1. Introduction
A block cipher is a basic building block in modern cryptography, usually modeled as a random permutation on fixed-length inputs. In practice, messages are often much longer than a single block and may vary in length, which requires the use of block cipher modes of operation to extend encryption to arbitrary-length inputs. Modes of operation are generally divided into three categories: encryption modes, authentication modes, and authenticated encryption modes. The earliest encryption modes, such as ECB, CBC, OFB, and CFB, provided confidentiality only. To ensure integrity, authentication modes such as CBC-MAC were developed, and later integrated designs such as CCM, GCM, and OCB were proposed to achieve both confidentiality and integrity.
The progress of quantum algorithms has posed serious challenges to these modes. When adversaries are allowed quantum query access to the underlying primitive, algorithms such as Grover’s search [
1] and Simon’s algorithm [
2] can be applied to mount attacks. Under this setting, reduced-round Feistel and Lai–Massey structures, the Even–Mansour cipher, LRW [
3,
4,
5,
6,
7], authentication modes including CBC-MAC, PMAC, and GMAC [
7], and authenticated encryption modes such as OCB and GCM [
7,
8,
9,
10] have been shown to be insecure.
Against this background, the quantum security of encryption modes has become a central research topic. The natural adaptation of the classical indistinguishability under chosen-plaintext attack (IND-CPA) model to the quantum setting is the IND-qCPA model [
11], where challenge queries remain classical, encryption queries may be quantum, and the adversary’s distinguishing advantage quantifies security. Because encryption modes aim only at confidentiality, proving IND-qCPA security suffices in the quantum setting. It is important to note that existing quantum security models are probabilistic, in which a random value
r is included during the encryption process. Unlike plaintexts and ciphertexts, which may be in quantum superposition, the random value
r is always treated as a classical number.
Based on the nature of the random value r, encryption schemes can be categorized into IV-based encryption schemes and nonce-based encryption schemes. Among these, an initialization vector is required to be random, whereas a nonce N is required only to be arbitrarily chosen but non-repeating. Compared with random IVs, nonces are easier to generate, avoid reliance on high-quality randomness, and better match practical deployment requirements in modern cryptographic protocols.
The quantum security of encryption schemes varies depending on the type of random value employed. In 2016, Vivekanand et al. [
12] demonstrated that encryption modes such as CBC, CFB, OFB, and CTR achieve IND-qCPA security when a random IV is used. In 2021, Bhaumik et al. [
8] proposed a new design called QCB, based on OCB, and proved that QCB satisfies IND-qCPA security under the non-adaptive nonce setting. Here, a non-adaptive nonce refers to one that may be arbitrarily chosen but must be selected entirely in advance prior to any encryption queries. In 2025, Lang et al. [
13] provided the first formal definition of IND-qCPA security in the adaptive nonce model, although no concrete instantiation has been proposed to date. In addition, there are also studies on the quantum security of block ciphers and their modes of operation [
14,
15,
16,
17].
We refer to IV-based IND-qCPA as R-IND-qCPA and nonce-based IND-qCPA as N-IND-qCPA. Although CBC, CFB, OFB, and CTR achieve IND-qCPA security when a random
is used (that is, they are R-IND-qCPA secure),
Section 3 demonstrates that replacing the
with a nonce
N not only fails to provide IND-qCPA security but also undermines even IND-CPA security. Enhancing encryption schemes to achieve N-IND-qCPA security constitutes a primary focus of this work.
The main results in the paper are as follows (
Table 1):
We present a general transformation that converts any R-IND-qCPA secure encryption scheme into an N-IND-qCPA secure scheme.
We propose enhanced variants of CBC, CFB, OFB, and CTR, referred to as CBC2, CFB2, OFB2, and CTR2, and provide formal proofs of their security under the N-IND-qCPA definition.
We further show that nonce-based stream cipher encryption inherently satisfies N-IND-qCPA security.
The structure of this paper is organized as follows:
Section 2 introduces definitions and notation;
Section 3 presents N-IND-CPA attacks against CBC, CFB, OFB, and CTR;
Section 4 provides the N-IND-qCPA security proof for CBC2;
Section 5 discusses improvements and proofs for other encryption schemes; and
Section 6 offers concluding remarks.
2. Preliminaries
2.1. Notations
Block Cipher. A block cipher is a map with key space and message space such that for every key , is a permutation on . Let denote the map .
Let denote selecting an element x from the set uniformly at random. Let be a set of all permutations on . Let be a random permutation on . A block cipher keyed by K is a function . We call the input and output of as plaintext and ciphertext, respectively. Let be the set of all functions from to . We write as .
IV-Based Encryption Scheme. Encryption schemes are typically defined as either probabilistic or stateful. In the context of symmetric cryptography, the randomness or state involved in the encryption process is usually represented explicitly by an initialization vector (IV), meaning that both encryption and decryption can be formalized as deterministic algorithms. The following provides the syntax definition of an IV-based encryption scheme. An IV-based encryption scheme is a pair of algorithms , where and are deterministic functions with key space, IV space , plaintext space , and ciphertext space . We require that for any and and . Note that here, for a probabilistic encryption scheme is randomly selected from .
Nonce-Based Encryption Scheme. If the only requirement on the initialization vector (IV) is that it must not repeat, then even allowing the adversary to choose the IV is acceptable. In this case, the IV is referred to as a nonce, and the corresponding construction is called a nonce-based encryption scheme. Because the syntax of IV-based and nonce-based encryption schemes is identical, the latter simply relaxes the requirements on how the IV is generated. This relaxation greatly facilitates the secure deployment of symmetric encryption, as producing a random IV would otherwise require the additional implementation of a secure random number generator. To highlight the distinction, in the syntax definition the IV space is usually replaced by a nonce space .
2.2. Security Definitions
Let be an adversary. Let denote an algorithm that performs queries on the oracle and produces the bit of b. In the context of a (keyed) function f, for a classical query X, the response is the value . In contrast, a quantum query is given as a quantum superposition state , and the response is given by .
For two oracles
and
, the classical and quantum distinguishing advantage of
is defined respectively as follows:
where we use · to denote a classical query and ⊙ to denote a quantum query.
Definition 1 (PRF/qPRF).
A (quantum-secure) pseudorandom function ((q)PRF) is an efficiently computable function family for all (quantum) algorithms ,where g is a random function from to and where we replace the ∗ symbol by · to denote a classical query or ⊙ to denote a quantum query). Definition 2 (PRF/qPRF/PRP/qPRP Advantages).
Let be a function. Let be a block cipher. Let be a random function. Let be a random permutation. We assume that all keys are random. The PRF/qPRF/PRP/qPRP advantages are defined as follows: Definition 3 (Secure Stream Cipher).
