Post-Quantum Secure Lightweight Revocable IBE with Decryption Key Exposure Resistance
Abstract
1. Introduction
1.1. Motivations
1.2. Contributions
- Proposing a dual-key combination trapdoor generation mechanism
- Starting from an Inhomogeneous Small Integer Solution (ISIS) instance, KGC generates and distributes short bases to users of different identities as their identity keys.
- In each time period, the KGC constructs a new ISIS instance using the additive inverse of the target matrix and generates short bases as time keys for non-revoked users. Due to the target matrix in the ISIS instance, users cannot directly compute the decryption key for any time period using the short basis alone.
- Non-revoked users must linearly combine their identity key and time key to obtain the short basis trapdoor corresponding to the public key matrix, thus solving for the current time period’s re-randomized decryption key. By allowing non-revoked users to compute the current decryption key from both keys while denying this capability to revoked users, the scheme successfully achieves controlled key derivation.
- Constructing a post-quantum secure lightweight RIBE scheme with DKER
- By adopting the above mechanism for key generation and distribution, treating identity keys as user secret keys and time keys as key updates, we construct a Post-Quantum Secure, Lightweight RIBE scheme with DKER (PQS-LRIBE-DKER).
- Controllable key derivation enables indirect revocation in the scheme. Ultimately, the scheme shifts the periodic computational burden of revocation to a more powerful KGC, maintains a one-to-one correspondence between plaintext and ciphertext, and significantly reduces the sender’s computational load and the system’s communication overhead.
- Providing rigorous formal security proofs
- Assuming the hardness of the Learning with Errors (LWE) and ISIS problems, the proposed scheme has been proven to possess selective identity security in the standard model.
1.3. Related Works
2. Preliminaries
- For all distinct u, v , the matrix is full rank;
- is computable in polynomial time in nlogq.
2.1. Lattice and Discrete Gaussians
2.2. Useful Facts
2.3. Sampling Algorithms
- : On input q, n, output a pair () such that A is statistically close to a uniform matrix in and S is a basis for satisfying and .: On input a rank n matrix A in , a matrix , a short basis of , a Gaussian parameter , output a vector sampled from a distribution statistically close to .: On input a rank n matrix A in , the gadget matrix G and its trapdoor , and a Gaussian parameter , output a vector sampled from a distribution statistically close to .
2.4. Hardness Assumptions
2.5. Complete Subtree
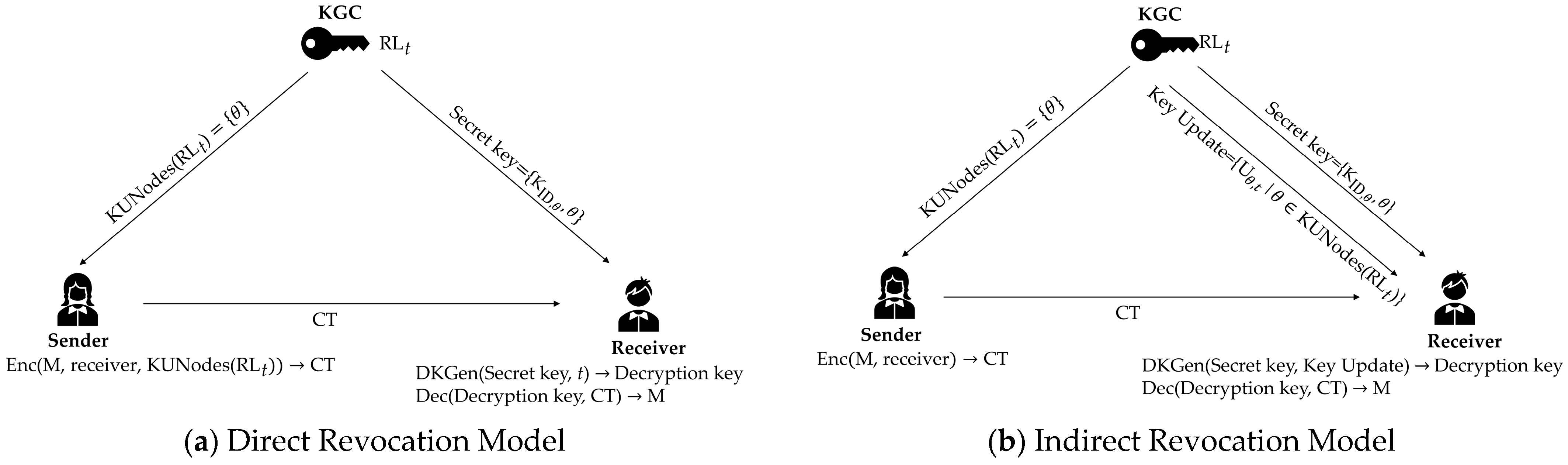
3. Formal Definitions for RIBE with DKER
3.1. Scheme Model for RIBE with DKER
- (PP, MSK): Executed by KGC, this algorithm takes a security parameter and the maximum number of users N in the system as input, generating the system public parameters PP and the system master secret key MSK as output.
