1. Introduction
New-generation mobile communication systems, 5G NR networks, are worldwide-deployed communication systems. The 5G wireless system, which is not the straightforward evolution of traditional 4G cellular networks, is developed as a multipurpose mobile network with many new service functionalities [
1]. 5G networks can provide not only traditional voice and data communication but also numerous new use cases, applications for various industries, and connectivity for devices and applications across society [
2,
3]. Examples include vehicle-to-vehicle and vehicle-to-infrastructure communication, industrial automation, health services, smart cities, and smart homes [
4,
5]. Compared to 4G LTE, 5G NR and the future development of B5G systems have introduced a series of technical indicators. To meet these performance requirements, 5G systems will leverage various emerging technologies, such as heterogeneous networks (HetNets) [
6,
7], massive multiple-input multiple-output (mMIMO) [
8], millimeter-wave (mmWave) communication [
9,
10], device-to-device (D2D) communication [
11,
12], machine-to-machine (M2M) communication [
13], reconfigurable intelligent surfaces (RISs) [
14], and network slicing [
15], among others.
D2D and M2M communications have many different characteristics compared to the traditional communication services designed for human interaction. For instance, the communication among many sensors and controllers in closed-loop control systems of automated industries requires a maximum latency of 5 ms and a reliable packet error rate ranging from
to
[
16]. In terms of traffic safety, the packet error rate cannot exceed
. These typical applications involve short data packets (code length ranges from several hundred to one thousand) and impose very high requirements on latency and reliability. For the applications targeting these machine communications, various solutions have been proposed, including fewer symbols in OFDM signal packets, reducing transmission time. The theoretical limit for the transmission of these short data packets depends on the specific transmission environments and the technologies employed.
Shannon’s limit provides the theoretical maximum performance when the encoding blocklength tends towards infinity. However, in practical situations, Shannon’s limit does not apply to the performance of moderate-length codes [
17]. The finite-blocklength performance bounds in binary input additive white Gaussian noise (BIAWGN) channels have adequately addressed this issue. Recently, numerous significant advancements related to finite-blocklength analysis have emerged. Ref. [
18] leverages the property of joint convexity to address a broad spectrum of use cases, thereby facilitating the efficient resolution of joint optimization problems in multi-user environments in the finite-blocklength regime. In [
19], Behrooz Makki derives closed-form expressions for message-decoding probabilities, throughput, expected delay, and error probability in hybrid automatic repeat request (HARQ) configurations. Moreover, the expectation and variance of the maximum achievable rate in a mMIMO system with a finite blocklength are rigorously analyzed [
20]. However, the finite-blocklength performance analysis is not suitable for higher-order modulation schemes, for which effective solutions have been proposed in the existing literature [
21,
22,
23]. Moreover, to ensure transmission reliability while also meeting low-latency constraints, a limited number of retransmissions is typically required in practical wireless networks. Combining rate-compatible coding and incremental redundancy retransmission schemes, the performance analysis of finite-length coded retransmission with high-order modulation is an urgent issue that needs to be addressed.
In this paper, we analyze the performance of finite-length coded modulation in a retransmission scenario when rate-compatible code is modulated and transmitted using different modulation schemes in the first and second transmissions. The remaining structure of this paper is represented as follows. Firstly, we review the theoretical formulas for predicting the performance of finite-length coded modulation and provide a brief explanation of the calculation of key parameters in this formula under retransmission scenarios. Next, we revisit the model for tuning on the theoretical prediction formula and elaborate on the usage of the model. Here, we refine this method to make it more general. Finally, through simulation results, we demonstrate the good adaptability of this calibration model to retransmission scenarios. Based on the simulation results, we also offer some recommendations for the retransmission approach of coded modulation.
3. Practical Application with Retransmission
In this section, we consider the coded modulation retransmission scenario in incremental redundancy (IR) HARQ and the calculations of key parameters with the theoretical formula and a calibration model proposed by Eva C. Song and Guosen Yue [
26], which are easy to use and have extremely good accuracy.
When the first segment of a rate-compatible coding scheme with a high-rate code of length n fails to be received, the transmitter then sends the redundancy version of coded bits with identical length n to the receiving end, resulting in a half-rate code of length for decoding. During retransmission, the modulation order is usually lowered according to the specific modulation and coding scheme (MCS), such as the MCS table in 5G NR, thereby better handling errors and enhancing the robustness of transmission.