A secure stream cipher is an efficiently computable function that takes a key k and nonce N, then outputs a keystream of length L. For all probabilistic polynomial-time adversaries , the following advantage is negligible:where g is a random function from to . In the following, we present the definitions of R-IND-CPA and N-IND-CPA.
Definition 4 (R-IND-CPA). For an encryption scheme and an adversary , we define the advantage of indistinguishability under a chosen plaintext attack in the random-IV setting (R-IND-CPA) using the following game:
Key Generation: The challenger picks a random key K and a random bit b.
Queries: is allowed to make two types of queries:
Challenge Queries: sends two plaintexts to which the challenger chooses randomness R and responds with .
Encryption Queries: For each such query of P, the challenger chooses randomness R and responds with .
Guess: produces a bit and wins if .
The R-IND-CPA advantage of an adversary is defined as Definition 5 (N-IND-CPA). For an encryption scheme and an adversary , we define the advantage of indistinguishability under a chosen plaintext attack in the nonce setting (N-IND-CPA) using the following game:
Key Generation: The challenger picks a random key K and a random bit b.
Queries: is allowed to make two types of queries:
Challenge Queries: sends a nonce N and two plaintexts , to which the challenger responds with .
Encryption Queries: For each such query of , the challenger chooses randomness R and responds with .
Guess: produces a bit , and wins if .
We stress that the nonce N in the above game never repeats. The N-IND-CPA advantage of an adversary is defined as In the following, we define R-IND-qCPA and N-IND-qCPA.
Definition 6 (R-IND-qCPA). For an encryption scheme and an adversary , we define the advantage of indistinguishability under a quantum chosen plaintext attack in the random-IV setting (R-IND-qCPA) using the following game:
Key Generation: The challenger picks a random key K and a random bit b.
Queries: is allowed to make two types of queries:
Challenge Queries: sends two classical messages , to which the challenger chooses classical randomness R and responds with classical .