- : Executed by the KGC, this algorithm takes the system public parameters PP, the master secret key MSK, and a user’s identity ID as input, generating a secret key as the output.
- : Executed by KGC, this algorithm takes the system public parameters PP, the master secret key MSK, and the revocation list RL as input, generating the key update for time period t as output.
- Enc: Executed by the sender, this algorithm takes the system public parameters PP, a user’s identity ID, a plaintext message m, and a time period t as input, generating a ciphertext as output.
- : Executed by the receiver, this algorithm takes the system public parameters PP, a secret key , and a key update as input, generating the decryption key for the receiver with identity in time period t as output.
- : Executed by the receiver, this algorithm takes a ciphertext and a decryption key as input, generating the plaintext message m as output.
3.2. Security Model for RIBE with DKER
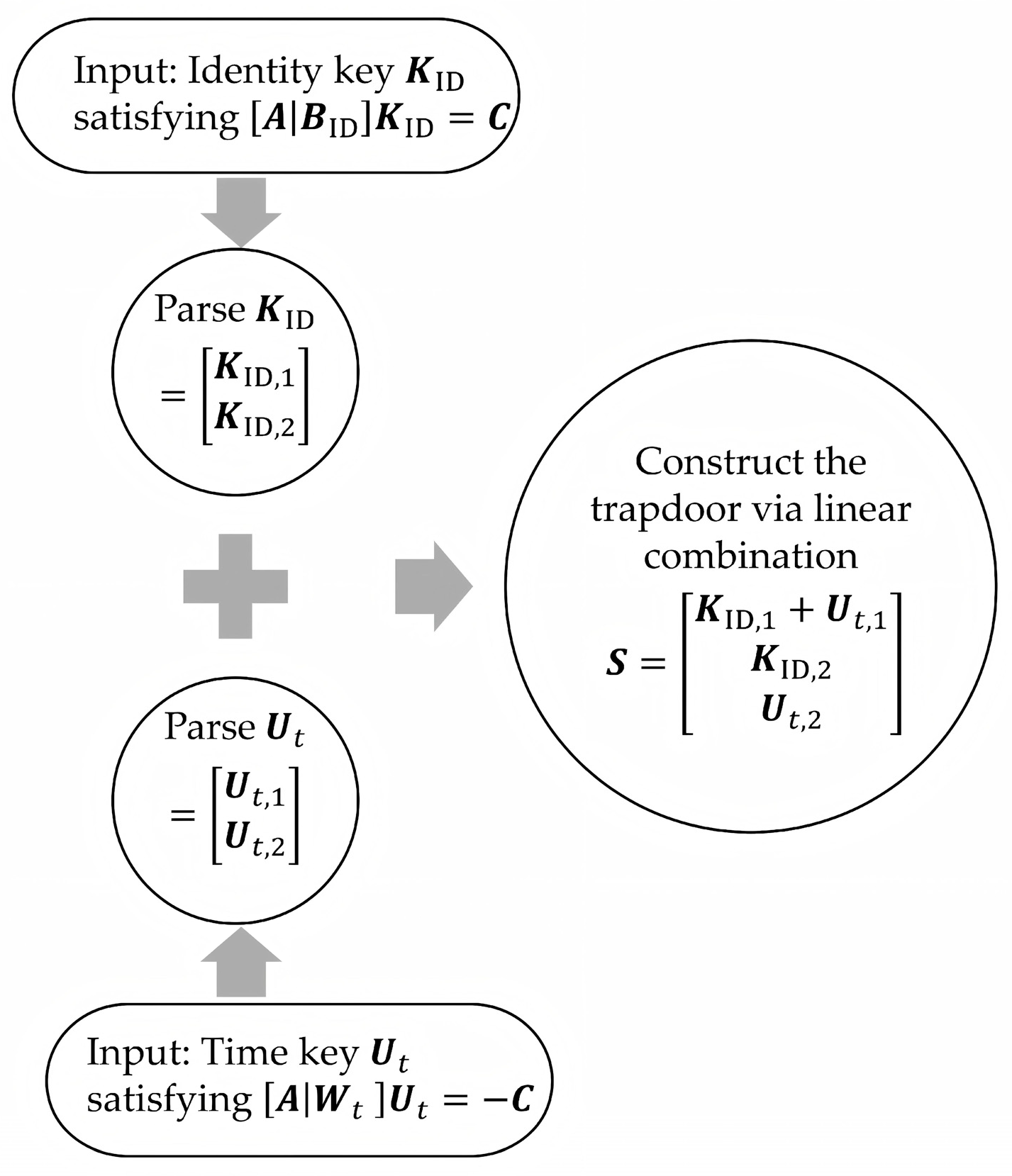
4. Dual-Key Combination Trapdoor Generation Mechanism
- Setup. KGC generates a matrix A and its corresponding trapdoor using a trapdoor generation algorithm. Matrix A serves as a system’s public parameter, while the trapdoor serves as the system’s master secret key.
- Secret Key Generation. KGC inputs into the algorithm SampleLeft and generates a secret key for each user. This key satisfies the equation . Here, C is a public parameter, is a matrix representing the user identity, and G is the gadget matrix.
- Key Update Generation. In each time period, KGC inputs into the algorithm SampleLeft. Given the equation , it generates and broadcasts key updates for non-revoked users. is a matrix representing the time period t.
