Abstract
We study a node-wise monotone barrier coupling law, motivated by the synaptic coupling of neural central pattern generators. It is illustrated that this coupling imitates the desirable properties of neural central pattern generators. In particular, the coupling law (1) allows us to assign multiple central patterns on the circle and (2) allows for rapid switching between different patterns via simple ‘kicks’. In the end, we achieve full control by partitioning the state space by utilizing a barrier effect and assigning a unique steady-state behavior to each element of the resulting partition. We analyze the global behavior and study the viability of the design.
1. Introduction
The design of individual coupling laws to achieve asymptotic consensus on a common point in a vector space is a well-studied problem [1,2,3]. The analysis relies on convexity. In particular, for the real line, if each agent moves toward a strict inner point of the convex hull of the values of its neighbors, then the minimal (maximal) value among all the agents can only increase (decrease) until they become equal.
For nonlinear spaces, this argument, relying on convexity, cannot be used globally. In particular, for multiple agents on the circle, there is no ‘minimal’ or ‘maximal’. The convexity argument applies only when all agents are initially placed within a semi-circle [2,4]. In this respect, a number of papers have considered the construction of local controllers to achieve (almost) global convergence properties. In particular, modified Kuramoto coupling, Gossip algorithms, and hybrid coupling have been proposed. Meanwhile, to the best of our knowledge, these works either apply to particular interconnection topologies, such as trees and all-to-all interconnection [5,6,7], use auxiliary variables in the embedding space [6,7,8], use global information such as the number of agents N [9], can lead to unnecessarily slow convergence rates [10], or are only analyzed for two agents [11].
Indeed, global convergence properties are hard to achieve in general for the problem of consensus (or formation control) on the circle, unless the control is stochastic. In other words, in general, there are multiple steady-state behaviors or even chaotic ones. From an engineering viewpoint, this issue can be resolved, if we have our control on the multiple central patterns and their associated domain of attraction. For this purpose, we introduce a barrier effect in our coupling, motivated by the neural central pattern generators (CPGs), to partition the state space into finite regions, where for each partition, there exists a unique steady-state behavior.
Neural CPGs produce diverse rhythms in networks for the purpose of collectively generating movements such as breathing, chewing, swallowing, walking, and heart beating [12] in animals. Understanding the mechanisms behind the control and regulation of CPGs may result in technological advances, leading to systems that can rapidly adapt to sudden changes, similar to the way that CPGs adapt in fractions of a second to respond to events, e.g., in choking prevention or predator escape [12]. Besides the ability to accommodate multiple central patterns in the network and rapidly switch between them, such systems also exhibit robustness with respect to individual variability. Indeed, in the study of a network of nonidentical neurons interconnected via excitatory synaptic coupling (a particular type of CPGs), it was shown that the network is robust to heterogeneity and has the emergent behavior (central pattern) of synchronous spiking, even with the weak coupling strength and the impulsive nature of communication [13,14].
Ref. [14] argues that the key feature that provides these attractive properties of CPGs is the fast threshold modulation: a mechanism behind rapid synchronization initially discovered in [15], which can be illustrated by a barrier effect in phase models, as will be discussed in Section 2. Thus, in this paper, we focus on the problem of formation control on the circle and study a node-wise monotone barrier coupling law. In the end, we illustrate that by only assuming the barrier effect, the network exhibits attractive properties of CPGs. In particular:
- 1.
- It allows us to assign multiple central patterns in the steady-state behavior of the network with possibly different formations and common angular frequencies;
- 2.
- It allows rapid switching between different central patterns via a simple ‘kick’ (e.g., an impulsive input) or sudden disturbance.
Moreover, it brings robustness with respect to individual variability. For the considered node-wise coupling law, we then concentrate on the question of the viability of assigning one or multiple central patterns in the network, from an engineering viewpoint.
This paper is organized as follows. In Section 2, we motivate the relevance between coupling functions with a barrier effect in phase models and the synaptic coupling in CPGs. Then, with a brief review of graph theory given in Section 3, we introduce the node-wise monotone barrier coupling law in Section 4, which is the subject of study in this paper. Given the main convergence result in Section 4, we then focus our study on central patterns, where Section 5 and Section 6 consider the analysis and design aspects, respectively. We conclude in Section 7. The proof for the convergence result is given in Appendix B, which uses the graph theoretical lemma introduced in Appendix A.
Notation: , , , and denote the set of real numbers, integers, positive integers, and nonnegative integers, respectively. For vectors or matrices , . For a set , its cardinality is denoted by . The function denotes the signum function defined as for nonzero s, and for . In this paper, the modulo operation with respect to (mod ) results in a value in , and the modulo operation with respect to 1 (mod 1) results in a value in , for simplicity of notation.
2. Motivation of the Barrier Effect
Fast threshold modulation is a mechanism behind rapid and robust synchronization of nonidentical neuronal spiking systems, e.g., the Fitzhugh–Nagumo model, Morris–Lecar model, and Hodgkin–Huxley model, under weak synaptic coupling. In particular, it provides attractive properties of:
- rapid convergence to a central pattern;
- robustness with respect to heterogeneity,
in the following way [14], at the singular limit, i.e., when there is a sufficient time scale separation (illustrated for the central pattern of synchronous spiking):
- 1.
- At the singular limit, the individual system is an oscillator having jumps, which can be described as a hybrid system, that has a jump set of a lower dimension (see (1) and its description for an example).
- 2.
- At the singular limit, this provides a rapid convergence to the neighborhood of the limit cycle given that the coupling is weak.
- 3.
- Then, at the singular limit, the synaptic coupling alters the jump set of an individual in a way that the network-wise jump set demonstrating a central pattern becomes an open set (see (2) and its description for an example).
- 4.
- This open set with nonzero volume is what provides rapid convergence and robustness with respect to heterogeneity.
- 5.