Encryption Queries: For each such query of P, the challenger chooses classical randomness R and encrypts each plaintext in the quantum superposition using R as the randomness:
Guess: produces a bit and wins if .
The R-IND-qCPA advantage of an adversary is defined as Definition 7 (N-IND-qCPA). For an encryption scheme and an adversary , we define the advantage of indistinguishability under a quantum chosen plaintext attack in the nonce setting (N-IND-qCPA) using the following game:
Key Generation: The challenger picks a random key K and a random bit b.
Queries: is allowed to make two types of queries:
Challenge Queries: sends a classical nonce N and two classical messages , to which the challenger responds with classical .
Encryption Queries: For each such query of a classical nonce N and a plaintext in the quantum superposition, the challenger encrypts using the following transformation:
Guess: produces a bit and wins if .
The N-IND-qCPA advantage of an adversary is defined as 2.3. Encryption Modes
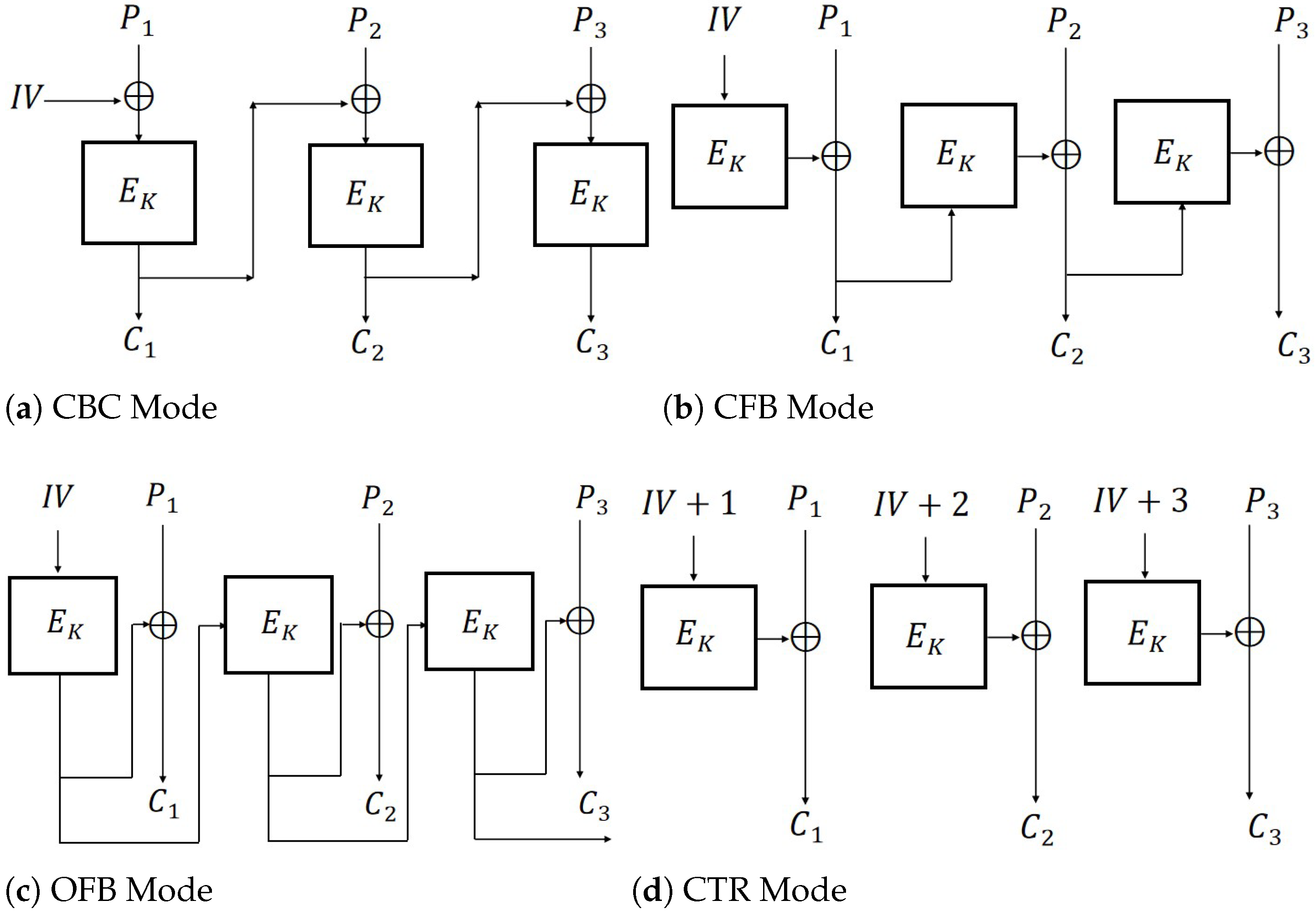
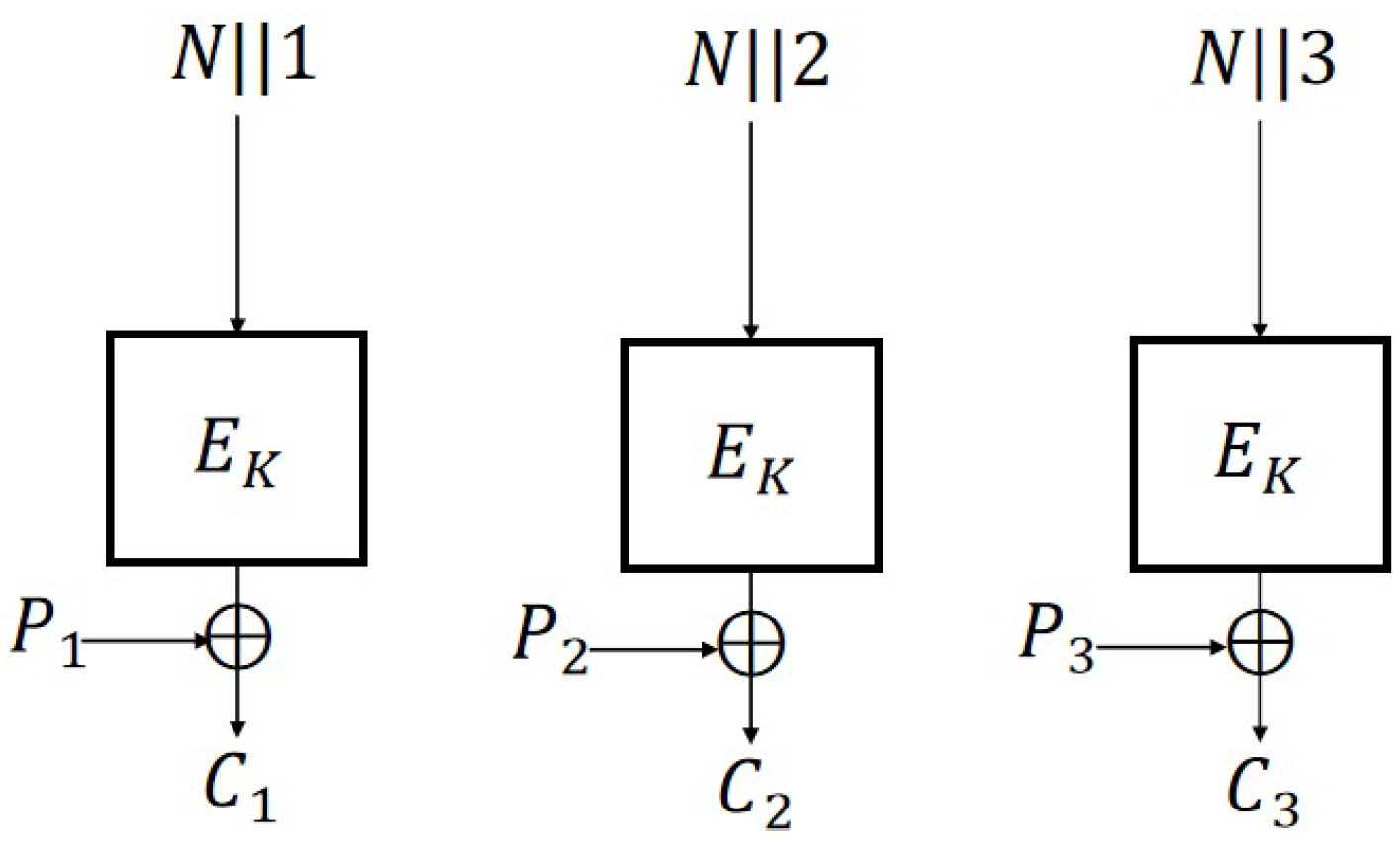
The encryption schemes CBC, CFB, OFB, and CTR (
Figure 1) are defined as follows:
Definition 8 (CBC Mode). Let and . For a given message , where is a block of the message, the symmetric encryption scheme is defined as follows:
Enc: and for . En.
Dec: For a given ciphertext and , for . De.
Definition 9 (CFB Mode). Let and . For a given message , where is a block of the message, the symmetric encryption scheme is defined as follows:
Enc: and for . En.
Dec: For a given ciphertext and , for . De.
Definition 10 (OFB Mode). Let and . For a given message , where is a block of the message, the symmetric encryption scheme is defined as follows:
Enc: , and for . En.
Dec: For a given ciphertext and , for . De.
Definition 11 (CTR Mode). Let and . For a given message , where is a block of the message, the symmetric encryption scheme is defined as follows:
Enc: and for . En.
Dec: For a given ciphertext and , for . De.
According to [
12], CBC, CFB, OFB and CTR are R-IND-qCPA secure, and therefore R-IND-CPA secure.
Theorem 1 (Theorem 3 and Theorem 4 in [
12]).
If the function E is a quantum secure PRF, then , , , and are R-IND-qCPA secure. However, our research will indicate that none of them are N-IND-CPA secure, and therefore not N-IND-qCPA secure.