In [
26], the calculations of
C and
V for the parallel complex Gaussian channels with an
m-QAM input are provided by (15) and (16), respectively. Similarly, we can consider the coded modulation in the retransmission scenario as the receiver simultaneously receiving two equal-length coded blocks from a rate-compatible coding scheme with different modulations
-QAM and
-QAM over the same channel.
Therefore, in this scenario,
C and
V in (
9) are computed by
where
and
can get by (
16) and (
17) on the constellations of
-QAM and
-QAM, respectively. The proof of
C and
V is provided in
Appendix A.
In terms of practical coding, ref. [
26] proposes the following models:
where
and
can get by (
18) and (
19), respectively.
refers to the gap between the theoretical capacity and the rate that practical coding can achieve when the blocklength is finite.
is the correction parameter for the channel dispersion
V.
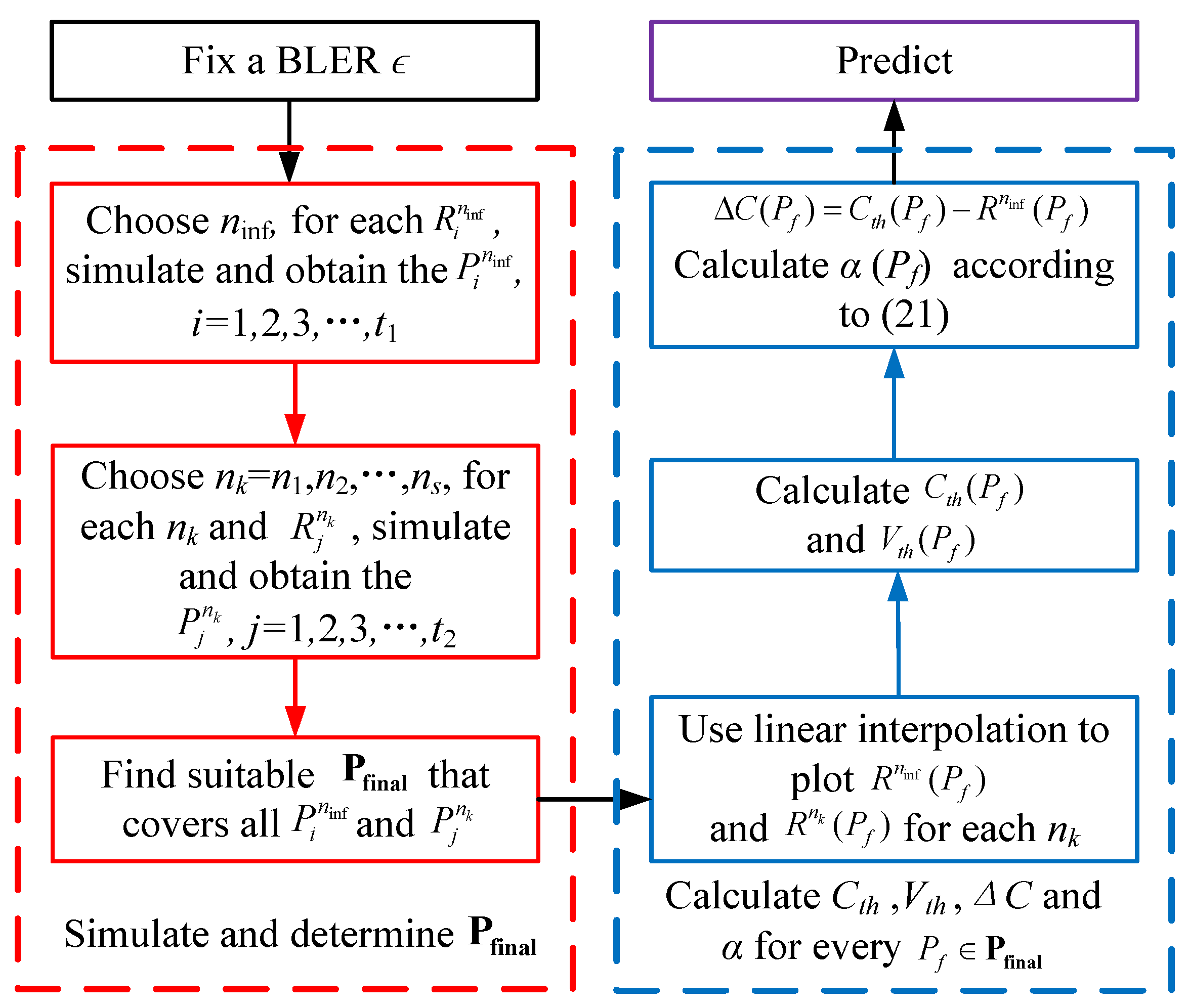
We follow the flowchart shown in
Figure 1 to calculate the parameters in (
20). Firstly, select a targeting BLER
and a sufficiently long blocklength
as an approximation for infinite blocklength, where a practical rate-compatible coding scheme is employed for the necessary initial simulation, such as LTE-turbo codes and 5G-LDPC codes. Then, for each specific rate
, obtain the
required to achieve the BLER
based on simulation. Next, select several short blocklengths
for tuning. For each
and specific rate
, obtain the
required to achieve the BLER
based on simulation.