- In particular, by the creation of this open set, the phenomenon of synchronous spiking happens in a hierarchical way: one neuron spikes and this yields a spike of neighboring neurons, and so on to the entire network, at an instant in the singular limit. The mechanism is called fast threshold modulation, as the threshold (jump set) is altered rapidly.
For example, at the singular limit, the neuronal model in [14] can be illustrated by a one-dimensional hybrid system:
where dictates the state-dependent velocity of the individual oscillator and and are the position of the threshold (jump set) and the jumping point, respectively, such that . It is intuitively clear that this is an oscillator repeating its trajectory from to .
What a fast threshold modulation does is that given another system , it widens a jump set for the synchronous jump from to with some points such that . In particular, at the singular limit, the neuronal network in [14] (with two neurons) can be illustrated by a hybrid system:
with an appropriate network-wise jump map . Note that by the creation of this open set, even when the neighboring neuron is not at its jump set (threshold) , but only if sufficiently near to it, i.e., , then the spike of the neuron x modulates the jump set and triggers a spike of the neighboring neuron . This happens instantly in the singular limit. Therefore, even if the frequencies of individual oscillators are different (heterogeneity), we can obtain a synchronous spiking solution. We emphasize that this creation of an open set can happen even under a weak coupling strength [14]. At the stable positively invariant set inside this new jump set, the convergence rate is independent of the weak coupling strength, and this is what provides rapid convergence. We refer to [14] for a more exhaustive illustration.
Although it is difficult to define a phase for individual systems in such a network, as the range of individual oscillation changes by the action of a neighborhood, if we were to model it in a phase model, then the action of a fast threshold modulation can only be realized by a barrier effect (whether it is discontinuous or continuous), as, in the singular limit, the new open jump set introduces a region , where a phase pulling of infinite power happens by the neuron x at the threshold , and clearly demonstrates a boundary that discriminates the behavior of neuron . For instance, if the phase that corresponds to position is , then as the phase difference approaches the new threshold , the effect of coupling becomes infinitely strong, where the phase corresponds to position .
In the rest of the paper, we will relax this characteristic to an arbitrary coupling law with a barrier effect and consider a network of phase models. It will be shown that this is sufficient to recover the attractive properties of CPGs: rapid convergence and robustness. Moreover, unlike the specific case illustrated in this section only for synchronization, it will be illustrated that this phase network exhibits multiple central patterns, and we can even design them. Before starting this investigation, we briefly review the necessary graph theoretical tools in the next section.
3. Graph Theoretical Preliminaries
A (weighted directed) graph is a pair consisting of a finite nonempty set of nodes and an edge set of ordered pairs of nodes , where for all (i.e., the graph does not contain self-loops). The set denotes the neighbors of the node i. A tuple is called a path (of length l) from the node to the node , if for all . If are distinct, then the path is called elementary. A loop is an elementary path with . A strongly connected graph is a graph for which any pair of distinct nodes j and i are connected via a path in from j to i.
is called undirected, if implies . Given a graph , let and:
The pair is called a subgraph of . If , then is a spanning subgraph. If a graph is connected, then there exists an agent i, called a root of the graph, from which information can propagate to all other agents j along paths in . A spanning subgraph of obtained by removing all edges that do not belong to one of these paths is called a spanning tree of . Note that any node of the strongly connected graph is a root. Note also that a strongly connected graph is connected, but not vice versa.
An independent strongly connected component (iSCC) of is an induced subgraph , , such that it is maximal subject to being strongly connected and satisfies for any and . For any digraph , there exists a uniquely defined set of number of iSCCs. if and only if the graph is connected.
The Laplacian matrix of a graph is defined as , where is the adjacency matrix of the graph and is the diagonal matrix whose diagonal entries are determined such that each row sum of is zero. By its construction, it contains at least one eigenvalue of zero, whose corresponding eigenvector is , and all the other eigenvalues have nonnegative real parts. For directed graphs (digraphs), the zero eigenvalue is simple if and only if the corresponding graph is connected.
We like to stress that for any connected digraph , the indices can be well assigned so that the Laplacian matrix associated with the graph can be written as:
where and are the Laplacian matrices of the unique iSCC, , and the subgraph induced by the rest of the agents, respectively. Since is the Laplacian matrix of a strongly connected graph, it is known that there exists a vector , which satisfies and for all . In particular, we have .
4. Node-Wise Monotone Barrier Coupling Law
Motivated by Section 2, we consider the node-wise monotone barrier coupling law for a group of N agents evolving on the circle as:
where represents the phase of agent i, is a subset of whose elements are indices of the agents that send information to agent i (hence, ), is the ‘intrinsic’ frequency, and denotes a coupling function on the domain extended to -periodically. is the interconnection weight and is the phase bias.
Let denote an element of the N-torus . Note that as the coupling function will have a barrier effect, i.e., as , we want our trajectories to reside inside the set . Note also that for the network to be well-defined for , we should have ; that is, the network should be quantized, as any addition of in the phase difference should not alter the coupling input .
We note here that in the rest of the paper, the N-torus will be realized by , and in that regard, the partition of consisting of a finite number of sets:
where each one associated with a sequence of integers will take a critical role (as, e.g., in the following theorem) with its associated extension to space:
Note that for to be nonempty, we should have , where , and thus, the number of sets is upper bounded by .
Assumption 1.
The communication graph is connected; contains a spanning tree. The adjacency elements , are positive integers.
Assumption 2.
The coupling functions , are differentiable, strictly monotonically increasing, and have a barrier effect so that as .
Theorem 1.
Under Assumptions 1 and 2, for any given , each solution trajectory of (3) starting from the extended space uniquely exists and resides inside (hence, forward complete) and converges to a central pattern of phase-locking behavior determined by:
- A common frequency ;
- A formation : a phase difference given for each edge.
In particular, there exists a steady-state solution of (3) corresponding to that resides inside . Finally, for each trajectory, the control input , is bounded uniformly on .