3. N-IND-CPA/N-IND-qCPA Attacks with Nonce-Based Encryption Scheme
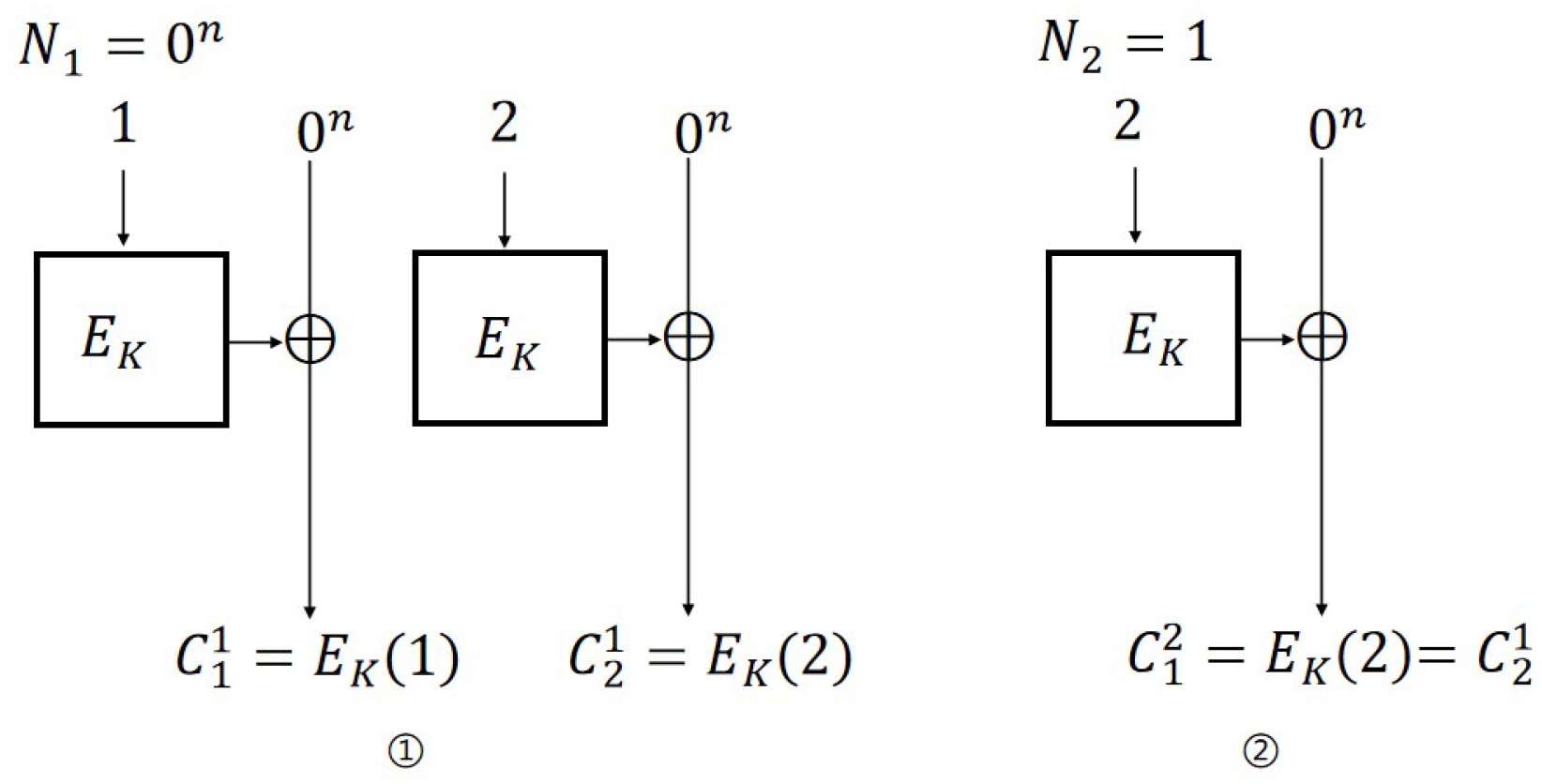
We noticed that , , , and only maintain the security of Theorem 1 when is a random . If we replace with nonce N (which can be selected but not repeated), then CBC, CFB, OFB, and CTR do not even maintain classical security; therefore, they are not N-IND-qCPA secure. For convenience, we define as the i-th block in the j-th query. It is easy to argue that the advantage of these attacks is 1.
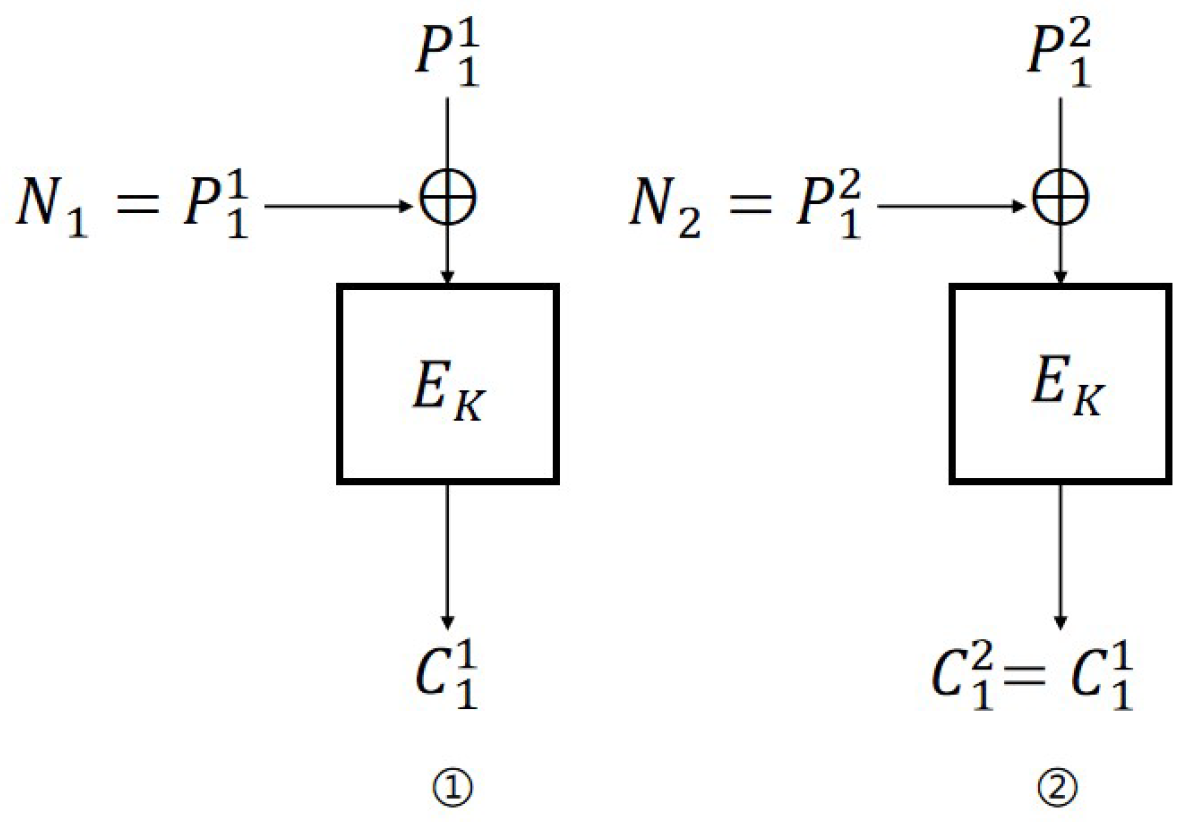
IND-CPA attack on CBC mode. The IND-CPA attack on CBC is similar to the attack in [
18]. The specific process (
Figure 2) is as follows:
Encryption query: Let ; then, .
Challenge query: Let , , , and ; then, if , otherwise .
For CBC mode, as long as , there will be ; thus, the probability of adversary ’s success is 1. The distinguishing advantages are: . Therefore, .