We simulate to obtain the
and
variables using the following method: Given the modulation scheme, code blocklength
or
, and rate
R, we vary the values of SNR to obtain a set of data for different SNRs and BLERs
. Then, around the given BLER
, we identify two different BLERs which are the nearest neighbors
and perform linear interpolation based on their corresponding SNRs
and
to obtain the SNR
corresponding to the desired BLER
. The linear interpolation formula is as follows.
Let the
be the desired BLER; then, we can get the SNR
by (
21).
Next, based on the
and
obtained from above, determine a smallest range (or slightly larger) of
to cover all the
and
. For example, if we simulate to obtain
(dB) and
(dB), then we can choose
(dB). After that, use linear interpolation to connect all the
and
to get
and
in the range
. Then, calculate the theoretical channel capacity
and the theoretical channel dispersion
according to (
18) and (
19), respectively. Next, calculate
and for every
, find
that minimizes (
22) to get
.
Finally, for any given code length
n and
, compute
C and
V according to (
18) and (
19), and obtain
and
from the steps above. Predict
R by using (
20), which is shown in Algorithm 1.
| Algorithm 1: Calculation algorithm of the model to predict R |
Input: , , , , Output: R - 1
Fix a BLER - 2
Simulate to get based on , , - 3
Simulate to get based on , , - 4
Choose a range that covers all the and - 5
Use linear interpolation to connect all the and to get and in the range - 6
Calculate , for - 7
for - 8
For every , calculate that minimizes ( 22) to get - 9
returnfor every
|
The above method incorporates some modifications to the method proposed in [
26]. When using (
22), the SNR required for calculating each
is the same, but the simulated SNR often varies for different selected
and
. Therefore, after obtaining the simulation data points, we select a range
to unify the different SNRs obtained from the simulation that required in the formula.
4. Numerical Example
In this section, we demonstrate that the proposed model is also applicable to the scenario of retransmission and we analyze the results with different coded modulation combinations. In the following examples, we always use the rate-compatible coding scheme based on 5G-LDPC codes and BP decoding in the transmitter and receiver. Assume that 16-QAM and QPSK are used in two transmissions, respectively, where the coded bits in the first half and the second half of each encoding segment are modulated by 16-QAM and QPSK, respectively.
In our simulations, the rate
R is computed by
where
is the original code rate,
and
refer to the modulation orders for the two segments. In this example, an LDPC code with a code rate of
, 16-
, and
are employed in the two transmissions; thus, the rate here is
.
Since the number of message bits remains the same after retransmission, the code length becomes twice as long, and the highest code rate of 5G-LDPC codes is in the first transmission. Then, after retransmission with , the highest rate here is .
We select as an approximation for infinite code length, which approaches the maximum length 8448 of information bits in the 5G-LDPC coding scheme, with , for tuning. We choose the code rates like and to make the code with length 360 have an integer number of information bits. Then, we predict the retransmission performance of the coded modulation with .