Proof.
We show in Appendix B.1 that the set is positively invariant for the network (3) extended to and also that the control input is uniformly bounded. Then, the convergence to a central pattern and the existence of a corresponding steady-state solution that resides inside is shown in Appendix B.2. □
In the following sections, we will further investigate the following:
- The shape of the central pattern ;
- The number of different central patterns ;
- What central patterns can be assigned;
- How to achieve these central patterns.
Remark 1.
We neglect the analysis of the convergence rate, as it depends on the slope of our coupling functions , which can be made arbitrarily large.
5. Analysis of Central Patterns
This subsection corresponds to the analysis part of the study of the considered node-wise monotone barrier coupling law. In particular, for a given set of fixed intrinsic frequencies , a set of coupling functions , a set of interconnection weights , and a set of phase biases , we first specify the shape of the central pattern .
Theorem 2.
Under Assumptions 1 and 2, every trajectory of (3) starting from converges to the unique central pattern . Here, is the unique solution of:
where denotes the unique iSCC, , are the components of the left eigenvector of associated with the zero eigenvalue, and the inverse is defined as a mapping from into . is uniquely defined by the relation , where is the unique solution of:
such that .
Proof.
Note first that by Theorem 1, for the given sequence , each trajectory starting from has a central pattern of phase-locking behavior that the trajectory converges to. Being the central pattern, should satisfy:
By Theorem 1, there exists such that . Without loss of generality, we assume . This implies:
Remark 2.
Here, we can see the resiliency of the generated patterns with respect to individual variability. In particular, is a sigmoidal function, and thus, Equation (6) rejects outliers , as done by the median in statistics, which is the solution of the similar equation:
In general, becomes more tolerant to variation in that is far from . This is also true for the formation, as can be seen in (7). The effect of variation in that is far from () becomes negligible through due to the barrier effect.
From this characterization of the shape of the central pattern, we have the following conclusion.
Theorem 3.
Under Assumptions 1 and 2, a network of agents on the circle communicating according to (3) introduces a partition of consisting of number of sets , . Every trajectory starting from resides inside and converges to a unique central pattern of phase-locking behavior. Each set has the following structure:
Proof.
Given that any initial point of a trajectory in is contained in one of the sets , associated with some , the convergence to a unique central pattern for any trajectory starting from each set is given by Theorem 2.
Note that for each set , there exists a finite number of sequences , such that any point in that corresponds to a set is contained in one of the sets , in the partition of . For each unique central pattern, let us collect all the corresponding sets , for all positively invariant sets resulting in that particular central pattern, to construct a set . Then, each set can be represented as a union of a collection of sets , . This is because, otherwise, there exist a sequence and such that and with some . This yields a contradiction, as trajectories that start from and reside inside and converge to the same central pattern. □
Now, we specify a collection of sequences , that defines the set . For this purpose, we define an equivalence relation for two sequences and if they have the same central pattern or equivalently that and are contained in the same set , and denote it as . We also denote the equivalence class as .
Theorem 4.
Two sequences and are equivalent, i.e., , if and only if:
- ;
- The following equation has a unique integer solution , or equivalently, that the vector on the right-hand side is spanned by the columns of the Laplacian matrix with integer-valued weights:
The second condition is equivalent to for all , where and are the corresponding solutions of (7) for and , respectively.
Proof.
Remark 3.
According to Theorem 4, a strongly connected graph that has the following form of Laplacian matrix ensures that two sequences and are equivalent if and only if :
This includes the cases of directed ring graphs and undirected line graphs, which have as the left eigenvector associated with the zero eigenvalue, resulting in N or different central patterns (Remark 4).
The number of different central patterns of the network (3), , can be fully characterized by a graph theoretical interpretation as the number of different equivalence classes such that there exists , satisfying . The following remark and corollary may aid in the analytical investigation to determine or at least its upper bound (as in Remark 3). Meanwhile, such a number can be obtained by numerical computation.
Remark 4.
Unlike the number of different central patterns, , which is complicated to find, the number of different is straightforward. In particular, the left eigenvector of associated with the zero eigenvalue can always be taken as an integer vector where the common denominator of the components is 1. This is because, is integer-valued, and thus, Gaussian elimination will produce rational eigenvectors. Then, the number of different is simply upper bounded by or . This is because, we have from that:
and hence, for each , we get:
Corollary 1.
if and only if:
- for the graph , which is strongly connected;
- There exist integers , such that:
In other words, if , then for any set of integers , we have:
where , . In particular, if all the followers () have only one neighbor, , and , , then if and only if .
Proof.
The first claim directly follows from Theorem 4. The second claim follows because under this additional assumption, for any and , there exist integers , such that:
This is because there is no loop in graph . Or one can simply consider as a single node, which makes the entire graph a spanning tree. □
Before concluding this section, we note that, ultimately, by only assuming the barrier effect in our coupling functions, we observe the desirable properties of neural CPGs in the network on the circle:
- The network exhibits number of different central patterns.
- A simple ‘kick’ (e.g., an impulsive input that instantly shifts the state of the network) that pushes the steady-state solution of outside the boundary of rapidly switches the central pattern (Remark 1).
- The number of different central patterns and the steady-state solution are robust to model uncertainties, noises, and disturbances, given that the barrier effect is consistent (Remark 2).
This provides numerous advantages in the problem of formation control on the circle:
- When considering a single formation in the network on the circle, global convergence is hard to achieve in general (unless the control is stochastic). This is because the required convexity is not retained globally in nonlinear spaces. From an engineering viewpoint, this issue can be resolved, if we have control over the multiple central patterns and their associated domains of attraction. Barrier coupling laws partition the state space into finite regions, where for each partition there exists a unique steady-state behavior.