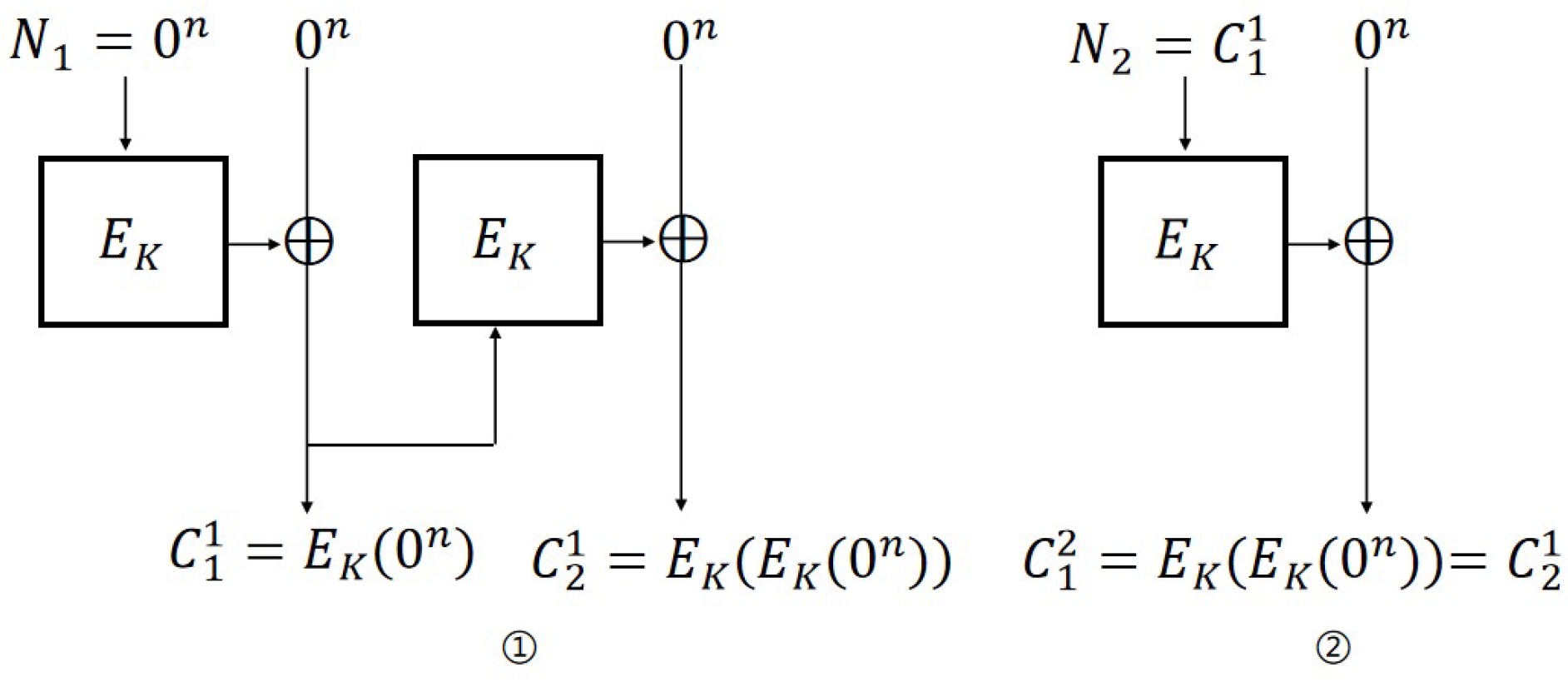
IND-CPA attack on CFB mode. The steps of the IND-CPA attack (
Figure 3) against the CFB scheme are as follows:
Encryption query: Let ; then, and .
Challenge query: Let , , , and ; then, if , otherwise .
For CFB mode, the probability of adversary ’s success is 1. The distinguishing advantages are: . Therefore, .
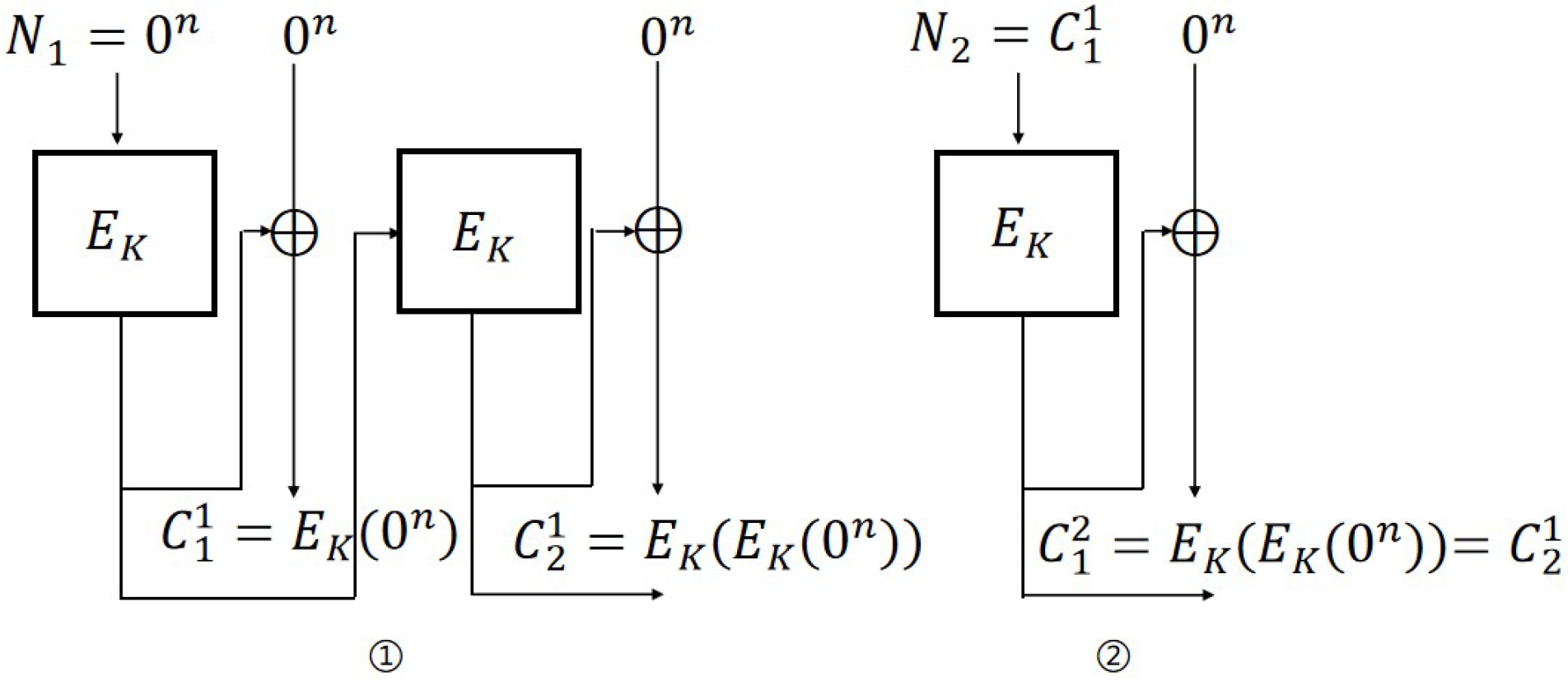
IND-CPA attack on OFB mode. The steps of the IND-CPA attack (
Figure 4) against the OFB scheme are as follows:
Encryption query: Let ; then, and .