- Decryption Key Generation. The user possesses the short basis S, which satisfies . The receiver needs to generate the decryption key satisfying , where u is a public parameter. The user accomplishes this by outsourcing the sampling of an intermediate vector x satisfying to an untrusted server. After obtaining x, the user computes This derivation is valid because , which produces a valid short solution to the target equation.
5. Post-Quantum Secure, Lightweight RIBE Scheme with DKER
5.1. Setup
- Run the trapdoor generation algorithm to generate a matrix and its corresponding trapdoor .
- Select uniformly random matrices B, W, and select an n-dimensional vector uniformly at random.
- Create a binary tree BT containing at least N leaf nodes. Mark all leaf nodes as unassigned. For each node in the binary tree, select a uniformly random matrix
- Output the system public parameters and the master secret key .
5.2. GenSK
- Randomly select an unassigned leaf node in the binary tree BT, and store the identity ID in this leaf node. Let denote the leaf node storing identity ID. Let denote the set of all nodes on the path from the leaf node to the root node (including both the leaf and the root).
- Let , where the hash function H is defined in Definition 1, and G is the gadget matrix in Lemma 3.
- For the identity ID and each node in , generate satisfying the equation , as follows:
- Select a uniformly random matrix . Compute .
- Sample .
- Split into two parts, the first m rows denoted as , and the last m rows denoted as . Similarly, split into and . Construct the key update matrix as: .
- Output the secret key .
5.3. KeyUp
- Run the KUNode algorithm, inputting the binary tree BT and the revocation list for time period t. This outputs the node update set for time period t.
- Compute , where the hash function H is defined in Definition 1, and G is the gadget matrix from Lemma 3.
- For each node in the , generate a key update satisfying the equation , as follows:
- Select a uniformly random matrix . Compute .
- Sample .