- For instance, in a situation where a fleet of drones move in a balanced formation until they encounter obstacles, e.g., a scenario in which they have to pass between two buildings, and this impulsive event is detected by some of the drones in the formation. Then, this event can be made to trigger a ‘kick,’ which could alternate the formation of the network, for example, to a line, so that they can be safely guided through a narrow passage.
To best utilize these advantages, in the next section, we seek the viability of assigning multiple patterns from a practical viewpoint.
Remark 5.
If we cut the barrier function at a finite region, that is, with some but is still strictly increasing and satisfies , then since the monotonicity is preserved, the behavior of the network will be either converging to some central pattern and achieving phase-locking behavior or moving to the discontinuous boundary. In particular, if we let ():
where are such that and so that the resulting function is still strictly increasing, then there are no new central patterns generated when δ is sufficiently small. Therefore, for the partition, where the central pattern corresponding to the coupling functions , is outside the saturated region, i.e., which has such that , the trajectory starting from that partition moves to the boundary. This becomes clear if we observe the dynamics of . Then, depending on the vector field on the opposite side, it either moves to another region associated with another sequence in a finite time or stays on the boundary. In other words, if we set and for each such that for all central patterns , then the original behavior will be mostly maintained, while some might converge to the boundary and stay there.
6. Design of Central Patterns
This subsection corresponds to the synthesis part of the study of the considered node-wise monotone barrier coupling law. In particular, for a given fixed connected digraph , a set of intrinsic frequencies , and a central pattern , we seek the viability of assigning the given central pattern to the network (3) under several scenarios that are governed by the choice of freedom we have for the design parameters:
- A set of interconnection weights (we allow for design purposes);
- A set of phase biases ;
- A set of coupling functions .
Moreover, among the viable solutions that we can get, we further consider the problem of providing some of the additional desired characteristics, such as:
- Utilizing a minimal number of edges;
- Minimizing the number of alternative central patterns;
- Assigning other given central patterns.
In so doing, we illustrate our findings with examples. We begin with the following theorem on the viability of assigning one central pattern.
Theorem 5.
- 1.
- It is almost impossible to assign the given central pattern if we only have the freedom to choose the set of interconnection weights .
- 2.
- If we have freedom of choice for either the set of coupling functions or the set of phase biases , then we could always assign the given central pattern .
- 3.
- If our coupling functions are the scaled version of a single fixed function , i.e., with positive coefficients to ensure monotonicity, then we can assign the given central pattern if and only if:
Proof.
The first claim follows from the fact that the following:
forms only a measure zero set in , as it is parametrized by a set of integers and hence, is countable.
The second claim follows from the fact that there always exists or such that:
as , , are barrier functions. In particular, if we have freedom of choice for the set of coupling functions , then we choose any such that it satisfies Assumption 2 and , where . Otherwise, if we have freedom of choice for the set of phase biases , then we choose as:
The final claim also follows from the fact that , , are barrier functions. In particular, we choose as:
□
Coupling functions that have a prototypical shape, i.e., , are reminiscent of the physiology of CPGs, where the central patterns are designed by the maximal conductances of the synaptic coupling [12]. From a practical viewpoint, it reduces the problem of choosing the coupling functions to an algebraic problem.
Proposition 1.
The necessary and sufficient condition (12) for viability can always be satisfied
- If we have freedom of choice for the phase biases.
- If we only have freedom of choice for the interconnection weights, then (12) can be satisfied when:
- -
- ;
- -
- There exists such that is an irrational number.
- If, in addition, our interconnection weights are to take a prototypical ratio, i.e., with positive integers , then (12) can be satisfied when:
- -
- ;
- -
- is an irrational number, where .
Proof.
The first point is trivial, as, for any given , we can always choose so that becomes positive (or negative).
For the second and the third points, we first prove the following claim.
Claim: Let be an irrational number. Then, for any , there exists such that .
Proof of claim: The proof is by contradiction. Suppose that
Then, there exists such that:
By the definition of , for:
there exists such that:
If we let:
then this implies that , and hence:
and
Since is an irrational number, we have , and (14) further implies:
In other words, we have
which is a contradiction. This completes the proof of the claim. □
For the second point, under this sufficient condition on the existence of , we can simply let , and seek for a nonnegative integer such that:
Such an integer always exists, because is an irrational number. In particular, without loss of generality, assume that is positive and let be such that . Then, for and , our claim ensures the existence of such that . Therefore, if there exists such that:
then this implies that there exists such that:
and hence, also becomes positive.
The third point follows similarly, except that we consider instead of :
□
Note that given a formation , we can perform an arbitrarily small perturbation so that the above irrational number condition is satisfied, and hence, we can achieve our design goal with arbitrary precision. In particular, in the former case, we can even select an arbitrary edge to ensure that is an irrational number. This is because any formation can be generated by a sequence of phases as , and thus, with any irrational number , if we perturb as , , then for almost all sufficiently small rational numbers , becomes irrational.
Based on this viability analysis, in the following subsections, we further provide guidelines for achieving the additional desired characteristics, illustrated and further discussed with examples.
6.1. Design Guideline for Utilizing a Minimal Number of Edges
Among all of the possible choices we could take for assigning a central pattern, we provide a design guideline that maximizes the number of interconnection weights that we can set to zero, given a digraph .
If we have freedom of choice for either the set of coupling functions or the set of phase biases, then according to Theorem 5, we can simply choose our interconnection weights so that the reduced subgraph (governed by positive weights) still contains a spanning tree (Assumption 1) and maximizes the number of interconnection weights that are zero. In particular, edges are sufficient. For the design, one could pick any node from the unique iSCC of the original graph, and then take any spanning tree that connects to it.
On the other hand, if we consider the scaled version of coupling functions as in Theorem 5 and only have freedom of choice for the interconnection weights, then (to assign the given central pattern) we must include at least one edge for each , such that is an irrational number (Proposition 1). Thus, for each , we need at least one positive interconnection weight . If we denote such a set of at most N edges by , then an associated least communication subgraph, which contains (hence satisfying (12)) and satisfies Assumption 1, can be found as follows.