Challenge query: Let , , and ; then, if , otherwise .
For OFB mode, the probability of adversary ’s success is 1. The distinguishing advantages are: . Therefore, .
IND-CPA attack on CTR mode. The steps of the IND-CPA attack (
Figure 5) against the CTR scheme are as follows:
Encryption query: Let ; then, and .
Challenge query: Let , , , and ; then, if , otherwise .
For CTR mode, the probability of adversary ’s success is 1. The distinguishing advantages are: . Therefore, .
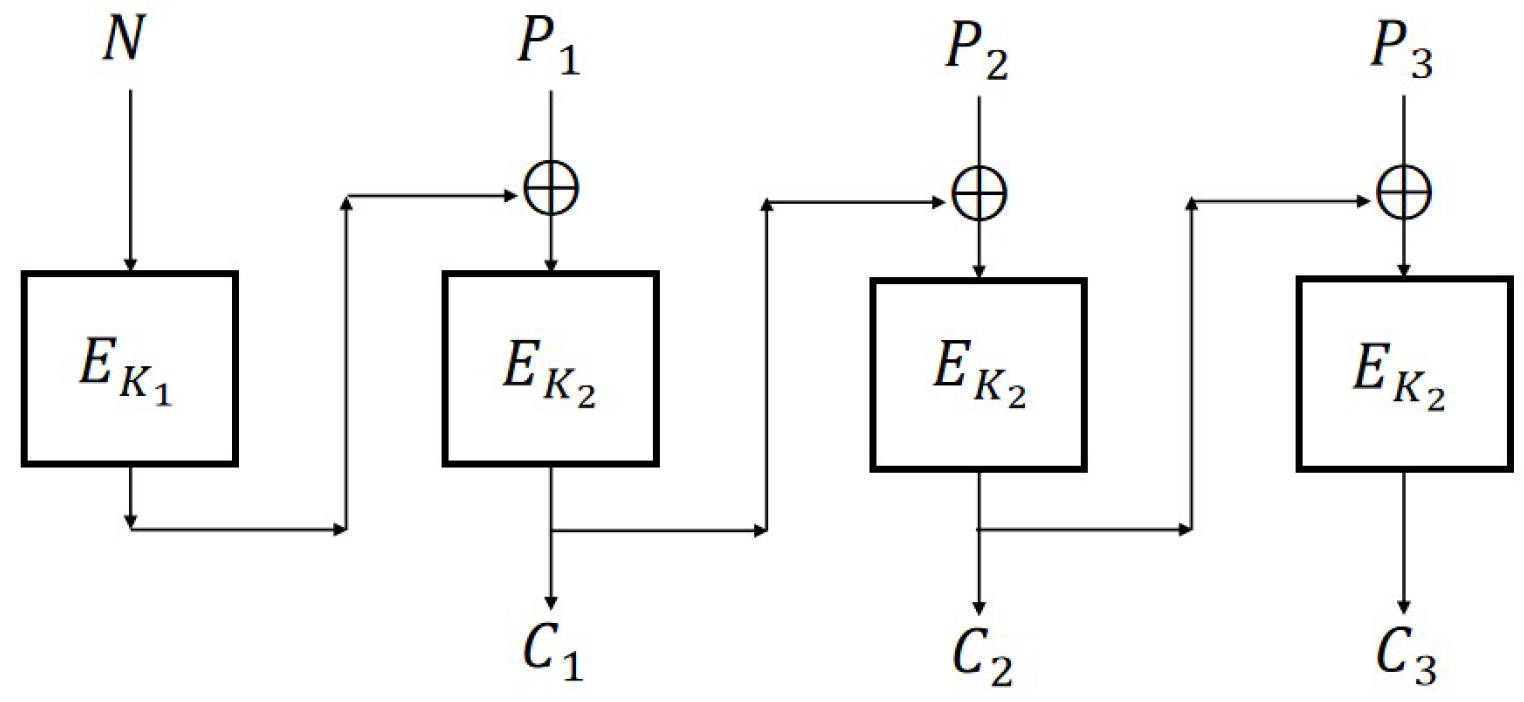
4. CBC2 Mode Is N-IND-qCPA Secure
From
Section 3, we know that CBC, CFB, OFB, and CTR are IND-qCPA secure when based on IV, while they are classical insecure when based on nonce. Based on CBC, Rogaway [
18] proposed an improved version of CBC2 (
Figure 6) which can achieve N-IND-CPA security by adding a key.
Definition 12 (CBC2 Scheme [
18]).
Let . For a given message and nonce N, where m is a polynomial in n, the symmetric encryption scheme is defined as follows:Enc: and for . En.
Dec: For a given ciphertext and N, , for . De.
For CBC2 scheme, the following theorem holds:
Theorem 2 (Theorem 1 in [
18]).