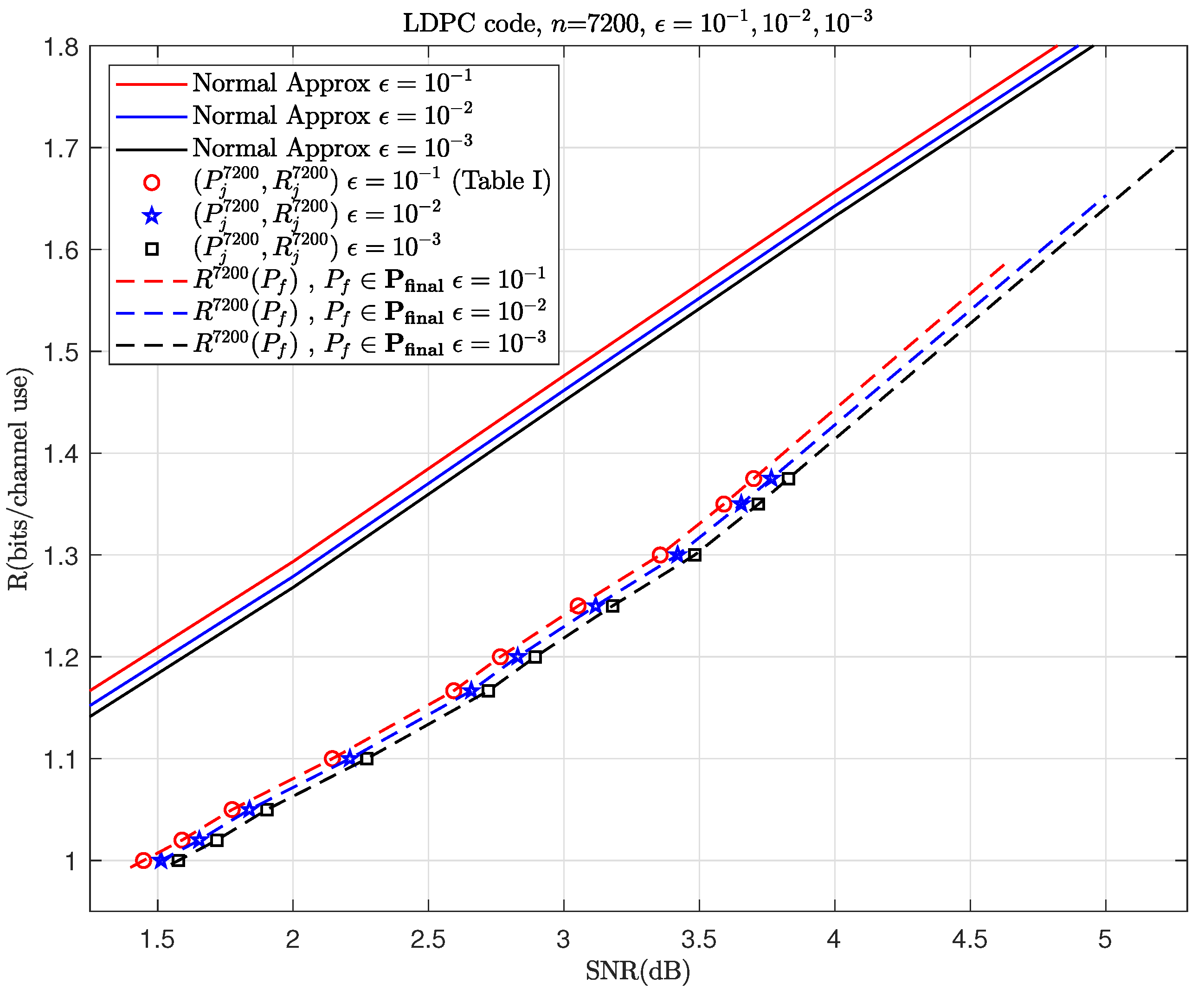
With this example, let us go through the steps outlined in Algorithm 1. Choose a fixed BLER
and then simulate to obtain
Figure 2 and
Figure 3a,b. In this example,
(dB) can cover all the simulation points
and
. Then,
Table 1 and
Table 2 calculate
and
, respectively. Finally, using (
20) and the previously obtained parameters, we can predict
R. By repeating the steps mentioned above for
and
, we can get the results shown in
Figure 4. As shown in
Figure 4, the prediction performance of this model is also very good in the retransmission scenario with a moderate blocklength and different modulations.
To more clearly distinguish between the simulation data points used before prediction and those used to validate the accuracy of the prediction afterward, we plot the simulation data points required before prediction in
Figure 2 and
Figure 3a,b as hollow points and the simulation data points used for validation after prediction in
Figure 4,
Figure 5,
Figure 6 and
Figure 7 as solid points, respectively. The predicted curves in
Figure 4,
Figure 5,
Figure 6 and
Figure 7 are derived from the initial simulations, Algorithm 1, as well as the analytical formulas. The simulation points on the predicted curves are obtained by selecting certain SNRs and spectral efficiencies within the interval after predicting the performance and then conducting simulations for verification. The comparisons between the simulated points and the predicted curves show very small discrepancies. When the SNR is the same, the simulation value may be a little lower than the prediction curve.