- 1.
- Consider the reduced graph . Add a minimum number of edges so that the new reduced graph contains a spanning tree. This can be completed as follows.
- (a)
- The reduced graph consists of its iSCCs and followers. Consider each iSCC and its followers as a single node (a follower can be included in multiple nodes), and define an edge from one node to another if there is an edge in the original edge set from any agent inside one node to any agent in the iSCC of another node.
- (b)
- This new graph is strongly connected. Thus, take any spanning tree of it and add one corresponding edge from the original edge set .
- 2.
- Then, include all other edges in , and add a minimum number of edges so that the new subgraph contains a spanning tree. This can be completed as follows.
- (a)
- The graph obtained by including all other edges in consists of its iSCCs and followers. By construction, there exists unique iSCC included in .
- (b)
- Now consider the iSCC included in and its followers as a single node and consider all other iSCCs each as a single node, and define a graph according to the edge set .
- (c)
- Then, this new graph contains a spanning tree which has its root node as the node that corresponds to the iSCC included in . Take this spanning tree and add one corresponding edge from the original edge set .
Example 1.
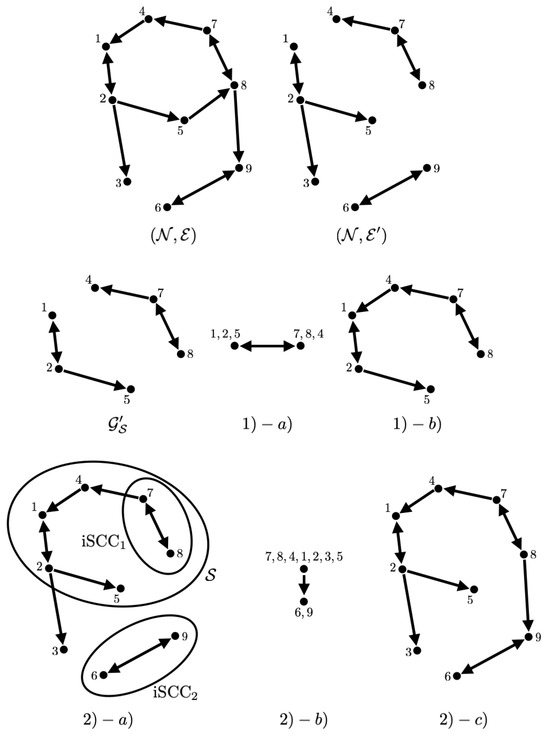
Let us take an example for the above procedure. For this purpose, let us consider a graph with and with represented by in Figure 1. If the formation is governed by from given as:
then the set and the set of edges such that is an irrational number are obtained as in Figure 1. The procedure described above is illustrated in Figure 1.

Figure 1.
Illustration of the graphs and , and the process (1) and (2) in obtaining the least communication subgraph in Example 1.
Meanwhile, note that as discussed after Proposition 1, we can introduce an infinitesimally small perturbation in the formation to select as whatever we want. In this sense, we can make the number of positive interconnection weights or N, by choosing such that contains a spanning tree. In particular, we can simply make to be a spanning tree, if there exists such that:
or if not, then make to be a spanning tree with an additional edge for the root node i. Such an attempt for the situation illustrated in Example 1 can be found in Section 6.3.
6.2. Design Guideline for Minimizing the Number of Alternative Central Patterns
Note that according to Corollary 1, when we choose our nonnegative interconnection weights to be such that the reduced subgraph governed by positive weights is a spanning tree and those positive weights are unity, then our central pattern becomes unique and we have almost global convergence. This is because all of the followers have only one neighbor and , , hence if and only if . Note that is a singleton , and hence, if and only if . Since , any admissible () gives ; the number of different central patterns is one.
In this manner, if we have freedom to choose either the set of coupling functions or the set of phase biases, then as in Section 6.1, we can simply choose our interconnection weights so that the reduced subgraph is a spanning tree. Then, no alternative central pattern exists.
On the other hand, if our coupling functions have a prototypical shape as in Theorem 5 and only have freedom of choice for the interconnection weights, then in principle, becomes a large integer, and thus, the number of alternative central patterns becomes large. Meanwhile, if we have a large number of neighbors for each agent, and the formation is uniformly distributed, then we have a better chance of decreasing the number, as there will likely be an edge such that . However, in general, finding a set of interconnection weights that gives a minimal number of alternative central patterns under the restriction of our coupling functions is a hard problem. The best we could do is to reduce the number of neighbors and reduce the interconnection weights, as, in general, the equivalence relation specified in Theorem 4 is complicated, and the fact that is an integer gives an additional restriction via the equality (11) and it is most likely that different are not equivalent. This is to reduce the number of admissible (), in particular, its upper bound .
Remark 6.
According to Remark 5, if we have chosen our interconnection weights, coupling functions, and phase biases, then we can simply cut our coupling functions at a finite region , to satisfy , only for the desired central pattern. This increases the chance of yielding almost global convergence, even under the restriction . The trajectory might converge to the boundary and stay, but we can always give a kick to make it converge to the desired central pattern.
6.3. Further Discussions on Example 1
In this subsection, we follow Example 1. However, instead we consider an infinitesimal perturbation on the given formation, so that we can choose the set of edges such that is an irrational number, which yields the graph represented in Figure 2, a spanning tree with one additional edge (as discussed at the end of Section 6.1). This is achieved for the formation governed by from given as:

Figure 2.
Illustration of the graphs and in Section 6.3.
Note that the only difference is , , and , and the difference is smaller than .