- Split into two parts, the first m rows denoted as , and the last m rows denoted as . Similarly, split into and . Construct the key update matrix as:
- Broadcast the key update .
5.4. Enc
- Select uniformly random matrices R, V, and select a uniformly random vector .
- Sample noise , and sample an m-dimensional noise vector .
- Compute: , , where is an identity matrix.
- Output the ciphertext .
5.5. GenDK
- Compare the binary tree nodes associated with their secret key against the nodes in the key update for time period t. If a common node exists, denote this node as and proceed with the following steps. Otherwise, the algorithm aborts.
- Select from their secret key and from the key update . Generate the decryption key satisfying the equation .
- Select a vector and compute.
- Sample .
- Construct the combined matrix S using the secret key component and the key update component : .
- Compute .
- Split the vector into three blocks of m elements each, denoted as , , and . Split the resulting vector into three blocks of m elements each, denoted as and . Construct the final decryption key vector:
- Output decryption key .
5.6. Dec
- Compute . If then ; otherwise .
- Output the message .
6. Performance Comparison
6.1. Correctness
6.2. Security Analysis
- .For , select and compute .
- .For , compute .
- Select and compute .
- Sample .
For , select uniformly random matrices .- Select and compute .
- Sample .
- ID ≠ ID∗.
- Select and compute .
- Sample .
- .
- Select and set .
- Sample .
- .For , select and return to the adversary .For ,
- Select and set .
- Sample .
- .
- Select and set .
- Sample .
- Select a matrix and compute .
- Solve for the secret key satisfying the equation .
- Select a matrix and compute .
- Sample .
- Compute using and .
- Select a vector and set .
- Sample .
- Compute using.
- Compute .
- Perform row blocking on the vector , dividing it into three blocks of m rows each, denoted as , , and . Perform row blocking on the , dividing it into three blocks of m rows each, denoted as , and . Construct the final decryption key vector by adding the corresponding blocks:
- Output decryption key .
- Select a matrix and let .
- Next, solve for the key update satisfying the equation .
- Select a matrix and compute .
- Sample .
- Compute the decryption key using and . The remaining steps are the same as in the scheme.
- Let .
- Compute . Send the challenge ciphertext to the adversary .
- When , the challenge ciphertext is:
- When the are uniformly random elements, the distribution of the challenge ciphertext is identical to that in Game 6.
6.3. Comparison of Complexity
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| IBE | Identity-Based Encryption |
| RIBE | Revocable Identity-Based Encryption |
| DKER | Decryption Key Exposure Resistance |
| ISIS | Inhomogeneous Small Integer Solution |
| KGC | Key Generation Center |
| PQS-LRIBE-DKER | Post-Quantum Secure Lightweight RIBE scheme with DKER |
| LWE | Learning with Errors |
References
- Shamir, A. Identity-Based Cryptosystems and Signature Schemes. In Proceedings of the International Cryptology Conference, Santa Barbara, CA, USA, 19–22 August 1984; pp. 47–53. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M. Identity-Based Encryption from the Weil Pairing. In Proceedings of the International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; pp. 213–229. [Google Scholar] [CrossRef]
- Boldyreva, A.; Goyal, V.; Kumar, V. Identity-based encryption with efficient revocation. In Proceedings of the ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 27–31 October 2008; pp. 417–426. [Google Scholar] [CrossRef]