The calculation environments for simulations and predictions are the same. We use MATLAB 2023b to calculate, use MATLAB’s built-in functions ldpcEncode and ldpcDecode for encoding and decoding LDPC codes, use MATLAB’s built-in functions qammod and qamdemod for modulation and demodulation, and we use MATLAB’s built-in functions awgn to add noise.
The following examples show the prediction results of moderate-blocklength coded retransmission with other modulation schemes, like 1024-
and 256-
, in the first and the second transmissions. They are shown in
Figure 5,
Figure 6 and
Figure 7, respectively.
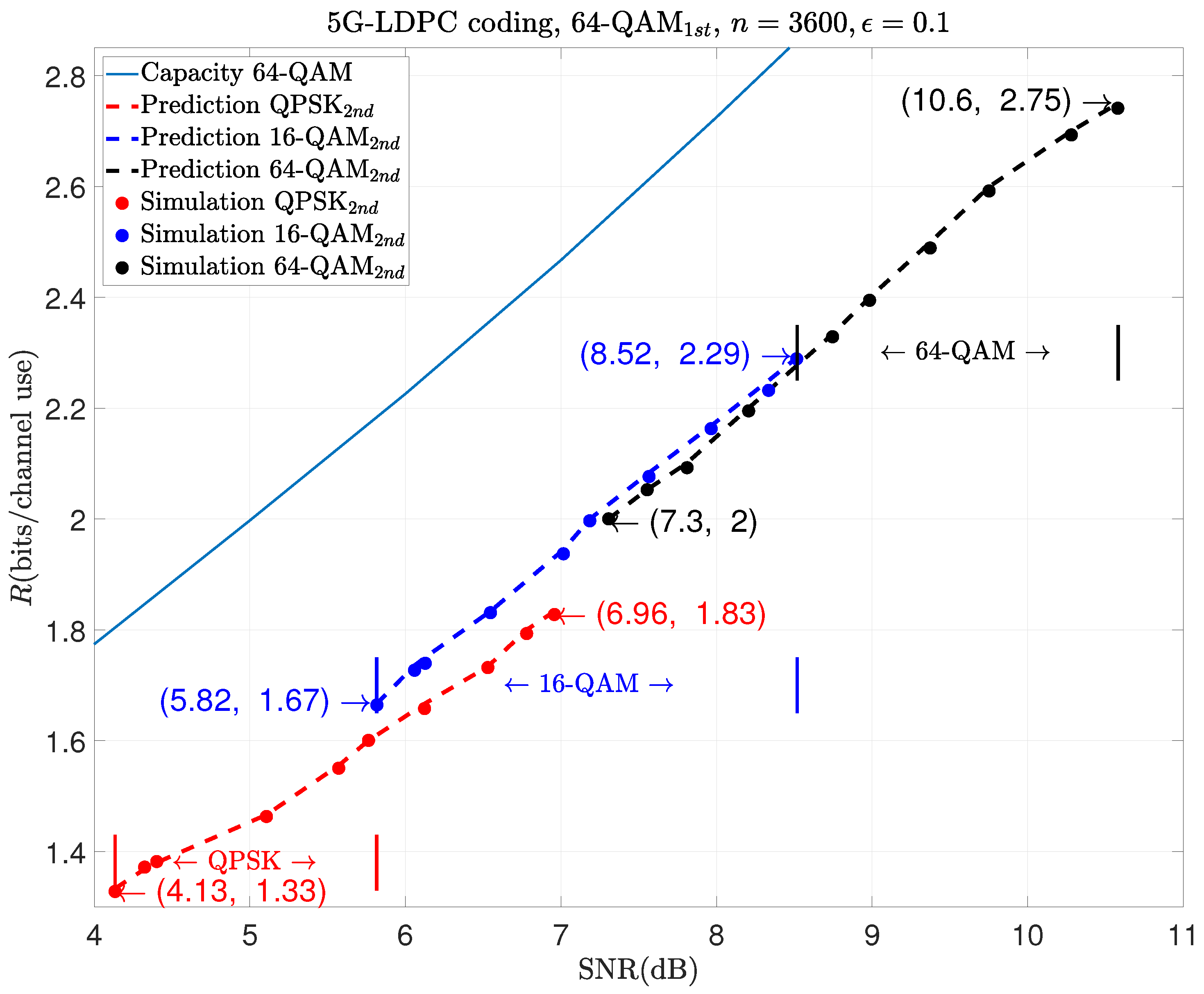
As shown in these figures, different combinations of modulation schemes can cover different ranges of rates. In
Figure 5, we can see that the combination of 64-QAM and QPSK covers the rate range from 1.33 to 1.83 in the SNR from 4.13 dB to 6.96 dB; that of 64-QAM and 16-QAM covers the rate range from 1.67 to 2.29 in the SNR from 5.82 dB to 8.52 dB; and 64-QAM combined with 64-QAM covers the rate range from 2 to 2.75 in the SNR from 7.3 dB to 10.6 dB.