Now consider the situation where our objective central pattern is determined by the above given phases and a common frequency , while given that the intrinsic frequencies are and for . Moreover, say our coupling functions are scaled versions of a single function as in Theorem 5. If additionally, the phase biases are fixed as:
then to satisfy (12), we should first choose for each , so that:
This can be achieved simply by setting , , and for all other edges. Then, we choose for each so that:
The corresponding simulation result with different initial conditions is given in Figure 3. Note that we obtain three different central patterns. This is because only are possible (Remark 4), and they result in three different equivalence classes , , and according to Theorem 4 (their differences are integer span of the column of the Laplacian matrix, ) and Corollary 1. This is smaller than the number of different central patterns for the network obtained in Example 1, because the smallest possible is 1 and is 4 in Example 1, and the number of different central patterns even with for all other edges (which makes the inverse of again the integer matrix) is 5.

Figure 3.
Simulation results for initial conditions (1) (2) (3) , where , for all cases. These correspond to the equivalence classes (1) (2) (3) . The equivalence class corresponds to the objective formation. The graph represents the phase differences , .
On the other hand, if we have freedom of choice for the phase biases in the above situation, then we can also take as unity, by taking and , and this gives almost global convergence. The simulation result with the initial condition that resulted in different central patterns in Figure 3 is given in Figure 4a. We observe that now we have convergence to the unique central pattern that we assigned. One can check that the number of different central patterns is 1 in this case. In particular, only are possible (Remark 4), but they are all in the same equivalence class according to Theorem 4 (their differences are integer spans of the column of the Laplacian matrix, ) and Corollary 1.
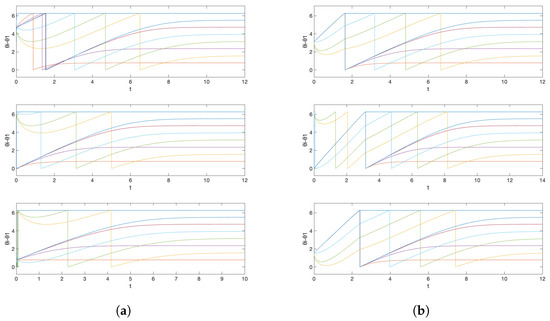
Figure 4.
Simulation results for initial conditions (1) (2) (3) , where , for all cases, when (a) we allow the freedom of choice on the phase biases and (b) we saturate the prototypical barrier function. The graph represents the phase differences , .
On the contrary, if we preserve the restriction that the phase biases are fixed as (15), but, as discussed in Remark 6, instead saturate the prototypical barrier function so that now with sufficiently small , then we again obtain almost global convergence. The saturation region is chosen so that for all . Note that, in this case, we must have and . This is illustrated in Figure 4b with the same initial condition that resulted in a different central pattern in Figure 3. This happens because, for the alternative central patterns, does not satisfy , , as this is equivalent to with some small , while they have their common frequency bigger than 2 for and smaller than 0 for . Therefore, the trajectory starting from that corresponding partition travels to the discontinuous boundary, which in this case, results in a transition to the partition that corresponds to our desired central pattern.
6.4. Assigning Multiple Central Patterns
The following theorem characterizes the viability of assigning multiple central patterns , for a given fixed connected digraph and a set of intrinsic frequencies .
Theorem 6.
For a set of interconnection weights and a set of phase biases , if we have freedom of choice for the set of coupling functions , then we could assign the given multiple central patterns , () if and only if:
- has the same order as : if is the sorted index such that:then we have, with equality being preserved:
Hence, if, in addition, we have freedom of choice for the set of phase biases , then, it is always possible when .
Proof.
We can simply choose any such that it satisfies Assumption 2 and for all , where , . □
Given a digraph , a set of intrinsic frequencies , and multiple desired central patterns , , it might be possible to select a set of interconnection weights so that the above necessary and sufficient condition is fulfilled. However, in such cases, due to the choice of interconnection weights (which in general satisfies ) the number of alternative central patterns increases (at least the number of such that ).
Theorem 6 and the corresponding advantages in formation control are illustrated in the following examples.
Example 2.

For graph , if and , and , then we have two different central patterns. If , , , and , then we can set the alternative central pattern to be near the boundary, for instance, as and , since , and , . A suitable set of coupling functions is as follows:
Then, since only the alternative central pattern is near the boundary, with a persistent small kick (e.g., a train of impulsive inputs) on or , we have almost global convergence to the desired central pattern and . This is illustrated in Figure 5.

Figure 5.
Simulation results for initial conditions (1) , and (2) , , when (a) there are no ‘kicks’ and (b) there is a small persistent excitation given to , which ‘kicks’ the trajectory from the near-boundary central pattern (1) to the robust central pattern (2). These correspond to the equivalence classes (1) and (2) .
Example 3.

Another example is given for the three agents that constitute a directed ring; . From Remark 4, we notice that if , then the number of different is two, and by the structure of the Laplacian matrix, if , for all , then all the sequences associated with each are equivalent (Remark 3). Therefore, the number of different central patterns becomes two. We assign for this network a uniformly distributed central pattern with two different permutations by letting:
To satisfy the necessary and sufficient condition in Theorem 6 and to satisfy , we utilized:
Then, for any intrinsic frequency , we can assign both central patterns simultaneously. Here, we take , , and . A suitable set of coupling functions is:
This is illustrated in Figure 6.

Figure 6.
Simulation results for initial conditions (1) , and (2) , , . These correspond to the equivalence classes (1) and (2) .
Example 4.

Our final example concerns an arbitrary odd number with star-shaped graph . If for all , and , then we have two different central patterns. In particular, if for all , , and , , then we can assign two central patterns (with completely opposite behaviors), where one represents perfect balanced formation, i.e., , for all , and the other represents perfect synchronization, i.e., , for all . This is because and , , , and , . We can utilize coupling functions in the form of , where and form the unique solution of the linear equation:
For , and form the unique solution of the linear equation:
For , and form the unique solution of the linear equation:
This is illustrated in Figure 7 for the case when .

Figure 7.
