield, J.J. Neural networks and physical systems with emergent collective computational abilities. Proc. Natl. Acad. Sci. USA 1982, 79, 2554–2558. [Google Scholar] [CrossRef]
- Peng, Y.; Fu, C.; Cao, G.; Song, W.; Chen, J.; Sham, C.W. JPEG-compatible Joint Image Compression and Encryption Algorithm with File Size Preservation. ACM Trans. Multimed. Comput. Commun. Appl. 2024, 20, 1–20. [Google Scholar] [CrossRef]
- Xu, S.; Horng, J.H.; Chang, C.C.; Chang, C.C. Reversible Data Hiding in Encrypted JPEG Images with Polynomial Secret Sharing for IoT Security. IEEE Internet Things J. 2025, 12, 1098–1108. [Google Scholar] [CrossRef]
- Yasui, T.; Kuribayashi, M.; Funabiki, N.; Echizen, I. Near-Optimal Detection for Binary Tardos Code by Estimating Collusion Strategy. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2069–2080. [Google Scholar] [CrossRef]
- Mao, J.; Tang, H.; Lyu, S.; Zhou, Z.; Cao, X. Content-Aware Quantization Index Modulation: Leveraging Data Statistics for Enhanced Image Watermarking. IEEE Trans. Inf. Forensics Secur. 2024, 19, 1935–1947. [Google Scholar] [CrossRef]
- Al-Haj, A.; Abdel-Nabi, H. An efficient watermarking algorithm for medical images. Multimed. Tools Appl. 2021, 80, 26021–26047. [Google Scholar] [CrossRef]
- Bouslimi, D.; Coatrieux, G.; Cozic, M.; Roux, C. A Joint Encryption/Watermarking System for Verifying the Reliability of Medical Images. IEEE Trans. Inf. Technol. Biomed. 2012, 16, 891–899. [Google Scholar] [CrossRef]
- Thakur, S.; Singh, A.K.; Ghrera, S.P.; Elhoseny, M. Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimed. Tools Appl. 2019, 78, 3457–3470. [Google Scholar] [CrossRef]
- Liu, S.; Yu, N.; Xi, S.; Ji, X.; Yuan, H.; Wang, X.; Zhu, Z. Hybrid watermarking and encryption techniques for securing three-dimensional information. Phys. Scr. 2024, 99, 055543. [Google Scholar] [CrossRef]





| Image | Proposed | [24] | [25] | [32] | ||||
|---|---|---|---|---|---|---|---|---|
| Entropy | Time (s) | Entropy | Time (s) | Entropy | Time (s) | Entropy | Time (s) | |
| Plane | 6.5628 | 0.7694 | 7.999724 | 44.3256 | 7.999715 | 168.352 | 5.3678 | 0.8935 |
| Baboon | 6.6258 | 0.7928 | 7.999745 | 45.3287 | 7.999716 | 176.239 | 5.2336 | 0.8637 |
| Watch | 6.1246 | 0.7593 | 7.999769 | 43.2687 | 7.999782 | 168.325 | 5.4263 | 0.8691 |
| Peppers | 6.3926 | 0.7789 | 7.999769 | 46.2189 | 7.999763 | 158.326 | 5.1256 | 0.8536 |
| Attack | Plane | Baboon | Watch | |||
|---|---|---|---|---|---|---|
| Proposed | [31] | Proposed | [31] | Proposed | [31] | |
| No attack | 0.9996 | 0.9989 | 0.9962 | 0.9908 | 0.9962 | 0.9993 |
| Upper left corner cropping (1/16) | 0.9345 | 0.5523 | 0.8235 | 0.2912 | 0.9796 | 0.8965 |
| Center cropping (1/16) | 0.9652 | 0.3158 | 0.8291 | 0.1891 | 0.9548 | −0.0217 |
| Around cropping (1/8) | 0.6613 | −0.1561 | 0.8039 | 0.1726 | 0.9537 | −0.3612 |
| Salt and pepper (0.005) | 0.8435 | 0.8028 | 0.8863 | 0.8327 | 0.8996 | 0.8938 |
| Salt and pepper (0.01) | 0.7929 | 0.7102 | 0.8192 | 0.6958 | 0.8765 | 0.7821 |
| Salt and pepper (0.02) | 0.7682 | 0.5123 | 0.8186 | 0.6128 | 0.8798 | 0.5587 |
| Gaussian noise (0.001) | 0.7956 | 0.6127 | 0.8278 | 0.5736 | 0.8537 | 0.4367 |
| Gaussian noise (0.005) | 0.7893 | 0.6539 | 0.8293 | 0.6312 | 0.8856 | 0.5129 |
| Gaussian noise (0.01) | 0.7639 | 0.6678 | 0.8369 | 0.6218 | 0.8678 | 0.5357 |
| Ours | [45] | [44] | [46] | [15] | [47] | [14] | [31] | |
|---|---|---|---|---|---|---|---|---|
| Watermarking | Yes | Yes | Yes | Yes | No | Yes | Yes | Yes |
| Selective encryption | Yes | No | No | No | No | No | No | No |
| Tracing | Yes | Yes | No | Yes | No | Yes | Yes | Yes |
| Scalability | Yes | No | No | No | No | No | No | No |
| Encryption domain | DWT/DCT | Spatial | Spatial | Spatial | Spatial | No | No | Spatial |
| Encryption scheme | Chaos | RC4 | RC4 | Chaos | Chaos | No | No | Chaos |
| Watermark domain | DWT | Spatial | Spatial | DWT/DCT | No | FRFT | DWT/DCT | DWT |
| Watermark detection | Encrypted | Plaintext | Plaintext | Plaintext | No | Plaintext | Plaintext | Plaintext |
| Controllable security level | Yes | No | No | No | No | No | No | No |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ye, C.; Tan, S.; Wang, J.; Shi, L.; Zuo, Q.; Feng, W. Social Image Security with Encryption and Watermarking in Hybrid Domains. Entropy 2025, 27, 276. https://doi.org/10.3390/e27030276
Ye C, Tan S, Wang J, Shi L, Zuo Q, Feng W. Social Image Security with Encryption and Watermarking in Hybrid Domains. Entropy. 2025; 27(3):276. https://doi.org/10.3390/e27030276
Chicago/Turabian StyleYe, Conghuan, Shenglong Tan, Jun Wang, Li Shi, Qiankun Zuo, and Wei Feng. 2025. "Social Image Security with Encryption and Watermarking in Hybrid Domains" Entropy 27, no. 3: 276. https://doi.org/10.3390/e27030276
APA StyleYe, C., Tan, S., Wang, J., Shi, L., Zuo, Q., & Feng, W. (2025). Social Image Security with Encryption and Watermarking in Hybrid Domains. Entropy, 27(3), 276. https://doi.org/10.3390/e27030276