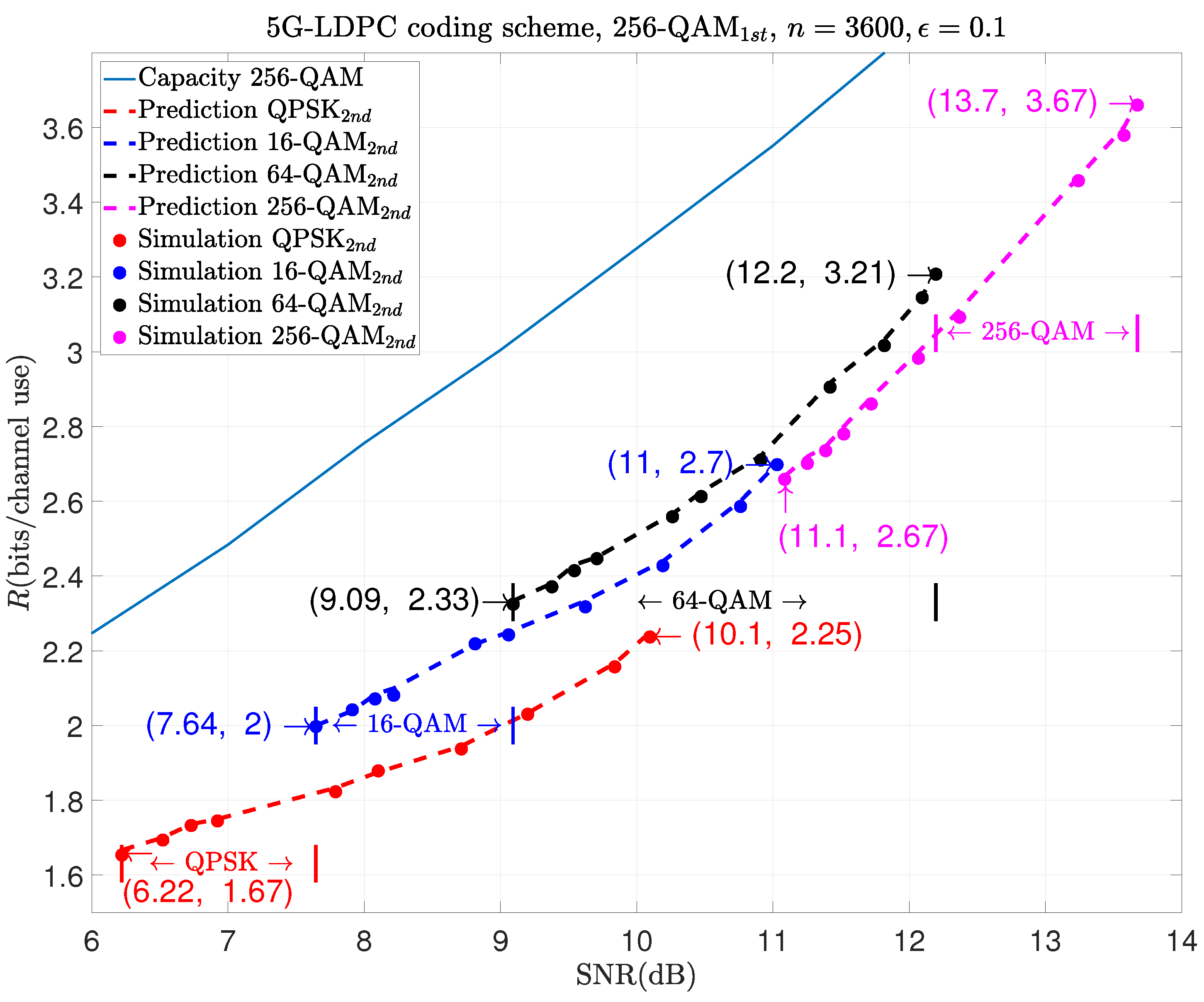
The results in
Figure 6 show that if 256-QAM is used for the initial transmission and if the aim for a retransmission is to achieve the rate range between 2 and 2.25, we can use QPSK or 16-QAM for the retransmission. In this case, the required SNR range is between 7.64 dB and 10.1 dB. Similarly, if 16-QAM or 64-QAM is used for the retransmission, the corresponding SNR range is between 9.09 dB and 11 dB, resulting in a rate range of 2.33 to 2.7. If 256-QAM is still used during retransmission, it will cover a rate range from 2.67 to 3.67 in the SNR from 11.1 dB to 13.7 dB.