Simulation results for initial conditions (1) and , and (2) and , .
7. Conclusions
By introducing the node-wise monotone barrier coupling law, we proposed a tool to simultaneously assign multiple central patterns on the circle, where a transition between different patterns can happen via a simple ‘kick’. We characterized the shape of the generated central patterns, identified the number of different central patterns, analyzed the viability of assigning desired patterns, and provided design guidelines.
Compared with our initial work [16], where instead of the node-wise monotone barrier coupling law, we had utilized the edge-wise version:
we no longer have to confine ourselves to undirected graphs . The analysis of the generated central pattern has become less straightforward, but instead, we obtained a general understanding of the number of different central patterns. From a design perspective, for a similar number of restrictions, we now have fewer limitations and more straightforward design guidelines.
Future consideration will be given to quantitive analysis of the robustness, extension of the framework to other nonlinear spaces, and its use in practical design problems. An example is to control a cluster of drones. Energy perspectives as considered in [16] are also of interest, where a relevant problem for investigation is the minimization of energy to maintain the given formation or the minimization of energy for transitions among multiple desired patterns.
Author Contributions
Conceptualization, C.M. and J.G.L.; Methodology, J.G.L. and C.M.; Software, G.V.G. and J.G.L.; Formal analysis, J.G.L.; Investigation, J.G.L. and C.M.; Writing—original draft, J.G.L.; Writing—review and editing, C.M.; Visualization, G.V.G.; Supervision, C.M. All authors have read and agreed to the published version of the manuscript.
Funding
J.G.L. was supported by the National Research Foundation of Korea grant funded by the Korean government (Ministry of Science and ICT) under No. NRF-2017R1E1A1A03070342. C.M. was supported by a Presidential Postdoctoral Fellowship at NTU and an Early Career Research Fellowship at the University of Cambridge. G.V.G. was supported by the UCL Centre for Doctoral Training in Data Intensive Science funded by STFC, and by an Overseas Research Scholarship from UCL.
Institutional Review Board Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Acknowledgments
The authors are most grateful to Rodolphe Sepulchre for inspiring this work and for their guidance and support.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Essential Graph Theoretical Lemma
The following lemma is essential in the proof of Theorem 1, which is given in Appendix B.
Lemma A1.
Under Assumption 1, for any such that , where denotes the unique iSCC, there exists , such that for any vector :
with some coefficients . Moreover, there exists and such that and .
Proof.
Consider a subgraph . Then, there exists iSCCs denoted as , , and the rest denoted as . We will first assume that Lemma A1 holds for the index set ; that is, is given for such that for any vector :
then we will show that for each , we can find , such that for any vector :
This will complete the proof. By repeating this argument (i.e., by replacing the role of with ), we arrive after finitely many steps at the stage of assuming that Lemma A1 holds for the index set , but is empty; that is, the subgraph only consists of iSCCs, so that the assumption holds trivially.
Let us carry out the steps of the proof described above. For this purpose, note that by Assumption 1 and the fact that , for each , there exist and such that . This is because otherwise, becomes the unique iSCC of the entire graph, but this is not possible, since . Now, let denote the Laplacian matrix of the subgraph . Then, (A2) for only those corresponding to can be represented as:
with some diagonal matrix such that by the existence of , , . Thus, first let be the left eigenvector of associated with the zero eigenvalue. Then, we have and:
Next, let be the set of all indices such that the element of corresponding to agent i is positive. Clearly, is not empty. Now, we can find sufficiently small such that:
satisfies:
and that , where denotes the vector of appropriate size with 1 only in the position that corresponds to the index set and 0 elsewhere. In particular:
Therefore, by repeating this argument, due to the fact that is strongly connected, we arrive after finitely many steps at the situation where . This implies that:
Therefore, we can find sufficiently large such that satisfies:
and we conclude (A2) as desired. □
Appendix B. Proof of Theorem 1
Appendix B.1. Is Positively Invariant
The existence of a unique (local) solution starting from is simply given by the fact that the system dynamics is locally Lipschitz continuous inside . Now, the rest of the proof is by contradiction. Suppose that there is a particular solution of (3) such that holds only for a finite time interval and is violated at . This implies that there is a time sequence such that is strictly increasing and , and:
where is such that . This implies for all . Let us first assume that is nonempty. We will first show that a contradiction occurs if , where denotes the unique iSCC. If , we will then show that it is possible to construct another time sequence (based on ), such that:
where the notation denotes the cardinality of the set. By repeating this argument (i.e., by replacing the role of with ), we arrive after finitely many steps at the index set such that , which yields a contradiction. This means that there is no such sequence that makes nonempty. Similarly, it can be seen that there is no sequence that makes nonempty. Therefore, we conclude there is no such finite time T, and thus, for all .
Let us carry out the steps of the proof described above. For convenience, we write instead of in the following. Note that, by the definition of , for each , there exists a sufficiently large such that for all . Hence, if , then for any given set of positive coefficients , , there is k such that:
This is because, if , then the sum converges to zero, but is negative for all finite k, and otherwise if , then there exists sufficiently small such that the sum is nonzero for all . However, this is violated if , corresponds to the elements of the left eigenvector of the Laplacian matrix associated with the zero eigenvalue, because then:
Hence, we have shown that is not possible and we continue the proof for the case that . For this purpose, let:
where , is given by Lemma A1 considering the index set . Note that is continuously differentiable, on , and . Let us now consider a strictly decreasing sequence of positive numbers such that and . Choose a subsequence of such that:
Based on this subsequence, we now construct a sequence such that (see Figure A1):
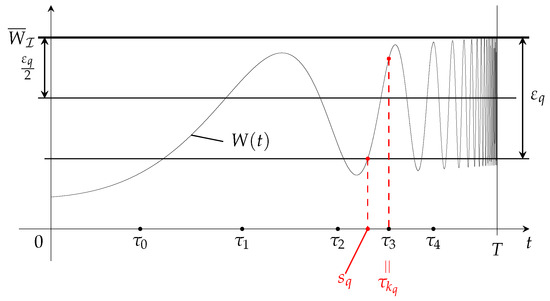
Figure A1.