If the function E is a secure PRP, then is N-IND-CPA secure. Next, we will demonstrate that CBC2 also satisfies N-IND-qCPA security in quantum environments:
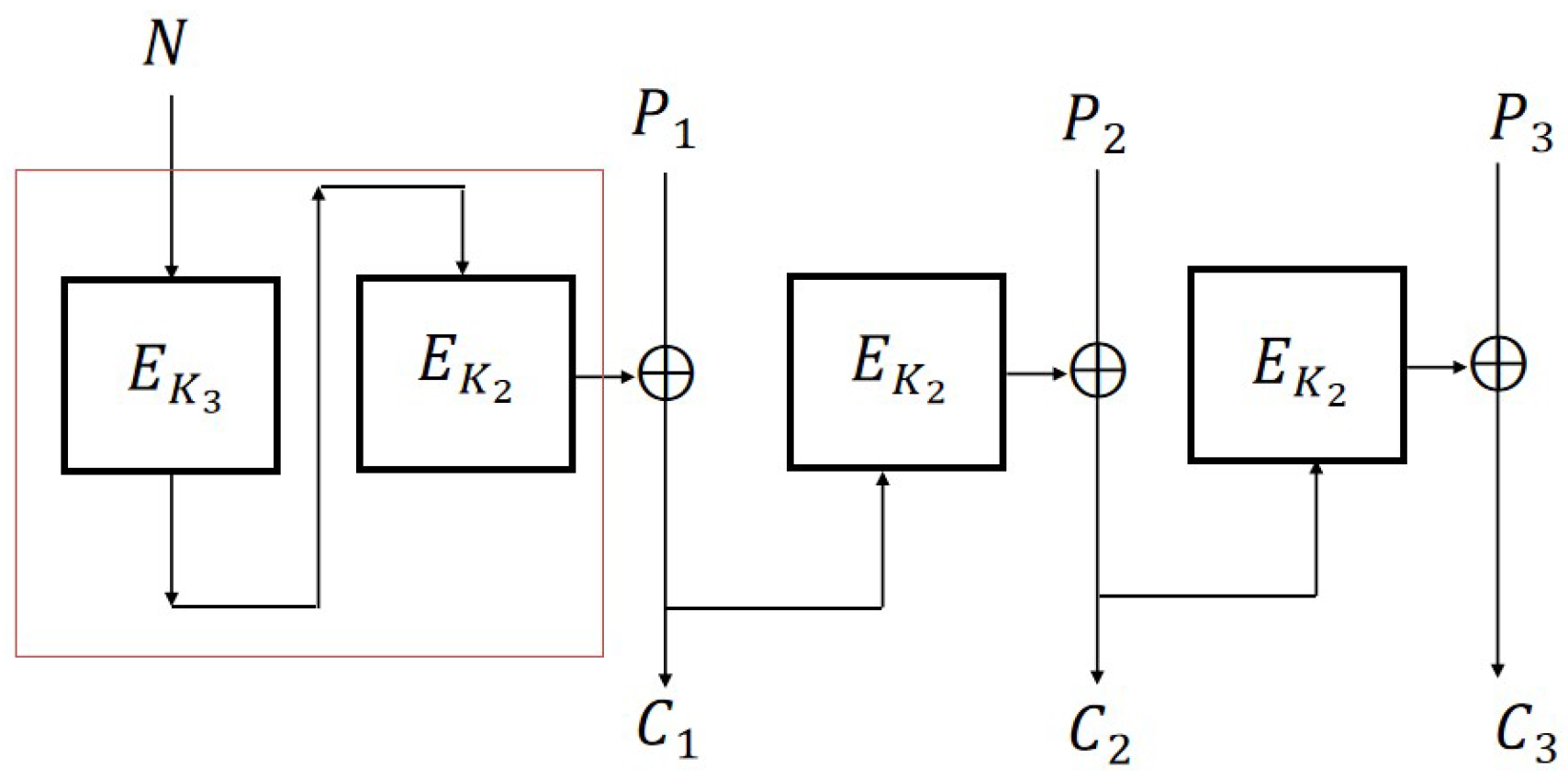
Theorem 3. If the function E is a quantum secure PRF, then is N-IND-qCPA secure.
From
Figure 7, it can be seen that in CBC2, the nonce
N is first encrypted using
and the output at this time is a random value, which can be essentially understood as transforming the adaptive nonce into a random IV through one encryption.
The following theorem ensures the validity of Theorem 3:
Theorem 4 (From R-IND-qCPA secure to N-IND-qCPA secure.). If the function E is a quantum secure PRF, , then encryption scheme is R-IND-qCPA secure with classical random . Let ; then, is N-IND-qCPA secure with a classical adaptive nonce N (N cannot be repeated).
Proof. We prove this proposition using the game-playing technique. (
Table 2).
: The adversary is given oracle access to the quantum oracle of .
: We change
E to ideal random function
f. Let
be adversary run to the quantum oracle of
or
. Let
be an adversary run to the classical oracle of
E or random function
f. Adversary
starts by running
and simulating the games
and
for it. In order to simulate the calls to
,
uses its own oracles from the PRF game. Note that
N is a classic number, and choosing a non-repeating
N is easy. Then, adversary
keeps track of all the sets appearing in the games
or
and enforces the corresponding game rules. In the end, adversary
returns the same bit that
returns. Let
make at most
q quantum queries, then let
make at most
q quantum queries. It holds that
: The adversary is given oracle access to the quantum oracle of
. Let
be an adversary run to the quantum oracle of
or
. Let
be an adversary run to the classical oracle of random function
f or random
.
uses its own oracles to simulate
. Then, adversary
starts by running
and simulating the games
and
for it. Adversary
keeps track of all the sets appearing in games
or
and enforces the corresponding game rules. In the end, adversary
returns the same bit that
returns. Let
make at most
q quantum queries, then let
make at most
q quantum queries. It holds that
□
5. N-IND-qCPA Secure Modification Modes
According to Theorem 4, CFB and OFB can be enhanced to N-IND-qCPA secure versions, which we denote as CFB2 and OFB2, respectively. Additionally, we define the improved CTR version, denoted as CTR2, which is N-IND-qCPA secure.
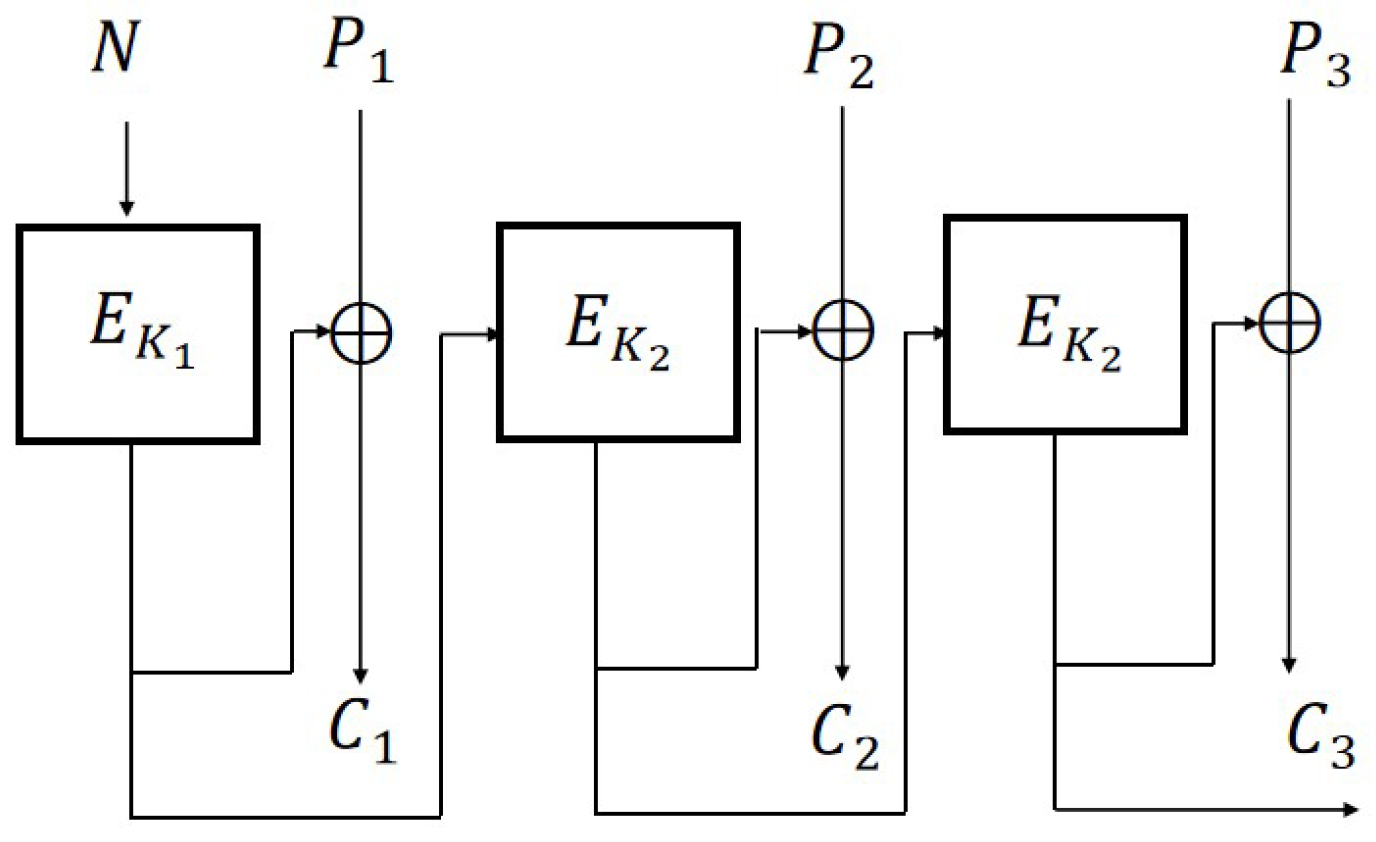
5.1. CFB2 Mode
We use different keys
and
to encrypt adaptive nonce
N and message
P, respectively. The improved version of CFB with N-IND-qCPA secure is shown in
Figure 8.