However, we can also see in these three figures that using the same modulation scheme during retransmission as before results in poorer performance. For example, in
Figure 7, to achieve the same rate like
, the combination of 1024-QAM and 1024-QAM performs about 0.34 dB poorer than that of 1024-QAM and 256-QAM.
The results above can guide us in selecting different modulation schemes based on varying data rate requirements during retransmission. For example, as illustrated in
Figure 7, when using 1024-QAM for the initial transmission, if the rate is between 2.33 and 2.67, it would be better to use 16-QAM for retransmission. This is because the minimum code rate of LDPC code is 1/3, and the minimum rate of 1024-QAM combined with 64-QAM is
. Similarly, if the rate is between 3 and 4.12, it would be better to use 256-QAM for retransmission because the maximum code rate after retransmission is
, and the maximum rate of 1024-QAM combined with 256-QAM is
. If the rate is greater than 4.12, we only use 1024-QAM to retransmit. Similar conclusions can be drawn for 64-QAM and 256-QAM in
Figure 5 and
Figure 6.
5. Efficiency Analysis
Figure 8 takes the MCS of 5G NR with the BG1 matrix as an example, where we select a set of coding parameters with blocklengths ranging from
(
) to the maximum length of
(
). The ranges of code rates, respectively, cover [
,
] and [
,
] in the first transmission and retransmission with a total
different code rates. Increasing the value of
can further fine-tune the prediction accuracy. For the system-level simulations that are crucial for the design of 5G networks, it is generally required to obtain the link-level BLER performance metrics for all data points in
Figure 8 through simulations. Then, for the specific link settings of code rates and blocklengths, the BLER performances can be directly obtained via linear interpolation with the nearby data points. For future mobile communication systems, with wider ranges of code rates and blocklengths and lower BLER targets, the performance evaluations for link-level simulations with multiple retransmissions will significantly increase the computational complexity. Our proposed performance prediction scheme can effectively reduce the computational load while ensuring evaluation accuracy.
In the above example of MCSs shown in
Figure 8, once the
-QAM,
-QAM and BLER are determined before or after retransmission, we only need to simulate all the rate data for three sets of blocklengths (the blue points in three red rectangle boxes in
Figure 8) to predict the rates for any other blocklength (other blue points in
Figure 8). Hence, when the BLERs and SNRs for the coded modulation combinations with all the different blocklengths and code rates are required for system-level simulations, using our algorithm can significantly improve the efficiency of performance evaluations. As shown in
Figure 8, assuming that a single testing of BLER
evaluation for a code with
requires a time of
, then obtaining one set of data requires a time of
for all code rates considered before or after retransmission. As the blocklength increases, the simulation time will also increase linearly, which means that the simulation testings of performance evaluation for the codes with
and
require a computation time of
and
, respectively. Therefore, the total simulation time required to obtain all the data needed for the performance prediction of MCSs with
-QAM and
-QAM is
. Since the time required for the calculations of
and
is negligible compared to that of simulation tests for performance evaluations, the total computational complexity needed to complete the entire prediction can be approximately evaluated by
. Then, if we need the rate data of codes from
to 8448 according to all the lifting values of 5G-LDPC codes shown in
Figure 8, the total computational complexity required for a brute-force Monte Carlo simulation should be about
, which is clearly greater than
. Since each modulation combination for retransmission requires a separate simulation, this algorithm can significantly reduce the computational complexity when a large amount of SNR-R relationship data corresponding to various blocklengths are needed, given a specific BLER
.