- Chen, J.; Lim, H.W.; Ling, S.; Wang, H.; Nguyen, K. Revocable Identity-Based Encryption from Lattices. In Proceedings of the Australasian Conference on Information Security and Privacy, Sydney, Australia, 9–11 July 2012; pp. 390–403. [Google Scholar] [CrossRef]
- Seo, J.H.; Emura, K. Revocable Identity-Based Encryption Revisited: Security Model and Construction. In Proceedings of the International Workshop on Public Key Cryptography, Nara, Japan, 26–28 February 2013; pp. 216–234. [Google Scholar] [CrossRef]
- Wang, Q.; Huang, H.; Li, J.; Yuan, Q. Revocable IBE with En-DKER from Lattices: A Novel Approach for Lattice Basis Delegation. In Proceedings of the European Symposium on Research in Computer Security, Hague, The Netherlands, 25–29 September 2023; pp. 66–85. [Google Scholar] [CrossRef]
- Agrawal, S.; Boneh, D.; Boyen, X. Efficient Lattice (H)IBE in the Standard Model. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Nice, France, 30 May–3 June 2010; pp. 553–572. [Google Scholar] [CrossRef]
- Libert, B.; Ling, S.; Nguyen, K.; Wang, H. Zero-Knowledge Arguments for Lattice-Based Accumulators: Logarithmic-Size Ring Signatures and Group Signatures Without Trapdoors. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Hanoi, Vietnam, 4–8 December 2016; pp. 1–31. [Google Scholar] [CrossRef]
- Nguyen, K.; Wang, H.; Zhang, J. Server-Aided Revocable Identity-Based Encryption from Lattices. In Proceedings of the International Conference on Cryptology and Network Security, Milan, Italy, 8–10 November 2016; pp. 107–123. [Google Scholar] [CrossRef]
- Zhang, Y.; Liu, X.; Hu, Y.; Jia, H. Revocable Identity-Based Encryption with Server-Aided Ciphertext Evolution from Lattices. In Proceedings of the International Conference on Information Security and Cryptology, Seoul, Republic of Korea, 1–3 December 2021; pp. 442–465. [Google Scholar] [CrossRef]
- Zhang, Y.; Liu, X.; Hu, Y.; Jia, H. Cloud-Aided Scalable Revocable Identity-Based Encryption with Ciphertext Update from Lattices. In Proceedings of the International Conference on Frontiers in Cyber Security, Haikou, China, 26–28 November 2021; pp. 269–287. [Google Scholar] [CrossRef]
- Chen, Z.; Deng, L.; Ruan, Y.; Feng, S.; Wang, T.; Wang, B. An efficient revocable identity-based encryption with ciphertext evolution in the cloud-assisted system. Concurr. Comput. Pract. Exp. 2023, 35, e7735. [Google Scholar] [CrossRef]
- Huang, J.-J.; Chen, G.-Y.; Lo, N.-W. Poster: Post-Quantum Identity-Based Matching Encryption with Revocable Decryption Key. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, Salt Lake City, UT, USA, 14–18 October 2024; pp. 5006–5008. [Google Scholar] [CrossRef]
- Nishimura, T.; Takayasu, A. Efficient Revocable Identity-Based Encryption from Middle-Product LWE. In Proceedings of the Australasian Conference on Information Security and Privacy, Wollongong, Australia, 14–16 July 2025; pp. 64–83. [Google Scholar] [CrossRef]
- Takayasu, A.; Watanabe, Y. Lattice-Based Revocable Identity-Based Encryption with Bounded Decryption Key Exposure Resistance. In Proceedings of the Australasian Conference on Information Security and Privacy, Auckland, New Zealand, 11–13 July 2017; pp. 184–204. [Google Scholar] [CrossRef]
- Katsumata, S.; Matsuda, T.; Takayasu, A. Lattice-Based Revocable (Hierarchical) IBE with Decryption Key Exposure Resistance. In Proceedings of the IACR International Workshop on Public Key Cryptography, Beijing, China, 14–17 April 2019; pp. 441–471. [Google Scholar] [CrossRef]
- Huang, H.; Li, J.; Bi, S.; Yuan, Q. An efficient lattice-based integrated revocable identity-based encryption. Sci. Rep. 2025, 15, 16729. [Google Scholar] [CrossRef] [PubMed]