Let
. We can obtain a simplified version of CFB2 (
Figure 9) as follows:
Definition 13 (CFB2 Mode). Let . For a given message and nonce N, where m is a polynomial in n, the symmetric encryption scheme is defined as follows:
Enc: and for . En.
Dec: For a given ciphertext , for , . De.
Theorem 4 directly implies the following theorem.
Theorem 5. If the function E is a quantum secure PRF, then is N-IND-qCPA secure.
5.2. OFB2 Mode
Definition 14 (OFB2 Mode). Let . For a given message and nonce N, where m is a polynomial in n, the symmetric encryption scheme is defined as follows:
Enc: , for . Then for . En.
Dec: For a given ciphertext , , , for . De.
Theorem 4 directly implies the following theorem.
Theorem 6. If the function E is a quantum secure PRF, then is N-IND-qCPA secure.
5.3. CTR2 Mode
Because each message block of CTR2 has nonce
N as an input, directly referencing the conclusion of Theorem 4 would lead to a significant increase in the number of keys. Therefore, we consider making improvements in terms of the input. We divide the input into two parts,
N and
, and concatenate them directly. Correspondingly, the length of the block cipher
used at this time is
, and the lengths of
and
are also
. We define the N-IND-qCPA secure CTR2 scheme (
Figure 11) as follows:
Definition 15 (CTR2 Mode). Let . For a given message and nonce N, where m is a polynomial in n, the symmetric encryption scheme is defined as follows:
Enc: and for . En.
Dec: For a given ciphertext and , for . De.
For the CTR2 scheme, the following theorem holds:
Theorem 7. If the function E is a secure PRF, then is N-IND-qCPA secure.
Proof. We prove this proposition using the game-playing technique. (
Table 3).
: The adversary is given oracle access to the quantum oracle of .
: We change the
ith
E to ideal random function
f. Let
be an adversary run to the quantum oracle of
or
. Let
be an adversary run to the classical oracle of
E or random function
f. Adversary
starts by running
and simulating the games
and
for it. In order to simulate the calls to
,
uses its own oracles from PRF game. Note that
N is a classic number, and choosing a non-repeating
N is easy. Then, adversary
keeps track of all the sets appearing in the games
or
and enforces the corresponding game rules. In the end, adversary
returns the same bit that
returns. Let
make at most
q quantum queries, then let
make at most
q quantum queries. It holds that
For quantum states
P, game
returns the XOR value between a quantum message block and a classical random number. Therefore, game
returns a random quantum state. It holds that
□
We note that CTR2 is a stream cipher, and the conclusion and proof of Theorem 7 can be correspondingly extended to stream ciphers.
Theorem 8. [Nonce-based stream cipher encryption is N-IND-qCPA] Let G be a secure nonce-based stream cipher, ; then, is N-IND-qCPA secure.
Proof. The proof of this theorem is similar to Theorem 7. We prove this proposition using the game-playing technique. (
Table 4).
: The adversary is given oracle access to the quantum oracle of .
: We change
G to an ideal random function
f. Let
be an adversary run to the quantum oracle of
or
. Let
be an adversary run to the classical oracle of
G or random function
f. Similar to the previous proof, we have
: We change random function
f to random
. Let
be an adversary run to the quantum oracle of
or
, and let
For quantum states P, game returns the XOR value between a quantum message block and a classical random number. Therefore, game returns a random quantum state, and is N-IND-qCPA secure. □
Note that if OFB2 is also a stream cipher, the N-IND-qCPA security of (Theorem 6) can also be directly derived from Theorem 8.
6. Conclusions
The first contribution of this paper is a general conversion method from R-IND-qCPA to N-IND-qCPA security (Theorem 4). Specifically, if an encryption scheme is R-IND-qCPA secure with random , then the construction achieves N-IND-qCPA security with adaptive but non-repeating nonce N. Conceptually, this transformation encrypts the adaptive nonce once, thereby turning it into a random IV. As a direct application, CBC2 is proven N-IND-qCPA secure. We note, however, that this method generally incurs one additional encryption operation.
In contrast, for CFB and OFB, the situation is more favorable; since these schemes already involve encrypting the IV once, the additional operation can be merged. Thus, the modified variants CFB2 and OFB2 achieve N-IND-qCPA security without extra computational overhead, requiring only distinct keys for the initial block and the subsequent blocks.
Our final result establishes that nonce-based stream ciphers are inherently N-IND-qCPA secure (Theorem 8). If G is a secure nonce-based stream cipher, then satisfies N-IND-qCPA security. This can be understood as XORing quantum plaintext states with classical randomness. As a corollary, we derive the N-IND-qCPA secure version CTR2.
When compared to random IVs, nonces that are selectable yet non-repeating offer better alignment with practical deployment requirements. Future research should focus on extending these techniques to further enhance the N-IND-qCPA security of other IV-based encryption schemes. Meanwhile, integrating confidentiality with integrity to develop quantum-secure authenticated encryption schemes represents another important direction for future research.