Illustration of the choice of the sequence based on .
On the other hand, if we compute , then we have:
where , , for simplicity. We denote the first sum by . Invoking Lemma A1 for the index set , we, therefore, have that ():
Again, by Lemma A1, at least one (), where (), is positive. Thus, it follows from (A6) that as . Since:
where , we have:
Therefore, for each sufficiently large q, there is an index such that . Since is a finite set, there is a subsequence such that ; hence:
that is, . Consequently:
By construction, and we can conclude (A3) as desired. Noting that the above proof holds even if we let , so that there is no time sequence such that is strictly increasing and which makes () nonempty, it follows that the control input is bounded uniformly on .
Appendix B.2. Convergence to a Unique Central Pattern
Given the forward invariance in , the convergence of the trajectory to an integral curve corresponding to a central pattern of phase locking behavior can be shown simply by monotonicity. In particular, the linearization of (3) can be found as:
and is strictly monotonic with respect to the positive orthant inside the positively invariant set due to Assumptions 1 and 2. The Perron–Frobenius vector of the system on is as this is the eigenvector of:
associated with the eigenvalue having the largest real part, which is zero. This ensures that for any trajectory starting from , there exists a central pattern such that the trajectory converges to a trajectory of form , where:
Such a trajectory actually exists in as the control input is bounded uniformly on (Appendix B). Further details may be found in [16,17,18].
References
- Moreau, L. Stability of continuous-time distributed consensus algorithms. In Proceedings of the 2004 43rd IEEE Conference on Decision and Control (CDC) (IEEE Cat. No.04CH37601), Nassau, Bahamas, 14–17 December 2004; Volume 4, pp. 3998–4003. [Google Scholar] [CrossRef]
- Moreau, L. Stability of multiagent systems with time-dependent communication links. IEEE Trans. Autom. Control 2005, 50, 169–182. [Google Scholar] [CrossRef]
- Olfati-Saber, R.; Fax, J.A.; Murray, R.M. Consensus and Cooperation in Networked Multi-Agent Systems. Proc. IEEE 2007, 95, 215–233. [Google Scholar] [CrossRef]
- Jadbabaie, A.; Lin, J.; Morse, A. Coordination of groups of mobile autonomous agents using nearest neighbor rules. IEEE Trans. Autom. Control 2003, 48, 988–1001. [Google Scholar] [CrossRef]
- Sepulchre, R.; Paley, D.A.; Leonard, N.E. Stabilization of Planar Collective Motion: All-to-All Communication. IEEE Trans. Autom. Control 2007, 52, 811–824. [Google Scholar] [CrossRef]
- Scardovi, L.; Sarlette, A.; Sepulchre, R. Synchronization and balancing on the N-torus. Syst. Control Lett. 2007, 56, 335–341. [Google Scholar] [CrossRef]
- Sarlette, A.; Sepulchre, R. Consensus Optimization on Manifolds. SIAM J. Control Optim. 2009, 48, 56–76. [Google Scholar] [CrossRef]
- Sepulchre, R.; Paley, D.A.; Leonard, N.E. Stabilization of Planar Collective Motion with Limited Communication. IEEE Trans. Autom. Control 2008, 53, 706–719. [Google Scholar] [CrossRef]
- Sarlette, A.; Sepulchre, R. Synchronization on the circle. In The Complexity of Dynamical Systems: A Multi-Disciplinary Perspective; Dubbeldam, J., Green, K., Lenstra, D., Eds.; Wiley: Hoboken, NJ, USA, 2011. [Google Scholar]
- Sarlette, A.; Tuna, S.E.; Blondel, V.D.; Sepulchre, R. Global synchronization on the circle. IFAC Proc. Vol. 2008, 41, 9045–9050. [Google Scholar] [CrossRef]
- Bertollo, R.; Panteley, E.; Postoyan, R.; Zaccarian, L. Uniform global asymptotic synchronization of Kuramoto oscillators via hybrid coupling. IFAC-PapersOnLine 2020, 53, 5819–5824. [Google Scholar] [CrossRef]
- Drion, G.; Franci, A.; Sepulchre, R. Cellular switches orchestrate rhythmic circuits. Biol. Cybern. 2019, 113, 71–82. [Google Scholar] [CrossRef] [PubMed]
- Lee, J.G.; Sepulchre, R. Rapid synchronization under weak synaptic coupling. In Proceedings of the 2020 59th IEEE Conference on Decision and Control (CDC), Jeju, Republic of Korea, 14–18 December 2020; pp. 6168–6173. [Google Scholar] [CrossRef]
- Lee, J.G.; Sepulchre, R.J. Rapid and robust synchronization via weak synaptic coupling. Automatica 2024, 160, 111416. [Google Scholar] [CrossRef]
- Somers, D.; Kopell, N. Rapid synchronization through fast threshold modulation. Biol. Cybern. 1993, 68, 393–407. [Google Scholar] [CrossRef] [PubMed]
- Mostajeran, C.; Lee, J.G.; Van Goffrier, G.; Sepulchre, R. Target formation on the circle by monotone system design. In Proceedings of the 2021 60th IEEE Conference on Decision and Control (CDC), Austin, TX, USA, 14–17 December 2021; pp. 7106–7111. [Google Scholar] [CrossRef]
- Forni, F.; Sepulchre, R. Differentially Positive Systems. IEEE Trans. Autom. Control 2016, 61, 346–359. [Google Scholar] [CrossRef]
- Mostajeran, C.; Sepulchre, R. Positivity, Monotonicity, and Consensus on Lie Groups. SIAM J. Control Optim. 2018, 56, 2436–2461. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).