- Xia, F.; Mao, J.; Shao, Z.; Xu, L.; Zhao, R.; Yang, Y. An Authentication Mechanism for IoT Devices Based on Traceable and Revocable Identity-Based Encryption. In Proceedings of the International Conference on Artificial Intelligence and Security, virtual, 19–23 July 2021; pp. 550–562. [Google Scholar] [CrossRef]
- Wang, C.; Han, Y.; Duan, X.; Guo, K. Hierarchical Identity-Based Conditional Proxy Re-encryption Scheme Based RLWE and NTRU Variant. In Proceedings of the International Conference of Pioneering Computer Scientists, Engineers and Educators, Taiyuan, China, 17–20 September 2021; pp. 240–259. [Google Scholar] [CrossRef]
- Okano, Y.; Tomida, J.; Nagai, A.; Yoneyama, K.; Fujioka, A.; Suzuki, K. Revocable Hierarchical Identity-Based Authenticated Key Exchange. In Proceedings of the International Conference on Information Security and Cryptology, Seoul, Republic of Korea, 1–3 December 2021; pp. 3–27. [Google Scholar] [CrossRef]
- Zhu, Y.; Zhou, Y.; Wang, J.; Yang, B.; Zhang, M. Revocable-Hierarchical-Identity-Based Inner Product Function Encryption in Smart Healthcare. IEEE Internet Things J. 2025, 12, 15319–15332. [Google Scholar] [CrossRef]
- Asharov, G.; Jain, A.; López-Alt, A.; Tromer, E.; Vaikuntanathan, V.; Wichs, D. Multiparty Computation with Low Communication, Computation and Interaction via Threshold FHE. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; pp. 483–501. [Google Scholar] [CrossRef]
- Regev, O. On lattices, learning with errors, random linear codes, and cryptography. In Proceedings of the ACM Symposium on Theory of Computing, Baltimore, MD, USA, 22–24 May 2005; pp. 84–93. [Google Scholar] [CrossRef]
- Gentry, C.; Peikert, C.; Vaikuntanathan, V. Trapdoors for hard lattices and new cryptographic constructions. In Proceedings of the ACM Symposium on Theory of Computing, Victoria, BC, Canada, 17–20 May 2008; pp. 197–206. [Google Scholar] [CrossRef]
- Keita, E.; Jae Hong, S.; Yohei, W. Efficient revocable identity-based encryption with short public parameters. Theor. Comput. Sci. 2021, 863, 127–155. [Google Scholar] [CrossRef]
- Zhang, Y.; Liu, X.; Hu, Y. Simplified Server-Aided Revocable Identity-Based Encryption from Lattices. In Proceedings of the International Conference on Provable Security, Chongqing, China, 10–12 November 2022; pp. 71–87. [Google Scholar] [CrossRef]

| Scheme | Revocation Model | Post-Quantum Secure | Periodic Workload of KGC | Computational Cost of User |
|---|---|---|---|---|
| Scalable RIBE with DKER [5] | Indirect | F | ||
| Efficient RIBE with DKER [25] | Indirect | F | ||
| LB-RIBE with B-DKER [15] | Indirect | T | ||
| LB-RHIBE with DKER [16] | Indirect | T | ||
| LB-RIBE with En-DKER [6] | Direct | T | 0 | |
| LB-SA-RIBE [26] | Server-aided | T | ||
| OO-IRIBE-EnDKER [17] | Direct | T | 0 | |
| PQS-LRIBE-DKER | Indirect | T |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, D.; Ju, H.; Yan, Z.; Feng, S.; Li, F. Post-Quantum Secure Lightweight Revocable IBE with Decryption Key Exposure Resistance. Entropy 2025, 27, 1160. https://doi.org/10.3390/e27111160
Zhang D, Ju H, Yan Z, Feng S, Li F. Post-Quantum Secure Lightweight Revocable IBE with Decryption Key Exposure Resistance. Entropy. 2025; 27(11):1160. https://doi.org/10.3390/e27111160
Chicago/Turabian StyleZhang, Dandan, Hongwei Ju, Zixuan Yan, Shanqiang Feng, and Fengyin Li. 2025. "Post-Quantum Secure Lightweight Revocable IBE with Decryption Key Exposure Resistance" Entropy 27, no. 11: 1160. https://doi.org/10.3390/e27111160
APA StyleZhang, D., Ju, H., Yan, Z., Feng, S., & Li, F. (2025). Post-Quantum Secure Lightweight Revocable IBE with Decryption Key Exposure Resistance. Entropy, 27(11), 1160. https://doi.org/10.3390/e27111160





